| .. | ||
| decrypt.ps1 | ||
| Readme.md | ||
| Result.png | ||
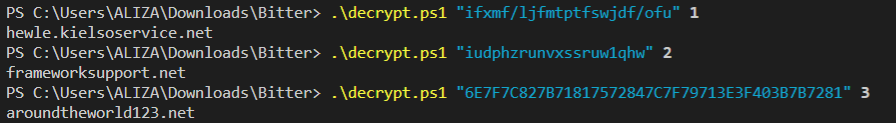
Tool for decoding the encoded strings of ArtraDownloader
This tool decoding the encoded strings of the three variants of ArtraDownloader used by the APT Bitter group (August 2019)
The following syntax is the next :
> decrypt.ps1 "[Encoded string]" [Num Variant]