Gadget M5Core2 + HydraBus Update
parent
c349f12c5d
commit
4a47c29293
Binary file not shown.
|
After Width: | Height: | Size: 182 KiB |
Binary file not shown.
|
After Width: | Height: | Size: 75 KiB |
|
|
@ -1,15 +1,20 @@
|
||||||
# Bus Pirate
|
# Bus Pirate
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
## Update Bus Pirate
|
## Firmwares
|
||||||
|
|
||||||
```powershell
|
* [BusPirate/Bus_Pirate](https://github.com/BusPirate/Bus_Pirate)
|
||||||
git clone https://github.com/BusPirate/Bus_Pirate.git
|
```powershell
|
||||||
cd Bus_Pirate/package/BPv4-firmware/pirate-loader-v4-source/pirate-loader_lnx
|
cd Bus_Pirate/package/BPv4-firmware/pirate-loader-v4-source/pirate-loader_lnx
|
||||||
sudo ./pirate-loader_lnx --dev=/dev/ttyACM0 --hex=../BPv4-firmware-v6.3-r2151.hex
|
sudo ./pirate-loader_lnx --dev=/dev/ttyACM0 --hex=../BPv4-firmware-v6.3-r2151.hex
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
## Examples
|
||||||
|
|
||||||
|
Dump firmware over SPI using a Bus Pirate
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
# Identify EEPROM chip
|
# Identify EEPROM chip
|
||||||
|
|
@ -23,3 +28,5 @@ sudo flashrom -p Buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -c (Chip name) -r (
|
||||||
## References
|
## References
|
||||||
|
|
||||||
* [Bus Pirate Unboxing - Toolkit - Hacker Warehouse - 4 juin 2018](https://youtu.be/lP8vMvBu3Bg)
|
* [Bus Pirate Unboxing - Toolkit - Hacker Warehouse - 4 juin 2018](https://youtu.be/lP8vMvBu3Bg)
|
||||||
|
* [Bus Pirate 5 REV 10 Hardware](https://hardware.buspirate.com/)
|
||||||
|
* [Ph0wn, my first IoT CTF - Part 2 - Sebastien Andrivet - 19 December 2018](https://sebastien.andrivet.com/fr/posts/ph0wn-my-first-iot-ctf-part-2/)
|
||||||
|
|
@ -2,7 +2,7 @@
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## **Firmwares**
|
## Firmwares
|
||||||
|
|
||||||
* [Flipper Zero Firmware](https://github.com/flipperdevices/flipperzero-firmware)
|
* [Flipper Zero Firmware](https://github.com/flipperdevices/flipperzero-firmware)
|
||||||
* [Flipper Zero Unleashed Firmware](https://github.com/Eng1n33r/flipperzero-firmware)
|
* [Flipper Zero Unleashed Firmware](https://github.com/Eng1n33r/flipperzero-firmware)
|
||||||
|
|
@ -32,9 +32,15 @@
|
||||||
* [Flipper Zero: Want some good news? - Penthertz](https://www.youtube.com/watch?v=tB0eYatvu0k)
|
* [Flipper Zero: Want some good news? - Penthertz](https://www.youtube.com/watch?v=tB0eYatvu0k)
|
||||||
* [Flipper Zero: is this for you? Follow our 1st tests! - Penthertz](https://www.youtube.com/watch?v=W5YYObSBUno)
|
* [Flipper Zero: is this for you? Follow our 1st tests! - Penthertz](https://www.youtube.com/watch?v=W5YYObSBUno)
|
||||||
|
|
||||||
|
|
||||||
## Tutorials and Resources
|
## Tutorials and Resources
|
||||||
|
|
||||||
* [Flipper Zero Hacking 101 - pingywon](https://flipper.pingywon.com/flipper/)
|
* [Flipper Zero Hacking 101 - pingywon](https://flipper.pingywon.com/flipper/)
|
||||||
* [Flipper Zero Playground - UberGuidoZ](https://github.com/UberGuidoZ/Flipper)
|
* [Flipper Zero Playground - UberGuidoZ](https://github.com/UberGuidoZ/Flipper)
|
||||||
* [Flashing Flipper Zero with RogueMaster CFW](https://interestingsoup.com/n00b-guide-flashing-flipper-zero-to-rougemaster/)
|
* [Flashing Flipper Zero with RogueMaster CFW](https://interestingsoup.com/n00b-guide-flashing-flipper-zero-to-rougemaster/)
|
||||||
* [Unleashed Firmware - Update firmware](https://github.com/DarkFlippers/unleashed-firmware/blob/dev/documentation/HowToInstall.md)
|
* [Unleashed Firmware - Update firmware](https://github.com/DarkFlippers/unleashed-firmware/blob/dev/documentation/HowToInstall.md)
|
||||||
|
|
||||||
|
|
||||||
|
## References
|
||||||
|
|
||||||
|
* [The Ultimate Guide / CheatSheet to Flipper Zero - Ilias Mavropoulos - 17/01/2024](https://infosecwriteups.com/the-ultimate-guide-cheatsheet-to-flipper-zero-d4c42d79d32c)
|
||||||
|
|
@ -1,6 +1,6 @@
|
||||||
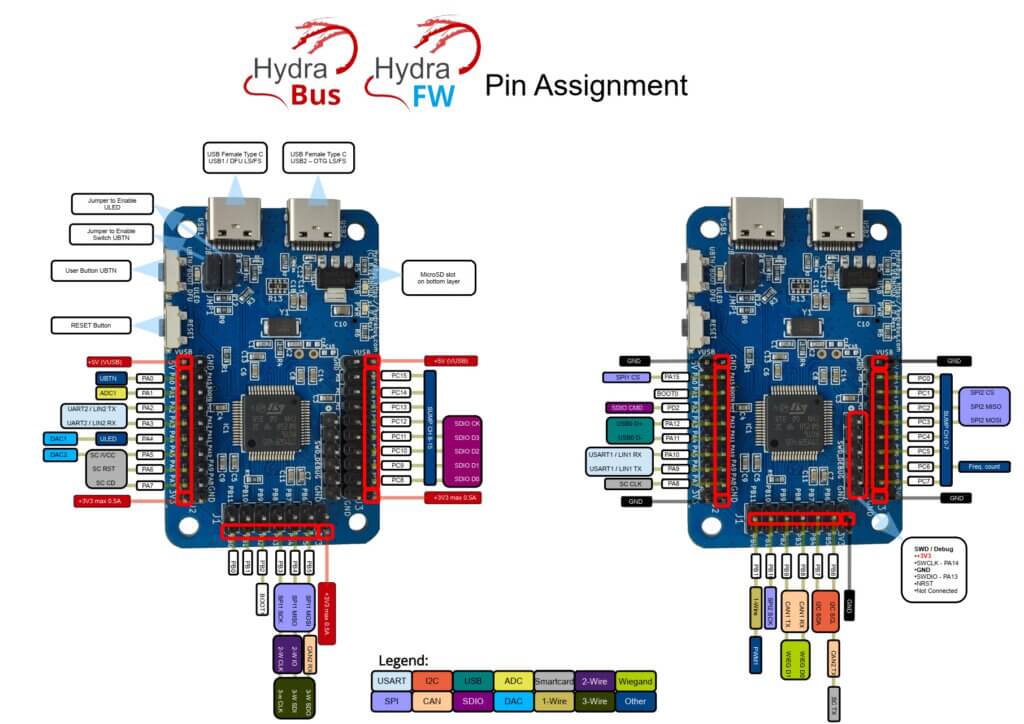
# HydraBus
|
# HydraBus
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
|
||||||
## Features
|
## Features
|
||||||
|
|
@ -16,11 +16,17 @@ External interactions:
|
||||||
- UART
|
- UART
|
||||||
- I2C
|
- I2C
|
||||||
- CAN/LIN Bus
|
- CAN/LIN Bus
|
||||||
|
- SUMP
|
||||||
|
- JTAG
|
||||||
- SPI Bus
|
- SPI Bus
|
||||||
- SD/SDIO
|
- SD/SDIO
|
||||||
- USB Bus
|
- USB Bus
|
||||||
- ADC / DAC (Analog / Digital)
|
- ADC / DAC (Analog / Digital)
|
||||||
- GPIO
|
- GPIO
|
||||||
|
- NFC
|
||||||
|
- Wiegand
|
||||||
|
- NAND flash
|
||||||
|
- 1-wire,2-wire,3-wire
|
||||||
|
|
||||||
|
|
||||||
## Firmware
|
## Firmware
|
||||||
|
|
@ -29,16 +35,50 @@ External interactions:
|
||||||
* [hydrabus/hydrafw_hydranfc_shield_v2](https://github.com/hydrabus/hydrafw_hydranfc_shield_v2) - HydraFW dedicated to HydraBus v1 / HydraNFC Shield v2
|
* [hydrabus/hydrafw_hydranfc_shield_v2](https://github.com/hydrabus/hydrafw_hydranfc_shield_v2) - HydraFW dedicated to HydraBus v1 / HydraNFC Shield v2
|
||||||
* [bvernoux/blackmagic](https://github.com/bvernoux/blackmagic) - In application debugger for ARM Cortex microcontrollers
|
* [bvernoux/blackmagic](https://github.com/bvernoux/blackmagic) - In application debugger for ARM Cortex microcontrollers
|
||||||
|
|
||||||
Commands examples:
|
|
||||||
|
|
||||||
```ps1
|
## Commands
|
||||||
show system/memory/threads
|
|
||||||
```
|
* Basic info: `show system`
|
||||||
|
```ps1> show system
|
||||||
|
HydraFW (HydraBus) v0.11-1-g4d74500 2023-05-09
|
||||||
|
sysTime: 0x000d82dd.
|
||||||
|
cyclecounter: 0x76ac02b9 cycles.
|
||||||
|
cyclecounter64: 0x0000000076ac02cb cycles.
|
||||||
|
10ms delay: 1680035 cycles.
|
||||||
|
```
|
||||||
|
|
||||||
|
* Determine the port name: `ls -l /dev/tty*`
|
||||||
|
* Interact witht the HydraBus: `screen /dev/ttyACM0`
|
||||||
|
* Switch to SPI mode: `spi`
|
||||||
|
* Determine the pin for SPI: `show pins`
|
||||||
|
|
||||||
|
|
||||||
|
## Syntax
|
||||||
|
|
||||||
|
| Value | Description |
|
||||||
|
|-------|-------------|
|
||||||
|
| [ | Chip select (CS) active (low) |
|
||||||
|
| ] | CS disable (high) |
|
||||||
|
| r | Read one byte by sending dummy byte (0xff). r:1...255 for bulk reads |
|
||||||
|
| hd | Read one byte by sending dummy byte (0xff). hd:1...4294967295 for bulk reads. Displays a hexdump of the result |
|
||||||
|
| w | Followed by values to write byte(s). w:1...255 for bulk writes |
|
||||||
|
| 0b | Write this binary value. Format is 0b00000000 for a byte, but partial bytes are also fine: 0b1001 |
|
||||||
|
| 0 | Write this Octal value. Format is prefixed by a 0 (values from 000 to 077) |
|
||||||
|
| " | Write an ASCII-encoded string |
|
||||||
|
| 0h/0x | Write this HEX value. Format is 0h01 or 0x01. Partial bytes are fine: 0xA. A-F can be lower-case or capital letters |
|
||||||
|
| 0-255 | Write this decimal value. Any number not preceded by 0x, 0h, or 0b is interpreted as a decimal value |
|
||||||
|
|
||||||
|
Examples:
|
||||||
|
|
||||||
|
* Read Identification (0x9F): `[ 0x9F r:3 ]`
|
||||||
|
* Read Data (0x03) at the address (0x00:3) and read 32 bytes (hd:32) `[ 0x03 0x00:3 hd:32 ]`
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
|
* [HydraBus/HydraFW wiki - Benjamin Vernoux - Jan 21, 2021](https://github.com/hydrabus/hydrafw/wiki/)
|
||||||
* [HydraBus v1.0 Specifications - HydraBus](https://hydrabus.com/hydrabus-1-0-specifications)
|
* [HydraBus v1.0 Specifications - HydraBus](https://hydrabus.com/hydrabus-1-0-specifications)
|
||||||
* [HydraBus Assembly Video - Lab401 - 30 may 2017](https://youtu.be/9lFEPG8EG6w)
|
* [HydraBus Assembly Video - Lab401 - 30 may 2017](https://youtu.be/9lFEPG8EG6w)
|
||||||
* [BlackAlps17: Hydrabus: Lowering the entry fee to the IoT bugfest - Benjamin Vernoux - 2 dec. 2017](https://www.youtube.com/watch?v=theYbzPhYH8)
|
* [BlackAlps17: Hydrabus: Lowering the entry fee to the IoT bugfest - Benjamin Vernoux - 2 dec. 2017](https://www.youtube.com/watch?v=theYbzPhYH8)
|
||||||
* [HydraBus - An Open Source Platform - RMLL Sec 2017](https://archives.pass-the-salt.org/RMLL%20Security%20Tracks/2017/slides/RMLL-Sec-2017-hydrabus.pdf)
|
* [HydraBus - An Open Source Platform - RMLL Sec 2017](https://archives.pass-the-salt.org/RMLL%20Security%20Tracks/2017/slides/RMLL-Sec-2017-hydrabus.pdf)
|
||||||
|
* [Ph0wn, my first IoT CTF - Part 3 - Sebastien Andrivet - Dec. 19, 2018](https://sebastien.andrivet.com/en/posts/ph0wn-my-first-iot-ctf-part-3/)
|
||||||
|
|
@ -0,0 +1,44 @@
|
||||||
|
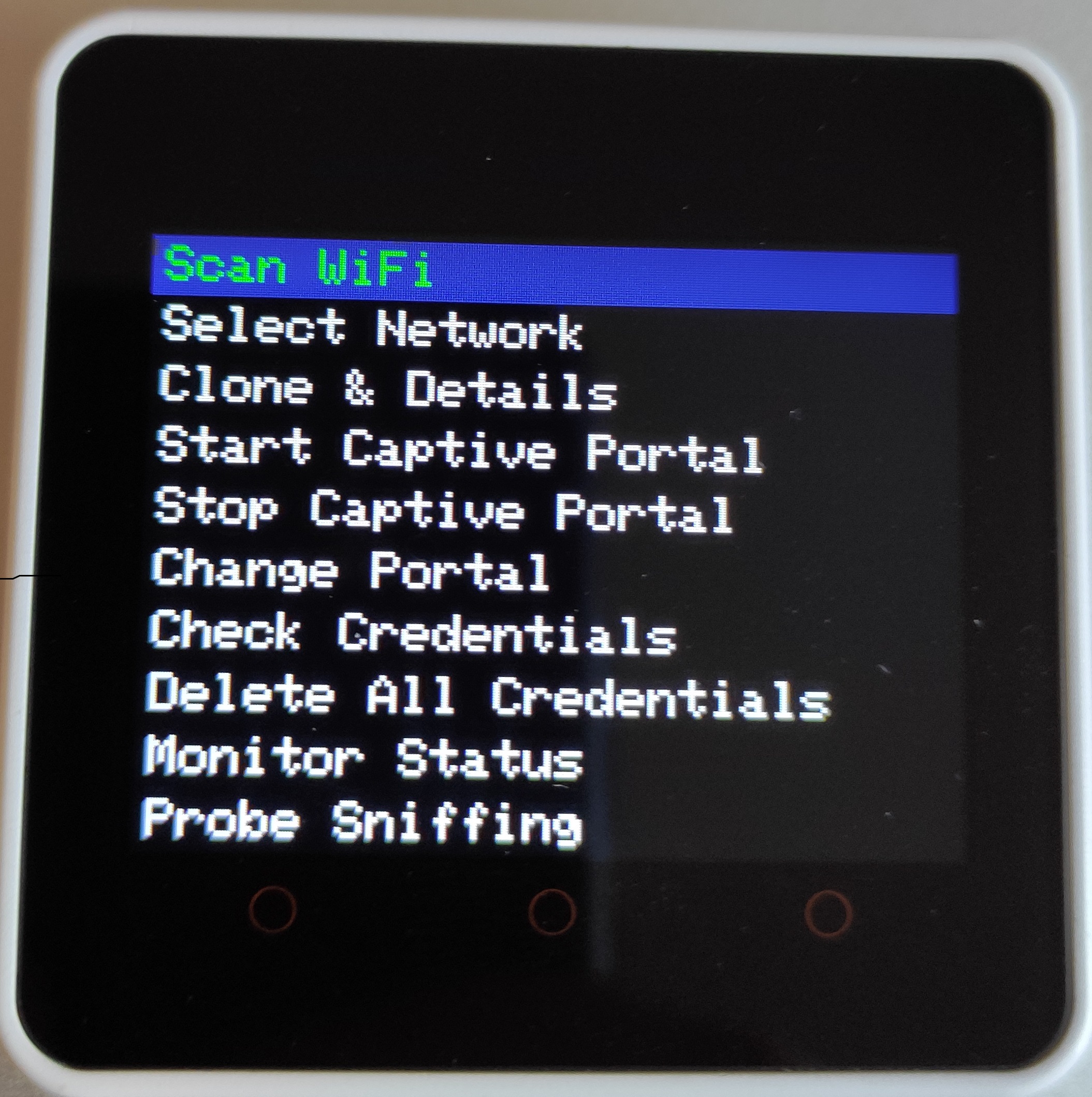
# Evil M5Core2
|
||||||
|
|
||||||
|
> Evil-M5Core2 is an easy Evil portal and rogue app deployement software designed to work on M5Stack Core2.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## Features
|
||||||
|
|
||||||
|
* **WiFi Network Scanning**: Identify and display nearby WiFi networks.
|
||||||
|
* **Network Cloning**: Check information and replicate networks for in-depth analysis.
|
||||||
|
* **Captive Portal Management**: Create and operate a captive portal to prompt users with a page upon connection.
|
||||||
|
* **Credential Handling**: Capture and manage portal credentials.
|
||||||
|
* **Remote Web Server**: Monitor the device remotely via a simple web interface that can provide credentials and upload portal that store file on SD card.
|
||||||
|
* **Sniffing probes**: Sniff and store on SD near probes.
|
||||||
|
* **Karma Attack**: Try a simple Karma Attack on a captured probe.
|
||||||
|
* **Automated Karma Attack**: Try Karma Attack on near probe automatically
|
||||||
|
|
||||||
|
|
||||||
|
## Firmwares
|
||||||
|
|
||||||
|
* Firmware: [7h30th3r0n3/Evil-M5Core2](https://github.com/7h30th3r0n3/Evil-M5Core2)
|
||||||
|
|
||||||
|
**Requirements**:
|
||||||
|
|
||||||
|
* `M5Stack` boards manager
|
||||||
|
* `M5Unified` library
|
||||||
|
|
||||||
|
|
||||||
|
**Install**:
|
||||||
|
|
||||||
|
* Connect your `M5Core2` to your computer.
|
||||||
|
* Open the `Arduino IDE` and load the provided code.
|
||||||
|
* Ensure `M5unified` and `adafruit_neopixel` libraries are installed.
|
||||||
|
* Ensure `esp32` and `M5stack` board are installed. (Error occur with esp32 `3.0.0-alpha3`, please use esp32 `v2.0.14` and below)
|
||||||
|
* Place SD file content needed on the SD card. (IMG startup and sites folder)
|
||||||
|
* Upload the script to your `M5Core2` device.
|
||||||
|
* Restart the device if needed.
|
||||||
|
|
||||||
|
|
||||||
|
## References
|
||||||
|
|
||||||
|
* [Evil-M5Core2 v1.1.3 - Serial Command - Github Project](https://github.com/7h30th3r0n3/Evil-M5Core2)
|
||||||
|
* [Evil Portal Meets Marauder on M5Stack!! Evil-M5Core2 Is the Best of Both Worlds! - Talking Sasquach - 7 jan 2024](https://youtu.be/jcVm4cysmnE)
|
||||||
|
|
@ -34,8 +34,9 @@
|
||||||
|
|
||||||
## Twitch & Streaming
|
## Twitch & Streaming
|
||||||
|
|
||||||
* [Twitch/virtualabs](https://www.twitch.tv/virtualabs)
|
* [Twitch - virtualabs](https://www.twitch.tv/virtualabs)
|
||||||
* [VirtuVOD - VOD of twitch.tv/virtualabs](https://www.youtube.com/@VirtuVOD)
|
* [Youtube - VirtuVOD - VOD of twitch.tv/virtualabs](https://www.youtube.com/@VirtuVOD)
|
||||||
|
* [Youtube - WHID We Hack In Disguise](https://www.youtube.com/@whid_ninja)
|
||||||
|
|
||||||
|
|
||||||
## Books
|
## Books
|
||||||
|
|
|
||||||
|
|
@ -1,10 +1,8 @@
|
||||||
# Bluetooth
|
# Bluetooth
|
||||||
|
|
||||||
### Challenge
|
## Bluetooth configuration
|
||||||
|
|
||||||
* BLE HackMe (https://www.microsoft.com/store/apps/9N7PNVS9J1B7) - works with nRF Connect (Android), [Introduction\_to\_BLE\_security](http://smartlockpicking.com/slides/HITB\_Cyberweek\_2020\_A\_Practical\_Introduction\_to\_BLE\_security.pdf) / https://github.com/smartlockpicking/BLE\_HackMe
|
Configuration for Kali Linux
|
||||||
|
|
||||||
### Bluetooth configuration for Kali Linux
|
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
$ sudo apt-get install bluetooth blueman bluez
|
$ sudo apt-get install bluetooth blueman bluez
|
||||||
|
|
@ -13,10 +11,10 @@ $ sudo hciconfig hci0 up
|
||||||
|
|
||||||
$ sudo hcitool lescan
|
$ sudo hcitool lescan
|
||||||
00:1A:7D:DA:71:06 Ph0wn Beacon
|
00:1A:7D:DA:71:06 Ph0wn Beacon
|
||||||
25:55:84:20:73:70 (unknown
|
25:55:84:20:73:70 (unknown)
|
||||||
```
|
```
|
||||||
|
|
||||||
Apt doesn't have a recent version of bluez, recompile it with the following lines.
|
`apt` doesn't have a recent version of bluez, recompile it with the following lines.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
wget https://www.kernel.org/pub/linux/bluetooth/bluez-5.18.tar.xz
|
wget https://www.kernel.org/pub/linux/bluetooth/bluez-5.18.tar.xz
|
||||||
|
|
@ -28,42 +26,31 @@ make -j8 && sudo make install
|
||||||
sudo cp attrib/gatttool /usr/local/bin/
|
sudo cp attrib/gatttool /usr/local/bin/
|
||||||
```
|
```
|
||||||
|
|
||||||
### Enumerate services and characteristics
|
## BLE - Enumerate services and characteristics
|
||||||
|
|
||||||
> BLE is based on specification called General Attribute profile (GATT), that defines how communication/data transfer between client and server.
|
> BLE is based on specification called General Attribute profile (GATT), that defines how communication/data transfer between client and server.
|
||||||
|
|
||||||
```powershell
|
* Using [bettercap/bettercap](https://github.com/bettercap/bettercap)
|
||||||
sudo apt-get install git build-essential libglib2.0-dev python-setuptools
|
```powershell
|
||||||
git clone https://github.com/IanHarvey/bluepy.git
|
sudo bettercap -eval "net.recon off; events.stream off; ble.recon on"
|
||||||
cd bluepy
|
ble.show
|
||||||
python setup.py build
|
ble.enum 04:52:de:ad:be:ef
|
||||||
sudo python setup.py install
|
```
|
||||||
git clone git clone https://github.com/hackgnar/bleah
|
|
||||||
cd bleah
|
|
||||||
python setup.py build
|
|
||||||
sudo python setup.py install
|
|
||||||
|
|
||||||
sudo bleah -b $MAC -e
|
* Using [expliot_framework/expliot](https://expliot.readthedocs.io/en/latest/index.html)
|
||||||
```
|
```powershell
|
||||||
|
# List of Services
|
||||||
|
run ble.generic.scan -a <mac address> -s
|
||||||
|
# List of characteristics
|
||||||
|
run ble.generic.scan -a <mac address> -c
|
||||||
|
```
|
||||||
|
|
||||||
Using bettercap
|
* Using [hackgnar/bleah](https://github.com/hackgnar/bleah)
|
||||||
|
```powershell
|
||||||
|
sudo bleah -b $MAC -e
|
||||||
|
```
|
||||||
|
|
||||||
```powershell
|
Using [bluez/gatttool](https://manpages.debian.org/unstable/bluez/gatttool.1.en.html), we can enumerate the services and their characteristics, use `sudo gatttool -b $MAC -I` to have an interactive gatttool shell:
|
||||||
sudo bettercap -eval "net.recon off; events.stream off; ble.recon on"
|
|
||||||
ble.show
|
|
||||||
ble.enum 04:52:de:ad:be:ef
|
|
||||||
```
|
|
||||||
|
|
||||||
Using expliot
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
# List of Services
|
|
||||||
run ble.generic.scan -a <mac address> -s
|
|
||||||
# List of characteristics
|
|
||||||
run ble.generic.scan -a <mac address> -c
|
|
||||||
```
|
|
||||||
|
|
||||||
Using gatttool, we can enumerate the services and their characteristics, use `sudo gatttool -b $MAC -I` to have an interactive gatttool shell:
|
|
||||||
|
|
||||||
* Services: They are set of provided features and associated behaviors to interact with the peripheral. Each service contains a collection of characteristics.
|
* Services: They are set of provided features and associated behaviors to interact with the peripheral. Each service contains a collection of characteristics.
|
||||||
* Characteristics: Characteristics are defined attribute types that contain a single logical value
|
* Characteristics: Characteristics are defined attribute types that contain a single logical value
|
||||||
|
|
@ -83,7 +70,8 @@ handle = 0x0002, char properties = 0x20, char value handle = 0x0003, uuid = 0000
|
||||||
handle = 0x0015, char properties = 0x02, char value handle = 0x0016, uuid = 00002a00-0000-1000-8000-00805f9b34fb
|
handle = 0x0015, char properties = 0x02, char value handle = 0x0016, uuid = 00002a00-0000-1000-8000-00805f9b34fb
|
||||||
```
|
```
|
||||||
|
|
||||||
### Read BLE data
|
|
||||||
|
## BLE - Read data
|
||||||
|
|
||||||
Read data with gatttool
|
Read data with gatttool
|
||||||
|
|
||||||
|
|
@ -103,47 +91,50 @@ Characteristic value/descriptor: 44 65 63 72 79 70 74 20 74 68 65 20 6d 65 73 73
|
||||||
$ gatttool -b $MAC --char-read -a 0x002a|awk -F':' '{print $2}'|tr -d ' '|xxd -r -p;printf '\n'
|
$ gatttool -b $MAC --char-read -a 0x002a|awk -F':' '{print $2}'|tr -d ' '|xxd -r -p;printf '\n'
|
||||||
```
|
```
|
||||||
|
|
||||||
### Read BLE notification/indication
|
## BLE - Read notification/indication
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
$ gatttool -b $MAC -a 0x0040 --char-write-req --value=0100 --listen
|
$ gatttool -b $MAC -a 0x0040 --char-write-req --value=0100 --listen
|
||||||
$ gatttool -b $MAC -a 0x0044 --char-write-req --value=0200 --listen
|
$ gatttool -b $MAC -a 0x0044 --char-write-req --value=0200 --listen
|
||||||
```
|
```
|
||||||
|
|
||||||
### Write BLE data
|
|
||||||
|
|
||||||
Write data with bettercap
|
## BLE - Write data
|
||||||
|
|
||||||
```powershell
|
* Using [bettercap/bettercap](https://github.com/bettercap/bettercap)
|
||||||
ble.recon on
|
```powershell
|
||||||
ble.write 04:52:de:ad:be:ef 234bfbd5e3b34536a3fe723620d4b78d ffffffffffffffff
|
ble.recon on
|
||||||
```
|
ble.write 04:52:de:ad:be:ef 234bfbd5e3b34536a3fe723620d4b78d ffffffffffffffff
|
||||||
|
```
|
||||||
|
|
||||||
Write data with gatttool
|
* Using [bluez/gatttool](#)
|
||||||
|
```powershell
|
||||||
|
$ gatttool -b $MAC --char-write-req -a 0x002c -n $(echo -n "12345678901234567890"|xxd -ps)
|
||||||
|
|
||||||
```powershell
|
# With char-write, we perform a Write Command and don't expect a response from the server
|
||||||
$ gatttool -b $MAC --char-write-req -a 0x002c -n $(echo -n "12345678901234567890"|xxd -ps)
|
# With char-write-req, we perform a Write Request and expect a response from the server
|
||||||
|
$ gatttool -b $MAC -a 0x0050 --char-write-req --value=$(echo -n 'hello' | xxd -p)
|
||||||
|
|
||||||
# With char-write, we perform a Write Command and don't expect a response from the server
|
# inside gatttool shell
|
||||||
# With char-write-req, we perform a Write Request and expect a response from the server
|
[00:1A:7D:DA:71:06][LE]> char-write-req 0x000c 476f6f64205061646177616e21212121
|
||||||
$ gatttool -b $MAC -a 0x0050 --char-write-req --value=$(echo -n 'hello' | xxd -p)
|
[00:1A:7D:DA:71:06][LE]> char-read-hnd 0x000c
|
||||||
|
Characteristic value/descriptor: 43 6f 6e [...] 2e
|
||||||
|
```
|
||||||
|
|
||||||
# inside gatttool shell
|
|
||||||
[00:1A:7D:DA:71:06][LE]> char-write-req 0x000c 476f6f64205061646177616e21212121
|
|
||||||
[00:1A:7D:DA:71:06][LE]> char-read-hnd 0x000c
|
|
||||||
Characteristic value/descriptor: 43 6f 6e [...] 2e
|
|
||||||
```
|
|
||||||
|
|
||||||
### Change Bluetooth MAC
|
## Bluetooth MAC
|
||||||
|
|
||||||
|
Change the Bluetooth MAC address
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
$ bdaddr -r 11:22:33:44:55:66
|
$ bdaddr -r 11:22:33:44:55:66
|
||||||
$ gatttool -I -b E8:77:6D:8B:09:96 -t random
|
$ gatttool -I -b E8:77:6D:8B:09:96 -t random
|
||||||
```
|
```
|
||||||
|
|
||||||
### Sniff Bluetooth communication
|
|
||||||
|
|
||||||
#### Using Ubertooth
|
## Sniff Bluetooth communication
|
||||||
|
|
||||||
|
### Using Ubertooth
|
||||||
|
|
||||||
:warning: You need 3 ubertooth.
|
:warning: You need 3 ubertooth.
|
||||||
|
|
||||||
|
|
@ -153,16 +144,28 @@ ubertooth-btle -U 1 -A 38 -f -c bulb_38.pcap
|
||||||
ubertooth-btle -U 2 -A 39 -f -c bulb_39.pcap
|
ubertooth-btle -U 2 -A 39 -f -c bulb_39.pcap
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Using Micro::Bit
|
### Using Micro::Bit
|
||||||
|
|
||||||
* https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEF%20CON%2025%20-%20Damien-Cauquil-Weaponizing-the-BBC-MicroBit.pdf
|
* [WEAPONIZING THE BBC MICRO:BIT - DAMIEN CAUQUIL / VIRTUALABS - DEF CON 25 - JULY 28, 2017](https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEF%20CON%2025%20-%20Damien-Cauquil-Weaponizing-the-BBC-MicroBit.pdf)
|
||||||
|
|
||||||
#### Using Android HCI
|
|
||||||
|
### Using Android HCI
|
||||||
|
|
||||||
Enable the Bluetooth HCI log on the device via Developer Options—also from the SDK, there is a helpful tool called the **Bluetooth HCI snoop log** (available after version 4.4)
|
Enable the Bluetooth HCI log on the device via Developer Options—also from the SDK, there is a helpful tool called the **Bluetooth HCI snoop log** (available after version 4.4)
|
||||||
|
|
||||||
> It works like a hook in the stack to capture all the HCI packets in a file. For most Android devices, the log file is at /sdcard/btsnoop\_hci.log or /sdcard/oem\_log/btsnoop/
|
> It works like a hook in the stack to capture all the HCI packets in a file. For most Android devices, the log file is at `/sdcard/btsnoop_hci.log` or `/sdcard/oem_log/btsnoop/`
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
$ adb pull /sdcard/oem_log/btsnoop/<your log file>.log
|
$ adb pull /sdcard/oem_log/btsnoop/<your log file>.log
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
## Challenges
|
||||||
|
|
||||||
|
* [BLE HackMe](https://www.microsoft.com/store/apps/9N7PNVS9J1B7) - works with nRF Connect (Android),
|
||||||
|
|
||||||
|
|
||||||
|
## References
|
||||||
|
|
||||||
|
* [A Practical Introduction to Bluetooth Low Energy security without any special hardware - Slawomir Jasek - 19 November 2020](https://www.smartlockpicking.com/slides/HITB_Cyberweek_2020_A_Practical_Introduction_To_BLE_Security.pdf)
|
||||||
|
* [Denial of Pleasure: Attacking Unusual BLE Targets with a Flipper Zero - Matteo Mandolini & Luca Bongiorni](https://www.whid.ninja/blog/denial-of-pleasure-attacking-unusual-ble-targets-with-a-flipper-zero)
|
||||||
|
|
@ -8,7 +8,7 @@
|
||||||
* [riverloopsec/killerbee](https://github.com/riverloopsec/killerbee) - IEEE 802.15.4/ZigBee Security Research Toolkit
|
* [riverloopsec/killerbee](https://github.com/riverloopsec/killerbee) - IEEE 802.15.4/ZigBee Security Research Toolkit
|
||||||
|
|
||||||
|
|
||||||
## ZigBee Default Trust Center Link Key
|
## Default Trust Center Link Key
|
||||||
|
|
||||||
Zigbee includes several layers of security, including AES-128 encryption, to ensure that data is transmitted securely across the network.
|
Zigbee includes several layers of security, including AES-128 encryption, to ensure that data is transmitted securely across the network.
|
||||||
|
|
||||||
|
|
@ -22,6 +22,7 @@ You can use it in Wireshark: Edit > Preferences > Protocols > Zigbee NWK, then "
|
||||||
|
|
||||||
Example: [CVE-2020-28952 - Athom Homey Static and Well-known Keys](https://yougottahackthat.com/blog/1260/athom-homey-security-static-and-well-known-keys-cve-2020-28952)
|
Example: [CVE-2020-28952 - Athom Homey Static and Well-known Keys](https://yougottahackthat.com/blog/1260/athom-homey-security-static-and-well-known-keys-cve-2020-28952)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
* [AN1233: Zigbee Security - Silabs](https://www.silabs.com/documents/public/application-notes/an1233-zigbee-security.pdf)
|
* [AN1233: Zigbee Security - Silabs](https://www.silabs.com/documents/public/application-notes/an1233-zigbee-security.pdf)
|
||||||
|
|
|
||||||
Loading…
Reference in New Issue