mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2025-01-18 17:28:49 +00:00
Merge pull request #676 from dahalsharad/add-wcd-exploit-description-and-image
added Web Cache Deception exploit, description and demonstrative image
This commit is contained in:
commit
a71a793648
BIN
Web Cache Deception/Images/wcd.jpg
Normal file
BIN
Web Cache Deception/Images/wcd.jpg
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 106 KiB |
@ -1,4 +1,5 @@
|
||||
# Web Cache Deception
|
||||
> Web Cache Deception (WCD) is a security vulnerability that occurs when a web server or caching proxy misinterprets a client's request for a web resource and subsequently serves a different resource, which may often be more sensitive or private, after caching it.
|
||||
|
||||
## Summary
|
||||
|
||||
@ -18,11 +19,19 @@
|
||||
|
||||
## Exploit
|
||||
|
||||
1. Browser requests a resource such as `http://www.example.com/home.php/non-existent.css`.
|
||||
2. Server returns the content of `http://www.example.com/home.php`, most probably with HTTP caching headers that instruct to not cache this page.
|
||||
3. The response goes through the proxy.
|
||||
4. The proxy identifies that the file has a css extension.
|
||||
5. Under the cache directory, the proxy creates a directory named home.php, and caches the imposter "CSS" file (non-existent.css) inside.
|
||||
Example of Web Cache Deception:
|
||||
|
||||
Imagine an attacker lures a logged-in victim into accessing `http://www.example.com/home.php/non-existent.css`
|
||||
|
||||
1. The victim's browser requests the resource `http://www.example.com/home.php/non-existent.css`
|
||||
2. The requested resource is searched for in the cache server, but it's not found (resource not in cache).
|
||||
3. The request is then forwarded to the main server.
|
||||
4. The main server returns the content of `http://www.example.com/home.php`, most probably with HTTP caching headers that instruct not to cache this page.
|
||||
5. The response passes through the cache server.
|
||||
6. The cache server identifies that the file has a CSS extension.
|
||||
7. Under the cache directory, the cache server creates a directory named home.php and caches the imposter "CSS" file (non-existent.css) inside it.
|
||||
8. When the attacker requests `http://www.example.com/home.php/non-existent.css`, the request is sent to the cache server, and the cache server returns the cached file with the victim's sensitive `home.php` data.
|
||||

|
||||
|
||||
|
||||
### Methodology - Caching Sensitive Data
|
||||
@ -35,7 +44,7 @@
|
||||
5. The content of the cache is displayed
|
||||
|
||||
Video of the attack by Omer Gil - Web Cache Deception Attack in PayPal Home Page
|
||||
[](https://vimeo.com/249130093)
|
||||
[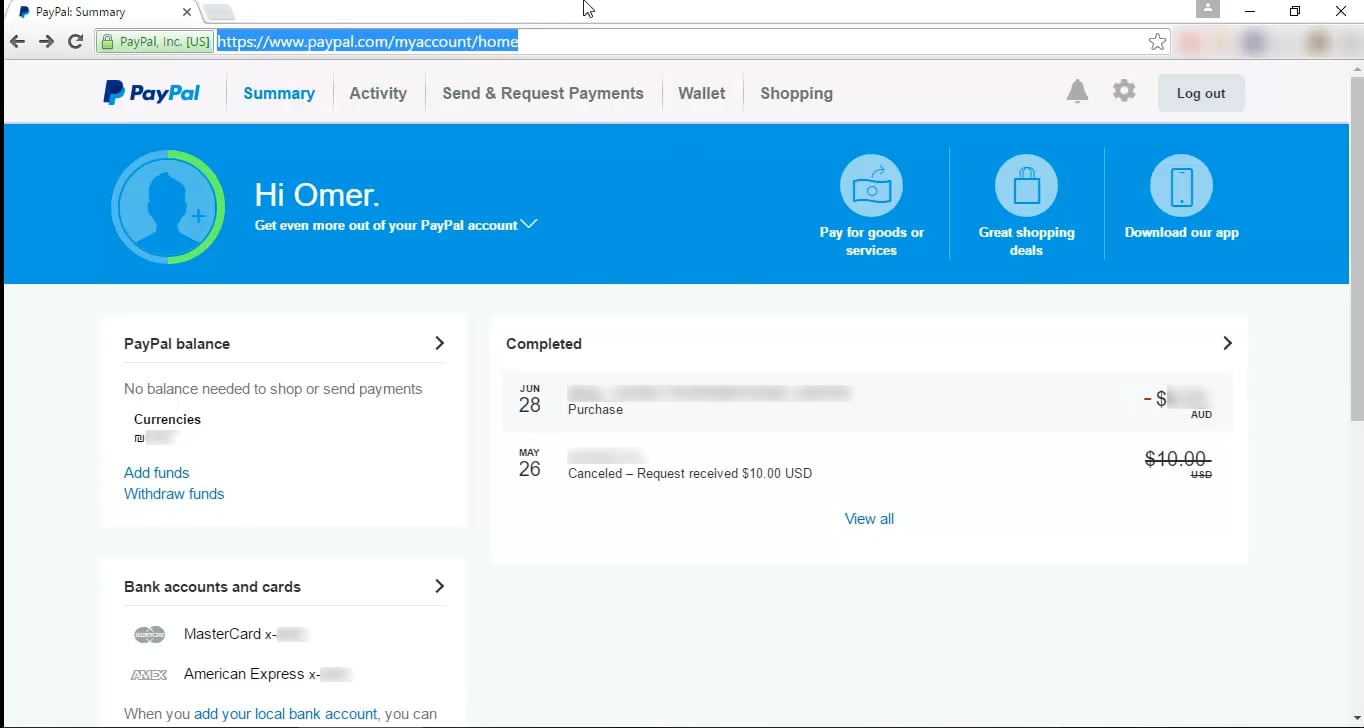](https://vimeo.com/249130093)
|
||||
|
||||
**Example 2** - Web Cache Deception on OpenAI
|
||||
1. Attacker crafts a dedicated .css path of the `/api/auth/session` endpoint.
|
||||
@ -92,6 +101,7 @@ CloudFlare has a list of default extensions that gets cached behind their Load B
|
||||
| CLASS | EXE | JS | PICT | SWF | XLS | XLSX |
|
||||
|
||||
|
||||
|
||||
## Labs
|
||||
|
||||
* [PortSwigger Labs for Web cache deception](https://portswigger.net/web-security/all-labs#web-cache-poisoning)
|
||||
|
||||
Loading…
Reference in New Issue
Block a user