Glitches + Gadgets (Hydra, GoodFET, Proxmark)
parent
60cb3bd093
commit
8a5e389336
Binary file not shown.
|
After Width: | Height: | Size: 950 KiB |
|
Before Width: | Height: | Size: 305 KiB After Width: | Height: | Size: 305 KiB |
|
|
@ -1,3 +0,0 @@
|
|||
# SPI
|
||||
|
||||
TODO
|
||||
|
|
@ -1,5 +1,7 @@
|
|||
# UART
|
||||
|
||||
## Table of contents
|
||||
|
||||
* [What is it ?](#what-is-it-)
|
||||
* [Identifying UART ports](#identifying-uart-ports)
|
||||
* [Using a multimeter](#using-a-multimeter)
|
||||
|
|
@ -14,6 +16,7 @@
|
|||
* [Examples](#examples)
|
||||
|
||||
## What is it ?
|
||||
|
||||
UART stands for Universal asynchronous receiver transmitter. Used for serial communications over a computer or peripheral device serial port.
|
||||
|
||||
UART peripherals are commonly integrated in many embedded devices. UART communication makes use of baud rate to maintain synchronism between two devices. The baud rate is the rate at which information is transferred in a communication channel.
|
||||
|
|
@ -25,6 +28,7 @@ Generally, the line is held high (at a logical 1 value) while UART is in idle st
|
|||
We call the most common configuration **8N1**: eight data bits, no parity, and 1 stop bit.
|
||||
|
||||
## Identifying UART ports
|
||||
|
||||
A UART pinout has **four** ports:
|
||||
|
||||
* **TX** (Transmit)
|
||||
|
|
|
|||
|
|
@ -1,19 +1,17 @@
|
|||
# Firmware Dumping
|
||||
|
||||
## Summary
|
||||
## Flash Memory Types
|
||||
|
||||
* [Send a new firmware into the microcontroller](#send-a-new-firmware-into-the-microcontroller)
|
||||
* [Dump firmware using debug port](#dump-firmware-using-debug-port)
|
||||
* [Convert ihex to elf](#convert-ihex-to-elf)
|
||||
* [Over-the-air updates](#over-the-air-updates)
|
||||
* [Explore firmware](#explore-firmware)
|
||||
* [Type of firmware](#type-of-firmware)
|
||||
* [Check entropy](#check-entropy)
|
||||
* [Unsquashfs](#unsquashfs)
|
||||
* [Encrypted firmware](#encrypted-firmware)
|
||||
* NOR Flash (SOIC8 package)
|
||||
* SPI Flash
|
||||
* Mostly error "Fault-free" memory
|
||||
* Used for embedded device that need fast execution, but low storage capacity
|
||||
* NAND Flash (TSOP48 package)
|
||||
* eMMC Flash (BGA{153} package)
|
||||
* UFS Universal Flash Storage
|
||||
|
||||
|
||||
## Send a new firmware into the microcontroller
|
||||
## Flash a new firmware into the microcontroller
|
||||
|
||||
* Using [avrdudes/avrdude](https://github.com/avrdudes/avrdude)
|
||||
```powershell
|
||||
|
|
@ -26,6 +24,7 @@
|
|||
# default
|
||||
$ avrdude -c usbasp -p m328p -C /etc/avrdude.conf -U flash:w:hardcodedPassword.ino.arduino_standard.hex
|
||||
```
|
||||
|
||||
* Using [raspberrypi/picotool](https://github.com/raspberrypi/picotool)
|
||||
```ps1
|
||||
# extension indicates the type (bin, uf2)
|
||||
|
|
@ -33,7 +32,7 @@
|
|||
```
|
||||
|
||||
|
||||
## Dump firmware using debug port
|
||||
## Dump flash using debug port
|
||||
|
||||
* Using [avrdudes/avrdude](https://github.com/avrdudes/avrdude)
|
||||
```powershell
|
||||
|
|
@ -84,6 +83,19 @@
|
|||
```
|
||||
|
||||
|
||||
## Dump Flash via SPI
|
||||
|
||||
```ps1
|
||||
flashrom -p serprog:dev=/dev/ttyACM0,spispeed=160k -r dump_spi.bin -c "MX25L6406E/MX25L6408E"
|
||||
```
|
||||
|
||||
* Using HydraBus: [hydrabus/hydrafw/hydra_spi_dump.py](https://github.com/hydrabus/hydrafw/blob/master/contrib/hydra_spi_dump/hydra_spi_dump.py)
|
||||
```ps1
|
||||
./hydra_spi_dump.py firmware.bin 1024 0x000000 fast
|
||||
```
|
||||
|
||||
|
||||
|
||||
## Convert ihex to elf
|
||||
|
||||
> The Intel HEX is a transitional file format for microcontrollers, (E)PROMs, and other devices. The documentation states that HEXs can be converted to binary files and programmed into a configuration device.
|
||||
|
|
@ -182,3 +194,8 @@ sudo unsquashfs -f -d /media/seagate /tmp/file.squashfs
|
|||

|
||||
|
||||
* [MINDSHARE: DEALING WITH ENCRYPTED ROUTER FIRMWARE](https://www.zerodayinitiative.com/blog/2020/2/6/mindshare-dealing-with-encrypted-router-firmware)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Extracting Firmware from Embedded Devices (SPI NOR Flash) - Flashback Team - 9 sept. 2022](https://www.youtube.com/watch?v=nruUuDalNR0)
|
||||
|
|
@ -142,6 +142,9 @@ $ uefi-firmware-parser --test ~/firmware/*
|
|||
~/firmware/O990-A03.exe.hdr: DellPFS
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Loader un binaire Arduino dans IDA - Posted on January 26, 2014 by thanatos](https://thanat0s.trollprod.org/2014/01/loader-un-binaire-arduino-dans-ida/)
|
||||
* [Loader un binaire Arduino dans IDA - Posted on January 26, 2014 by thanatos](https://thanat0s.trollprod.org/2014/01/loader-un-binaire-arduino-dans-ida/)
|
||||
* [REcon 2014 - Reverse Engineering Flash Memory For Fun and Benefit - Matt Oh](https://youtu.be/nTPfKT61730)
|
||||
* [Reverse Engineering Flash Memory for Fun and Benefit - Jeong Wook (Matt) Oh](https://www.blackhat.com/docs/us-14/materials/us-14-Oh-Reverse-Engineering-Flash-Memory-For-Fun-And-Benefit-WP.pdf)
|
||||
|
|
@ -2,7 +2,8 @@
|
|||
|
||||

|
||||
|
||||
### Update Bus Pirate
|
||||
|
||||
## Update Bus Pirate
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/BusPirate/Bus_Pirate.git
|
||||
|
|
@ -12,8 +13,13 @@ sudo ./pirate-loader_lnx --dev=/dev/ttyACM0 --hex=../BPv4-firmware-v6.3-r2151.he
|
|||
|
||||
```powershell
|
||||
# Identify EEPROM chip
|
||||
sudo flashrom –p buspirate_spi:dev=/dev/ttyUSB0
|
||||
sudo flashrom -p buspirate_spi:dev=/dev/ttyUSB0
|
||||
|
||||
# Dump firmware using a bus pirate (SPI)
|
||||
sudo flashrom –p Buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M –c (Chip name) –r (Name.bin)
|
||||
```
|
||||
sudo flashrom -p Buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -c (Chip name) -r (Name.bin)
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Bus Pirate Unboxing - Toolkit - Hacker Warehouse - 4 juin 2018](https://youtu.be/lP8vMvBu3Bg)
|
||||
|
|
@ -1,8 +1,8 @@
|
|||
# Flipper Zero
|
||||
|
||||

|
||||

|
||||
|
||||
### **Firmwares**
|
||||
## **Firmwares**
|
||||
|
||||
* [Flipper Zero Firmware](https://github.com/flipperdevices/flipperzero-firmware)
|
||||
* [Flipper Zero Unleashed Firmware](https://github.com/Eng1n33r/flipperzero-firmware)
|
||||
|
|
@ -10,7 +10,7 @@
|
|||
|
||||
* [Awesome FlipperZero](https://github.com/djsime1/awesome-flipperzero)
|
||||
|
||||
#### Firmware Update - PC
|
||||
### Firmware Update - PC
|
||||
|
||||
1. Update to the latest firmware using [https://flipperzero.one/update](https://flipperzero.one/update)
|
||||
2. Download and install qFlipper
|
||||
|
|
@ -21,22 +21,20 @@
|
|||
7. On the Flipper Zero, once booted, press down, and left until you are on the 'Browser' screen. Scroll down until you see the 'update' directory and click on it.
|
||||
8. You should now see the contents you uploaded and an 'update' option. Hover over the 'update' option, click the center button on your Flipper, once again on the 'Run in App' option.
|
||||
|
||||
#### Firmware Update - WebUpdater
|
||||
### Firmware Update - WebUpdater
|
||||
|
||||
* [DarkFlippers/unleashed-firmware - Web Update](https://lab.flipper.net/?url=https://unleashedflip.com/fw_extra_apps/flipper-z-f7-update-unlshd-038e.tgz&channel=release-cfw&version=unlshd-038e)
|
||||
* [RogueMaster/flipperzero-firmware-wPlugins - Web Update](https://lab.flipper.net/?url=https%3A%2F%2Frogue-master.net%2F%3Ffile%3DRM0322-1504-0.79.2-22158b0.tgz&channel=RM0322-1504-0.79.2-22158b0&version=0.79.2)
|
||||
|
||||
|
||||
### Videos
|
||||
## Videos
|
||||
|
||||
* [Flipper Zero: Want some good news? - Penthertz](https://www.youtube.com/watch?v=tB0eYatvu0k)
|
||||
* [Flipper Zero: is this for you? Follow our 1st tests! - Penthertz](https://www.youtube.com/watch?v=W5YYObSBUno)
|
||||
|
||||
### Tutorials and Resources
|
||||
## Tutorials and Resources
|
||||
|
||||
* [Flipper Zero Hacking 101 - pingywon](https://flipper.pingywon.com/flipper/)
|
||||
* [Flipper Zero Playground - UberGuidoZ](https://github.com/UberGuidoZ/Flipper)
|
||||
* [Flashing Flipper Zero with RogueMaster CFW](https://interestingsoup.com/n00b-guide-flashing-flipper-zero-to-rougemaster/)
|
||||
* [Unleashed Firmware - Update firmware](https://github.com/DarkFlippers/unleashed-firmware/blob/dev/documentation/HowToInstall.md)
|
||||
|
||||
|
||||
* [Unleashed Firmware - Update firmware](https://github.com/DarkFlippers/unleashed-firmware/blob/dev/documentation/HowToInstall.md)
|
||||
|
|
@ -0,0 +1,16 @@
|
|||
# GoodFET
|
||||
|
||||
* [travisgoodspeed/goodfet](https://github.com/travisgoodspeed/goodfet) - An embedded bus adapter for various microcontrollers and radios.
|
||||
* [greatscottgadgets/Facedancer](https://github.com/greatscottgadgets/Facedancer) - modern FaceDancer core for multiple devices-- including GreatFET
|
||||
|
||||
|
||||
## Facedancer
|
||||
|
||||
The Facedancer21 is the twenty-fourth hardware revision of the GoodFET, owing its heritage to the GoodFET41 and Facedancer20. Unlike the general-purpose GoodFET boards, the only purpose of this board is to allow USB devices to be written in host-side Python, so that one workstation can fuzz-test the USB device drivers of another host.
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [GoodFET](https://goodfet.sourceforge.net/)
|
||||
* [Facedancer21 - GoodFET](https://goodfet.sourceforge.net/hardware/facedancer21/)
|
||||
* [Black Hat USA 2016 GreatFET Making GoodFET Great Again - 5 oct. 2019](https://youtu.be/IqhWqqvtNlY)
|
||||
|
|
@ -0,0 +1,44 @@
|
|||
# HydraBus
|
||||
|
||||
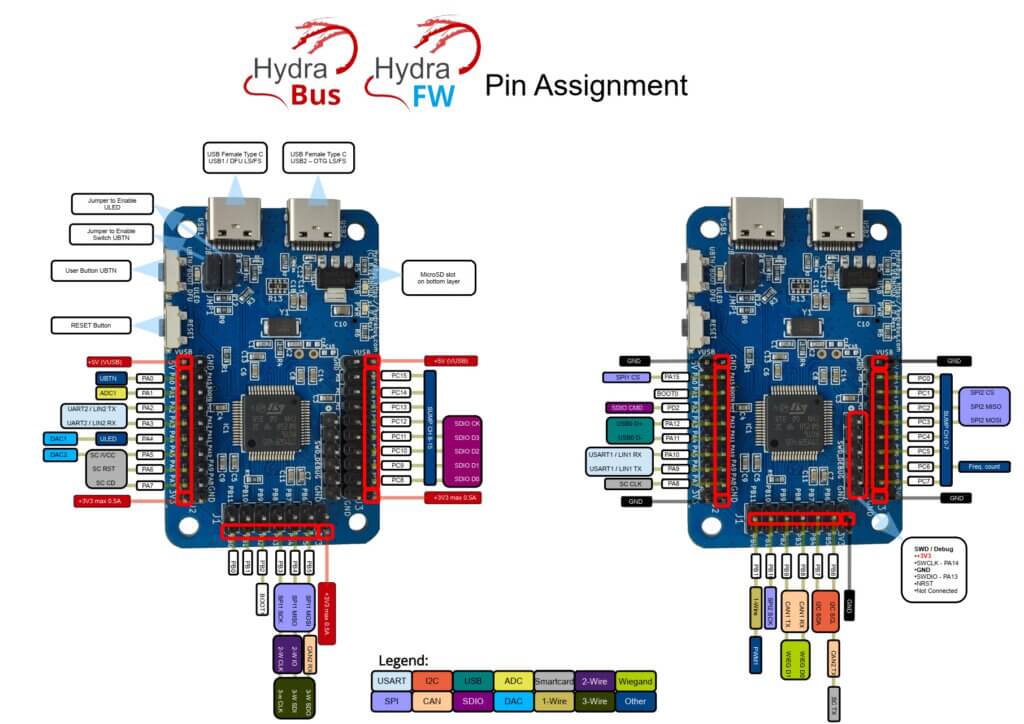
|
||||
|
||||
|
||||
## Features
|
||||
|
||||
Support many extensions:
|
||||
|
||||
- HydraNFC
|
||||
- HydraFlash
|
||||
- HydraLINCAN
|
||||
|
||||
External interactions:
|
||||
|
||||
- UART
|
||||
- I2C
|
||||
- CAN/LIN Bus
|
||||
- SPI Bus
|
||||
- SD/SDIO
|
||||
- USB Bus
|
||||
- ADC / DAC (Analog / Digital)
|
||||
- GPIO
|
||||
|
||||
|
||||
## Firmware
|
||||
|
||||
* [hydrabus/hydrafw](https://github.com/hydrabus/hydrafw) - HydraFW official firmware for HydraBus/HydraNFC
|
||||
* [hydrabus/hydrafw_hydranfc_shield_v2](https://github.com/hydrabus/hydrafw_hydranfc_shield_v2) - HydraFW dedicated to HydraBus v1 / HydraNFC Shield v2
|
||||
* [bvernoux/blackmagic](https://github.com/bvernoux/blackmagic) - In application debugger for ARM Cortex microcontrollers
|
||||
|
||||
Commands examples:
|
||||
|
||||
```ps1
|
||||
show system/memory/threads
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [HydraBus v1.0 Specifications - HydraBus](https://hydrabus.com/hydrabus-1-0-specifications)
|
||||
* [HydraBus Assembly Video - Lab401 - 30 may 2017](https://youtu.be/9lFEPG8EG6w)
|
||||
* [BlackAlps17: Hydrabus: Lowering the entry fee to the IoT bugfest - Benjamin Vernoux - 2 dec. 2017](https://www.youtube.com/watch?v=theYbzPhYH8)
|
||||
* [HydraBus - An Open Source Platform - RMLL Sec 2017](https://archives.pass-the-salt.org/RMLL%20Security%20Tracks/2017/slides/RMLL-Sec-2017-hydrabus.pdf)
|
||||
|
|
@ -0,0 +1,17 @@
|
|||
# HydraFlash
|
||||
|
||||
> Designed to dump Flash NAND chips
|
||||
|
||||
|
||||
## Usage
|
||||
|
||||
* [hydrabus/DumpFlash-Hydrabus](https://github.com/hydrabus/DumpFlash-Hydrabus)
|
||||
```ps1
|
||||
pip install git+https://github.com/hydrabus/DumpFlash-Hydrabus
|
||||
python2 DumpFlash.py -d /dev/hydrabus -i
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Hydrabus NAND Flash shield - hydrabus/HydraFlash](https://github.com/hydrabus/HydraFlash)
|
||||
|
|
@ -0,0 +1,34 @@
|
|||
# HydraNFC
|
||||
|
||||
## Features
|
||||
|
||||
* Support of microSD (FAT16/FAT32) card up to 32GB
|
||||
* Virtual Serial Port access through micro USB with VT100 terminal/shell
|
||||
* Basic UID read for Vicinity/ISO15693
|
||||
* Basic UID read for ISO14443-A/MIFARE ® card 4 or 7bytes UID
|
||||
* Read MIFARE Ultralight® tag content (full dump)
|
||||
* Tag Emulation UID ISO14443A & MIFARE Classic® 1K
|
||||
* Sniffer mode in an autonomous/stand-alone mode
|
||||
* Real-time ISO14443A sniffer mode
|
||||
|
||||
|
||||
## Firmware
|
||||
|
||||
* [hydrabus/hydrafw_hydranfc_shield_v2](https://github.com/hydrabus/hydrafw_hydranfc_shield_v2) - HydraFW dedicated to HydraBus v1 / HydraNFC Shield v2
|
||||
|
||||
Using console, type `nfc` + `Enter` to enter NFC mode dedicated to HydraNFC Shield v2.
|
||||
|
||||
```ps1
|
||||
> nfc
|
||||
NFCv2> nfc-all
|
||||
NFCv2> show
|
||||
NFCv2> nfc-all scan
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [HydraFW HydraNFC v2 guide - Benjamin Vernoux - Jul 4, 2021](https://github.com/hydrabus/hydrafw_hydranfc_shield_v2/wiki/HydraFW-HydraNFC-v2-guide)
|
||||
* [HydraNFC Getting Started - Lab401 - 30 mai 2017](https://youtu.be/-bYXXqPaB4s)
|
||||
* [HydraBus / HydraNFC unboxing & Assembly - Lab401 - 30 mai 2017](https://youtu.be/D-alGCsmqPU)
|
||||
* [HydraNFC - LAB401 product presentation - 17 mai 2018](https://youtu.be/MCmCK9y7Ojk)
|
||||
|
|
@ -0,0 +1,32 @@
|
|||
# HydraUSB3
|
||||
|
||||
> HydraUSB3 (WCH CH569) open source test firmware / examples / libraries to experiment with streaming / high-speed protocols (USB2 HS, USB3 SS, HSPI, SerDes...)
|
||||
|
||||
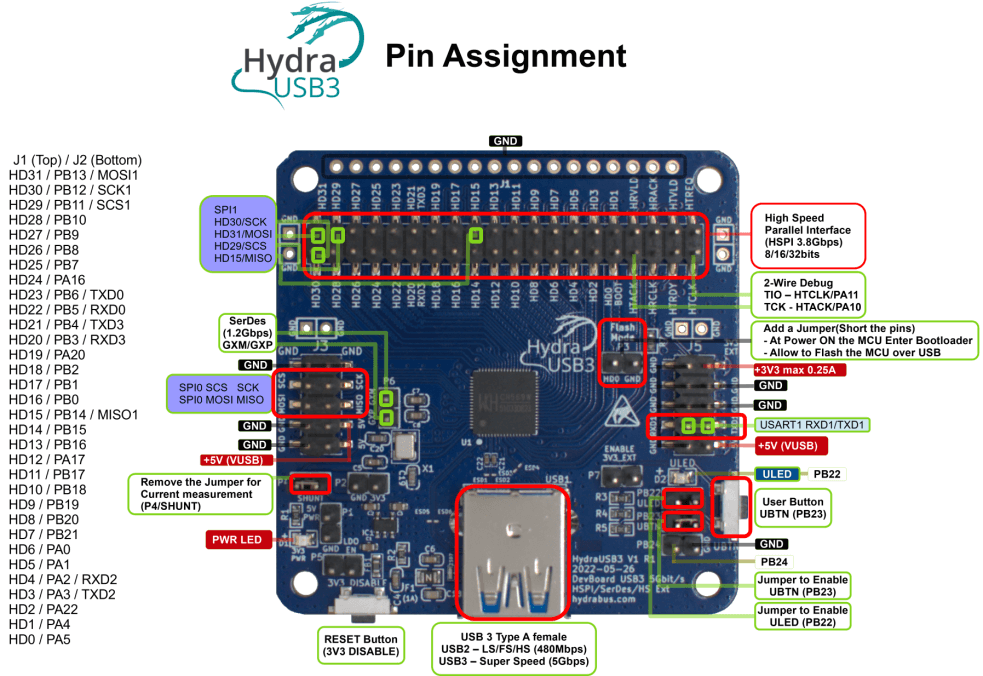
|
||||
|
||||
* [hydrausb3/hydrausb3_fw](https://github.com/hydrausb3/hydrausb3_fw) - Firmware
|
||||
* [hydrausb3/hydrausb3_hw](https://github.com/hydrausb3/hydrausb3_hw) - Hardware documentation
|
||||
|
||||
> **Warning**
|
||||
> It is MANDATORY to buy a “USB 3 Type A male to USB 3 Type A male cable” (the cable shall have Power+Data with USB2 and USB3 SS signals)
|
||||
|
||||
|
||||
## Firmware Flashing
|
||||
|
||||
**Linux**
|
||||
|
||||
* [How to build flash and use examples on Linux with shell](https://github.com/hydrausb3/hydrausb3_fw/wiki/how-to-build-flash-and-use-examples-on-linux)
|
||||
* [How to build flash and use examples on Linux with Eclipse IDE](https://github.com/hydrausb3/hydrausb3_fw/wiki/how-to-build-flash-and-use-examples-on-linux-Eclipse-IDE)
|
||||
|
||||
**Windows** (requires MSYS2/MINGW64)
|
||||
|
||||
* [How to build flash and use examples on Windows with MSYS2/MINGW64 shell](https://github.com/hydrausb3/hydrausb3_fw/wiki/how-to-build-flash-and-use-examples-on-windows)
|
||||
* [How to build flash and use examples on Windows with Eclipse IDE](https://github.com/hydrausb3/hydrausb3_fw/wiki/how-to-build-flash-and-use-examples-on-windows-Eclipse-IDE)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [HydraUSB3 v1.0 Specifications - HydraBus](https://hydrabus.com/hydrausb3-v1-0-specifications)
|
||||
* [GreHack2022 - Reverse Engineering of advanced RISC-V MCU with USB3 & High Speed peripherals - Benjamin Vernoux](https://github.com/hydrausb3/grehack22)
|
||||
* [GreHack22 - SecureDUO](https://github.com/chrisrdlg/gh22_SecureDuo)
|
||||
* [WCH CH569 SerDes Reverse Engineering - hydrausb3](https://github.com/hydrausb3/wch-ch569-serdes)
|
||||
|
|
@ -0,0 +1,8 @@
|
|||
# Logic Analyzer
|
||||
|
||||
TODO
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* []()
|
||||
|
|
@ -0,0 +1,9 @@
|
|||
# Proxmark
|
||||
|
||||
##
|
||||
|
||||
TODO
|
||||
|
||||
## References
|
||||
|
||||
* []()
|
||||
|
|
@ -2,8 +2,11 @@
|
|||
|
||||
### Raspberrypi As Poor Man’s Hardware Hacking Tool
|
||||
|
||||
[https://payatu.com/using-rasberrypi-as-poor-mans-hardware-hacking-tool](https://payatu.com/using-rasberrypi-as-poor-mans-hardware-hacking-tool)
|
||||
|
||||
* SPI – Serial Peripheral Interface
|
||||
* I2C – Inter-IC Communication
|
||||
* Debugger – JTAG/SWD
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Raspberry Pi As Poor Man’s Hardware Hacking Tool - Arun-Magesh - December 14, 2018](https://payatu.com/using-rasberrypi-as-poor-mans-hardware-hacking-tool)
|
||||
|
|
@ -1,6 +1,6 @@
|
|||
# Links & Hardware Kits
|
||||
|
||||
### Hardware Challenges & CTF
|
||||
## Hardware Challenges & CTF
|
||||
|
||||
* [BLE CTF](https://github.com/hackgnar/ble\_ctf)
|
||||
* [Learning Bluetooth Hackery with BLE CTF](http://www.hackgnar.com/2018/06/learning-bluetooth-hackery-with-ble-ctf.html)
|
||||
|
|
@ -13,7 +13,7 @@
|
|||
* [findTheDatasheet - FR](https://shoxxdj.fr/dvid-hardware-find-the-datasheet/)
|
||||
* [defaultPassword - FR](https://shoxxdj.fr/dvid-firmware-defaultpassword/)
|
||||
* [GreHack 2019: IOT Security: Hack The Damn Vulnerable IoT Device - Arnaud Courty](https://www.youtube.com/watch?v=C1vQGfzPWuY)
|
||||
* Riscure CTF 3
|
||||
* [Riscure CTF 3 (2017)](https://github.com/Riscure/Rhme-2017)
|
||||
* [Solving AVR reverse engineering challenge with radare2 - rhme2 Jumpy (reversing 100)](https://www.youtube.com/watch?v=zk3JdMOQPc8\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=5)
|
||||
* [Using UART / Serial to interact with an embedded device - rhme2 Setup](https://www.youtube.com/watch?v=TM-cuV9Nd1E\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=2)
|
||||
* [SHA1 length extension attack on the Secure Filesystem - rhme2 Secure Filesystem (crypto 100)](https://www.youtube.com/watch?v=6QQ4kgDWQ9w\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=3)
|
||||
|
|
@ -21,13 +21,17 @@
|
|||
* [Defeat a stack cookie with bruteforce - rhme2 Photo manager (pwn 100)](https://www.youtube.com/watch?v=01EX0mjya5A\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=6)
|
||||
* [Format string exploit on an arduino - rhme2 Casino (pwn 150)](https://www.youtube.com/watch?v=fRgNtGXDMlY\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=8)
|
||||
* [Identifying UART and main() in an AVR firmware (ft. Zeta Two) part 1 - rhme2](https://www.youtube.com/watch?v=hyoPAOTrUMc\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=23)
|
||||
* [Riscure CTF 2 (2016)](https://github.com/Riscure/Rhme-2016)
|
||||
* [riscure embedded hardware CTF is over - loopback 0x03 - LiveOverflow - 3 march 2017](https://youtu.be/FI4serDzE4w)
|
||||
* [Riscure CTF 1 (2015)](https://github.com/Riscure/RHme-2015)
|
||||
* [Reversing Raw Binary Firmware Files in Ghidra](https://gist.github.com/nstarke/ed0aba2c882b8b3078747a567ee00520)
|
||||
* [Dumper un Arduino - thanatos](https://thanat0s.trollprod.org/2014/01/dumper-un-arduino/)
|
||||
* [Dumping the Firmware from the device Using buspirate - Veera Babu](http://blog.isecurion.com/2017/07/06/dumping-the-firmware-from-the-device-using-buspirate/)
|
||||
* [Embedded/IoT Linux for Red-Blue Teams](https://www.pentesteracademy.com/course?id=37)
|
||||
* [From printed circuits boards to exploits (PWNING IOT DEVICES LIKE A BOSS) @virtualabs | Hack in Paris '18-](https://hackinparis.com/data/slides/2018/talks/HIP2018\_Damien\_Cauquil\_From\_Printed\_Circuit\_Boards\_To\_Exploits.pdf)
|
||||
|
||||
### Books
|
||||
|
||||
## Books
|
||||
|
||||
* [IoT Penetration Testing Cookbook: Identify vulnerabilities and secure your smart devices - Aaron Guzman, Aditya Gupta - Nov. 29 2017](https://www.amazon.ca/Penetration-Testing-Cookbook-Aaron-Guzman/dp/1787280578)
|
||||
* [The IoT Hacker's Handbook: A Practical Guide to Hacking the Internet of Things - Aditya Gupta - April 1 2019](https://www.amazon.ca/IoT-Hackers-Handbook-Practical-Internet/dp/1484242998)
|
||||
|
|
@ -35,9 +39,10 @@
|
|||
* [Advanced Penetration Testing Hacking IoT - Richard Knowell - April 2 2019](https://www.amazon.ca/Advanced-Penetration-Testing-Hacking-IoT/dp/1092533591)
|
||||
|
||||
|
||||
### Hardware Kit
|
||||
## Hardware Kits
|
||||
|
||||

|
||||

|
||||

|
||||

|
||||

|
||||
|
|
@ -6,6 +6,7 @@
|
|||
## Install and configuration
|
||||
|
||||
Dependencies to install first
|
||||
|
||||
```ps1
|
||||
sudo apt-get install p7zip git build-essential libreadline5 libreadline-dev libusb-0.1-4 libusb-dev libqt4-dev perl pkg-config wget libncurses5-dev gcc-arm-none-eabi libstdc++-arm-none-eabi-newlib ncurses-dev libpcsclite-dev pcscd
|
||||
```
|
||||
|
|
|
|||
|
|
@ -1,8 +1,34 @@
|
|||
# SPI
|
||||
|
||||
SPI is a serial peripheral interface. The controller selects a chip it send and receive information to and from. NOR flash chips with an SPI interface are commonly used as firmware boot chip. SPI has one read and one write line. In QSPI mode, 4 lines are used in parallel.
|
||||
Serial Peripheral Interface (SPI), is a type of communication protocol used primarily in microcontroller-based systems
|
||||
The controller selects a chip it send and receive information to and from. NOR flash chips with an SPI interface are commonly used as firmware boot chip. SPI has one read and one write line. In QSPI mode, 4 lines are used in parallel.
|
||||
|
||||
### Dump Firmware via SPI
|
||||
SPI mainly involves four lines or wires:
|
||||
|
||||
* MOSI (Master Out Slave In): This is the line through which the master sends data to the slave.
|
||||
* MISO (Master In Slave Out): Through this line, the slave sends data back to the master.
|
||||
* SCLK (Serial Clock): This line is like a clock ticking, controlled by the master. It helps in timing the data transfer, ensuring both master and slave are synchronized.
|
||||
* SS (Slave Select)/CS (Chip Select): When the master wants to talk to a particular slave, it uses this line to select the slave.
|
||||
|
||||
|
||||
## Interact via SPI
|
||||
|
||||

|
||||
|
||||
* Connect to HydraBus and communicate via the SPI protocol
|
||||
```ps1
|
||||
screen /dev/ttyACM0 115200
|
||||
spi
|
||||
|
||||
# RDID Read Identification Sequence example
|
||||
[ 0x9f hd:3 ]
|
||||
|
||||
# Read data from the beginning of the chip
|
||||
[ 0x03 0x00 0x00 0x00 hd:1024 ]
|
||||
```
|
||||
|
||||
|
||||
## Dump Firmware via SPI
|
||||
|
||||
```powershell
|
||||
sudo raspi-confi > Interface > SPI(P4)
|
||||
|
|
@ -19,7 +45,8 @@ An ESP8266 and ESP32 have several SPI busses available in hardware, SPI0 is hook
|
|||
$ python ./esptool.py read_flash --spi-connection HSPI 0 0x400000 flash_dump.bin
|
||||
```
|
||||
|
||||
### SPIFFS
|
||||
|
||||
## SPIFFS
|
||||
|
||||
```powershell
|
||||
$ cd ~/.arduino15/packages/esp32/tools/esptool/2.3.1
|
||||
|
|
@ -29,7 +56,8 @@ $ cd ~/.arduino15/packages/esp32/tools/mkspiffs/0.2.3
|
|||
$ ./mkspiffs -u /tmp/data -p 256 -b 8192 -s 1028096 /tmp/spiffs/bin
|
||||
```
|
||||
|
||||
### ESP32 Diagrams
|
||||
|
||||
## ESP32 Diagrams
|
||||
|
||||
Color coded which pins can be connected from the ESP HSPI pins to an SPI flash. The pink interfaces (DQ1 and DQ2) are optional, they are only used in QSPI mode.
|
||||
|
||||
|
|
@ -38,6 +66,7 @@ Color coded which pins can be connected from the ESP HSPI pins to an SPI flash.
|
|||
<img src="https://raw.githubusercontent.com/swisskyrepo/HardwareAllTheThings/master/docs/assets/Qspi.png" style="max-width: 400px;">
|
||||
</p>
|
||||
|
||||
### References
|
||||
|
||||
* https://www.youtube.com/watch?v=Bn5zajZ4I5E
|
||||
## References
|
||||
|
||||
* [Hardware Router CTF - Pen Test Partners - 9 mars 2020](https://www.youtube.com/watch?v=Bn5zajZ4I5E)
|
||||
|
|
@ -0,0 +1,22 @@
|
|||
# USB
|
||||
|
||||
## USB Type 2
|
||||
|
||||
|
||||
## USB Type 3
|
||||
|
||||
|
||||
## USB Type C
|
||||
|
||||
|
||||
## Fuzzing
|
||||
|
||||
- [HydraBus/HydraUSB3](https://hydrabus.com/hydrausb3-v1-0-specifications)
|
||||
- [goodfet/Facedancer21](https://goodfet.sourceforge.net/hardware/facedancer21/) - The purpose of this board is to allow USB devices to be written in host-side Python, so that one workstation can fuzz-test the USB device drivers of another host.
|
||||
- [USB Studio](#)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [HydraUSB3 v1.0 Specifications](https://hydrabus.com/hydrausb3-v1-0-specifications)
|
||||
* [Nullcon Goa 2023 | Cracking With Automated USB Fuzz - Subba Bachina & Conna - 31 dec. 2023](https://youtu.be/4uHg6toV69k)
|
||||
|
|
@ -1,13 +1,12 @@
|
|||
# Secure Boot
|
||||
|
||||
- Secure Boot is a **security feature implemented in modern computer systems**, primarily in those using the **Unified Extensible Firmware Interface (UEFI) firmware.**
|
||||
- Secure Boot is a **security feature implemented in modern computer systems**, primarily in those using the **Unified Extensible Firmware Interface (UEFI) firmware.**
|
||||
- Its main purpose is to ensure that **only trusted** and **authenticated software** is loaded during the boot process, protecting the system against unauthorized or malicious code that could compromise its integrity and security.
|
||||
|
||||
- During boot, UEFI Secure Boot checks the signature of each piece of boot software, including **UEFI firmware drivers** (also known as option ROMs), **Extensible Firmware Interface** (EFI) applications, and the operating system drivers and binaries. If the signatures are valid or trusted by the **Original Equipment Manufacturer** (OEM), the machine boots and the firmware gives control to the operating system.
|
||||
- During boot, UEFI Secure Boot checks the signature of each piece of boot software, including **UEFI firmware drivers** (also known as option ROMs), **Extensible Firmware Interface** (EFI) applications, and the operating system drivers and binaries. If the signatures are valid or trusted by the **Original Equipment Manufacturer** (OEM), the machine boots and the firmware gives control to the operating system.
|
||||
|
||||
|
||||
### References
|
||||
## References
|
||||
|
||||
* [Windows UEFI Bootkit in Rust](https://github.com/memN0ps/bootkit-rs)
|
||||
* [AzureDocs - Secure Boot](https://github.com/MicrosoftDocs/azure-docs/blob/main/articles/security/fundamentals/secure-boot.md)
|
||||
* [Awesome UEFI Security](https://github.com/river-li/awesome-uefi-security#documentations-book)
|
||||
* [Windows UEFI Bootkit in Rust - memN0ps](https://github.com/memN0ps/bootkit-rs)
|
||||
* [AzureDocs - Secure Boot - MicrosoftDocs](https://github.com/MicrosoftDocs/azure-docs/blob/main/articles/security/fundamentals/secure-boot.md)
|
||||
* [Awesome UEFI Security - river-li](https://github.com/river-li/awesome-uefi-security#documentations-book)
|
||||
|
|
|
|||
|
|
@ -1,12 +1,46 @@
|
|||
# Fault Injection
|
||||
|
||||
### AVR Glitch: Modifying Code Execution Paths Using Only Voltage
|
||||
## Power / VCC Glitch
|
||||
|
||||
[https://flawed.net.nz/2017/01/29/avr-glitch-modifying-code-execution-paths-using-only-voltage/](https://flawed.net.nz/2017/01/29/avr-glitch-modifying-code-execution-paths-using-only-voltage/)
|
||||
Power glitch injection is a physical attack technique used to test and exploit vulnerabilities in electronic devices by causing controlled, temporary power disturbances.
|
||||
A VCC glitch, also known as a supply voltage glitch, is a specific type of power glitch attack targeting the voltage supply (VCC) of a microcontroller or integrated circuit (IC) in electronic devices.
|
||||
|
||||
### Pin2pwn
|
||||
* [Fiasco - Riscure Hardware CTF 2016](https://github.com/hydrabus/rhme-2016/blob/master/FaultInjection/Fiasco.md) - solved using HydraBus + Custom Board with MOSFET
|
||||
```ps1
|
||||
gpio glitch trigger PB0 pin PC15 length 100 offsets 191200
|
||||
gpio glitch trigger PB0 pin PC15 length 100 offsets 191300
|
||||
```
|
||||
|
||||
[https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEF%20CON%2024%20-%20Brad-Dixon-Pin2Pwn-How-to-Root-An-Embedded-Linux-Box-With-A-Sewing-Needle-UPDATED.pdf](https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEF%20CON%2024%20-%20Brad-Dixon-Pin2Pwn-How-to-Root-An-Embedded-Linux-Box-With-A-Sewing-Needle-UPDATED.pdf)
|
||||
* [Hardware Power Glitch Attack (Fault Injection) - rhme2 Fiesta (FI 100)](https://youtu.be/6Pf3pY3GxBM) - solved using a [custom code](https://gist.github.com/LiveOverflow/cad0e905691ab5a8a2474d483a604d67) running on a Xilinx FPGA
|
||||
* [AVR Glitch: Modifying Code Execution Paths Using Only Voltage](https://flawed.net.nz/2017/01/29/avr-glitch-modifying-code-execution-paths-using-only-voltage/)
|
||||
|
||||
|
||||
## Electromagnetic Fault
|
||||
|
||||
Electromagnetic Fault Injection is an advanced technique used in hardware security and testing, where electromagnetic pulses are used to induce faults in electronic devices
|
||||
|
||||
**Tools**
|
||||
|
||||
* Create a custom Electromagnetic fault injection tool: [Dirt cheap Electromagnetic Fault Injection](https://pedro-javierf.github.io/devblog/dirtcheapemfaultinjection/)
|
||||
|
||||
|
||||
**Challenges**
|
||||
|
||||
* [Fiesta - Riscure Hardware CTF 2016 - pedro-javierf](https://pedro-javierf.github.io/devblog/rhmefaultinjection/) - solved using a custom EMFI
|
||||
|
||||
|
||||
## Clock Glitch
|
||||
|
||||
This technique involves momentarily disrupting or altering the clock signal of a device to induce errors or malfunctions in its operation.
|
||||
|
||||
**Challenges**
|
||||
|
||||
* [Fiesta - Riscure Hardware CTF 2016 - jcldf](https://twitter.com/jcldf/status/1235859271176171521) - solved using a clock glitch
|
||||
|
||||
|
||||
## Pin2pwn
|
||||
|
||||
[pin2pwn: How to Root an Embedded Linux Box with a Sewing Needle - Brad Dixon - Carve Systems - DEFCON 24](https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEF%20CON%2024%20-%20Brad-Dixon-Pin2Pwn-How-to-Root-An-Embedded-Linux-Box-With-A-Sewing-Needle-UPDATED.pdf)
|
||||
|
||||
In the case of an external SPI flash, it is possible for an attacker to short these pins :
|
||||
|
||||
|
|
@ -16,4 +50,12 @@ The MCU will not be able to get data from the external flash and then show a sta
|
|||
|
||||
Here is a practical example, putting a cable between MOSI and Chip Select :
|
||||
|
||||

|
||||

|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [rhme-2016 write-up Fault Injection - hydrabus](https://github.com/hydrabus/rhme-2016/tree/master/FaultInjection)
|
||||
* [Solving rhme fiesta from Riscure Hardware CTF 2016 with EM Fault Injection - Dangling Pointr - 2020, Oct 11](https://pedro-javierf.github.io/devblog/rhmefaultinjection/)
|
||||
* [Hardware Power Glitch Attack (Fault Injection) - rhme2 Fiesta (FI 100) - LiveOverflow - 16 june 2017](https://www.youtube.com/watch?v=6Pf3pY3GxBM)
|
||||
* [pin2pwn: How to Root an Embedded Linux Box with a Sewing Needle - Brad Dixon - Carve Systems - DEFCON 24](https://media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEF%20CON%2024%20-%20Brad-Dixon-Pin2Pwn-How-to-Root-An-Embedded-Linux-Box-With-A-Sewing-Needle-UPDATED.pdf)
|
||||
Loading…
Reference in New Issue