3.6 KiB
3.6 KiB
Neutrino physics 101
Table of Contents
- Malware analysis
- Threat Intelligence
- Cyber kill chain
- Indicators Of Compromise (IOC)
- Yara Rules
- References MITRE ATT&CK Matrix
- Links
Malware analysis
The initial vector
The initial vector is an malicious document using a macro. As the first look, we can note some constant variables can be replace and deletefor improvement the reading of the code.
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHOneMask = 16515072
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHTwoMask = 258048
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHThreeMask = 4032
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHFourMask = 63
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHighMask = 16711680
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHMidMask = 65280
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHLowMask = 255
Private Const MNAJSAQQQQQQ18 = 262144
Private Const MNAJSAQQQQQQ12 = 4096
Private Const MNAJSAQQQQQQ6 = 64
Private Const MNAJSAQQQQQQ8 = 256
Private Const MNAJSAQQQQQQ16 = 65536
We can see the both functions for auto-open the macro in the reading of the document for the Word and Excel document. This is for a common code for the both vectors or for reduce the rate of the detection, hard to say it.
Sub AutoOpen()
AddSpace
End Sub
Private Sub Workbook_Open()
AddSpace
End Sub
Threat Intelligence
Cyber kill chain
The process graph resume cyber kill chains used by the attacker :
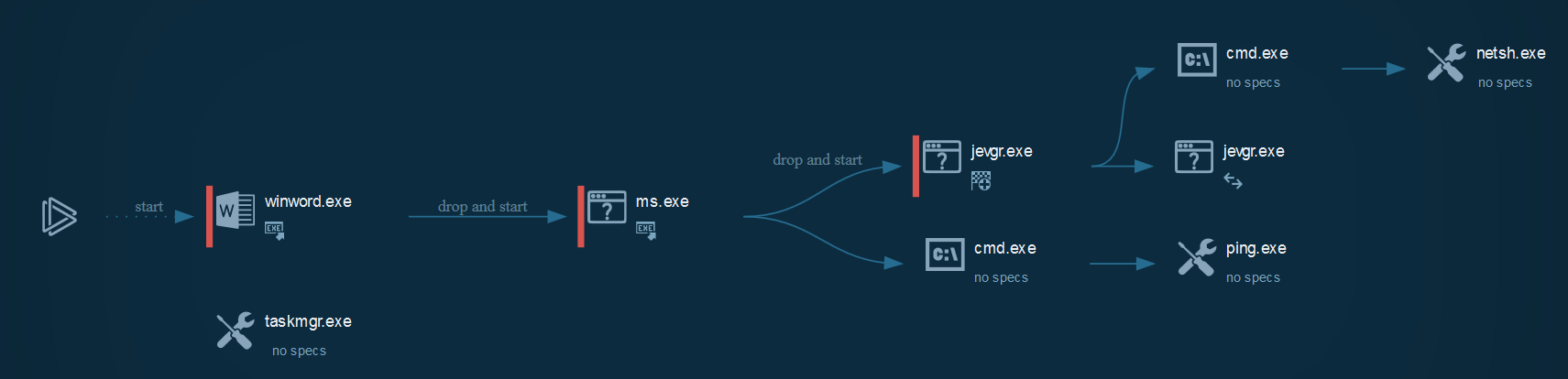
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|
The IOC can be exported in JSON
References MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|