229 lines
20 KiB
Markdown
229 lines
20 KiB
Markdown
# Analysis of the Donot APT campaign
|
|
## Table of Contents
|
|
* [Malware analysis](#Malware-analysis)
|
|
+ [86ccedaa93743e83787f53e09e376713.docx](#malware1)
|
|
+ [d2263c15dfcccfef16ecf1c1c9304064befddf49cdbbd40abd12513481d7faf7.doc](#malware2)
|
|
+ [01d85719c5fec354431881f304307bb5521ecf6cb50eec4d3ec40d103dd3d3ae.docx](#malware3)
|
|
+ [pk_17e3a134ee4bcb50a9f608409853628ac619fd24cffd8d15868cf96ce63bb775.doc](#malware4)
|
|
+ [A1719.docx, INGOs Spending on Rohingyas.doc, Scan0012.docx](#malware5)
|
|
* [Cyber Threat Intel](#Cyber-Threat-Intel)
|
|
+ [Opendir analysis](#opendir)
|
|
+ [Victimology](#Victimology)
|
|
* [Indicators Of Compromise (IOC)](#IOC)
|
|
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
|
|
* [Links](#Links)
|
|
+ [Original Tweet](#Original-Tweet)
|
|
+ [Link Anyrun](#Links-Anyrun)
|
|
+ [Documents](#Documents)
|
|
|
|
## Malware analysis <a name="Malware-analysis"></a>
|
|
### 86ccedaa93743e83787f53e09e376713.docx <a name="malware1"></a>
|
|
###### The first sample of the campaign is a maldoc file using cve-2017-0199 (Template injection) for requests and executed the next stage of the infection.
|
|

|
|
###### This use RTF file with the cve-2018-0802 for execute embedded excel object by the CLSID of the Excel COM object. This push the persistence by lnk file for reload the infection on the Start Menu.
|
|

|
|

|
|
###### This extract and execute the zip archive from the RTF file.
|
|

|
|
###### On the backdoor, we can see that can push an environment variable and create the "Mknyh" Mutex.
|
|

|
|

|
|
###### After performing the action, this install the let's encrypt certificate and collect the informations about the system and send it in the C2.
|
|

|
|

|
|

|
|
###### This collects the list of disks and the types of this.
|
|

|
|
###### This can save and execute a stream from the C2.
|
|

|
|

|
|
### d2263c15dfcccfef16ecf1c1c9304064befddf49cdbbd40abd12513481d7faf7.doc <a name="malware2"></a>
|
|
###### The second samples use the same TTPs and use Template injection.
|
|

|
|
###### The RTF file download and executed to drop the same backdoor and same method of persistence by the Start Menu.
|
|

|
|
### 01d85719c5fec354431881f304307bb5521ecf6cb50eec4d3ec40d103dd3d3ae.docx <a name="malware3"></a>
|
|
###### The next sample uses Template injection too for download and executed to drop the RTF file.
|
|

|
|
###### The first RTF perform a redirection by template injection to the second RTF file extracts the backdoor and executes on another instance of explorer.
|
|

|
|
###### The backdoor uses a timer for as anti-sandbox method and check the features. Again add a persistence in Start Menu.
|
|

|
|

|
|
###### This push in memory the backdoor and check the system informations.
|
|

|
|

|
|
###### This has the capacity to hijack the AVAST AV, send the informations and request to the C2 for commands. This can save a file and execute it on the computer.
|
|

|
|

|
|

|
|
###### This send the informations collected to the C2, by parts in base 64 (Here on template sandbox). If the upload works this send a reply in base 64 (T0s= -> OK).
|
|

|
|
###### We can confirm that Backdoor.Win32.Mocker with a custom tag "WankyCat".
|
|
### pk_17e3a134ee4bcb50a9f608409853628ac619fd24cffd8d15868cf96ce63bb775.doc <a name="malware4"></a>
|
|
###### This continues to use Template injection and to push the persistence by Start Menu.
|
|

|
|
###### The RTF file dropped extract a js file, a dll and an exe file.
|
|

|
|
###### The js file executes the dll and the exe file for bypass the UAC by the UACme tool. The backdoor is the same that the first sample.
|
|

|
|

|
|
### A1719.docx, INGOs Spending on Rohingyas.doc, Scan0012.docx <a name="malware5"></a>
|
|
###### The TTPs is the same that the second sample for the last samples.
|
|

|
|

|
|
|
|
## Cyber Threat Intel <a name="Cyber-Threat-Intel"></a>
|
|
### Opendir analysis <a name="opendir"></a>
|
|
###### We can note that the server is main hosted by DigitalOcean cloud provider.
|
|
|IP|URL|Opendir|ASN|Organization|Route|Coordinates|Country|
|
|
| :---------------: | :--------------- | :---------------: | :---------------: | :---------------: | :---------------: | :---------------: |:---------------: |
|
|
|178.62.188.63|hxxp[:]//en-content.com/SecurityM/EFILE|Yes|AS14061|DigitalOcean Amsterdam|178.62.128.0/18|52.3740,4.8897|Netherlands|
|
|
|178.62.186.233|hxxp[:]//bsodsupport.icu/ScanSecurity/XLSSN|Yes|AS14061|DigitalOcean Amsterdam|178.62.128.0/18|52.3740,4.8897|Netherlands|
|
|
|156.67.222.128|hxxp[:]//noitfication-office-client.890m.com/fcfdae-9dfc335ca-bd10/NHSORE/jjhl|No|AS47583|Hostinger International Limited|156.67.208.0/20|1.3667,103.8000|Singapore|
|
|
|159.89.104.38|hxxp[:]//plug.msplugin.icu/MicrosoftSecurityScan/DOCSDOC|No|AS14061|DigitalOcean, LLC|159.89.96.0/20|50.1155,8.6842|Germany|
|
|
|157.230.213.81|hxxp[:]//mscheck.icu/SecurityScan/XLSS|No|AS14061|DigitalOcean, LLC|157.230.208.0/20|40.8043,-74.0121|United States|
|
|
|146.185.139.134|hxxp[:]//sdn.host/MicrosoftSecurityScan/11MVEM1X|No|AS14061|DigitalOcean Amsterdam|146.185.128.0/19|52.3740,4.8897|Netherlands|
|
|
|146.185.139.134|hxxp[:]//sdn.host/MicrosoftSecurityScan/FRSI080222F|No|AS14061|DigitalOcean Amsterdam|146.185.128.0/19|52.3740,4.8897|Netherlands|
|
|
###### The group use multiple OS and Web Servers, this can be explained by two possible reasons. First, Donot can be multiple groups with differents levels of skills or the attacker have don't protect some servers due this used for weak interest targets.
|
|
|
|
|IP|URL|Opendir|Webserver|OS|
|
|
| :---------------: | :---------------: | :---------------: | :---------------: | :---------------: |
|
|
|178.62.188.63|hxxp[:]//en-content.com/SecurityM/EFILE|Yes|Apache|CentOS|
|
|
|178.62.186.233|hxxp[:]//bsodsupport.icu/ScanSecurity/XLSSN|Yes|Apache|CentOS|
|
|
|156.67.222.128|hxxp[:]//noitfication-office-client.890m.com/fcfdae-9dfc335ca-bd10/NHSORE/jjhl|No|LiteSpeed|CentOS|
|
|
|159.89.104.38|hxxp[:]//plug.msplugin.icu/MicrosoftSecurityScan/DOCSDOC|No|Apache|CentOS|
|
|
|157.230.213.81|hxxp[:]//mscheck.icu/SecurityScan/XLSS|No|Nginx ?|Ubuntu ?|
|
|
|146.185.139.134|hxxp[:]//sdn.host/MicrosoftSecurityScan/11MVEM1X|No|Nginx|Ubuntu|
|
|
|146.185.139.134|hxxp[:]//sdn.host/MicrosoftSecurityScan/FRSI080222F|No|Nginx|Ubuntu|
|
|
###### List of files on the opendir :
|
|
|IP|URL|Files|Date (Last modified)|Size|
|
|
| :---------------: | :---------------: | :---------------: | :---------------: |:---------------: |
|
|
|178.62.188.63|hxxp[:]//en-content.com/SecurityM/|DFILE<br>DFILE-<br>EFILE<br>EFILE-<br>LIN|2019-08-30 12:46<br>2019-08-29 12:05<br>2019-08-30 12:49<br>2019-08-29 12:19<br>2019-08-30 12:49|1.1M<br>1.1M<br>685K<br>685K<br>685K|
|
|
|178.62.186.233|hxxp[:]//bsodsupport.icu/ScanSecurity/|DOCS<br>DOCSN<br>DOCSN-1<br>XLSS<br>XLSSN<br>XLSSN-1|2019-08-16 08:17<br>2019-08-27 07:03<br>2019-08-22 08:52<br>2019-08-16 08:26<br>2019-08-28 06:39<br>2019-08-22 08:59|1.1M<br>1.1M<br>1.7M<br>697K<br>685K<br>885K|
|
|
###### We can confirm that the campaign have begin early August 2019 and reuse old tools.
|
|

|
|
### Victimology <a name="Victimology"></a>
|
|
###### The victimology is based only on the actual enemies of India since the early August and focus on China (reconciliation with Greece) for help Pakistan in Kashmir crisis, Pakistan (Kashmir crisis), Iran (telecom directory) possible allied for Pakistan, same thing for Saudi Arabia.
|
|
###### We can see a transfer order for Chinese people in Greek.
|
|

|
|
###### But the more interesting rest the Iran number directory, we can see that originally available on the Ministry of Foreign Affairs in Nepal.
|
|

|
|

|
|
###### Now, we can observe that the content is removed from the website.
|
|

|
|
###### This rest possible to findable this in the cache.This can give a probable conclusion that Iran will be aware about the Donot operation against, or Nepal is aware about it.
|
|

|
|
###### This offers an idea when the group have found and reedit the pdf to word document for weaponizing it as opportunity to exploit. This is interesting to note this that the group will limit as domains known rather than novelty, it would have been possible to edit the pdf with a JavaScript shellcode for the same result.
|
|
###### This can note that a group in the Donot organization is charged to collect the opportunities to exploit. We can note too that the group reuse old operations and samples for theirs operations.
|
|

|
|
|
|
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
|
###### The process graphs resume all the cyber kill chains used by the attacker.
|
|

|
|
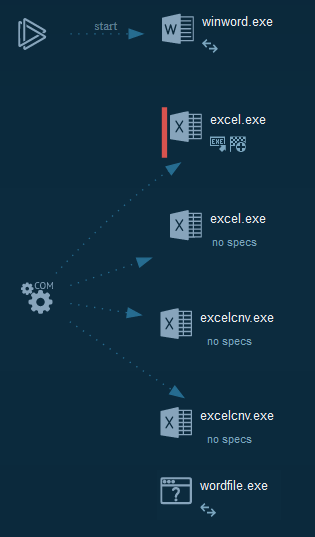
|
|
###### We can note that in majority of time, this use RTF exploits as downloader and execution methods.
|
|
## References MITRE ATT&CK Matrix <a name="Ref-MITRE-ATTACK"></a>
|
|
###### List of all the references with MITRE ATT&CK Matrix
|
|
|
|
|Enterprise tactics|Technics used|Ref URL|
|
|
| :---------------: |:-------------| :------------- |
|
|
|Discovery|Query Registry|https://attack.mitre.org/techniques/T1012/|
|
|
|Execution|Command-Line Interface<br>Rundll32<br>Execution through Module Load<br>Exploitation for Client Execution<br>User Execution|https://attack.mitre.org/techniques/T1059/<br>https://attack.mitre.org/techniques/T1085/<br>https://attack.mitre.org/techniques/T1129/<br>https://attack.mitre.org/techniques/T1203/<br>https://attack.mitre.org/techniques/T1204/|
|
|
|Lateral Movement|Remote File Copy|https://attack.mitre.org/techniques/T1105/|
|
|
|Persistence|Registry Run Keys / Startup Folder|https://attack.mitre.org/techniques/T1060/|
|
|
|Defense Evasion|Rundll32|https://attack.mitre.org/techniques/T1085/|
|
|
|
|
|
|
## Indicators Of Compromise (IOC) <a name="IOC"></a>
|
|
|
|
###### List of all the Indicators Of Compromise (IOC)
|
|
|
|
| Indicator | Description|
|
|
| ------------- |:-------------:|
|
|
|86ccedaa93743e83787f53e09e376713.docx|36eb4d0e5f2435e6a01d10ac9e0b362e49de990ac841ba536f63d5be76e99794|
|
|
|d2263c15dfcccfef16ecf1c1c9304064befddf49cdbbd40abd12513481d7faf7.docx|d2263c15dfcccfef16ecf1c1c9304064befddf49cdbbd40abd12513481d7faf7|
|
|
|01d85719c5fec354431881f304307bb5521ecf6cb50eec4d3ec40d103dd3d3ae.docx|01d85719c5fec354431881f304307bb5521ecf6cb50eec4d3ec40d103dd3d3ae|
|
|
|pk_17e3a134ee4bcb50a9f608409853628ac619fd24cffd8d15868cf96ce63bb775|17e3a134ee4bcb50a9f608409853628ac619fd24cffd8d15868cf96ce63bb775|
|
|
|A1719.docx|6b5d8a52ca5c9e90339c6c0f574dd5f6c4aaa63c88cf974d8caf6e3690259c14|
|
|
|57ecda52cfb12afa08e84fe86cd61a95.zip|557cdd4332765a5d223693f5c1e605bae17464919fd57f9a62a86e33cb07be7e|
|
|
|Scan0012.docx|5a19a1df087e0cc12e554b04dc383fb50b7c4a926ac34611acb43ab3cc4404e9|
|
|
|kb8989476.rtf|51dfa1d8c62598b0d03f77faa57887dcdeb0075216c35f5018609fbcb82c8672|
|
|
|C:\Windows\Tasks\wordfile.exe|9a3061631ff634d8f573b36c885e41f8d4508c53f372c858b8b484b1f928b49f|
|
|
|wine.exe|bb5d713e81f782fc1bbd636eb97689e2010e71f4219ef80b90d979a6045b345a|
|
|
|C:\Windows\Tasks\A64.dll|894bd1b82b451fd08d8ac3a3d4e8e248bbc1c153c557aebdfeaa7e1ffafef4d6|
|
|
|C:\Windows\Tasks\Serviceflow.exe|ecbaac40bd504defe4f5eaba468e53de10e99f4dca5d05790d26e3ee4e5ce37f|
|
|
|C:\Windows\Tasks\sinter.exe|6584b9e3849142d9c479ca58a0098636b556220e76b1ae1376f56dbdb80feb56|
|
|
|C:\ProgramData\AudioDriver64\Olmapi32.dll|bc362886422771ee4059284095c49da865ffaf73d2dbb1de3cf5f2ace568617d|
|
|
|EFILE|b64691a3fff3b17eb1a169180f470bf1ea36c7793fe36e93ba8aad55fe4a5a83|
|
|
|DFILE|746b2a03a6413f97b66fc96c3e12204488f13f0c4b2255bee427b54291a9a639|
|
|
|DFILE-|ddc7d7cdc8ceb6a9c5cc776ccd7916cd4c16612aa54c5e0a9827303c6ab38eef|
|
|
|EFILE-|ed4a1c94b4e3b813ac352446aded7a7bbe1698cba436451a7d54b0bc55bf5b52|
|
|
|DOCS|322f48a07af27b22f9cd29f14abe390349262ac9db901759b03553fe0d71446e|
|
|
|DOCSN|c0a23116c1c7ced59ff8eae5ee96a48d436dd2e5b435a291003889d2ed9489e1|
|
|
|DOCSN-1|0ed911e6d672e8a830d13b2f62a06a74dd7bfff82a31cc8a5c169f2689c4255b|
|
|
|XLSS|365b35cff4e0314c6fa2bb5cd66d6040efba93b5857d5536bd6fea4d871afe33|
|
|
|XLSSN|cea33a195f791bb5db28d53b3a81dd407e107aa33a913475d07080df6167e7c6|
|
|
|XLSSN-1|f345c969b58aeda8e78743db529f3a0ff81ba227880bd90d46e47bf9a37b932b|
|
|
|en-content.com|Domain requested|
|
|
|bsodsupport.icu|Domain requested|
|
|
|cloud-storage-service.com|Domain requested|
|
|
|office360-pub.16mb.com|Domain requested|
|
|
|noitfication-office-client.890m.com|Domain requested|
|
|
|plug.msplugin.icu|Domain requested|
|
|
|mscheck.icu|Domain requested|
|
|
|sdn.host|Domain requested|
|
|
|178.62.186.233|IP requested|
|
|
|178.62.188.63|IP requested|
|
|
|156.67.222.128|IP requested|
|
|
|159.89.104.38|IP requested|
|
|
|157.230.213.81|IP requested|
|
|
|146.185.139.134|IP requested|
|
|
|hxxp[:]//en-content.com/SecurityM/EFILE|HTTP/HTTPS requests|
|
|
|hxxp[:]//en-content.com/SecurityM/DFILE|HTTP/HTTPS requests|
|
|
|hxxp[:]//en-content.com/SecurityM/DFILE-|HTTP/HTTPS requests|
|
|
|hxxp[:]//en-content.com/SecurityM/EFILE-|HTTP/HTTPS requests|
|
|
|hxxp[:]//en-content.com/SecurityM/LIN|HTTP/HTTPS requests|
|
|
|hxxp[:]//bsodsupport.icu/ScanSecurity/DOCS|HTTP/HTTPS requests|
|
|
|hxxp[:]//bsodsupport.icu/ScanSecurity/DOCSN|HTTP/HTTPS requests|
|
|
|hxxp[:]//bsodsupport.icu/ScanSecurity/DOCSN-1|HTTP/HTTPS requests|
|
|
|hxxp[:]//bsodsupport.icu/ScanSecurity/XLSS|HTTP/HTTPS requests|
|
|
|hxxp[:]//bsodsupport.icu/ScanSecurity/XLSSN|HTTP/HTTPS requests|
|
|
|hxxp[:]//bsodsupport.icu/ScanSecurity/XLSSN-1|HTTP/HTTPS requests|
|
|
|hxxp[:]//cloud-storage-service.com/pub/officex32x64/kb8989476|HTTP/HTTPS requests|
|
|
|hxxp[:]//noitfication-office-client.890m.com/fcfdae-9dfc335ca-bd10/NHSORE/jjhl|HTTP/HTTPS requests|
|
|
|hxxp[:]//plug.msplugin.icu/MicrosoftSecurityScan/DOCSDOC|HTTP/HTTPS requests|
|
|
|hxxp[:]//mscheck.icu/SecurityScan/XLSS|HTTP/HTTPS requests|
|
|
|hxxp[:]//sdn.host/MicrosoftSecurityScan/11MVEM1X|HTTP/HTTPS requests|
|
|
|hxxp[:]//sdn.host/MicrosoftSecurityScan/FRSI080222F|HTTP/HTTPS requests|
|
|
|hxxp[:]//account-support.site/supp/accsite/cod.php|HTTP/HTTPS requests|
|
|
|support.worldupdate.live|Domain C2|
|
|
|account-support.site|Domain C2|
|
|
|skillsnew.top|Domain C2|
|
|
|mystrylust.pw|Domain C2|
|
|
|216.170.126.139|IP C2|
|
|
|46.105.40.12|IP C2|
|
|
|82.196.7.221|IP C2|
|
|
|37.139.28.208|IP C2|
|
|
|
|
###### This can be exported as JSON format [Export in JSON](https://raw.githubusercontent.com/StrangerealIntel/CyberThreatIntel/master/Indian/APT/Donot/17-09-19/IOC_Donot_25-09-19.json)
|
|
|
|
## Links <a name="Links"></a>
|
|
###### Original tweet: [https://twitter.com/Timele9527/status/1173431630171492352](https://twitter.com/Timele9527/status/1173431630171492352) <a name="Original-Tweet"></a>
|
|
###### Links Anyrun: <a name="Links-Anyrun"></a>
|
|
###### Samples :
|
|
* [86ccedaa93743e83787f53e09e376713.docx](https://app.any.run/tasks/0df3deaf-e8e9-4b23-8b64-fed49b85811f)
|
|
* [d2263c15dfcccfef16ecf1c1c9304064befddf49cdbbd40abd12513481d7faf7.doc](https://app.any.run/tasks/63251738-19fb-4155-ae23-0a8d4d780682)
|
|
* [01d85719c5fec354431881f304307bb5521ecf6cb50eec4d3ec40d103dd3d3ae.docx](https://app.any.run/tasks/43bb63ce-4c78-4c1c-ae1d-a85b0106d983)
|
|
* [17e3a134ee4bcb50a9f608409853628ac619fd24cffd8d15868cf96ce63bb775.doc](https://app.any.run/tasks/e194a69c-9e4e-4c7b-9e73-f6b144af95e1)
|
|
* [A1719.docx](https://app.any.run/tasks/524aff0c-2f82-4f03-8ad0-16928adcf1f2)
|
|
* [INGOs Spending on Rohingyas.doc](https://app.any.run/tasks/411a27d8-9b47-4f87-bd06-35d813ab1457)
|
|
* [Scan0012.docx](https://app.any.run/tasks/f3397ba6-f8a0-46c5-b40f-f91bdfddc5db)
|
|
* [wine.exe](https://app.any.run/tasks/aeb75861-d2bc-4a2c-863f-6ec10f758abf)
|
|
|
|
###### Opendir:
|
|
* [SecurityM Opendir](https://app.any.run/tasks/793250a3-e767-47a8-9042-fce7c89a0471)
|
|
* [ScanSecurity Opendir](https://app.any.run/tasks/ae0325de-4aa2-40f0-8b17-1ca540cf2b9f)
|
|
###### Documents: <a name="Documents"></a>
|
|
* [UACme](https://github.com/hfiref0x/UACME)
|