diff --git a/Indian/APT/Donot/17-09-19/Malware analysis.md b/Indian/APT/Donot/17-09-19/Malware analysis.md
index 8dacfaf..ee6d871 100644
--- a/Indian/APT/Donot/17-09-19/Malware analysis.md
+++ b/Indian/APT/Donot/17-09-19/Malware analysis.md
@@ -119,9 +119,10 @@

## Cyber kill chain
-###### The process graphs resume all the cyber kill chains used by the attacker. We can note that in majority of time, this use RTF exploits as downloader and execution methods.
+###### The process graphs resume all the cyber kill chains used by the attacker.

-
+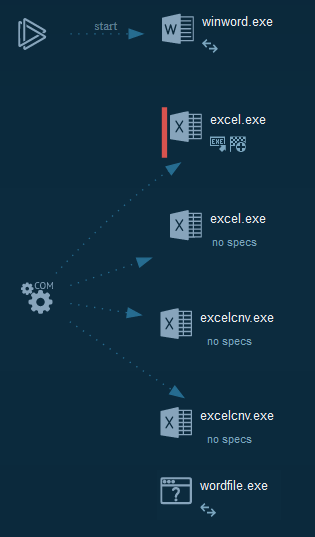
+###### We can note that in majority of time, this use RTF exploits as downloader and execution methods.
## References MITRE ATT&CK Matrix
###### List of all the references with MITRE ATT&CK Matrix