Gadgets - Raspberry Pi + Arduino + Logic Analyzer
parent
8a5e389336
commit
663bdb06f1
|
|
@ -1,5 +1,7 @@
|
||||||
# 🔌 Hardware All The Things
|
# 🔌 Hardware All The Things
|
||||||
|
|
||||||
|
An alternative display version is available at [Hardware All The Things - Web version](https://swisskyrepo.github.io/HardwareAllTheThings/).
|
||||||
|
|
||||||
## Welcome to the Hardware wiki!
|
## Welcome to the Hardware wiki!
|
||||||
|
|
||||||
Welcome to our comprehensive Hardware Security Wiki, a curated collection of valuable payloads and bypass techniques tailored for Hardware and IoT Security. This repository serves as a dynamic and collaborative space, encouraging contributions from security enthusiasts and professionals alike.
|
Welcome to our comprehensive Hardware Security Wiki, a curated collection of valuable payloads and bypass techniques tailored for Hardware and IoT Security. This repository serves as a dynamic and collaborative space, encouraging contributions from security enthusiasts and professionals alike.
|
||||||
|
|
@ -18,6 +20,6 @@ Our goal is to foster a community-driven platform where individuals can share, l
|
||||||
We believe in the power of community and collective knowledge. Therefore, we warmly invite you to contribute your unique payloads, bypass techniques, and innovative strategies to enrich our repository.
|
We believe in the power of community and collective knowledge. Therefore, we warmly invite you to contribute your unique payloads, bypass techniques, and innovative strategies to enrich our repository.
|
||||||
Your contributions help keep this project alive and kicking, ensuring that we can continue to bring you the latest and greatest in hardware and IoT security.
|
Your contributions help keep this project alive and kicking, ensuring that we can continue to bring you the latest and greatest in hardware and IoT security.
|
||||||
|
|
||||||
|
You can also share the project and contribute with a Github Sponsorship.
|
||||||
[](https://twitter.com/intent/tweet?text=Hardware%20All%20The%20Things,%20a%20curated%20collection%20of%20valuable%20payloads%20and%20bypass%20techniques%20tailored%20for%20Hardware%20and%20IoT%20Security%20-%20by%20@pentest_swissky&url=https://swisskyrepo.github.io/HardwareAllTheThings/)
|
[](https://twitter.com/intent/tweet?text=Hardware%20All%20The%20Things,%20a%20curated%20collection%20of%20valuable%20payloads%20and%20bypass%20techniques%20tailored%20for%20Hardware%20and%20IoT%20Security%20-%20by%20@pentest_swissky&url=https://swisskyrepo.github.io/HardwareAllTheThings/)
|
||||||
|
|
||||||
[](https://github.com/sponsors/swisskyrepo)
|
[](https://github.com/sponsors/swisskyrepo)
|
||||||
|
|
@ -18,6 +18,6 @@ Our goal is to foster a community-driven platform where individuals can share, l
|
||||||
We believe in the power of community and collective knowledge. Therefore, we warmly invite you to contribute your unique payloads, bypass techniques, and innovative strategies to enrich our repository.
|
We believe in the power of community and collective knowledge. Therefore, we warmly invite you to contribute your unique payloads, bypass techniques, and innovative strategies to enrich our repository.
|
||||||
Your contributions help keep this project alive and kicking, ensuring that we can continue to bring you the latest and greatest in hardware and IoT security.
|
Your contributions help keep this project alive and kicking, ensuring that we can continue to bring you the latest and greatest in hardware and IoT security.
|
||||||
|
|
||||||
|
You can also share the project and contribute with a Github Sponsorship.
|
||||||
[](https://twitter.com/intent/tweet?text=Hardware%20All%20The%20Things,%20a%20curated%20collection%20of%20valuable%20payloads%20and%20bypass%20techniques%20tailored%20for%20Hardware%20and%20IoT%20Security%20-%20by%20@pentest_swissky&url=https://swisskyrepo.github.io/HardwareAllTheThings/)
|
[](https://twitter.com/intent/tweet?text=Hardware%20All%20The%20Things,%20a%20curated%20collection%20of%20valuable%20payloads%20and%20bypass%20techniques%20tailored%20for%20Hardware%20and%20IoT%20Security%20-%20by%20@pentest_swissky&url=https://swisskyrepo.github.io/HardwareAllTheThings/)
|
||||||
|
|
||||||
[](https://github.com/sponsors/swisskyrepo)
|
[](https://github.com/sponsors/swisskyrepo)
|
||||||
Binary file not shown.
|
After Width: | Height: | Size: 171 KiB |
|
|
@ -1,12 +1,13 @@
|
||||||
# JTAG
|
# JTAG
|
||||||
|
|
||||||
### Summary
|
## Summary
|
||||||
|
|
||||||
* JTAG Pins
|
* JTAG Pins
|
||||||
* JTAGEnum
|
* JTAGEnum
|
||||||
* References
|
* References
|
||||||
|
|
||||||
### JTAG Pins
|
|
||||||
|
## JTAG Pins
|
||||||
|
|
||||||
> Allows testing, debugging, firmware manipulation and boundary scanning
|
> Allows testing, debugging, firmware manipulation and boundary scanning
|
||||||
|
|
||||||
|
|
@ -30,11 +31,13 @@ $ avarice --program --file test.elf --part atmega128 --jtag /dev/ttyUSB0 :4444
|
||||||
$ avrdude -p m128 -c jtagmkI –P /dev/ttyUSB0 -U flash:r:”/home/avr/flash.bin":r
|
$ avrdude -p m128 -c jtagmkI –P /dev/ttyUSB0 -U flash:r:”/home/avr/flash.bin":r
|
||||||
```
|
```
|
||||||
|
|
||||||
### Enumeration methods
|
|
||||||
|
## Enumeration methods
|
||||||
|
|
||||||
For enumeration methods see [Enumeration/JTAG](/enumeration/jtag/)
|
For enumeration methods see [Enumeration/JTAG](/enumeration/jtag/)
|
||||||
|
|
||||||
### References
|
|
||||||
|
## References
|
||||||
|
|
||||||
* [JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices by Dylan Ayrey](https://www.praetorian.com/blog/jtagulator-vs-jtagenum-tools-for-identifying-jtag-pins-in-iot-devices?edition=2019)
|
* [JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices by Dylan Ayrey](https://www.praetorian.com/blog/jtagulator-vs-jtagenum-tools-for-identifying-jtag-pins-in-iot-devices?edition=2019)
|
||||||
* [JTAG PIN Identification - February 21, 2017](https://just2secure.blogspot.com/2017/02/jtag-pin-identification.html)
|
* [JTAG PIN Identification - February 21, 2017](https://just2secure.blogspot.com/2017/02/jtag-pin-identification.html)
|
||||||
|
|
|
||||||
|
|
@ -1,20 +1,5 @@
|
||||||
# UART
|
# UART
|
||||||
|
|
||||||
## Table of contents
|
|
||||||
|
|
||||||
* [What is it ?](#what-is-it-)
|
|
||||||
* [Identifying UART ports](#identifying-uart-ports)
|
|
||||||
* [Using a multimeter](#using-a-multimeter)
|
|
||||||
* [Using a logic analyzer](#using-a-logic-analyzer)
|
|
||||||
* [Connect to serial port](#connect-to-serial-port)
|
|
||||||
* [WARNING](#warning)
|
|
||||||
* [Examples](#examples)
|
|
||||||
* [Connection using a USB to TTL](#connection-using-a-usb-to-ttl)
|
|
||||||
* [Detect the baud rate](#detect-the-baud-rate)
|
|
||||||
* [Interact with UART](#interact-with-uart)
|
|
||||||
* [UART over BLE](#uart-over-ble)
|
|
||||||
* [Examples](#examples)
|
|
||||||
|
|
||||||
## What is it ?
|
## What is it ?
|
||||||
|
|
||||||
UART stands for Universal asynchronous receiver transmitter. Used for serial communications over a computer or peripheral device serial port.
|
UART stands for Universal asynchronous receiver transmitter. Used for serial communications over a computer or peripheral device serial port.
|
||||||
|
|
@ -27,6 +12,7 @@ Generally, the line is held high (at a logical 1 value) while UART is in idle st
|
||||||
|
|
||||||
We call the most common configuration **8N1**: eight data bits, no parity, and 1 stop bit.
|
We call the most common configuration **8N1**: eight data bits, no parity, and 1 stop bit.
|
||||||
|
|
||||||
|
|
||||||
## Identifying UART ports
|
## Identifying UART ports
|
||||||
|
|
||||||
A UART pinout has **four** ports:
|
A UART pinout has **four** ports:
|
||||||
|
|
@ -51,37 +37,47 @@ Keep in mind that some devices **emulate** UART ports by programming the General
|
||||||
It is advised to capture the communication at **4 times the baudrate speed**, to avoid decoding issues.
|
It is advised to capture the communication at **4 times the baudrate speed**, to avoid decoding issues.
|
||||||
|
|
||||||
### Using a multimeter
|
### Using a multimeter
|
||||||
|
|
||||||
#### GNR pin
|
#### GNR pin
|
||||||
|
|
||||||
First identify the GRN pin, by using the multimeter in continuity mode.
|
First identify the GRN pin, by using the multimeter in continuity mode.
|
||||||
|
|
||||||
Place the black probe on any grounded metallic surface, be it a part of the tested PCB or not. Then place the red probe on each of the ports. When you hear a beeping sound, you found a GND pin.
|
Place the black probe on any grounded metallic surface, be it a part of the tested PCB or not. Then place the red probe on each of the ports. When you hear a beeping sound, you found a GND pin.
|
||||||
|
|
||||||
#### VCC pin
|
#### VCC pin
|
||||||
|
|
||||||
Turn the multimeter to the DC voltage mode in and set it up to 20V of voltage. Keep the black probe on a grounded surface. Place the red probe on a suspected pin and turn on the device.
|
Turn the multimeter to the DC voltage mode in and set it up to 20V of voltage. Keep the black probe on a grounded surface. Place the red probe on a suspected pin and turn on the device.
|
||||||
|
|
||||||
If the multimeter measures a constant voltage of either 3.3V or 5V, you've found the VCC pin.
|
If the multimeter measures a constant voltage of either 3.3V or 5V, you've found the VCC pin.
|
||||||
|
|
||||||
#### TX pin
|
#### TX pin
|
||||||
|
|
||||||
Keep the multimeter mode at DC voltage of 20V or less, and leave the black probe in a grounded surface. Move the red probe to the suspected pin and power cycle the device. If the voltage fluctuates for a few seconds and then stabilizes at the VCC value, you've most likely found the TX pin.
|
Keep the multimeter mode at DC voltage of 20V or less, and leave the black probe in a grounded surface. Move the red probe to the suspected pin and power cycle the device. If the voltage fluctuates for a few seconds and then stabilizes at the VCC value, you've most likely found the TX pin.
|
||||||
|
|
||||||
This behavior happens because, during bootup, the device sends serial data through that TX pin for debugging purposes. Once it finishes booting, the UART line goes idle.
|
This behavior happens because, during bootup, the device sends serial data through that TX pin for debugging purposes. Once it finishes booting, the UART line goes idle.
|
||||||
|
|
||||||
#### Rx pin
|
#### Rx pin
|
||||||
|
|
||||||
If you've already identified the rest of the UART pins, the nearby fourth pin is most likely the RX pin.
|
If you've already identified the rest of the UART pins, the nearby fourth pin is most likely the RX pin.
|
||||||
|
|
||||||
Otherwise, you can identify it because it has the lowest voltage fluctuation and lowest overall value of all the UART pins.
|
Otherwise, you can identify it because it has the lowest voltage fluctuation and lowest overall value of all the UART pins.
|
||||||
|
|
||||||
|
|
||||||
### Using a logic analyzer
|
### Using a logic analyzer
|
||||||
|
|
||||||
A logic analyzer is an electronic instrument that captures and displays multiple signals from a digital system or digital circuit.
|
A logic analyzer is an electronic instrument that captures and displays multiple signals from a digital system or digital circuit.
|
||||||
|
|
||||||
To find the UART pins we will connect the pins to a logic analyzer and look for data being transmitted.
|
To find the UART pins we will connect the pins to a logic analyzer and look for data being transmitted.
|
||||||
|
|
||||||
|
|
||||||
#### Hardware setup
|
#### Hardware setup
|
||||||
|
|
||||||
Make sure any system you're testing is **powered off** when you connect the logic analyzer's probes to it **to avoid short-circuiting**.
|
Make sure any system you're testing is **powered off** when you connect the logic analyzer's probes to it **to avoid short-circuiting**.
|
||||||
|
|
||||||
* Connect the suspected TX pin to any channel of the logic analyzer.
|
* Connect the suspected TX pin to any channel of the logic analyzer.
|
||||||
* Connect one of your logic analyzer's GND pins to the PCB that you're testing GND pins so they **share a common ground**.
|
* Connect one of your logic analyzer's GND pins to the PCB that you're testing GND pins so they **share a common ground**.
|
||||||
|
|
||||||
|
|
||||||
#### Software setup
|
#### Software setup
|
||||||
|
|
||||||
##### PulseView / Sigrok
|
##### PulseView / Sigrok
|
||||||
|
|
@ -128,31 +124,36 @@ Now try with the popular baud rates with both the suspected pins and try to comp
|
||||||
|
|
||||||
|
|
||||||
## Connect to serial port
|
## Connect to serial port
|
||||||
|
|
||||||
### WARNING
|
### WARNING
|
||||||
It's not a big deal if you confuse the UART RX and TX ports with each other, because you can easily swap the wires connecting to them without any consequences. But confusing the VCC with the GND and connecting wires to them incorrectly **might fry the circuit**.
|
It's not a big deal if you confuse the UART RX and TX ports with each other, because you can easily swap the wires connecting to them without any consequences. But confusing the VCC with the GND and connecting wires to them incorrectly **might fry the circuit**.
|
||||||
|
|
||||||
### Examples
|
### Examples
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
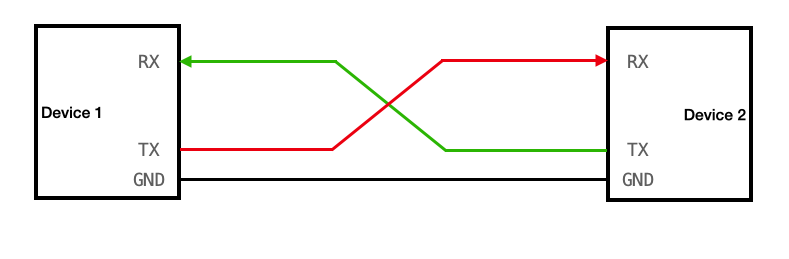
|

|
||||||
|
|
||||||
### Connection using a USB to TTL
|
### Connection using a USB to TTL
|
||||||
|
|
||||||
Once the ports are connected, plug the adapter into your computer. You now need to find the **device file descriptor**. To do that enter the following command : `sudo dmesg`.
|
Once the ports are connected, plug the adapter into your computer. You now need to find the **device file descriptor**. To do that enter the following command : `sudo dmesg`.
|
||||||
|
|
||||||
Typically, it will be assigned to `/dev/ttyUSB0` **if you don't have any other peripheral devices attached**.
|
Typically, it will be assigned to `/dev/ttyUSB0` **if you don't have any other peripheral devices attached**.
|
||||||
|
|
||||||
Under Ubuntu or Debian, a non-root user cannot have access to serial ports such as ttyS0 or ttyUSB0 if he is not a member of the **dialout** group ! The equivalent group on Arch based distributions is **uucp**. In other words, you just have to add yourself to this group to have access.
|
Under Ubuntu or Debian, a non-root user cannot have access to serial ports such as ttyS0 or ttyUSB0 if he is not a member of the **dialout** group ! The equivalent group on Arch based distributions is **uucp**. In other words, you just have to add yourself to this group to have access.
|
||||||
|
|
||||||
Ubuntu or Debian: `sudo usermod -a -G dialout $USER`
|
* Ubuntu or Debian: `sudo usermod -a -G dialout $USER`
|
||||||
|
* Arch based: `sudo usermod -a -G uucp $USER`
|
||||||
|
|
||||||
Arch based: `sudo usermod -a -G uucp $USER`
|
|
||||||
|
|
||||||
### Detect the baud rate
|
### Detect the baud rate
|
||||||
|
|
||||||
#### Most common baud rate
|
#### Most common baud rate
|
||||||
The most common baud rates for UART are `9600`, `19200`, `38400`, `57600` and `115200`.
|
The most common baud rates for UART are `9600`, `19200`, `38400`, `57600` and `115200`.
|
||||||
|
|
||||||
A table of other used but less common baud rates can be found here: [Here](https://lucidar.me/en/serialib/most-used-baud-rates-table/)
|
A table of other used but less common baud rates can be found here: [Here](https://lucidar.me/en/serialib/most-used-baud-rates-table/)
|
||||||
|
|
||||||
|
|
||||||
#### Autodetect the baud rate using a script
|
#### Autodetect the baud rate using a script
|
||||||
Link: [baudrate.py](https://github.com/devttys0/baudrate/blob/master/baudrate.py)
|
Link: [baudrate.py](https://github.com/devttys0/baudrate/blob/master/baudrate.py)
|
||||||
```bash
|
```bash
|
||||||
|
|
@ -166,6 +167,7 @@ pip2.7 install serial
|
||||||
python2.7 baudrate.py -p /dev/ttyUSB0
|
python2.7 baudrate.py -p /dev/ttyUSB0
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
#### Using PulseView
|
#### Using PulseView
|
||||||
|
|
||||||
It is possible to get baudrate using the duration of a bit periode, using PulseView or any other bus analysis tools :
|
It is possible to get baudrate using the duration of a bit periode, using PulseView or any other bus analysis tools :
|
||||||
|
|
@ -183,6 +185,7 @@ The closest common baudrate is : 115200. COnfigure the decoder and you should se
|
||||||

|

|
||||||
|
|
||||||
### Interact with UART
|
### Interact with UART
|
||||||
|
|
||||||
Different command line tools to interact with UART:
|
Different command line tools to interact with UART:
|
||||||
```powershell
|
```powershell
|
||||||
cu -l /dev/ttyUSB0 -s 115200
|
cu -l /dev/ttyUSB0 -s 115200
|
||||||
|
|
@ -211,6 +214,7 @@ with open('/home/audit/Documents/IOT/passwords.lst', 'r') as f:
|
||||||
time.sleep(10)
|
time.sleep(10)
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## UART over BLE
|
## UART over BLE
|
||||||
|
|
||||||
It’s an emulation of serial port over BLE. The UUID of the Nordic UART Service is `6E400001-B5A3-F393-E0A9-E50E24DCCA9E`. This service exposes two characteristics: one for transmitting and one for receiving.
|
It’s an emulation of serial port over BLE. The UUID of the Nordic UART Service is `6E400001-B5A3-F393-E0A9-E50E24DCCA9E`. This service exposes two characteristics: one for transmitting and one for receiving.
|
||||||
|
|
|
||||||
|
|
@ -9,10 +9,12 @@ There are several tools and ways to enumerate JTAG pins. Here are few:
|
||||||
* [Using an Arduino Pro Micro](#jtagenum-with-arduino-or-raspberry-pi)
|
* [Using an Arduino Pro Micro](#jtagenum-with-arduino-or-raspberry-pi)
|
||||||
* [Using an Raspberry Pi Pico](#searching-jtag-pins-with-raspberry-pi-pico)
|
* [Using an Raspberry Pi Pico](#searching-jtag-pins-with-raspberry-pi-pico)
|
||||||
|
|
||||||
|
|
||||||
## Searching JTAG pins with Raspberry PI Pico
|
## Searching JTAG pins with Raspberry PI Pico
|
||||||
|
|
||||||
* Raspberry Pi Pico: [https://github.com/racerxdl/JTAGscan](https://github.com/racerxdl/JTAGscan) made by [szymonh](https://github.com/szymonh/) adapted to RP2040 by [racerxdl](https://github.com/racerxdl/JTAGscan)
|
* Raspberry Pi Pico: [https://github.com/racerxdl/JTAGscan](https://github.com/racerxdl/JTAGscan) made by [szymonh](https://github.com/szymonh/) adapted to RP2040 by [racerxdl](https://github.com/racerxdl/JTAGscan)
|
||||||
|
|
||||||
|
|
||||||
### How does it work?
|
### How does it work?
|
||||||
|
|
||||||
JTAGscan iterates over all defined pins (currently for RP2040, the first 16 pins) searching for TMS, TCK, TDO and TDI.
|
JTAGscan iterates over all defined pins (currently for RP2040, the first 16 pins) searching for TMS, TCK, TDO and TDI.
|
||||||
|
|
@ -22,6 +24,7 @@ It has two approaches:
|
||||||
* Try reading `IDCODE` - Only requires TMS, TCK and TDO so it's faster. Unfortunately not all devices support `IDCODE` command (although most of them do). This doesn't find the TDI pin.
|
* Try reading `IDCODE` - Only requires TMS, TCK and TDO so it's faster. Unfortunately not all devices support `IDCODE` command (although most of them do). This doesn't find the TDI pin.
|
||||||
* Shifting bits in `BYPASS` mode. This can find all pins, but it is slower (since not only you have one more pin to iterate over, but also need to shift "enough" bits through the JTAG Chain).
|
* Shifting bits in `BYPASS` mode. This can find all pins, but it is slower (since not only you have one more pin to iterate over, but also need to shift "enough" bits through the JTAG Chain).
|
||||||
|
|
||||||
|
|
||||||
### Hardware suggestions
|
### Hardware suggestions
|
||||||
|
|
||||||
Any raspberry pi pico board should work fine for scanning JTAG ports. Make sure you check the VCC of the target to see if it is 3.3V. Being other voltage level will require a level-shifter to avoid damage.
|
Any raspberry pi pico board should work fine for scanning JTAG ports. Make sure you check the VCC of the target to see if it is 3.3V. Being other voltage level will require a level-shifter to avoid damage.
|
||||||
|
|
@ -30,6 +33,7 @@ It is also recommended to use series 33 Ohm resistors in series with every teste
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
### Programming the PiPico
|
### Programming the PiPico
|
||||||
|
|
||||||
1. Go to `Releases` and download the `jtagscan-xxxx.zip`
|
1. Go to `Releases` and download the `jtagscan-xxxx.zip`
|
||||||
|
|
@ -38,6 +42,7 @@ It is also recommended to use series 33 Ohm resistors in series with every teste
|
||||||
4. A new "disk" should appear in your machine. Drag the `uf2` file to the disk
|
4. A new "disk" should appear in your machine. Drag the `uf2` file to the disk
|
||||||
5. The raspberry pi pico should reboot and be recognized as a usb-serial converter
|
5. The raspberry pi pico should reboot and be recognized as a usb-serial converter
|
||||||
|
|
||||||
|
|
||||||
### Using
|
### Using
|
||||||
|
|
||||||
Open the detected serial port in your favorite serial terminal application (for example, [PuTTY](https://www.putty.org/))
|
Open the detected serial port in your favorite serial terminal application (for example, [PuTTY](https://www.putty.org/))
|
||||||
|
|
@ -108,7 +113,8 @@ Arduino PIN Layout
|
||||||
|
|
||||||
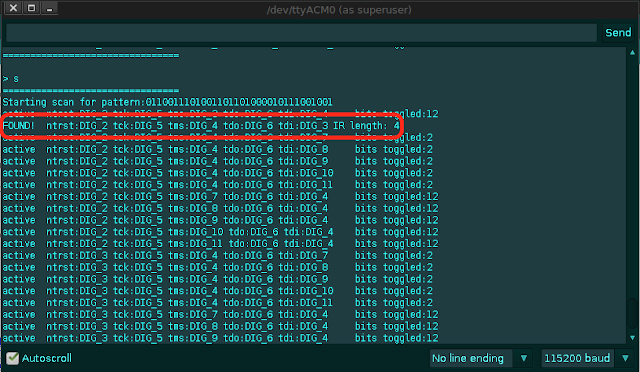
|

|
||||||
|
|
||||||
### References
|
|
||||||
|
## References
|
||||||
|
|
||||||
* [JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices by Dylan Ayrey](https://www.praetorian.com/blog/jtagulator-vs-jtagenum-tools-for-identifying-jtag-pins-in-iot-devices?edition=2019)
|
* [JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices by Dylan Ayrey](https://www.praetorian.com/blog/jtagulator-vs-jtagenum-tools-for-identifying-jtag-pins-in-iot-devices?edition=2019)
|
||||||
* [JTAG PIN Identification - February 21, 2017](https://just2secure.blogspot.com/2017/02/jtag-pin-identification.html)
|
* [JTAG PIN Identification - February 21, 2017](https://just2secure.blogspot.com/2017/02/jtag-pin-identification.html)
|
||||||
|
|
|
||||||
|
|
@ -19,6 +19,7 @@
|
||||||
$ avrdude -p m328p -c usbasp -P /dev/ttyUSB0 -b 9600 -U flash:w:flash_raw.bin
|
$ avrdude -p m328p -c usbasp -P /dev/ttyUSB0 -b 9600 -U flash:w:flash_raw.bin
|
||||||
|
|
||||||
# send ihex firmware
|
# send ihex firmware
|
||||||
|
$ avrdude -c arduino -p atmega328p -P /dev/ttyUSB* -b115200 -u -V -U flash:w:CHALLENGE.hex
|
||||||
$ avrdude -c usbasp -p m328p -F -U flash:r:dump.hex:i
|
$ avrdude -c usbasp -p m328p -F -U flash:r:dump.hex:i
|
||||||
|
|
||||||
# default
|
# default
|
||||||
|
|
@ -54,6 +55,7 @@
|
||||||
```powershell
|
```powershell
|
||||||
sudo openocd -f /home/maki/tools/hardware/openocd/tcl/interface/stlink-v2-1.cfg -f /home/maki/tools/hardware/openocd/tcl/target/nrf51.cfg -f dump_fw.cfg
|
sudo openocd -f /home/maki/tools/hardware/openocd/tcl/interface/stlink-v2-1.cfg -f /home/maki/tools/hardware/openocd/tcl/target/nrf51.cfg -f dump_fw.cfg
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using [raspberrypi/picotool](https://github.com/raspberrypi/picotool)
|
* Using [raspberrypi/picotool](https://github.com/raspberrypi/picotool)
|
||||||
* Build PicoTool, you will need the pico-sdk
|
* Build PicoTool, you will need the pico-sdk
|
||||||
```ps1
|
```ps1
|
||||||
|
|
@ -85,9 +87,18 @@
|
||||||
|
|
||||||
## Dump Flash via SPI
|
## Dump Flash via SPI
|
||||||
|
|
||||||
```ps1
|
|
||||||
flashrom -p serprog:dev=/dev/ttyACM0,spispeed=160k -r dump_spi.bin -c "MX25L6406E/MX25L6408E"
|
* Using [flashrom/flashroom](https://github.com/flashrom/flashrom)
|
||||||
```
|
```ps1
|
||||||
|
sudo apt-get install build-essential pciutils usbutils libpci-dev libusb-dev libftdi1 libftdi-dev zlib1g-dev subversion libusb-1.0-0-dev
|
||||||
|
svn co svn://flashrom.org/flashrom/trunk flashrom
|
||||||
|
cd flashrom
|
||||||
|
make
|
||||||
|
|
||||||
|
flashrom -p ft232_spi:type:232h -r spidump.bin
|
||||||
|
flashrom -p linux_spi:dev=/dev/spidev0.0,spispeed=512 -r spi_dump.bin
|
||||||
|
flashrom -p serprog:dev=/dev/ttyACM0,spispeed=160k -r dump_spi.bin -c "MX25L6406E/MX25L6408E"
|
||||||
|
```
|
||||||
|
|
||||||
* Using HydraBus: [hydrabus/hydrafw/hydra_spi_dump.py](https://github.com/hydrabus/hydrafw/blob/master/contrib/hydra_spi_dump/hydra_spi_dump.py)
|
* Using HydraBus: [hydrabus/hydrafw/hydra_spi_dump.py](https://github.com/hydrabus/hydrafw/blob/master/contrib/hydra_spi_dump/hydra_spi_dump.py)
|
||||||
```ps1
|
```ps1
|
||||||
|
|
@ -95,7 +106,6 @@ flashrom -p serprog:dev=/dev/ttyACM0,spispeed=160k -r dump_spi.bin -c "MX25L6406
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
## Convert ihex to elf
|
## Convert ihex to elf
|
||||||
|
|
||||||
> The Intel HEX is a transitional file format for microcontrollers, (E)PROMs, and other devices. The documentation states that HEXs can be converted to binary files and programmed into a configuration device.
|
> The Intel HEX is a transitional file format for microcontrollers, (E)PROMs, and other devices. The documentation states that HEXs can be converted to binary files and programmed into a configuration device.
|
||||||
|
|
@ -137,32 +147,53 @@ Inspect the assembly with `avr-objdump -m avr -D chest.hex`.\
|
||||||
Emulate : `qemu-system-avr -S -s -nographic -serial tcp::5678,server=on,wait=off -machine uno -bios chest.bin`
|
Emulate : `qemu-system-avr -S -s -nographic -serial tcp::5678,server=on,wait=off -machine uno -bios chest.bin`
|
||||||
|
|
||||||
|
|
||||||
## Over-the-air updates
|
|
||||||
|
|
||||||
TODO
|
|
||||||
|
|
||||||
|
|
||||||
## Explore firmware
|
## Explore firmware
|
||||||
|
|
||||||
```powershell
|
* strings
|
||||||
$ binwalk -Me file.bin
|
```ps1
|
||||||
$ strings file.bin
|
$ strings file.bin
|
||||||
|
|
||||||
$ strings -e l file.bin
|
$ strings -e l file.bin
|
||||||
The strings -e flag specifies the encoding of the characters. -el specifies little-endian characters 16-bits wide (e.g. UTF-16)
|
The strings -e flag specifies the encoding of the characters. -el specifies little-endian characters 16-bits wide (e.g. UTF-16)
|
||||||
|
|
||||||
$ strings -tx file.bin
|
$ strings -tx file.bin
|
||||||
The -t flag will return the offset of the string within the file. -tx will return it in hex format, T-to in octal and -td in decimal.
|
The -t flag will return the offset of the string within the file. -tx will return it in hex format, T-to in octal and -td in decimal.
|
||||||
|
```
|
||||||
|
|
||||||
$ dd if=firmware.bin of=firmware.chunk bs=1 skip=$((0x200)) count=$((0x400-0x200))
|
* dd
|
||||||
If we wanted to run it a little faster, we could increase the block size:
|
```ps1
|
||||||
$ dd if=firmware.bin of=firmware.chunk bs=$((0x100)) skip=$((0x200/0x100)) count=$(((0x400-0x200)/0x100))
|
$ dd if=firmware.bin of=firmware.chunk bs=1 skip=$((0x200)) count=$((0x400-0x200))
|
||||||
|
If we wanted to run it a little faster, we could increase the block size:
|
||||||
|
$ dd if=firmware.bin of=firmware.chunk bs=$((0x100)) skip=$((0x200/0x100)) count=$(((0x400-0x200)/0x100))
|
||||||
|
```
|
||||||
|
|
||||||
$ binwalk -Y dump.elf
|
* binwalk
|
||||||
DECIMAL HEXADECIMAL DESCRIPTION
|
```powershell
|
||||||
--------------------------------------------------------------------------------
|
$ binwalk -Me file.bin
|
||||||
3708 0xE7C ARM executable code, 16-bit (Thumb), little endian, at least 522 valid instructions
|
$ binwalk -Y dump.elf
|
||||||
```
|
DECIMAL HEXADECIMAL DESCRIPTION
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
3708 0xE7C ARM executable code, 16-bit (Thumb), little endian, at least 522 valid instructions
|
||||||
|
```
|
||||||
|
|
||||||
|
* Unsquashfs
|
||||||
|
```powershell
|
||||||
|
sudo unsquashfs -f -d /media/seagate /tmp/file.squashfs
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
## Write new firmware
|
||||||
|
|
||||||
|
* Repack firmware
|
||||||
|
```ps1
|
||||||
|
mksquashfs4 squashfs-root myrootfs {options}
|
||||||
|
dd if=myrootfs of=dump/bin bs=1 seek=<offset> conv=notrunc
|
||||||
|
```
|
||||||
|
|
||||||
|
* Flashrom write
|
||||||
|
```ps1
|
||||||
|
flashrom -p ft2232_spi:type=232H -w dump.bin
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
## Type of firmware
|
## Type of firmware
|
||||||
|
|
@ -182,11 +213,6 @@ $ binwalk -E fw
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Unsquashfs
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
sudo unsquashfs -f -d /media/seagate /tmp/file.squashfs
|
|
||||||
```
|
|
||||||
|
|
||||||
|
|
||||||
## Encrypted firmware
|
## Encrypted firmware
|
||||||
|
|
@ -196,6 +222,12 @@ sudo unsquashfs -f -d /media/seagate /tmp/file.squashfs
|
||||||
* [MINDSHARE: DEALING WITH ENCRYPTED ROUTER FIRMWARE](https://www.zerodayinitiative.com/blog/2020/2/6/mindshare-dealing-with-encrypted-router-firmware)
|
* [MINDSHARE: DEALING WITH ENCRYPTED ROUTER FIRMWARE](https://www.zerodayinitiative.com/blog/2020/2/6/mindshare-dealing-with-encrypted-router-firmware)
|
||||||
|
|
||||||
|
|
||||||
|
## Over-the-air updates
|
||||||
|
|
||||||
|
TODO
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
* [Extracting Firmware from Embedded Devices (SPI NOR Flash) - Flashback Team - 9 sept. 2022](https://www.youtube.com/watch?v=nruUuDalNR0)
|
* [Extracting Firmware from Embedded Devices (SPI NOR Flash) - Flashback Team - 9 sept. 2022](https://www.youtube.com/watch?v=nruUuDalNR0)
|
||||||
|
* [Real Hardware Hacking for S$30 or Less - Joe FitzPatrick - 31 march 2020](https://youtu.be/wVPochUgTvw)
|
||||||
|
|
@ -1,18 +1,8 @@
|
||||||
# Firmware Reverse Engineering
|
# Firmware Reverse Engineering
|
||||||
|
|
||||||
### Summary
|
## Loading bare-metal binaries into IDA
|
||||||
|
|
||||||
* Loading bare-metal binaries into IDA
|
Requirements:
|
||||||
* Loading bare-metal binaries into Radare2
|
|
||||||
* Loading bare-metal binaries into Ghidra
|
|
||||||
* ESPTool
|
|
||||||
* nRF5x Firmware disassembly tools
|
|
||||||
* Pure disassemblers
|
|
||||||
* Simulating AVR
|
|
||||||
|
|
||||||
### Loading bare-metal binaries into IDA
|
|
||||||
|
|
||||||
Prerequisite:
|
|
||||||
|
|
||||||
* The **load address** is the address in memory that the binary is being executed from.
|
* The **load address** is the address in memory that the binary is being executed from.
|
||||||
* The **entry point** is the location within the binary where the processor starts executing.
|
* The **entry point** is the location within the binary where the processor starts executing.
|
||||||
|
|
@ -23,7 +13,8 @@ Prerequisite:
|
||||||
|
|
||||||
* ESP8266 : [https://github.com/themadinventor/ida-xtensa](https://github.com/themadinventor/ida-xtensa)
|
* ESP8266 : [https://github.com/themadinventor/ida-xtensa](https://github.com/themadinventor/ida-xtensa)
|
||||||
|
|
||||||
### Loading bare-metal binaries into Radare2
|
|
||||||
|
## Loading bare-metal binaries into Radare2
|
||||||
|
|
||||||
Radare2 can disassemble `avr`, `arduino` natively
|
Radare2 can disassemble `avr`, `arduino` natively
|
||||||
|
|
||||||
|
|
@ -66,11 +57,23 @@ jmp 0x373a
|
||||||
jmp 0x59ae
|
jmp 0x59ae
|
||||||
```
|
```
|
||||||
|
|
||||||
### Loading bare-metal binaries into Ghidra
|
|
||||||
|
## Loading bare-metal binaries into Ghidra
|
||||||
|
|
||||||
|
SVD-Loader for Ghidra automates the entire generation of peripheral structs and memory maps for over 650 different microcontrollers
|
||||||
|
|
||||||
* SVD-Loader for Ghidra: Simplifying bare-metal ARM reverse engineering - [svd-loader/](https://leveldown.de/blog/svd-loader/)
|
* SVD-Loader for Ghidra: Simplifying bare-metal ARM reverse engineering - [svd-loader/](https://leveldown.de/blog/svd-loader/)
|
||||||
|
|
||||||
### ESPTool
|
**Usage**
|
||||||
|
|
||||||
|
* Load a binary file
|
||||||
|
* Open it in the code-browser, do not analyze it
|
||||||
|
* Run the SVD-Loader Script
|
||||||
|
* Select an SVD file
|
||||||
|
* Analyze the file
|
||||||
|
|
||||||
|
|
||||||
|
## ESPTool
|
||||||
|
|
||||||
ESP8266 and ESP32 serial bootloader utility : [espressif/esptool](https://github.com/espressif/esptool)
|
ESP8266 and ESP32 serial bootloader utility : [espressif/esptool](https://github.com/espressif/esptool)
|
||||||
|
|
||||||
|
|
@ -83,7 +86,8 @@ Entry point: 4010f29c
|
||||||
Segment 1: len 0x00568 load 0x4010f000 file_offs 0x00000008
|
Segment 1: len 0x00568 load 0x4010f000 file_offs 0x00000008
|
||||||
```
|
```
|
||||||
|
|
||||||
### nRF5x Firmware disassembly tools
|
|
||||||
|
## nRF5x Firmware disassembly tools
|
||||||
|
|
||||||
* [DigitalSecurity/nrf5x-tools](https://github.com/DigitalSecurity/nrf5x-tools)
|
* [DigitalSecurity/nrf5x-tools](https://github.com/DigitalSecurity/nrf5x-tools)
|
||||||
|
|
||||||
|
|
@ -109,7 +113,8 @@ ROM address : 0x23000
|
||||||
ROM length : 0x5d000
|
ROM length : 0x5d000
|
||||||
```
|
```
|
||||||
|
|
||||||
### Pure disassemblers
|
|
||||||
|
## Pure disassemblers
|
||||||
|
|
||||||
* Vavrdisasm -- vAVRdisasm will auto-recognize Atmel Generic, Intel HEX8, and Motorola S-Record files - [vsergeev/vavrdisasm](https://github.com/vsergeev/vavrdisasm)
|
* Vavrdisasm -- vAVRdisasm will auto-recognize Atmel Generic, Intel HEX8, and Motorola S-Record files - [vsergeev/vavrdisasm](https://github.com/vsergeev/vavrdisasm)
|
||||||
* [ODA - The Online Disassembler](https://www.onlinedisassembler.com/odaweb/)
|
* [ODA - The Online Disassembler](https://www.onlinedisassembler.com/odaweb/)
|
||||||
|
|
@ -120,7 +125,8 @@ ROM length : 0x5d000
|
||||||
$ avr-objdump -m avr -D main.hex > main.hex.dis
|
$ avr-objdump -m avr -D main.hex > main.hex.dis
|
||||||
```
|
```
|
||||||
|
|
||||||
### Simulating AVR
|
|
||||||
|
## Simulating AVR
|
||||||
|
|
||||||
> Programs compiled for Arduino can be simulated using AVR Studio or the newer Atmel Studio. I have used the former along with hapsim. Hapsim works by hooking into AVR Studio and can simulate peripherals like the UART, LCD etc.
|
> Programs compiled for Arduino can be simulated using AVR Studio or the newer Atmel Studio. I have used the former along with hapsim. Hapsim works by hooking into AVR Studio and can simulate peripherals like the UART, LCD etc.
|
||||||
|
|
||||||
|
|
@ -128,7 +134,8 @@ ROM length : 0x5d000
|
||||||
$ simulavr -P atmega128 -F 16000000 –f build-crumbuino128/ex1.1.elf
|
$ simulavr -P atmega128 -F 16000000 –f build-crumbuino128/ex1.1.elf
|
||||||
```
|
```
|
||||||
|
|
||||||
### UEFI Firmware
|
|
||||||
|
## UEFI Firmware
|
||||||
|
|
||||||
Parse BIOS/Intel ME/UEFI firmware related structures: Volumes, FileSystems, Files, etc - [theopolis/uefi-firmware-parser](https://github.com/theopolis/uefi-firmware-parser)
|
Parse BIOS/Intel ME/UEFI firmware related structures: Volumes, FileSystems, Files, etc - [theopolis/uefi-firmware-parser](https://github.com/theopolis/uefi-firmware-parser)
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,9 +1,11 @@
|
||||||
# Arduino
|
# Arduino
|
||||||
|
|
||||||
### Logic Analyzer for Arduino, AVR, ESP8266 and STM32
|
##
|
||||||
|
|
||||||
[https://github.com/aster94/logic-analyzer](https://github.com/aster94/logic-analyzer)
|
* [Logic Analyzer for Arduino, AVR, ESP8266 and STM32 - aster94/logic-analyzer](https://github.com/aster94/logic-analyzer)
|
||||||
|
* [JTAGulator-like for Arduino, Teensy, STM32 Bluepill, Texas Instruments Tiva and RaspberryPi - cyphunk/JTAGenum](https://github.com/cyphunk/JTAGenum)
|
||||||
|
|
||||||
### JTAGulator-like for Arduino, Teensy, STM32 Bluepill, Texas Instruments Tiva and RaspberryPi
|
|
||||||
|
|
||||||
[https://github.com/cyphunk/JTAGenum](https://github.com/cyphunk/JTAGenum)
|
## References
|
||||||
|
|
||||||
|
* []()
|
||||||
|
|
@ -1,8 +1,29 @@
|
||||||
# Logic Analyzer
|
# Logic Analyzer
|
||||||
|
|
||||||
TODO
|
## Sigrok / Pulseview
|
||||||
|
|
||||||
|
* [Sigrok wiki > Downloads](https://sigrok.org/wiki/Downloads)
|
||||||
|
```ps1
|
||||||
|
sigrok/kali-rolling 0.3 all
|
||||||
|
Logic analyzer and protocol decoder software suite (metapackage)
|
||||||
|
|
||||||
|
pulseview/kali-rolling 0.4.2-3+b1 amd64
|
||||||
|
sigrok logic analyzer, oscilloscope, and MSO GUI
|
||||||
|
```
|
||||||
|
|
||||||
|
## Saleae
|
||||||
|
|
||||||
|
* [Logic 2 Software](https://support.saleae.com/logic-software/sw-download)
|
||||||
|
|
||||||
|
|
||||||
|
## Interact
|
||||||
|
|
||||||
|
```ps1
|
||||||
|
screen /dev/ttyUSB0 19200
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
* []()
|
* [LOGIC ANALYZERS: TAPPING INTO RASPBERRY PI SECRETS - Arya Voronova - August 31, 2023](https://hackaday.com/2023/08/31/logic-analyzers-tapping-into-raspberry-pi-secrets/)
|
||||||
|
* [LOGIC ANALYZERS: CAPABILITIES AND LIMITATIONS - Arya Voronova - September 12, 2023](https://hackaday.com/2023/09/12/logic-analyzers-capabilities-and-limitations/)
|
||||||
|
|
@ -1,10 +1,13 @@
|
||||||
# Raspberry Pi
|
# Raspberry Pi
|
||||||
|
|
||||||
### Raspberrypi As Poor Man’s Hardware Hacking Tool
|
## GPIO Header
|
||||||
|
|
||||||
* SPI – Serial Peripheral Interface
|

|
||||||
* I2C – Inter-IC Communication
|
|
||||||
* Debugger – JTAG/SWD
|
|
||||||
|
## Tools
|
||||||
|
|
||||||
|
* [raspi-sec-tool](https://github.com/arunmagesh/raspi-sec-tool) - using Raspberry pi as hacking tool
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
|
||||||
|
|
@ -23,6 +23,7 @@
|
||||||
* [Identifying UART and main() in an AVR firmware (ft. Zeta Two) part 1 - rhme2](https://www.youtube.com/watch?v=hyoPAOTrUMc\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=23)
|
* [Identifying UART and main() in an AVR firmware (ft. Zeta Two) part 1 - rhme2](https://www.youtube.com/watch?v=hyoPAOTrUMc\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=23)
|
||||||
* [Riscure CTF 2 (2016)](https://github.com/Riscure/Rhme-2016)
|
* [Riscure CTF 2 (2016)](https://github.com/Riscure/Rhme-2016)
|
||||||
* [riscure embedded hardware CTF is over - loopback 0x03 - LiveOverflow - 3 march 2017](https://youtu.be/FI4serDzE4w)
|
* [riscure embedded hardware CTF is over - loopback 0x03 - LiveOverflow - 3 march 2017](https://youtu.be/FI4serDzE4w)
|
||||||
|
* [rhme-2016 write-up Team HydraBus](https://github.com/hydrabus/rhme-2016)
|
||||||
* [Riscure CTF 1 (2015)](https://github.com/Riscure/RHme-2015)
|
* [Riscure CTF 1 (2015)](https://github.com/Riscure/RHme-2015)
|
||||||
* [Reversing Raw Binary Firmware Files in Ghidra](https://gist.github.com/nstarke/ed0aba2c882b8b3078747a567ee00520)
|
* [Reversing Raw Binary Firmware Files in Ghidra](https://gist.github.com/nstarke/ed0aba2c882b8b3078747a567ee00520)
|
||||||
* [Dumper un Arduino - thanatos](https://thanat0s.trollprod.org/2014/01/dumper-un-arduino/)
|
* [Dumper un Arduino - thanatos](https://thanat0s.trollprod.org/2014/01/dumper-un-arduino/)
|
||||||
|
|
@ -44,5 +45,5 @@
|
||||||

|

|
||||||

|

|
||||||

|

|
||||||

|

|
||||||

|

|
||||||
|
|
@ -1,3 +1,34 @@
|
||||||
# I2C
|
# I2C
|
||||||
|
|
||||||
TODO
|
I2C (Inter-Integrated Circuit), pronounced "I-squared-C" or "I-two-C", is a popular communication protocol mainly used for low-speed, short-distance communication in embedded systems.
|
||||||
|
|
||||||
|
|
||||||
|
## Analysis
|
||||||
|
|
||||||
|
:warning: Enable I2C on the Raspberry Pi via `raspi-config`
|
||||||
|
|
||||||
|
* i2c-tools
|
||||||
|
```ps1
|
||||||
|
sudo apt-get install i2c-tools
|
||||||
|
i2cdetect -y 1
|
||||||
|
```
|
||||||
|
|
||||||
|
* eeprog
|
||||||
|
```ps1
|
||||||
|
wget http://darkswarm.org/eeprog-0.7.6-tear5.tar.gz
|
||||||
|
tar -xvf eeprog-0.7.6-tear5.tar.gz eeprog-0.7.6-tear12/
|
||||||
|
cd eeprog-0.7.6-tear12/
|
||||||
|
make
|
||||||
|
sudo make install
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
## Read / Write
|
||||||
|
|
||||||
|
* Read: `./eeprog -x /dev/i2c-1 0x50 -16 -r 0x00:0x10`
|
||||||
|
* Write: `echo "hello" | ./eeprog -f -16 -w 0 -t 5 /dev/i2c-1 0x50`
|
||||||
|
|
||||||
|
|
||||||
|
## References
|
||||||
|
|
||||||
|
* [How to Scan and Detect I2C Addresses - Carter Nelson](https://learn.adafruit.com/scanning-i2c-addresses/raspberry-pi)
|
||||||
|
|
|
||||||
Loading…
Reference in New Issue