Blog - Picture in description
parent
8b23da02c9
commit
1eb5595f01
|
|
@ -5,10 +5,10 @@ title: UYBHYS - Sea Monster Attack & Defense CTF
|
||||||
|
|
||||||
Last week-end I teamed up with members from [Aperikube](https://www.aperikube.fr) for an Attack/Defense CTF which took place in Brest - France. In this "small" blog post I will write about this experience, the challenges and our methodology :)
|
Last week-end I teamed up with members from [Aperikube](https://www.aperikube.fr) for an Attack/Defense CTF which took place in Brest - France. In this "small" blog post I will write about this experience, the challenges and our methodology :)
|
||||||
|
|
||||||
<!--more-->
|
|
||||||
|
|
||||||
{: .center-image }
|
{: .center-image }
|
||||||
|
|
||||||
|
<!--more-->
|
||||||
|
|
||||||
Rules & informations about the CTF are available in the following PDF : [CTF_UYBHYS.pdf]({{ site.baseurl }}/files/CTF_UYBHYS.pdf)
|
Rules & informations about the CTF are available in the following PDF : [CTF_UYBHYS.pdf]({{ site.baseurl }}/files/CTF_UYBHYS.pdf)
|
||||||
|
|
||||||
## CTF Architecture
|
## CTF Architecture
|
||||||
|
|
|
||||||
|
|
@ -5,10 +5,17 @@ title: Ph0wn - Smart Devices CTF
|
||||||
|
|
||||||
Another week another CTF, this time it was the [Ph0wn](https://ph0wn.org) at Sophia Antipolis (France). I teamed up with members from [@Maki](https://twitter.com/maki_mitz), [@iansus](https://twitter.com/iansus), [@MansourCyril](https://twitter.com/MansourCyril) and [@0hax](https://twitter.com/0hax2). We reached the **second place** of this IoT/Hardware CTF.
|
Another week another CTF, this time it was the [Ph0wn](https://ph0wn.org) at Sophia Antipolis (France). I teamed up with members from [@Maki](https://twitter.com/maki_mitz), [@iansus](https://twitter.com/iansus), [@MansourCyril](https://twitter.com/MansourCyril) and [@0hax](https://twitter.com/0hax2). We reached the **second place** of this IoT/Hardware CTF.
|
||||||
|
|
||||||
<!--more-->
|
|
||||||
|
|
||||||
{: .center-image }
|
{: .center-image }
|
||||||
|
|
||||||
|
Challenges:
|
||||||
|
|
||||||
|
- [Rookie - Sunny day](#)
|
||||||
|
- [Hardware - Ant-Maker](#)
|
||||||
|
- [Misc - Compromised Sensor](#)
|
||||||
|
- [Misc - Domotics](#)
|
||||||
|
- [Crypto - Shamir Quest](#)
|
||||||
|
|
||||||
|
<!--more-->
|
||||||
|
|
||||||
## Writeups' challenges
|
## Writeups' challenges
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -7,10 +7,10 @@ title: DVID - Damn Vulnerable IoT Device
|
||||||
|
|
||||||
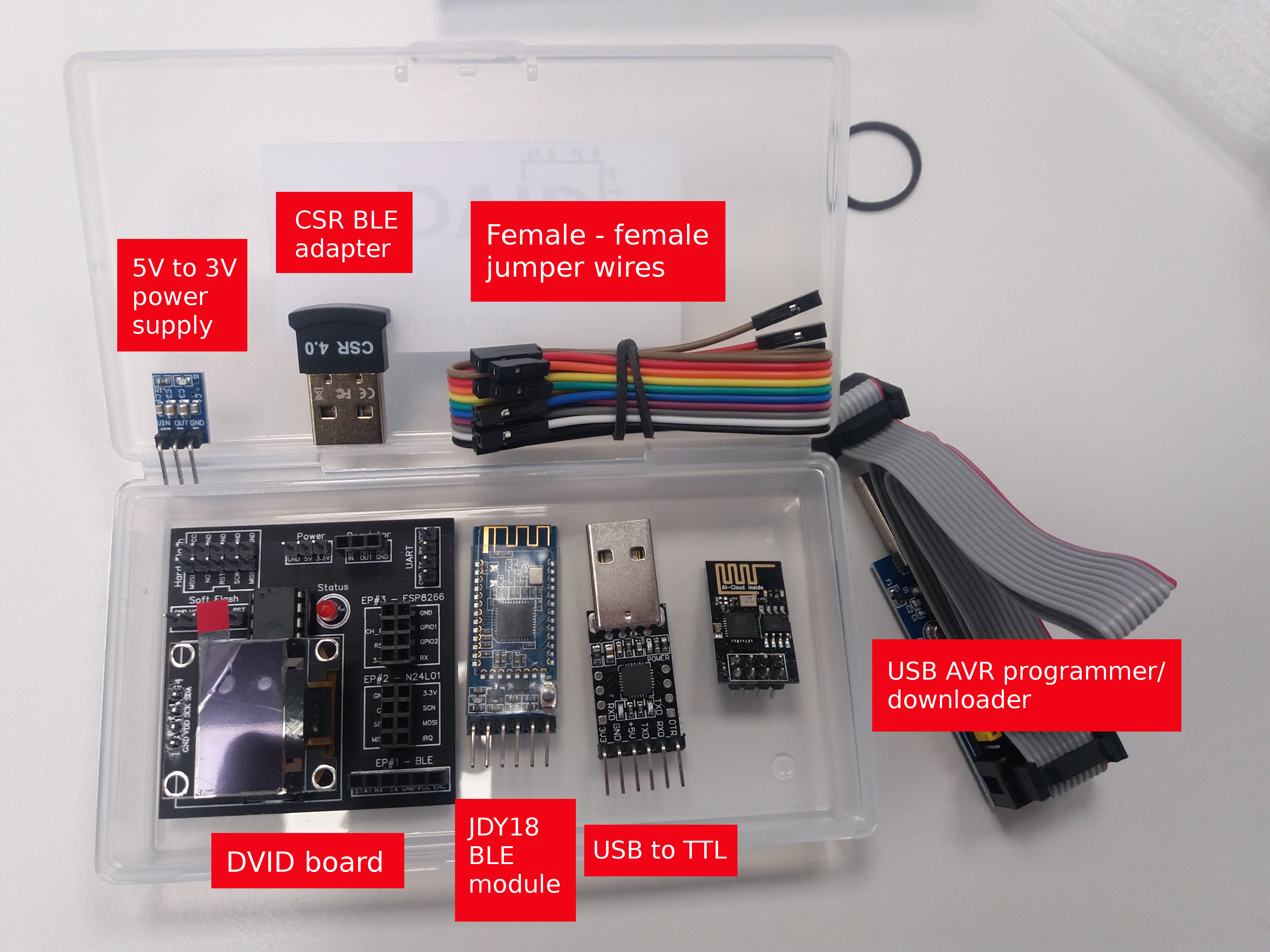
Who ever wanted to learn about Hardware Hacking ? I found this small opensource **IoT hacking** learning board while I was in a security event. It is designed by [@vulcainreo](https://twitter.com/vulcainreo/) and cost around 45€, more than 300 units were shipped around the world.
|
Who ever wanted to learn about Hardware Hacking ? I found this small opensource **IoT hacking** learning board while I was in a security event. It is designed by [@vulcainreo](https://twitter.com/vulcainreo/) and cost around 45€, more than 300 units were shipped around the world.
|
||||||
|
|
||||||
<!--more-->
|
|
||||||
|
|
||||||
Let's dig into this awesome project and clone the git : `https://github.com/Vulcainreo/DVID.git` !
|
Let's dig into this awesome project and clone the git : `https://github.com/Vulcainreo/DVID.git` !
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
## Challenges' Writeup
|
## Challenges' Writeup
|
||||||
|
|
||||||
* [Hardware - findTheDatasheet](#hardware---findthedatasheet)
|
* [Hardware - findTheDatasheet](#hardware---findthedatasheet)
|
||||||
|
|
@ -18,6 +18,8 @@ Let's dig into this awesome project and clone the git : `https://github.com/Vulc
|
||||||
* [Firmware - Hardcoded Password](#firmware---hardcoded-password)
|
* [Firmware - Hardcoded Password](#firmware---hardcoded-password)
|
||||||
* [Bluetooth - Advertising](#bluetooth---advertising)
|
* [Bluetooth - Advertising](#bluetooth---advertising)
|
||||||
|
|
||||||
|
<!--more-->
|
||||||
|
|
||||||
### Hardware - findTheDatasheet
|
### Hardware - findTheDatasheet
|
||||||
|
|
||||||
> A password is displayed on the pin PD1
|
> A password is displayed on the pin PD1
|
||||||
|
|
|
||||||
Loading…
Reference in New Issue