|
|
||
|---|---|---|
| .. | ||
| docs | ||
| README.md | ||
| payload.txt | ||
README.md
Defend Yourself From CVE-2023-23397
This script allows you to set the Firewall rule that will allow you to defend against CVE-2023-23397.
Category: Credentials
I decided to set Credentials as the category because of the type of CVE.
Index
Payload Description
This script allows you to set the Firewall rule that will allow you to defend against CVE-2023-23397.
Open a PowerShell, set the Firewall rule trough NetSecurity module.
CVE-2023-23397 Description
Summary
Microsoft Threat Intelligence discovered limited, targeted abuse of a vulnerability in Microsoft Outlook for Windows that allows for new technology LAN manager (NTLM) credential theft to an untrusted network, such as the Internet. Microsoft has released CVE-2023-23397 to address the critical elevation of privilege (EoP) vulnerability affecting Microsoft Outlook for Windows. We strongly recommend all customers update Microsoft Outlook for Windows to remain secure.
Impacted Products
All supported versions of Microsoft Outlook for Windows are affected. Other versions of Microsoft Outlook such as Android, iOS, Mac, as well as Outlook on the web and other M365 services are not affected.
Technical Details
CVE-2023-23397 is a critical EoP vulnerability in Microsoft Outlook that is triggered when an attacker sends a message with an extended MAPI property with a UNC path to an SMB (TCP 445) share on a threat actor-controlled server on an untrusted network. No user interaction is required.
The threat actor is using a connection to the remote SMB server sends the user’s NTLM negotiation message, which the attacker can then relay for authentication against other systems that support NTLM authentication.
Note
Tested on:
- Windows 11 Eng
Dependencies
- ExecutionPolicy Bypass
Settings
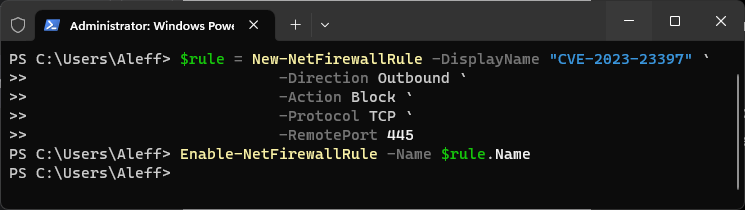
In this payload, I created a new firewall rule called "CVE-2023-23397". The direction is set to "Outbound," the action is "Block" (block traffic), the protocol is "TCP," and the remote port is 445 (SMB). Next, the rule is enabled using the Enable-NetFirewallRule cmdlet by specifying the name of the previously created rule.
Remember that you must run PowerShell with administrative privileges to create and manage firewall rules.
Administrative Privileges
- I used the Payload Starting a PowerShell with administrator permissions in Windows 10/11 by Hak5 Payloads
DELAY 1000
GUI x
DELAY 500
STRING a
DELAY 500
LEFT_ARROW
DELAY 500
ENTER