5.3 KiB
5.3 KiB
Malware analysis on Bitter APT campaign (31-08-19)
Table of Contents
- Malware analysis
- Cyber Threat Intel
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware-analysis
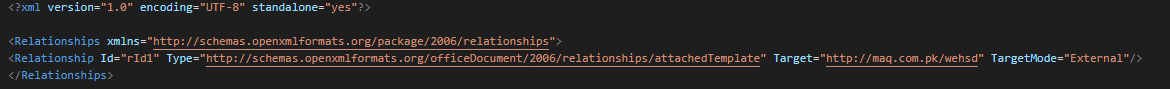
Initial vector
Use a document with a remote template injection as initial vector. This download the
Cyber kill chain
This process graph represents the cyber kill chain of Bitter sample.
Cyber Threat Intel
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| IMG76329797.xls | e66181155a9cd827def409135334ecf173459e001e79853e1b38f2b8e5d8cc59 |
| Inj.dll | 84833991F1705A01A11149C9D037C8379A9C2D463DC30A2FEC27BFA52D218FA6 |
| mse60dc.exe | de314d038d9b0f8ff32cfe3391c4eec53a3e453297978e46c9b90df2542ed592 |
| bitly.com | domain requested |
| xaasxasxasx.blogspot.com | domain requested |
| resources.blogblog.com domain requested | |
| pastebin.com domain requested | |
| 67.199.248.14 | ip requested |
| 67.199.248.15 | ip requested |
| 104.20.208.21 | ip requested |
| http[:]//www[.]bitly[.]com/aswoesx8sxwxxd | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/rjfk3j9m | HTTP/HTTPS requests |
| https[:]///pastebin[.]com/raw/tgP7S1Qe | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/0rhAppFq | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/c3V923PW | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/VFUXDF7C | HTTP/HTTPS requests |
| http[:]//www[.]ichoubyou[.]net/ao/?3f9L=Lo3E2+YBaBWDL2bUvw2B2SYfQBwPkMAIH1i2HT9ocxT5reT2XuVh6G9ligbLGsBAAwhLuQ==&BbBX=LhTpETx8Zdn | HTTP/HTTPS requests |
| http[:]//www[.]grupomsi[.]com/ao/?3f9L=Kbq++Y0aAgDxGCx7fxZFucXlrMdtuSyVttVG37Ejsga78k8ZP/EpUCryDr6PmBWAbaydAw==&BbBX=LhTpETx8Zdn&sql=1 | HTTP/HTTPS requests |
| http[:]//www[.]grupomsi[.]com/ao/ | HTTP/HTTPS requests |
| http[:]//www[.]theaterloops[.]com/ao/?3f9L=M0MA2fUiqMbVb6H3GNVaAqJS8mhIciwdMXRISKDsKJcWUJLkZY1j+YIFBEd9s0Uz5tYaIQ==&BbBX=LhTpETx8Zdn&sql=1 | HTTP/HTTPS requests |
| http[:]//www[.]theaterloops[.]com/ao/ | HTTP/HTTPS requests |
| http[:]//www[.]sukfat[.]com/ao/ | HTTP/HTTPS requests |
| http[:]//www[.]sukfat[.]com/ao/?3f9L=i08SS1jJNzlL2PYEM5jjY78DODQHD8SSq/VJ1wVBwRJ7J5CmvaFz3C5neJ7p21NB5nPOdg==&BbBX=LhTpETx8Zdn | HTTP/HTTPS requests |
| www[.]hongmenwenhua[.]com | Domain C2 |
| www[.]ichoubyou[.]net | Domain C2 |
| www[.]grupomsi[.]com | Domain C2 |
| www[.]sukfat[.]com | Domain C2 |
| www[.]theaterloops[.]com | Domain C2 |
| 210.188.195.164 | IP C2 |
| 23.20.239.12 | IP C2 |
| 185.68.16.122 | IP C2 |
| 199.192.23.220 | IP C2 |