4.6 KiB
4.6 KiB
[Update] Malware analysis on Gamaredon APT campaign (06-08-19)
Table of Contents
Malware-analysis
Analysis of the TTPs
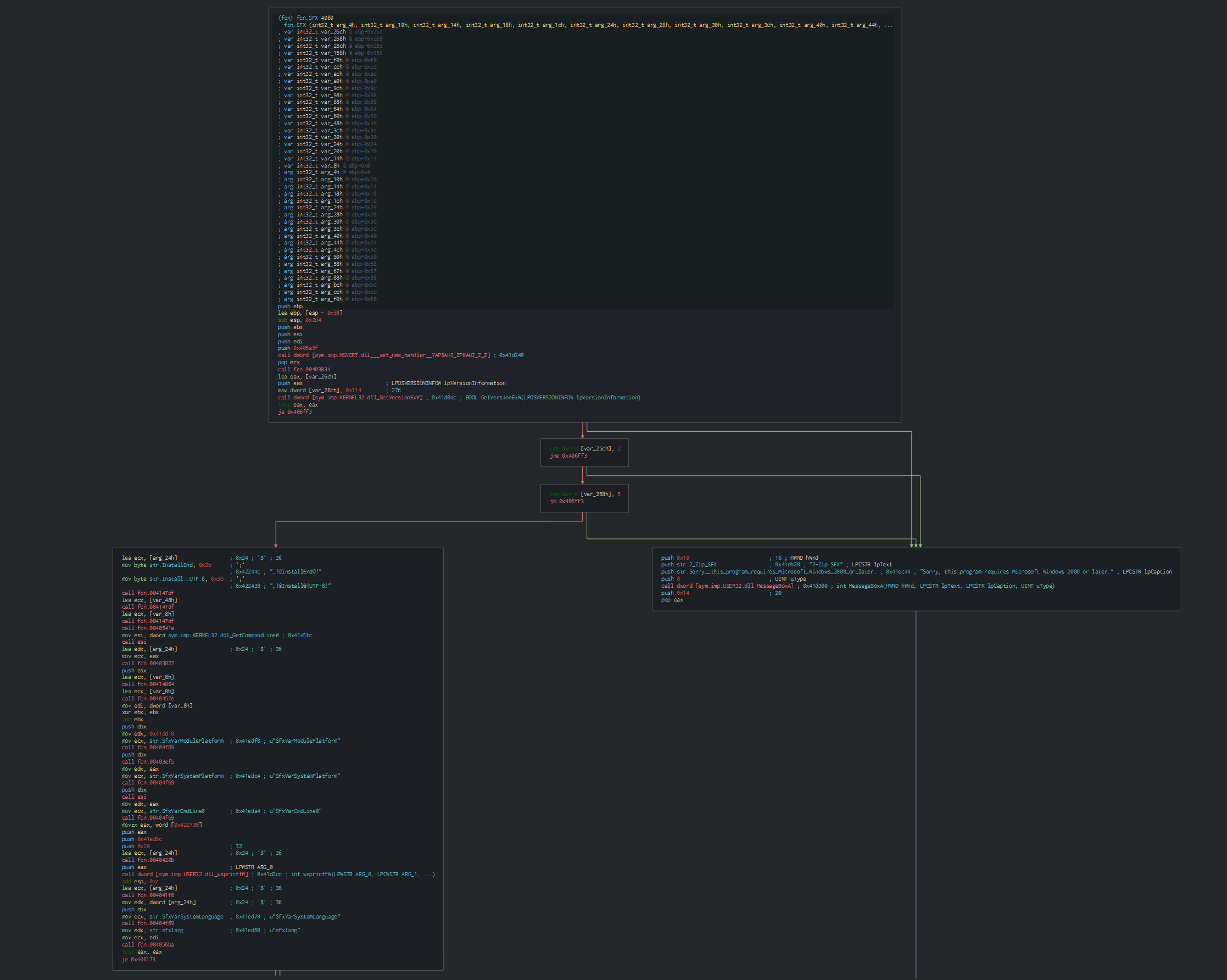
Like the last sample analysed, the new samples uses an SFX archive for extract the files and execute the fake document and the payload.
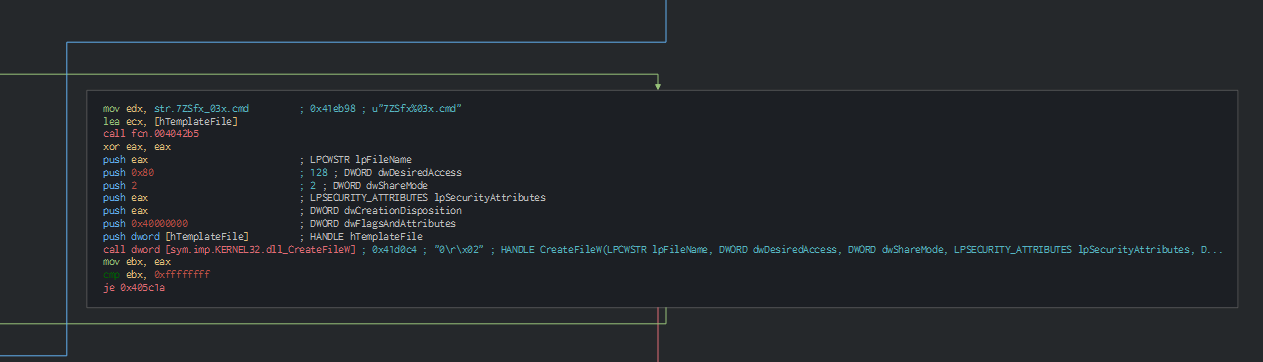
We can see again the cmd file extracted by the SFX archive. The randomization of the obfuscated strings has been by the algorithm in the archive.
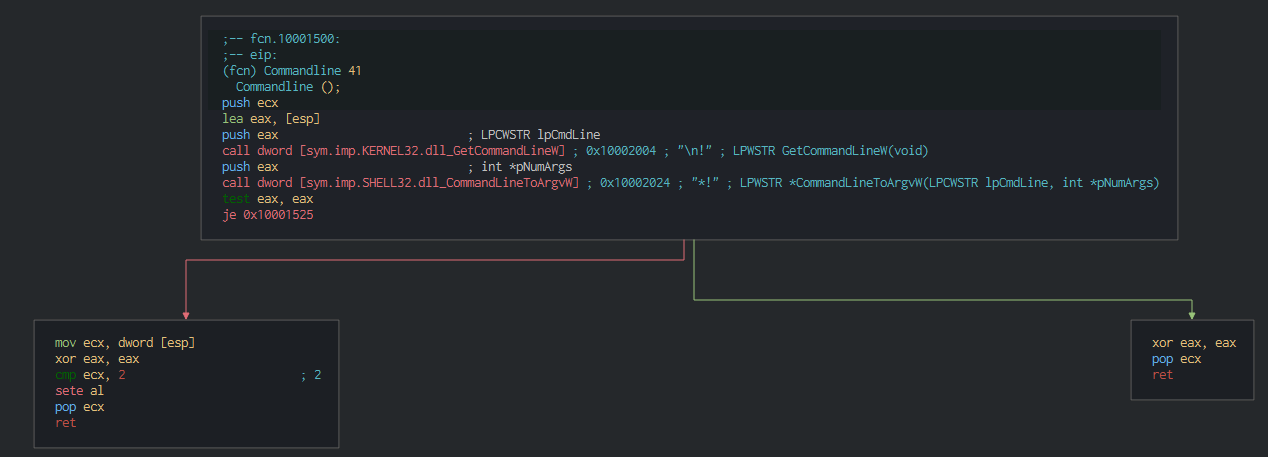
Also this use the function GetCommandLineA for getting a pointer to the command-line string for the current process.
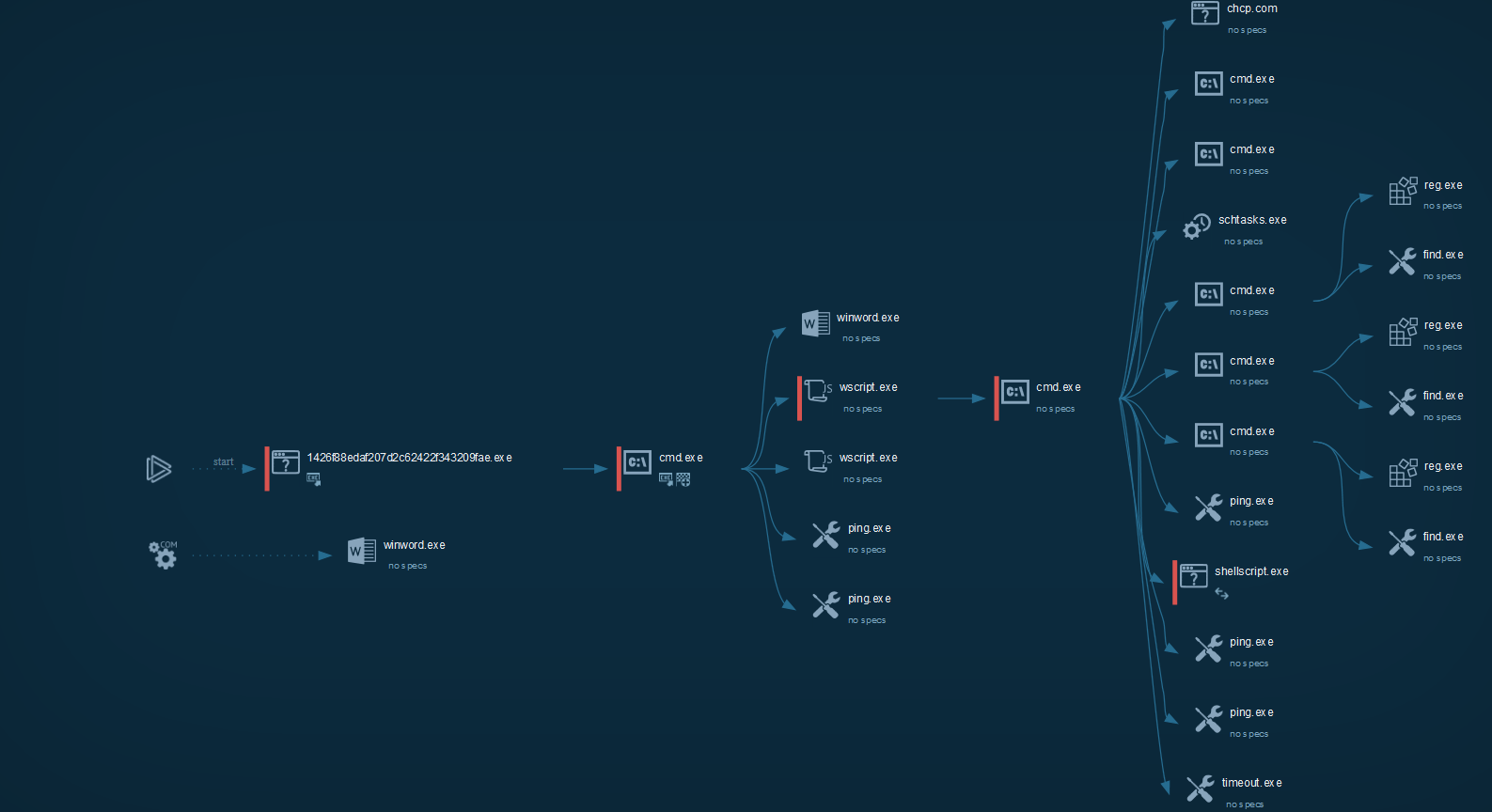
Cyber kill chain
The process graph resume the cyber kill chain used by the attacker. We can observe that the TTPs are the same.
Cyber Threat Intel
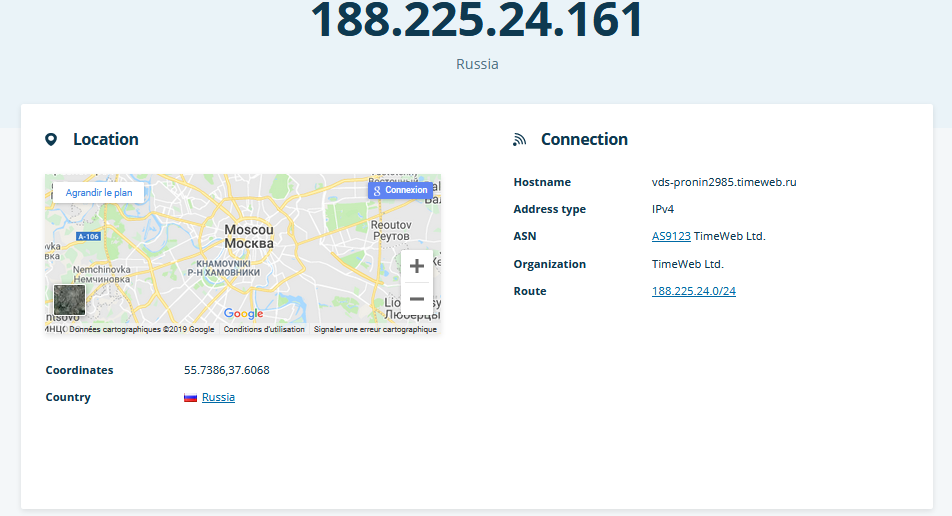
Both latest spotted samples have the same C2 hosted in a Russia provider.
The domain seems don't be registered on list of the domain added.
Like the last sample, this comes at a crisis period between Russia and Ukraine, Ukraine rest the main target of Gamaredon group.
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | T1059 - Starts CMD.EXE for commands execution T1106 - Execution through API T1053 - Scheduled Task T1064 - Scripting |
https://attack.mitre.org/techniques/T1059 https://attack.mitre.org/techniques/T1106 https://attack.mitre.org/techniques/T1053 https://attack.mitre.org/techniques/T1064 |
| Persistence | T1060 - Registry Run Keys / Startup Folder T1053 - Scheduled Task |
https://attack.mitre.org/techniques/T1060 https://attack.mitre.org/techniques/T1053 |
| Privilege Escalation | T1053 - Scheduled Task | https://attack.mitre.org/techniques/T1053 |
| Defense Evasion | T1112 - Modify Registry T1064 - Scripting |
https://attack.mitre.org/techniques/T1112 https://attack.mitre.org/techniques/T1064 |
| Discovery | T1012 - Query Registry | https://attack.mitre.org/techniques/T1012 |
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| 02013f0c6767eb7f0538510ba6ede0103e797fa7b9bc2733d00e3710702fdf1c.scr | 02013f0c6767eb7f0538510ba6ede0103e797fa7b9bc2733d00e3710702fdf1c |
| FDGSKGN.vbs | 630c0c86faf828bc4645526ca58b855d1a2db57cca0e406c1d5b7e2de88a1322 |
| PowerShellCertificates_C4BA3647.ps1 | 8f33ce796ee08525d32f5794ebd355914140e43e4b63e09b384dabda93a8b22c |
| 9856.txt | a48ad33695a44de887bba8f2f3174fd8fb01a46a19e3ec9078b0118647ccf599 |
| 176.57.215.22 | IP C2 |
| http[:]//shell-create.ddns.net/ | URL request |
| shell-create.ddns.net | Domain C2 |
This can be exported as JSON format Export in JSON
Links
- Original tweet: https://twitter.com/RedDrip7/status/1161900271477252101
- Ref previous analysiss: Gamaradon sample analysis 06-08-19
- Anyrun Links: