Update Malware Analysis 04-10-2019.md
This commit is contained in:
parent
b9ff1c5fab
commit
d86b2af470
@ -8,7 +8,7 @@
|
|||||||
+ [Link Anyrun](#Links-Anyrun)
|
+ [Link Anyrun](#Links-Anyrun)
|
||||||
|
|
||||||
## Malware analysis <a name="Malware-analysis"></a>
|
## Malware analysis <a name="Malware-analysis"></a>
|
||||||
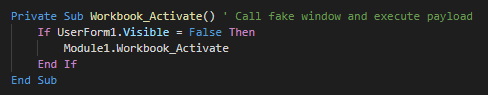
###### The inital vector is a malicious excel file who used a XLM macro (macro v4). This use an function for launch the payload when the excel windows is active (selected as primary window). As first action, this execute the module 1.
|
###### The initial vector is a malicious excel file which used an XLM macro (macro v4). This uses a function for launch the payload when the excel windows is active (selected as primary window). As first action, this executes the module 1.
|
||||||
|

|
||||||
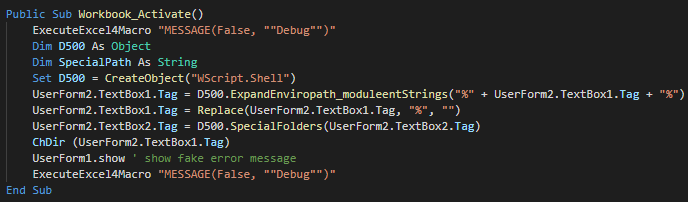
###### The function call in Module 1 create a Wscript object for change the current directory, show the fake message and push debug messages.
|
###### The function call in Module 1 create a Wscript object for change the current directory, show the fake message and push debug messages.
|
||||||
|

|
||||||
@ -24,10 +24,10 @@
|
|||||||
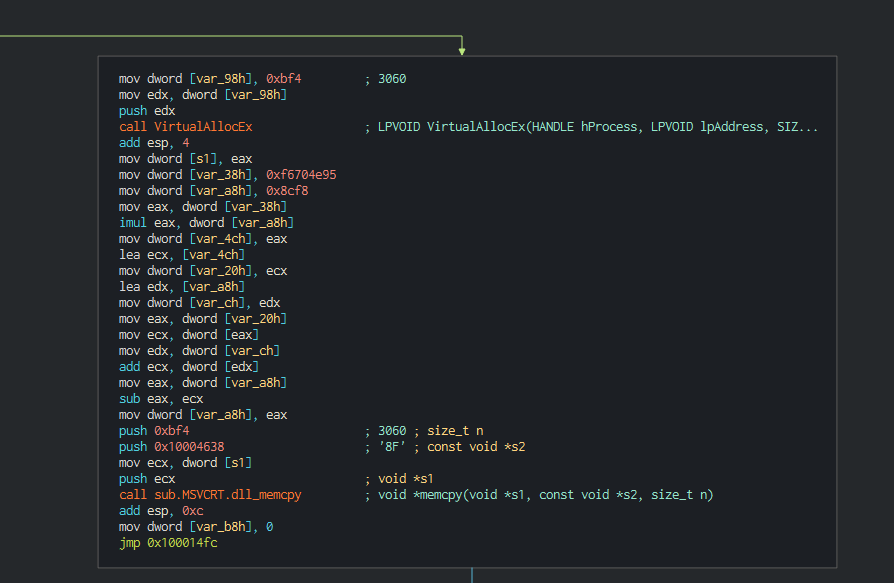
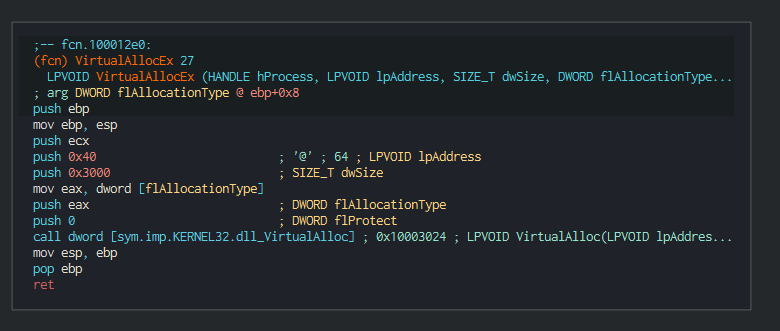
###### The implant executed push all in memory with a call of VirtualAlloc function.
|
###### The implant executed push all in memory with a call of VirtualAlloc function.
|
||||||
|

|
||||||
|

|
||||||
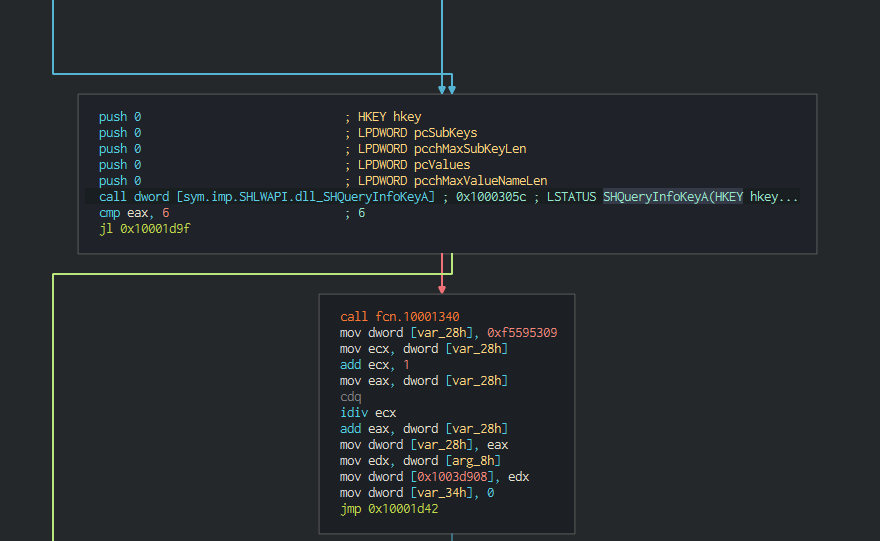
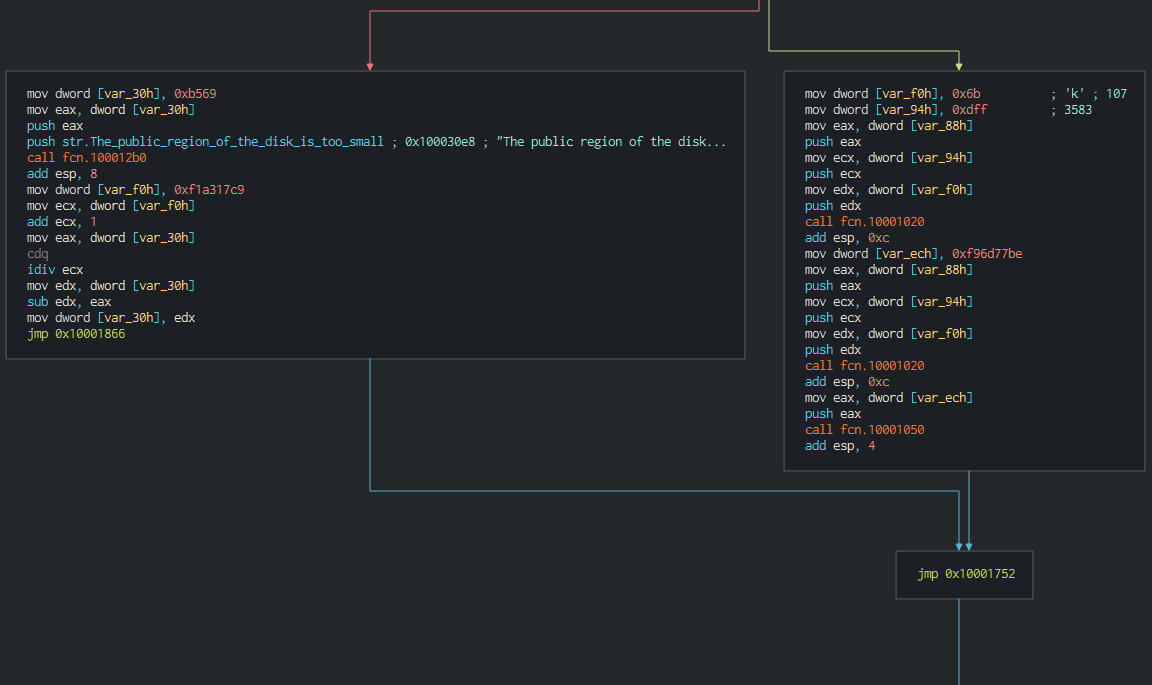
###### Once this, this check the system informations, the process executed on the computer and try to detect if this run in a sandbox (low size of the disk).
|
###### Once this, this checks the system informations, the process executed on the computer and try to detect if this run in a sandbox (low size of the disk).
|
||||||
|

|
||||||
|

|
||||||
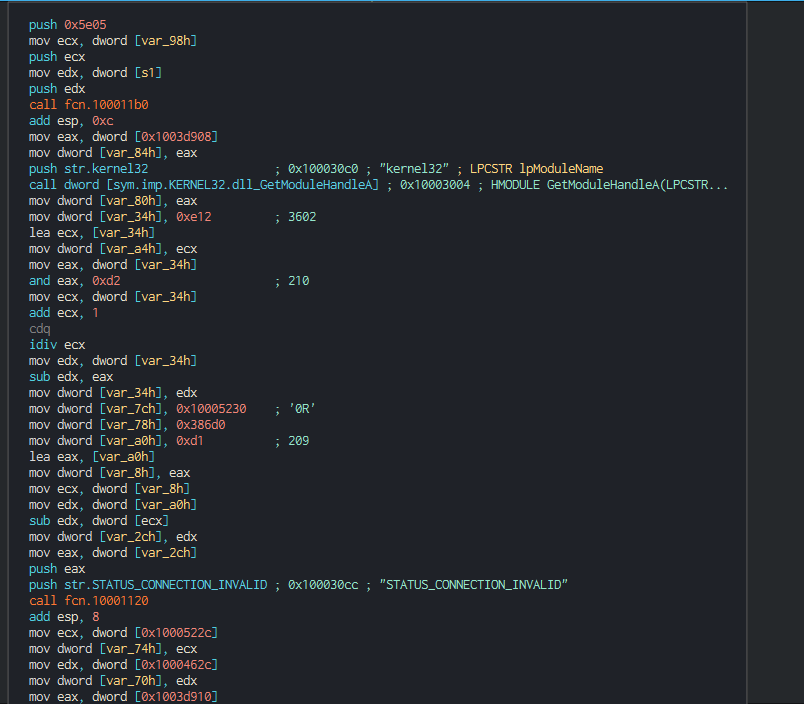
###### This send the informations to the C2 and wait the next instruction of the group.
|
###### This sends the informations to the C2 and wait for the next instruction of the group.
|
||||||
|

|
||||||
###### We can list the informations send in the following variables :
|
###### We can list the informations send in the following variables :
|
||||||
|
|
||||||
@ -38,12 +38,11 @@
|
|||||||
|&OS=|Version of the OS|
|
|&OS=|Version of the OS|
|
||||||
|&PR=|List of process (separed by %7C)|
|
|&PR=|List of process (separed by %7C)|
|
||||||
|
|
||||||
###### And is presented this way (extracted from sandbox):
|
###### And is presented this way (extracted from the sandbox):
|
||||||
|
|
||||||
``&D=User-PC&U=admin&OS=6.1&PR=Dwm.exe%7CEXCEL.EXE%7CExplorer.EXE%7Ctaskhost.exe%7Cwindanr.exe%7C``
|
``&D=User-PC&U=admin&OS=6.1&PR=Dwm.exe%7CEXCEL.EXE%7CExplorer.EXE%7Ctaskhost.exe%7Cwindanr.exe%7C``
|
||||||
|
|
||||||
###### That interesting to note that the group get only the process for see if the victim have security messures (AV, endpoint...) before launch the next step, that can be in the logic of the lastest analysis of the group to used clop ransomware.
|
###### That interesting to note that the group get only the process for see if the victim have security messures (AV, endpoint...) before launch the next step.This drop the clop ransomware if we observe the latest analysis on this subject.The group change currently the trust certificate for bypass the security messures that we can see on the analysis of [VK_Intel](https://twitter.com/vk_intel) :
|
||||||
The change currently the trust certificate for bypass the security messures, we can observed on the analysis of [VK_Intel](https://twitter.com/vk_intel) :
|
|
||||||
* [https://twitter.com/VK_Intel/status/1162810558774747137](https://twitter.com/VK_Intel/status/1162810558774747137)
|
* [https://twitter.com/VK_Intel/status/1162810558774747137](https://twitter.com/VK_Intel/status/1162810558774747137)
|
||||||
* [https://twitter.com/VK_Intel/status/1157761784582983685](https://twitter.com/VK_Intel/status/1157761784582983685)
|
* [https://twitter.com/VK_Intel/status/1157761784582983685](https://twitter.com/VK_Intel/status/1157761784582983685)
|
||||||
* [https://twitter.com/VK_Intel/status/1157742218549039105](https://twitter.com/VK_Intel/status/1157742218549039105)
|
* [https://twitter.com/VK_Intel/status/1157742218549039105](https://twitter.com/VK_Intel/status/1157742218549039105)
|
||||||
@ -51,10 +50,9 @@ The change currently the trust certificate for bypass the security messures, we
|
|||||||
* [https://twitter.com/VK_Intel/status/1145041163839266823](https://twitter.com/VK_Intel/status/1145041163839266823)
|
* [https://twitter.com/VK_Intel/status/1145041163839266823](https://twitter.com/VK_Intel/status/1145041163839266823)
|
||||||
* [https://twitter.com/VK_Intel/status/1136069755222335490](https://twitter.com/VK_Intel/status/1136069755222335490)
|
* [https://twitter.com/VK_Intel/status/1136069755222335490](https://twitter.com/VK_Intel/status/1136069755222335490)
|
||||||
|
|
||||||
###
|
|
||||||
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
||||||
###### The process graphs resume all the cyber kill chains used by the attacker.
|
###### The process graphs resume all the cyber kill chains used by the attacker.
|
||||||
![alt text]()
|

|
||||||
|
|
||||||
## References MITRE ATT&CK Matrix <a name="Ref-MITRE-ATTACK"></a>
|
## References MITRE ATT&CK Matrix <a name="Ref-MITRE-ATTACK"></a>
|
||||||
###### List of all the references with MITRE ATT&CK Matrix
|
###### List of all the references with MITRE ATT&CK Matrix
|
||||||
@ -112,6 +110,5 @@ The change currently the trust certificate for bypass the security messures, we
|
|||||||
* [https://twitter.com/KorbenD_Intel/status/1179858006584037377](https://twitter.com/KorbenD_Intel/status/1179858006584037377)
|
* [https://twitter.com/KorbenD_Intel/status/1179858006584037377](https://twitter.com/KorbenD_Intel/status/1179858006584037377)
|
||||||
* [https://twitter.com/58_158_177_102/status/1177498806016823296](https://twitter.com/58_158_177_102/status/1177498806016823296)
|
* [https://twitter.com/58_158_177_102/status/1177498806016823296](https://twitter.com/58_158_177_102/status/1177498806016823296)
|
||||||
###### Links Anyrun: <a name="Links-Anyrun"></a>
|
###### Links Anyrun: <a name="Links-Anyrun"></a>
|
||||||
###### Samples :
|
|
||||||
* [Letter 7711.xls](https://app.any.run/tasks/d3699368-76cb-4c9f-b5c5-c4e25eb2e318)
|
* [Letter 7711.xls](https://app.any.run/tasks/d3699368-76cb-4c9f-b5c5-c4e25eb2e318)
|
||||||
* [REP 7072.xls](https://app.any.run/tasks/ae70ad41-d5d7-4dca-98d2-b72bfbae45fa)
|
* [REP 7072.xls](https://app.any.run/tasks/ae70ad41-d5d7-4dca-98d2-b72bfbae45fa)
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user