|
|
||
|---|---|---|
| .github/workflows | ||
| cmd/nuclei | ||
| internal/runner | ||
| pkg | ||
| static | ||
| .gitignore | ||
| .goreleaser.yml | ||
| Dockerfile | ||
| LICENSE | ||
| README.md | ||
| THANKS.md | ||
| go.mod | ||
| go.sum | ||
README.md
Nuclei is a fast tool for configurable targeted scanning based on templates offering massive extensibility and ease of use.
Nuclei is used to send requests across targets based on a template leading to zero false positives and providing effective scanning for known paths. Main use cases for nuclei are during initial reconnaissance phase to quickly check for low hanging fruits or CVEs across targets that are known and easily detectable. It uses retryablehttp-go library designed to handle various errors and retries in case of blocking by WAFs, this is also one of our core modules from custom-queries.
We have also open-sourced a dedicated repository to maintain various type of templates, we hope that you will contribute there too. Templates are provided in hopes that these will be useful and will allow everyone to build their own templates for the scanner. Checkout the guide at GUIDE.md for a primer on nuclei templates.
Resources
Features
- Simple and modular code base making it easy to contribute.
- Fast And fully configurable using a template based engine.
- Handles edge cases doing retries, backoffs etc for handling WAFs.
- Smart matching functionality for zero false positive scanning.
Usage
nuclei -h
This will display help for the tool. Here are all the switches it supports.
| Flag | Description | Example |
|---|---|---|
| -c | Number of concurrent requests (default 10) | nuclei -c 100 |
| -l | List of urls to run templates | nuclei -l urls.txt |
| -target | Target to scan using templates | nuclei -target hxxps://example.com |
| -t | Templates input file/files to check across hosts | nuclei -t git-core.yaml |
| -t | Templates input file/files to check across hosts | nuclei -t nuclei-templates/cves/ |
| -nC | Don't Use colors in output | nuclei -nC |
| -json | Prints and write output in json format | nuclei -json |
| -o | File to save output result (optional) | nuclei -o output.txt |
| -silent | Show only found results in output | nuclei -silent |
| -retries | Number of times to retry a failed request (default 1) | nuclei -retries 1 |
| -timeout | Seconds to wait before timeout (default 5) | nuclei -timeout 5 |
| -debug | Allow debugging of request/responses. | nuclei -debug |
| -update-templates | Download and updates nuclei templates | nuclei -update-templates |
| -update-directory | Directory for storing nuclei-templates(optional) | nuclei -update-directory templates |
| -v | Shows verbose output of all sent requests | nuclei -v |
| -version | Show version of nuclei | nuclei -version |
| -proxy-url | Proxy URL | nuclei -proxy-url hxxp://127.0.0.1:8080 |
| -proxy-socks-url | Socks proxy URL | nuclei -proxy-socks-url socks5://127.0.0.1:8080 |
| -H | Custom Header | nuclei -H "x-bug-bounty: hacker" |
Installation Instructions
From Binary
The installation is easy. You can download the pre-built binaries for your platform from the Releases page. Extract them using tar, move it to your $PATHand you're ready to go.
> tar -xzvf nuclei-linux-amd64.tar.gz
> mv nuclei /usr/bin/
> nuclei -h
From Source
nuclei requires go1.13+ to install successfully. Run the following command to get the repo -
> GO111MODULE=on go get -u -v github.com/projectdiscovery/nuclei/cmd/nuclei
In order to update the tool, you can use -u flag with go get command.
Running in a Docker Container
You can use the nuclei dockerhub image. Simply run -
> docker pull projectdiscovery/nuclei
- After downloading or building the container, run the following:
> docker run -it projectdiscovery/nuclei
For example, this will run the tool against all the hosts in urls.txt and output the results to your host file system:
> cat urls.txt | docker run -v /path-to-nuclei-templates:/go/src/app/ -i projectdiscovery/nuclei -t ./files/git-config.yaml > results.txt
Remember to change /path-to-nuclei-templates to the real path on your host file system.
Nuclei templates
You can download or update the nuclei templates using update-templates flag.
> nuclei -update-templates
or download it from nuclei templates Github project.
> git clone https://github.com/projectdiscovery/nuclei-templates.git
Running nuclei
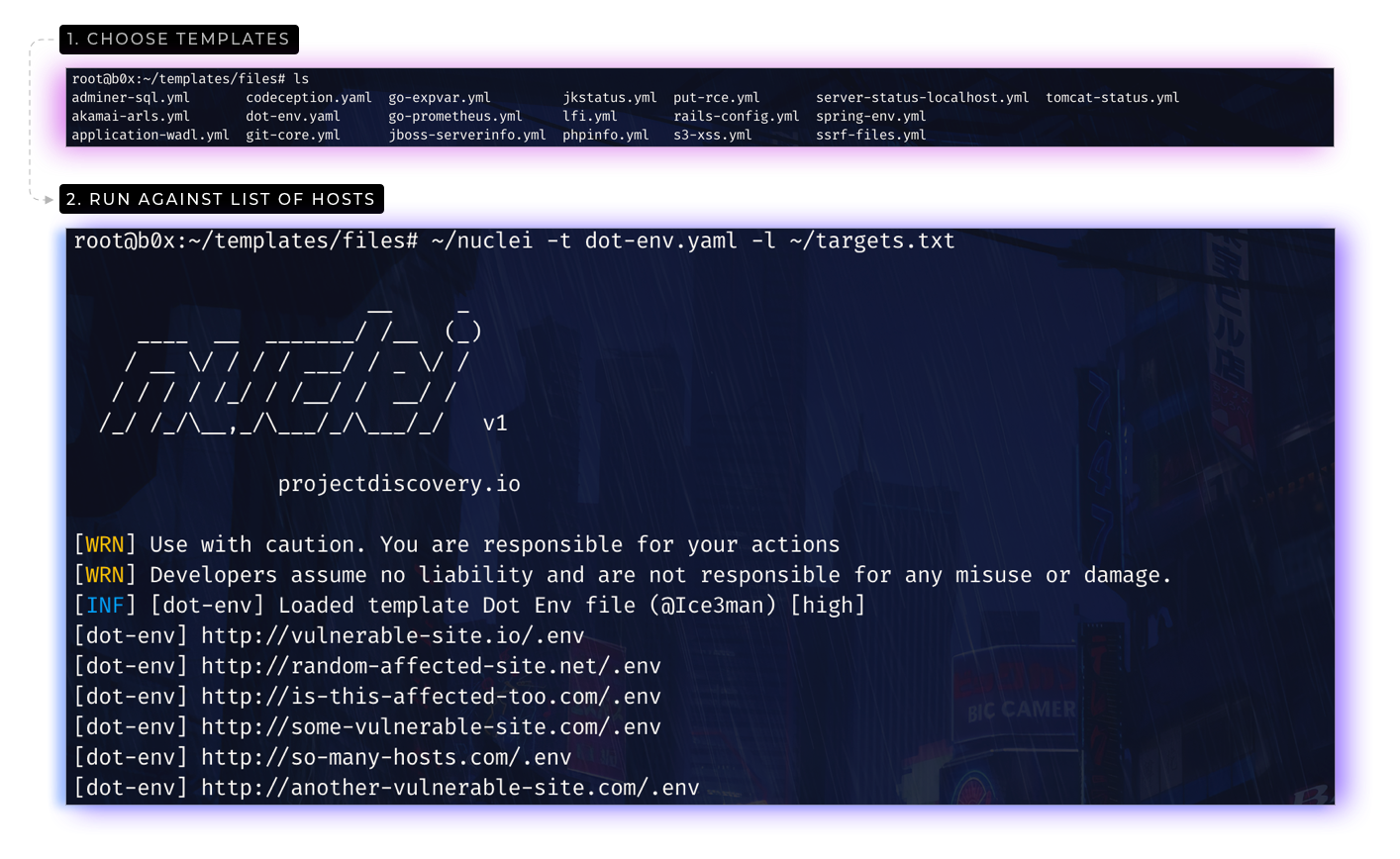
1. Running nuclei with a single template.
This will run the tool against all the hosts in urls.txt and returns the matched results.
> nuclei -l urls.txt -t files/git-core.yaml -o results.txt
You can also pass the list of hosts at standard input (STDIN). This allows for easy integration in automation pipelines.
This will run the tool against all the hosts in urls.txt and returns the matched results.
> cat urls.txt | nuclei -t files/git-core.yaml -o results.txt
2. Running nuclei with multiple templates.
This will run the tool against all the hosts in urls.txt with all the templates in the path-to-templates directory and returns the matched results.
> nuclei -l urls.txt -t cves/ -o results.txt
3. Automating nuclei with subfinder and any other similar tool.
> subfinder -d hackerone.com -silent | httpx -silent | nuclei -t cves/ -o results.txt
Please refer to this guide to build your own custom templates.
Thanks
nuclei is made with 🖤 by the projectdiscovery team. Community contributions have made the project what it is. See the Thanks.md file for more details. Do also check out these similar awesome projects that may fit in your workflow:
https://portswigger.net/burp
https://github.com/ffuf/ffuf
https://github.com/jaeles-project/jaeles
https://github.com/ameenmaali/qsfuzz
https://github.com/proabiral/inception
https://github.com/hannob/snallygaster