# SideWinder same targets, same TTPs, time to counter-attack !
## Table of Contents
* [Malware analysis](#Malware-analysis)
* [Threat Intelligence](#Intel)
* [Cyber kill chain](#Cyber-kill-chain)
* [Indicators Of Compromise (IOC)](#IOC)
* [Yara Rules](#Yara)
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
* [Knowledge Graph](#Knowledge)
* [Links](#Links)
+ [Original Tweet](#tweet)
+ [Link Anyrun](#Links-Anyrun)
+ [Ressources](#Ressources)
Malware analysis
The initial vector
![]()
Threat Intelligence
Cyber kill chain
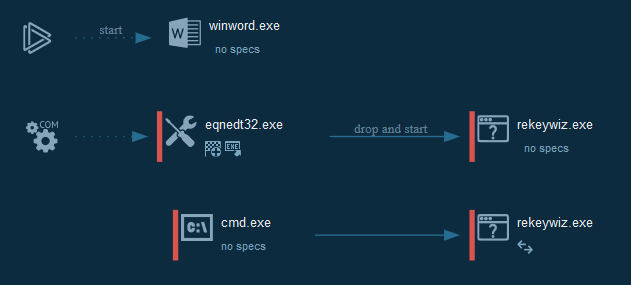
The process graph resume cyber kill chains used by the attacker :
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
|Indicator|Description|
| ------------- |:-------------:|
|||
The IOC can be exported in JSON
References MITRE ATT&CK Matrix
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
|Execution|Execution through Module Load
Exploitation for Client Execution|https://attack.mitre.org/techniques/T1129/
https://attack.mitre.org/techniques/T1203/|
|Persistence|Registry Run Keys / Startup Folder|https://attack.mitre.org/techniques/T1060/|
|Discovery|Query Registry|https://attack.mitre.org/techniques/T1012/|
This can be exported as JSON format Export in JSON
Yara Rules
A list of YARA Rule is available here
Knowledge Graph
The following diagram shows the relationships of the techniques used by the groups and their corresponding malware:
![]()
Links
Original tweet:
* [https://twitter.com/RedDrip7/status/1206898954383740929](https://twitter.com/RedDrip7/status/1206898954383740929)
Links Anyrun:
* [Policy on Embedded Systems.doc](https://app.any.run/tasks/1fac2867-012c-4298-af36-a4810d9b72db)
* [adsfa.rtf](https://app.any.run/tasks/72ec8c7c-5542-48fe-8400-ba840de9c0bd)
* [out.rtf](https://app.any.run/tasks/34c8345c-b661-4ca5-ba15-58dcc4e6d968)
Resources :
* [The SideWinder campaign continue](https://github.com/StrangerealIntel/CyberThreatIntel/blob/master/Indian/APT/SideWinder/11-10-2019/Analysis.md)
