Update Malware Analysis 04-10-2019.md
This commit is contained in:
parent
d9e41089a2
commit
d2e9fdf73b
@ -1,6 +1,7 @@
|
||||
# Analysis of the new TA505 campaign
|
||||
## Table of Contents
|
||||
* [Malware analysis](#Malware-analysis)
|
||||
* [Cyber Threat Intel](#Cyber-Threat-Intel)
|
||||
* [Indicators Of Compromise (IOC)](#IOC)
|
||||
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
|
||||
* [Links](#Links)
|
||||
@ -50,6 +51,13 @@
|
||||
* [https://twitter.com/VK_Intel/status/1145041163839266823](https://twitter.com/VK_Intel/status/1145041163839266823)
|
||||
* [https://twitter.com/VK_Intel/status/1136069755222335490](https://twitter.com/VK_Intel/status/1136069755222335490)
|
||||
|
||||
## Cyber Threat Intel <a name="Cyber-Threat-Intel"></a>
|
||||
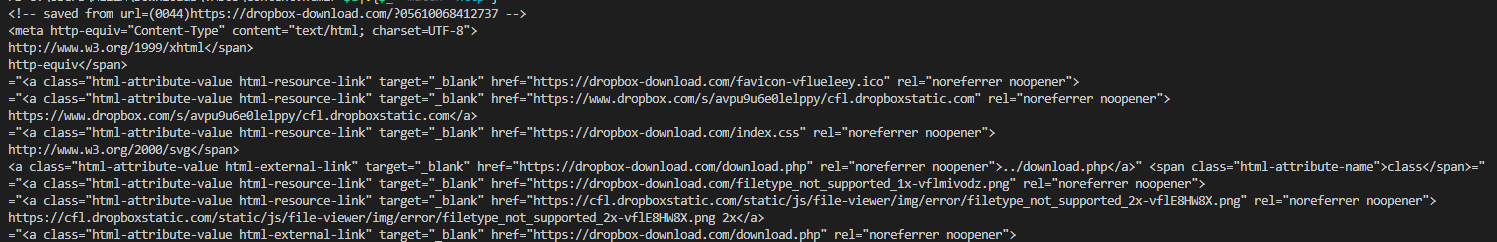
###### Recently, new domains used by the group have been spotted by [Suspicious Link](https://twitter.com/killamjr). On the HTML document, we can see that the fake page usurps dropbox in using external references and the path on the malicious excel document.
|
||||
|
||||
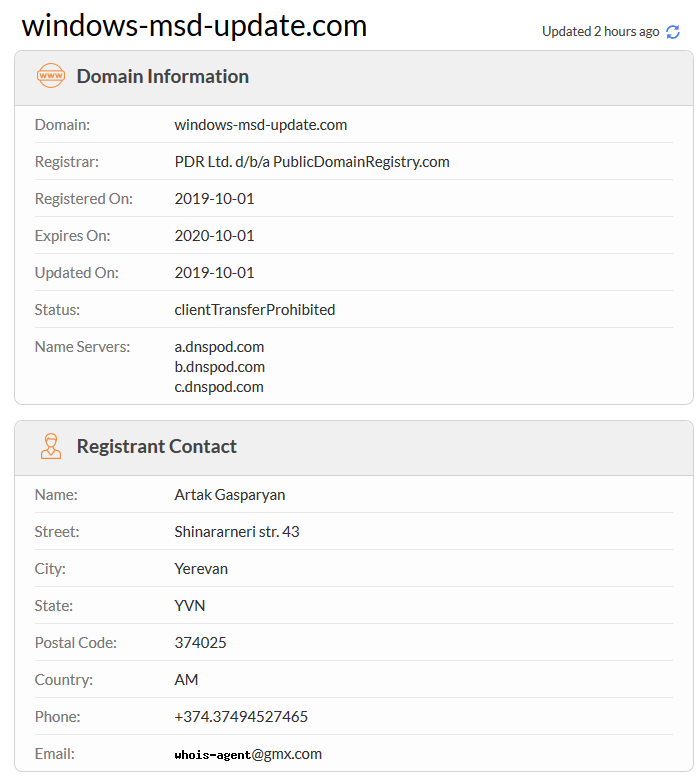
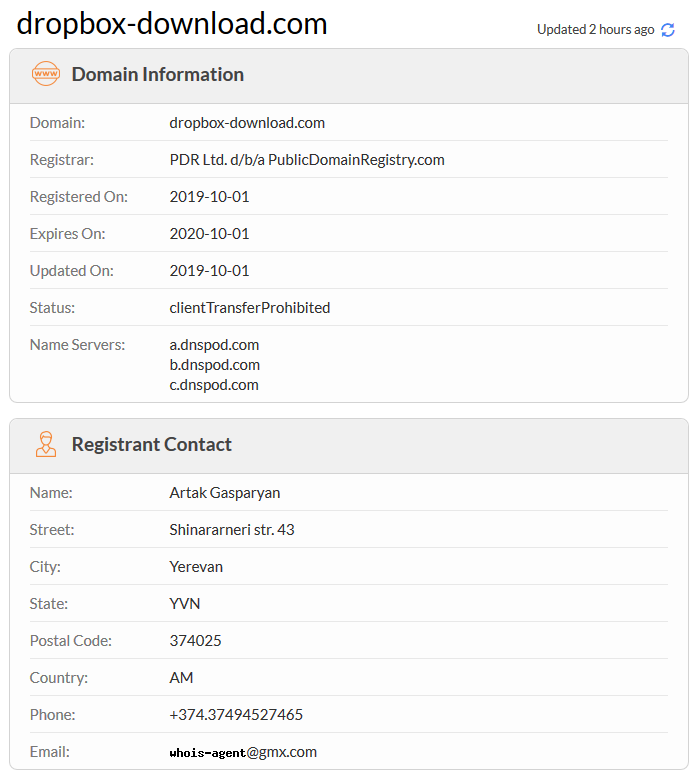
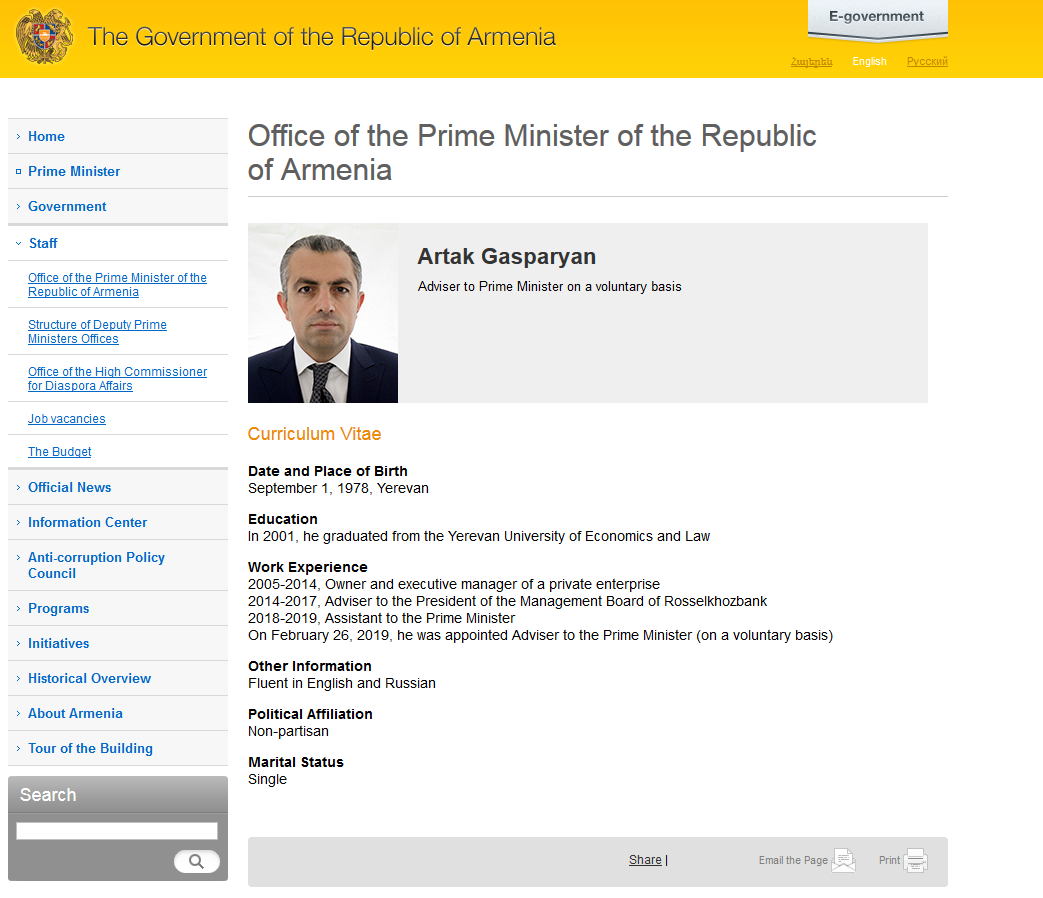
###### We can see in more that the personal informations is like the Office of the Prime Minister of the Republic of Armenia.
|
||||
|
||||
|
||||
|
||||
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
||||
###### The process graphs resume all the cyber kill chains used by the attacker.
|
||||

|
||||
@ -118,7 +126,6 @@
|
||||
|request.xls|A78E87D350C8CF3F6D7DB126C5FADD7D837AEF23DF01194FC0973561CD20818E|
|
||||
|windows-msd-update.com|Domain C2|
|
||||
|
||||
|
||||
###### This can be exported as JSON format [Export in JSON](https://raw.githubusercontent.com/StrangerealIntel/CyberThreatIntel/master/cybercriminal%20groups/TA505/04-10-2019/IOC_TA505_07-10-19.json)
|
||||
|
||||
## Links <a name="Links"></a>
|
||||
@ -126,6 +133,7 @@
|
||||
* [https://twitter.com/James_inthe_box/status/1179077549302829056](https://twitter.com/James_inthe_box/status/1179077549302829056) <a name="Original-Tweet"></a>
|
||||
* [https://twitter.com/KorbenD_Intel/status/1179858006584037377](https://twitter.com/KorbenD_Intel/status/1179858006584037377)
|
||||
* [https://twitter.com/58_158_177_102/status/1177498806016823296](https://twitter.com/58_158_177_102/status/1177498806016823296)
|
||||
* [https://twitter.com/killamjr/status/1181294324061003777](https://twitter.com/killamjr/status/1181294324061003777)
|
||||
###### Links Anyrun: <a name="Links-Anyrun"></a>
|
||||
* [Letter 7711.xls](https://app.any.run/tasks/d3699368-76cb-4c9f-b5c5-c4e25eb2e318)
|
||||
* [REP 7072.xls](https://app.any.run/tasks/ae70ad41-d5d7-4dca-98d2-b72bfbae45fa)
|
||||
|
||||
Loading…
Reference in New Issue
Block a user