3.1 KiB
3.1 KiB
APT33 continue to target US companies
Table of Contents
- Malware analysis
- Threat Intelligence
- Cyber kill chain
- Indicators Of Compromise (IOC)
- Yara Rules
- References MITRE ATT&CK Matrix
- Knowledge Graph
- Links
Malware analysis
The initial vector
Threat Intelligence
Cyber kill chain
The process graph resume cyber kill chains used by the attacker :
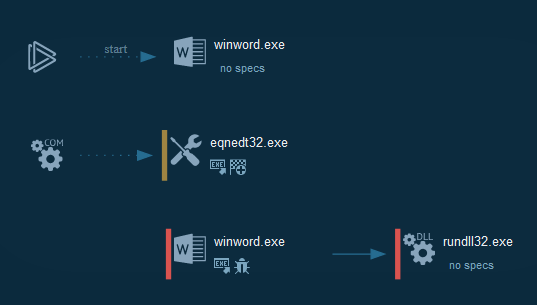
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
The IOC can be exported in JSON
References MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | Rundll32 Execution through Module Load User Execution |
https://attack.mitre.org/techniques/T1085/ https://attack.mitre.org/techniques/T1129/ https://attack.mitre.org/techniques/T1204/ |
| Persistence | Office Application Startup | https://attack.mitre.org/techniques/T1137/ |
| Defense Evasion | Rundll32 | https://attack.mitre.org/techniques/T1085/ |
| Discovery | Query Registry | https://attack.mitre.org/techniques/T1012/ |
This can be exported as JSON format Export in JSON
Yara Rules
A list of YARA Rule is available here
Knowledge Graph
The following diagram shows the relationships of the techniques used by the groups and their corresponding malware: