From f5acc04247fe54ca9fd9ebdb1e179351031dbb60 Mon Sep 17 00:00:00 2001
From: StrangerealIntel <54320855+StrangerealIntel@users.noreply.github.com>
Date: Thu, 26 Sep 2019 00:47:41 +0200
Subject: [PATCH] Update Malware analysis.md
---
Indian/APT/Donot/17-09-19/Malware analysis.md | 5 +++--
1 file changed, 3 insertions(+), 2 deletions(-)
diff --git a/Indian/APT/Donot/17-09-19/Malware analysis.md b/Indian/APT/Donot/17-09-19/Malware analysis.md
index 8dacfaf..ee6d871 100644
--- a/Indian/APT/Donot/17-09-19/Malware analysis.md
+++ b/Indian/APT/Donot/17-09-19/Malware analysis.md
@@ -119,9 +119,10 @@

## Cyber kill chain
-###### The process graphs resume all the cyber kill chains used by the attacker. We can note that in majority of time, this use RTF exploits as downloader and execution methods.
+###### The process graphs resume all the cyber kill chains used by the attacker.

-
+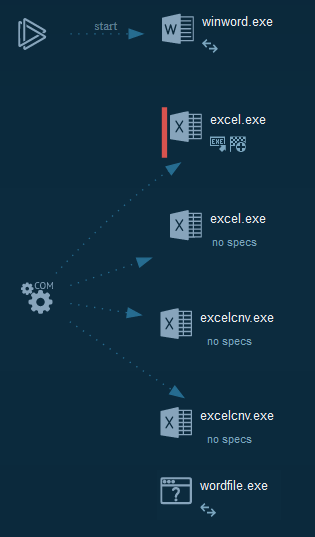
+###### We can note that in majority of time, this use RTF exploits as downloader and execution methods.
## References MITRE ATT&CK Matrix
###### List of all the references with MITRE ATT&CK Matrix